Cybersecurity Training
Network Cloud Network Security Analysis Icon Icons PDF
Persuade your audience using this Network Cloud Network Security Analysis Icon Icons PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Network Cloud, Network Security, Analysis Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icon For Digital Cyber Safety And Security Report Pictures PDF
Persuade your audience using this Icon For Digital Cyber Safety And Security Report Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Report, Icon For Digital, Cyber Safety. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Security Risk Analysis Shield Software Icon Themes PDF
Persuade your audience using this Cyber Security Risk Analysis Shield Software Icon Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Risk Analysis, Shield Software Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Eight Steps Infographics To Improve Cyber Security Icons PDF
Persuade your audience using this eight steps infographics to improve cyber security icons pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including threats, knowledge, monitoring, authentication, protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
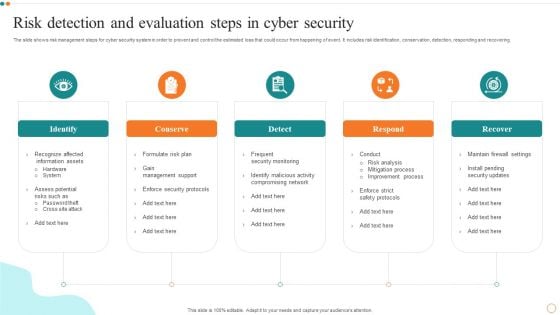
Risk Detection And Evaluation Steps In Cyber Security Designs PDF
Persuade your audience using this Risk Detection And Evaluation Steps In Cyber Security Designs PDF. This PPT design covers Five stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Detection, Evaluation Steps. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
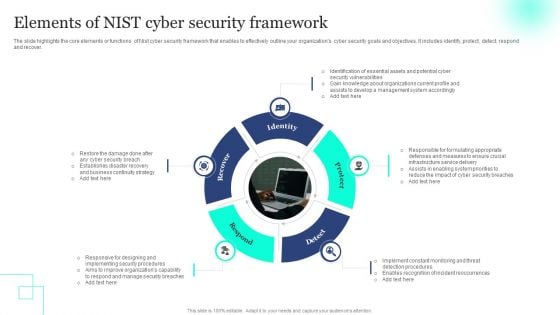
Elements Of NIST Cyber Security Framework Ideas PDF
The slide highlights the core elements or functions of Nist cyber security framework that enables to effectively outline your organizations cyber security goals and objectives. It includes identify, protect, detect, respond and recover. Persuade your audience using this Elements Of NIST Cyber Security Framework Ideas PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Reoccurrences, Vulnerabilities, Framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
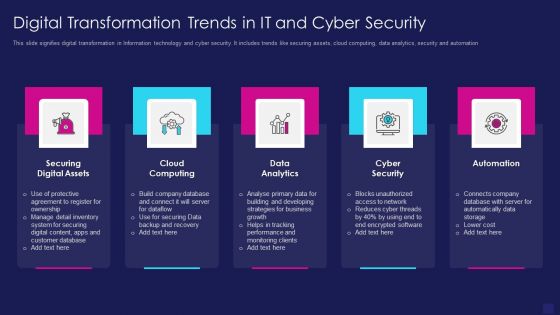
Digital Transformation Trends In It And Cyber Security Designs PDF
This slide signifies digital transformation in Information technology and cyber security. It includes trends like securing assets, cloud computing, data analytics, security and automation. Persuade your audience using this digital transformation trends in it and cyber security designs pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including securing digital assets, cloud computing, data analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
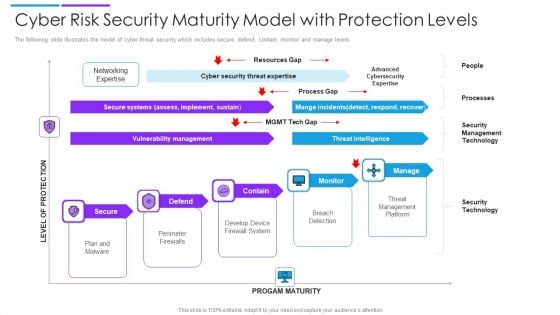
Cyber Risk Security Maturity Model With Protection Levels Mockup PDF
The following slide illustrates the model of cyber threat security which includes secure, defend, contain, monitor and manage levels. Persuade your audience using this cyber risk security maturity model with protection levels mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including secure systems, vulnerability management, threat intelligence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Best Practices For Cyber Safety At Job Safety Infographics PDF
This slide covers the best practices for cyber safety at workplace which includes protecting the data, using strong password protection, connecting to the secure wi-fi, investing in security systems, etc. Presenting best practices for cyber safety at job safety infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including protecting data, connect to secure wi fi, invest in security systems, strong password protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
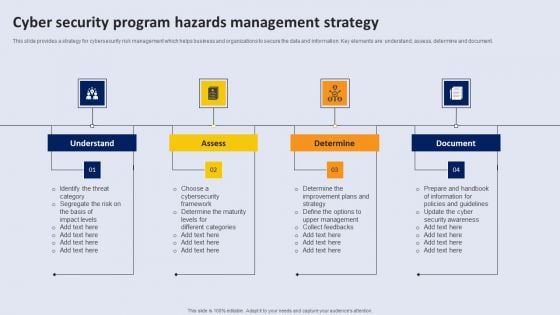
Cyber Security Program Hazards Management Strategy Topics PDF
This slide provides a strategy for cyber security risk management which helps business and organizations to secure the data and information. Key elements are understand, assess, determine and document.Persuade your audience using this Cyber Security Program Hazards Management Strategy Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Determine. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Practices For Selecting Managed Cyber Security Solutions Service Provider Ppt Professional Aids PDF
The following slide exhibits four practices for selecting managed security service provider. Expertise, cost, business requirements and testimonials are some of the practices which will help the organization in selecting trusted security providers. Persuade your audience using this Key Practices For Selecting Managed Cyber Security Solutions Service Provider Ppt Professional Aids PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Expertise, Cost, Business Requirements, Testimonials. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
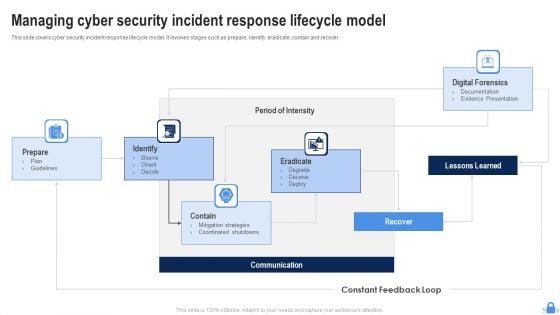
Managing Cyber Security Incident Response Lifecycle Model Ppt Graphics PDF
This slide covers cyber security incident response lifecycle model. It involves stages such as prepare, identify, eradicate, contain and recover. Persuade your audience using this Managing Cyber Security Incident Response Lifecycle Model Ppt Graphics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare, Identify, Contain, Communication, Eradicate, Lessons Learned. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
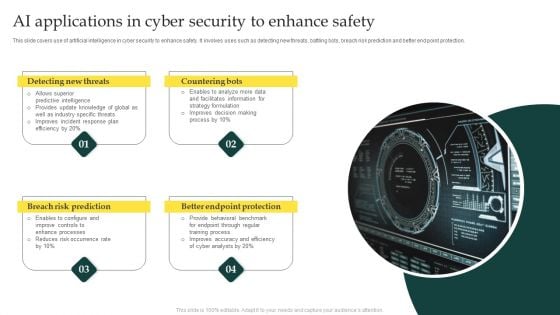
AI Applications In Cyber Security To Enhance Safety Elements PDF
This slide covers use of artificial intelligence in cyber security to enhance safety. It involves uses such as detecting new threats, battling bots, breach risk prediction and better end point protection.Persuade your audience using this AI Applications In Cyber Security To Enhance Safety Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Prediction, Endpoint Protection, Countering Bots. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
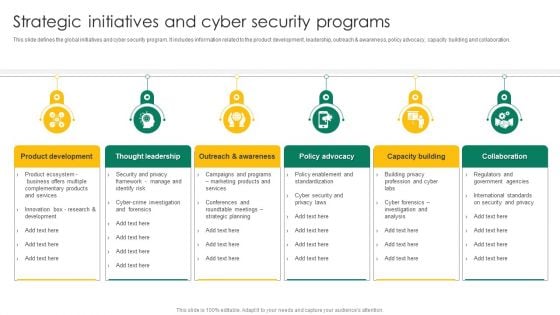
Strategic Initiatives And Cyber Security Programs Ppt Summary Picture PDF
This slide defines the global initiatives and cyber security program. it includes information related to the product development, leadership, outreach and awareness, policy advocacy, capacity building and collaboration. Persuade your audience using this Strategic Initiatives And Cyber Security Programs Ppt Summary Picture PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Product Development, Thought Leadership, Policy Advocacy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
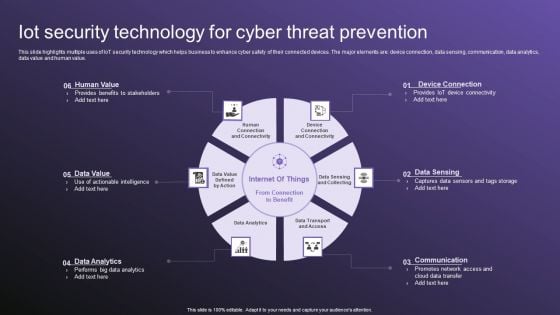
Iot Security Technology For Cyber Threat Prevention Clipart PDF
This slide highlights multiple uses of IoT security technology which helps business to enhance cyber safety of their connected devices. The major elements are device connection, data sensing, communication, data analytics, data value and human value. Persuade your audience using this Iot Security Technology For Cyber Threat Prevention Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Human Value, Data Value, Data Analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Risk Intelligence Services For Enterprise Security Icons PDF
Persuade your audience using this cyber risk intelligence services for enterprise security icons pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including incident resolution, threat protection, it services. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
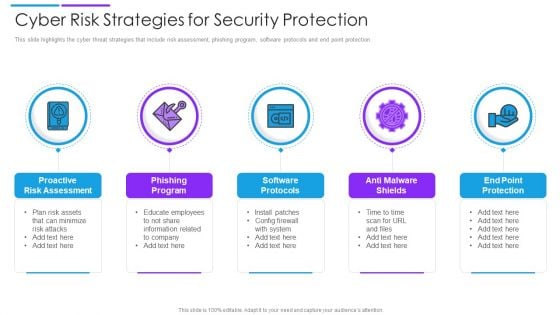
Cyber Risk Strategies For Security Protection Mockup PDF
This slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Persuade your audience using this cyber risk strategies for security protection mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including proactive risk assessment, phishing program, software protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Cyber Security Risk Assessment Process Inspiration PDF
The slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Persuade your audience using this Business Cyber Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Detect, Respond, Protect, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
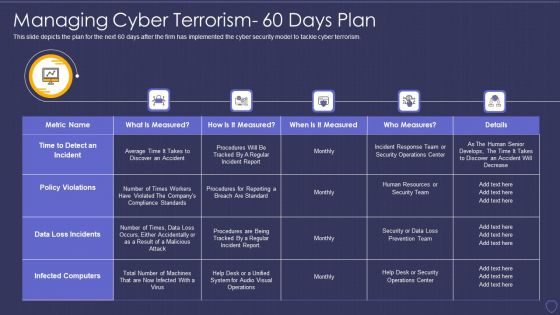
Global Cyber Terrorism Incidents On The Rise IT Managing Cyber Terrorism 60 Days Plan Professional PDF
This slide depicts the plan for the next 60 days after the firm has implemented the cyber security model to tackle cyber terrorism. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it managing cyber terrorism 60 days plan professional pdf bundle. Topics like time to detect an incident, policy violations, data loss incidents, infected computers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF
The following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Presenting this PowerPoint presentation, titled Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Computer Bug And Cyber Security Vector Illustration Ppt PowerPoint Presentation Portfolio Skills PDF
Presenting this set of slides with name computer bug and cyber security vector illustration ppt powerpoint presentation portfolio skills pdf. This is a three stage process. The stages in this process are computer bug and cyber security vector illustration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
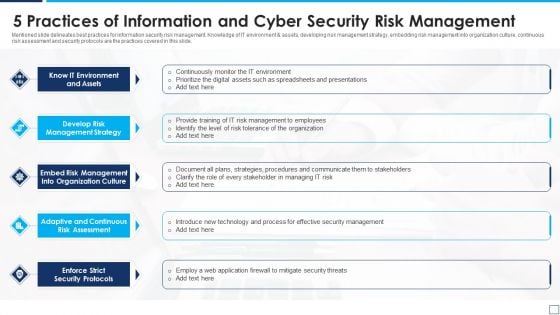
5 Practices Of Information And Cyber Security Risk Management Graphics PDF
Mentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting 5 practices of information and cyber security risk management graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including know it environment and assets, develop risk management strategy, enforce strict security protocols. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
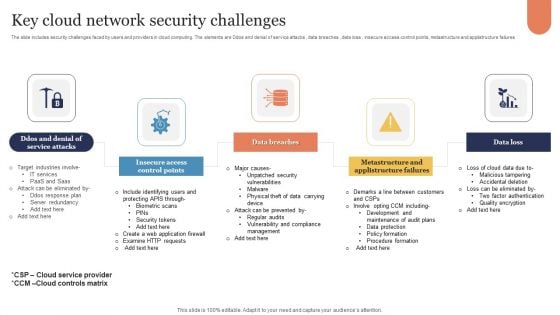
Key Cloud Network Security Challenges Sample PDF
The slide includes security challenges faced by users and providers in cloud computing. The elements are Ddos and denial of service attacks , data breaches , data loss , insecure access control points, metastructure and applistructure failures Persuade your audience using this Key Cloud Network Security Challenges Sample PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Insecure Access Control Points, Data Breaches, Data Loss. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Do you have to make sure that everyone on your team knows about any specific topic. I yes, then you should give Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
IT Network Security And Protection Vector Icon Ppt PowerPoint Presentation Gallery Slides PDF
Persuade your audience using this it network security and protection vector icon ppt powerpoint presentation gallery slides pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including it network security and protection vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
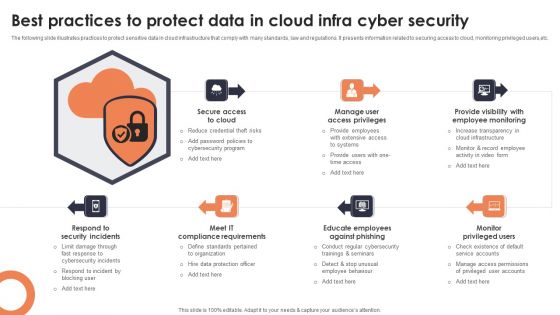
Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF
The following slide illustrates practices to protect sensitive data in cloud infrastructure that comply with many standards, law and regulations. It presents information related to securing access to cloud, monitoring privileged users,etc. Presenting Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Secure Access Cloud, Manage User Access Privileges, Provide Visibility Employee. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cyber Security Technology For Data Protection Ppt PowerPoint Presentation Ideas Visual Aids PDF
Persuade your audience using this cyber security technology for data protection ppt powerpoint presentation ideas visual aids pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including cyber security technology for data protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Security With Protection Shield Vector Icon Ppt PowerPoint Presentation File Visual Aids PDF
Persuade your audience using this cyber security with protection shield vector icon ppt powerpoint presentation file visual aids pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including cyber security with protection shield vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Managing Cyber Security Incident Response Icon Ppt Portfolio Model PDF
Persuade your audience using this IT Managing Cyber Security Incident Response Icon Ppt Portfolio Model PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Managing, Cyber Security, Incident Response, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Security Cases Action Plan Response Team Icon Ppt PowerPoint Presentation Icon Diagrams PDF
Persuade your audience using this Cyber Security Cases Action Plan Response Team Icon Ppt PowerPoint Presentation Icon Diagrams PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security, Cases Action Plan, Response Team, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
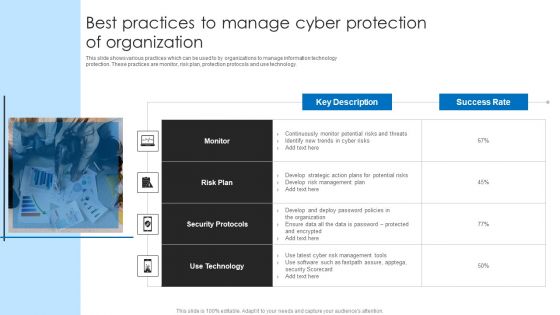
Best Practices To Manage Cyber Protection Of Organization Microsoft PDF
This slide shows various practices which can be used to by organizations to manage information technology protection. These practices are monitor, risk plan, protection protocols and use technology. Persuade your audience using this Best Practices To Manage Cyber Protection Of Organization Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Plan, Security Protocols, Technology. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Online Payment Techniques Best Practices To Maintain Digital Wallet Security
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Online Payment Techniques Best Practices To Maintain Digital Wallet Security template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Online Payment Techniques Best Practices To Maintain Digital Wallet Security that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private.
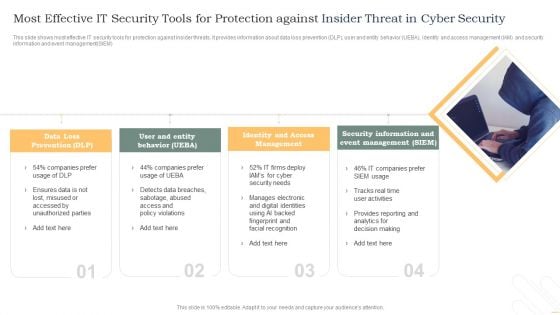
Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V
This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc. Get a simple yet stunning designed Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc.
Network And Information Threat Safety Vector Icon Ppt PowerPoint Presentation File Example PDF
Persuade your audience using this network and information threat safety vector icon ppt powerpoint presentation file example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including network and information threat safety vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
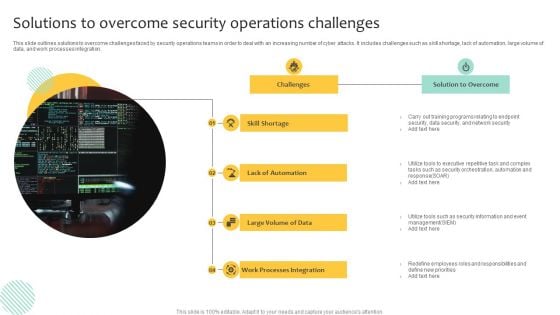
Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
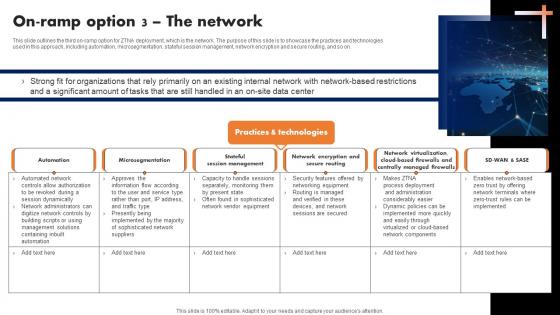
On Ramp Option 3 The Network Software Defined Perimeter SDP
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Software Defined Perimeter SDP from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
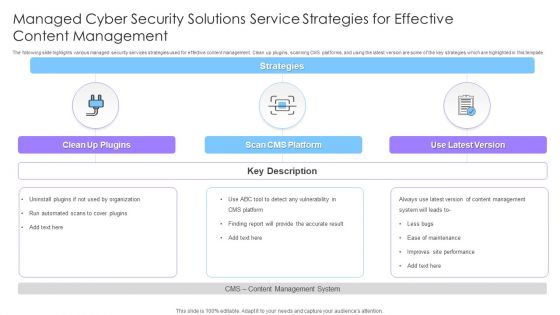
Managed Cyber Security Solutions Service Strategies For Effective Content Management Ppt Styles Example File PDF
The following slide highlights various managed security services strategies used for effective content management. Clean up plugins, scanning CMS platforms, and using the latest version are some of the key strategies which are highlighted in this template. Persuade your audience using this Managed Cyber Security Solutions Service Strategies For Effective Content Management Ppt Styles Example File PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Managed Cyber Security, Solutions Service Strategies, Effective Content Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
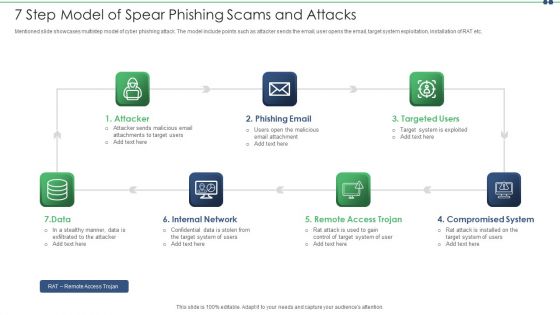
7 Step Model Of Spear Phishing Scams And Attacks Designs PDF
Mentioned slide showcases multistep model of cyber phishing attack. The model include points such as attacker sends the email, user opens the email, target system exploitation, installation of RAT etc. Persuade your audience using this 7 step model of spear phishing scams and attacks designs pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including internal network, compromised system, targeted users. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
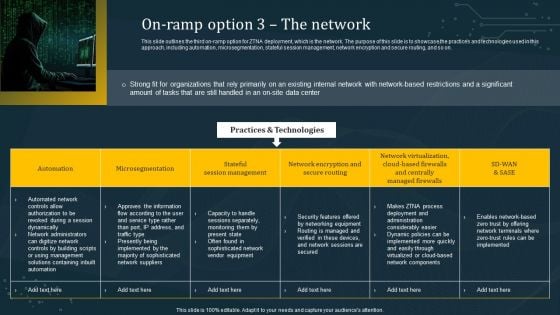
On Ramp Option 3 The Network Structure PDF
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Do you know about Slidesgeeks On Ramp Option 3 The Network Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
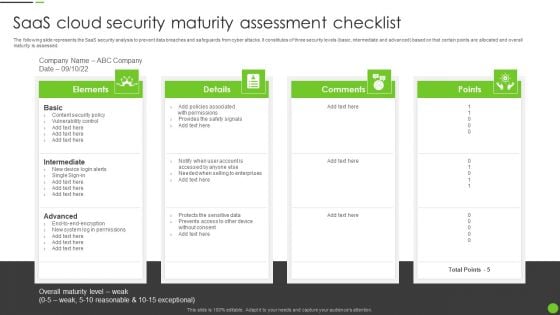
Saas Cloud Security Maturity Assessment Checklist Ppt PowerPoint Presentation File Portfolio PDF
The following slide represents the SaaS security analysis to prevent data breaches and safeguards from cyber attacks. It constitutes of three security levels basic, intermediate and advanced based on that certain points are allocated and overall maturity is assessed. Persuade your audience using this Saas Cloud Security Maturity Assessment Checklist Ppt PowerPoint Presentation File Portfolio PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Intermediate, Advanced, Content Security Policy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
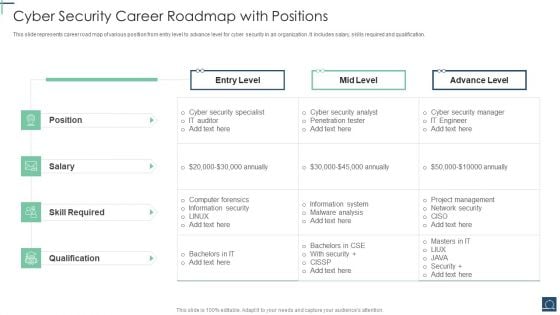
Cyber Security Career Roadmap With Positions Ppt PowerPoint Presentation File Portrait PDF
This slide represents career road map of various position from entry level to advance level for cyber security in an organization .It includes salary, skills required and qualification. Pitch your topic with ease and precision using this Cyber Security Career Roadmap With Positions Ppt PowerPoint Presentation File Portrait PDF. This layout presents information on Cyber Security Specialist, Skill Required, Advance Level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Wireless Network Security System Icon Depicting Router Connectivity Background PDF
Persuade your audience using this wireless network security system icon depicting router connectivity background pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including wireless network security system icon depicting router connectivity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Wireless Remote Control For Network Security System Themes PDF
Persuade your audience using this wireless remote control for network security system themes pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including wireless remote control for network security system. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Service Assessment Icon To Track Network Security Information PDF
Persuade your audience using this Service Assessment Icon To Track Network Security Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Service Assessment Icon To Track Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Online Business Challenges And Best Practices Brochure Pdf
The slide displays pain points in e-commerce along with best practices to prevent facing these issues. It includes challenges such as limited capital, huge marketing efforts, cyber security issues, etc and best practices such as government support, public relation strategy, etc. Pitch your topic with ease and precision using this Online Business Challenges And Best Practices Brochure Pdf. This layout presents information on Pain Points, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide displays pain points in e-commerce along with best practices to prevent facing these issues. It includes challenges such as limited capital, huge marketing efforts, cyber security issues, etc and best practices such as government support, public relation strategy, etc.
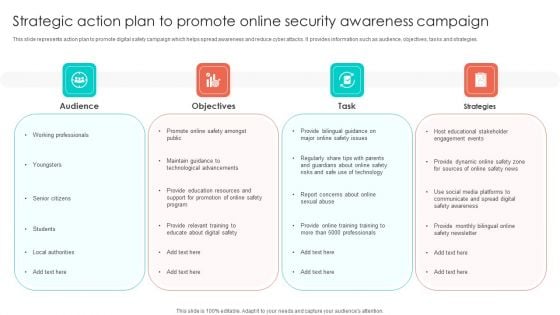
Strategic Action Plan To Promote Online Security Awareness Campaign Portrait PDF
This slide represents action plan to promote digital safety campaign which helps spread awareness and reduce cyber attacks. It provides information such as audience, objectives, tasks and strategies. Persuade your audience using this Strategic Action Plan To Promote Online Security Awareness Campaign Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Objectives, Task, Strategies, Audience. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Top Four Network IT Security Analysis Tools Guidelines PDF
This slide covers the tools used for the security analysis of the networks with their usage according to their needs on different occasions. It also includes the price or cost of these tools. Persuade your audience using this Top Four Network IT Security Analysis Tools Guidelines PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Network IT Security, Analysis Tools. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
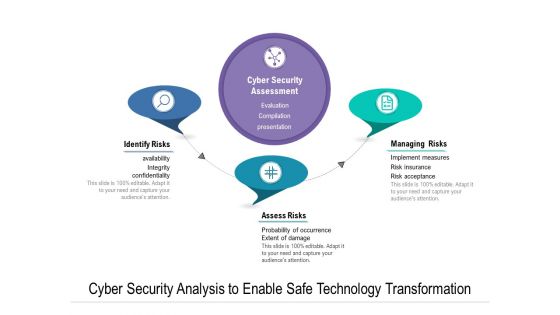
Cyber Security Analysis To Enable Safe Technology Transformation Ppt PowerPoint Presentation Visual Aids Styles PDF
Persuade your audience using this cyber security analysis to enable safe technology transformation ppt powerpoint presentation visual aids styles pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cyber security assessment, identify risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
8 Steps Circle Of Internal Audit And Cyber Security Ppt PowerPoint Presentation Gallery Themes PDF
Persuade your audience using this 8 steps circle of internal audit and cyber security ppt powerpoint presentation gallery themes pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including 8 steps circle of internal audit and cyber security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Security Incident Alert Icon With Desktop Screen Ppt Gallery Layouts PDF
Persuade your audience using this Cyber Security Incident Alert Icon With Desktop Screen Ppt Gallery Layouts PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Incident, Alert Icon, Desktop Screen. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Security Incident Icon With Man In Black Hood Ppt Inspiration Images PDF
Persuade your audience using this Cyber Security Incident Icon With Man In Black Hood Ppt Inspiration Images PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Incident, Icon With Man, Black Hood. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Overview Of Key Insights On Cyber Security Trends Icon Microsoft PDF
Persuade your audience using this Overview Of Key Insights On Cyber Security Trends Icon Microsoft PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Overview Of Key Insights, Cyber Security Trends Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF
This slide covers quarterly cyber security planning roadmap by management to reduce risk with program maturity and cost .It consist secure , defend, contain, manage and anticipate. Persuade your audience using this Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Management, Level Risk Reduction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
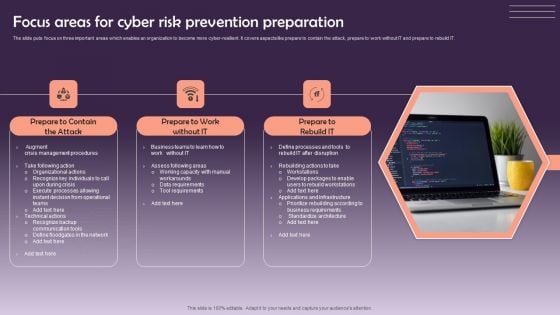
Focus Areas For Cyber Risk Prevention Preparation Pictures PDF
The slide puts focus on three important areas which enables an organization to become more cyber-resilient. It covers aspects like prepare to contain the attack, prepare to work without IT and prepare to rebuild IT. Persuade your audience using this Focus Areas For Cyber Risk Prevention Preparation Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare To Contain, Prepare To Work, Prepare To Rebuild. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
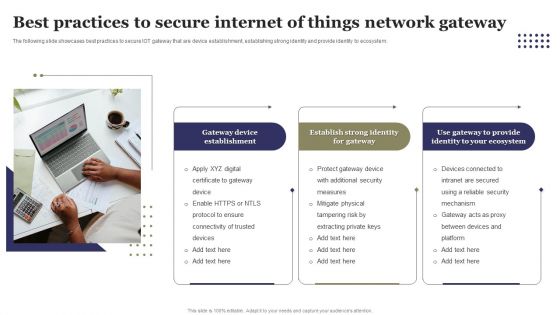
Best Practices To Secure Internet Of Things Network Gateway Ppt Outline Elements PDF
The following slide showcases best practices to secure IOT gateway that are device establishment, establishing strong identity and provide identity to ecosystem. Presenting Best Practices To Secure Internet Of Things Network Gateway Ppt Outline Elements PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Performance Metrics For Project Management Office, Requirement Gathering. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
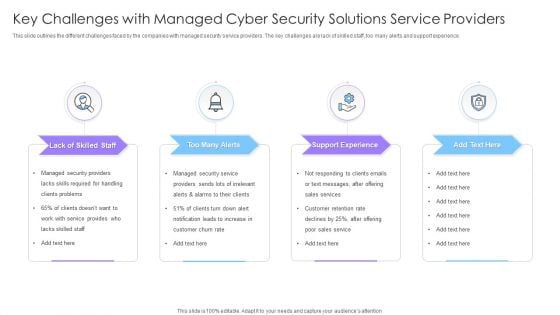
Key Challenges With Managed Cyber Security Solutions Service Providers Ppt Pictures Visual Aids PDF
This slide outlines the different challenges faced by the companies with managed security service providers. The key challenges are lack of skilled staff, too many alerts and support experience. Presenting Key Challenges With Managed Cyber Security Solutions Service Providers Ppt Pictures Visual Aids PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Too Many Alerts, Support Experience, Lack Skilled Staff. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
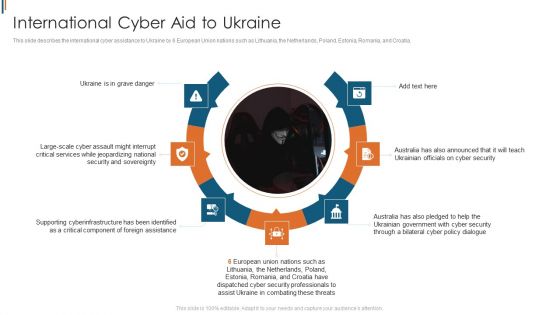
Ukraine Cyberwarfare International Cyber Aid To Ukraine Brochure Pdf
This slide describes the international cyber assistance to Ukraine by 6 European Union nations such as Lithuania, the Netherlands, Poland, Estonia, Romania, and Croatia. This is a ukraine cyberwarfare international cyber aid to ukraine brochure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ukraine is in grave danger, australia has also announced that it will teach ukrainian officials on cyber security, australia has also pledged to help the ukrainian government with cyber security through a bilateral cyber policy dialogue. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Icon Of Wireless Network Security System For WIFI Networks With Smart Lock Sample PDF
Persuade your audience using this icon of wireless network security system for wifi networks with smart lock sample pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including icon of wireless network security system for wifi networks with smart lock. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































