Data Breach
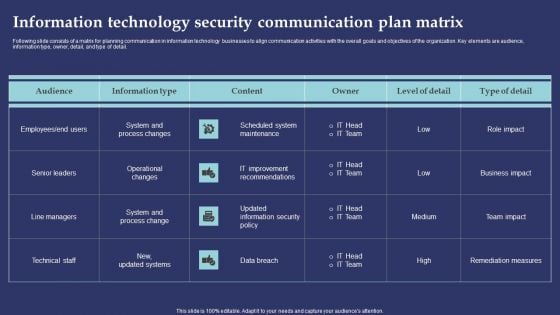
Information Technology Security Communication Plan Matrix Template PDF
Following slide consists of a matrix for planning communication in information technology businesses to align communication activities with the overall goals and objectives of the organization. Key elements are audience, information type, owner, detail, and type of detail. Showcasing this set of slides titled Information Technology Security Communication Plan Matrix Template PDF. The topics addressed in these templates are Scheduled System Maintenance, IT Improvement Recommendations, Data Breach. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
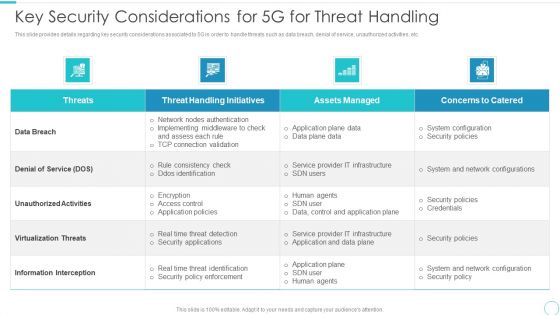
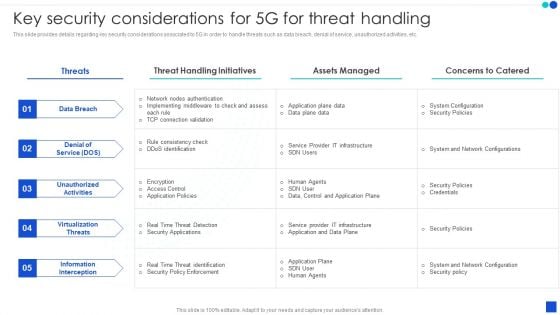
5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF Use them to share invaluable insights on Concerns To Catered, Handling Initiatives, Implementing Middleware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
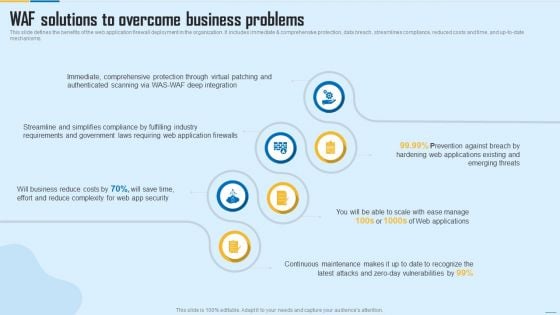
WAF Solutions To Overcome Business Problems WAF Platform Clipart PDF
This slide defines the benefits of the web application firewall deployment in the organization. It includes immediate and comprehensive protection, data breach, streamlines compliance, reduced costs and time, and up to date mechanisms. This is a WAF Solutions To Overcome Business Problems WAF Platform Clipart PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Requirements, Security, Applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
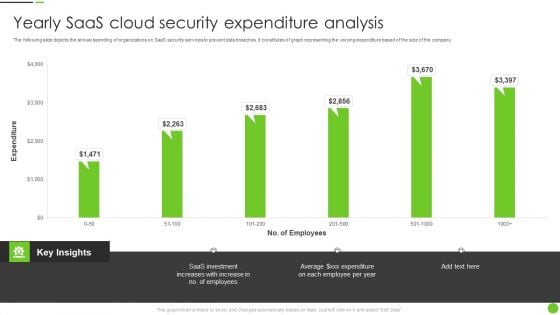
Yearly Saas Cloud Security Expenditure Analysis Ppt PowerPoint Presentation File Deck PDF
The following slide depicts the annual spending of organizations on SaaS security services to prevent data breaches. It constitutes of graph representing the varying expenditure based of the size of the company. Pitch your topic with ease and precision using this Yearly Saas Cloud Security Expenditure Analysis Ppt PowerPoint Presentation File Deck PDF. This layout presents information on Saas Investment, Employees. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
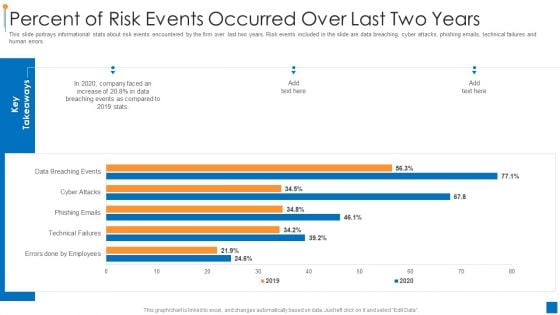
International Organization Standardization 270001 Percent Of Risk Events Occurred Over Last Two Years Demonstration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an awe inspiring pitch with this creative international organization standardization 270001 percent of risk events occurred over last two years demonstration pdf bundle. Topics like percent of risk events occurred over last two years can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
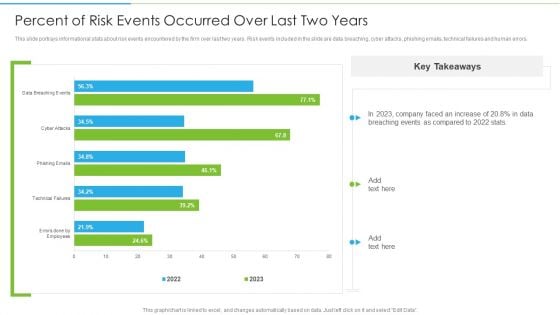
Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Percent Of Risk Events Occurred Over Last Rules PDF. Use them to share invaluable insights on Technical Failures, Phishing Emails, Cyber Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
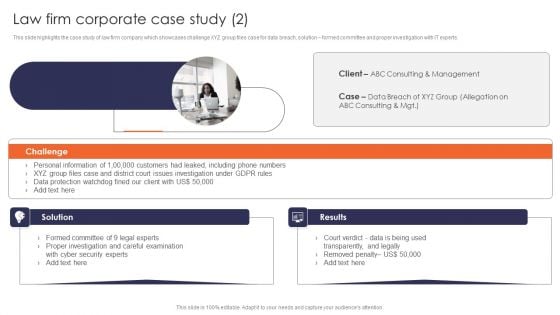
Law Firm Corporate Case Study Multinational Legal Firm Company Profile Formats PDF
This slide highlights the case study of law firm company which showcases challenge XYZ group files case for data breach, solution formed committee and proper investigation with IT experts. Presenting Law Firm Corporate Case Study Multinational Legal Firm Company Profile Formats PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Challenge, Law Firm Corporate, Case Study. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Solutions To Overcome Various Security For Cloud Based Systems Challenges Mockup PDF
This slide shows solutions to various challenges faced by organizations to provide cloud security. These challenges are data breaches, lack of expertise, insider threats and unsecured APIs. Showcasing this set of slides titled Solutions To Overcome Various Security For Cloud Based Systems Challenges Mockup PDF. The topics addressed in these templates are Solutions To Overcome, Various Security For Cloud, Based Systems Challenges . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Web App Firewall Services IT WAF Solutions To Overcome Business Problems Icons PDF
This slide defines the benefits of the web application firewall deployment in the organization. It includes immediate and comprehensive protection, data breach, streamlines compliance, reduced costs and time, and up to date mechanisms. This is a web app firewall services it waf solutions to overcome business problems icons pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, security, costs, requirements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
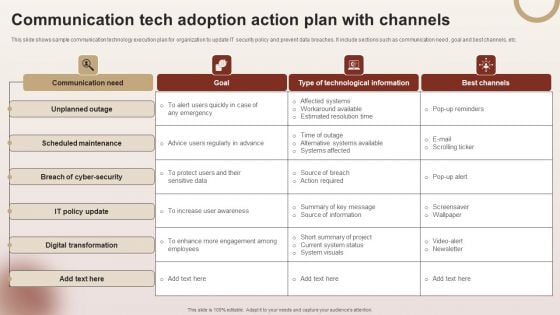
Communication Tech Adoption Action Plan With Channels Ideas PDF
This slide shows sample communication technology execution plan for organization to update IT security policy and prevent data breaches. It include sections such as communication need , goal and best channels, etc. Showcasing this set of slides titled Communication Tech Adoption Action Plan With Channels Ideas PDF. The topics addressed in these templates are Goal, Technological Information, Best Channels. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Law And Enforcement Company Profile Law Firm Corporate Case Study Graphics PDF
This slide highlights the case study of law firm company which showcases challenge XYZ group files case for data breach, solution formed committee and proper investigation with IT experts. Presenting Law And Enforcement Company Profile Law Firm Corporate Case Study Graphics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Challenge, Solution, Results. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Need For Cyber Security Awareness Training Professional PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Presenting Need For Cyber Security Awareness Training Professional PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Organization Different, Technological Defenses, Awareness Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
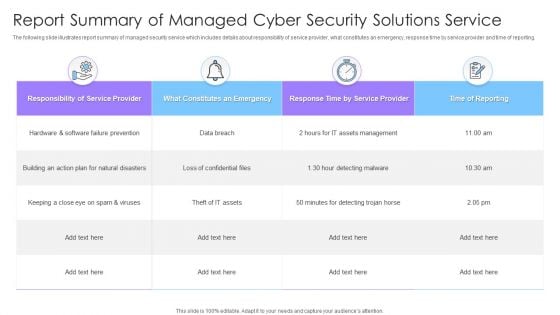
Report Summary Of Managed Cyber Security Solutions Service Ppt Portfolio Slides
The following slide illustrates report summary of managed security service which includes details about responsibility of service provider, what constitutes an emergency, response time by service provider and time of reporting. Showcasing this set of slides titled Report Summary Of Managed Cyber Security Solutions Service Ppt Portfolio Slides. The topics addressed in these templates are Responsibility Of Service Provider, Time Of Reporting, Data Breach. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Process For Responding To Internet Security Threats Template PDF
This slide exhibits process for responding to security data breach. It includes multiple steps such as- analyzing the current damage, keeping record how much damage is caused and so on. Pitch your topic with ease and precision using this process for responding to internet security threats template pdf. This layout presents information on process for responding to internet security threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
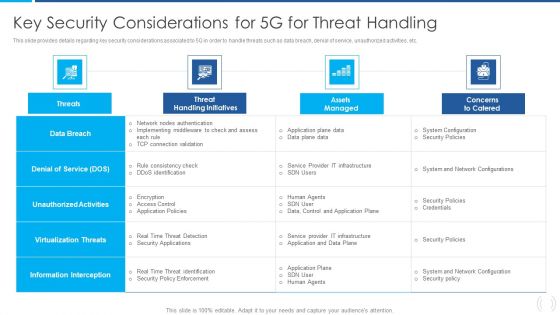
Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Proactive Method For 5G Deployment By Telecom Companies Key Security Considerations For 5G For Threat Handling Designs PDF bundle. Topics like Virtualization Threats, Information Interception, Unauthorized Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Legal And Law Assistance LLP Business Customer Testimonials And Reviews Designs PDF
This slide highlights the customer reviews for law firm company which includes cases from different legal matters i.e. theft and fraud case, criminal case and family case. Presenting Legal And Law Assistance LLP Business Customer Testimonials And Reviews Designs PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Case Data Breach, Case Trade Ban, Theft And Fraud. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Mitigation Plan For Insurance Risk Management Ppt Layouts Icons PDF
This slide showcase insurance risk for small business along with the mitigation plan to protect business operations. It covers the risks such as data breach, property damage, liability risk, and building project. Presenting Mitigation Plan For Insurance Risk Management Ppt Layouts Icons PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Categories Risk, Risk Mitigation, Insurance Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF. Use them to share invaluable insights on Nodes Authentication, Rule Consistency, Policy Enforcement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
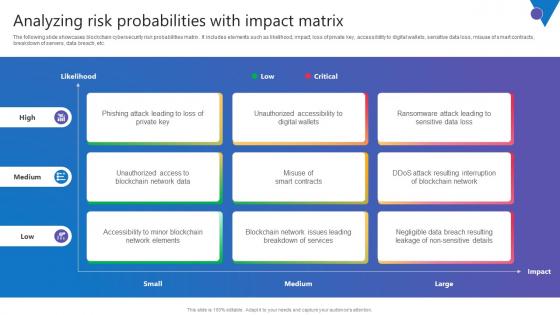
Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc. Presenting this PowerPoint presentation, titled Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc.
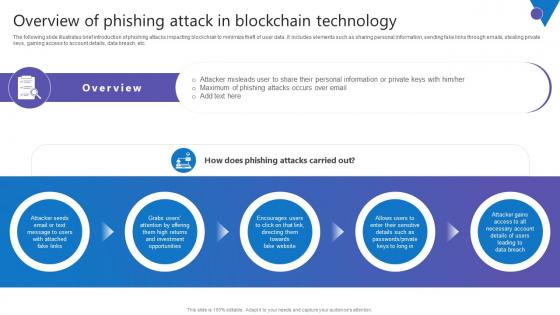
Overview Of Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide illustrates brief introduction of phishing attacks impacting blockchian to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Presenting this PowerPoint presentation, titled Overview Of Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Overview Of Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Overview Of Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide illustrates brief introduction of phishing attacks impacting blockchian to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc.
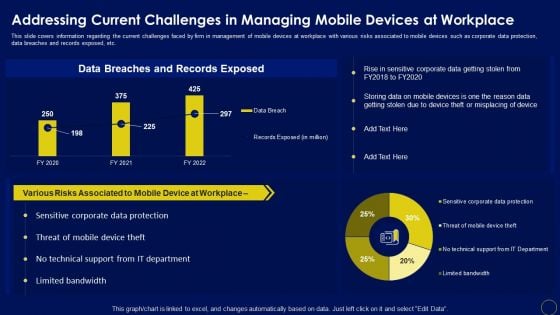
Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
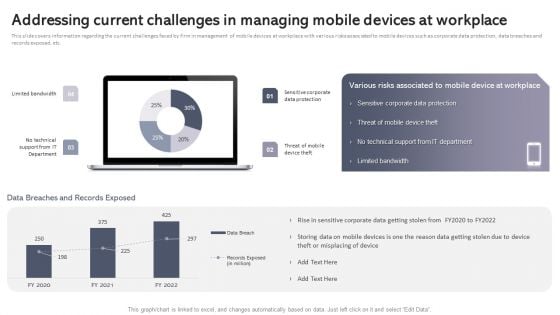
Addressing Current Challenges In Managing Mobile Devices At Workplace Diagrams PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Presenting this PowerPoint presentation, titled Addressing Current Challenges In Managing Mobile Devices At Workplace Diagrams PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Addressing Current Challenges In Managing Mobile Devices At Workplace Diagrams PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Addressing Current Challenges In Managing Mobile Devices At Workplace Diagrams PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
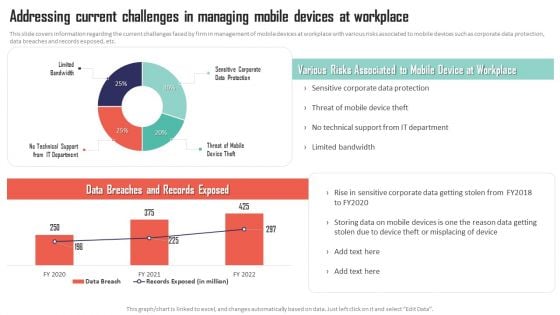
Mobile Device Management Addressing Current Challenges In Managing Mobile Devices Professional PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Get a simple yet stunning designed Mobile Device Management Addressing Current Challenges In Managing Mobile Devices Professional PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mobile Device Management Addressing Current Challenges In Managing Mobile Devices Professional PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Current Performance Business Managing Risks And Establishing Trust Through Efficient Demonstration Pdf
This slide highlights the performance of various compliance metrics indicating non compliance in the company. It includes metrics such as compliance rate, training completion rate, policy violations, mean time to issue resolution, incident response time, risk mitigation time, risk assessments conducted, and the number of data breaches. Are you searching for a Current Performance Business Managing Risks And Establishing Trust Through Efficient Demonstration Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Current Performance Business Managing Risks And Establishing Trust Through Efficient Demonstration Pdf from Slidegeeks today. This slide highlights the performance of various compliance metrics indicating non compliance in the company. It includes metrics such as compliance rate, training completion rate, policy violations, mean time to issue resolution, incident response time, risk mitigation time, risk assessments conducted, and the number of data breaches.
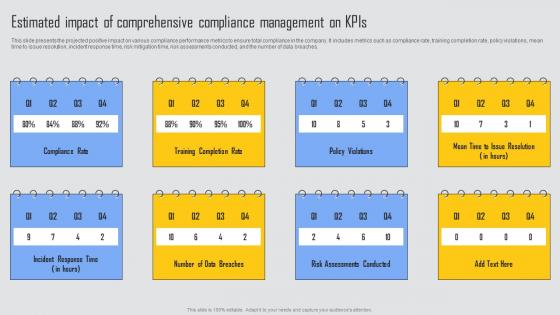
Estimated Impact Of Comprehensive Managing Risks And Establishing Trust Through Efficient Slides Pdf
This slide presents the projected positive impact on various compliance performance metrics to ensure total compliance in the company. It includes metrics such as compliance rate, training completion rate, policy violations, mean time to issue resolution, incident response time, risk mitigation time, risk assessments conducted, and the number of data breaches. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Estimated Impact Of Comprehensive Managing Risks And Establishing Trust Through Efficient Slides Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide presents the projected positive impact on various compliance performance metrics to ensure total compliance in the company. It includes metrics such as compliance rate, training completion rate, policy violations, mean time to issue resolution, incident response time, risk mitigation time, risk assessments conducted, and the number of data breaches.

Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF
The following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF
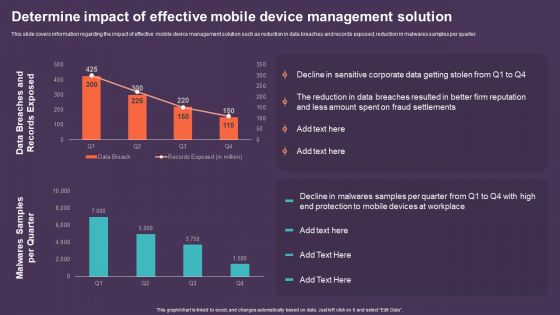
Mobile Device Management For Improving IT Operations Determine Impact Of Effective Mobile Device Guidelines PDF
This slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter. This Mobile Device Management For Improving IT Operations Determine Impact Of Effective Mobile Device Guidelines PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
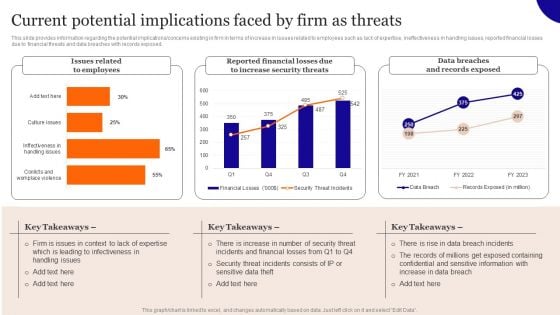
Current Potential Implications Faced By Firm As Threats Download PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Create an editable Current Potential Implications Faced By Firm As Threats Download PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Current Potential Implications Faced By Firm As Threats Download PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
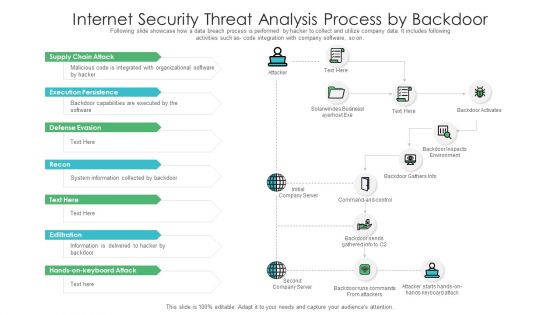
Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
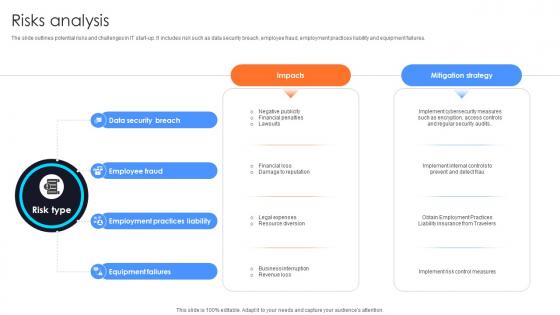
Risks Analysis Information Technology Startup Go To Market Strategy GTM SS V
The slide outlines potential risks and challenges in IT start-up. It includes risk such as data security breach, employee fraud, employment practices liability and equipment failures.This modern and well-arranged Risks Analysis Information Technology Startup Go To Market Strategy GTM SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide outlines potential risks and challenges in IT start-up. It includes risk such as data security breach, employee fraud, employment practices liability and equipment failures.
5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download 5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the 5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF.

Prevention Of Information Need For Cyber Security Awareness Training Graphics PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Retrieve professionally designed Prevention Of Information Need For Cyber Security Awareness Training Graphics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Are you searching for a Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF from Slidegeeks today.

Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF can be your best option for delivering a presentation. Represent everything in detail using Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Need For Cyber Security Awareness Training Ppt Gallery Template PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Welcome to our selection of the Need For Cyber Security Awareness Training Ppt Gallery Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Retrieve professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

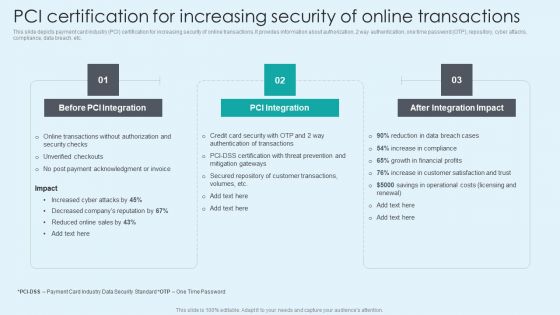
PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Slidegeeks has constructed PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
PCI Certification For Increasing Security Of Online Transactions Background PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Explore a selection of the finest PCI Certification For Increasing Security Of Online Transactions Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our PCI Certification For Increasing Security Of Online Transactions Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
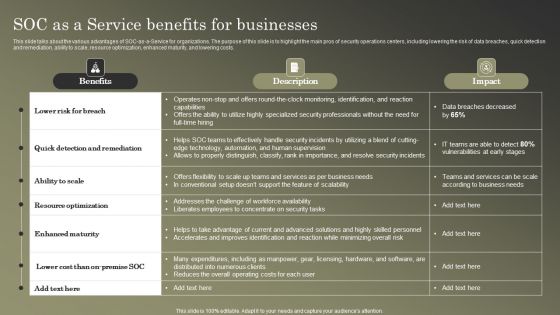
Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF
This slide talks about the various advantages of SOC-as-a-Service for organizations. The purpose of this slide is to highlight the main pros of security operations centers, including lowering the risk of data breaches, quick detection and remediation, ability to scale, resource optimization, enhanced maturity, and lowering costs. Find highly impressive Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
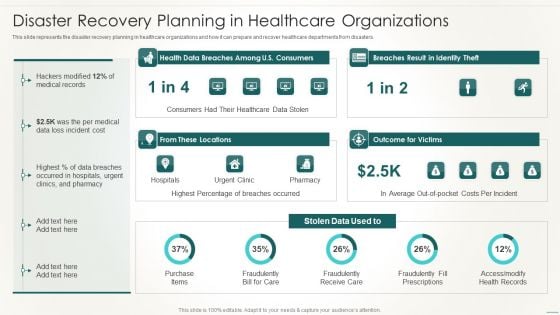
Information Technology Disaster Resilience Plan Disaster Recovery Planning Pictures PDF
This slide represents the disaster recovery planning in healthcare organizations and how it can prepare and recover healthcare departments from disasters.Deliver an awe inspiring pitch with this creative Information Technology Disaster Resilience Plan Disaster Recovery Planning Pictures PDF bundle. Topics like Healthcare Data, Highest Percentage, Breaches Occurred can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Strategy To Be Adopted 3 Restrict Access To Physical Devices Guidelines PDF
This slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 3 restrict access to physical devices guidelines pdf to provide visual cues and insights. Share and navigate important information on strategy to be adopted 3 restrict access to physical devices guidelines pdf stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 3 restrict access to physical devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
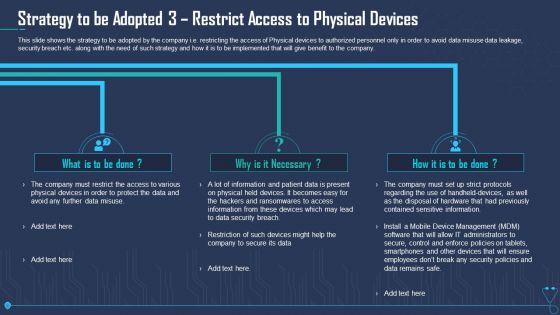
Strategy To Be Adopted 3 Restrict Access To Physical Devices Pictures PDF
This slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 3 restrict access to physical devices pictures pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 3 restrict access to physical devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Essential Measures For Business Cyber Security Assessment Plan Rules PDF
This slide demonstrates the safety measures in a business security plan that helps in decreasing the frequency of security threats data hacks, information breaches etc. The measures include handy backups, multi layer security, protective software, and employee training. Presenting Essential Measures For Business Cyber Security Assessment Plan Rules PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
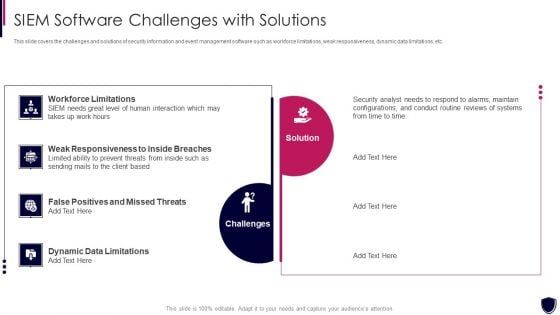
Enhancing Cyber Safety With Vulnerability Administration SIEM Software Challenges Slides PDF
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. This is a enhancing cyber safety with vulnerability administration siem software challenges slides pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like workforce limitations, challenges, solution, weak responsiveness to inside breaches, dynamic data limitations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
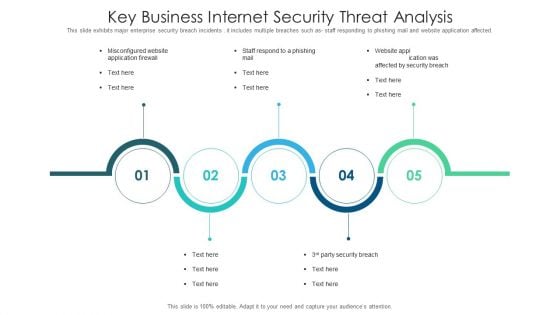
Key Business Internet Security Threat Analysis Slides PDF
This slide exhibits major enterprise security breach incidents . it includes multiple breaches such as staff responding to phishing mail and website application affected. Presenting key business internet security threat analysis slides pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including key business internet security threat analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
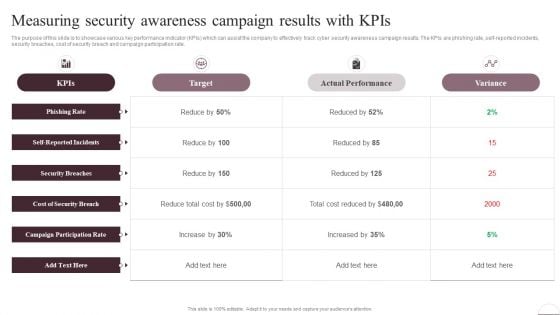
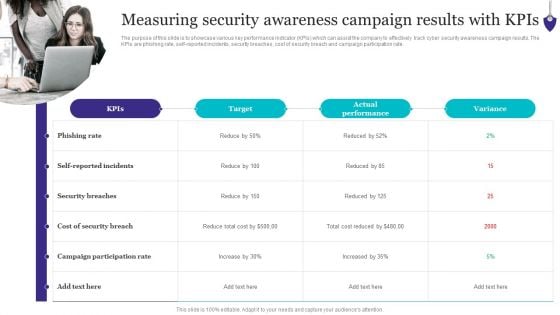
Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF from Slidegeeks and deliver a wonderful presentation.
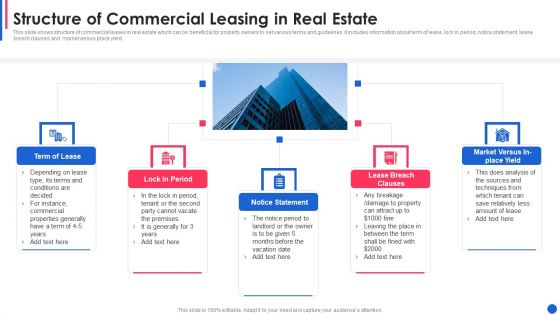
Structure Of Commercial Leasing In Real Estate Diagrams PDF
This slide shows structure of commercial leases in real estate which can be beneficial for property owners to set various terms and guidelines. It includes information about term of lease, lock in period, notice statement, lease breach clauses and market versus place yield.Presenting structure of commercial leasing in real estate diagrams pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including notice statement, lease breach clauses, lock in period This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Problems Management And Action Plan Microsoft PDF
The following slide illustrates the cyber security risk management plan to outline business security threats and draft proposed strategies. It also includes elements such as objectives, issues, breach response actions, employee training etc. Persuade your audience using this Cyber Security Problems Management And Action Plan Microsoft PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objectives, Breach Response Actions, Employee Training. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
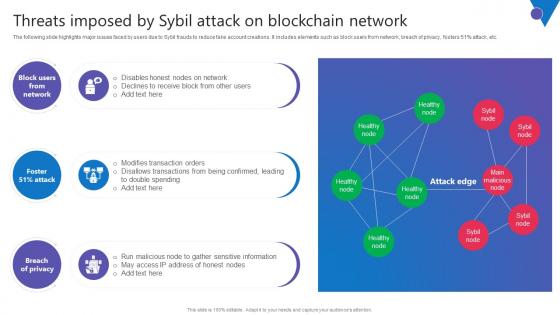
Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc.
Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. Explore a selection of the finest Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Organizing Security Awareness Measuring Security Awareness Campaign Results Download PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Incident Conveyance Plan Timeline For Safety Teams In Large Events Inspiration Pdf
The following slide presents an Incident communication plan timeline to be followed by security teams in case of breach or mishappening in large events. Key elements covered are incident communicated by attendee or staff, incident verified, action plan developed, etc. Showcasing this set of slides titled Incident Conveyance Plan Timeline For Safety Teams In Large Events Inspiration Pdf. The topics addressed in these templates are Operations Resume, Treatment Validation . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide presents an Incident communication plan timeline to be followed by security teams in case of breach or mishappening in large events. Key elements covered are incident communicated by attendee or staff, incident verified, action plan developed, etc.
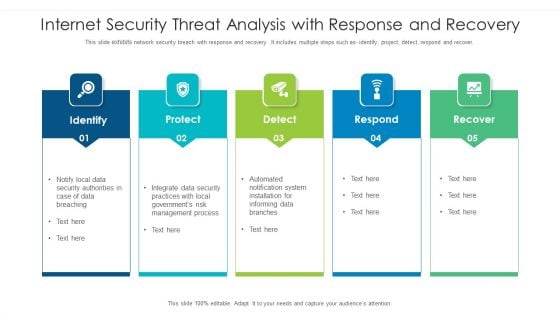
Internet Security Threat Analysis With Response And Recovery Information PDF
This slide exhibits network security breach with response and recovery .It includes multiple steps such as- identify, project, detect, respond and recover. Pitch your topic with ease and precision using this internet security threat analysis with response and recovery information pdf. This layout presents information on internet security threat analysis with response and recovery. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Client Relationship Administration Proposal Template Implementation Agreement Brochure PDF
Presenting client relationship administration proposal template implementation agreement brochure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like confidentiality, breach of contract, termination, liability for trangression, schedules and deadlines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Analyzing The Impact Of Security Threats On Organization Elements PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets .Deliver and pitch your topic in the best possible manner with this Analyzing The Impact Of Security Threats On Organization Elements PDF. Use them to share invaluable insights on Security Threats, Impact Organization, Average Financial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Electronic Game Pitch Deck What Video Game Experience Challenges Are Faced By Prospect Topics PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances. Deliver an awe inspiring pitch with this creative electronic game pitch deck what video game experience challenges are faced by prospect topics pdf bundle. Topics like security threats, regulatory compliances, systems information breach can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
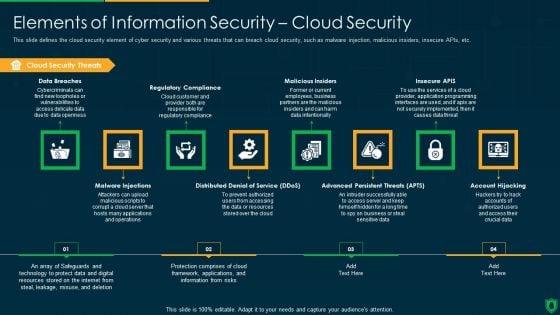
Info Security Elements Of Information Security Cloud Security Ppt PowerPoint Presentation Gallery Graphics Download PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting info security elements of information security cloud security ppt powerpoint presentation gallery graphics download pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like cloud security threats, regulatory compliance, malicious insiders, insecure apis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
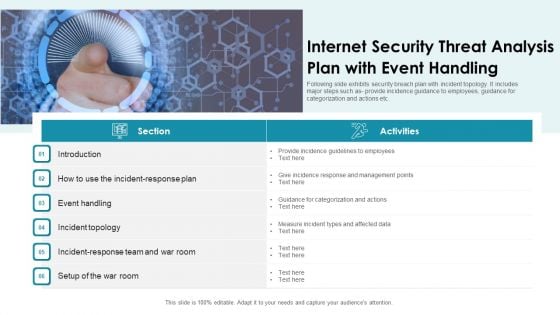
Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
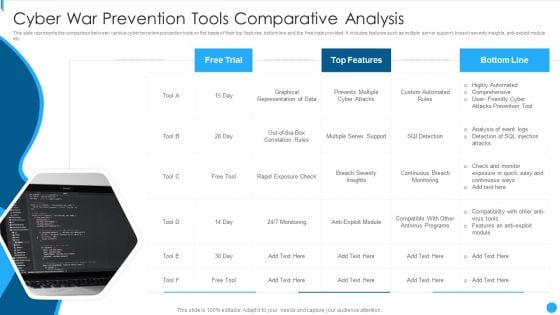
Cyber War Prevention Tools Comparative Analysis Formats PDF
This slide represents the comparison between various cyber terrorism prevention tools on the basis of their top features, bottom line and the free trials provided. It includes features such as multiple server support, breach severity insights, anti exploit module etc.Presenting Cyber War Prevention Tools Comparative Analysis Formats PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Custom Automated, Antivirus Programs, Analysis Of Event This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Elements Of Electronic Information Security Cloud Security Ppt Outline Background Designs PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a cybersecurity elements of electronic information security cloud security ppt outline background designs pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, information, risks, resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Multiplayer Gameplay System Venture Capitalist PPT What Video Game Experience Challenges Are Faced By Prospect Structure PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances.This is a multiplayer gameplay system venture capitalist ppt what video game experience challenges are faced by prospect structure pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security threats, everchanging government, systems information breach You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































