Data Privacy

Governance Risk And Compliance Implementation Process To Manage Security Risks Pictures PDF
Mentioned slide outlines 3 step process of governance, risk and compliance GRC. Information covered in this slide is related to governance, risk management and compliance which will assist organization to successfully mitigate IT and security risks. Presenting Governance Risk And Compliance Implementation Process To Manage Security Risks Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Governance, Risk Management, Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
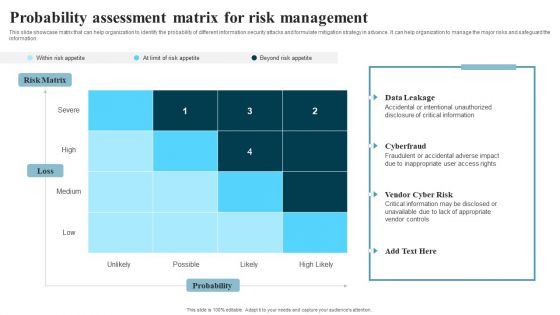
Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Make sure to capture your audiences attention in your business displays with our gratis customizable Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
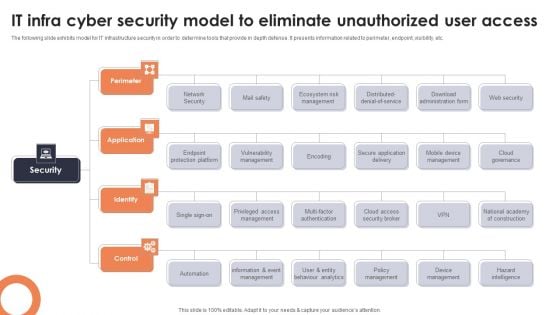
IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF
The following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defense. It presents information related to perimeter, endpoint, visibility, etc. Presenting IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Perimeter, Application, Identify. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Determine Various Quality Awards Received By Firm Food Security Excellence Ppt Portfolio Influencers PDF
This slide provides information regarding various quality awards received by food processing firm over the years. Presenting determine various quality awards received by firm food security excellence ppt portfolio influencers pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like performance, manufacturing, corporate, manufacturing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
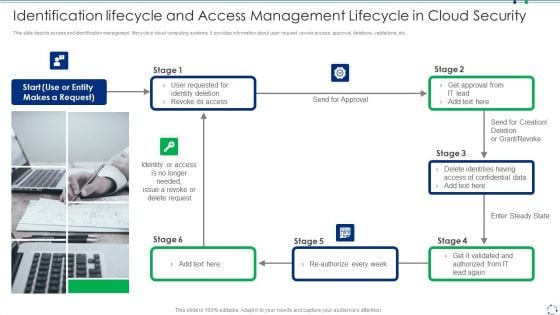
Identification Lifecycle And Access Management Lifecycle In Cloud Security Guidelines PDF
This slide depicts access and identification management lifecycle in cloud computing systems. It provides information about user request, revoke access, approval, deletions, validations, etc.Presenting identification lifecycle and access management lifecycle in cloud security guidelines pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including identity deletion, revoke its access, identity or access This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Facilitating IT Intelligence Architecture Contingency Plan For Threat Handling In Security Centre Professional PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Deliver and pitch your topic in the best possible manner with this Facilitating IT Intelligence Architecture Contingency Plan For Threat Handling In Security Centre Professional PDF Use them to share invaluable insights on Contingency Solutions, Contingency Considerations, Information Documentation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
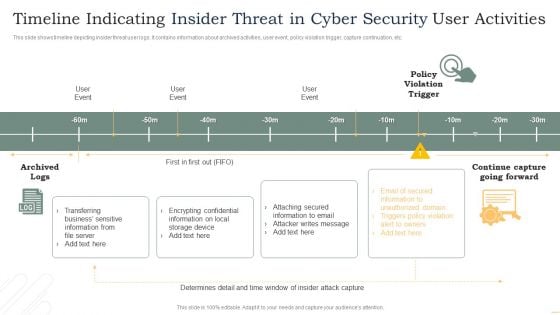
Timeline Indicating Insider Threat In Cyber Security User Activities Microsoft PDF
This slide shows timeline depicting insider threat user logs. It contains information about archived activities, user event, policy violation trigger, capture continuation, etc. Pitch your topic with ease and precision using this Timeline Indicating Insider Threat In Cyber Security User Activities Microsoft PDF. This layout presents information on User Event, Policy Violation Trigger, Archived Logs. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
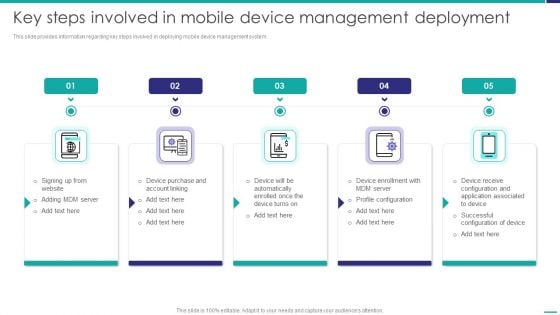
Key Steps Involved In Mobile Device Management Deployment Mobile Device Security Management Infographics PDF
This slide provides information regarding key steps involved in deploying mobile device management system. Presenting Key Steps Involved In Mobile Device Management Deployment Mobile Device Security Management Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Device Purchase, Device Automatically, Profile Configuration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Assets Security Management Strategy Critical Business Functions Recovery Priorities Template PDF
After the crisis hits, the firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. There are so many reasons you need a Organizational Assets Security Management Strategy Critical Business Functions Recovery Priorities Template PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cyber Security For Your Organization Determining Roles And Responsibilities For Risk Handling Ppt Outline Example PDF
Presenting this set of slides with name cyber security for your organization determining roles and responsibilities for risk handling ppt outline example pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management, executive, line management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Determining Roles And Responsibilities For Risk Handling Ideas PDF
Presenting this set of slides with name strategies to mitigate cyber security risks determining roles and responsibilities for risk handling ideas pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Picture Showing Security Officer In Building Control Room Ppt PowerPoint Presentation File Layout Ideas PDF
Pitch your topic with ease and precision using this picture showing security officer in building control room ppt powerpoint presentation file layout ideas pdf. This layout presents information on picture showing security officer in building control room. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Vector Showing Security Guard At Entrance Of Shopping Mall Ppt PowerPoint Presentation Gallery Design Ideas PDF
Pitch your topic with ease and precision using this vector showing security guard at entrance of shopping mall ppt powerpoint presentation gallery design ideas pdf. This layout presents information on vector showing security guard at entrance of shopping mall. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Develop Corporate Cyber Security Risk Mitigation Plan Why Us For Organization Cyber Protection Services Sample PDF
Presenting develop corporate cyber security risk mitigation plan why us for organization cyber protection services sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like knowledge, system security, net development, it support services. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
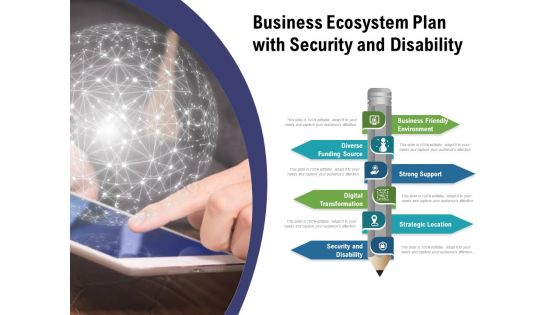
Business Ecosystem Plan With Security And Disability Ppt PowerPoint Presentation File Example PDF
Presenting business ecosystem plan with security and disability ppt powerpoint presentation file example pdf. to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including business friendly environment, diverse, funding source, strong support, strategic location, security and disability, digital transformation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
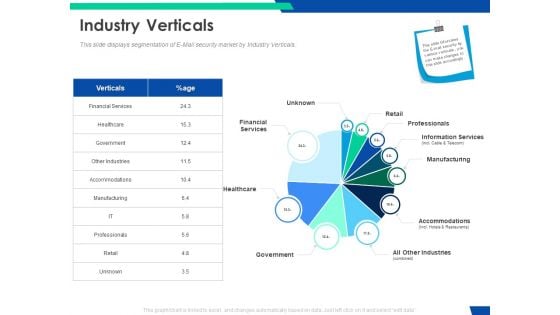
Cloud Based Email Security Market Report Industry Verticals Ppt Layouts Background Designs PDF
This slide displays segmentation of E Mail security market by Industry Verticals. Deliver and pitch your topic in the best possible manner with this cloud based email security market report industry verticals ppt layouts background designs pdf. Use them to share invaluable insights on financial services, retail, professionals, information services, manufacturing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

United States Marine Officers Port Security Officers On Patrol 01 Ppt PowerPoint Presentation Model Good PDF
Pitch your topic with ease and precision using this united states marine officers port security officers on patrol 01 ppt powerpoint presentation model good pdf. This layout presents information on united states marine officers port security officers on patrol 01. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
United States Marine Officers Security Escort Holding Weapon On Boat Ppt PowerPoint Presentation Outline Icon PDF
Pitch your topic with ease and precision using this united states marine officers security escort holding weapon on boat ppt powerpoint presentation outline icon pdf. This layout presents information on united states marine officers security escort holding weapon on boat. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
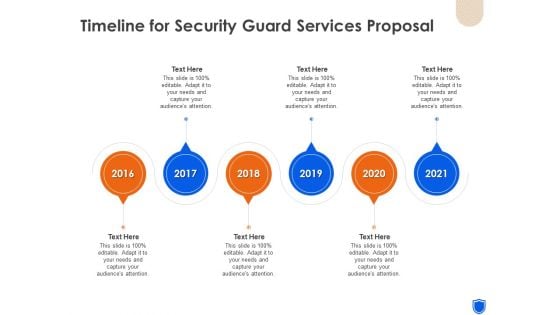
Timeline For Security Guard Services Proposal Ppt Visual Aids Slides PDF
Presenting timeline for security guard services proposal ppt visual aids slides pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like timeline, security guard services, 2016 to 2021. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Requirement For Security Planning And Risk Mitigation Process Ppt PowerPoint Presentation Infographics Icon PDF
Pitch your topic with ease and precision using this requirement for security planning and risk mitigation process ppt powerpoint presentation infographics icon pdf. This layout presents information on main requirements, supporting requirements, security plan review, threat levels, impact risks, risk steward. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
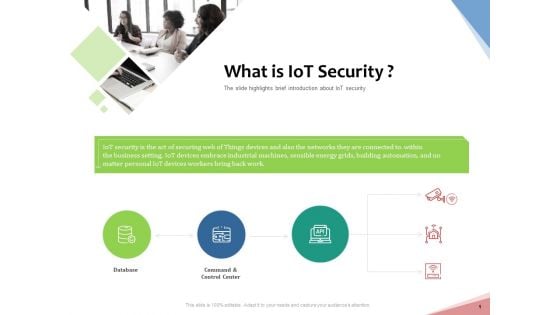
Machine To Machine Communication Outline What Is Iot Security Ppt PowerPoint Presentation Show PDF
The slide highlights brief introduction about IoT security. Presenting machine to machine communication outline what is iot security ppt powerpoint presentation show pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like database, command and control center, building automation, business. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Workforce Security Realization Coaching Plan Communication Plan General Format Brochure PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. Presenting workforce security realization coaching plan communication plan general format brochure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, description, frequency, audience. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Organizational Network Staff Learning Security Awareness Tracking Kpis Event Ppt Slides Clipart Images PDF
Presenting organizational network staff learning security awareness tracking kpis event ppt slides clipart images pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like compliance, security culture, incident reduction. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Security Solutions Budget For Effective Secops System Management Rules PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this organizational security solutions budget for effective secops system management rules pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
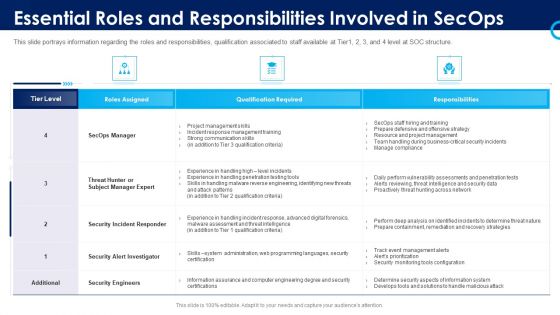
Organizational Security Solutions Essential Roles And Responsibilities Involved In Secops Download PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure. Deliver and pitch your topic in the best possible manner with this organizational security solutions essential roles and responsibilities involved in secops download pdf. Use them to share invaluable insights on security engineers, business, communication skills, management, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
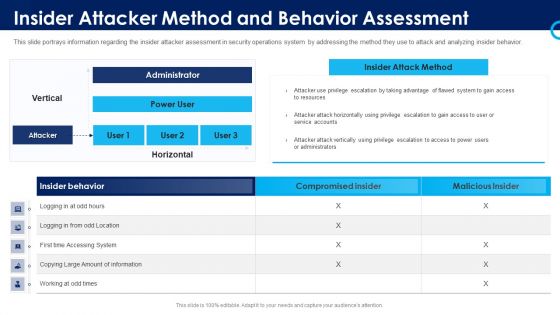
Organizational Security Solutions Insider Attacker Method And Behavior Assessment Introduction PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this organizational security solutions insider attacker method and behavior assessment introduction pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Case Study 4 Improving Patient Security And Reducing Risk Of Violence Graphics PDF
Presenting case study 4 improving patient security and reducing risk of violence graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like building management, security management, power management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
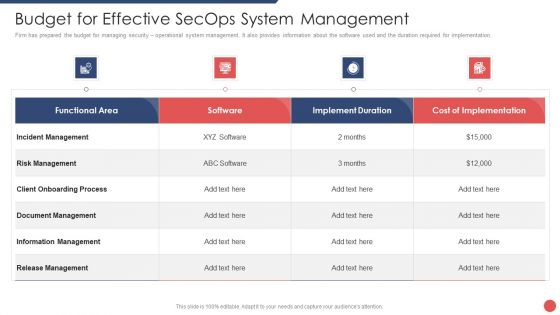
Security Functioning Centre Budget For Effective Secops System Management Formats PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this security functioning centre budget for effective secops system management formats pdf. Use them to share invaluable insights on incident management, risk management, client onboarding process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
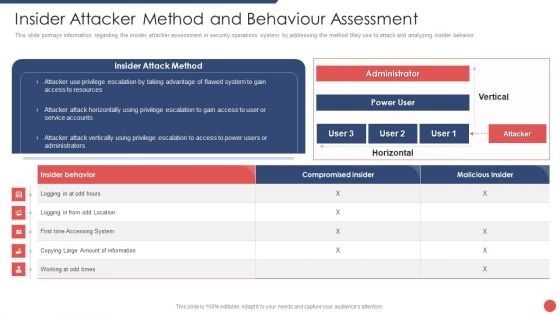
Security Functioning Centre Insider Attacker Method And Behaviour Assessment Ideas PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this security functioning centre insider attacker method and behaviour assessment ideas pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Functioning Centre Impact Of Successful Implementation Of Secops System Slides PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Deliver an awe inspiring pitch with this creative security functioning centre impact of successful implementation of secops system slides pdf bundle. Topics like security analyst productivity, threat, improvement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enhanced Protection Corporate Event Administration Security And Operational Tasks Maintenance Checklist Slides PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration security and operational tasks maintenance checklist slides pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Enhanced Protection Corporate Event Administration Security Operations Implementation Timeline Activity Template PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration security operations implementation timeline activity template pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
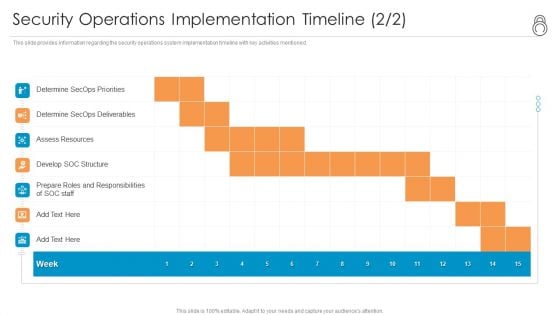
Enhanced Protection Corporate Event Administration Security Operations Implementation Timeline Staff Background PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration security operations implementation timeline staff background pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
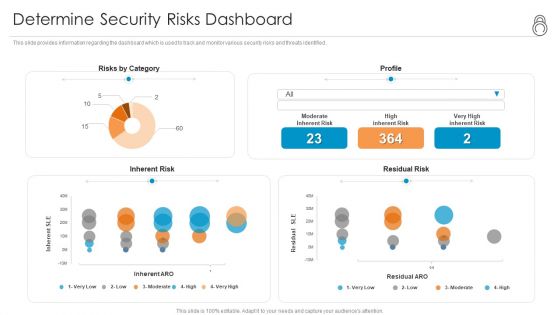
Enhanced Protection Corporate Event Administration Determine Security Risks Dashboard Summary PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration determine security risks dashboard summary pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Process Integration Budget For Effective Secops System Management Brochure PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this security and process integration budget for effective secops system management brochure pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Process Integration Essential Roles And Responsibilities Involved In Secops Background PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure. Deliver and pitch your topic in the best possible manner with this security and process integration essential roles and responsibilities involved in secops background pdf. Use them to share invaluable insights on security engineers, business, communication skills, management, training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
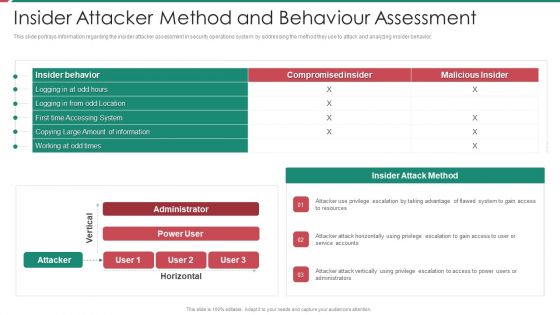
Security And Process Integration Insider Attacker Method And Behaviour Assessment Microsoft PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this security and process integration insider attacker method and behaviour assessment microsoft pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Management Plan Steps In Detail Identifying Goals And Objectives Clipart PDF
Presenting security management plan steps in detail identifying goals and objectives clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like implementation of security, organizational objectives, represent the business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Differentiating 2 Items Visual For Secure Cloud Service Free Mockup PDF
Presenting differentiating 2 items visual for secure cloud service free mockup pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like differentiating 2 items visual for secure cloud service free. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
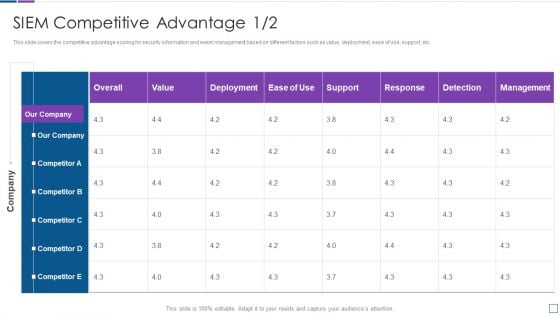
Competitive Advantage Real Time Assessment Of Security Threats SIEM Pictures PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver an awe inspiring pitch with this creative competitive advantage real time assessment of security threats siem pictures pdf bundle. Topics like siem competitive advantage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security And Safety Measures For Hotels Across Hospitality Sector Icons PDF
This slide outlines safety measures for various hotels across hospitality sector. It involves measures such as surveillance cameras, cybersecurity, mobile room keys and providing staff training.Presenting Security And Safety Measures For Hotels Across Hospitality Sector Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Cybersecurity, Security And Ensure, Staff Training This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Safety And Security Objectives In Cyber Physical Systems Ppt Slides Themes PDF
This slide represents cyber physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Presenting Safety And Security Objectives In Cyber Physical Systems Ppt Slides Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Availability, Authenticity, Confidentiality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
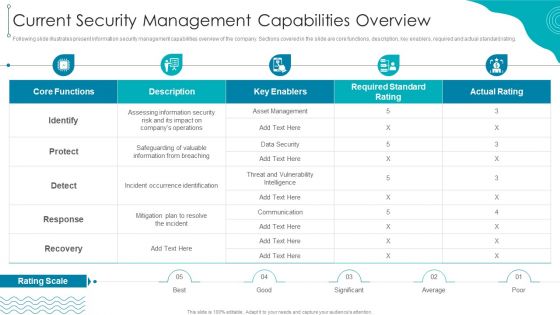
ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF bundle. Topics like Occurrence Identification, Communication, Required Standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
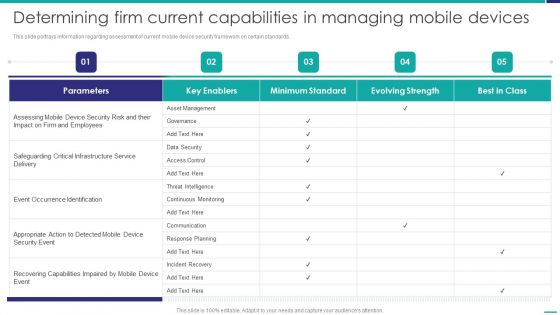
Determining Firm Current Capabilities In Managing Mobile Devices Mobile Device Security Management Summary PDF
This slide portrays information regarding assessment of current mobile device security framework on certain standards. Deliver and pitch your topic in the best possible manner with this Determining Firm Current Capabilities In Managing Mobile Devices Mobile Device Security Management Summary PDF. Use them to share invaluable insights on Asset Management, Critical Infrastructure, Recovering Capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Tracking Mobile Device Activities At Workplace Mobile Device Security Management Topics PDF
This slide covers information regarding the tracking mobile device activities at workplace with details about device security, ownership, last seen status. Deliver and pitch your topic in the best possible manner with this Tracking Mobile Device Activities At Workplace Mobile Device Security Management Topics PDF. Use them to share invaluable insights on Ownership, Seen Breakdown, Total Deployment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Issues Management Process For Enhancing Cyber Security Ppt Icon Picture PDF
This slide signifies increasing cyber security and IT through problem management process. It includes stages like detection, define, investigate, identify resolutions, implement and follow up. Presenting Issues Management Process For Enhancing Cyber Security Ppt Icon Picture PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Problem Detection, Define, Investigate, Identify Resolutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
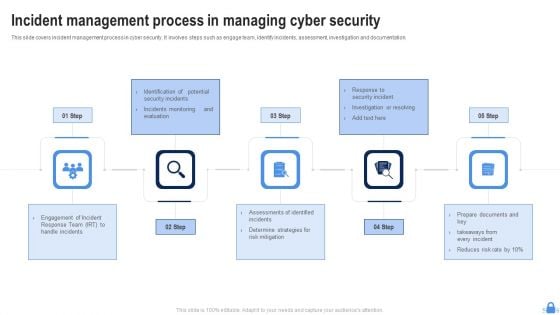
Incident Management Process In Managing Cyber Security Ppt Portfolio Template PDF
This slide covers incident management process in cyber security. It involves steps such as engage team, identify incidents, assessment, investigation and documentation. Presenting Incident Management Process In Managing Cyber Security Ppt Portfolio Template PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Determine Strategies, Risk Mitigation, Engagement Incident. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
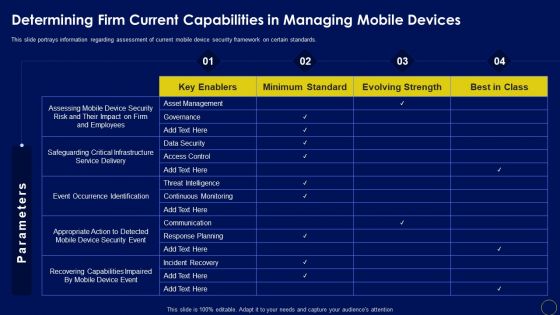
Determining Firm Current Capabilities In Managing Business Mobile Device Security Management Graphics PDF
This slide portrays information regarding assessment of current mobile device security framework on certain standards. Find a pre-designed and impeccable Determining Firm Current Capabilities In Managing Business Mobile Device Security Management Graphics PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Governance Risk And Compliance Icon To Manage IT And Security Risk Guidelines PDF
Presenting Governance Risk And Compliance Icon To Manage IT And Security Risk Guidelines PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Governance, Risk And Compliance, Icon To Manage, IT And Security, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
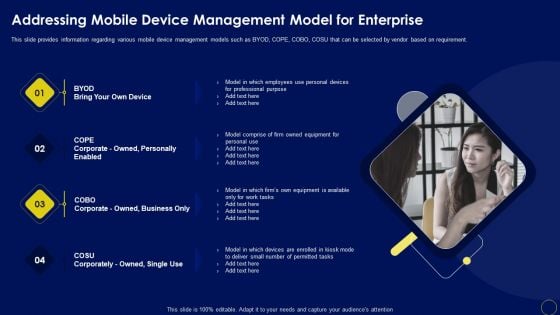
Addressing Mobile Device Management Business Mobile Device Security Management And Mitigation Background PDF
This slide provides information regarding various mobile device management models such as BYOD, COPE, COBO, COSU that can be selected by vendor based on requirement. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Addressing Mobile Device Management Business Mobile Device Security Management And Mitigation Background PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
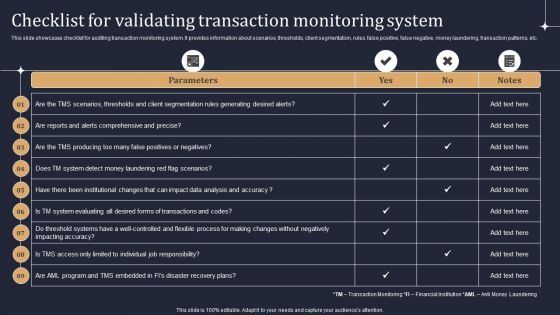
KYC Transaction Monitoring System Business Security Checklist For Validating Transaction Professional PDF
This slide showcases checklist for auditing transaction monitoring system. It provides information about scenarios, thresholds, client segmentation, rules, false positive, false negative, money laundering, transaction patterns, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created KYC Transaction Monitoring System Business Security Checklist For Validating Transaction Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Amazon Tactical Plan How Amazon Secured Brand Position By Maintaining Leadership Microsoft PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features AND services, and subsidiaries. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Amazon Tactical Plan How Amazon Secured Brand Position By Maintaining Leadership Microsoft PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
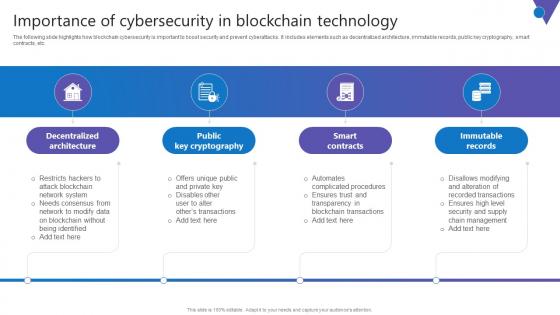
Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Find highly impressive Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc.
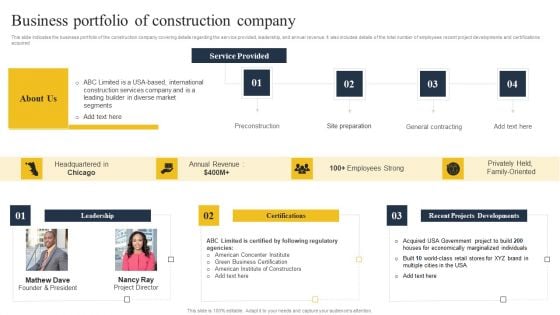
Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF
This slide indicates the business portfolio of the construction company covering details regarding the service provided, leadership, and annual revenue. It also includes details of the total number of employees recent project developments and certifications acquired. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF

Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Slidegeeks has constructed Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
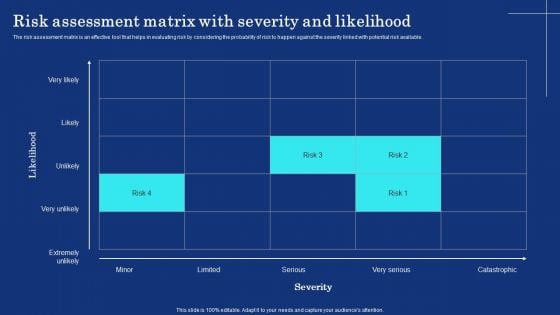
Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF
The risk assessment matrix is an effective tool that helps in evaluating risk by considering the probability of risk to happen against the severity linked with potential risk available. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF.
Operational Safety Guidelines Air Workplace Safety Protocol And Security Practices Icons Pdf
This slides highlights the operational safety guidelines to minimize air compressor hazards. It showcases different protective gears with pre operation, operation and post operation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Operational Safety Guidelines Air Workplace Safety Protocol And Security Practices Icons Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Operational Safety Guidelines Air Workplace Safety Protocol And Security Practices Icons Pdf. This slides highlights the operational safety guidelines to minimize air compressor hazards. It showcases different protective gears with pre operation, operation and post operation.
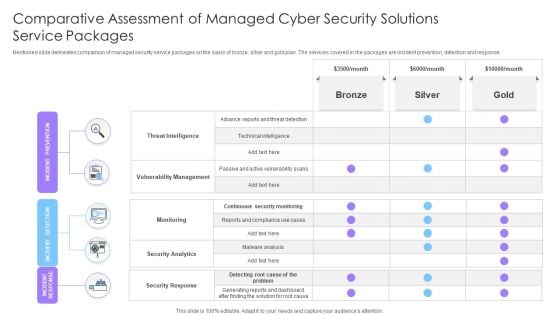
Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF
Mentioned slide delineates comparison of managed security service packages on the basis of bronze, silver and gold plan. The services covered in the packages are incident prevention, detection and response. Showcasing this set of slides titled Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF. The topics addressed in these templates are Threat Intelligence, Vulnerability Management, Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF
This slide shows potential threats along with prevention for online business websites that could damage the business and also lose trust of online customers. the certain threats includes direct site attacks, password assault, social engineering and malwares. Showcasing this set of slides titled E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF. The topics addressed in these templates are Business Security Risks, Threat Type, Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
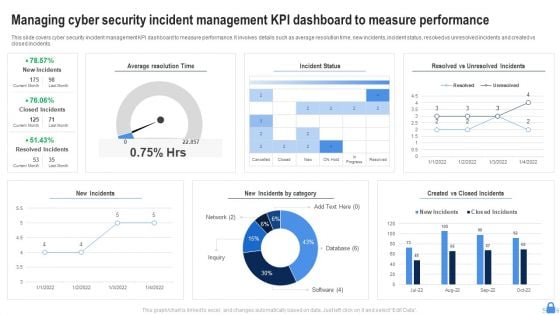
Managing Cyber Security Incident Management KPI Dashboard To Measure Performance Download PDF
This slide covers cyber security incident management KPI dashboard to measure performance. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled Managing Cyber Security Incident Management KPI Dashboard To Measure Performance Download PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































