Data Privacy

Various Rights Of Credit Card Users Swipe Smartly A Practical Guide Fin SS V
This slide shows extensive information regarding various rights of credit card users who uses credit cards for purchases or other expenses. These rights includes right to privacy, receive clear terms, dispute charges, etc. This modern and well-arranged Various Rights Of Credit Card Users Swipe Smartly A Practical Guide Fin SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide shows extensive information regarding various rights of credit card users who uses credit cards for purchases or other expenses. These rights includes right to privacy, receive clear terms, dispute charges, etc.
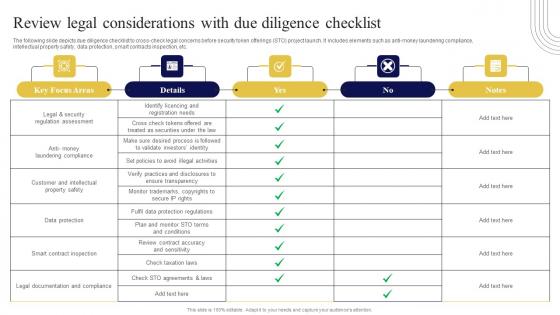
Review Legal Considerations With Due Exploring Investment Opportunities Summary Pdf
The following slide depicts due diligence checklist to cross-check legal concerns before security token offerings STO project launch. It includes elements such as anti-money laundering compliance, intellectual property safety, data protection, smart contracts inspection, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Review Legal Considerations With Due Exploring Investment Opportunities Summary Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Review Legal Considerations With Due Exploring Investment Opportunities Summary Pdf today and make your presentation stand out from the rest The following slide depicts due diligence checklist to cross-check legal concerns before security token offerings STO project launch. It includes elements such as anti-money laundering compliance, intellectual property safety, data protection, smart contracts inspection, etc.
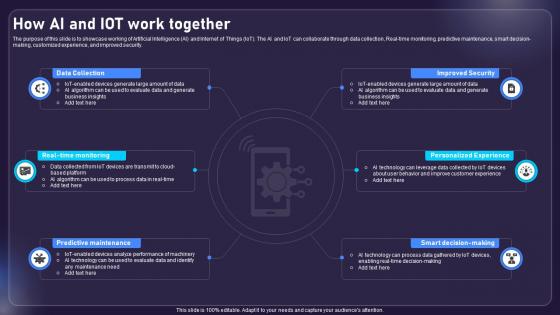
How Ai And Iot Work Together AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase working of Artificial Intelligence AI and Internet of Things IoT. The AI and IoT can collaborate through data collection, Real-time monitoring, predictive maintenance, smart decision-making, customized experience, and improved security. This How Ai And Iot Work Together AIOT Applications For Various Industries IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Ai And Iot Work Together AIOT Applications For Various Industries IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The purpose of this slide is to showcase working of Artificial Intelligence AI and Internet of Things IoT. The AI and IoT can collaborate through data collection, Real-time monitoring, predictive maintenance, smart decision-making, customized experience, and improved security.
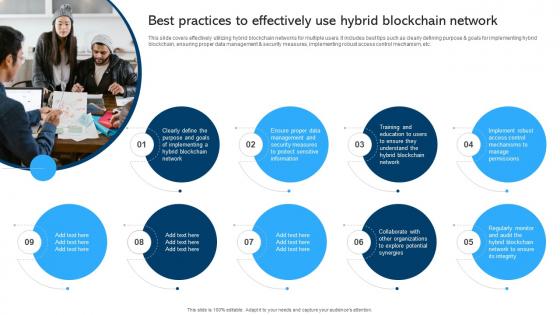
Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V
This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc. Welcome to our selection of the Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc.
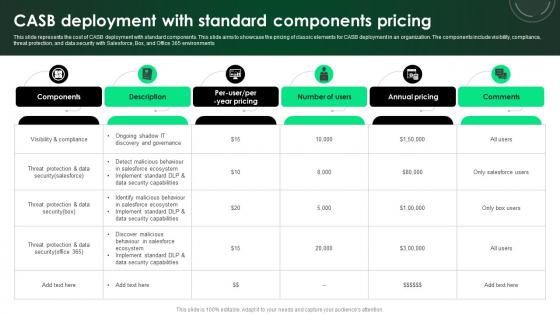
CASB 2 0 IT CASB Deployment With Standard Components Pricing
This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CASB 2 0 IT CASB Deployment With Standard Components Pricing can be your best option for delivering a presentation. Represent everything in detail using CASB 2 0 IT CASB Deployment With Standard Components Pricing and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments
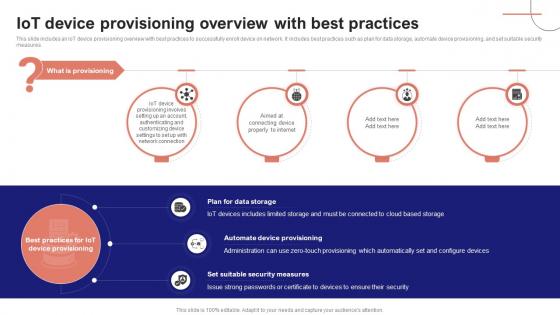
IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT Ss V
This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT SS V can be your best option for delivering a presentation. Represent everything in detail using IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures.
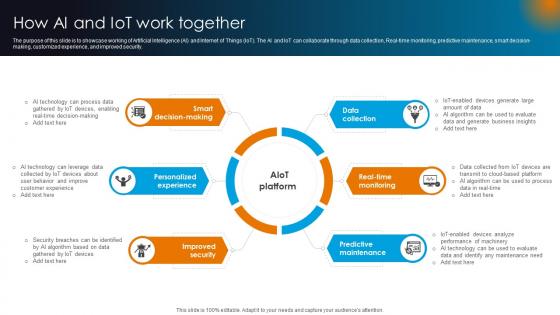
Integrating AI With IoT How Ai And IoT Work Together IoT SS V
The purpose of this slide is to showcase working of Artificial Intelligence AI and Internet of Things IoT. The AI and IoT can collaborate through data collection, Real-time monitoring, predictive maintenance, smart decision-making, customized experience, and improved security. This modern and well-arranged Integrating AI With IoT How Ai And IoT Work Together IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The purpose of this slide is to showcase working of Artificial Intelligence AI and Internet of Things IoT. The AI and IoT can collaborate through data collection, Real-time monitoring, predictive maintenance, smart decision-making, customized experience, and improved security.
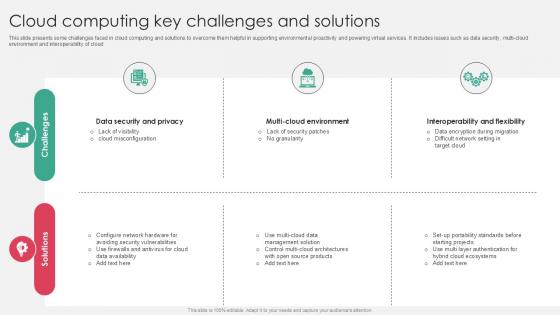
Cloud Computing Key Challenges And Solutions PPT Presentation SS
This slide presents some challenges faced in cloud computing and solutions to overcome them helpful in supporting environmental proactivity and powering virtual services. It includes issues such as data security, multi-cloud environment and interoperability of cloud. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cloud Computing Key Challenges And Solutions PPT Presentation SS a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cloud Computing Key Challenges And Solutions PPT Presentation SS. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide presents some challenges faced in cloud computing and solutions to overcome them helpful in supporting environmental proactivity and powering virtual services. It includes issues such as data security, multi-cloud environment and interoperability of cloud

ERP Powerpoint Ppt Template Bundles
Want to outdo your competitors Create a persuasive presentation template, pitch your business offerings, and win your clients using this well-structured ERP Powerpoint Ppt Template Bundles. Deploy this presentation template of colorful, graphical Education Sector, Health Care, Food Industry, Workflow Management, Resource Allocation slides that encourages a roomful of people to go through the entire proposal. Use this actionable PPT slide and highlight your company background, products, team, and experience to create the desired impact. Incorporate this presentation template and save time and effort in creating a presentation from scratch to highlight the uniqueness of your business. Download now. Enterprise Resource Planning ERP is a software system that support organizations in optimizing their key business processes, such as finance, HR, manufacturing, supply chain, sales, and procurement, by offering a unified perspective of operations and providing a unified data source. The purpose is to enhance operational efficiency, provide real-time data and insights and reduce operational expenses. This template includes ERP systems applications across various domains, security threats and prevention strategies, role of AI and major impacts.
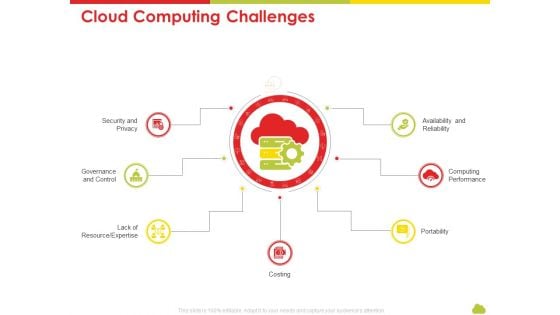
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Cloud Computing Challenges Download PDF
Presenting mesh computing technology hybrid private public iaas paas saas workplan cloud computing challenges download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like portability, costing, resource, security and privacy, availability and reliability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
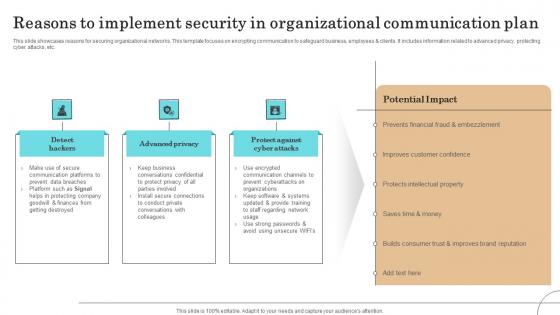
Reasons To Implement Security In Organizational Communication Plan Sample Pdf
This slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.Showcasing this set of slides titled Reasons To Implement Security In Organizational Communication Plan Sample Pdf The topics addressed in these templates are Communication Platforms, Protecting Company, Improves Customer Confidence All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.

Concept Of Locked Money Finance PowerPoint Templates And PowerPoint Themes 1012
Concept Of Locked Money Finance PowerPoint Templates And PowerPoint Themes 1012-Develop competitive advantage with our above template which contains a diagram of 3d money and lock. This image signifies the concept of data security. This image has been conceived to enable you to emphatically communicate your ideas in your Business and Financial PPT presentations on finance, protection and banking. Our PPT images are so perfectly designed that it reveals the very basis of our PPT template to make your clients understand.-Concept Of Locked Money Finance PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Money and lock, security, success, money, finance, business Describe your path to success with our Concept Of Locked Money Finance PowerPoint Templates And PowerPoint Themes 1012. You will come out on top.

Dollars With Lock And Chain Money Investment PowerPoint Templates And PowerPoint Themes 1012
Dollars With Lock And Chain Money Investment PowerPoint Templates And PowerPoint Themes 1012-Create dynamic Microsoft office PPT Presentations with our professional templates containing a graphic of dollars with lock and chain. This image signifies the concept of data security and money investment. This image has been conceived to enable you to emphatically communicate your ideas in your Business and Financial PPT presentations on finance, protection and banking. Our PPT images are so perfectly designed that it reveals the very basis of our PPT template to make your clients understand.-Dollars With Lock And Chain Money Investment PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Dollars chained and locked, business, security, finance, money, chains Buzz the right word with our Dollars With Lock And Chain Money Investment PowerPoint Templates And PowerPoint Themes 1012. You will come out on top.
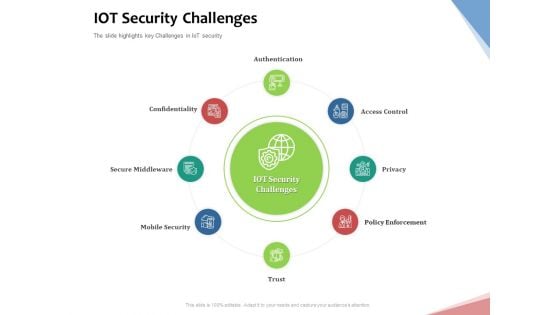
Machine To Machine Communication Outline Iot Security Challenges Ppt File Background Designs PDF
The slide highlights key Challenges in IoT security. Presenting machine to machine communication outline iot security challenges ppt file background designs pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like authentication, access control, privacy, policy enforcement, trust, mobile security, secure middleware, confidentiality. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
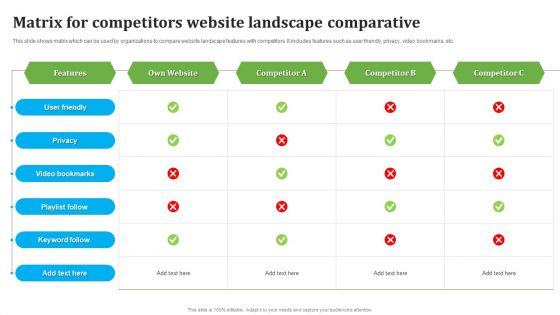
Matrix For Competitors Website Landscape Comparative Themes PDF
This slide shows matrix which can be used by organizations to compare website landscape features with competitors. It includes features such as user friendly, privacy, video bookmarks, etc. Pitch your topic with ease and precision using this Matrix For Competitors Website Landscape Comparative Themes PDF. This layout presents information onMatrix Competitors, Website Landscape Comparative . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Comparative Analysis Of Top Content Management Developing And Creating Digital Content Strategy SS V
The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc. There are so many reasons you need a Comparative Analysis Of Top Content Management Developing And Creating Digital Content Strategy SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc.
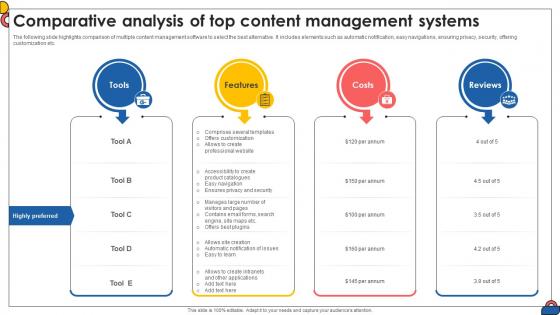
Comparative Analysis Of Top Content Management Comprehensive Guide To Implement Strategy SS V
The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Analysis Of Top Content Management Comprehensive Guide To Implement Strategy SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Analysis Of Top Content Management Comprehensive Guide To Implement Strategy SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc.
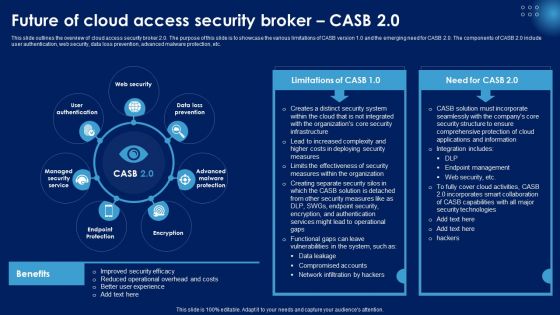
Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF
This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Explore a selection of the finest Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
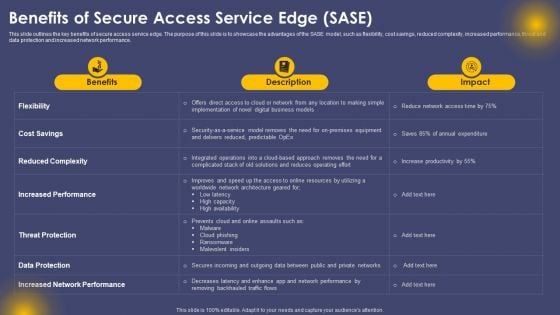
Benefits Of Secure Access Service Edge SASE Ppt Pictures Demonstration PDF
This slide outlines the key benefits of secure access service edge. The purpose of this slide is to showcase the advantages of the SASE model, such as flexibility, cost savings, reduced complexity, increased performance, threat and data protection and increased network performance. This Benefits Of Secure Access Service Edge SASE Ppt Pictures Demonstration PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Cloud Security Implementation Strategy Ppt Presentation

Securing Investor Funding The DocuSign Elevator Pitch Deck Ppt Template

Network Security Using Firewall As A Service Ppt PowerPoint Presentation Complete Deck With Slides
This Network Security Using Firewall As A Service Ppt PowerPoint Presentation Complete Deck With Slides is designed to help you retain your audiences attention. This content-ready PowerPoint Template enables you to take your audience on a journey and share information in a way that is easier to recall. It helps you highlight the crucial parts of your work so that the audience does not get saddled with information download. This eight three slide PPT Deck comes prepared with the graphs and charts you could need to showcase your information through visuals. You only need to enter your own data in them. Download this editable PowerPoint Theme and walk into that meeting with confidence. Our Network Security Using Firewall As A Service Ppt PowerPoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Bridging Blockchains A Deep Key Benefits Of Atomic Swap Technology BCT SS V
This slide mentions key advantages obtained by using atomic swap technique to achieve blockchain interoperability. It includes decentralized nature, enhanced security, interoperability, reduced counterparty risk and privacy. Are you searching for a Bridging Blockchains A Deep Key Benefits Of Atomic Swap Technology BCT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Bridging Blockchains A Deep Key Benefits Of Atomic Swap Technology BCT SS V from Slidegeeks today. This slide mentions key advantages obtained by using atomic swap technique to achieve blockchain interoperability. It includes decentralized nature, enhanced security, interoperability, reduced counterparty risk and privacy.

Understanding Various Blockchain Key Benefits Of Atomic Swap Technology BCT SS V
This slide mentions key advantages obtained by using atomic swap technique to achieve blockchain interoperability. It includes decentralized nature, enhanced security, interoperability, reduced counterparty risk and privacy. Slidegeeks has constructed Understanding Various Blockchain Key Benefits Of Atomic Swap Technology BCT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide mentions key advantages obtained by using atomic swap technique to achieve blockchain interoperability. It includes decentralized nature, enhanced security, interoperability, reduced counterparty risk and privacy.
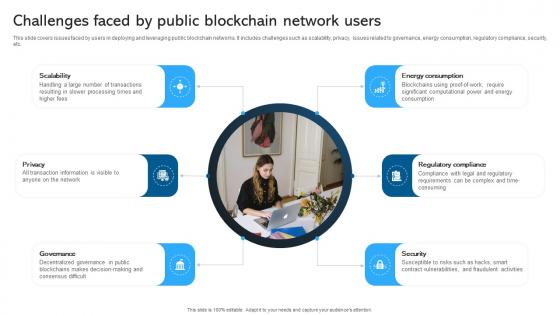
Comprehensive Manual Challenges Faced By Public Blockchain Network Users BCT SS V
This slide covers issues faced by users in deploying and leveraging public blockchain networks. It includes challenges such as scalability, privacy, issues related to governance, energy consumption, regulatory compliance, security, etc. Boost your pitch with our creative Comprehensive Manual Challenges Faced By Public Blockchain Network Users BCT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers issues faced by users in deploying and leveraging public blockchain networks. It includes challenges such as scalability, privacy, issues related to governance, energy consumption, regulatory compliance, security, etc.
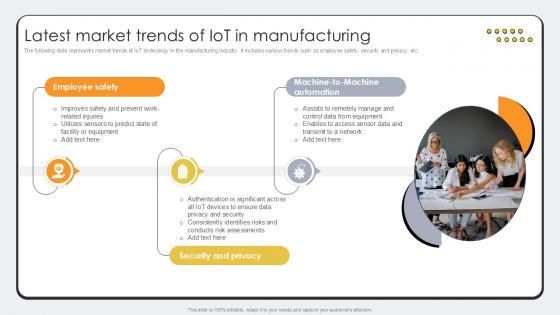
Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example
The following slide represents market trends of IoT technology in the manufacturing industry. It includes various trends such as employee safety, security and privacy, etc. Presenting this PowerPoint presentation, titled Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide represents market trends of IoT technology in the manufacturing industry. It includes various trends such as employee safety, security and privacy, etc.

Stock Photo Internet Symbol With Lock PowerPoint Slide
This image slide displays internet symbol with lock. This conceptual image slide has been designed with graphic of blue color at the rate symbol and lock. This image slide depicts online security. Use this PowerPoint template, in your presentations to express views on e-mail, internet, security, safeguard, password and privacy. This image may also be used to exhibit technology protection. This wonderful image is sure to help you achieve your goal of making professional presentations.
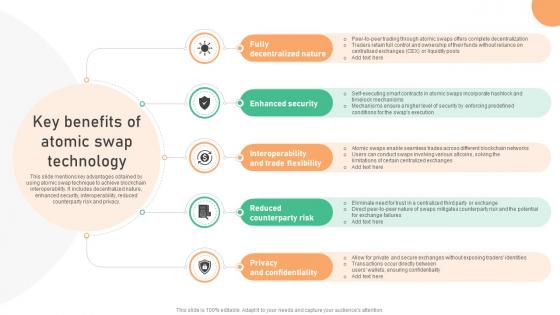
Seamless Integration The Power Key Benefits Of Atomic Swap Technology BCT SS V
This slide mentions key advantages obtained by using atomic swap technique to achieve blockchain interoperability. It includes decentralized nature, enhanced security, interoperability, reduced counterparty risk and privacy. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Seamless Integration The Power Key Benefits Of Atomic Swap Technology BCT SS V from Slidegeeks and deliver a wonderful presentation. This slide mentions key advantages obtained by using atomic swap technique to achieve blockchain interoperability. It includes decentralized nature, enhanced security, interoperability, reduced counterparty risk and privacy.
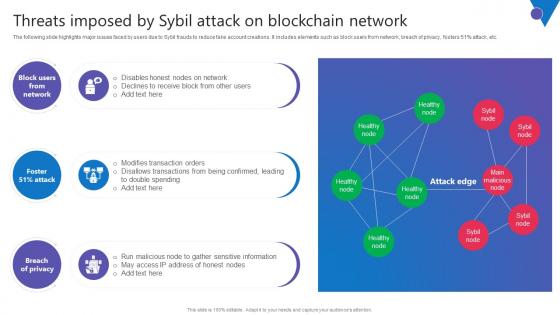
Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Threats Imposed By Sybil Attack Comprehensive Guide To Blockchain Digital Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide highlights major issues faced by users due to Sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc.

Why Invest With Us Digital Payment Platform Pitch Deck
This slide mentions the various reasons why potential investors should be investing with the company. Key reasons strong product offering, ROI for investors, security and privacy, AI integrated technology, investment option, growing user base. Explore a selection of the finest Why Invest With Us Digital Payment Platform Pitch Deck here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Why Invest With Us Digital Payment Platform Pitch Deck to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide mentions the various reasons why potential investors should be investing with the company. Key reasons strong product offering, ROI for investors, security and privacy, AI integrated technology, investment option, growing user base.

Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V
This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks. Find highly impressive Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Comprehensive Look At Blockchain Challenges Of Blockchain Integration BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks.

Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V
This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks. Find highly impressive Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Visionary Guide To Blockchain Challenges Of Blockchain Integration In Cybersecurity BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide mentions the various challenges faced in integrating blockchain technology in cybersecurity and their corresponding benefits of integration. Key challenges evaluated include scalability, interoperability, privacy, regulatory and security risks.
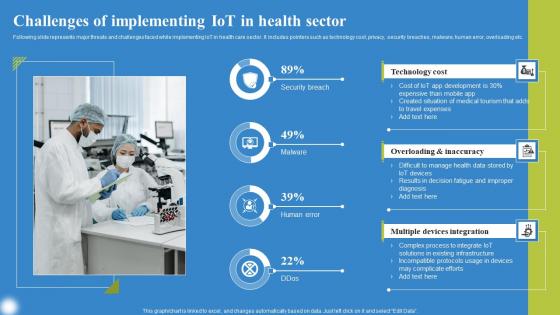
Challenges Of Implementing IoT Deploying IoT Solutions For Enhanced Healthcare Background Pdf
Following slide represents major threats and challenges faced while implementing IoT in health care sector. It includes pointers such as technology cost, privacy, security breaches, malware, human error, overloading etc. Retrieve professionally designed Challenges Of Implementing IoT Deploying IoT Solutions For Enhanced Healthcare Background Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Following slide represents major threats and challenges faced while implementing IoT in health care sector. It includes pointers such as technology cost, privacy, security breaches, malware, human error, overloading etc.
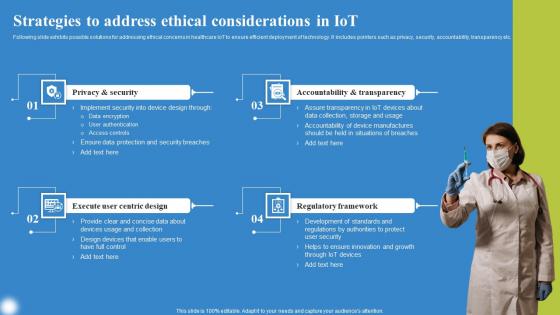
Strategies To Address Ethical Deploying IoT Solutions For Enhanced Healthcare Background Pdf
Following slide exhibits possible solutions for addressing ethical concerns in healthcare IoT to ensure efficient deployment of technology. It includes pointers such as privacy, security, accountability, transparency etc. Want to ace your presentation in front of a live audience Our Strategies To Address Ethical Deploying IoT Solutions For Enhanced Healthcare Background Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. Following slide exhibits possible solutions for addressing ethical concerns in healthcare IoT to ensure efficient deployment of technology. It includes pointers such as privacy, security, accountability, transparency etc.

Ethical Considerations In Artificial Intelligence Of Things AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase various ethical considerations in Artificial Intelligence of Things AIoT. Privacy, biasness, transparency, safety, and accountability are some of the major considerations that need to be addressed to ensure technology benefits society. Make sure to capture your audiences attention in your business displays with our gratis customizable Ethical Considerations In Artificial Intelligence Of Things AIOT Applications For Various Industries IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The purpose of this slide is to showcase various ethical considerations in Artificial Intelligence of Things AIoT. Privacy, biasness, transparency, safety, and accountability are some of the major considerations that need to be addressed to ensure technology benefits society.

A113 Comparative Assessment Of Various Payment Cryptocurrencies
Mentioned slide demonstrates comparative analysis of various crypto coins which can be used by businesses in cashless payment. It includes key points such as launch year, trading value, transaction rate, transaction fees, privacy, block time, and trading history. There are so many reasons you need a A113 Comparative Assessment Of Various Payment Cryptocurrencies. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Mentioned slide demonstrates comparative analysis of various crypto coins which can be used by businesses in cashless payment. It includes key points such as launch year, trading value, transaction rate, transaction fees, privacy, block time, and trading history.
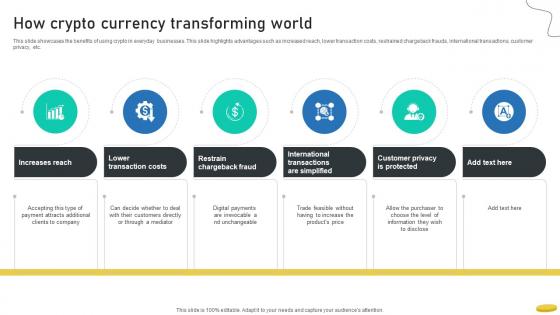
How Crypto Currency Transforming World Cryptocurrency Management With Blockchain
This slide showcases the benefits of using crypto in everyday businesses. This slide highlights advantages such as increased reach, lower transaction costs, restrained chargeback frauds, international transactions, customer privacy, etc.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download How Crypto Currency Transforming World Cryptocurrency Management With Blockchain to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the How Crypto Currency Transforming World Cryptocurrency Management With Blockchain. This slide showcases the benefits of using crypto in everyday businesses. This slide highlights advantages such as increased reach, lower transaction costs, restrained chargeback frauds, international transactions, customer privacy, etc.
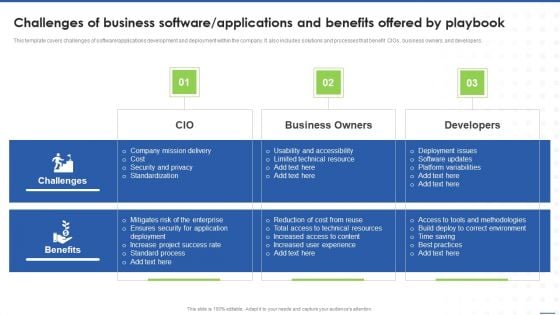
Challenges Of Business Software Applications And Benefits Offered By Playbook Mockup PDF
This template covers challenges of software applications development and deployment within the company. It also includes solutions and processes that benefit CIOs, business owners, and developers.Deliver an awe inspiring pitch with this creative Challenges Of Business Software Applications And Benefits Offered By Playbook Mockup PDF bundle. Topics like Company Mission, Security And Privacy, Limited Technical can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
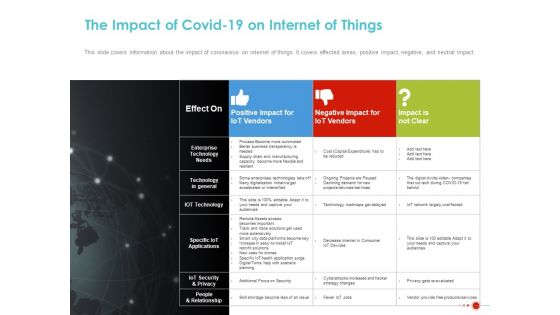
COVID 19 Mitigating Impact On High Tech Industry The Impact Of COVID 19 On Internet Of Things Brochure PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry the impact of covid 19 on internet of things brochure pdf. The topics discussed in these slides are positive impact, iot vendors, negative impact iot vendors, impact not clear, enterprise technology needs, technology general, iot technology, specific iot applications, iot security and privacy, people and relationship. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
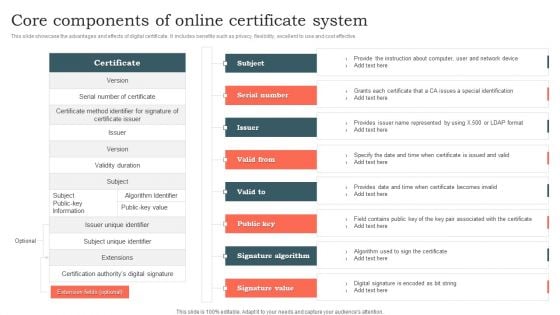
Core Components Of Online Certificate System Ppt Pictures Outline PDF
This slide showcase the advantages and effects of digital certificate. It includes benefits such as privacy, flexibility, excellent to use and cost effective. Showcasing this set of slides titled Core Components Of Online Certificate System Ppt Pictures Outline PDF. The topics addressed in these templates are Extension Fields, Certificate, Validity Duration. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Blockchain Business Methodology Impact On Business Operations Information PDF
This slide covers the details related to the advantages of blockchain technology for business. The purpose of this template is to defines blockchain as it helps to increase trust, security, transparency and bring other benefits to businesses. It includes details related to innovation, reduced cost, etc. Pitch your topic with ease and precision using this Blockchain Business Methodology Impact On Business Operations Information PDF. This layout presents information on Innovation, Security And Privacy, Tokenization, Cost. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Create an editable Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Automation Framework Impacts Of Ineffective Information Technology Security Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
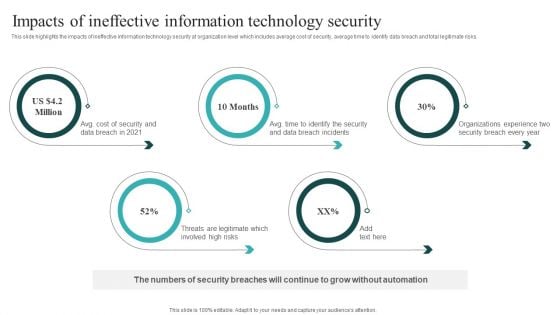
IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Get a simple yet stunning designed IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
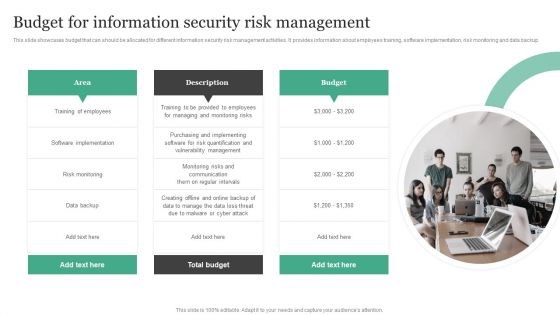
Budget For Information Security Risk Management Information Security Risk Administration Guidelines PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Budget For Information Security Risk Management Information Security Risk Administration Guidelines PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Budget For Information Security Risk Management Information Security Risk Administration Guidelines PDF.

Developing IT Security Strategy Budget For Information Security Risk Management Information PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. This Developing IT Security Strategy Budget For Information Security Risk Management Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Budget For Information Security Risk Management Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. This Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
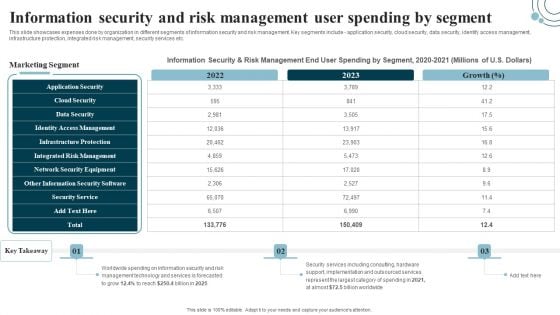
Developing IT Security Strategy Information Security And Risk Management User Spending Structure PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include - application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. Present like a pro with Developing IT Security Strategy Information Security And Risk Management User Spending Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Are you searching for a Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Organizing Security Awareness Need For Cyber Security Awareness Training Rules PDF from Slidegeeks today.
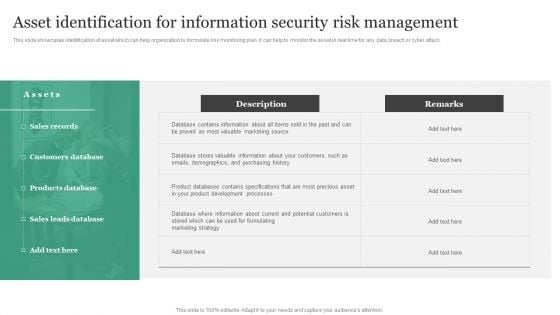
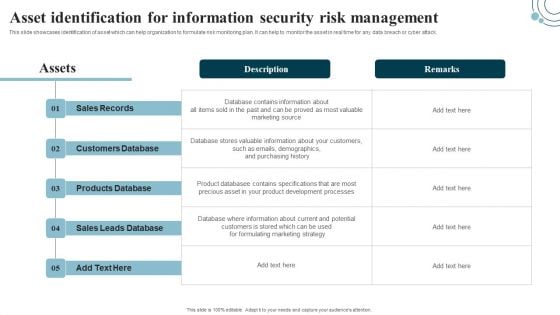
Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Slidegeeks has constructed Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Explore a selection of the finest Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. Take your projects to the next level with our ultimate collection of Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
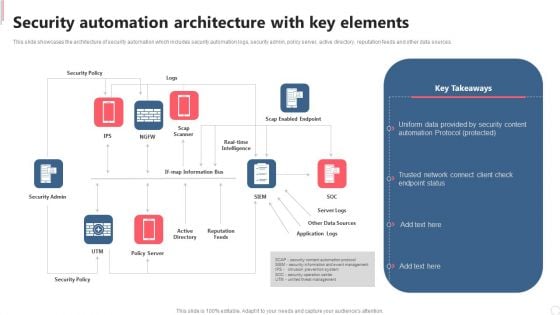
Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. This modern and well arranged Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Retrieve professionally designed Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.
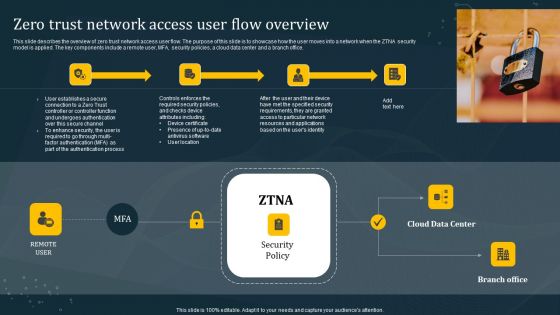
Zero Trust Network Access User Flow Overview Mockup PDF
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Create an editable Zero Trust Network Access User Flow Overview Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Zero Trust Network Access User Flow Overview Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Key Characteristics Of Modern ZTNA Solution Portrait PDF
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Are you searching for a Key Characteristics Of Modern ZTNA Solution Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Key Characteristics Of Modern ZTNA Solution Portrait PDF from Slidegeeks today.

Information Security Adhere To Strict Compliance Requirements Diagrams PDF
This slide shows that you can use a data classification engine to locate and categorize regulated and sensitive material also, compliance standards serve as a foundation. If you are looking for a format to display your unique thoughts, then the professionally designed Information Security Adhere To Strict Compliance Requirements Diagrams PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Security Adhere To Strict Compliance Requirements Diagrams PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Information Systems Security And Risk Management Plan Estimated Impact Of Information Security Risk Management Plan Ideas PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating. This Information Systems Security And Risk Management Plan Estimated Impact Of Information Security Risk Management Plan Ideas PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF
This slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Present like a pro with Challenges With Traditional Network Security Approaches Ppt Gallery Icon PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.


 Continue with Email
Continue with Email

 Home
Home


































