Data Protection Strategy Template
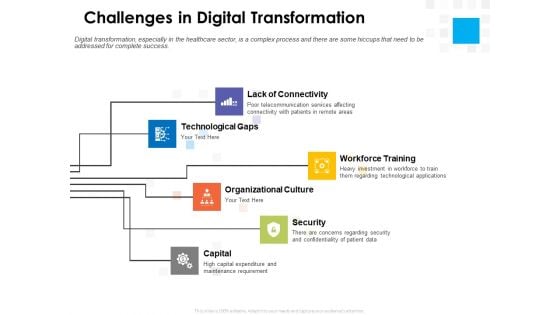
Digital Transformation Strategy Roadmap Challenges In Digital Transformation Ppt PowerPoint Presentation Model Introduction PDF
Presenting this set of slides with name digital transformation strategy roadmap challenges in digital transformation ppt powerpoint presentation model introduction pdf. This is a stage process. The stages in this process are lack connectivity, technological gaps, workforce training, organizational culture, security, capital. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Post COVID Recovery Strategy Oil Gas Industry Strategizing The New Normal For Energy Industry Demonstration PDF
This slide provides the details of the new normal for energy industry which focuses on oil and gas sector such as volatility, risks, supply security, vulnerability, automation and digitalization, Behavioural change, etc. Deliver an awe inspiring pitch with this creative post covid recovery strategy oil gas industry strategizing the new normal for energy industry demonstration pdf bundle. Topics like preparing for volatility and risks, focus on security of supply, new sense of vulnerability, introduce automation and digitalization, considering implications of behavioural change can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
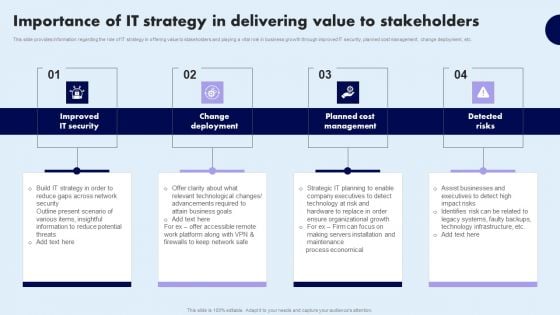
Importance Of IT Strategy In Delivering Value To Stakeholders Elements PDF
This slide provides information regarding the role of IT strategy in offering value to stakeholders and playing a vital role in business growth through improved IT security, planned cost management, change deployment, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Importance Of IT Strategy In Delivering Value To Stakeholders Elements PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
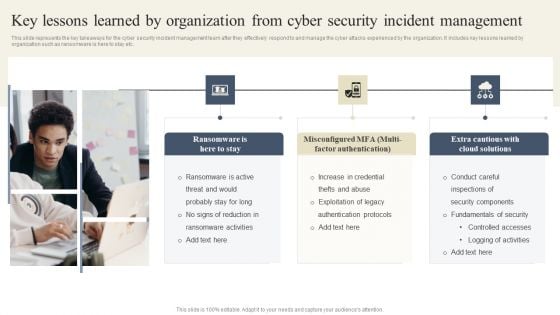
CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. This CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Increasing Business Awareness Overview Of Linked In Networking To Promote Strategy SS V
This slide presents an overview of linked-in networking to promote the insurance business online. It includes bets practices for influencing existence on linked din and goals such as, providing education, generate high-quality leads and improving presence in search results. Present like a pro with Increasing Business Awareness Overview Of Linked In Networking To Promote Strategy SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide presents an overview of linked-in networking to promote the insurance business online. It includes bets practices for influencing existence on linked din and goals such as, providing education, generate high-quality leads and improving presence in search results.
Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF
This slide signifies the strategic plan timeline to create effective cyber security project. It covers information about steps like identify, analyse, evaluate, prioritise, treat and monitor Persuade your audience using this Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate, Identify, Analyse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
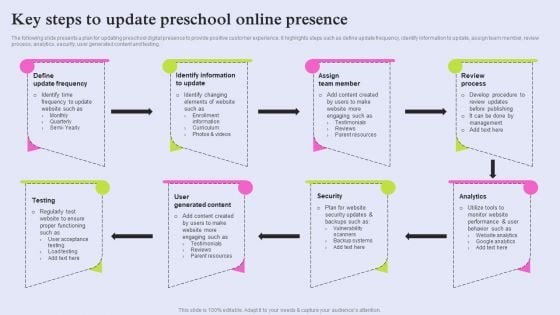
Pre School Marketing Strategy To Enhance Enrollment Rate Key Steps To Update Preschool Rules PDF
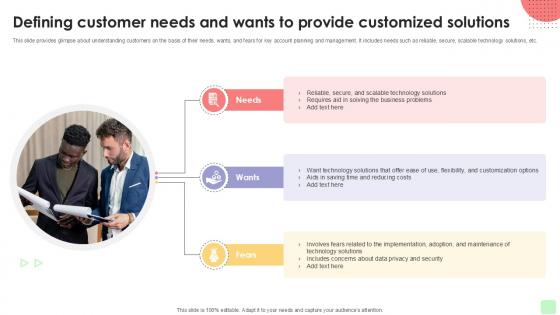
Defining Customer Needs And Wants Detailed Business Account PPT Presentation Strategy SS V
This slide provides glimpse about understanding customers on the basis of their needs, wants, and fears for key account planning and management. It includes needs such as reliable, secure, scalable technology solutions, etc. While your presentation may contain top-notch content, if it lacks visual appeal, youre not fully engaging your audience. Introducing our Defining Customer Needs And Wants Detailed Business Account PPT Presentation Strategy SS V deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, its downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck. This slide provides glimpse about understanding customers on the basis of their needs, wants, and fears for key account planning and management. It includes needs such as reliable, secure, scalable technology solutions, etc.
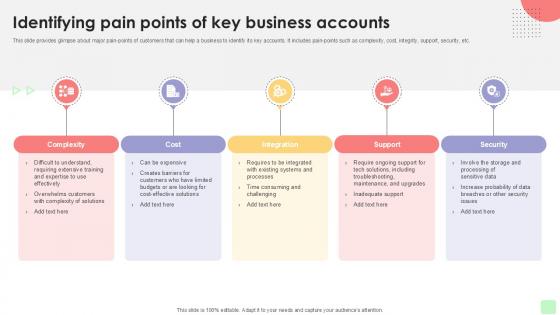
Identifying Pain Points Of Detailed Business Account PPT PowerPoint Strategy SS V
This slide provides glimpse about major pain points of customers that can help a business to identify its key accounts. It includes pain points such as complexity, cost, integrity, support, security, etc. While your presentation may contain top-notch content, if it lacks visual appeal, youre not fully engaging your audience. Introducing our Identifying Pain Points Of Detailed Business Account PPT PowerPoint Strategy SS V deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, its downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck. This slide provides glimpse about major pain points of customers that can help a business to identify its key accounts. It includes pain points such as complexity, cost, integrity, support, security, etc.

Impact Of Block Chain Strategy On B2B Ecommerce Platform Ideas PDF
This slide covers positive impact of block chain technology on B2B ecommerce business. It includes preventing tax liabilities, loyalty programs authencity, combating fake reviews, eliminate financial inefficiencies and efficient sales process.Persuade your audience using this Impact Of Block Chain Strategy On B2B Ecommerce Platform Ideas PDF This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Tax Liabilities, Programs Authenticity, Eliminate Financial Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
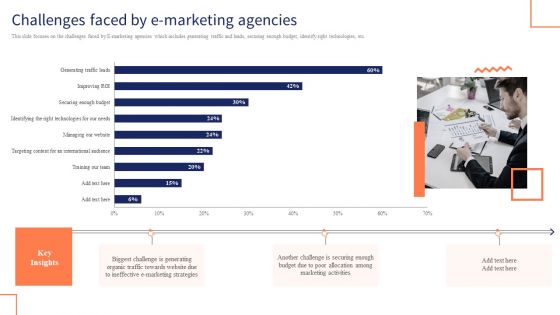
Optimizing Digital Channels To Enhance Marketing Strategy Challenges Faced By E Marketing Agencies Elements PDF
This slide focuses on the challenges faced by E marketing agencies which includes generating traffic and leads, securing enough budget, identify right technologies, etc. This Optimizing Digital Channels To Enhance Marketing Strategy Challenges Faced By E Marketing Agencies Elements PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Developing Firm Security Strategy Plan Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty two slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.
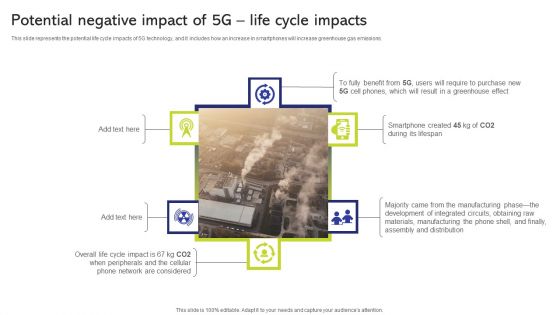
5G And 4G Networks Comparative Analysis Potential Negative Impact Of 5G Life Cycle Impacts Template PDF
This slide represents the potential life cycle impacts of 5G technology, and it includes how an increase in smartphones will increase greenhouse gas emissions. Deliver and pitch your topic in the best possible manner with this 5G And 4G Networks Comparative Analysis Potential Negative Impact Of 5G Life Cycle Impacts Template PDF. Use them to share invaluable insights on Require, Purchase, Development and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cognitive Radio Network IT Spectrum Database Overview And Limitations Template PDF
This slide describes the overview and limitations of the spectrum database that is proposed by the FCC to simplify spectrum sensing and avoid traditional costly and time-consuming processes. Its limitations include significant spectrum gaps, difficulty keeping up with dynamic and real-time spectrum activity, etc. Find highly impressive Cognitive Radio Network IT Spectrum Database Overview And Limitations Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cognitive Radio Network IT Spectrum Database Overview And Limitations Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
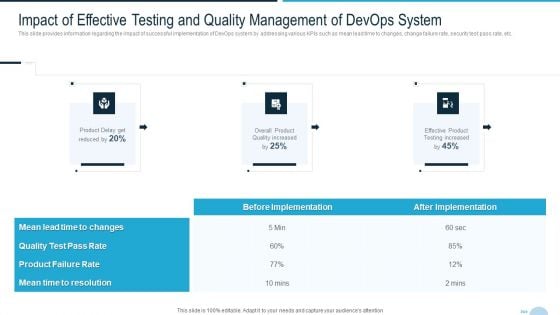
Development And Operations Quality Assurance And Validation IT Impact Of Effective Testing And Quality Template PDF
This slide provides information regarding the impact of successful implementation of DevOps system by addressing various KPIs such as mean lead time to changes, change failure rate, security test pass rate, etc. Deliver and pitch your topic in the best possible manner with this development and operations quality assurance and validation it impact of effective testing and quality template pdf Use them to share invaluable insights on product failure, quality test pass, mean time to resolution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

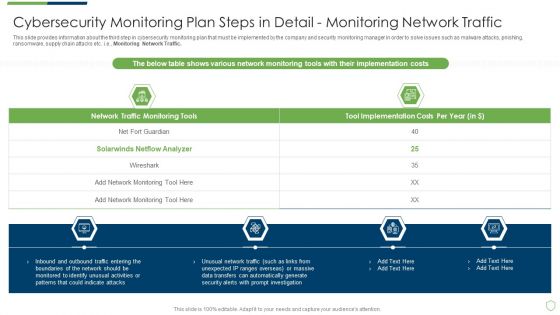
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Professional PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in professional pdf bundle. Topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
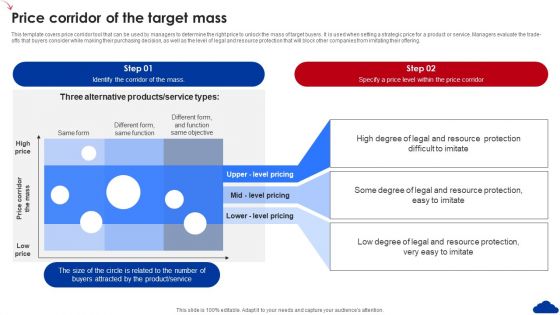
5 Step Guide For Transitioning To Blue Ocean Strategy Price Corridor Of The Target Mass Guidelines PDF
This template covers price corridor tool that can be used by managers to determine the right price to unlock the mass of target buyers. It is used when setting a strategic price for a product or service. Managers evaluate the trade-offs that buyers consider while making their purchasing decision, as well as the level of legal and resource protection that will block other companies from imitating their offering. Find a pre-designed and impeccable 5 Step Guide For Transitioning To Blue Ocean Strategy Price Corridor Of The Target Mass Guidelines PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Post COVID Recovery Strategy Oil Gas Industry Five Crisis Responses For Oil And Gas Companies Slides PDF
This slide covers the 5 crisis responses for oil and gas companies such as manage liquidity, cut costs and capital expenditure, consolidate, protect revenues streams, and monetize volatility. Deliver an awe inspiring pitch with this creative post covid recovery strategy oil gas industry five crisis responses for oil and gas companies slides pdf bundle. Topics like mzanage liquidity, consolidate, protect the revenues streams, cut costs and capital expenditure, monetize volatility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
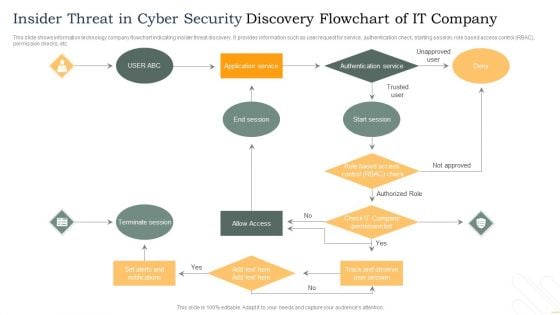
Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
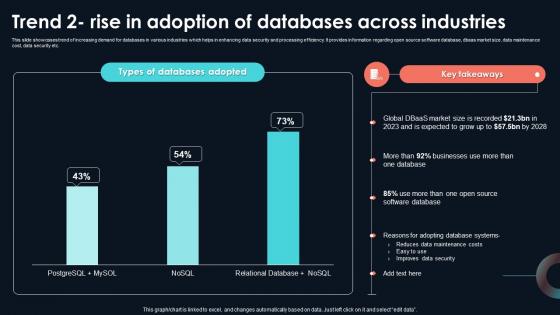
Trend 2 Rise In Adoption Of Databases Across Developing Strategic Insights Using Big Data Analytics SS V
This slide showcases trend of increasing demand for databases in various industries which helps in enhancing data security and processing efficiency. It provides information regarding open source software database, dbaas market size, data maintenance cost, data security etc. This Trend 2 Rise In Adoption Of Databases Across Developing Strategic Insights Using Big Data Analytics SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases trend of increasing demand for databases in various industries which helps in enhancing data security and processing efficiency. It provides information regarding open source software database, dbaas market size, data maintenance cost, data security etc.

Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Boost your pitch with our creative Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
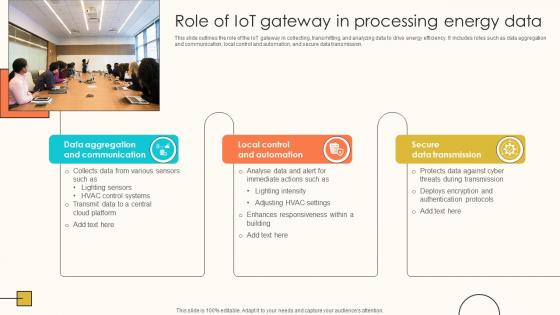
Role Of IoT Gateway In Processing Energy Data Internet Of Things Solutions To Enhance Energy IoT SS V
This slide outlines the role of the IoT gateway in collecting, transmitting, and analyzing data to drive energy efficiency. It includes roles such as data aggregation and communication, local control and automation, and secure data transmission. Do you know about Slidesgeeks Role Of IoT Gateway In Processing Energy Data Internet Of Things Solutions To Enhance Energy IoT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the role of the IoT gateway in collecting, transmitting, and analyzing data to drive energy efficiency. It includes roles such as data aggregation and communication, local control and automation, and secure data transmission.
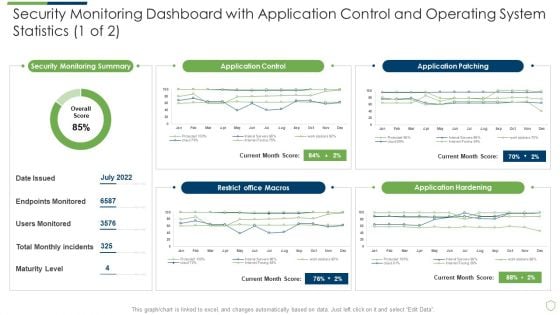
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Application Slides PDF
Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with application slides pdf. Use them to share invaluable insights on security monitoring dashboard with application control and operating system statistics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
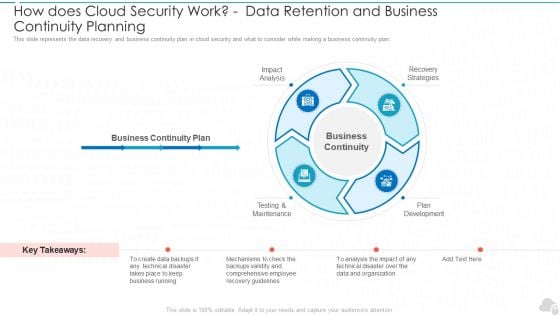
How Does Cloud Security Work Data Retention And Business Continuity Planning Cloud Computing Security IT Ppt Slides Demonstration PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. This is a how does cloud security work data retention and business continuity planning cloud computing security it ppt slides demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact analysis, testing and maintenance, plan development, recovery strategies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
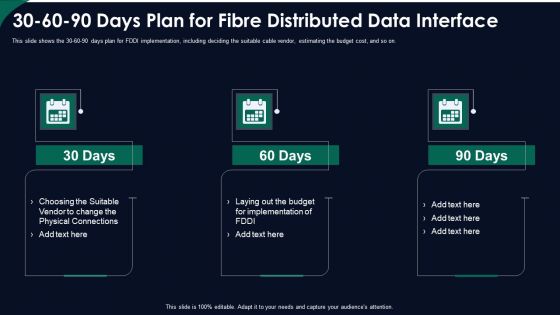
FDDI Network Standard IT 30 60 90 Days Plan For Fibre Distributed Data Interface Ppt Inspiration Diagrams PDF
This slide shows the 30 60 90 days plan for FDDI implementation, including deciding the suitable cable vendor, estimating the budget cost, and so on. This is a fddi network standard it 30 60 90 days plan for fibre distributed data interface ppt inspiration diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan for fibre distributed data interface. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps Elements PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps elements pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail review and risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
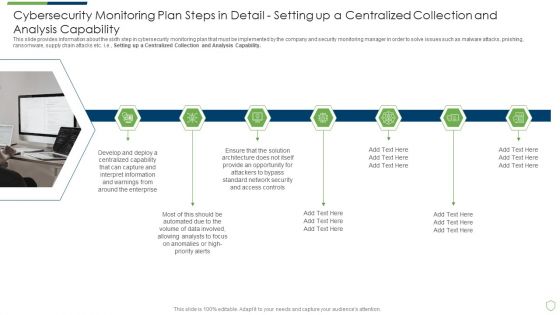
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Setting Brochure PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail setting brochure pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
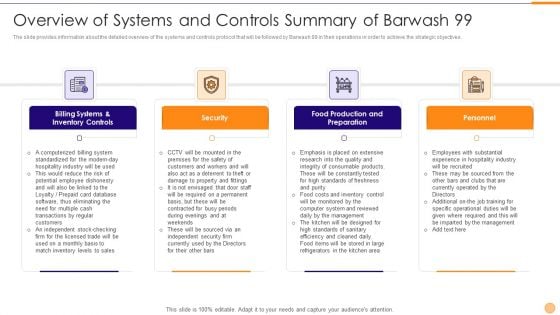
Classified Data Memo Record With Strategic Goals Overview Of Systems And Controls Summary Of Barwash 99 Rules PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. Presenting classified data memo record with strategic goals overview of systems and controls summary of barwash 99 rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like billing systems and inventory controls, security, food production and preparation, personnel. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Center Migration For Information Technology Systems Assessment And To Create Resilient Network Ppt PowerPoint Presentation Complete Deck
Executing a project plan for a business need Here is a top-notch solution for you to carry out the required tasks with complete precision and consistency. Deploy this easy-to-use Data Center Migration For Information Technology Systems Assessment And To Create Resilient Network Ppt PowerPoint Presentation Complete Deck to list the number of activities to be executed, key deliverables, and project phases to bring clarity for your team members. Grab this well-crafted fourty four slide complete deck to deliver a quality project within your deadline. The presentation template is also equipped to do this with its 100 precent editable and customizable capability. Download now.
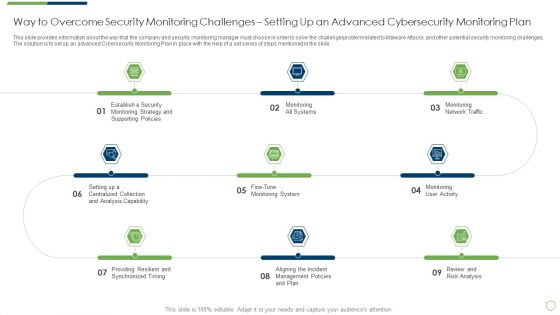
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This modern security observation plan to eradicate cybersecurity risk and data breach ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty six slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.
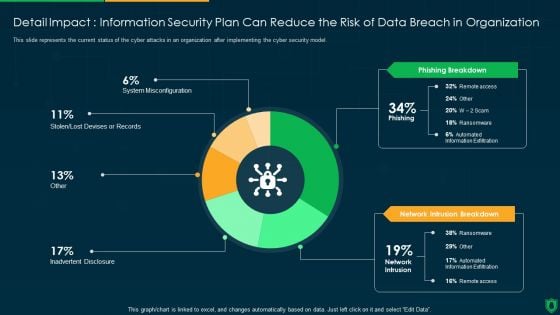
Detail Impact Information Security Plan Can Reduce The Risk Of Data Breach Ppt PowerPoint Presentation File Visual Aids PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an awe inspiring pitch with this creative detail impact information security plan can reduce the risk of data breach ppt powerpoint presentation file visual aids pdf bundle. Topics like phishing breakdown, network intrusion breakdown, inadvertent desclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Malicious Icons PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with malicious icons pdf bundle. Topics like security monitoring dashboard with malicious requests and average latency rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Challenges Slides PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring challenges slides pdf bundle. Topics like current security monitoring challenges the company is facing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Best Data Security Software 30 60 90 Days Plan For Company Online Database Security Proposal Sample PDF
Presenting this set of slides with name best data security software 30 60 90 days plan for company online database security proposal sample pdf. This is a three stage process. The stages in this process are 30 60 90 days plan, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
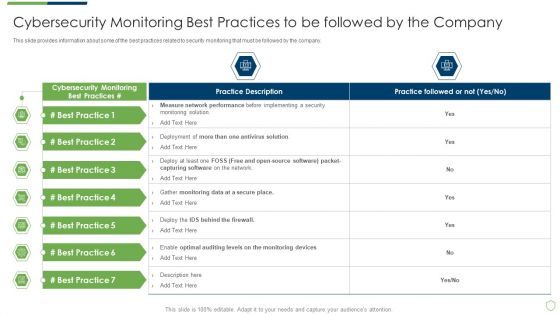
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Best Practices Introduction PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring best practices introduction pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
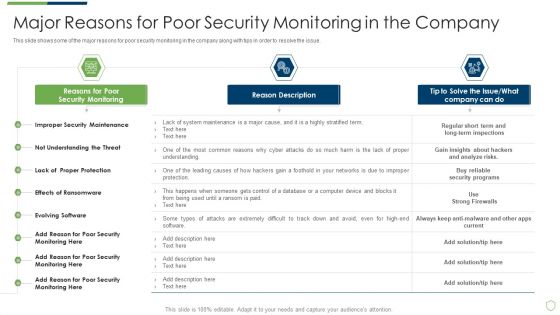
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Major Reasons For Poor Security Elements PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach major reasons for poor security elements pdf bundle. Topics like major reasons for poor security monitoring in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
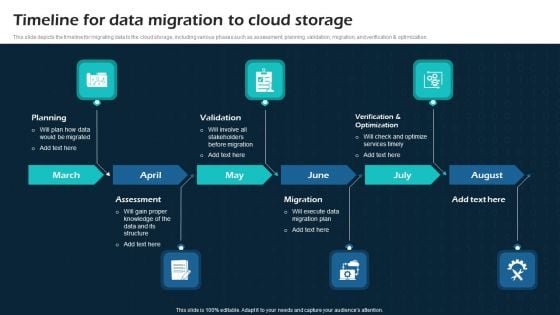
Timeline For Data Migration To Cloud Storage Virtual Cloud Network IT Ppt Visual Aids Example 2015 PDF
This slide depicts the timeline for migrating data to the cloud storage, including various phases such as assessment, planning, validation, migration, and verification and optimization. Presenting this PowerPoint presentation, titled Timeline For Data Migration To Cloud Storage Virtual Cloud Network IT Ppt Visual Aids Example 2015 PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Timeline For Data Migration To Cloud Storage Virtual Cloud Network IT Ppt Visual Aids Example 2015 PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Timeline For Data Migration To Cloud Storage Virtual Cloud Network IT Ppt Visual Aids Example 2015 PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
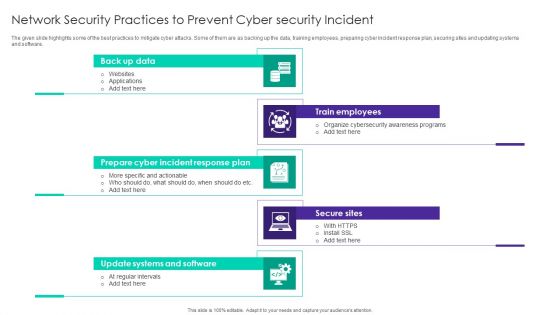
Network Security Practices To Prevent Cyber Security Incident Ppt Visual Aids Infographic Template PDF
The given slide highlights some of the best practices to mitigate cyber attacks. Some of them are as backing up the data, training employees, preparing cyber incident response plan, securing sites and updating systems and software. Persuade your audience using this Network Security Practices To Prevent Cyber Security Incident Ppt Visual Aids Infographic Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Back Up Data, Train Employees, Secure Sites, Prepare Cyber Incident. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Best Data Security Software Statement Of Work And Contract For Company Online Database Security Proposal Themes PDF
Presenting this set of slides with name best data security software statement of work and contract for company online database security proposal themes pdf. This is a six stage process. The stages in this process are services rendered, mutual cooperation, terms of payment, plans cancellation, confidentiality, terms and termination. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Reverse Proxy Server IT Secure Client Connection To Proxy Server Ppt Icon Graphics Template PDF
This slide represents the secure client connection to the proxy server and is effective for a little or no risk for data transmission between networks. This is a reverse proxy server it secure client connection to proxy server ppt icon graphics template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like server, proxy, cache. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Way To Overcome Security Monitoring Challenges Setting Up An Advanced Cybersecurity Template PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge or problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a way to overcome security monitoring challenges setting up an advanced cybersecurity template pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like establish security, monitoring strategy, supporting policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
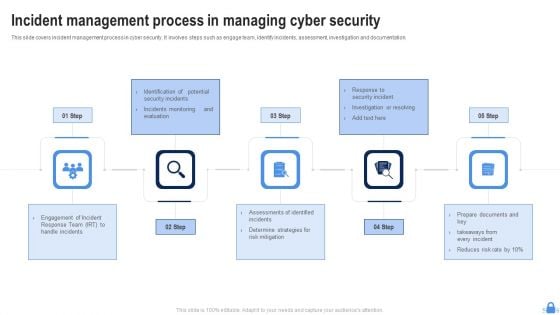
Incident Management Process In Managing Cyber Security Ppt Portfolio Template PDF
This slide covers incident management process in cyber security. It involves steps such as engage team, identify incidents, assessment, investigation and documentation. Presenting Incident Management Process In Managing Cyber Security Ppt Portfolio Template PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Determine Strategies, Risk Mitigation, Engagement Incident. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. This is a Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Major Components, Criticality Rating, Failure Cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
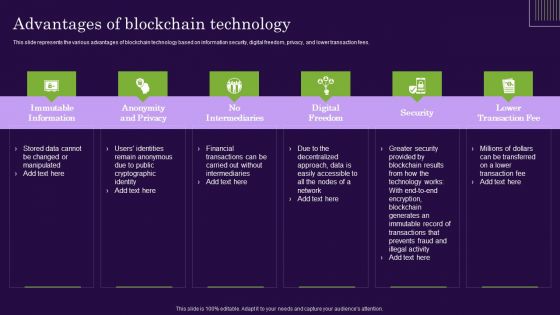
DLT Technology Advantages Of Blockchain Technology Ppt Infographic Template Example File
This slide represents the various advantages of blockchain technology based on information security, digital freedom, privacy, and lower transaction fees. Boost your pitch with our creative DLT Technology Advantages Of Blockchain Technology Ppt Infographic Template Example File. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.
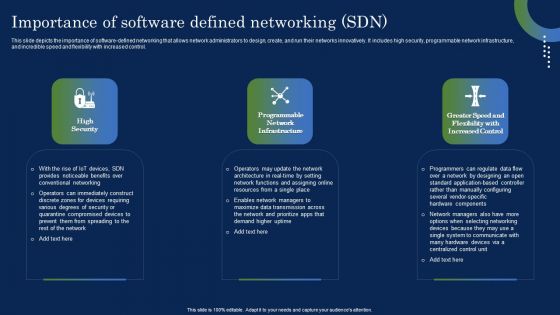
Deploying SDN System Importance Of Software Defined Networking SDN Template PDF
This slide depicts the importance of software-defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control. Find highly impressive Deploying SDN System Importance Of Software Defined Networking SDN Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Deploying SDN System Importance Of Software Defined Networking SDN Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
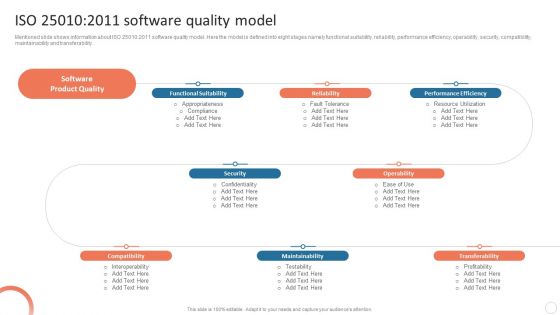
Quality Control Plan Iso 25010 2011 Software Quality Model Template PDF
Mentioned slide shows information about ISO 25010 2011 software quality model. Here the model is defined into eight stages namely functional suitability, reliability, performance efficiency, operability, security, compatibility, maintainability and transferability. Find highly impressive Quality Control Plan Iso 25010 2011 Software Quality Model Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Quality Control Plan Iso 25010 2011 Software Quality Model Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Key Steps For Successful Event Operations Management Ppt PowerPoint Presentation Infographic Template Slides PDF
Persuade your audience using this key steps for successful event operations management ppt powerpoint presentation infographic template slides pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including find and secure your venue, plan for entry and exit flow, use technology to streamline event logistics, create contingency plans, be generous with refunds. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
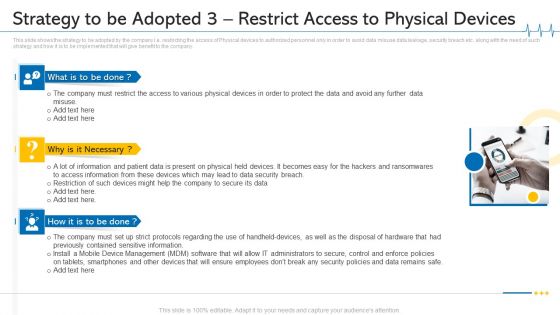
Minimize Cloud Risks Medical Care Business Case Competition Strategy To Be Adopted 3 Restrict Access To Physical Devices Ideas PDF
This slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. This is a minimize cloud risks medical care business case competition strategy to be adopted 3 restrict access to physical devices ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like mobile device management, data security breach, physical devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Areas Of Operation In Chief Information Officer Transition Plan Template PDF
This slide presents key areas of operation for chief information officer during transition plan, helpful in providing insights on assessment of workforce and strategies by CIO. It includes operating costs, delivery process, talent, architecture, security and compliance. Presenting Key Areas Of Operation In Chief Information Officer Transition Plan Template PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Operating Costs Delivery Process, Talent Architecture, Security Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
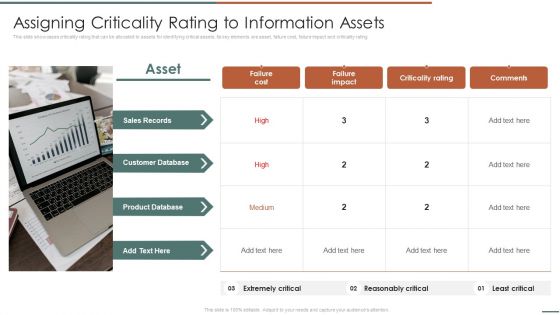
Information Security Risk Evaluation Assigning Criticality Rating To Information Assets Template PDF
This slide showcases criticality rating that can be allocated to assets for identifying critical assets. Its key elements are asset, failure cost, failure impact and criticality rating.Presenting Information Security Risk Evaluation Assigning Criticality Rating To Information Assets Template PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Customer Database, Product Database, Sales Records. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Technology Risks With Security Incident Management Ppt PowerPoint Presentation Gallery Graphics Template PDF
Presenting cloud technology risks with security incident management ppt powerpoint presentation gallery graphics template pdf. to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identification and allowance, management interface vulnerability, security incident management, application security management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Functioning Centre Timeframe For Incident Management Ppt Slides Template PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. This is a security functioning centre timeframe for incident management ppt slides template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeframe for incident management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Business Intranet For Secure Communication Vector Icon Ppt PowerPoint Presentation Infographic Template Design Ideas PDF
Presenting business intranet for secure communication vector icon ppt powerpoint presentation infographic template design ideas pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including business intranet for secure communication vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
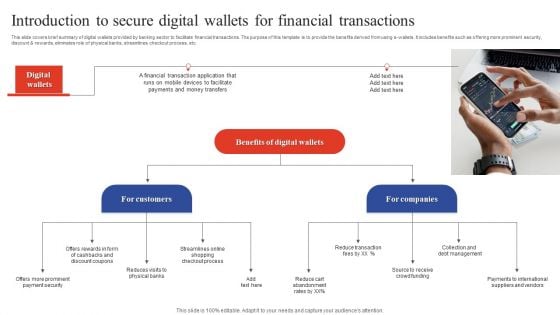
Deployment Of Omnichannel Banking Solutions Introduction To Secure Digital Wallets For Financial Transactions Template PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e-wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Retrieve professionally designed Deployment Of Omnichannel Banking Solutions Introduction To Secure Digital Wallets For Financial Transactions Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Software Professional Working On Website Global Security Icon Ppt PowerPoint Presentation Infographic Template Images PDF
Persuade your audience using this software professional working on website global security icon ppt powerpoint presentation infographic template images pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including software professional working on website global security icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mobile Device Management Assistance Business Mobile Device Security Management And Mitigation Template PDF
This slide provides information regarding mobile device management technology assistance to employees and to IT department associated to firm. Present like a pro with Mobile Device Management Assistance Business Mobile Device Security Management And Mitigation Template PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Small Business Venture Company Profile Company Introduction And Its Core Values Template PDF
This slide focuses on detailed company introduction which includes founded year, industry, headquarters and specialities with core values such as sustainability, honesty, integrity, ethical, innovation and authenticity.Presenting Small Business Venture Company Profile Company Introduction And Its Core Values Template PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Headquarters, Relationship Customers, Optimize Efficiency. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
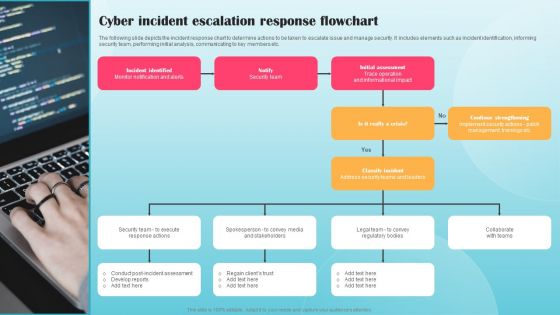
Cyber Incident Escalation Response Flowchart Ppt PowerPoint Presentation File Infographic Template PDF
The following slide depicts the incident response chart to determine actions to be taken to escalate issue and manage security. It includes elements such as incident identification, informing security team, performing initial analysis, communicating to key members etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Incident Escalation Response Flowchart Ppt PowerPoint Presentation File Infographic Template PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
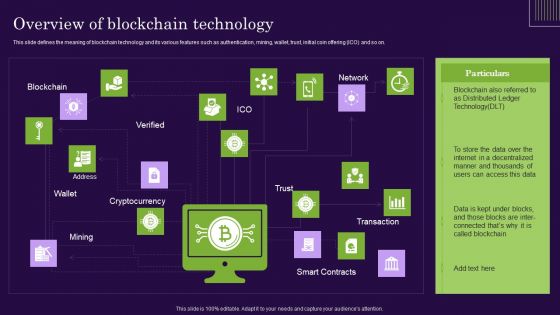
DLT Technology Overview Of Blockchain Technology Ppt Infographics Infographic Template PDF
This slide defines the meaning of blockchain technology and its various features such as authentication, mining, wallet, trust, initial coin offering ICO and so on. Take your projects to the next level with our ultimate collection of DLT Technology Overview Of Blockchain Technology Ppt Infographics Infographic Template PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors thell make your projects stand out from the rest.


 Continue with Email
Continue with Email

 Home
Home


































