Data Protection Strategy Template
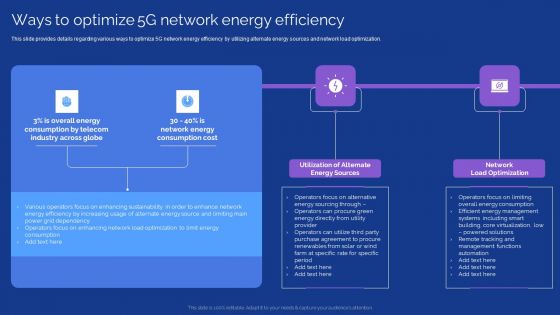
Development Guide For 5G World Ways To Optimize 5G Network Energy Efficiency Portrait PDF
This slide provides details regarding various ways to optimize 5G network energy efficiency by utilizing alternate energy sources and network load optimization. Are you searching for a Development Guide For 5G World Ways To Optimize 5G Network Energy Efficiency Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Development Guide For 5G World Ways To Optimize 5G Network Energy Efficiency Portrait PDF from Slidegeeks today.

Optimization Of IoT Remote Monitoring Factors To Consider While Selecting IoT Monitoring Devices IoT SS V
This slide provides an overview of the consideration factors for choosing IoT devices. Major factors covered are security and compliance, user-friendly interface, maintenance service, budget and deployment. Are you searching for a Optimization Of IoT Remote Monitoring Factors To Consider While Selecting IoT Monitoring Devices IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Optimization Of IoT Remote Monitoring Factors To Consider While Selecting IoT Monitoring Devices IoT SS V from Slidegeeks today. This slide provides an overview of the consideration factors for choosing IoT devices. Major factors covered are security and compliance, user-friendly interface, maintenance service, budget and deployment.

Insider Threat In Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Insider Threat In Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the thirty slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.
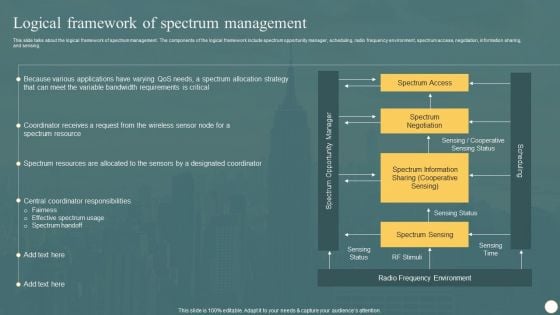
Cognitive Radio Network IT Logical Framework Of Spectrum Management Themes PDF
This slide talks about the logical framework of spectrum management. The components of the logical framework include spectrum opportunity manager, scheduling, radio frequency environment, spectrum access, negotiation, information sharing, and sensing. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cognitive Radio Network IT Logical Framework Of Spectrum Management Themes PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cognitive Radio Network IT Spectrum Database Technique For Cognitive Radio Slides PDF
This slide depicts the overview of the spectrum database technique for cognitive radio to simplify the spectrum sensing techniques and better utilize TV white space. It also comprises limitations of spectrum database technique, including significant formed proportion for a short time, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cognitive Radio Network IT Spectrum Database Technique For Cognitive Radio Slides PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
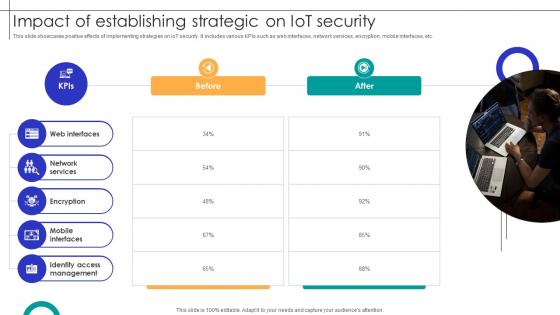
Impact Of Establishing Strategic On IOT Security Streamlining Production Ppt Presentation
This slide showcases positive effects of implementing strategies on IoT security. It includes various KPIs such as web interfaces, network services, encryption, mobile interfaces, etc. Retrieve professionally designed Impact Of Establishing Strategic On IOT Security Streamlining Production Ppt Presentation to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases positive effects of implementing strategies on IoT security. It includes various KPIs such as web interfaces, network services, encryption, mobile interfaces, etc.
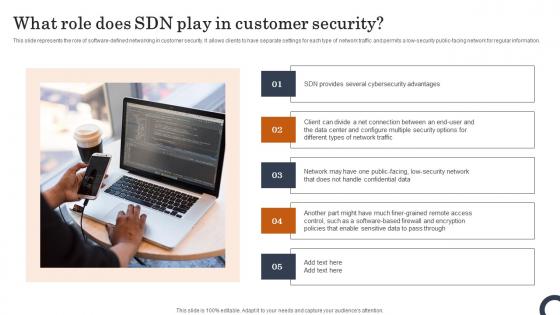
What Role Does SDN Play In Customer Security Evolution Of SDN Controllers Mockup Pdf
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. What Role Does SDN Play In Customer Security Evolution Of SDN Controllers Mockup Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information.
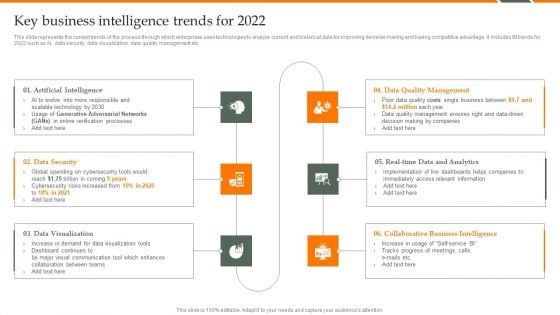
Human Resource Analytics Key Business Intelligence Trends For 2022 Elements PDF
This slide represents the current trends of the process through which enterprises uses technologies to analyze current and historical data for improving decision making and having competitive advantage. It includes BI trends for 2022 such as AI, data security, data visualization, data quality management etc. Welcome to our selection of the Human Resource Analytics Key Business Intelligence Trends For 2022 Elements PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
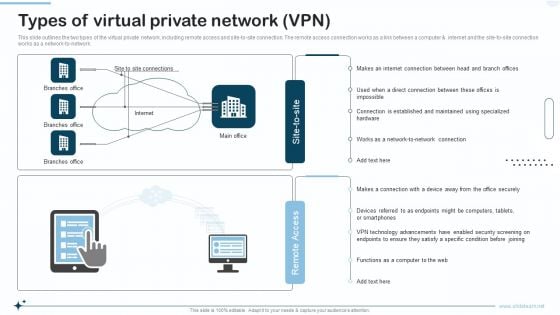
Naas Integrated Solution IT Types Of Virtual Private Network VPN Guidelines PDF
This slide outlines the two types of the virtual private network, including remote access and site-to-site connection. The remote access connection works as a link between a computer and internet and the site to site connection works as a network to network. Deliver an awe inspiring pitch with this creative Naas Integrated Solution IT Types Of Virtual Private Network VPN Guidelines PDF bundle. Topics like Technology Advancements, Virtual Private Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
5G Network Security Icon For Device Safety Sample Pdf
Pitch your topic with ease and precision using this 5G Network Security Icon For Device Safety Sample Pdf. This layout presents information on 5G Network Security, Device Safety. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our 5G Network Security Icon For Device Safety Sample Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
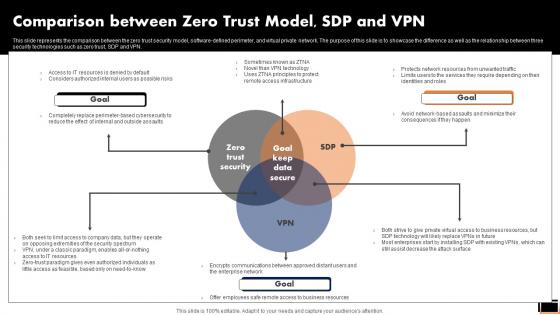
Comparison Between Zero Trust ModelSDP And Vpn Software Defined Perimeter SDP
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Present like a pro with Comparative Assessment Of Ztna Version 1 0 And 2 0 Software Defined Perimeter SDP. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
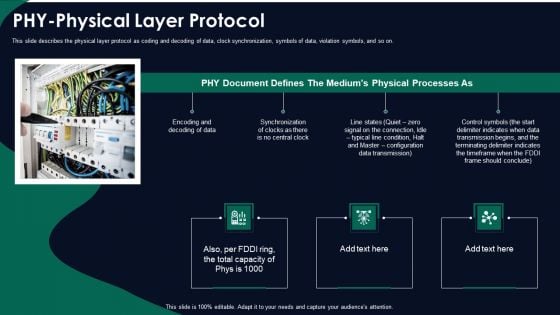
FDDI Network Standard IT Phy Physical Layer Protocol Ppt File Show PDF
This slide describes the physical layer protocol as coding and decoding of data, clock synchronization, symbols of data, violation symbols, and so on. Deliver an awe inspiring pitch with this creative fddi network standard it phy physical layer protocol ppt file show pdf bundle. Topics like phy physical layer protocol can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Characteristics Of Strong Devsecops Program In It Role Of Devsecops Ppt Slide
This slide discusses the features adopted for a strong DevSecOps program. The purpose of this slide is to explain the various characteristics these are security awareness and ownership, automated operations, wide scope, shift-left and shift-right, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Characteristics Of Strong Devsecops Program In It Role Of Devsecops Ppt Slide a try. Our experts have put a lot of knowledge and effort into creating this impeccable Characteristics Of Strong Devsecops Program In It Role Of Devsecops Ppt Slide You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide discusses the features adopted for a strong DevSecOps program. The purpose of this slide is to explain the various characteristics these are security awareness and ownership, automated operations, wide scope, shift-left and shift-right, etc.

Installation Cost Of Smart Home Systems Utilizing Smart Appliances IoT SS V
This slide provides an overview of the various systems installed in smart homes. Major smart systems covered are smart lighting systems, thermostats, smart locks, smart doorbells, security systems, motion sensors, smoke detection sensors, water sensors, alarm systems, security cameras, smart speakers, smart displays, smart plugs, robot vacuums, HVAC system, medical alert system. Are you searching for a Installation Cost Of Smart Home Systems Utilizing Smart Appliances IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Installation Cost Of Smart Home Systems Utilizing Smart Appliances IoT SS V from Slidegeeks today. This slide provides an overview of the various systems installed in smart homes. Major smart systems covered are smart lighting systems, thermostats, smart locks, smart doorbells, security systems, motion sensors, smoke detection sensors, water sensors, alarm systems, security cameras, smart speakers, smart displays, smart plugs, robot vacuums, HVAC system, medical alert system.
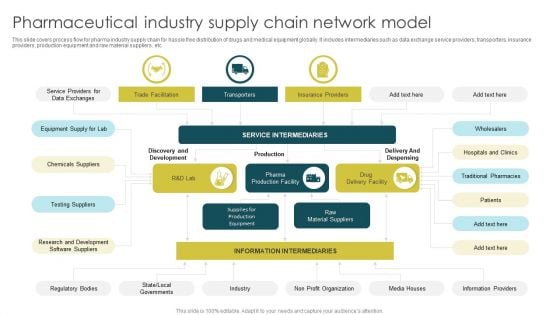
Pharmaceutical Industry Supply Chain Network Model Download PDF
This slide covers process flow for pharma industry supply chain for hassle free distribution of drugs and medical equipment globally. It includes intermediaries such as data exchange service providers, transporters, insurance providers, production equipment and raw material suppliers , etc. Pitch your topic with ease and precision using this Pharmaceutical Industry Supply Chain Network Model Download PDF. This layout presents information on Testing Suppliers, Chemicals Suppliers, Equipment Supply. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Integrating AI With IoT Real Life Example Of AIoT London City Airport IoT SS V
The purpose of this slide is to showcase real-life example of Artificial Intelligence of Things AIoT. The slide provides information about how London city airport improves its operational efficiency by enhancing security, passenger experience, and baggage handling. Get a simple yet stunning designed Integrating AI With IoT Real Life Example Of AIoT London City Airport IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Integrating AI With IoT Real Life Example Of AIoT London City Airport IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The purpose of this slide is to showcase real-life example of Artificial Intelligence of Things AIoT. The slide provides information about how London city airport improves its operational efficiency by enhancing security, passenger experience, and baggage handling.

Growth Driving Factors Of IoT Adoption In Banking Sector IoT In Banking For Digital Future IoT SS V
Following slide represents various factors that drives market growth of IoT adoption by banking sector to improve operational efficiency. It includes pointers such as efficiency, security, real time analytics, technological advancements, etc. Get a simple yet stunning designed Growth Driving Factors Of IoT Adoption In Banking Sector IoT In Banking For Digital Future IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Growth Driving Factors Of IoT Adoption In Banking Sector IoT In Banking For Digital Future IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. Following slide represents various factors that drives market growth of IoT adoption by banking sector to improve operational efficiency. It includes pointers such as efficiency, security, real time analytics, technological advancements, etc.
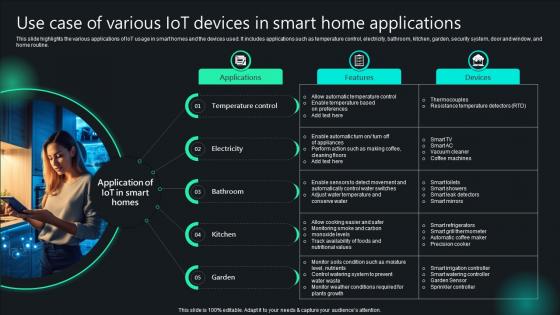
Unlocking Potential IoTs Application Use Case Of Various IoT Devices In Smart Home Applications IoT SS V
This slide highlights the various applications of IoT usage in smart homes and the devices used. It includes applications such as temperature control, electricity, bathroom, kitchen, garden, security system, door and window, and home routine. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Unlocking Potential IoTs Application Use Case Of Various IoT Devices In Smart Home Applications IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide highlights the various applications of IoT usage in smart homes and the devices used. It includes applications such as temperature control, electricity, bathroom, kitchen, garden, security system, door and window, and home routine.

Digitized Record Book Technology Pros And Cons Of Private Digital Ledger Download PDF
This slide represents the Pros and cons of the private blockchain framework based on factors such as speed, flexibility, trust-building, and security. Deliver an awe inspiring pitch with this creative digitized record book technology pros and cons of private digital ledger download pdf bundle. Topics like network, organization, data, lower security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Cyber Intelligent Computing System Infographics PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Cyber Intelligent Computing System Infographics PDF bundle. Topics like Systems Development, Systems Implementation, Security Strategy Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
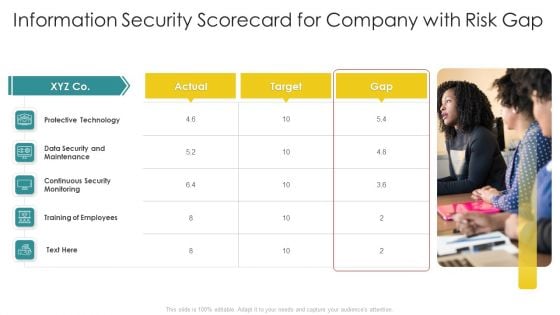
Cybersecurity Risk Scorecard Information Security Scorecard For Company With Risk Gap Professional PDF
Presenting cybersecurity risk scorecard information security scorecard for company with risk gap professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like protective technology, continuous security monitoring, training of employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
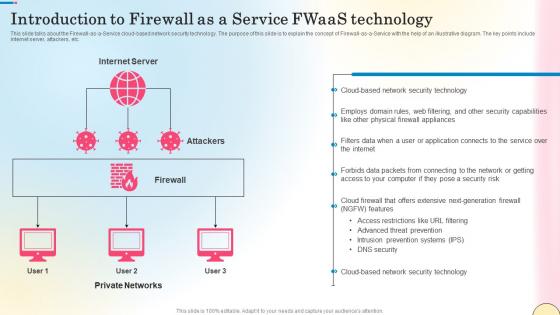
Introduction To Firewall As A Service Fwaas Technology Network Security Professional Pdf
This slide talks about the Firewall-as-a-Service cloud-based network security technology. The purpose of this slide is to explain the concept of Firewall-as-a-Service with the help of an illustrative diagram. The key points include internet server, attackers, etc. Retrieve professionally designed Introduction To Firewall As A Service Fwaas Technology Network Security Professional Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the Firewall-as-a-Service cloud-based network security technology. The purpose of this slide is to explain the concept of Firewall-as-a-Service with the help of an illustrative diagram. The key points include internet server, attackers, etc.
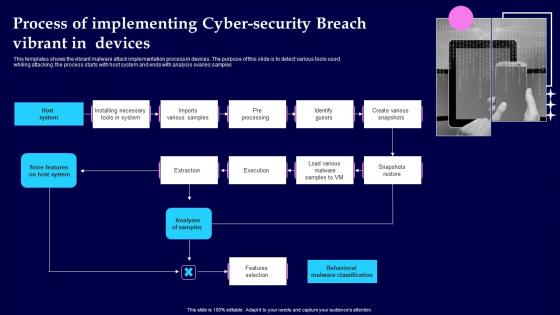
Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf
This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples Pitch your topic with ease and precision using this Process Of Implementing Cyber Security Breach Vibrant In Devices Demonstration Pdf This layout presents information on Analyses Of Samples, Features Selection, Pre Processing It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the vibrant malware attack implementation process in devices. The purpose of this slide is to detect various tools used whiling attacking .the process starts with host system and ends with analysis ovaries samples
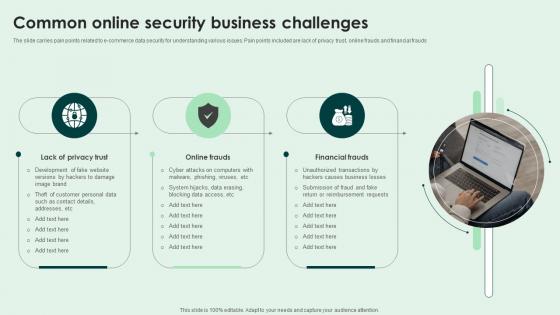
Common Online Security Business Challenges Guidelines Pdf
Showcasing this set of slides titled Common Online Security Business Challenges Guidelines Pdf. The topics addressed in these templates are Lack Of Privacy Trust, Online Frauds, Financial Frauds. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Common Online Security Business Challenges Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf
Showcasing this set of slides titled Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf The topics addressed in these templates are Ecommerce Payment Security, Distributed Ledger, Technology Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V
This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery. There are so many reasons you need a Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery.
Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf
Showcasing this set of slides titled Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf The topics addressed in these templates are Blockchain Internet, Things Security, Technology For Business All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Image For Blockchain Internet Of Things Security Technology For Business Professional Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Internet Of Things Security Technology Image For Mobile Application Download Pdf
Showcasing this set of slides titled Internet Of Things Security Technology Image For Mobile Application Download Pdf The topics addressed in these templates are Internet Of Things, Security Technology, Image For Mobile Application All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Internet Of Things Security Technology Image For Mobile Application Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
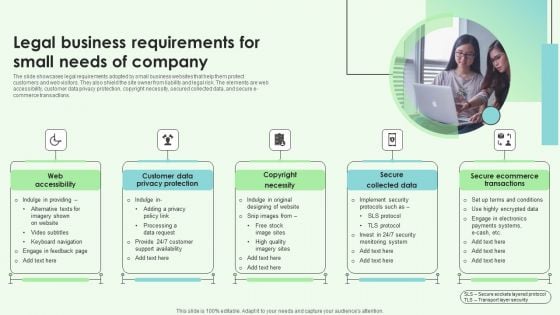
Legal Business Requirements For Small Needs Of Company Inspiration PDF
The slide showcases legal requirements adopted by small business websites that help them protect customers and web visitors. They also shield the site owner from liability and legal risk. The elements are web accessibility, customer data privacy protection, copyright necessity, secured collected data, and secure e-commerce transactions. Presenting Legal Business Requirements For Small Needs Of Company Inspiration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Copyright Necessity, Secure Collected Data, Secure Ecommerce Transactions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf
Showcasing this set of slides titled Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf The topics addressed in these templates are Cyber Security Breach, Icon Sending Malicious Emails All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Load Balancing Technique Weighted Load Balancing Vs Round Robin Information PDF
This slide represents a comparison between weighted load balancing and round robin load balancing and how weight is distributed in both approaches. Deliver an awe inspiring pitch with this creative Load Balancing Technique Weighted Load Balancing Vs Round Robin Information PDF bundle. Topics like Networks, Plan Data, Load Balancing Method can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
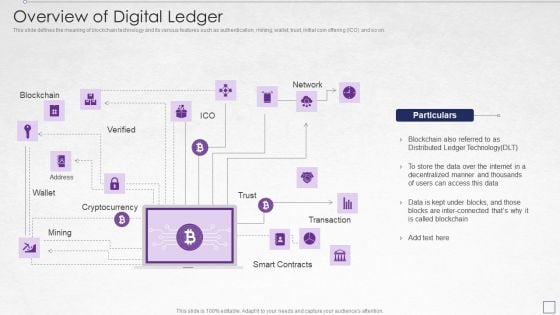
Digitized Record Book Technology Overview Of Digital Ledger Summary PDF
This slide defines the meaning of blockchain technology and its various features such as authentication, mining, wallet, trust, initial coin offering ICO and so on. Deliver an awe inspiring pitch with this creative digitized record book technology overview of digital ledger summary pdf bundle. Topics like data, internet, technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
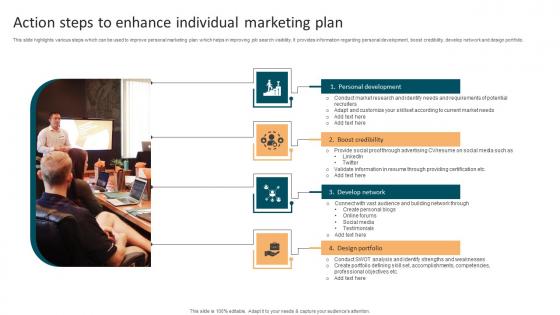
Action Steps To Enhance Individual Marketing Plan Graphics Pdf
This slide highlights various steps which can be used to improve personal marketing plan which helps in improving job search visibility. It provides information regarding personal development, boost credibility, develop network and design portfolio. Pitch your topic with ease and precision using this Action Steps To Enhance Individual Marketing Plan Graphics Pdf. This layout presents information on Personal Development, Boost Credibility, Develop Network . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights various steps which can be used to improve personal marketing plan which helps in improving job search visibility. It provides information regarding personal development, boost credibility, develop network and design portfolio.

Devsecops Pipeline Development Pre Commit Stage Role Of Devsecops Ppt Slide
This slide discusses the development pre-commit stage of the DevSecOps pipeline. The purpose of this slide is to explain the pre-commit phase that includes initial defense on developer laptops, early security implementation, and Git pre-commit hooks for feedback. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Devsecops Pipeline Development Pre Commit Stage Role Of Devsecops Ppt Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Devsecops Pipeline Development Pre Commit Stage Role Of Devsecops Ppt Slide This slide discusses the development pre-commit stage of the DevSecOps pipeline. The purpose of this slide is to explain the pre-commit phase that includes initial defense on developer laptops, early security implementation, and Git pre-commit hooks for feedback.

Security And Surveillance Company Profile Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fouty two slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.
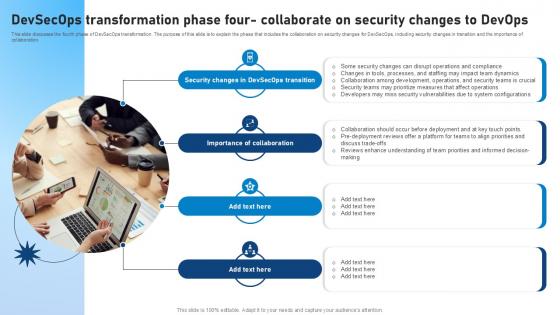
Devsecops Transformation Phase Four Collaborate On Security Role Of Devsecops Ppt Slide
This slide discusses the fourth phase of DevSecOps transformation. The purpose of this slide is to explain the phase that includes the collaboration on security changes for DevSecOps, including security changes in transition and the importance of collaboration. This Devsecops Transformation Phase Four Collaborate On Security Role Of Devsecops Ppt Slide is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Devsecops Transformation Phase Four Collaborate On Security Role Of Devsecops Ppt Slide features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the fourth phase of DevSecOps transformation. The purpose of this slide is to explain the phase that includes the collaboration on security changes for DevSecOps, including security changes in transition and the importance of collaboration.
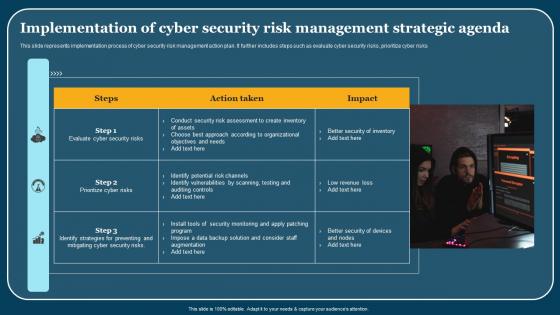
Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf
This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks. Pitch your topic with ease and precision using this Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf. This layout presents information on Steps, Action Taken, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks.
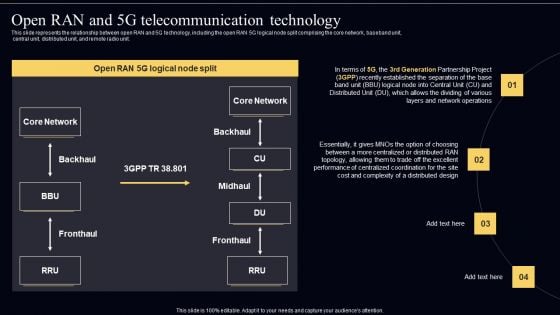
Open Radio Access Network IT Open RAN And 5G Telecommunication Technology Ideas PDF
This slide represents the relationship between open RAN and 5G technology, including the open RAN 5G logical node split comprising the core network, baseband unit, central unit, distributed unit, and remote radio unit. There are so many reasons you need a Open Radio Access Network IT Open RAN And 5G Telecommunication Technology Ideas PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
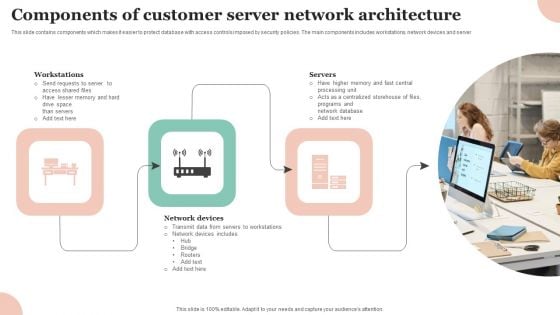
Components Of Customer Server Network Architecture Professional PDF
This slide contains components which makes it easier to protect database with access controls imposed by security policies. The main components includes workstations, network devices and server Persuade your audience using this Components Of Customer Server Network Architecture Professional PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Workstations, Network Devices, Servers . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icon Showcasing Online Security From Cyber Crime Clipart PDF
Showcasing this set of slides titled Icon Showcasing Online Security From Cyber Crime Clipart PDF. The topics addressed in these templates are Icon Showcasing Online, Security From Cyber Crime. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Sample Of Product Launch Plan Checklist Diagram Ppt Slides
This is a sample of product launch plan checklist diagram ppt slides. This is a two stage process. The stages in this process are launch planning key steps and tools, step, purpose, sample tool, product positioning analysis, volume protection analysis, distribution analysis, budget analysis.

Strategic Influencer Marketing Plan To Create Exploring Investment Opportunities Ideas Pdf
The following slide depicts influencer promotion plan for security token offerings STO project to generate more leads. It includes elements such as objectives, budget, giveaways, tracking and monitoring performance, etc. Slidegeeks has constructed Strategic Influencer Marketing Plan To Create Exploring Investment Opportunities Ideas Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The following slide depicts influencer promotion plan for security token offerings STO project to generate more leads. It includes elements such as objectives, budget, giveaways, tracking and monitoring performance, etc.
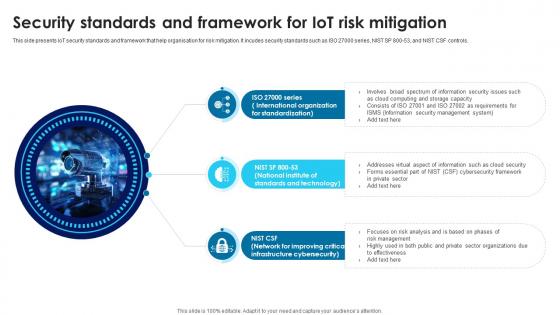
Building Trust With IoT Security Standards And Framework For IoT Risk Mitigation IoT SS V
This side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800-53, and NIST CSF controls. Present like a pro with Building Trust With IoT Security Standards And Framework For IoT Risk Mitigation IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800-53, and NIST CSF controls.
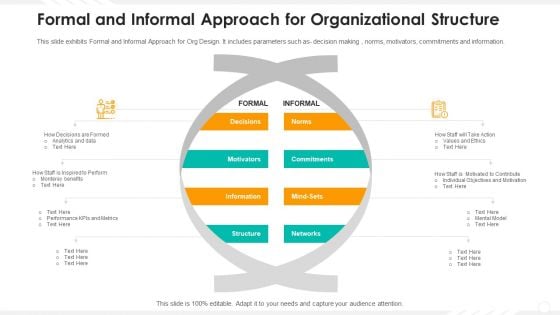
Formal And Informal Approach For Organizational Structure Microsoft PDF
Showcasing this set of slides titled formal and informal approach for organizational structure microsoft pdf. The topics addressed in these templates are information, networks, commitments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Image For Multiple Internet Of Things Security Device Technology Slides Pdf
Pitch your topic with ease and precision using this Image For Multiple Internet Of Things Security Device Technology Slides Pdf This layout presents information on Multiple Internet, Things Security, Device Technology It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Image For Multiple Internet Of Things Security Device Technology Slides Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
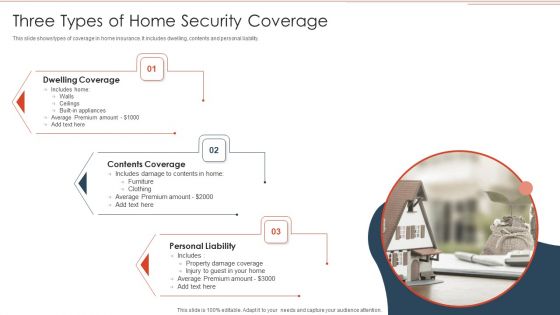
Three Types Of Home Security Coverage Demonstration PDF
This slide shows types of coverage in home insurance. It includes dwelling, contents and personal liability. Showcasing this set of slides titled Three Types Of Home Security Coverage Demonstration PDF. The topics addressed in these templates are Contents Coverage, Dwelling Coverage, Personal Liability. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
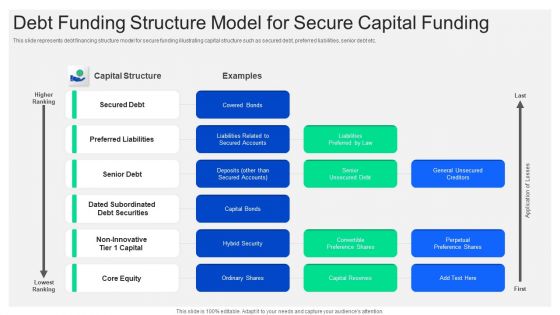
Debt Funding Structure Model For Secure Capital Funding Mockup PDF
This slide represents debt financing structure model for secure funding illustrating capital structure such as secured debt, preferred liabilities, senior debt etc. Showcasing this set of slides titled debt funding structure model for secure capital funding mockup pdf. The topics addressed in these templates are secured debt, capital structure, senior debt. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
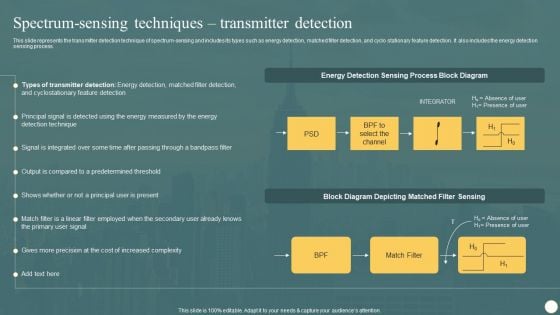
Cognitive Radio Network IT Spectrum Sensing Techniques Transmitter Detection Formats PDF
This slide represents the transmitter detection technique of spectrum sensing and includes its types such as energy detection, matched filter detection, and cyclo stationary feature detection. It also includes the energy detection sensing process. Explore a selection of the finest Cognitive Radio Network IT Spectrum Sensing Techniques Transmitter Detection Formats PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cognitive Radio Network IT Spectrum Sensing Techniques Transmitter Detection Formats PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
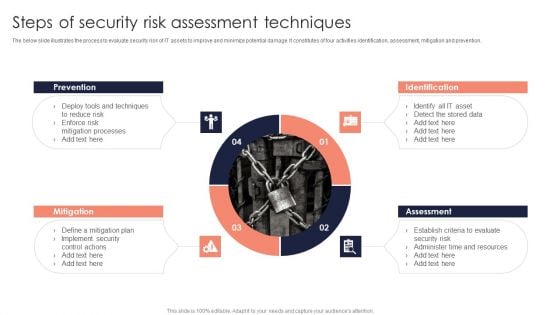
Steps Of Security Risk Assessment Techniques Introduction PDF
The below slide illustrates the process to evaluate security risk of IT assets to improve and minimize potential damage. It constitutes of four activities identification, assessment, mitigation and prevention. Showcasing this set of slides titled Steps Of Security Risk Assessment Techniques Introduction PDF. The topics addressed in these templates are Prevention, Identification, Assessment, Mitigation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
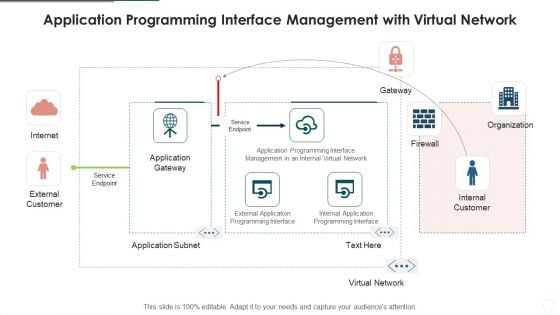
Application Programming Interface Management With Virtual Network Microsoft PDF
Showcasing this set of slides titled application programming interface management with virtual network microsoft pdf. The topics addressed in these templates are application gateway, service endpoint, external customer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
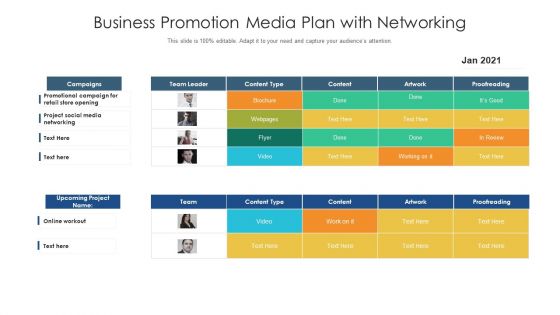
Business Promotion Media Plan With Networking Ppt PowerPoint Presentation Outline Rules PDF
Showcasing this set of slides titled business promotion media plan with networking ppt powerpoint presentation outline rules pdf. The topics addressed in these templates are Business Promotion Media Plan With Networking. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
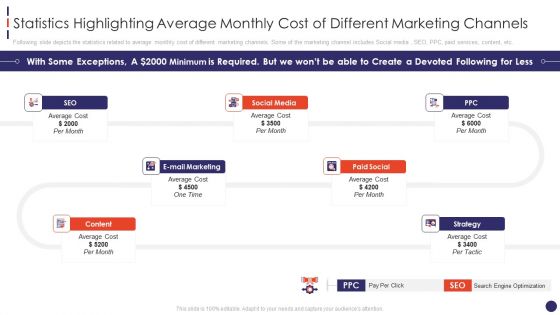
Social Network Firm Pitch Deck Statistics Highlighting Average Monthly Cost Of Demonstration PDF
Following slide depicts the statistics related to average monthly cost of different marketing channels. Some of the marketing channel includes Social media , SEO, PPC, paid services, content, etc.Deliver an awe inspiring pitch with this creative social network firm pitch deck statistics highlighting average monthly cost of demonstration pdf bundle. Topics like statistics highlighting average monthly cost of different marketing channels can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Building Trust With IoT Security Case Study 1 Enhancing Operational Technology By Integrating IoT SS V
This slide includes a case study of the company providing operational digital safety solutions integrating Cisco technology to enhance visibility at scale. It includes elements such as objectives of company , solutions implemented, and results. Slidegeeks is here to make your presentations a breeze with Building Trust With IoT Security Case Study 1 Enhancing Operational Technology By Integrating IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide includes a case study of the company providing operational digital safety solutions integrating Cisco technology to enhance visibility at scale. It includes elements such as objectives of company , solutions implemented, and results.
Internet Of Things Security Icon For Home Safety Background Pdf
Pitch your topic with ease and precision using this Internet Of Things Security Icon For Home Safety Background Pdf This layout presents information on Internet Of Things Security, Icon For Home Safety It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Internet Of Things Security Icon For Home Safety Background Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf
Pitch your topic with ease and precision using this Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf This layout presents information on Cyber Security Breach, Icon Corrupting Devices Files It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Performance Analysis Of Current Automated Regression Testing And Achieving PPT Slide
The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions. Find highly impressive Performance Analysis Of Current Automated Regression Testing And Achieving PPT Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Performance Analysis Of Current Automated Regression Testing And Achieving PPT Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions.

Objectives Of IBM Watson IoT Platform Exploring Google Cloud IoT Platform
This slide showcases the goals of IBM watson IoT platform. The purpose of this slide is to outline the objectives of IBM watson IoT platform which include device actions, bulk device management, secure communication, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Objectives Of IBM Watson IoT Platform Exploring Google Cloud IoT Platform for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases the goals of IBM watson IoT platform. The purpose of this slide is to outline the objectives of IBM watson IoT platform which include device actions, bulk device management, secure communication, etc.
Cyber Security Device Icon To Prevent Form Malicious Breach Structure Pdf
Pitch your topic with ease and precision using this Cyber Security Device Icon To Prevent Form Malicious Breach Structure Pdf This layout presents information on Cyber Security Device, Icon To Prevent Form Malicious Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Device Icon To Prevent Form Malicious Breach Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Content For Cognitive Radio Network Techniques Download PDF
Retrieve professionally designed Table Of Content For Cognitive Radio Network Techniques Download PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.


 Continue with Email
Continue with Email

 Home
Home


































