Data Protection Strategy Template
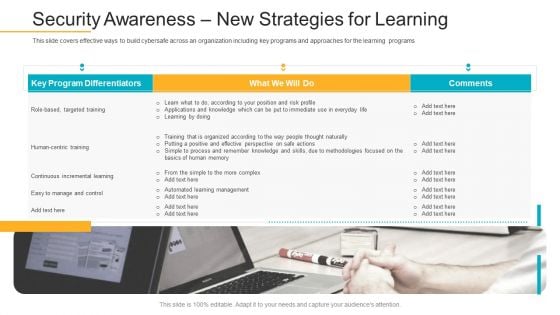
Data Breach Prevention Recognition Security Awareness New Strategies For Learning Download PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security awareness new strategies for learning download pdf bundle. Topics like cybersafe across, organization, key programs, approaches, learning programs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf
The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management.
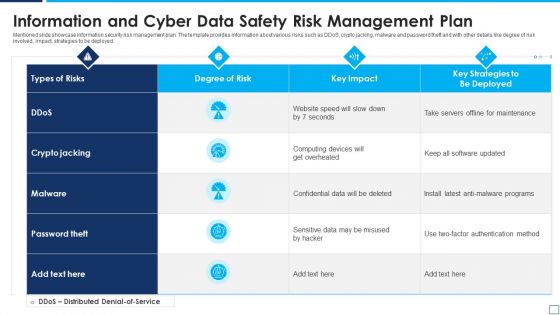
Information And Cyber Data Safety Risk Management Plan Summary PDF
Mentioned slide showcase information security risk management plan. The template provides information about various risks such as DDoS, crypto jacking, malware and password theft and with other details like degree of risk involved, impact, strategies to be deployed. Showcasing this set of slides titled information and cyber data safety risk management plan summary pdf. The topics addressed in these templates are information and cyber data safety risk management plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
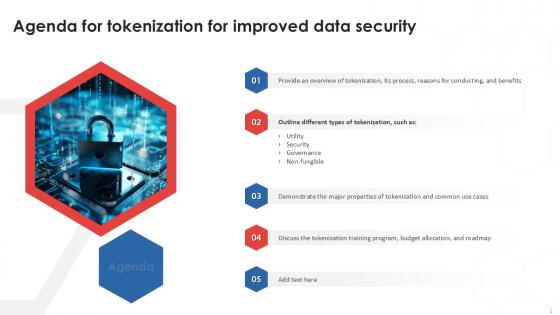
Agenda For Tokenization For Improved Data Security PPT Powerpoint
Find a pre-designed and impeccable Agenda For Tokenization For Improved Data Security PPT Powerpoint. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda For Tokenization For Improved Data Security PPT Powerpoint are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Information Technology Security Prepare Data Backup Ppt Layouts Slides PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a information technology security prepare data backup ppt layouts slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect, information, manipulation, deletion, prevent . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Effective Data Migration Types Of Cloud Migration Testing Methods
This slide showcases various cloud migration testing models used to analyze application performance such as system, security, recovery testing. Get a simple yet stunning designed Effective Data Migration Types Of Cloud Migration Testing Methods. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Effective Data Migration Types Of Cloud Migration Testing Methods can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases various cloud migration testing models used to analyze application performance such as system, security, recovery testing.

Big Data Techniques For Manufacturing Quality Management Introduction Pdf
The purpose of this slide is to showcase big data strategies that can be implemented in order improve quality control. It includes various tactics such as connecting performance metrics across multiple plants, using predictive modelling of manufacturing data, understanding supplier network performance and implementing real-time notices based on manufacturing data.Showcasing this set of slides titled Big Data Techniques For Manufacturing Quality Management Introduction Pdf The topics addressed in these templates are Connect Performance Metrics, Manufacturing Data, Network Performance All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The purpose of this slide is to showcase big data strategies that can be implemented in order improve quality control. It includes various tactics such as connecting performance metrics across multiple plants, using predictive modelling of manufacturing data, understanding supplier network performance and implementing real time notices based on manufacturing data.
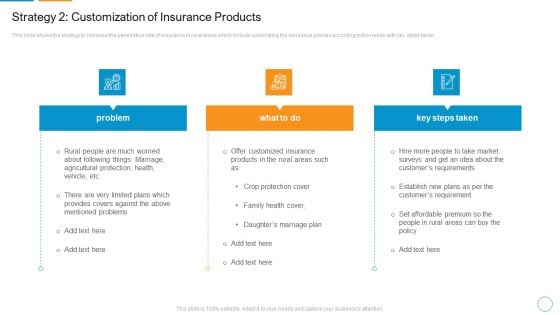
Strategy 2 Customization Of Insurance Products Infographics PDF
This slide shows the strategy to increase the penetration rate of insurance in rural areas which include customizing the insurance policies according to the needs with key steps taken.Presenting strategy 2 customization of insurance products infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like crop protection cover, family health cover, daughters marriage plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
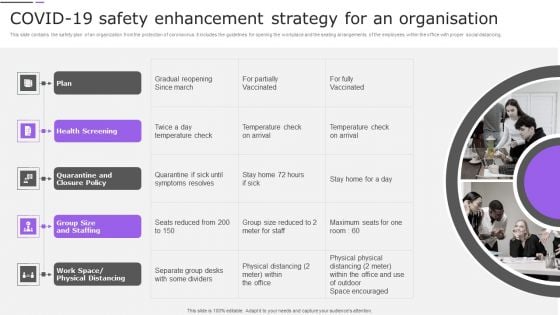
COVID19 Safety Enhancement Strategy For An Organisation Introduction PDF
This slide contains the safety plan of an organization from the protection of coronavirus. It includes the guidelines for opening the workplace and the seating arrangements of the employees within the office with proper social distancing.Presenting COVID19 Safety Enhancement Strategy For An Organisation Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Health Screening, Temperature Check, Physical Distancing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Overview Of Platform Tokenization In Data Security PPT Sample
This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc. Find a pre-designed and impeccable Overview Of Platform Tokenization In Data Security PPT Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc.
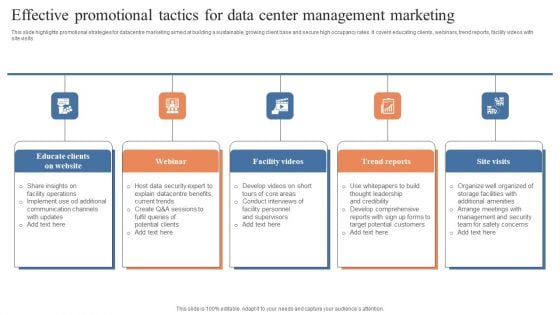
Effective Promotional Tactics For Data Center Management Marketing Rules PDF
This slide highlights promotional strategies for datacentre marketing aimed at building a sustainable, growing client base and secure high occupancy rates. It covers educating clients, webinars, trend reports, facility videos with site visits . Presenting Effective Promotional Tactics For Data Center Management Marketing Rules PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Educate Clients Website, Facility Videos, Trend Reports. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Best Practices For Tokenization In Data Security PPT Slides
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. Boost your pitch with our creative Best Practices For Tokenization In Data Security PPT Slides. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc.
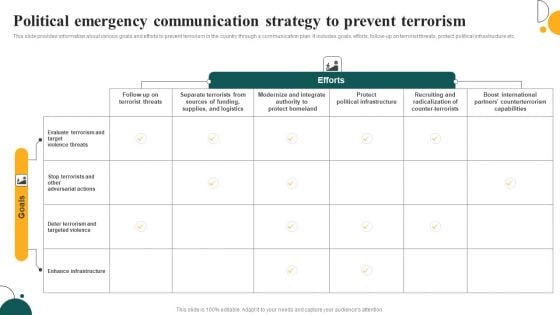
Political Emergency Communication Strategy To Prevent Terrorism Brochure PDF
This slide provides information about various goals and efforts to prevent terrorism in the country through a communication plan. It includes goals, efforts, follow-up on terrorist threats, protect political infrastructure etc. Pitch your topic with ease and precision using this Political Emergency Communication Strategy To Prevent Terrorism Brochure PDF. This layout presents information on Protect Homeland, Protect Political Infrastructure, Targeted Violence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Tokenization Working Process For Data Security PPT Powerpoint
This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Boost your pitch with our creative Tokenization Working Process For Data Security PPT Powerpoint. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc.
Cloud Data Security Using Cryptography Table Of Contents Inspiration Pdf
This modern and well arranged Cloud Data Security Using Cryptography Table Of Contents Inspiration Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Our Cloud Data Security Using Cryptography Table Of Contents Inspiration Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Safely Securing Business Machine Readable Data Ppt Ideas Diagrams PDF
Presenting safely securing business machine readable data ppt ideas diagrams pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including safely securing business machine readable data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Business Data IT Security Analysis Icon With Shield Download PDF
Presenting Business Data IT Security Analysis Icon With Shield Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Business Data IT Security, Analysis Icon With Shield. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Effective Data Migration Quality Assurance Testing Checklist For Effective Cloud
Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies. Boost your pitch with our creative Effective Data Migration Quality Assurance Testing Checklist For Effective Cloud. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies.

Customer Relationship Management Implementation Steps Enable Data Security Pictures PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver and pitch your topic in the best possible manner with this Customer Relationship Management Implementation Steps Enable Data Security Pictures PDF. Use them to share invaluable insights on Factor Authentication, Phishing Malware, Accessing Organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
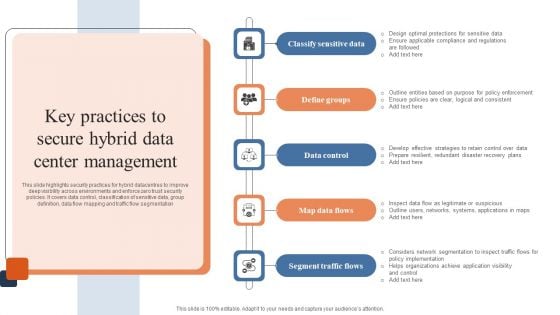
Key Practices To Secure Hybrid Data Center Management Ideas PDF
This slide highlights security practices for hybrid datacentres to improve deep visibility across environments and enforce zero trust security policies. It covers data control, classification of sensitive data, group definition, data flow mapping and traffic flow segmentation. Presenting Key Practices To Secure Hybrid Data Center Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Classify Sensitive Data, Define Groups, Data Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
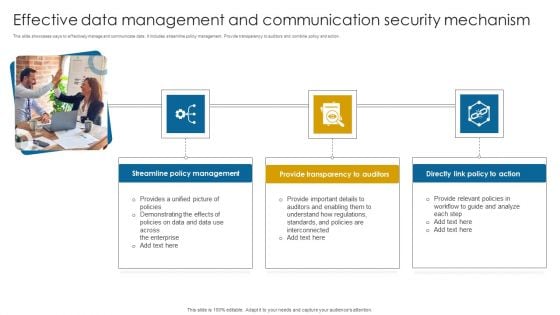
Effective Data Management And Communication Security Mechanism Themes PDF
This slide showcases ways to effectively manage and communicate data. It includes streamline policy management. Provide transparency to auditors and combine policy and action. Presenting Effective Data Management And Communication Security Mechanism Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Streamline Policy Management, Provide Transparency, Directly Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Process To Manage Firms Sensitive Data Mockup PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Boost your pitch with our creative Information Security Process To Manage Firms Sensitive Data Mockup PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
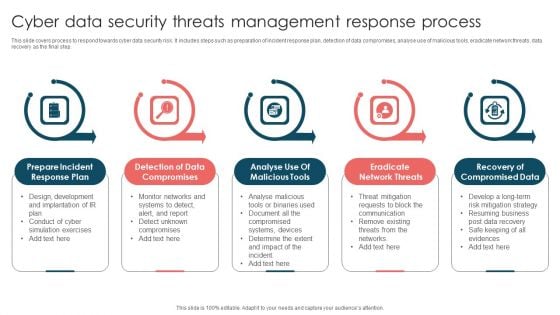
Cyber Data Security Threats Management Response Process Infographics PDF
This slide covers process to respond towards cyber data security risk. It includes steps such as preparation of incident response plan, detection of data compromises, analyse use of malicious tools, eradicate network threats, data recovery as the final step. Presenting Cyber Data Security Threats Management Response Process Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Prepare Incident, Response Plan, Detection Data Compromises, Eradicate Network Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
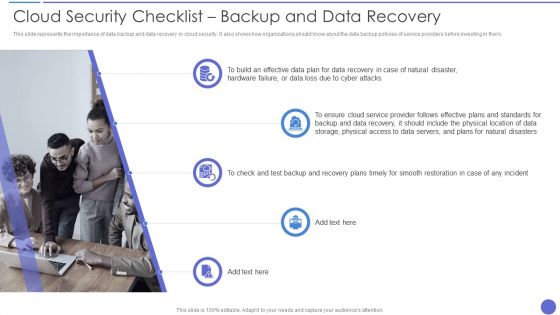
Cloud Security Checklist Backup And Data Recovery Inspiration PDF
This slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. This is a Cloud Security Checklist Backup And Data Recovery Inspiration PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Plan, Cloud Service, Location Of Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
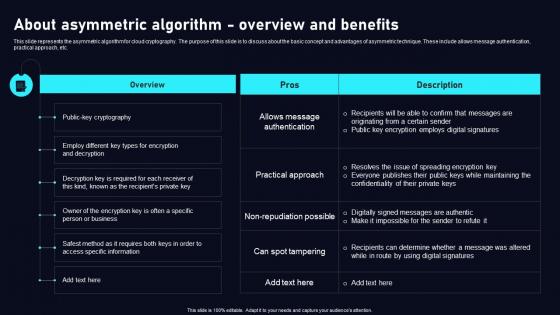
About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Get a simple yet stunning designed About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit About Asymmetric Algorithm Cloud Data Security Using Cryptography Brochure Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc.

Data Security Benefits Of Adopting Tokenization PPT Sample
This slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc. Find a pre-designed and impeccable Data Security Benefits Of Adopting Tokenization PPT Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc.
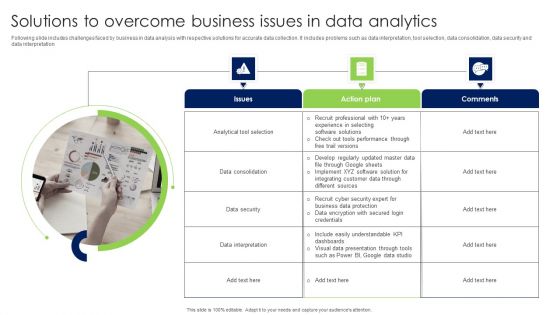
Solutions To Overcome Business Issues In Data Analytics Infographics PDF
Following slide includes challenges faced by business in data analysis with respective solutions for accurate data collection. It includes problems such as data interpretation, tool selection, data consolidation, data security and data interpretation Presenting Solutions To Overcome Business Issues In Data Analytics Infographics PDF to dispense important information. This template comprises Three stages. It also presents valuable insights into the topics including Issues, Action Plan, Comments. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Ways To Achieve And Maintain Data Accuracy Download PDF
The slide shows various methods to preserve data integrity. It includes various ways such as ensuring data quality, checking errors and managing cybersecurity threats.Presenting Ways To Achieve And Maintain Data Accuracy Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Implement Security, Data Security, Tools Techniques. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

5 Key Considerations To Initiate Data Centralization Introduction PDF
This slide showcases important points to consider while initiating for data centralization in the organization. Key five points highlighted here are data alignment, budget allocation, data security, cross-functionality and data monitoring. Presenting 5 Key Considerations To Initiate Data Centralization Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Data Monitoring, Data Security, Management System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
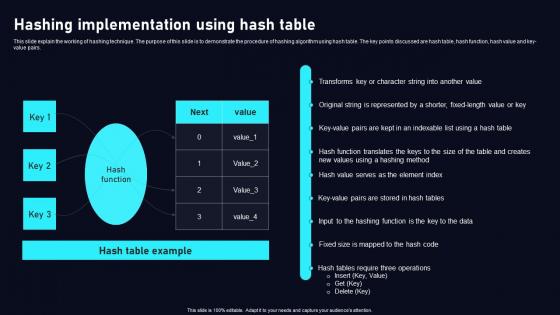
Hashing Implementation Using Cloud Data Security Using Cryptography Ideas Pdf
This slide explain the working of hashing technique. The purpose of this slide is to demonstrate the procedure of hashing algorithm using hash table. The key points discussed are hash table, hash function, hash value and key value pairs. Find a pre designed and impeccable Hashing Implementation Using Cloud Data Security Using Cryptography Ideas Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide explain the working of hashing technique. The purpose of this slide is to demonstrate the procedure of hashing algorithm using hash table. The key points discussed are hash table, hash function, hash value and key value pairs.
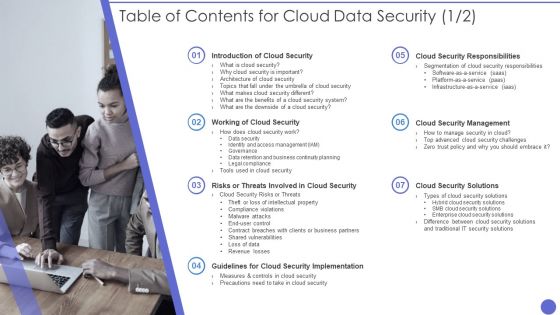
Table Of Contents For Cloud Data Security Formats PDF
Presenting Table Of Contents For Cloud Data Security Formats PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Cloud Security, Security System, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
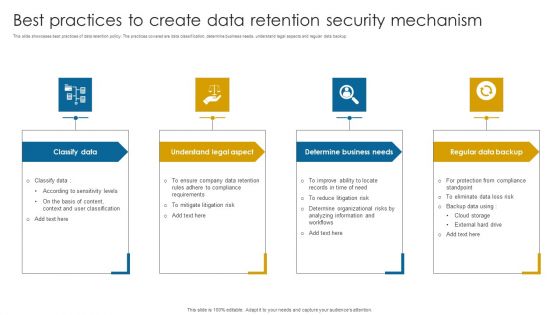
Best Practices To Create Data Retention Security Mechanism Topics PDF
This slide showcases best practices of data retention policy. The practices covered are data classification, determine business needs, understand legal aspects and regular data backup.Presenting Best Practices To Create Data Retention Security Mechanism Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Understand Legal Aspect, Determine Business Needs, Regular Data Backup . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

On Premises Data Center To Cloud Warm Recovery Background PDF
This slide describes the on premises data center to cloud warm recovery architecture and covers its elements such as application environment, building resources, and customer web requests. Deliver and pitch your topic in the best possible manner with this On Premises Data Center To Cloud Warm Recovery Background PDF. Use them to share invaluable insights on Application Environment, Build Resources, Network Endpoint and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Security Data Breach And Trend Analysis Professional PDF
The following slide reflects some trends in information technology security to assess financial loss occurred to companies due to data breach. It includes average cost and average number of days to determine and report data breach, number of new malware detected per day etc. Presenting Information Technology Security Data Breach And Trend Analysis Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Breach, Average Cost, Determine. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icons Slide For Securing Your Data With Tokenization Ppt Slide
Download our innovative and attention grabbing Icons Slide For Securing Your Data With Tokenization Ppt Slide template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide For Securing Your Data With Tokenization Ppt Slide are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cloud Security Threats Loss Of Data Guidelines PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. This is a Cloud Security Threats Loss Of Data Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategies, Service Provider, Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
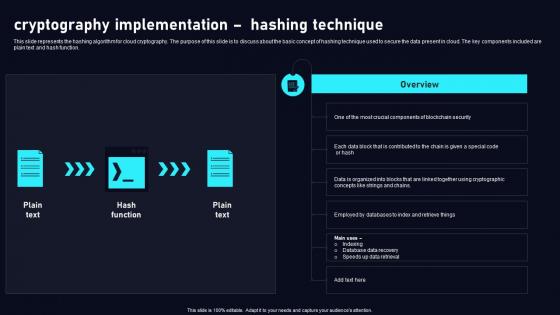
Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf
This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function. Are you searching for a Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf from Slidegeeks today. This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function.
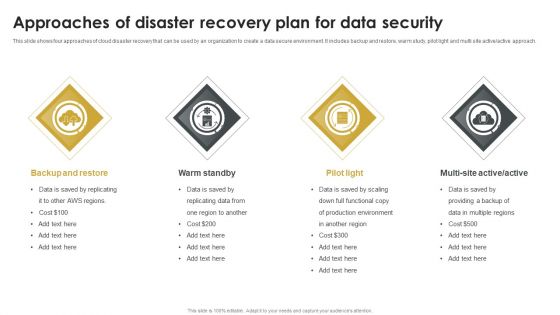
Approaches Of Disaster Recovery Plan For Data Security Topics PDF
This slide shows four approaches of cloud disaster recovery that can be used by an organization to create a data secure environment. It includes backup and restore, warm study, pilot light and multi site active or active approach. Presenting Approaches Of Disaster Recovery Plan For Data Security Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Warm Standby, Backup And Restore, Pilot Light. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Data Breach Security Communication Plan Icon Demonstration Pdf
Showcasing this set of slides titled Data Breach Security Communication Plan Icon Demonstration Pdf The topics addressed in these templates are Data Breach, Security Communication, Plan Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Data Breach Security Communication Plan Icon Demonstration Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
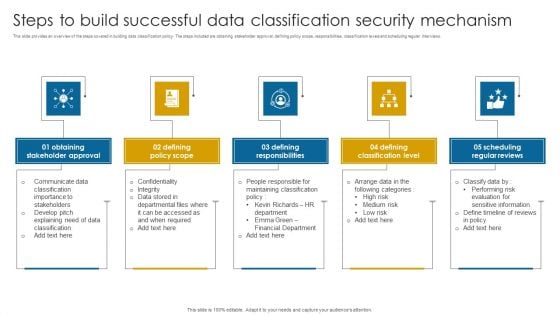
Steps To Build Successful Data Classification Security Mechanism Structure PDF
This slide provides an overview of the steps covered in building data classification policy. The steps included are obtaining stakeholder approval, defining policy scope, responsibilities, classification levels and scheduling regular interviews.Presenting Steps To Build Successful Data Classification Security Mechanism Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Stakeholder Approval, Defining Policy Scope, Defining Responsibilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cloud Computing Engineering Data Security Service Icon Portrait Pdf
Showcasing this set of slides titled Cloud Computing Engineering Data Security Service Icon Portrait Pdf The topics addressed in these templates are Cloud Computing, Engineering Data Security, Service Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cloud Computing Engineering Data Security Service Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf
Showcasing this set of slides titled Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf. The topics addressed in these templates are Encryption Techniques, IconSecuring, Big Data Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Online Business Framework Online Business Framework Data Diagrams PDF
This is a online business framework online business framework data diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data, network layer, software layer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Icons Slide For Data Security In Cloud Computing Ppt Presentation
Download our innovative and attention grabbing Icons Slide For Data Security In Cloud Computing Ppt Presentation template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide For Data Security In Cloud Computing Ppt Presentation are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Data Breach Prevention Recognition Communication Plan General Format Rules PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. This is a data breach prevention recognition communication plan general format rules pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like communication, description, frequency, audience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Agenda For Cloud Data Security Using Cryptography Structure Pdf
Find highly impressive Agenda For Cloud Data Security Using Cryptography Structure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Agenda For Cloud Data Security Using Cryptography Structure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Our Agenda For Cloud Data Security Using Cryptography Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
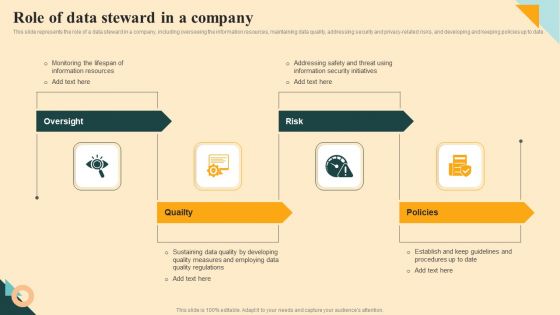
Role Of Data Steward In A Company Guidelines PDF
This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy-related risks, and developing and keeping policies up to date. The Role Of Data Steward In A Company Guidelines PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
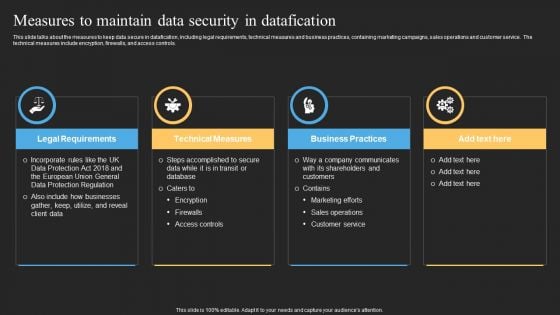
Datafy Measures To Maintain Data Security In Datafication Diagrams PDF
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Welcome to our selection of the Datafy Measures To Maintain Data Security In Datafication Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Companys Data Safety Recognition Security Awareness Training Roadmap Themes PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a companys data safety recognition security awareness training roadmap themes pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like physical security, data security, personal information, privacy threats, practices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
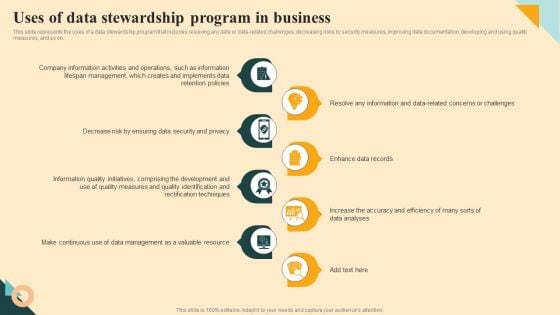
Uses Of Data Stewardship Program In Business Inspiration PDF
This slide represents the uses of a data stewardship program that includes resolving any data or data-related challenges, decreasing risks by security measures, improving data documentation, developing and using quality measures, and so on. Are you searching for a Uses Of Data Stewardship Program In Business Inspiration PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Uses Of Data Stewardship Program In Business Inspiration PDF from Slidegeeks today.
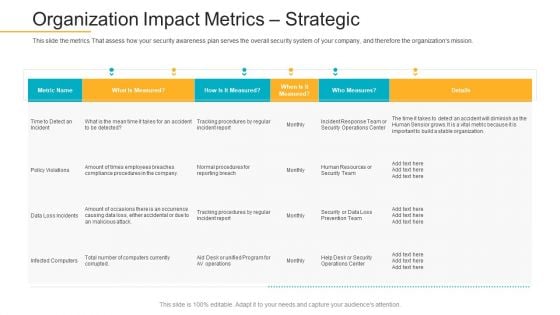
Data Breach Prevention Recognition Organization Impact Metrics Strategic Microsoft PDF
This slide the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition organization impact metrics strategic microsoft pdf. Use them to share invaluable insights on organization impact metrics strategic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Privacy IT Five Data Privacy Rules Topics PDF
This slide outlines the five data privacy rules, which are consent, purpose, disposal and destruction, access and security, accountability and disclosure. This is a information privacy it five data privacy rules topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disposal and destruction, access and security, accountability and disclosure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
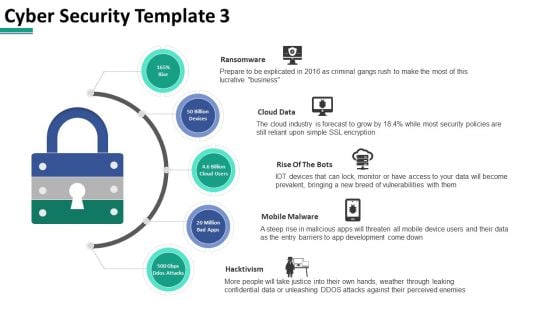
Cyber Security Cloud Data Ppt PowerPoint Presentation Summary Graphics Download
This is a cyber security cloud data ppt powerpoint presentation summary graphics download. This is a five stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
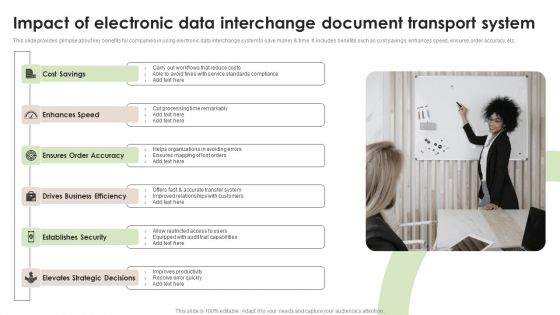
Impact Of Electronic Data Interchange Document Transport System Microsoft PDF
This slide provides glimpse about key benefits for companies in using electronic data interchange system to save money and time. It includes benefits such as cost savings, enhances speed, ensures order accuracy, etc.Presenting Impact Of Electronic Data Interchange Document Transport System Microsoft PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Enhances Speed, Drives Business, Establishes Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
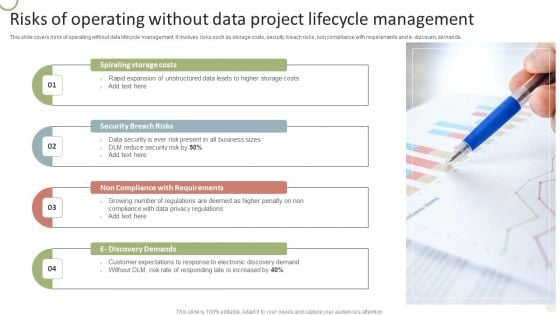
Risks Of Operating Without Data Project Lifecycle Management Ideas PDF
This slide covers risks of operating without data lifecycle management. It involves risks such as storage costs, security breach risks, non compliance with requirements and e- discovery demands.Presenting Risks Of Operating Without Data Project Lifecycle Management Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Rapid Expansion, Present Business, Discovery Demands. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Companys Data Safety Recognition Security Awareness Program Checklist Portrait PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. This is a companys data safety recognition security awareness program checklist portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementing security awareness, security awareness program, sustaining security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Concentric Data Flow Process 9 Stages Ppt Plans PowerPoint Slides
We present our concentric data flow process 9 stages ppt plans PowerPoint Slides.Download and present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject. Download our Flow Charts PowerPoint Templates because Our PowerPoint Templates and Slides offer you the widest possible range of options. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides offer you the widest possible range of options. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas.Use these PowerPoint slides for presentations relating to Flow, network, platform, diagram, connection, connect, business, flowchart, function, organization, coordinates, molecular, square, plan, interrelations, scheme, graphic, technology, graph, molecule, arrangement, comparison, scientific, variable, project, relationships, lines,attached, segments, interconnected, solution, organize, device, analyze, draft, pattern, construction, structure, nine, steps. The prominent colors used in the PowerPoint template are Gray, Blue light, White. Get your thoughts buzzing along. Our Concentric Data Flow Process 9 Stages Ppt Plans PowerPoint Slides will bring them on to the fast lane.
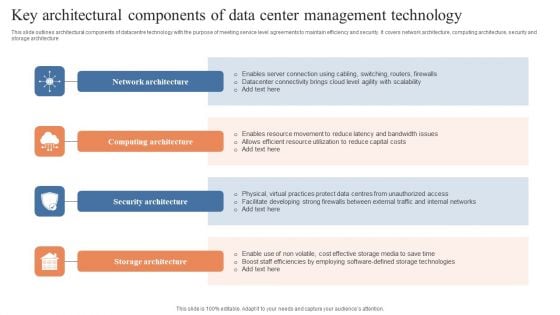
Key Architectural Components Of Data Center Management Technology Introduction PDF
This slide outlines architectural components of datacentre technology with the purpose of meeting service level agreements to maintain efficiency and security. It covers network architecture, computing architecture, security and storage architecture. Presenting Key Architectural Components Of Data Center Management Technology Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Network Architecture, Computing Architecture, Security Architecture. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Agenda For Data Security In Cloud Computing Ppt Powerpoint
Present like a pro with Agenda For Data Security In Cloud Computing Ppt Powerpoint. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Our Agenda For Data Security In Cloud Computing Ppt Powerpoint are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Data Breach Prevention Recognition Security Awareness Tracking Kpis Inspiration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a data breach prevention recognition security awareness tracking kpis inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































