Data Protection Strategy Template
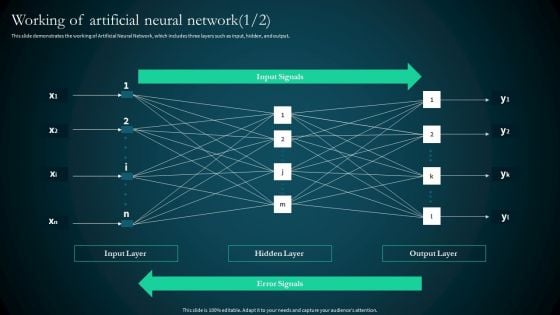
Artificial Reural Network Ann Computational Model Working Of Artificial Neural Network Pictures PDF
This slide demonstrates the working of Artificial Neural Network, which includes three layers such as input, hidden, and output. Slidegeeks has constructed Artificial Reural Network Ann Computational Model Working Of Artificial Neural Network Pictures PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
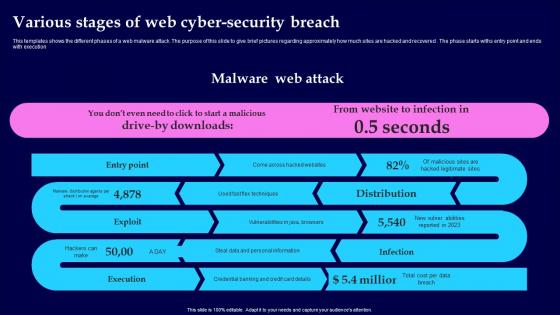
Various Stages Of Web Cyber Security Breach Introduction Pdf
This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution Pitch your topic with ease and precision using this Various Stages Of Web Cyber Security Breach Introduction Pdf This layout presents information on Malware Web Attack, Various Stages, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution
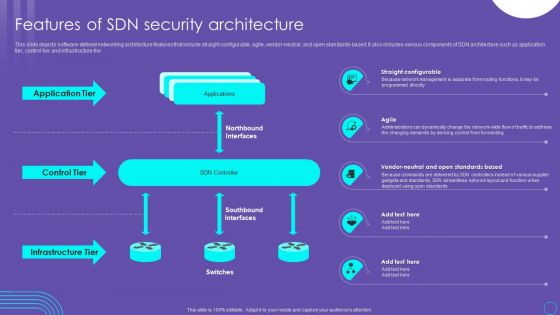
Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF
This slide depicts software defined networking architecture features that include straight configurable, agile, vendor neutral, and open standards based. It also includes various components of SDN architecture such as application tier, control tier and infrastructure tier. Find highly impressive Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
Identity Authentication Service Sap In Powerpoint And Google Slides Cpb
Introducing our well designed Identity Authentication Service Sap In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Identity Authentication Service Sap. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Identity Authentication Service Sap In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
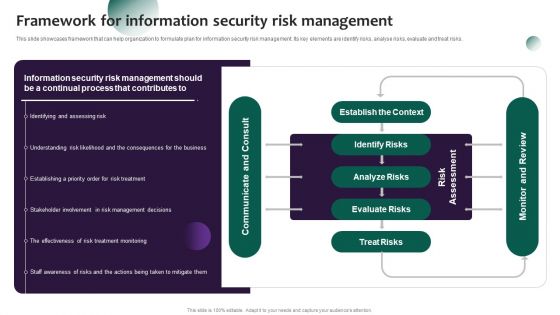
Information Systems Security And Risk Management Plan Framework For Information Security Risk Management Formats PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyse risks, evaluate and treat risks. Create an editable Information Systems Security And Risk Management Plan Framework For Information Security Risk Management Formats PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Information Systems Security And Risk Management Plan Framework For Information Security Risk Management Formats PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Prioritized Risk And Response Grid With Likelihood Severity And Detention Assessment Introduction PDF
This slide displays the project management risk and response matrix. It risk details such as effect, likelihood, severity, detention, Risk Priority Number RPN, and response strategy. Showcasing this set of slides titled Prioritized Risk And Response Grid With Likelihood Severity And Detention Assessment Introduction PDF. The topics addressed in these templates are Incompetent Security, Equipment, Insurance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
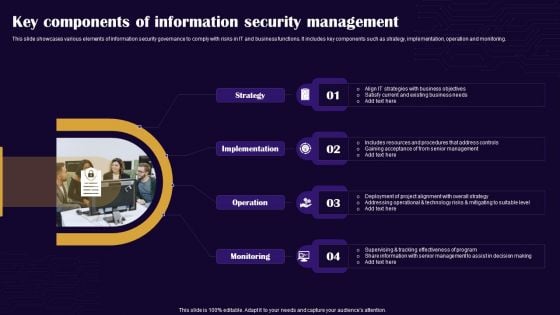
Key Components Of Information Security Management Graphics PDF
This slide showcases various elements of information security governance to comply with risks in IT and business functions. It includes key components such as strategy, implementation, operation and monitoring. Persuade your audience using this Key Components Of Information Security Management Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strategy, Implementation, Operation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Strategic Agenda Checklist Mockup Pdf
This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status. Showcasing this set of slides titled Cyber Security Strategic Agenda Checklist Mockup Pdf. The topics addressed in these templates are Cyber Security, Strategic Agenda Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status.

Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Slidegeeks has constructed Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
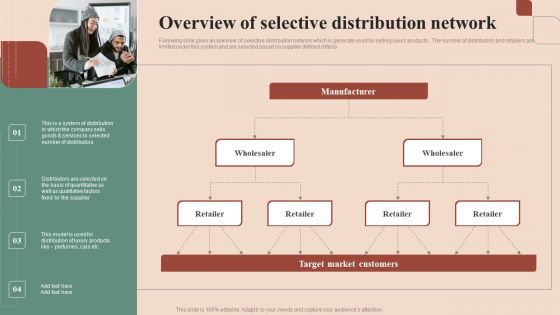
Maximizing Profit Returns With Right Distribution Source Overview Of Selective Distribution Network Information PDF
Following slide gives an overview of selective distribution network which is generally used for selling luxury products. The number of distributors and retailers are limited under this system and are selected based on supplier defined criteria. Following slide gives an overview of selective distribution network which is generally used for selling luxury products. The number of distributors and retailers are limited under this system and are selected based on supplier defined criteria. Are you searching for a Maximizing Profit Returns With Right Distribution Source Overview Of Selective Distribution Network Information PDF that is uncluttered, straightforward, and original. Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Maximizing Profit Returns With Right Distribution Source Overview Of Selective Distribution Network Information PDF from Slidegeeks today.
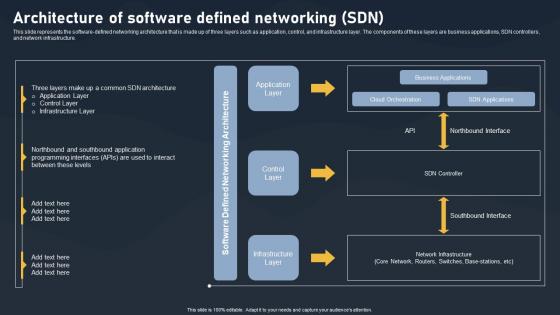
Architecture Of Software Defined Networking SDN Building Blocks Background Pdf
This slide represents the software-defined networking architecture that is made up of three layers such as application, control, and infrastructure layer. The components of these layers are business applications, SDN controllers, and network infrastructure.Explore a selection of the finest Architecture Of Software Defined Networking SDN Building Blocks Background Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Architecture Of Software Defined Networking SDN Building Blocks Background Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the software defined networking architecture that is made up of three layers such as application, control, and infrastructure layer. The components of these layers are business applications, SDN controllers, and network infrastructure.

Key Channels Community Networking Platform Business Model
This slide showcases companys content distribution channels for enhancing community experiences through websites, mobile applications android and iOS apps and social media networks, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Key Channels Community Networking Platform Business Model will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases companys content distribution channels for enhancing community experiences through websites, mobile applications android and iOS apps and social media networks, etc.

5G Evolution Architectural Technology Discovering Policy Framework For 5G Network Clipart PDF
This slide provides details regarding policy framework for 5G in terms of facilitating access to site locations, enabling backhaul deployments, harmonizing power density limitations, etc. Deliver an awe inspiring pitch with this creative 5G Evolution Architectural Technology Discovering Policy Framework For 5G Network Clipart PDF bundle. Topics like Facilitating Access, Regulatory Relaxations, Harmonizing Power can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Introduction To Smart Doorbells Used For Maintaining Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the video doorbells used to enhance security. The slide includes features of smart doorbells that are motion detection, video storage, multi-user functionality, night vision camera, etc. There are so many reasons you need a Introduction To Smart Doorbells Used For Maintaining Security Utilizing Smart Appliances IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide provides an overview of the video doorbells used to enhance security. The slide includes features of smart doorbells that are motion detection, video storage, multi-user functionality, night vision camera, etc.
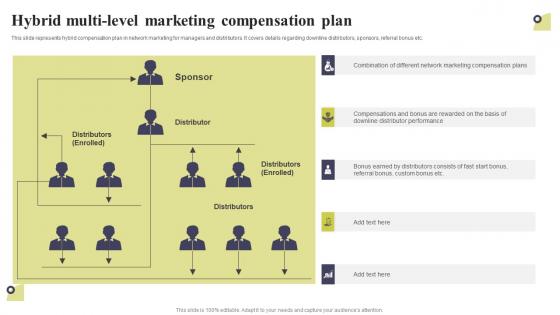
Hybrid Multi Level Marketing Compensation Plan Multi Level Marketing Download Pdf
This slide represents hybrid compensation plan in network marketing for managers and distributors. It covers details regarding downline distributors, sponsors, referral bonus etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Hybrid Multi Level Marketing Compensation Plan Multi Level Marketing Download Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents hybrid compensation plan in network marketing for managers and distributors. It covers details regarding downline distributors, sponsors, referral bonus etc.
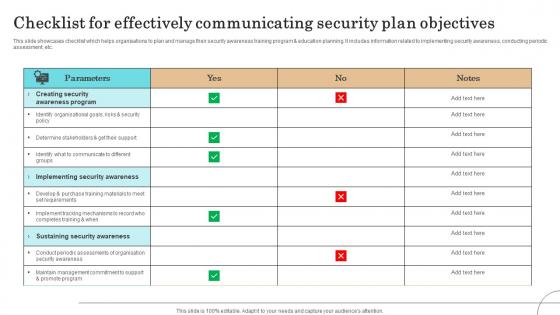
Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf
This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.Showcasing this set of slides titled Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf The topics addressed in these templates are Implementing Security Awareness, Sustaining Security Awareness, Awareness Program All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.

Zero Trust Model Service Initiated Zero Trust Network Topology Model
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Model Service Initiated Zero Trust Network Topology Model for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.
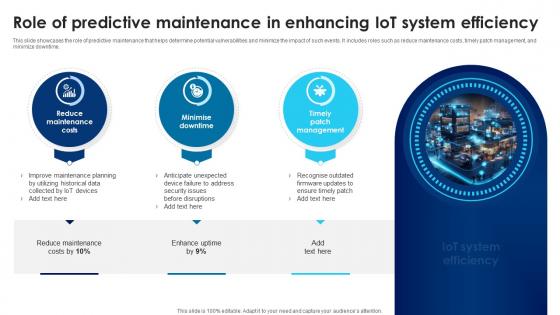
Building Trust With IoT Security Role Of Predictive Maintenance In Enhancing IoT System Efficiency IoT SS V
This slide showcases the role of predictive maintenance that helps determine potential vulnerabilities and minimize the impact of such events. It includes roles such as reduce maintenance costs, timely patch management, and minimize downtime. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Building Trust With IoT Security Role Of Predictive Maintenance In Enhancing IoT System Efficiency IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases the role of predictive maintenance that helps determine potential vulnerabilities and minimize the impact of such events. It includes roles such as reduce maintenance costs, timely patch management, and minimize downtime.
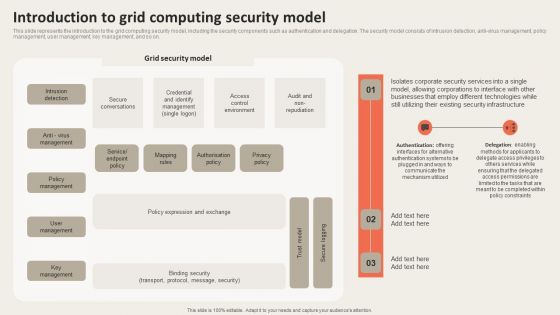
Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Tech Solution Company Elevator Pitch Deck Client Testimonials Summary PDF
This slide caters to the details related to the clients feedback based on their experiences. It consists of information about a company that provides solutions to manufacturers unique problems, creating secure, well designed solutions, and generating data-driven insights. Create an editable Tech Solution Company Elevator Pitch Deck Client Testimonials Summary PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Tech Solution Company Elevator Pitch Deck Client Testimonials Summary PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Comprehensive Manual For Overview Of Private Blockchain Networks BCT SS V
This slide covers brief summary of private blockchain networks. It includes benefits such as preventing fraud by using identity to confirm membership, higher performance due to lesser nodes, private blockchain are currently more scalable, etc. along with characteristics. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Comprehensive Manual For Overview Of Private Blockchain Networks BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide covers brief summary of private blockchain networks. It includes benefits such as preventing fraud by using identity to confirm membership, higher performance due to lesser nodes, private blockchain are currently more scalable, etc. along with characteristics.
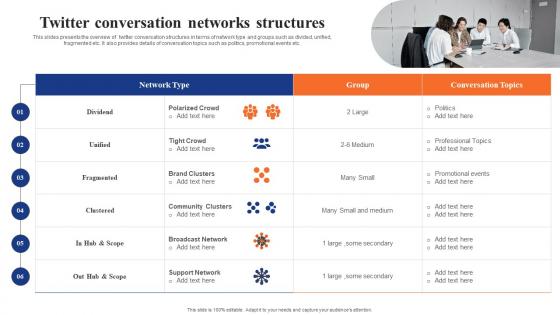
Digital Advertising Using Twitter Twitter Conversation Networks Structures Demonstration Pdf
This slides presents the overview of twitter conversation structures in terms of network type and groups such as divided, unified, fragmented etc. It also provides details of conversation topics such as politics, promotional events etc. Slidegeeks has constructed Digital Advertising Using Twitter Twitter Conversation Networks Structures Demonstration Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. This slides presents the overview of twitter conversation structures in terms of network type and groups such as divided, unified, fragmented etc. It also provides details of conversation topics such as politics, promotional events etc.
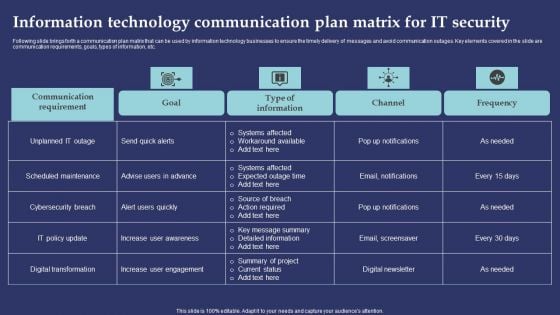
Information Technology Communication Plan Matrix For It Security Professional PDF
Following slide brings forth a communication plan matrix that can be used by information technology businesses to ensure the timely delivery of messages and avoid communication outages. Key elements covered in the slide are communication requirements, goals, types of information, etc. Showcasing this set of slides titled Information Technology Communication Plan Matrix For It Security Professional PDF. The topics addressed in these templates are Systems Affected, Workaround Available, Action Required. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Effective Network Marketing Promotion Tactics Table Of Contents Ideas Pdf
Take your projects to the next level with our ultimate collection of Effective Network Marketing Promotion Tactics Table Of Contents Ideas Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest Our Effective Network Marketing Promotion Tactics Table Of Contents Ideas Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Two Tier Network Marketing Revenue Icon Rules Pdf
Showcasing this set of slides titled Two Tier Network Marketing Revenue Icon Rules Pdf. The topics addressed in these templates are Two Tier Network, Marketing Revenue Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Two Tier Network Marketing Revenue Icon Rules Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
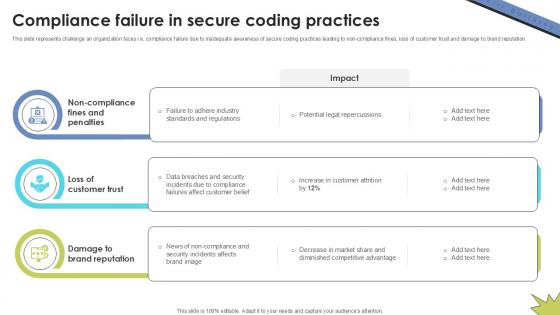
Compliance Failure In Secure Skill Building Plan For Application PPT Slide DTE SS V
This slide represents challenge an organization faces i.e. compliance failure due to inadequate awareness of secure coding practices leading to non-compliance fines, loss of customer trust and damage to brand reputation. Want to ace your presentation in front of a live audience Our Compliance Failure In Secure Skill Building Plan For Application PPT Slide DTE SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents challenge an organization faces i.e. compliance failure due to inadequate awareness of secure coding practices leading to non-compliance fines, loss of customer trust and damage to brand reputation.
Best Practices Of Cloud Management Action Plan Icons PDF
The following slide presents best practices of cloud migration strategy. It includes carefully working out a strategy, framing a cloud governance agenda, augmenting network etc.Persuade your audience using this Best Practices Of Cloud Management Action Plan Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Technology, Network, System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Business Password Manager In Powerpoint And Google Slides Cpb
Introducing our well-designed Business Password Manager In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Business Password Manager. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Business Password Manager In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
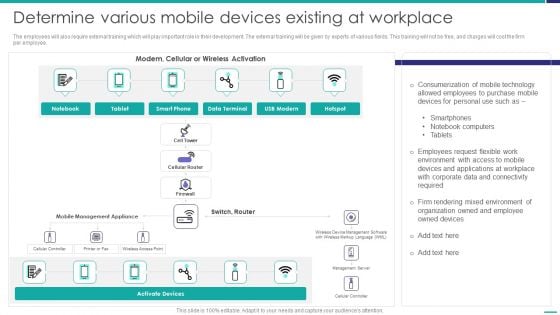
Determine Various Mobile Devices Existing At Workplace Mobile Device Security Management Guidelines PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative Determine Various Mobile Devices Existing At Workplace Mobile Device Security Management Guidelines PDF bundle. Topics like Corporate Data, Allowed Employees, Consumerization Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
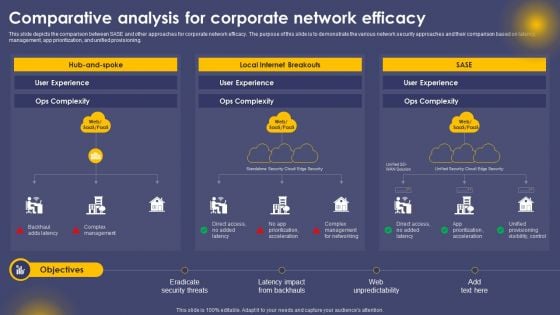
Comparative Analysis For Corporate Network Efficacy Ppt Model Master Slide PDF
This slide depicts the comparison between SASE and other approaches for corporate network efficacy. The purpose of this slide is to demonstrate the various network security approaches and their comparison based on latency, management, app prioritization, and unified provisioning. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Comparative Analysis For Corporate Network Efficacy Ppt Model Master Slide PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
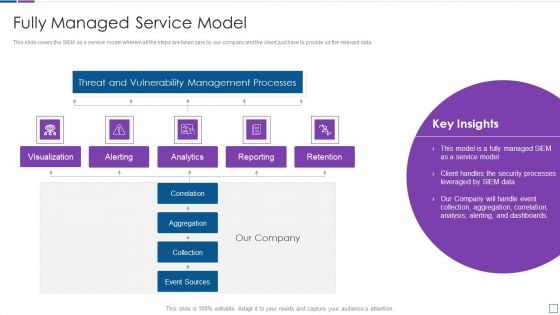
Real Time Assessment Of Security Threats Fully Managed Service Model Demonstration PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an awe inspiring pitch with this creative real time assessment of security threats fully managed service model demonstration pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V
This slide shows information regarding various types of threats associated with Bitcoins security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V. This slide shows information regarding various types of threats associated with Bitcoins security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.
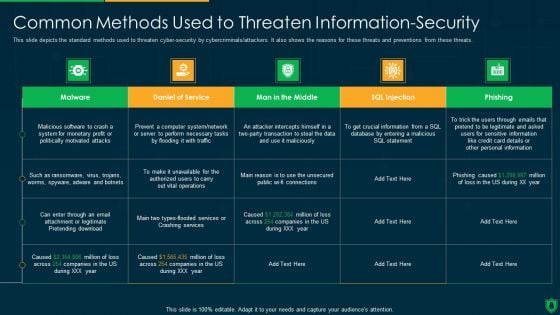
Info Security Common Methods Used To Threaten Information Security Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver an awe inspiring pitch with this creative info security common methods used to threaten information security ppt powerpoint presentation gallery clipart images pdf bundle. Topics like personal information, phishing caused, sql statement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
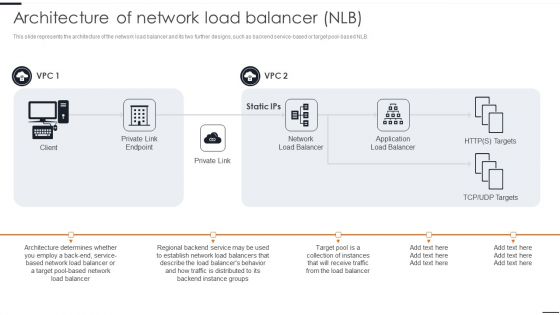
Elastic NLB Architecture Of Network Load Balancer NLB Brochure PDF
This slide represents the architecture of the network load balancer and its two further designs, such as backend service based or target pool based NLB. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Elastic NLB Architecture Of Network Load Balancer NLB Brochure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
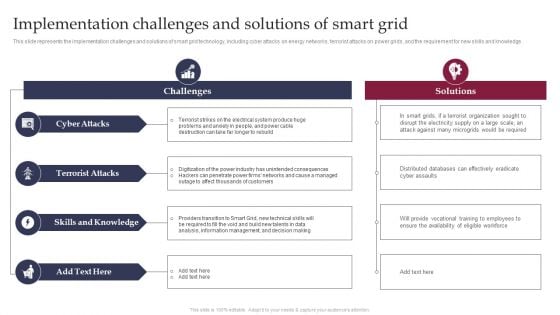
Smart Grid Technology Implementation Challenges And Solutions Designs PDF
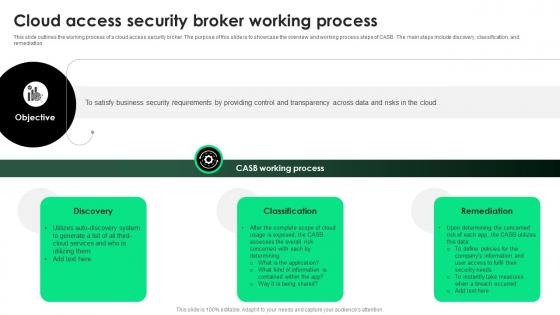
CASB 2 0 IT Cloud Access Security Broker Working Process
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download CASB 2 0 IT Cloud Access Security Broker Working Process to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the CASB 2 0 IT Cloud Access Security Broker Working Process. This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation.
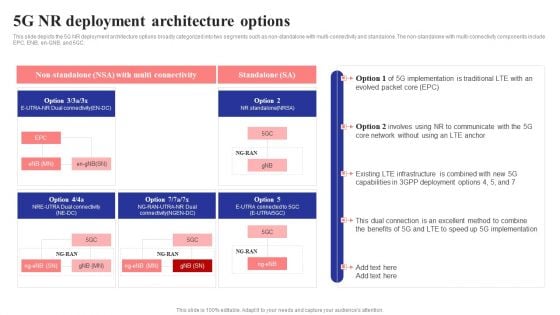
5G NR Deployment Architecture Options 5G Network Structure Background PDF
This slide depicts the 5G NR deployment architecture options broadly categorized into two segments such as non-standalone with multi-connectivity and standalone. The non-standalone with multi-connectivity components include EPC, ENB, en-GNB, and 5GC.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate 5G NR Deployment Architecture Options 5G Network Structure Background PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Table Of Contents For Securing Market Leadership Through Competitive Excellence Demonstration PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Securing Market Leadership Through Competitive Excellence Demonstration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
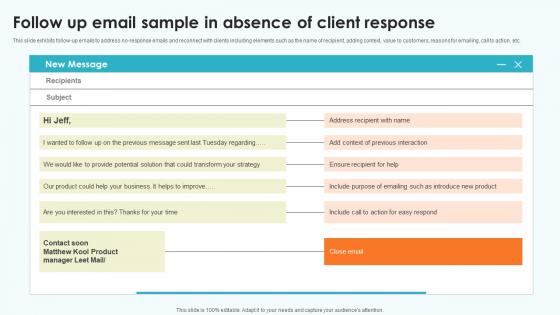
Elevating Sales Networks Follow Up Email Sample In Absence Of Client Response SA SS V
This slide exhibits follow-up emails to address no-response emails and reconnect with clients including elements such as the name of recipient, adding context, value to customers, reasons for emailing, call to action, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Elevating Sales Networks Follow Up Email Sample In Absence Of Client Response SA SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Elevating Sales Networks Follow Up Email Sample In Absence Of Client Response SA SS V. This slide exhibits follow-up emails to address no-response emails and reconnect with clients including elements such as the name of recipient, adding context, value to customers, reasons for emailing, call to action, etc.
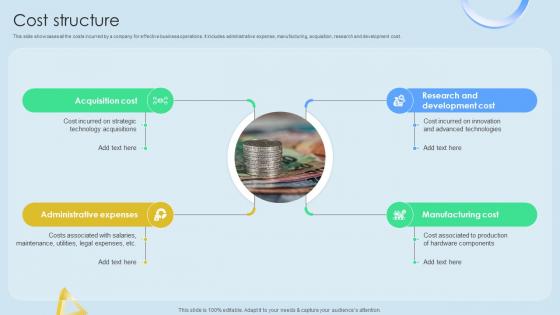
Cost Structure Cloud Networking Service Provider Business Model BMC SS V
This slide showcases all the costs incurred by a company for effective business operations. It includes administrative expense, manufacturing, acquisition, research and development cost. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cost Structure Cloud Networking Service Provider Business Model BMC SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases all the costs incurred by a company for effective business operations. It includes administrative expense, manufacturing, acquisition, research and development cost.
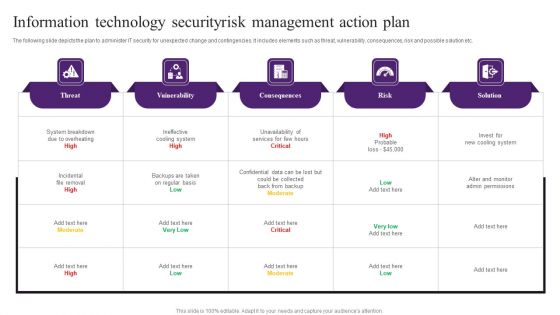
Information Technology Securityrisk Management Action Plan Themes PDF
The following slide depicts the plan to administer IT security for unexpected change and contingencies. It includes elements such as threat, vulnerability, consequences, risk and possible solution etc. Showcasing this set of slides titled Information Technology Securityrisk Management Action Plan Themes PDF. The topics addressed in these templates are Consequences, Vuinerability, System Breakdown. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Employee Incentives Icon For Healthcare And Financial Security Designs Pdf
Showcasing this set of slides titled Employee Incentives Icon For Healthcare And Financial Security Designs Pdf The topics addressed in these templates are Employee Incentives, Icon For Healthcare, Financial Security All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Employee Incentives Icon For Healthcare And Financial Security Designs Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Healthcare Information Security Risk Management And Management Plan Information PDF
This slide shows information security risk treatment and acceptance plan for hospitals which can benefit them in securing their data. It contains details such as possession type, risk acceptance criteria, treating the risk, techniques and approaches for risk, residual risk acceptance measures, etc. Pitch your topic with ease and precision using this Healthcare Information Security Risk Management And Management Plan Information PDF. This layout presents information on Measures, Risk Acceptance Criteria, Treating The Risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Network And In Stream Monitoring Technologies Ppt PowerPoint Presentation Ideas
Presenting this set of slides with name network and in stream monitoring technologies ppt powerpoint presentation ideas. This is a three stage process. The stages in this process are business, management, planning, strategy, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Transition Plan For Business Management Steps To Conduct Impacted Employee Analysis Clipart PDF
This slide covers the steps to conduct impacted employee analysis which includes collecting data, identifying impacted groups, job roles and duties, authenticating employee analysis data, etc. Retrieve professionally designed Transition Plan For Business Management Steps To Conduct Impacted Employee Analysis Clipart PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Table Of Contents For Amazon Strategic Growth Initiative On Global Scale Securing Elements PDF
Find highly impressive Table Of Contents For Amazon Strategic Growth Initiative On Global Scale Securing Elements PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents For Amazon Strategic Growth Initiative On Global Scale Securing Elements PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
Icon Showcasing Network Infrastructure Analysis Elements Pdf
Showcasing this set of slides titled Icon Showcasing Network Infrastructure Analysis Elements Pdf The topics addressed in these templates are Icon Showcasing Network, Infrastructure Analysis All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Icon Showcasing Network Infrastructure Analysis Elements Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Zero Trust Model Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Model Zero Trust Network Access Architecture Workflow here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Zero Trust Network Access Architecture Workflow to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
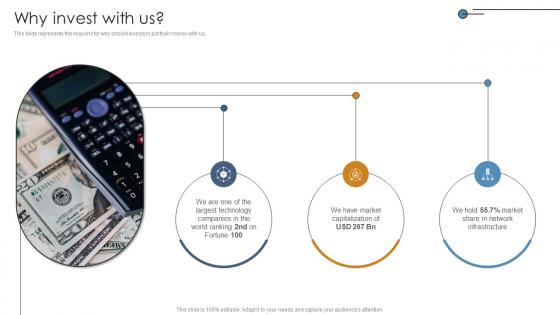
Why Invest With Us Networking Solutions Manufacturer Investor Funding Elevator Pitch Deck
This slide represents the reasons for why should investors put their money with us. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Why Invest With Us Networking Solutions Manufacturer Investor Funding Elevator Pitch Deck from Slidegeeks and deliver a wonderful presentation. This slide represents the reasons for why should investors put their money with us.

WAF Introduction Web Application Firewall Vs Network Firewall Background PDF
This slide describes the comparison between web application firewall and network firewall. The purpose of this slide is to showcase the relationship between web application firewall and network firewall. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. DownloadWAF Introduction Web Application Firewall Vs Network Firewall Background PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing theWAF Introduction Web Application Firewall Vs Network Firewall Background PDF.
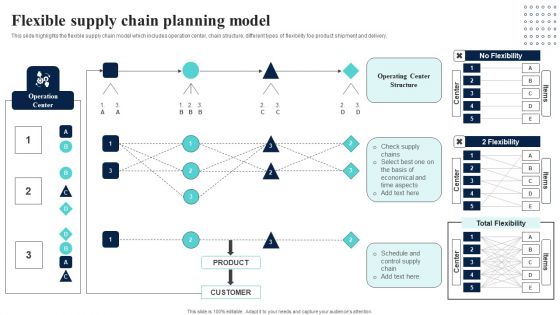
Supply Network Planning And Administration Tactics Flexible Supply Chain Planning Model Designs PDF
This slide highlights the flexible supply chain model which includes operation center, chain structure, different types of flexibility foe product shipment and delivery, There are so many reasons you need a Supply Network Planning And Administration Tactics Flexible Supply Chain Planning Model Designs PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
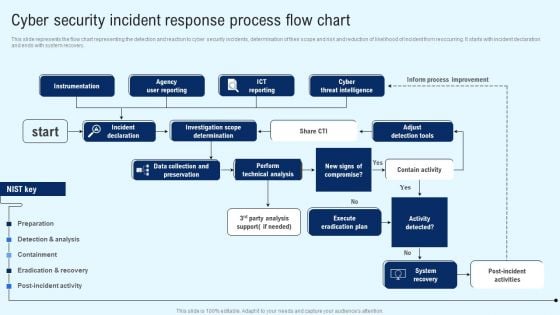
Implementing Cyber Security Incident Cyber Security Incident Response Process Flow Chart Designs PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Explore a selection of the finest Implementing Cyber Security Incident Cyber Security Incident Response Process Flow Chart Designs PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Implementing Cyber Security Incident Cyber Security Incident Response Process Flow Chart Designs PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
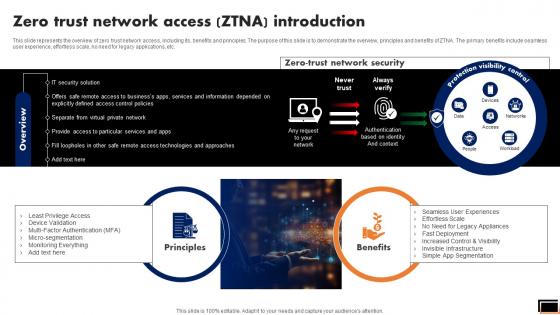
Zero Trust Network Access Ztna Introduction Software Defined Perimeter SDP
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Network Access Ztna Introduction Software Defined Perimeter SDP to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Network Access Ztna Introduction Software Defined Perimeter SDP. This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.

Blockchain In Financial Sector For Security Ppt PowerPoint Presentation File Slide Portrait PDF
Showcasing this set of slides titled blockchain in financial sector for security ppt powerpoint presentation file slide portrait pdf. The topics addressed in these templates are security, digital transactions, authentication of users. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Managed Network Services Table Of Contents Managed Network Services Ideas PDF
Find highly impressive Managed Network Services Table Of Contents Managed Network Services Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Managed Network Services Table Of Contents Managed Network Services Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
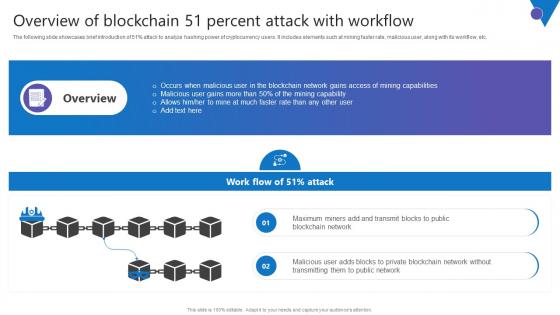
Overview Of Blockchain 51 Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide showcases brief introduction of 51percent attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Slidegeeks has constructed Overview Of Blockchain 51 Comprehensive Guide To Blockchain Digital Security Information Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. The following slide showcases brief introduction of 51percent attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc.

Deploying House Flipping Business Plan Major Challenges Faced By Investors During Fix And Flip Microsoft PDF
Find highly impressive Deploying House Flipping Business Plan Major Challenges Faced By Investors During Fix And Flip Microsoft PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Deploying House Flipping Business Plan Major Challenges Faced By Investors During Fix And Flip Microsoft PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Reasons To Adopt Zero Trust Network Access Model Software Defined Perimeter SDP
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Reasons To Adopt Zero Trust Network Access Model Software Defined Perimeter SDP to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Reasons To Adopt Zero Trust Network Access Model Software Defined Perimeter SDP. This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on.
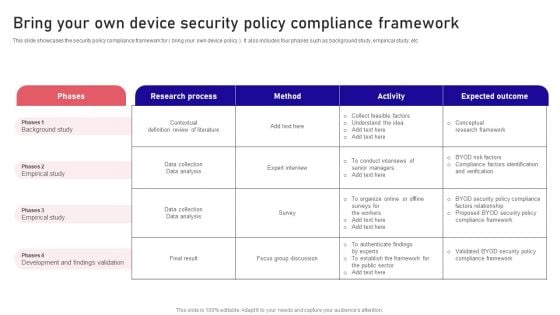
Bring Your Own Device Security Policy Compliance Framework Ideas PDF
This slide showcases the security policy compliance framework for bring your own device policy. It also includes four phases such as background study, empirical study, etc. Showcasing this set of slides titled Bring Your Own Device Security Policy Compliance Framework Ideas PDF. The topics addressed in these templates are Phases, Background Study, Empirical Study . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































