Data Protection

Table Of Contents For Network Load Balancing IT Cluster Ppt Show Information PDF
Presenting table of contents for network load balancing it cluster ppt show information pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like network, business, strategies, requirements. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
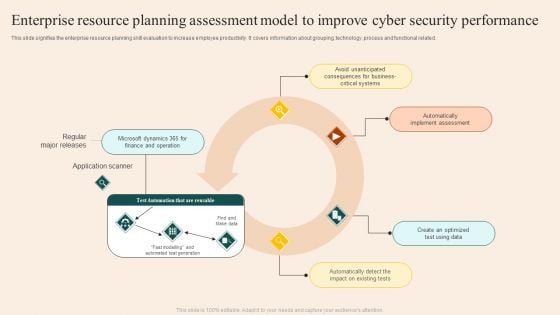
Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF
This slide signifies the enterprise resource planning skill evaluation to increase employee productivity. It covers information about grouping, technology ,process and functional related. Showcasing this set of slides titled Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF. The topics addressed in these templates are Regular Major Releases, Application Scanner, Implement Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
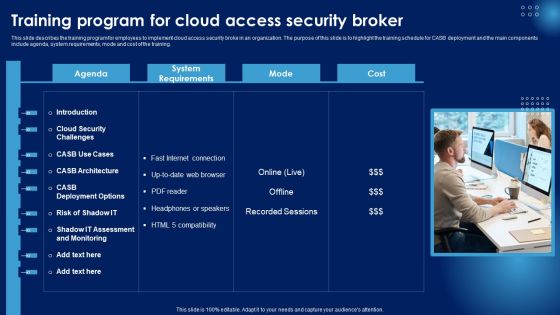
Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF
This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF today and make your presentation stand out from the rest.

Agile Model Improve Task Team Performance Various Information Technology Departments In Company Designs PDF
This slide shows the IT department structure in the company that includes various division such as Research and Development, Product Development, Administration Development, Support and Security Department and IT Services Development. This is a agile model improve task team performance various information technology departments in company designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like research, development, security, services, administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
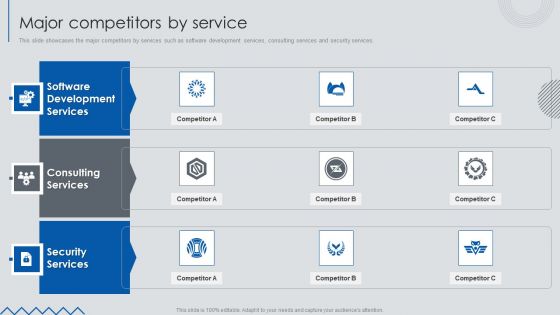
Information Technology Solutions Business Profile Major Competitors By Service Ideas PDF
This slide showcases the major competitors by services such as software development services, consulting services and security services.This is a Information Technology Solutions Business Profile Major Competitors By Service Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Software Development, Consulting Services, Security Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mastering Blockchain Wallets Best Practices For Enabling Blockchain Wallet Safety BCT SS V
This slide covers tips for enabling safety of blockchain wallets helping users. The purpose of this template is to provide an overview on key practices to be followed such as keeping small quantities of crypto assets in online, generating impenetrable wallets requiring authentication, ensuring wallet software and mobile is constantly updated, securing wallets with Fort Knox by using complex long form password, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Mastering Blockchain Wallets Best Practices For Enabling Blockchain Wallet Safety BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide covers tips for enabling safety of blockchain wallets helping users. The purpose of this template is to provide an overview on key practices to be followed such as keeping small quantities of crypto assets in online, generating impenetrable wallets requiring authentication, ensuring wallet software and mobile is constantly updated, securing wallets with Fort Knox by using complex long form password, etc.

Agenda For Techniques And Strategies To Reduce Security Management Risks Themes PDF
This is a agenda for techniques and strategies to reduce security management risks themes pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like enable organizational, structure and technology, internal and external You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Operating Designs PDF
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard operating designs pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
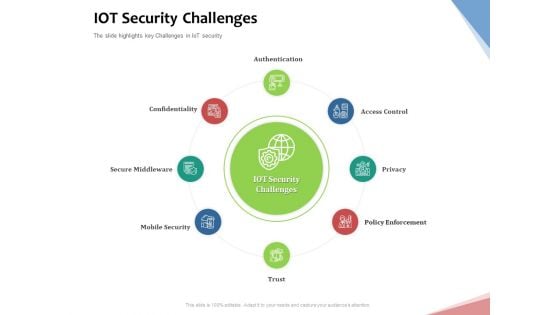
Machine To Machine Communication Outline Iot Security Challenges Ppt File Background Designs PDF
The slide highlights key Challenges in IoT security. Presenting machine to machine communication outline iot security challenges ppt file background designs pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like authentication, access control, privacy, policy enforcement, trust, mobile security, secure middleware, confidentiality. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Ppt Templates Social Network Branding PowerPoint Slides
PPT_templates_Social_network_Branding_PowerPoint_Slides-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! These PowerPoint presentation slides can be used to represent themes relating to --Activity, answer, background, black, blank, boxes, brainteaser, challenge, clue, crossword, down, empty, game, hobby, illustration, leisure, pastime, problem, puzzle, question, quiz, raster, rectangle, solution, spelling, square, template, tile, unfinished, up, vocabulary, white, word-PPT_templates_Social_network_Branding_PowerPoint_Slides Audit your thoughts with our Ppt Templates Social Network Branding PowerPoint Slides. They will authenticate their excellence.
PowerPoint Slides Marketing Puzzle Process Ppt Presentation
PowerPoint Slides Marketing Puzzle Process PPT Presentation-Puzzles PowerPoint templates being the perennial educational tool. Emphasize the process of your business/corporate growth. Highlight your ideas broad- based on strong fundamentals and illustrate how they step by step achieve the set growth factor.-These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go. Audit your thoughts with our PowerPoint Slides Marketing Puzzle Process Ppt Presentation. They will authenticate their excellence.
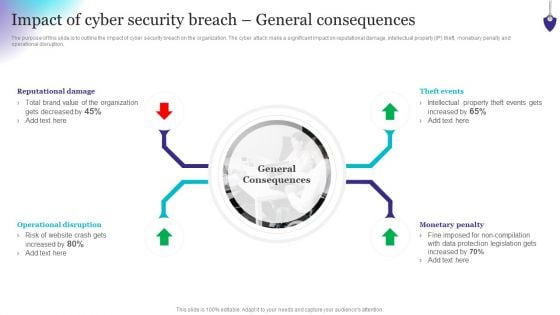
Organizing Security Awareness Impact Of Cyber Security Breach General Graphics PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetxary penalty and operational disruption. If you are looking for a format to display your unique thoughts, then the professionally designed Organizing Security Awareness Impact Of Cyber Security Breach General Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Organizing Security Awareness Impact Of Cyber Security Breach General Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Icon For Payment Security Technology In Market Investor Transactions Summary PDF
Presenting Icon For Payment Security Technology In Market Investor Transactions Summary PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Icon For Payment Security, Technology Market Investor, Transactions Summary. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
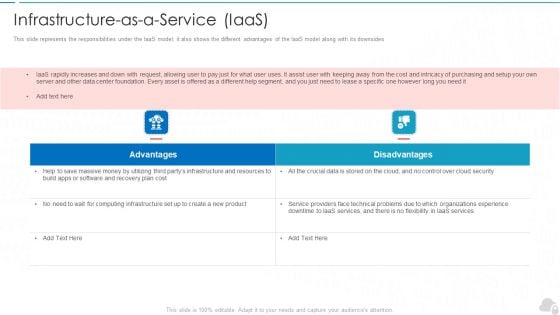
Infrastructure As A Service Iaas Cloud Computing Security IT Ppt Layouts Background Image PDF
This slide represents the responsibilities under the IaaS model it also shows the different advantages of the IaaS model along with its downsides. This is a infrastructure as a service iaas cloud computing security it ppt layouts background image pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advantages, disadvantages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
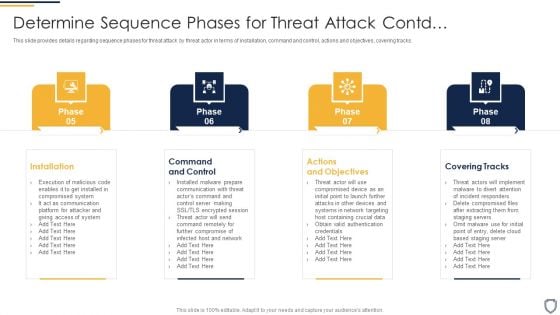
Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Contd Mockup PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a corporate security and risk management determine sequence phases for threat attack contd mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
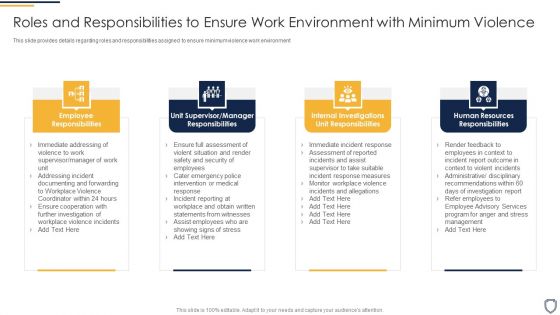
Corporate Security And Risk Management Roles And Responsibilities To Ensure Work Professional PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment This is a corporate security and risk management roles and responsibilities to ensure work professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, unit supervisor manager responsibilities, internal investigations unit responsibilities, human resources responsibilities . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
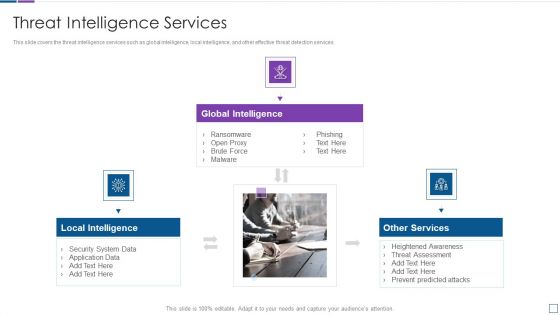
Real Time Assessment Of Security Threats Threat Intelligence Services Guidelines PDF
This slide covers the threat intelligence services such as global intelligence, local intelligence, and other effective threat detection services. This is a real time assessment of security threats threat intelligence services guidelines pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global intelligence, local intelligence, other services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security For Your Organization Table Of Contents Ppt Design Ideas PDF
Presenting this set of slides with name cyber security for your organization table of contents ppt design ideas pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, role personnel, dashboard, impact analysis, cost associated firm, cybersecurity contingency plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Table Of Contents Ppt Inspiration Professional PDF
Presenting this set of slides with name strategies to mitigate cyber security risks table of contents ppt inspiration professional pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role personnel, cost associated to firm, impact analysis dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Implementation Framework Table Of Contents Ppt PowerPoint Presentation Icon Portfolio PDF
Presenting this set of slides with name cyber security implementation framework table of contents ppt powerpoint presentation icon portfolio pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role of personnel, cost associated to firm, impact analysis, dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
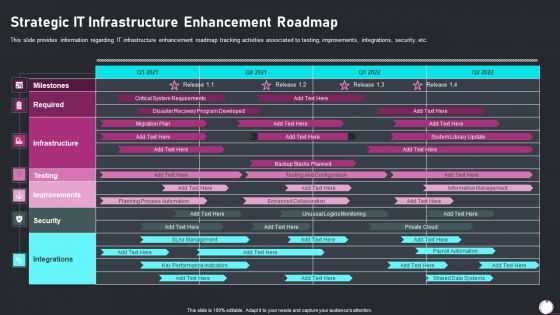
Information Technology Transformation Playbook Strategic IT Infrastructure Enhancement Elements PDF
This slide provides information regarding IT infrastructure enhancement roadmap tracking activities associated to testing, improvements, integrations, security, etc. Deliver and pitch your topic in the best possible manner with this information technology transformation playbook strategic it infrastructure enhancement elements pdf. Use them to share invaluable insights on required, infrastructure, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
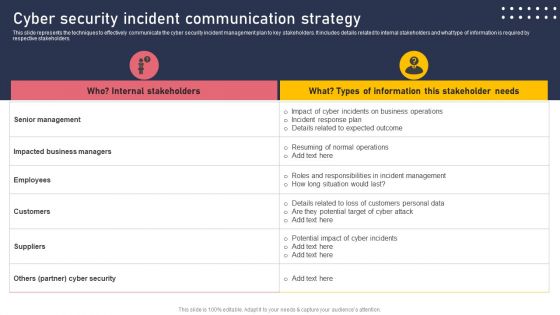
Cyber Security Incident Communication Strategy Formats PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Cyber Security Incident Communication Strategy Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
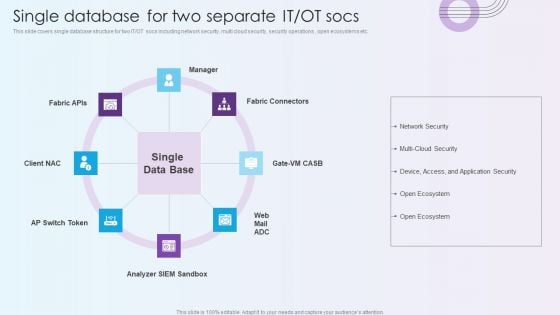
Digitalization Of Operative Enterprises Single Database For Two Separate IT OT Socs Structure PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc.This is a Digitalization Of Operative Enterprises Single Database For Two Separate IT OT Socs Structure PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyzer, Network Security, Multi Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
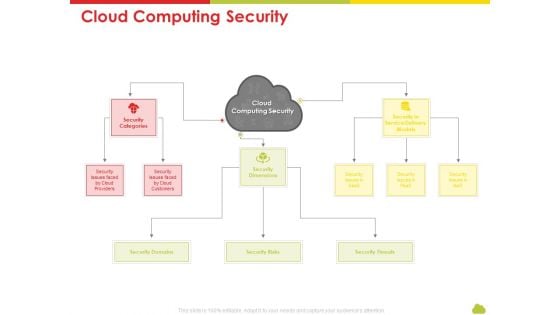
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Cloud Computing Security Rules PDF
Presenting mesh computing technology hybrid private public iaas paas saas workplan cloud computing security rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like risks, threats, domains, service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
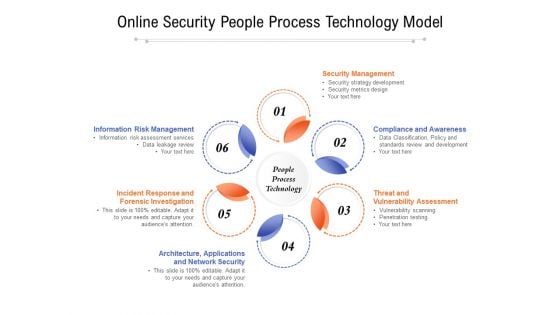
Online Security People Process Technology Model Ppt PowerPoint Presentation Slides Example Introduction PDF
Presenting online security people process technology model ppt powerpoint presentation slides example introduction pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including security management, compliance and awareness, threat and vulnerability assessment, architecture, applications, incident response and forensic investigation, information risk management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Make sure to capture your audiences attention in your business displays with our gratis customizable CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
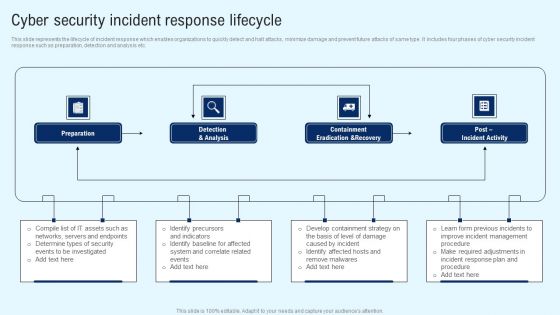
Implementing Cyber Security Incident Cyber Security Incident Response Lifecycle Brochure PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response Lifecycle Brochure PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
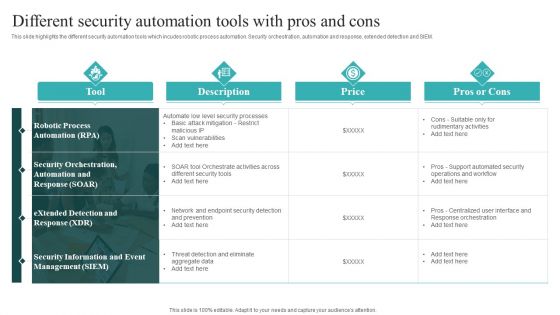
IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
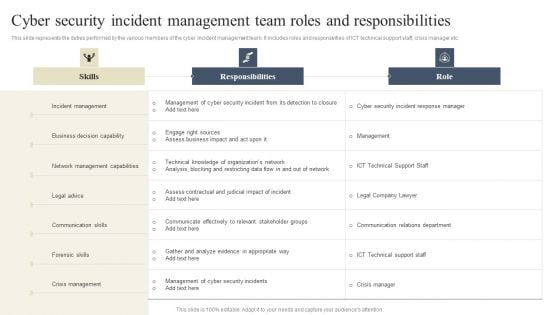
CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. If you are looking for a format to display your unique thoughts, then the professionally designed CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
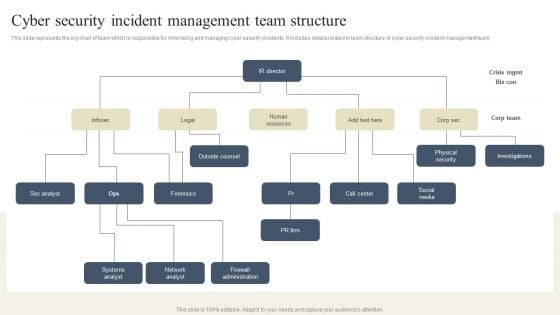
CYBER Security Breache Response Strategy Cyber Security Incident Management Team Structure Clipart PDF
This slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Structure Clipart PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
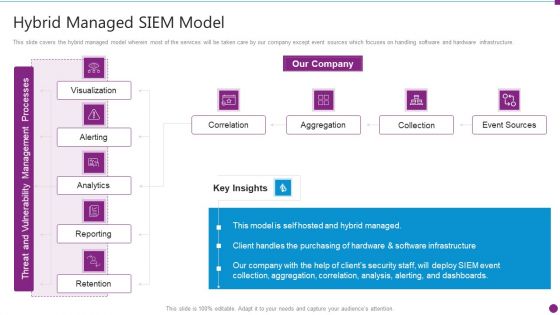
Security Information And Event Management Strategies For Financial Audit And Compliance Hybrid Managed Siem Model Topics PDF
This slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance hybrid managed siem model topics pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
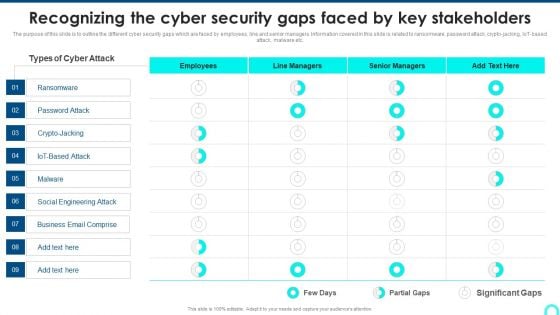
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Deliver and pitch your topic in the best possible manner with this Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF. Use them to share invaluable insights on Ransomware, Engineering Attack, Email Comprise and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
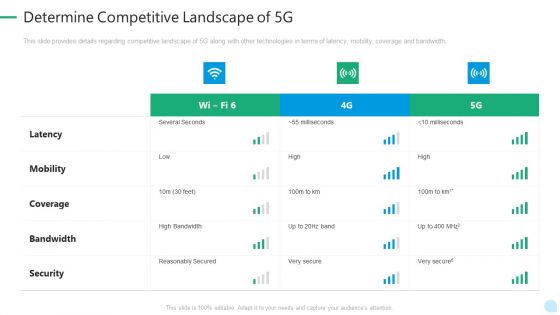
5G Network Technology Determine Competitive Landscape Of 5G Ppt Summary Visual Aids PDF
This slide provides details regarding competitive landscape of 5G along with other technologies in terms of latency, mobility, coverage and bandwidth. Deliver and pitch your topic in the best possible manner with this 5g network technology determine competitive landscape of 5g ppt summary visual aids pdf. Use them to share invaluable insights on latency, mobility, coverage, bandwidth, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
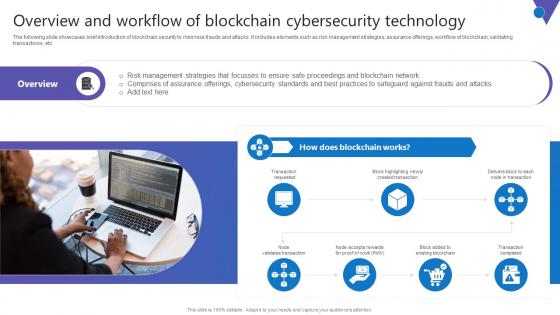
Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Explore a selection of the finest Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc.
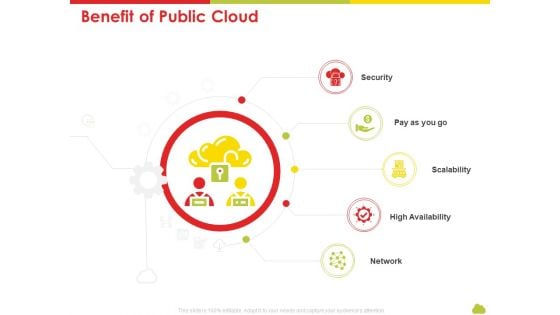
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Benefit Of Public Cloud Pictures PDF
This is a mesh computing technology hybrid private public iaas paas saas workplan benefit of public cloud pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, scalability, high availability, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF
This slide describes the integrity and confidentiality principle of GDPR, which implies putting suitable technologies and organizational safeguards to avoid hazards. Do you know about Slidesgeeks Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
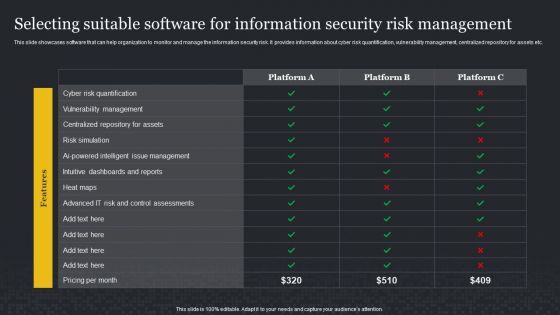
Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases software that can help organization to monitor and manage the information security risk. It provides information about cyber risk quantification, vulnerability management, centralized repository for assets etc. If you are looking for a format to display your unique thoughts, then the professionally designed Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cloud Technology Risks With Security Incident Management Ppt PowerPoint Presentation Gallery Graphics Template PDF
Presenting cloud technology risks with security incident management ppt powerpoint presentation gallery graphics template pdf. to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identification and allowance, management interface vulnerability, security incident management, application security management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
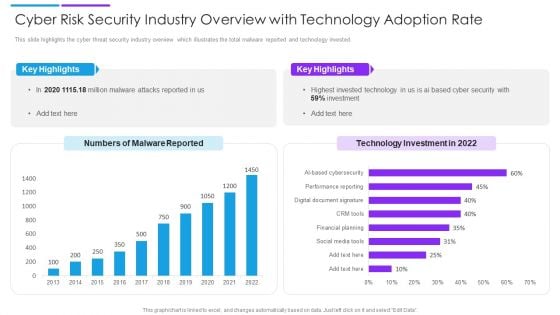
Cyber Risk Security Industry Overview With Technology Adoption Rate Slides PDF
This slide highlights the cyber threat security industry overview which illustrates the total malware reported and technology invested. Pitch your topic with ease and precision using this cyber risk security industry overview with technology adoption rate slides pdf. This layout presents information on key highlights, technology investment, malware reported. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
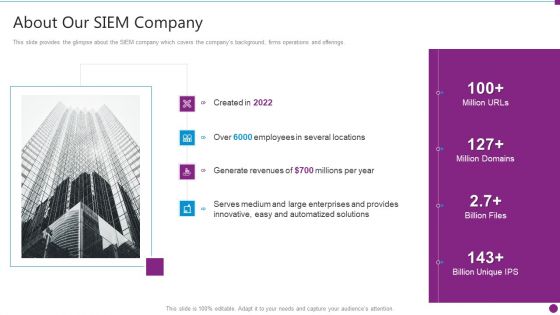
Security Information And Event Management Strategies For Financial Audit And Compliance About Our SIEM Company Summary PDF
This slide provides the glimpse about the SIEM company which covers the companys background, firms operations and offerings. This is a security information and event management strategies for financial audit and compliance about our siem company summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like about our siem company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
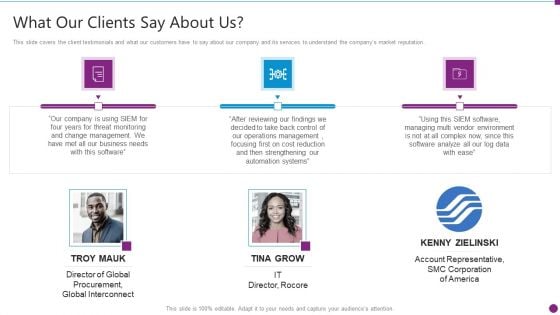
Security Information And Event Management Strategies For Financial Audit And Compliance What Our Clients Say About Us Diagrams PDF
This slide covers the client testimonials and what our customers have to say about our company and its services to understand the companys market reputation. This is a security information and event management strategies for financial audit and compliance what our clients say about us diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like what our clients say about us. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training. If you are looking for a format to display your unique thoughts, then the professionally designed Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Cloud Computing Network Building Icon Themes PDF
Persuade your audience using this Cloud Computing Network Building Icon Themes PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Computing, Network Building Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Virtual Coinage Icon For Secured Payment System Professional PDF
Presenting Virtual Coinage Icon For Secured Payment System Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Virtual Coinage Icon, Secured Payment System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
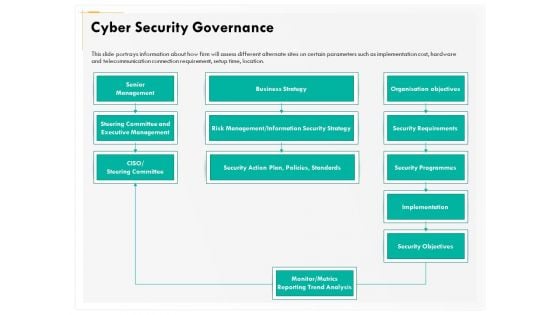
Computer Security Incident Handling Cyber Security Governance Ppt Gallery Summary PDF
Presenting this set of slides with name computer security incident handling cyber security governance ppt gallery summary pdf. The topics discussed in these slides are senior management, business strategy, security objectives, implementation, security requirements, risk management or information security strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
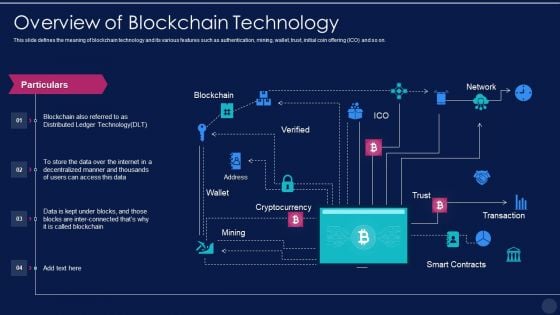
Blockchain Technology Framework IT Overview Of Blockchain Technology Professional PDF
This slide defines the meaning of blockchain technology and its various features such as authentication, mining, wallet, trust, initial coin offering ICO and so on. Deliver and pitch your topic in the best possible manner with this blockchain technology framework it overview of blockchain technology professional pdf. Use them to share invaluable insights on overview of blockchain technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
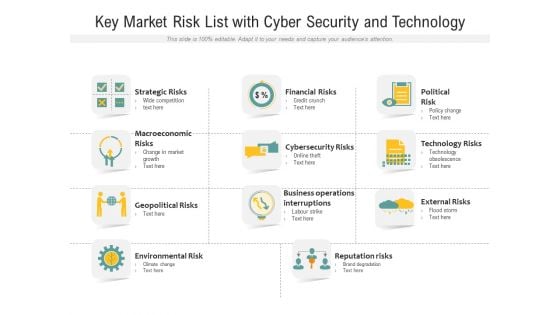
Key Market Risk List With Cyber Security And Technology Ppt PowerPoint Presentation File Show PDF
Showcasing this set of slides titled key market risk list with cyber security and technology ppt powerpoint presentation file show pdf. The topics addressed in these templates are strategic risks, macroeconomic, geopolitical risks, environmental risk, financial risks, cybersecurity risks, political risk, technology risks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Exploitation IT Use Of Security Programs Mockup PDF
This slide represents the usage of security programs such as secure socket layer, web application firewall, website, and software scanners that will secure and help detect malicious attacks. Presenting cyber exploitation it use of security programs mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like secure sockets layer, web application firewall, website and software scanners. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Addressing The Various Security Incidents And Attacks Icons PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.Create an editable Addressing The Various Security Incidents And Attacks Icons PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Addressing The Various Security Incidents And Attacks Icons PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
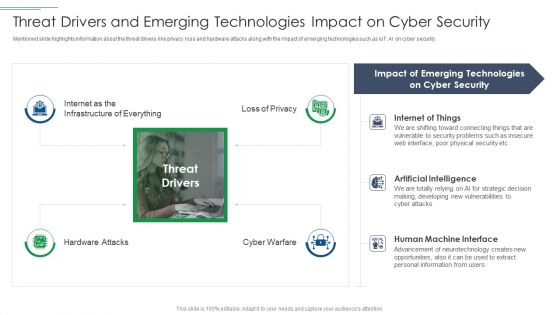
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
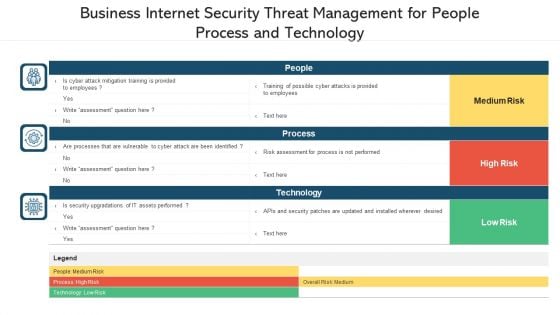
Business Internet Security Threat Management For People Process And Technology Ppt PowerPoint Presentation File Inspiration PDF
Pitch your topic with ease and precision using this business internet security threat management for people process and technology ppt powerpoint presentation file inspiration pdf. This layout presents information on people, process, technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
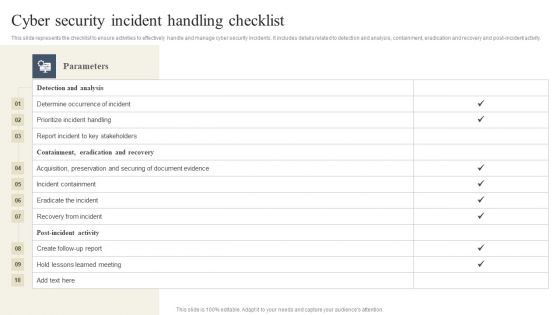
CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF today and make your presentation stand out from the rest.
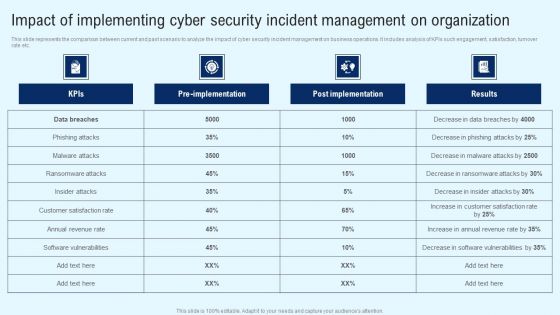
Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
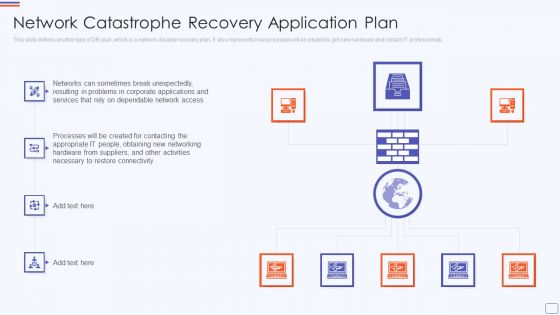
Network Catastrophe Recovery Application Plan Portrait PDF
This slide defines another type of DR plan, which is a network disaster recovery plan. It also represents how processes will be created to get new hardware and contact IT professionals. This is a network catastrophe recovery application plan portrait pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network catastrophe recovery application plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Services Network Server Icon Topics PDF
Showcasing this set of slides titled Cloud Services Network Server Icon Topics PDF. The topics addressed in these templates are Cloud Services, Network Server Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Digital Network Transformation Timeline Icon Clipart PDF
Showcasing this set of slides titled Digital Network Transformation Timeline Icon Clipart PDF. The topics addressed in these templates are Digital Network Transformation, Timeline Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
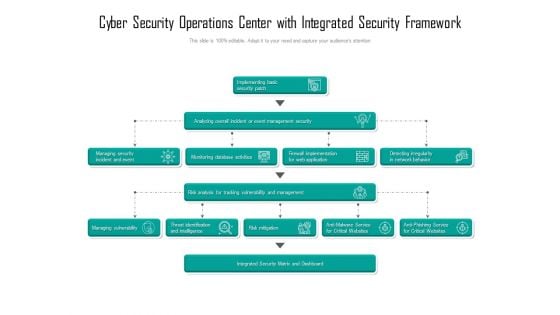
Cyber Security Operations Center With Integrated Security Framework Ppt Gallery Graphics Design PDF
Showcasing this set of slides titled cyber security operations center with integrated security framework ppt gallery graphics design pdf. The topics addressed in these templates are security, framework, management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
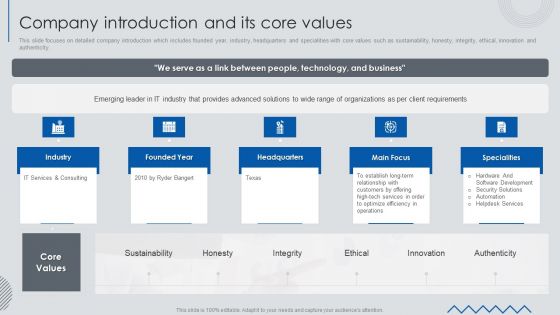
Information Technology Solutions Business Profile Company Introduction And Its Core Values Infographics PDF
This slide focuses on detailed company introduction which includes founded year, industry, headquarters and specialities with core values such as sustainability, honesty, integrity, ethical, innovation and authenticity.Presenting Information Technology Solutions Business Profile Company Introduction And Its Core Values Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Software Development, Security Solutions, Customers Offering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Mitigate Cyber Security Risks Cyber Security Governance Ppt Styles Model PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cyber security governance ppt styles model pdf. This is a one stage process. The stages in this process are senior management, steering committee and executive management, ciso steering committee, business strategy, risk management, information, security strategy, security action plan, policies, standards organisation, objectives security requirements, security programs, implementation, security objectives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































