Data Protection

Need Of Implementing HR Security Programs At Workplace Pictures PDF
This slide highlights the need of importance of workplace safety in an organization. This template aims to provide details regarding workplace safety to increase productivity, reduce turnover rates, safe working conditions, reduction in risk factors, avoid loss of resources, reduction in expenses, foster employee wellbeing and follow legal guidelines, etc. Showcasing this set of slides titled Need Of Implementing HR Security Programs At Workplace Pictures PDF. The topics addressed in these templates are Productivity, Working Environment, Absenteeism. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Workplace Risk Mitigation Strategies For HR Security Portrait PDF
This slide highlights techniques for minimizing risk factors in the workplace. the purpose of this template is to employ effective strategies for ensuring workforce safety eventually enhancing overall productivity and efficiency. It also provides details regarding the status of performance along with insights. Showcasing this set of slides titled Workplace Risk Mitigation Strategies For HR Security Portrait PDF. The topics addressed in these templates are Risk Assessment Management, Safety Training And Education, Compliance Regulations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Threat Security Before And After Artificial Intelligence Formats PDF
This slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Showcasing this set of slides titled Threat Security Before And After Artificial Intelligence Formats PDF. The topics addressed in these templates are Malware, Distributed Denial Service, Social Engineering. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
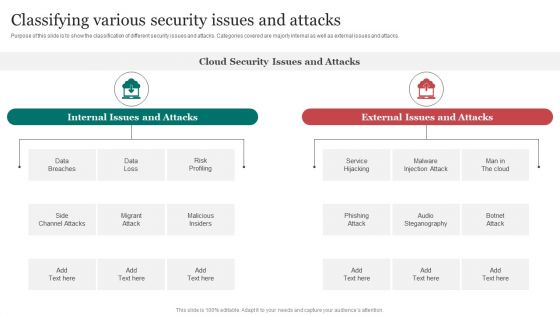
Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Slidegeeks is here to make your presentations a breeze with Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you Are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
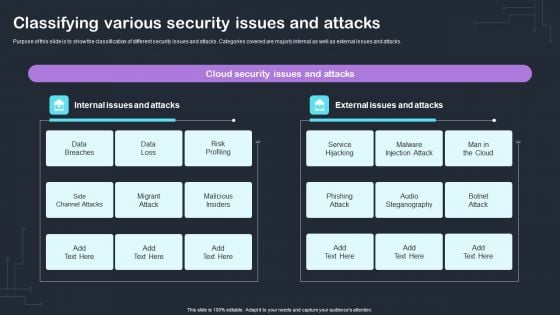
Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Slidegeeks is here to make your presentations a breeze with Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PD With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
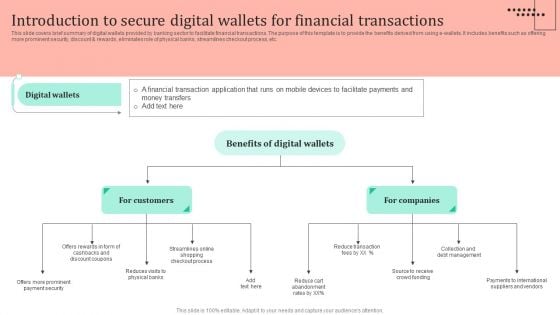
Omnichannel Strategy Implementation For Banking Solutions Introduction To Secure Digital Wallets For Financial Pictures PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Welcome to our selection of the Omnichannel Strategy Implementation For Banking Solutions Introduction To Secure Digital Wallets For Financial Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
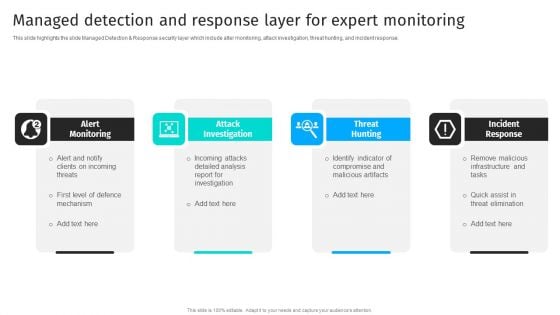
Security Automation To Analyze And Mitigate Cyberthreats Managed Detection And Response Layer Background PDF
This slide highlights the slide Managed Detection Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Security Automation To Analyze And Mitigate Cyberthreats Managed Detection And Response Layer Background PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Real Time Assessment Of Security Threats Estimating Total Cost Of Ownership Of SIEM Icons PDF
This slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support.Deliver an awe inspiring pitch with this creative real time assessment of security threats estimating total cost of ownership of siem icons pdf bundle. Topics like hardware, infrastructure, software, support can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
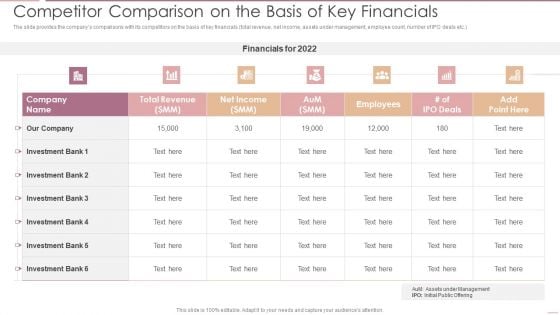
Investment Banking Security Underwriting Pitchbook Competitor Comparison On The Basis Of Key Financials Pictures PDF
The slide provides the companys comparisons with its competitors on the basis of key financials total revenue, net income, assets under management, employee count, number of IPO deals etc.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook Competitor Comparison On The Basis Of Key Financials Pictures PDF bundle. Topics like Total Revenue, Net Income, Investment Bank can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
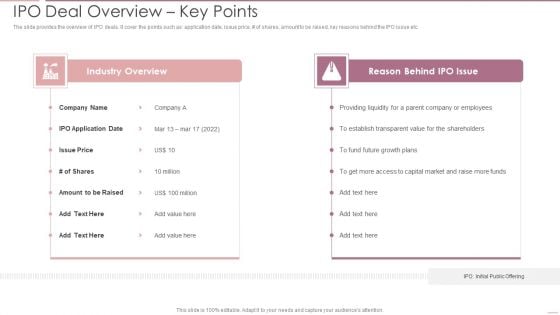
Investment Banking Security Underwriting Pitchbook IPO Deal Overview Key Points Brochure PDF
The slide provides the overview of IPO deals. It cover the points such as application date, issue price, of shares, amount to be raised, key reasons behind the IPO issue etc.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook IPO Deal Overview Key Points Brochure PDF bundle. Topics like Industry Overview, Reason Behind, Providing Liquidity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF
The slide provides the timeline of IPO issue and covers the five steps i.e. Pre-IPO planning, Preparation for Filing, SEC Review, Road Show, and Post IPODeliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF bundle. Topics like Organizational Meeting, Preparation Filling, Internal Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
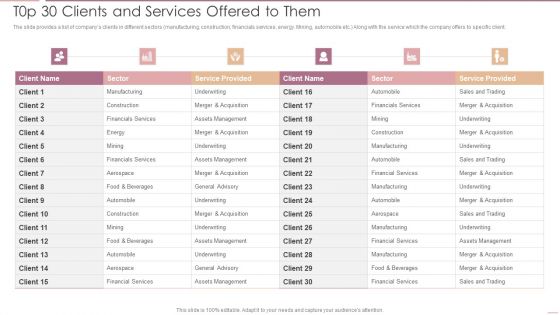
Investment Banking Security Underwriting Pitchbook T0p 30 Clients And Services Offered To Them Professional PDF
The slide provides a list of companys clients in different sectors manufacturing, construction, financials services, energy. Mining, automobile etc. Along with the service which the company offers to specific client.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook T0p 30 Clients And Services Offered To Them Professional PDF bundle. Topics like Financials Services, Assets Management, Underwriting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
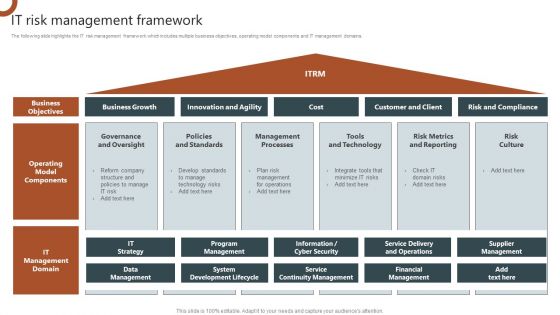
IT Risk Management Framework Organizations Risk Management And IT Security Ideas PDF
The following slide highlights the IT risk management framework which includes multiple business objectives, operating model components and IT management domains. There are so many reasons you need a IT Risk Management Framework Organizations Risk Management And IT Security Ideas PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
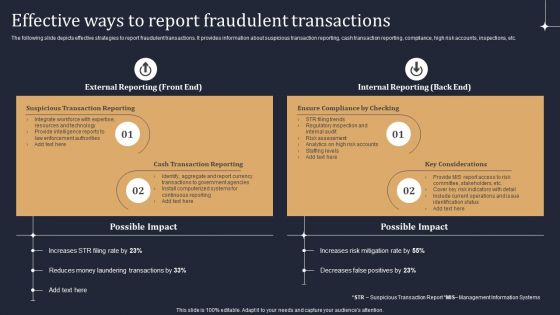
KYC Transaction Monitoring System Business Security Effective Ways To Report Fraudulent Transactions Summary PDF
The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download KYC Transaction Monitoring System Business Security Effective Ways To Report Fraudulent Transactions Summary PDF from Slidegeeks and deliver a wonderful presentation.
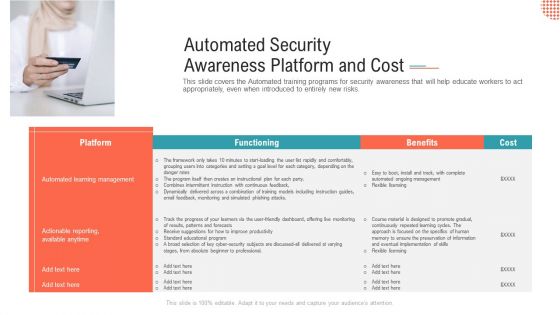
Automated Security Awareness Platform And Cost Graphics PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks.Presenting automated security awareness platform and cost graphics pdf. to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like automated learning management, actionable reporting, available anytime. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security And Surveillance Company Profile Business Development Strategy Icons PDF
This slide highlights the security company channel expansion strategy which showcases strategies for retail, multifamily and professional channels including instore lead generation and robust product offerings.Presenting Security And Surveillance Company Profile Business Development Strategy Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Professional Channels, National Operations, Remove Insurance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Hacker Dashboard For Threat Tracking Rules PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report.Deliver an awe inspiring pitch with this creative IT Security Hacker Dashboard For Threat Tracking Rules PDF bundle. Topics like Threat Dashboard, Loss Of Information, Regulations And Contracts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Measuring The Impact Of Security Awareness Training Structure PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. Deliver and pitch your topic in the best possible manner with this Measuring The Impact Of Security Awareness Training Structure PDF. Use them to share invaluable insights on Attack Significantly, Awareness Campaign, Social Engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
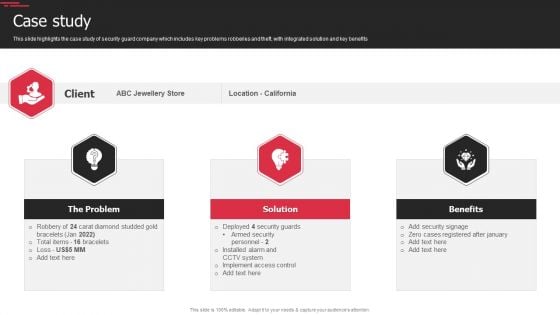
Security Agency Business Profile Case Study Elements PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. Presenting Security Agency Business Profile Case Study Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like The Problem, Solution, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
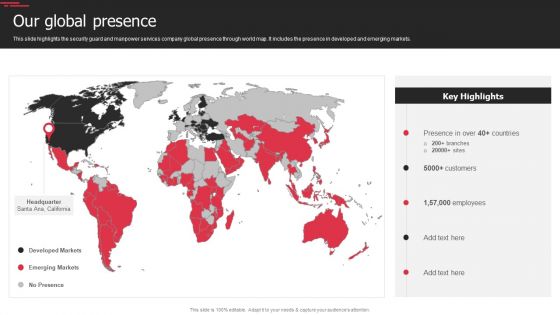
Security Agency Business Profile Our Global Presence Themes PDF
This slide highlights the security guard and manpower services company global presence through world map. It includes the presence in developed and emerging markets. Presenting Security Agency Business Profile Our Global Presence Themes PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Developed Markets, Customers, Employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Our Business Approach Introduction PDF
This slide highlights the business approach of security company which includes strategic planning, human resource management, participatory management and productivity management. Presenting Manpower Corporate Security Business Profile Our Business Approach Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Hr Management, Participatory Management, Productivity Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cyber Security Crisis Communication Process Framework Icons PDF
This slide showcases a model of crisis communication process for cyber security. It includes identify issues, set goals, and objectives, community and constraints, stakeholder assessment, communication and engagement tools, implement strategy and evaluate and follow up. Presenting Cyber Security Crisis Communication Process Framework Icons PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Implement Strategy, Identify Community, Set Goals And Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF
This slide defines the flowchart for web attack incident response. It includes information related to the steps taken to resolve the web attack incident taken place using the cybersecurity. Persuade your audience using this Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Prioritizing Security Response, Investigating, Preparing Report Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills
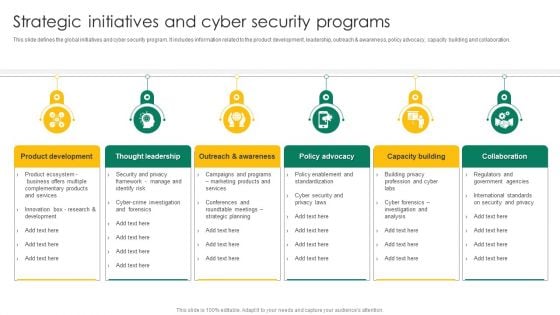
Strategic Initiatives And Cyber Security Programs Ppt Summary Picture PDF
This slide defines the global initiatives and cyber security program. it includes information related to the product development, leadership, outreach and awareness, policy advocacy, capacity building and collaboration. Persuade your audience using this Strategic Initiatives And Cyber Security Programs Ppt Summary Picture PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Product Development, Thought Leadership, Policy Advocacy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
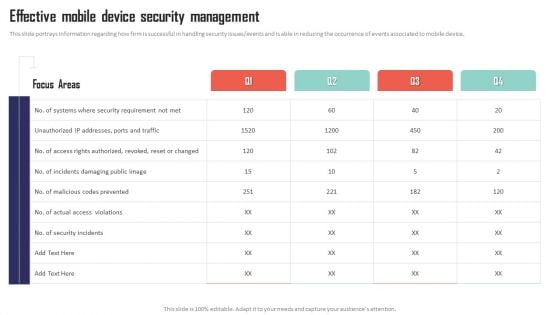
Mobile Device Management Effective Mobile Device Security Management Formats PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. Want to ace your presentation in front of a live audience Our Mobile Device Management Effective Mobile Device Security Management Formats PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Scope For Security Camera Services One Pager Sample Example Document
This slide depicts the project scope providing information about the multiple activities to be performed by the bidding company for the client. Presenting you an exemplary Scope For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Scope For Security Camera Services One Pager Sample Example Document brilliant piece now.
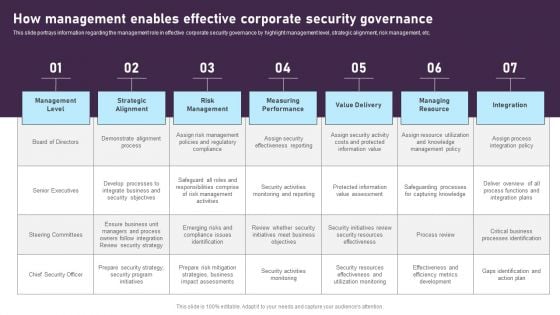
How Management Enables Effective Corporate Security Governance Graphics PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. This modern and well-arranged How Management Enables Effective Corporate Security Governance Graphics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
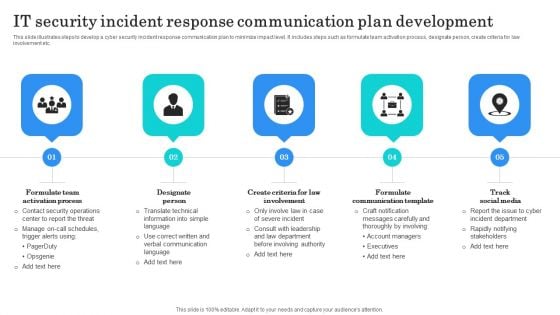
IT Security Incident Response Communication Plan Development Background PDF
This slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting IT Security Incident Response Communication Plan Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Team Activation, Designate Person, Formulate Communication Template. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF
This slide talks about the hashing SHA-256 algorithm used in blockchain technology, including its properties. The purpose of this slide is to give an overview of hashing and its properties, such as collision resistance, deterministic, quick, and irreversible. Create an editable Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Convergence Strategy Information Launch Of Cyber IT OT Strategy Ppt Summary Portrait PDF
This slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. This is a Convergence Strategy Information Launch Of Cyber IT OT Strategy Ppt Summary Portrait PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Audit Demanded, Enable Collaboration, Industrialize Process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
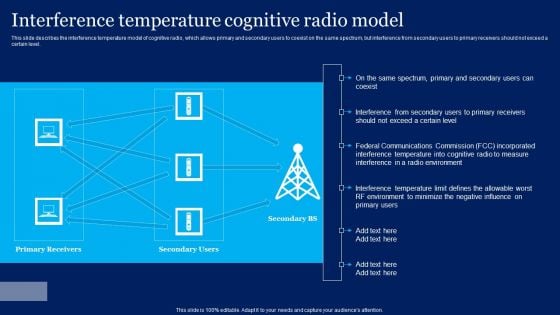
Cognitive Sensor Network Interference Temperature Cognitive Radio Model Ideas PDF
This slide describes the interference temperature model of cognitive radio, which allows primary and secondary users to coexist on the same spectrum, but interference from secondary users to primary receivers should not exceed a certain level. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cognitive Sensor Network Interference Temperature Cognitive Radio Model Ideas PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cognitive Sensor Network Interference Temperature Cognitive Radio Model Ideas PDF today and make your presentation stand out from the rest.
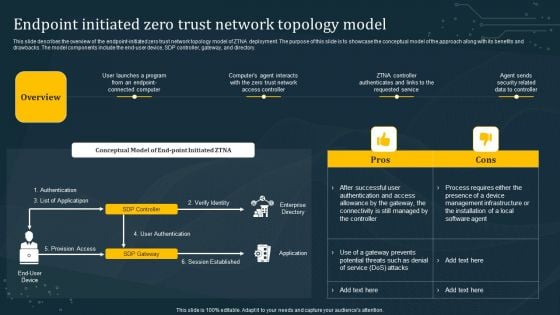
Endpoint Initiated Zero Trust Network Topology Model Sample PDF
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. This modern and well-arranged Endpoint Initiated Zero Trust Network Topology Model Sample PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
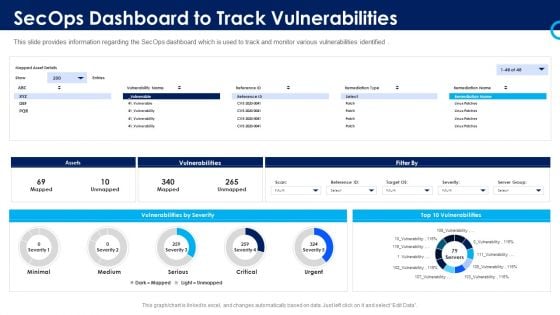
Organizational Security Solutions Secops Dashboard To Track Vulnerabilities Pictures PDF
This slide provides information regarding the SecOps dashboard which is used to track and monitor various vulnerabilities identified. Deliver and pitch your topic in the best possible manner with this organizational security solutions secops dashboard to track vulnerabilities pictures pdf. Use them to share invaluable insights on assets, vulnerabilities, severity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
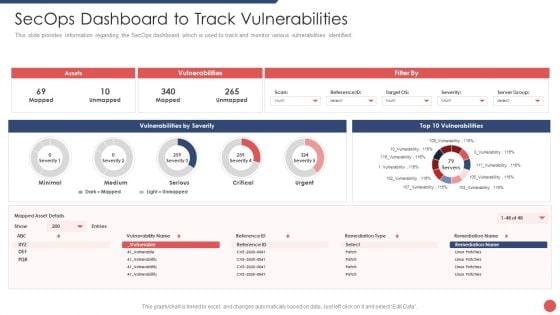
Security Functioning Centre Secops Dashboard To Track Vulnerabilities Portrait PDF
This slide provides information regarding the SecOps dashboard which is used to track and monitor various vulnerabilities identified. Deliver an awe inspiring pitch with this creative security functioning centre secops dashboard to track vulnerabilities portrait pdf bundle. Topics like assets, vulnerabilities, vulnerabilities by severity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Training Program Frameworks Contd Ppt Pictures Layout Ideas PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative Security Training Program Frameworks Contd Ppt Pictures Layout Ideas Pdf bundle. Topics like measures, implement, programs, risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
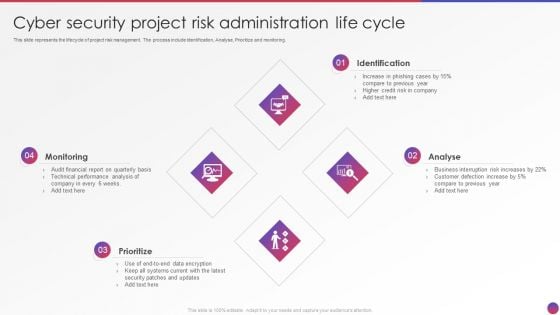
Cyber Security Project Risk Administration Life Cycle Summary PDF
This slide represents the lifecycle of project risk management. The process include Identification, Analyse, Prioritize and monitoring. Presenting Cyber Security Project Risk Administration Life Cycle Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Monitoring, Identification, Analyse, Prioritize. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
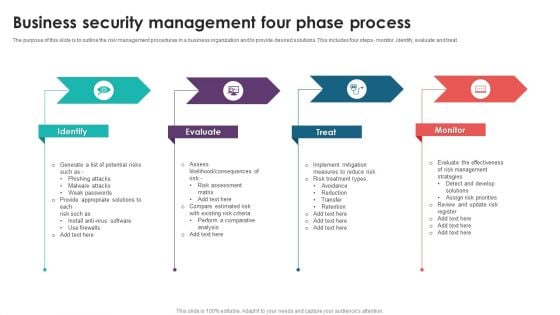
Business Security Management Four Phase Process Topics PDF
The purpose of this slide is to outline the risk management procedures in a business organization and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat. Presenting Business Security Management Four Phase Process Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identify, Evaluate, Treat, Monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
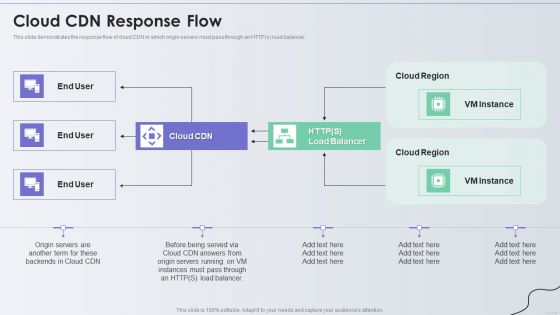
Distribution Network Cloud CDN Response Flow Themes PDF
This slide demonstrates the response flow of cloud CDN in which origin servers must pass through an HTTPs load balancer. Deliver and pitch your topic in the best possible manner with this Distribution Network Cloud CDN Response Flow Themes PDF. Use them to share invaluable insights on Cloud, CDN Response Flow and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
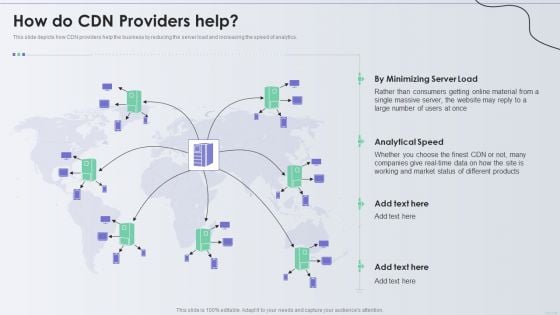
Distribution Network How Do CDN Providers Help Introduction PDF
This slide depicts how CDN providers help the business by reducing the server load and increasing the speed of analytics. Deliver and pitch your topic in the best possible manner with this Distribution Network How Do CDN Providers Help Introduction PDF. Use them to share invaluable insights on Products, Consumers, Material and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
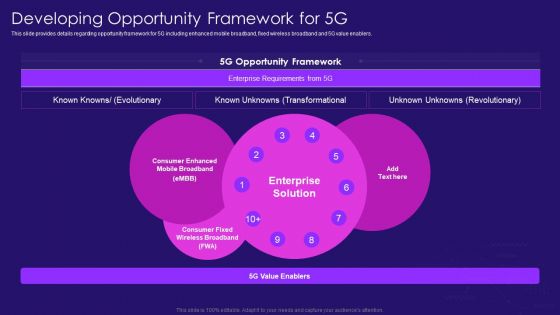
Developing Opportunity Framework For 5G Network Architecture Instructions Mockup PDF
This slide provides details regarding opportunity framework for 5G including enhanced mobile broadband, fixed wireless broadband and 5G value enablers. Deliver an awe inspiring pitch with this creative Developing Opportunity Framework For 5G Network Architecture Instructions Mockup PDF bundle. Topics like Enterprise Solution, Wireless Broadband, Consumer Enhanced can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Exploitation IT Preventing Measures For Social Media Accounts Themes PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies. Presenting cyber exploitation it preventing measures for social media accounts themes pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like social media policies, anti malware software, social media login credentials. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Determine Project Safety Management Team Structure Sample PDF
This slide provides information regarding project safety management team generally comprise of senior management personnel that have authority and resources to accelerate IT projects incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a project security administration it determine project safety management team structure sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like public affair advisor, security manager, legal advisor, medical advisor, crisis management advisor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
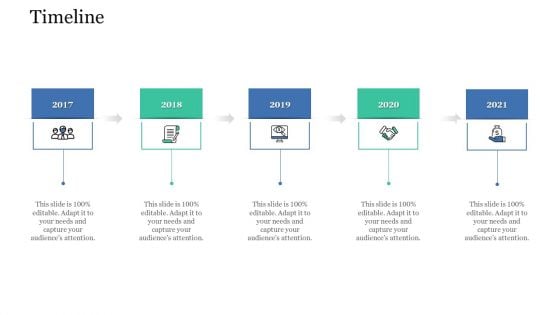
Levels In Logistic Network Management Timeline Demonstration PDF
This is a levels in logistic network management timeline demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2017 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain And DLT Framework Overview Of Blockchain Technology Diagrams PDF
This slide defines the meaning of blockchain technology and its various features such as authentication, mining, wallet, trust, initial coin offering ICO and so on. This is a Blockchain And DLT Framework Overview Of Blockchain Technology Diagrams PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Blockchain, Cryptocurrency, Transaction, Smart Contracts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
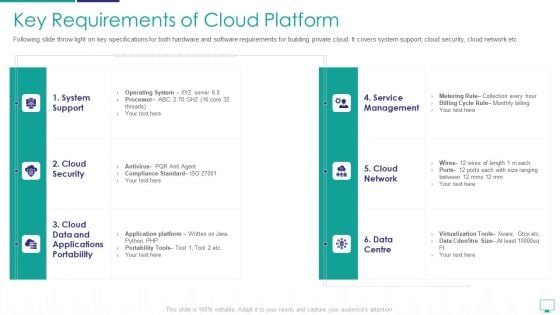
Key Requirements Of Cloud Platform Information PDF
Following slide throw light on key specifications for both hardware and software requirements for building private cloud. It covers system support, cloud security, cloud network etc. Deliver an awe inspiring pitch with this creative key requirements of cloud platform information pdf bundle. Topics like operating system, application platform, compliance standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
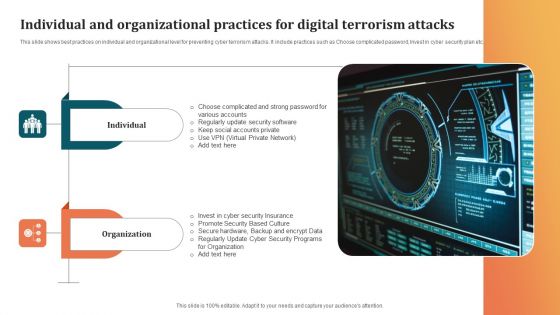
Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF
This slide shows best practices on individual and organizational level for preventing cyber terrorism attacks. It include practices such as Choose complicated password, Invest in cyber security plan etc. Pitch your topic with ease and precision using this Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF. This layout presents information on Organization, Promote Security, Security Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Awareness Training Program Challenges Ppt Styles Clipart PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Take your projects to the next level with our ultimate collection of Security Awareness Training Program Challenges Ppt Styles Clipart PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
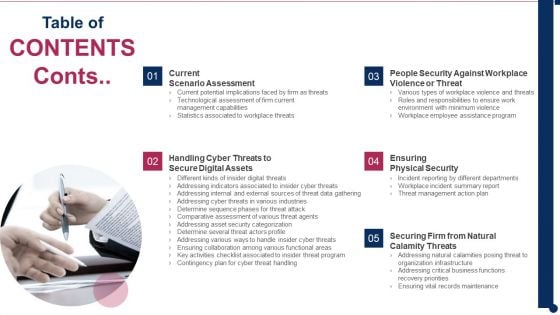
Threat Management At Workplace Contents Conts Diagrams Pdf
This is a threat management at workplace contents conts diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring physical security, current scenario assessment, people security against workplace violence or threat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
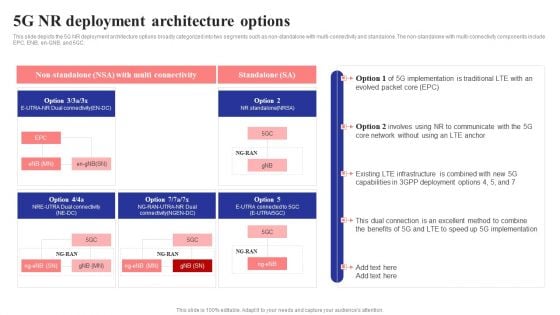
5G NR Deployment Architecture Options 5G Network Structure Background PDF
This slide depicts the 5G NR deployment architecture options broadly categorized into two segments such as non-standalone with multi-connectivity and standalone. The non-standalone with multi-connectivity components include EPC, ENB, en-GNB, and 5GC.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate 5G NR Deployment Architecture Options 5G Network Structure Background PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Transformer Neural Network Architecture Of Chatgpt Brochure PDF
This slide demonstrates the architecture diagram of ChatGPT. The purpose of this slide is to represent how ChatGPT uses transformer model to create cohesive responses. The main components self-attention layers, feed-forward layers, residual connections etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Transformer Neural Network Architecture Of Chatgpt Brochure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
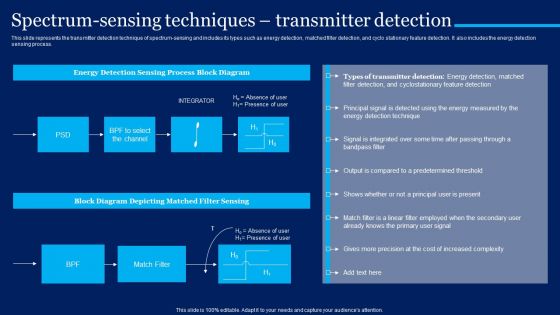
Cognitive Sensor Network Spectrum Sensing Techniques Transmitter Detection Professional PDF
This slide represents the transmitter detection technique of spectrum-sensing and includes its types such as energy detection, matched filter detection, and cyclo stationary feature detection. It also includes the energy detection sensing process. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Cognitive Sensor Network Spectrum Sensing Techniques Transmitter Detection Professional PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Mind Map Design For Entrepreneurial Networking Ppt Design
This is a mind map design for entrepreneurial networking ppt design. This is a six stage process. The stages in this process are mind map, business, idea, marketing, planning.
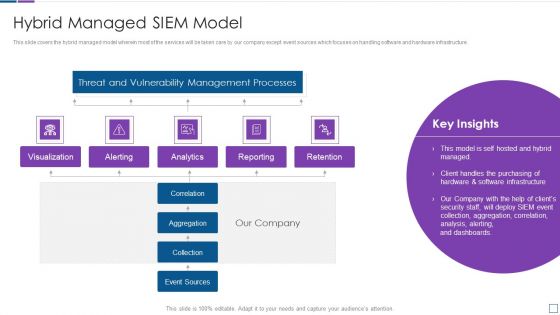
Real Time Assessment Of Security Threats Hybrid Managed SIEM Model Brochure PDF
This slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Deliver an awe inspiring pitch with this creative real time assessment of security threats hybrid managed siem model brochure pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
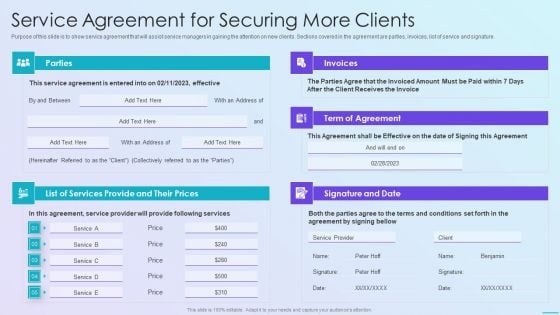
Playbook For Application Developers Service Agreement For Securing More Clients Ideas PDF
Purpose of this slide is to show service agreement that will assist service managers in gaining the attention on new clients. Sections covered in the agreement are parties, invoices, list of service and signature.Deliver and pitch your topic in the best possible manner with this playbook for application developers service agreement for securing more clients ideas pdf Use them to share invaluable insights on term of agreement, signature and date, invoices and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Investment Banking Security Underwriting Pitchbook Key Competitors Of The Company Graphics PDF
The slide provides the key players in the industry by companys size top large companies, mid market companies, small or boutique companies etc.. It has also mentioned the companys major competitors.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Key Competitors Of The Company Graphics PDF Use them to share invaluable insights on Investment Banks, Boutique Investment, Large Investment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
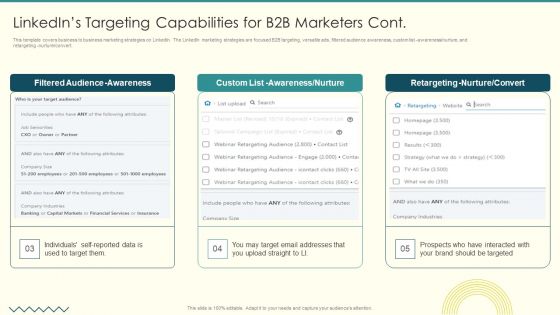
Security And Performance Digital Marketing Linkedins Targeting Capabilities For B2B Marketers Cont Graphics PDF
This template covers business to business marketing strategies on LinkedIn. The LinkedIn marketing strategies are focused B2B targeting, versatile ads, filtered audience awareness, custom list awareness nurture, and retargeting nurture convert.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Linkedins Targeting Capabilities For B2B Marketers Cont Graphics PDF bundle. Topics like Filtered Audience, Awareness Nurture, Retargeting Nurture can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
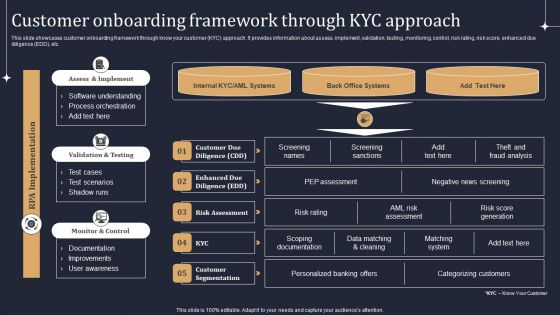
KYC Transaction Monitoring System Business Security Customer Onboarding Framework Introduction PDF
Welcome to our selection of the KYC Transaction Monitoring System Business Security Customer Onboarding Framework Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
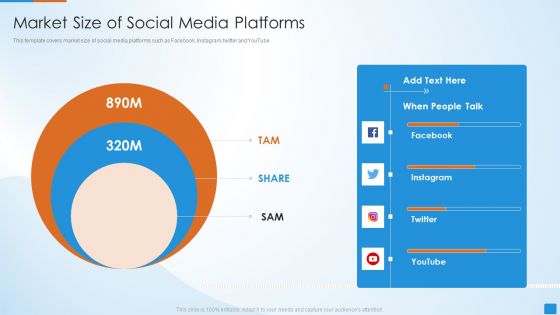
Social Network Strategy Pitch Deck Market Size Of Social Media Platforms Formats PDF
This template covers market size of social media platforms such as Facebook, Instagram, twitter and YouTube.This is a Social Network Strategy Pitch Deck Market Size Of Social Media Platforms Formats PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Market Size, Social Media Platforms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
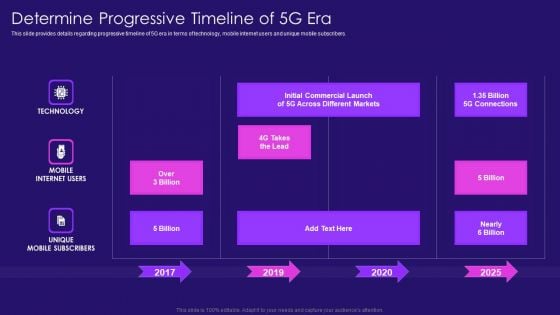
Determine Progressive Timeline Of 5G Era 5G Network Architecture Instructions Structure PDF
This slide provides details regarding progressive timeline of 5G era in terms of technology, mobile internet users and unique mobile subscribers. Deliver an awe inspiring pitch with this creative Determine Progressive Timeline Of 5G Era 5G Network Architecture Instructions Structure PDF bundle. Topics like Initial Commercial, Different Markets, Billion Connections can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Corporate Networking Relationship Management Purpose Of Business Relationship Management Icons PDF
This is a corporate networking relationship management purpose of business relationship management icons pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like create a useful and effective business relationship between the service provider and customers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































