Data Protection
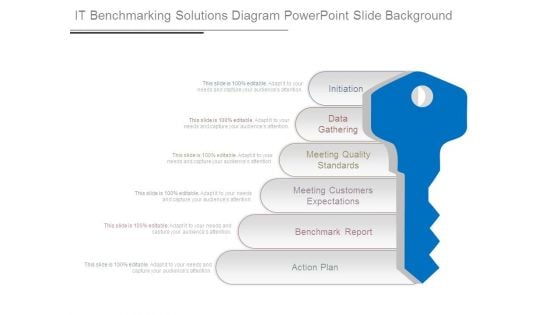
It Benchmarking Solutions Diagram Powerpoint Slide Background
This is a it benchmarking solutions diagram powerpoint slide background. This is a six stage process. The stages in this process are initiation, data gathering, meeting quality standards, meeting customers expectations, benchmark report, action plan.

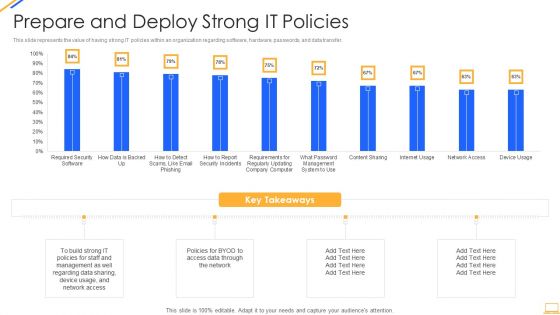
Information Security Prepare And Deploy Strong IT Policies Ppt Gallery Images PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative information security prepare and deploy strong it policies ppt gallery images pdf bundle. Topics like management, network, device, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Desktop Security Management Prepare And Deploy Strong It Policies Template PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this desktop security management prepare and deploy strong it policies template pdf. Use them to share invaluable insights on management, data, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Digital Archive Mouse PowerPoint Templates And PowerPoint Backgrounds 0311
Microsoft PowerPoint Template and Background with digital archived data symbol for databases Get the nod for your plans with our Digital Archive Mouse PowerPoint Templates And PowerPoint Backgrounds 0311. You will be at the top of your game.
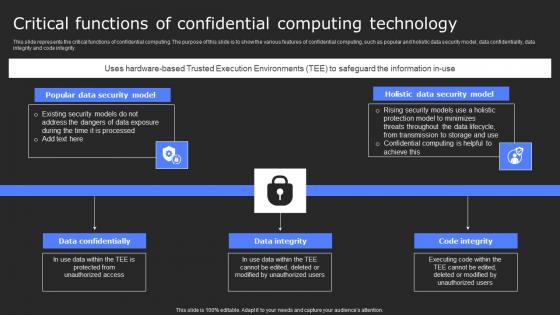
Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Are you searching for a Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf from Slidegeeks today. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.

Digital Files Security PowerPoint Template 1110
3d illustration of transparent binary and html data revolving around an open file folder Examine every deatail with our Digital Files Security PowerPoint Template 1110. Put each element to the test.
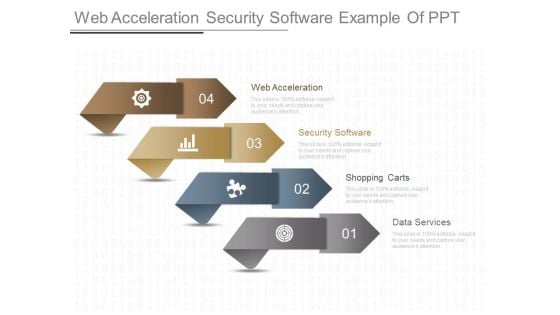
Web Acceleration Security Software Example Of Ppt
This is a web acceleration security software example of ppt. This is a four stage process. The stages in this process are web acceleration, security software, shopping carts, data services.
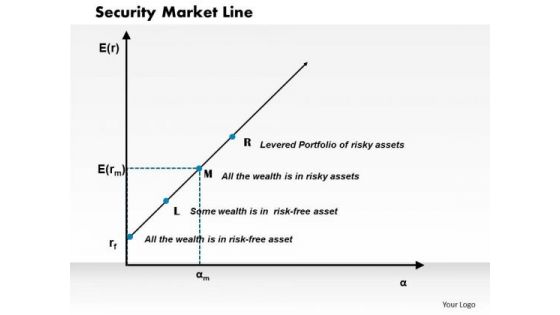
Business Framework Security Market Line PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.

Cloud Security Assessment Why Cloud Security Is Important Pictures PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Why Cloud Security Is Important Pictures PDF bundle. Topics like Centralized Security, Cost Effective, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
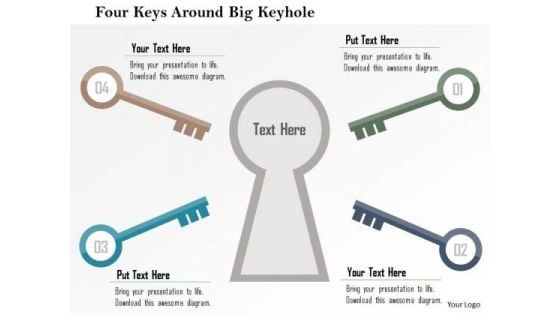
Business Diagram Four Keys Around Big Keyhole Presentation Template
Our above slide contains graphics of keys around big keyhole. It helps to exhibit finding possible solutions. Use this diagram to impart more clarity to data and to create more sound impact on viewers.
Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real-time reporting dashboards and google data studio reports.Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF. Use them to share invaluable insights on Demographics, Social Networks, Sessions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
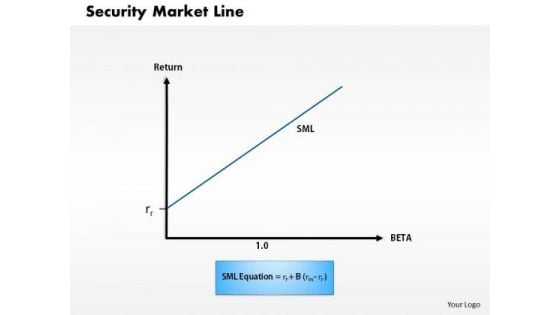
Business Framework Security Market Line 1 PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.
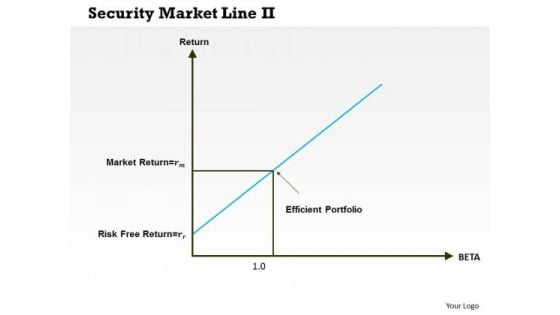
Business Framework Security Market Line 11 PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.
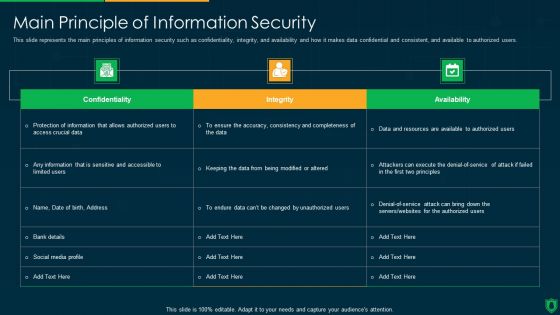
Info Security Main Principle Of Information Security Ppt PowerPoint Presentation File Background Designs PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an awe inspiring pitch with this creative info security main principle of information security ppt powerpoint presentation file background designs pdf bundle. Topics like integrity, confidentiality, availability, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
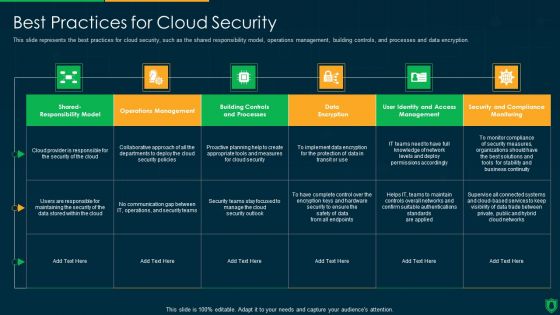
Info Security Best Practices For Cloud Security Ppt PowerPoint Presentation Gallery Visual Aids PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver and pitch your topic in the best possible manner with this info security best practices for cloud security ppt powerpoint presentation gallery visual aids pdf. Use them to share invaluable insights on communication gap, data encryption, operations management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

ESO System Center System Ppt PowerPoint Presentation File Portrait PDF
This slide covers enterprise security operation center system. It involves business security, data security, infrastructure, office network and application security. Showcasing this set of slides titled ESO System Center System Ppt PowerPoint Presentation File Portrait PDF. The topics addressed in these templates are Security Risks, Business Security, Data Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
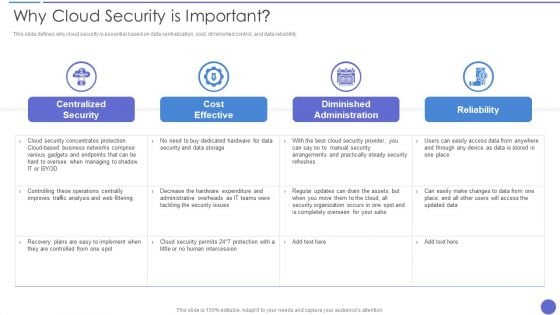
Why Cloud Security Is Important Demonstration PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. Deliver an awe inspiring pitch with this creative Why Cloud Security Is Important Demonstration PDF bundle. Topics like Cost Effective, Centralized Security, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf
The following slide showcases how cryptography assists in securing blockchain transactions and maintaining confidentiality. It includes elements such as data confidentiality, data integrity, digital signatures, consensus mechanism, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide showcases how cryptography assists in securing blockchain transactions and maintaining confidentiality. It includes elements such as data confidentiality, data integrity, digital signatures, consensus mechanism, etc.

Cloud Information Security Architecture Of Cloud Security Ppt Outline Graphics Design PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative Cloud Information Security Architecture Of Cloud Security Ppt Outline Graphics Design PDF bundle. Topics like Providers Responsibility, Application Security, Data Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
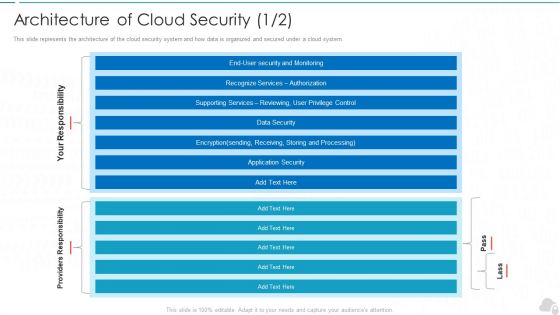
Architecture Of Cloud Security Authorization Cloud Computing Security IT Ppt Model Sample PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative architecture of cloud security authorization cloud computing security it ppt model sample pdf bundle. Topics like monitoring, security, authorization, services, data security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Why Cloud Security Is Important Cloud Computing Security IT Ppt Slides Graphics Template PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. Deliver and pitch your topic in the best possible manner with this why cloud security is important cloud computing security it ppt slides graphics template pdf. Use them to share invaluable insights on centralized security, cost effective, diminished administration, reliability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
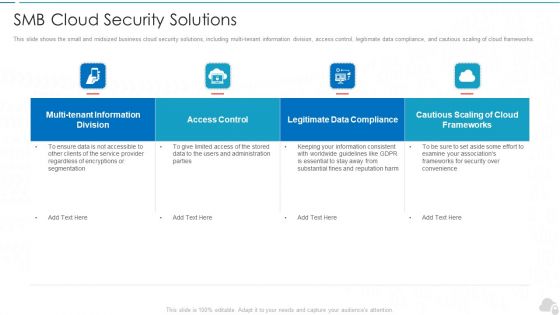
Smb Cloud Security Solutions Cloud Computing Security IT Ppt Portfolio Files PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. Deliver an awe inspiring pitch with this creative smb cloud security solutions cloud computing security it ppt portfolio files pdf bundle. Topics like access control, frameworks, legitimate data compliance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Offerings Information Technology Startup Go To Market Strategy GTM SS V
This slide presents the services offered by IT startup business. It includes services such as data analysis, business intelligence, cybersecurity and networking that help business clients to secure their data and take informed decisions.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Business Offerings Information Technology Startup Go To Market Strategy GTM SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide presents the services offered by IT startup business. It includes services such as data analysis, business intelligence, cybersecurity and networking that help business clients to secure their data and take informed decisions.
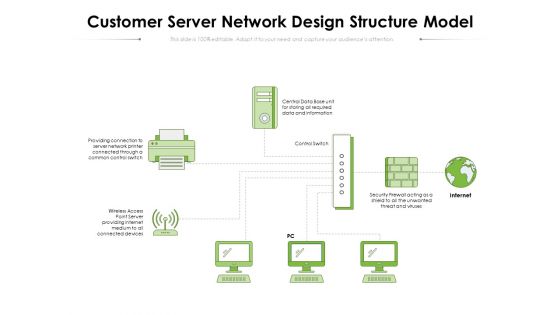
Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
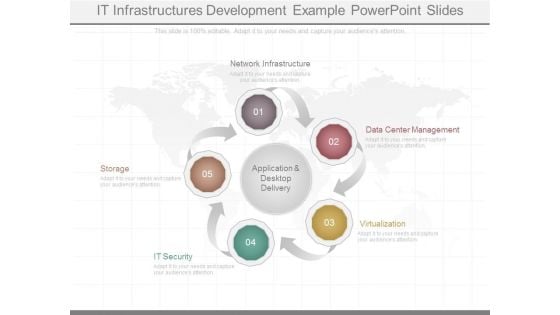
It Infrastructures Development Example Powerpoint Slides
This is a it infrastructures development example powerpoint slides. This is a five stage process. The stages in this process are application and desktop delivery, network infrastructure, data center management, storage, it security, virtualization.
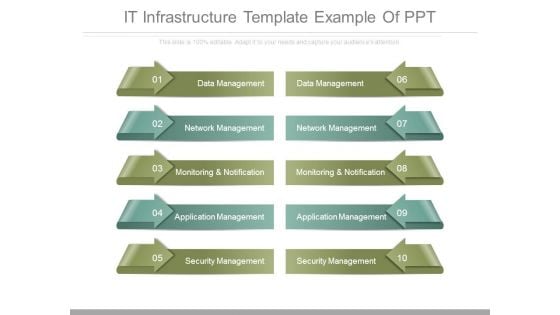
It Infrastructure Template Example Of Ppt
This is a it infrastructure template example of ppt. This is a ten stage process. The stages in this process are data management, network management, monitoring and notification, application management, security management.
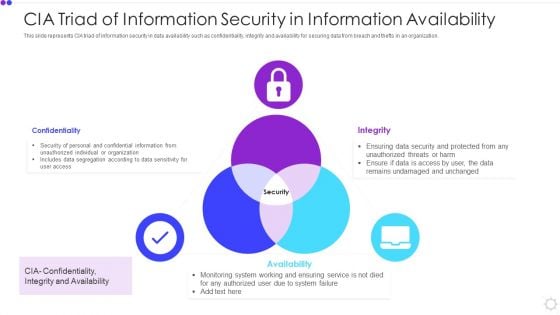
Cia Triad Of Information Security In Information Availability Microsoft PDF
This slide represents CIA triad of information security in data availability such as confidentiality, integrity and availability for securing data from breach and thefts in an organization. Presenting cia triad of information security in information availability microsoft pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including confidentiality, integrity, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
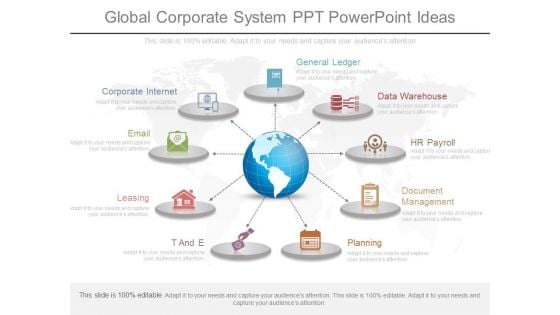
Global Corporate System Ppt Powerpoint Ideas
This is a global corporate system ppt powerpoint ideas. This is a nine stage process. The stages in this process are corporate internet, email, leasing, t and e, general ledger, data warehouse, hr payroll, document management, planning.
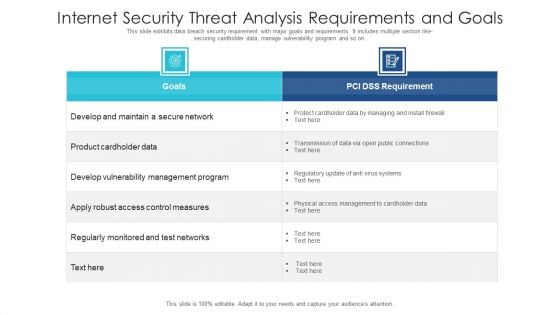
Internet Security Threat Analysis Requirements And Goals Ideas PDF
This slide exhibits data breach security requirement with major goals and requirements. It includes multiple section like- securing cardholder data, manage vulnerability program and so on. Showcasing this set of slides titled internet security threat analysis requirements and goals ideas pdf. The topics addressed in these templates are internet security threat analysis requirements and goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
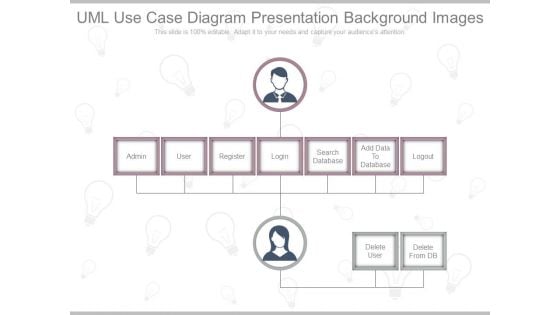
Uml Use Case Diagram Presentation Background Images
This is a uml use case diagram presentation background images. This is a seven stage process. The stages in this process are admin, user, register, login, search database, add data to database, logout.
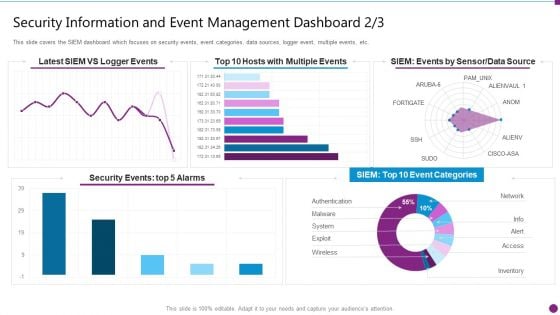
Security Information And Event Management Dashboard Events Ideas PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative security information and event management dashboard events ideas pdf bundle. Topics like security events, data source, event categories can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
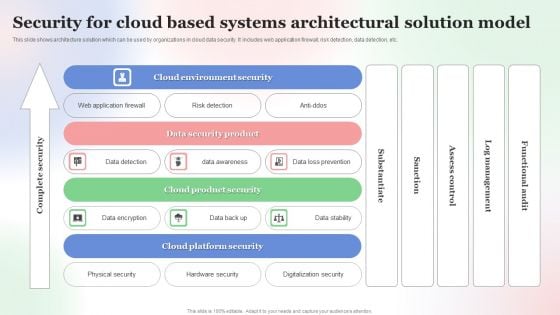
Security For Cloud Based Systems Architectural Solution Model Background PDF
This slide shows architecture solution which can be used by organizations in cloud data security. It includes web application firewall, risk detection, data detection, etc. Showcasing this set of slides titled Security For Cloud Based Systems Architectural Solution Model Background PDF. The topics addressed in these templates are Security For Cloud Based, Systems Architectural Solution Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
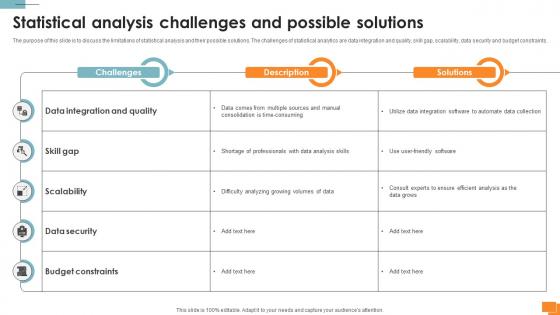
Statistical Tools For Evidence Statistical Analysis Challenges And Possible Solutions
The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints. Take your projects to the next level with our ultimate collection of Statistical Tools For Evidence Statistical Analysis Challenges And Possible Solutions. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The purpose of this slide is to discuss the limitations of statistical analysis and their possible solutions. The challenges of statistical analytics are data integration and quality, skill gap, scalability, data security and budget constraints.
Key Security Considerations For 5G For Threat Handling Icons PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling Icons PDF. Use them to share invaluable insights on Denial Of Service, Information Interception, Application Plane Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
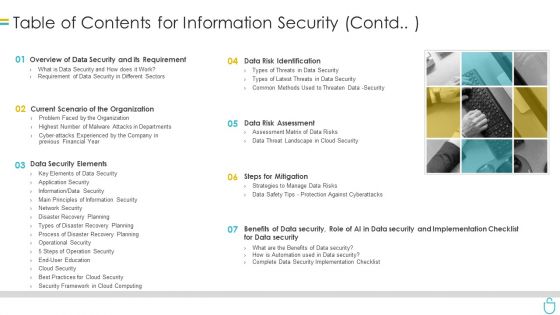
Table Of Contents For Information Security Contd Ppt Show Topics PDF
This is a table of contents for information security contd ppt show topics pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, requirement, data security, data risk assessment, steps for mitigation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
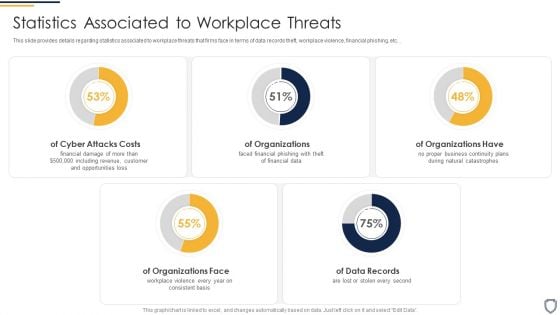
Corporate Security And Risk Management Statistics Associated To Workplace Threats Template PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. . Deliver an awe inspiring pitch with this creative corporate security and risk management statistics associated to workplace threats template pdf bundle. Topics like cyber attacks costs, organizations, organizations have, organizations face, data records can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Deliver an awe inspiring pitch with this creative Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF bundle. Topics like Servers Outside, Encrypted Secure, Outside Firewall can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
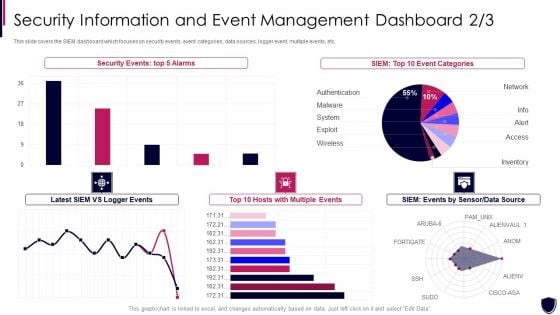
Enhancing Cyber Safety With Vulnerability Administration Security Information And Event Formats PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration security information and event formats pdf bundle. Topics like security events, event categories, data source, multiple events can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
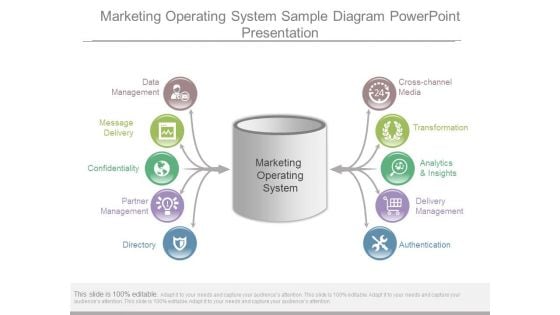
Marketing Operating System Sample Diagram Powerpoint Presentation
This is a marketing operating system sample diagram powerpoint presentation. This is a five stage process. The stages in this process are data management, message delivery, confidentiality, partner management, directory, cross channel media, transformation, analytics and insights, delivery management, authentication.
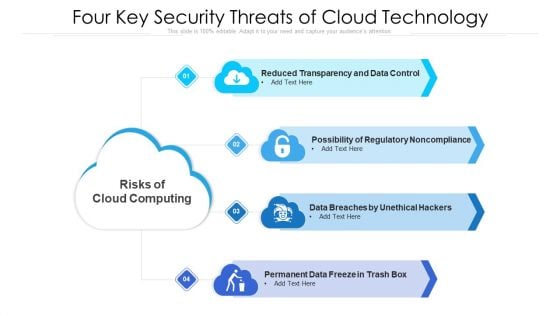
Four Key Security Threats Of Cloud Technology Ppt PowerPoint Presentation Gallery Introduction PDF
Presenting four key security threats of cloud technology ppt powerpoint presentation gallery introduction pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data breaches by unethical hackers, permanent data freeze in trash box, possibility of regulatory noncompliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
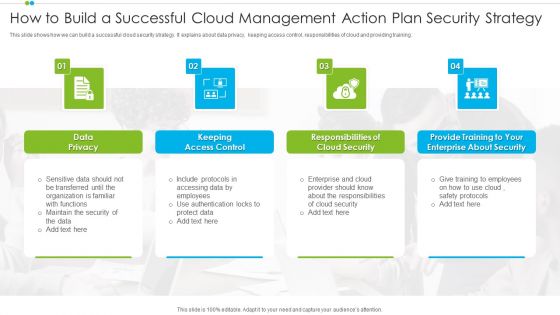
How To Build A Successful Cloud Management Action Plan Security Strategy Sample PDF
This slide shows how we can build a successful cloud security strategy. It explains about data privacy, keeping access control, responsibilities of cloud and providing training.Presenting How To Build A Successful Cloud Management Action Plan Security Strategy Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security, Enterprise, Data Privacy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
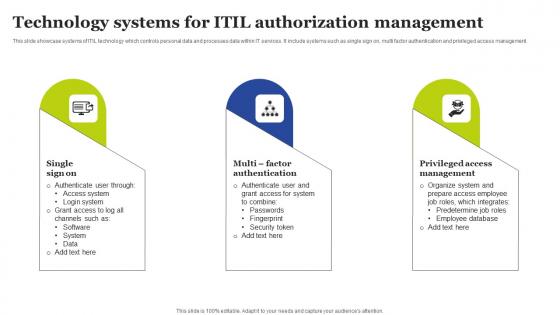
Technology Systems For ITIL Authorization Management Rules Pdf
This slide showcase systems of ITIL technology which controls personal data and processes data within IT services. It include systems such as single sign on, multi factor authentication and privileged access management. Pitch your topic with ease and precision using this Technology Systems For ITIL Authorization Management Rules Pdf This layout presents information on Single Sign, Multi Factor Authentication, Privileged Access Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcase systems of ITIL technology which controls personal data and processes data within IT services. It include systems such as single sign on, multi factor authentication and privileged access management.
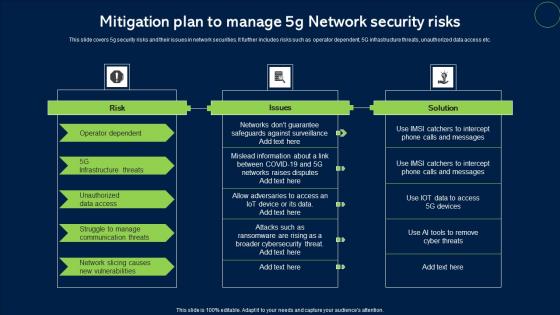
Mitigation Plan To Manage 5G Network Security Risks Microsoft Pdf
This slide covers 5g security risks and their issues in network securities. It further includes risks such as operator dependent, 5G infrastructure threats, unauthorized data access etc. Showcasing this set of slides titled Mitigation Plan To Manage 5G Network Security Risks Microsoft Pdf. The topics addressed in these templates are Risk, Issues, Solution. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide covers 5g security risks and their issues in network securities. It further includes risks such as operator dependent, 5G infrastructure threats, unauthorized data access etc.
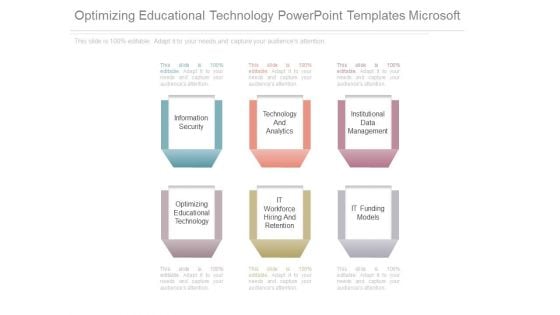
Optimizing Educational Technology Powerpoint Templates Microsoft
This is a optimizing educational technology powerpoint templates microsoft. This is a six stage process. The stages in this process are information security, technology and analytics, institutional data management, optimizing educational technology, it workforce hiring and retention, it funding models.
Integrated Technology Solutions Diagram Powerpoint Shapes
This is a integrated technology solutions diagram powerpoint shapes. This is a three stage process. The stages in this process are cross browser user interface library, optimized application object library, secure datastore for data and document.
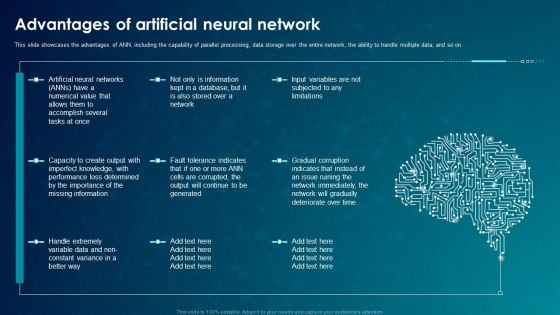
ANN System Advantages Of Artificial Neural Network Demonstration PDF
This slide showcases the advantages of ANN, including the capability of parallel processing, data storage over the entire network, the ability to handle multiple data, and so on. Deliver an awe inspiring pitch with this creative ANN System Advantages Of Artificial Neural Network Demonstration PDF bundle. Topics like Information, Database can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
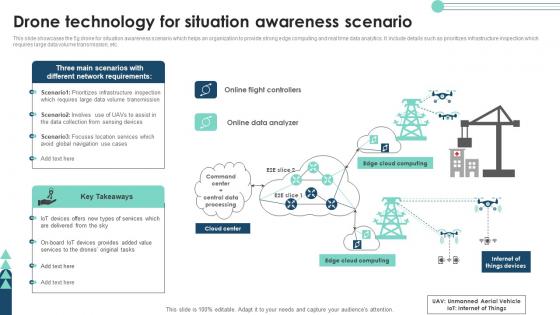
Drone Technology For Situation Awareness Scenario Clipart Pdf
This slide showcases the 5g drone for situation awareness scenario which helps an organization to provide strong edge computing and real time data analytics. It include details such as prioritizes infrastructure inspection which requires large data volume transmission, etc. Pitch your topic with ease and precision using this Drone Technology For Situation Awareness Scenario Clipart Pdf This layout presents information on Network Requirements, Key Takeaways, Drone Technology It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the 5g drone for situation awareness scenario which helps an organization to provide strong edge computing and real time data analytics. It include details such as prioritizes infrastructure inspection which requires large data volume transmission, etc.
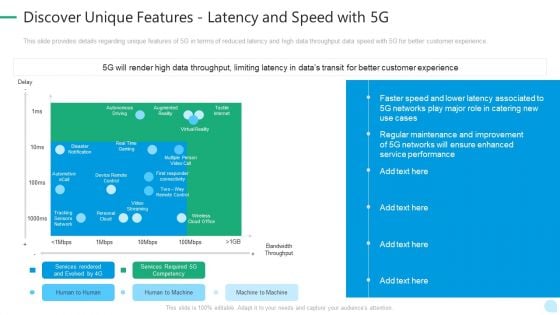
5G Network Technology Discover Unique Features Latency And Speed With 5G Ppt Portfolio Designs PDF
This slide provides details regarding unique features of 5G in terms of reduced latency and high data throughput data speed with 5G for better customer experience. Deliver an awe inspiring pitch with this creative 5g network technology discover unique features latency and speed with 5g ppt portfolio designs pdf bundle. Topics like service, performance, improvement, maintenance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
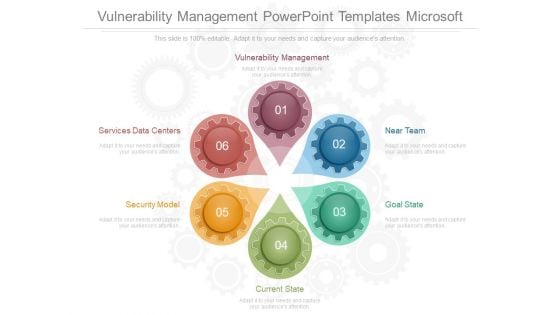
Vulnerability Management Powerpoint Templates Microsoft

Database Platform Powerpoint Slides Themes
This is a database platform powerpoint slides themes. This is a four stage process. The stages in this process are database platform, data warehouse platform, security and identity, development.
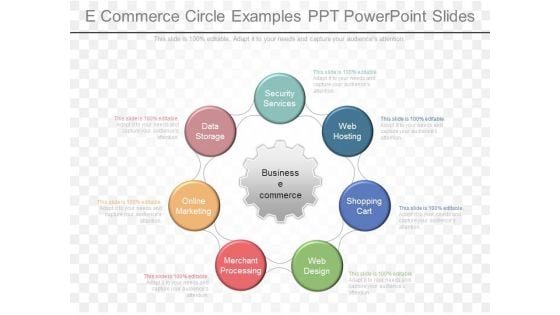
E Commerce Circle Examples Ppt Powerpoint Slides
This is a e commerce circle examples ppt powerpoint slides. This is a seven stage process. The stages in this process are business e commerce, security services, web hosting, shopping cart, web design, merchant processing, online marketing, data storage.
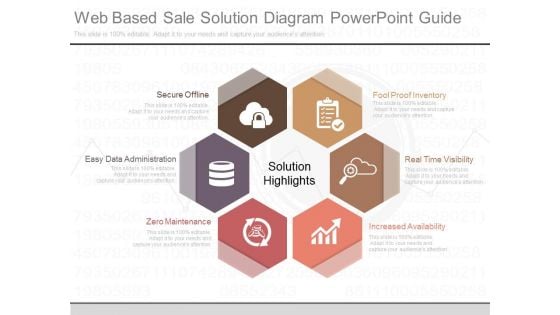
Web Based Sale Solution Diagram Powerpoint Guide
This is a web based sale solution diagram powerpoint guide. This is a six stage process. The stages in this process are fool proof inventory, real time visibility, increased availability, zero maintenance, easy data administration, secure offline.

Example Of Asset Lifecycle Management Ppt Powerpoint Layout
This is a example of asset lifecycle management ppt powerpoint layout. This is a three stage process. The stages in this process are corporate sustainability data security, market procurement insight, upgrade, planned unplanned change, disposition, acquisition.
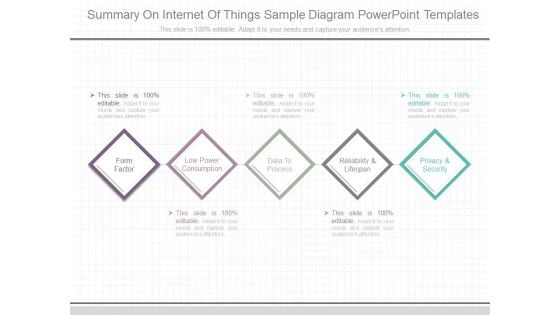
Summary On Internet Of Things Sample Diagram Powerpoint Templates
This is a summary on internet of things sample diagram powerpoint templates. This is a five stage process. The stages in this process are form factor, low power consumption, data to process, reliability and lifespan, privacy and security.
Seo Based Ecommerce Model For Marketing Ppt Presentation Design
This is a seo based ecommerce model for marketing ppt presentation design. This is a seven stage process. The stages in this process are security service, web hosting, shopping cart, web design, merchant processing, online marketing, data storage.
Architect Design And Solutions Diagram Powerpoint Slides
This is a architect design and solutions diagram powerpoint slides. This is a six stage process. The stages in this process are data safety, efficiently, speed, reliability, convenience, security.

Service Quality Management System Diagram Sample File
This is a service quality management system diagram sample file. This is a four stage process. The stages in this process are forma quality, linguistic quality, data security, short reaction time.
Enterprise Architecture Strategy Ppt Powerpoint Slides Designs
This is a enterprise architecture strategy ppt powerpoint slides designs. This is a six stage process. The stages in this process are business view, business layer, data layer, security layer, business architecture, process layer.
B2b Integration Examples Diagram Powerpoint Slide Themes
This is a b2b integration examples diagram powerpoint slide themes. This is a four stage process. The stages in this process are data integration, process modeling and design, governance and security, managed file transfer.

Wan Optimization Template Powerpoint Slides Rules
This is a wan optimization template powerpoint slides rules. This is a five stage process. The stages in this process are data center, remote office, application visibility, wan security, central management.


 Continue with Email
Continue with Email

 Home
Home


































