Data Protection
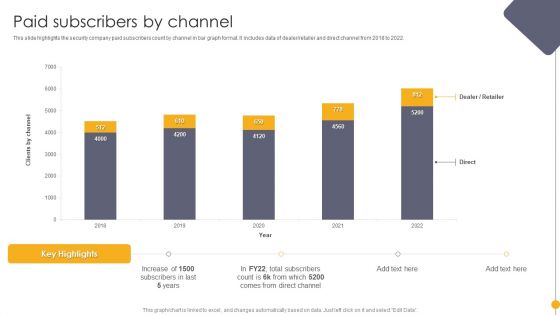
Portable Home Safety Systems Company Profile Paid Subscribers By Channel Demonstration PDF
This slide highlights the security company paid subscribers count by channel in bar graph format. It includes data of dealer or retailer and direct channel from 2018 to 2022. Deliver an awe inspiring pitch with this creative Portable Home Safety Systems Company Profile Paid Subscribers By Channel Demonstration PDF bundle. Topics like Total Subscribers, Dealer, Retailer, Direct, 2018 To 2022 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
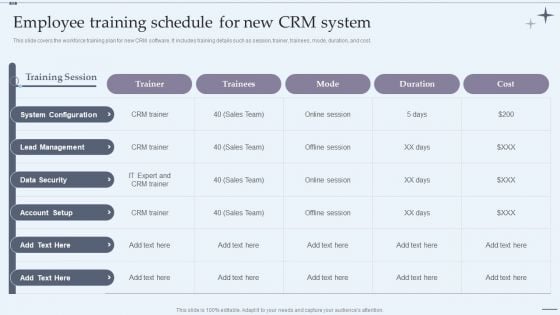
CRM System Implementation Stages Employee Training Schedule For New CRM System Mockup PDF
This slide covers the workforce training plan for new CRM software. It includes training details such as session, trainer, trainees, mode, duration, and cost. Deliver an awe inspiring pitch with this creative CRM System Implementation Stages Employee Training Schedule For New CRM System Mockup PDF bundle. Topics like System Configuration, Lead Management, Data Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
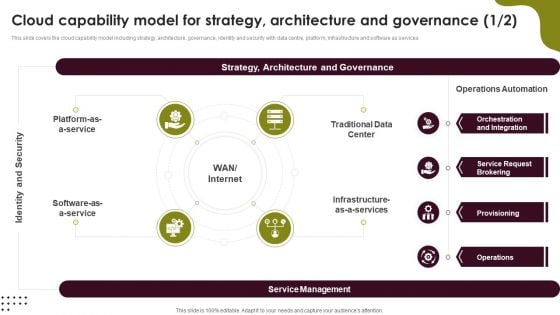
Cloud Computing Scalability Cloud Capability Model For Strategy Architecture Template PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services. There are so many reasons you need a Cloud Computing Scalability Cloud Capability Model For Strategy Architecture Template PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
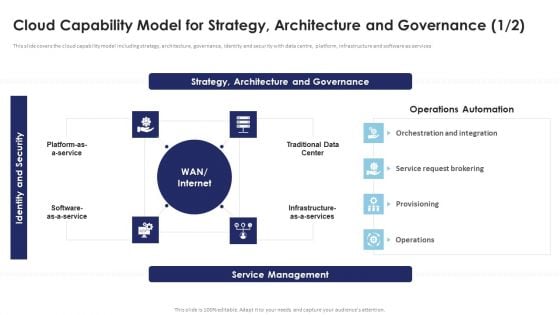
Multi Cloud Infrastructure Management Cloud Capability Model For Strategy Architecture Pictures PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services. There are so many reasons you need a Multi Cloud Infrastructure Management Cloud Capability Model For Strategy Architecture Pictures PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
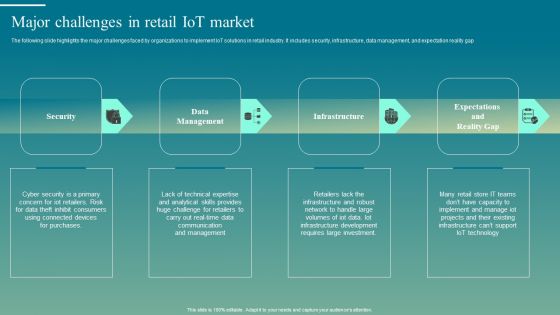
Deploying Iot Solutions In The Retail Market Major Challenges In Retail Iot Market Diagrams PDF
The following slide highlights the major challenges faced by organizations to implement IoT solutions in retail industry. It includes security, infrastructure, data management, and expectation reality gap. There are so many reasons you need a Deploying Iot Solutions In The Retail Market Major Challenges In Retail Iot Market Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
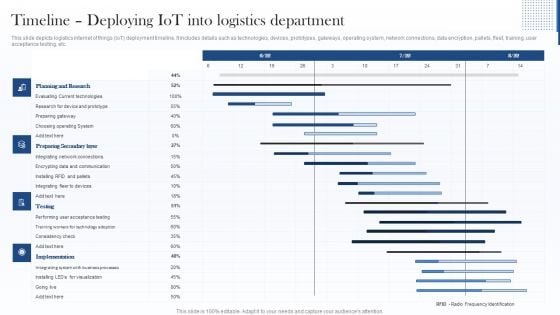
Timeline Deploying Iot Into Logistics Department Introduction PDF
This slide depicts logistics internet of things IoT deployment timeline. It includes details such as technologies, devices, prototypes, gateways, operating system, network connections, data encryption, pallets, fleet, training, user acceptance testing, etc. Deliver an awe inspiring pitch with this creative Timeline Deploying Iot Into Logistics Department Introduction PDF bundle. Topics like Preparing Secondary Layer, Planning And Research, Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Timeline Deploying Iot Into Logistics Department Clipart PDF
This slide depicts logistics internet of things IoT deployment timeline. It includes details such as technologies, devices, prototypes, gateways, operating system, network connections, data encryption, pallets, fleet, training, user acceptance testing, etc. Deliver an awe inspiring pitch with this creative Timeline Deploying Iot Into Logistics Department Clipart PDF bundle. Topics like Planning And Research, Preparing Secondary Layer, Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
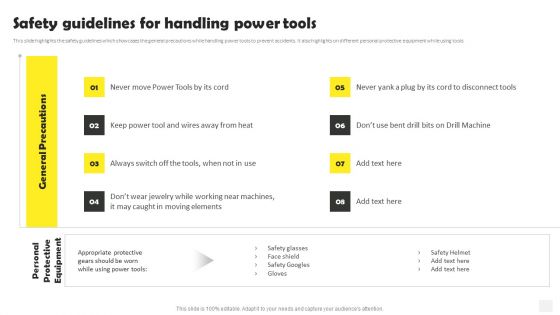
Occupational Health And Safety At Workplace Safety Guidelines For Handling Power Tools Themes PDF
This slide highlights the safety guidelines which showcases the general precautions while handling power tools to prevent accidents. It also highlights on different personal protective equipment while using tools. The Occupational Health And Safety At Workplace Safety Guidelines For Handling Power Tools Themes PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Load Balancing IT Weighted Load Balancing Vs Round Robin Graphics PDF
This slide represents a comparison between weighted load balancing and round-robin load balancing and how weight is distributed in both approaches. Deliver an awe inspiring pitch with this creative load balancing it weighted load balancing vs round robin graphics pdf bundle. Topics like servers, networks, method, plan data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
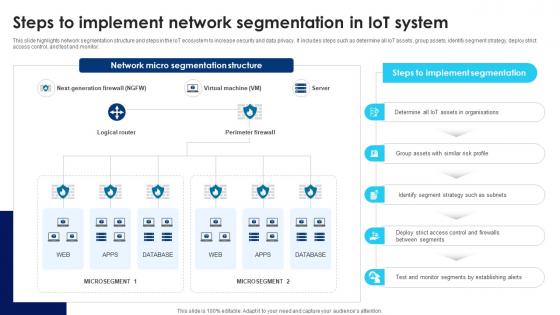
Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V
This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor. Slidegeeks is here to make your presentations a breeze with Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor.
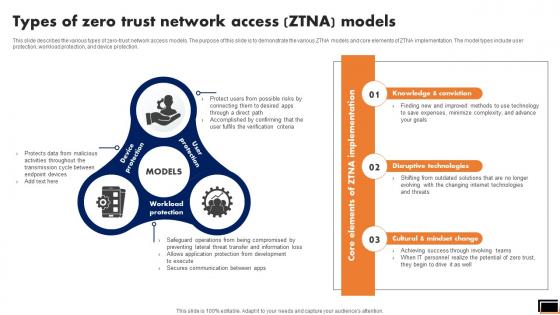
Types Of Zero Trust Network Access Ztna Models Software Defined Perimeter SDP
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Make sure to capture your audiences attention in your business displays with our gratis customizable Types Of Zero Trust Network Access Ztna Models Software Defined Perimeter SDP. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.
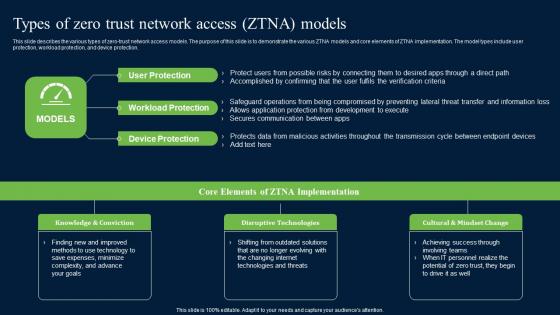
Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Boost your pitch with our creative Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.
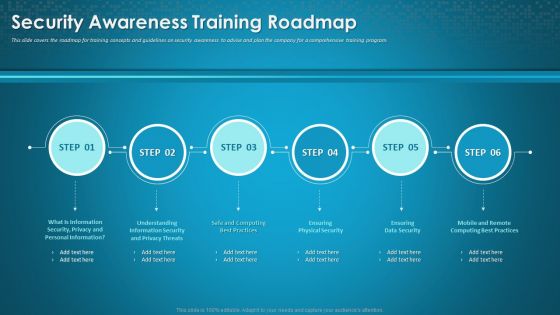
Organizational Network Staff Learning Security Awareness Training Roadmap Sample PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. Presenting organizational network staff learning security awareness training roadmap sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like ensuring data security, information security and privacy threats, ensuring physical security. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V
This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc.

Sample Of Information Filtering Template Presentation Examples
This is a sample of information filtering template presentation examples. This is a five stage process. The stages in this process are coverage, protection, intelligence, reliability, performance.
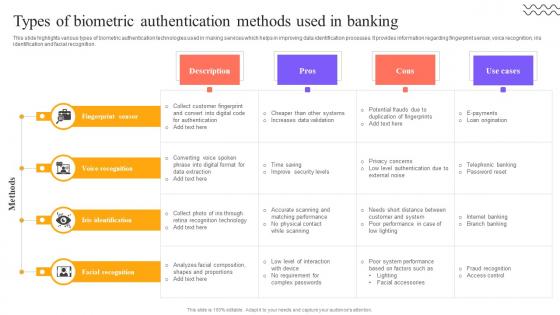
Digital Approach To Client Types Of Biometric Authentication Methods Used In Banking
This slide highlights various types of biometric authentication technologies used in making services which helps in improving data identification processes. It provides information regarding fingerprint sensor, voice recognition, iris identification and facial recognition. Presenting this PowerPoint presentation, titled Digital Approach To Client Types Of Biometric Authentication Methods Used In Banking, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Digital Approach To Client Types Of Biometric Authentication Methods Used In Banking. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Digital Approach To Client Types Of Biometric Authentication Methods Used In Banking that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide highlights various types of biometric authentication technologies used in making services which helps in improving data identification processes. It provides information regarding fingerprint sensor, voice recognition, iris identification and facial recognition.
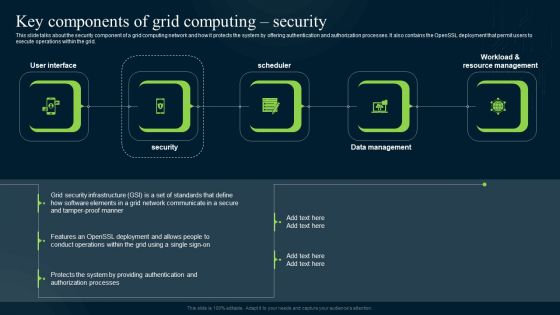
Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Explore a selection of the finest Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Environmental Marketing Creating Customer Convenience Through Sustainable Means Information PDF
This slide highlights that a company can create convenience for customers along with protecting the environment by making small changes in product designs, packaging, disposable methods etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Environmental Marketing Creating Customer Convenience Through Sustainable Means Information PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
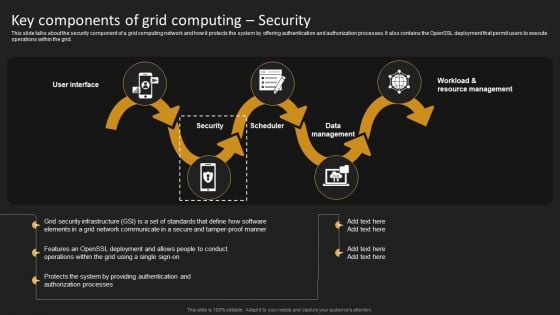
Key Components Of Grid Computing Security Structure PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Key Components Of Grid Computing Security Structure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
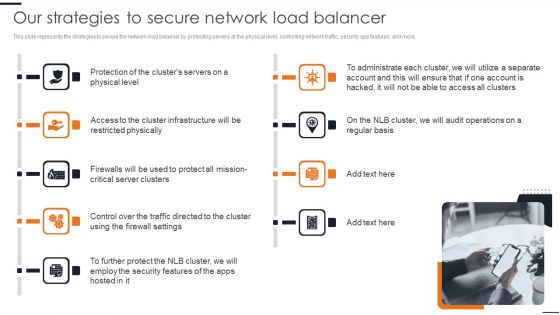
Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF
This slide represents the strategies to secure the network load balancer by protecting servers at the physical level, controlling network traffic, security app features, and more. This modern and well arranged Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012
Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012-The euro is the currency used by the Institutions of the European Union and is the official currency of the Eurozone. This Template shows the currency Euro under the Umbrella which signifies the increasing rate of Euro from 2010 to 2012. Stable ideas are the building blocks of a successful structure. Lay down the fundamentals to build upon. Take it up to a higher level with your thoughts. -Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Currency protected by umbrella, security, business, money, shapes, metaphor Start accelerating revenue growth with our Currency Umbrella Security PowerPoint Templates And PowerPoint Themes 1012. They will make you look good.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

SDN Security Architecture Comparison Between Software Defined Networking And SD WAN Structure PDF
This slide depicts the comparison between software defined networking and an SD WAN, which is an internet traffic distribution system that uses SDN ideas to dynamically find the most efficient path for traffic to and from branch locations and data center sites across WANs. Make sure to capture your audiences attention in your business displays with our gratis customizable SDN Security Architecture Comparison Between Software Defined Networking And SD WAN Structure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Comparative Analysis Of Digital Security Metrics For Small Businesses Icons Pdf
Pitch your topic with ease and precision using this Comparative Analysis Of Digital Security Metrics For Small Businesses Icons Pdf This layout presents information on Futuristic Approach, Data Driven Decisions, Exposed Assets It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the comparative analysis of cybersecurity KPIs for small businesses which helps an organization to carefully choose, select the best metric to track performance. It include details such as goal oriented, actionable, easy to understand, etc.

Implementing Packing Procedures In Warehouse Logistics Summary PDF
This slide presents steps for establishing packing procedures in warehouse logistics. It includes steps such as, selecting appropriate packing material, protective material, arranging items, labeling, weighing and moving. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Packing Procedures In Warehouse Logistics Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Packing Procedures In Warehouse Logistics Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
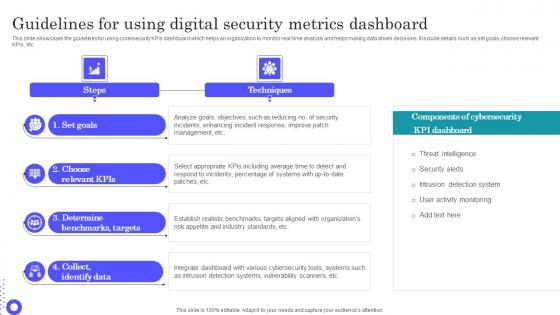
Guidelines For Using Digital Security Metrics Dashboard Introduction Pdf
Pitch your topic with ease and precision using this Guidelines For Using Digital Security Metrics Dashboard Introduction Pdf This layout presents information on Benchmarks Targets, Integrate Dashboard, Incidents Enhancing It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the guidelines for using cybersecurity KPIs dashboard which helps an organization to monitor real time analysis and helps making data driven decisions. It include details such as set goals, choose relevant KPIs, etc.

Integrating Naas Service Model Naas As An Enabler For Cloud Transformation Ppt Gallery Graphics Pictures PDF
This slide talks about how NaaS works as a key driver for cloud transformation by providing secure and protected connectivity between businesses and their customers, internet of things devices with corporate applications, and so on. Retrieve professionally designed Integrating Naas Service Model Naas As An Enabler For Cloud Transformation Ppt Gallery Graphics Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
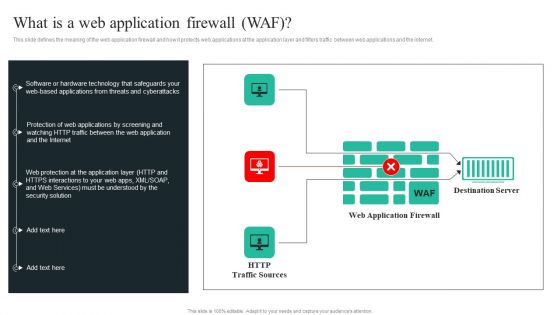
WAF Introduction What Is A Web Application Firewall WAF Background PDF
This slide defines the meaning of the web application firewall and how it protects web applications at the application layer and filters traffic between web applications and the internet. ThisWAF Introduction What Is A Web Application Firewall WAF Background PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Workplace Safety Best Practices Safety Guidelines For Handling Power Tools Ideas PDF
This slide highlights the safety guidelines which showcases the general precautions while handling power tools to prevent accidents. It also highlights on different personal protective equipment while using tools. Are you searching for a Workplace Safety Best Practices Safety Guidelines For Handling Power Tools Ideas PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Workplace Safety Best Practices Safety Guidelines For Handling Power Tools Ideas PDF from Slidegeeks today.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
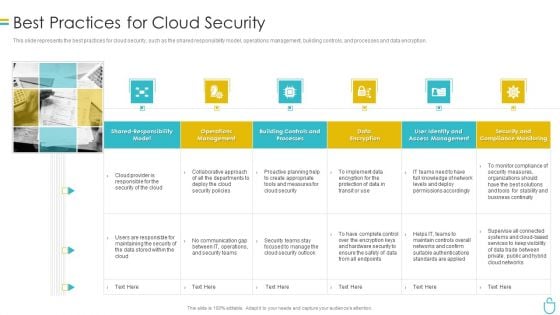
Information Security Best Practices For Cloud Security Ppt Ideas Deck PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting information security best practices for cloud security ppt ideas deck pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, measures, planning, teams, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
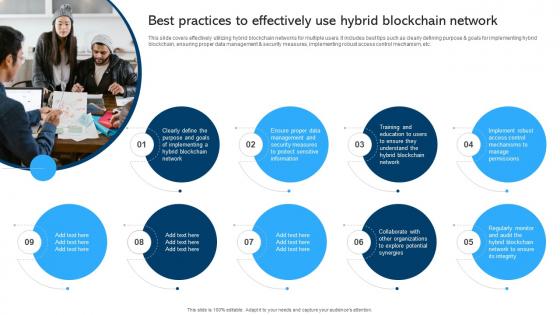
Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V
This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc. Welcome to our selection of the Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc.
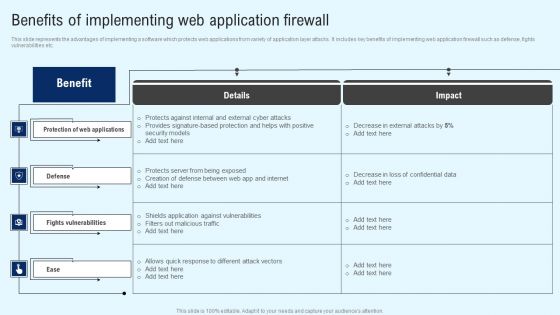
Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
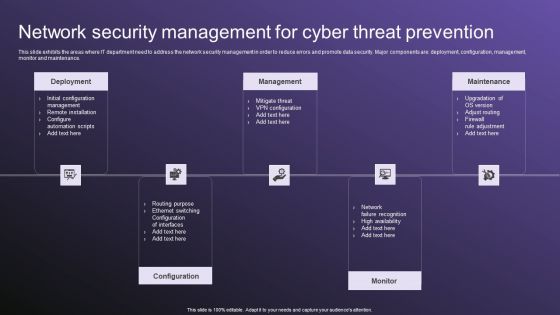
Network Security Management For Cyber Threat Prevention Demonstration PDF
This slide exhibits the areas where IT department need to address the network security management in order to reduce errors and promote data security. Major components are deployment, configuration, management, monitor and maintenance. Presenting Network Security Management For Cyber Threat Prevention Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Deployment, Management, Configuration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
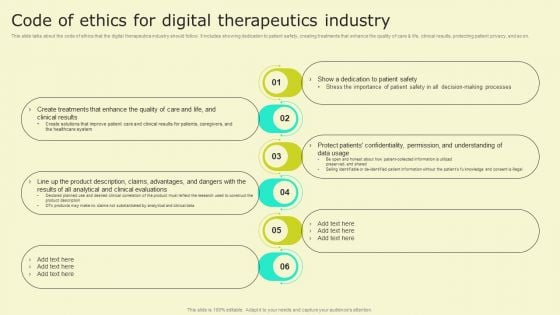
Digital Health Interventions Code Of Ethics For Digital Therapeutics Industry Background PDF
This slide talks about the code of ethics that the digital therapeutics industry should follow. It includes showing dedication to patient safety, creating treatments that enhance the quality of care and life, clinical results, protecting patient privacy, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Digital Health Interventions Code Of Ethics For Digital Therapeutics Industry Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Digital Health Interventions Code Of Ethics For Digital Therapeutics Industry Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cloud Network Security Threats And Solutions Infographics PDF
The slide showcases threats occurred due to data flowing between cloud service providers and organizations with their solutions. It includes lack of cloud security architecture and tactics, account hijacking , weak control plane , inadequate of identity, credentials, etc. Presenting Cloud Network Security Threats And Solutions Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats, Description, Solutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Distributed Ledger Security Protocol List Icon Structure Pdf
Pitch your topic with ease and precision using this Distributed Ledger Security Protocol List Icon Structure Pdf This layout presents information on Data Transfer Security, Distributed Ledger, Technology Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Distributed Ledger Security Protocol List Icon Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Measuring Instruments Ppt 6
Measuring Instruments PPT 6-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!-These PowerPoint slides can be used for themes relating to--Ampule, background, bandage, blister, blue, capsule, care, chrome, clamp, close-up, collection, emergency, equipment, forceps, glass, green, health, healthcare, healthcare and medicine, hospital, illness, instrument, mask, medical, medical instrument, medical supplies, medicament, medicine, metal, metallic, nobody, object, operation, pharmacy, pill, pincers, preparats, protective mask, rescue, scissors, stainless, steel, surgery, surgical, tablets, taking medicine, tool, tweezers, white, yellow Oversee plans with our Measuring Instruments Ppt 6. Download without worries with our money back guaranteee.
Microscope Research Medical PowerPoint Templates
Microscope Research Medical PowerPoint templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!-These PowerPoint slides can be used for themes relating to--Ampule, background, bandage, blister, blue, capsule, care, chrome, clamp, close-up, collection, emergency, equipment, forceps, glass, green, health, healthcare, healthcare and medicine, hospital, illness, instrument, mask, medical, medical instrument, medical supplies, medicament, medicine, metal, metallic, nobody, object, operation, pharmacy, pill, pincers, preparats, protective mask, rescue, scissors, stainless, steel, surgery, surgical, tablets, taking medicine, tool, tweezers, white, yellow Present like a film makerwith our Microscope Research Medical PowerPoint Templates. You'll deliver your best presentation yet.
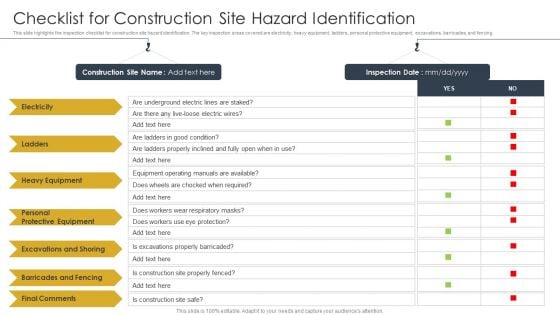
Checklist For Construction Site Hazard Identification Construction Site Safety Plan Structure PDF
This slide highlights the inspection checklist for construction site hazard identification. The key inspection areas covered are electricity, heavy equipment, ladders, personal protective equipment, excavations, barricades, and fencing. If you are looking for a format to display your unique thoughts, then the professionally designed Checklist For Construction Site Hazard Identification Construction Site Safety Plan Structure PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Checklist For Construction Site Hazard Identification Construction Site Safety Plan Structure PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
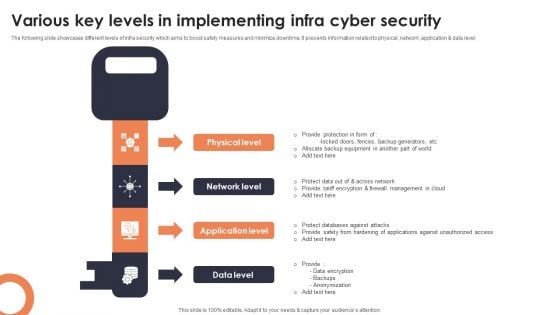
Various Key Levels In Implementing Infra Cyber Security Mockup PDF
The following slide showcases different levels of infra security which aims to boost safety measures and minimize downtime. It presents information related to physical, network, application and data level. Presenting Various Key Levels In Implementing Infra Cyber Security Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Physical Level, Network Level, Application Level. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Integrating Naas Service Model To Enhance Naas As An Enabler For Cloud Transformation Elements PDF
This slide talks about how naas works as a key driver for cloud transformation by providing secure and protected connectivity between businesses and their customers, internet of things devices with corporate applications, and soon. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Integrating Naas Service Model To Enhance Naas As An Enabler For Cloud Transformation Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything intoIntegrating Naas Service Model To Enhance Naas As An Enabler For Cloud Transformation Elements PDF.
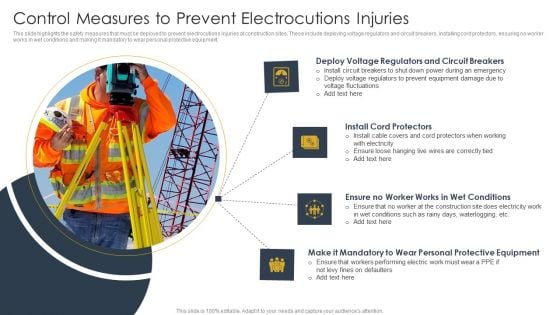
Control Measures To Prevent Electrocutions Injuries Construction Site Safety Plan Clipart PDF
This slide highlights the safety measures that must be deployed to prevent electrocutions injuries at construction sites. These include deploying voltage regulators and circuit breakers, installing cord protectors, ensuring no worker works in wet conditions and making it mandatory to wear personal protective equipment. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Control Measures To Prevent Electrocutions Injuries Construction Site Safety Plan Clipart PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Control Measures To Prevent Electrocutions Injuries Construction Site Safety Plan Clipart PDF
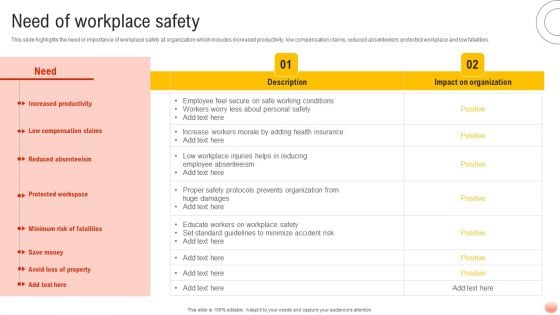
Best Practices For Occupational Health And Safety Need Of Workplace Safety Ideas PDF
This slide highlights the need or importance of workplace safety at organization which includes increased productivity, low compensation claims, reduced absenteeism, protected workplace and low fatalities. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Best Practices For Occupational Health And Safety Need Of Workplace Safety Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Best Practices For Occupational Health And Safety Need Of Workplace Safety Ideas PDF.

Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF. Use them to share invaluable insights on Nodes Authentication, Rule Consistency, Policy Enforcement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Checklist Access Control Rules PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Presenting Cloud Security Checklist Access Control Rules PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security, Systems, Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
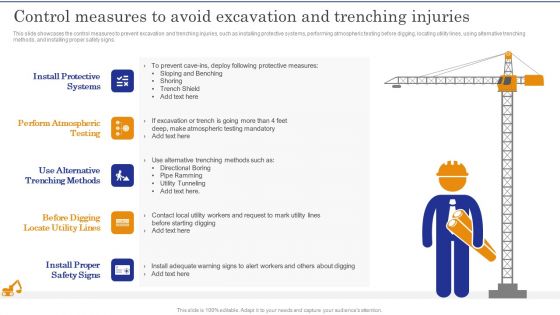
Construction Site Safety Measure Control Measures To Avoid Excavation And Trenching Injuries Mockup PDF
This slide showcases the control measures to prevent excavation and trenching injuries, such as installing protective systems, performing atmospheric testing before digging, locating utility lines, using alternative trenching methods, and installing proper safety signs.Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Construction Site Safety Measure Control Measures To Avoid Excavation And Trenching Injuries Mockup PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
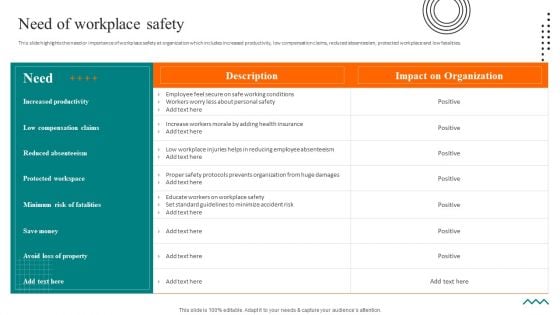
Workplace Safety Best Practices Need Of Workplace Safety Ideas PDF
This slide highlights the need or importance of workplace safety at organization which includes increased productivity, low compensation claims, reduced absenteeism, protected workplace and low fatalities. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Workplace Safety Best Practices Need Of Workplace Safety Ideas PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
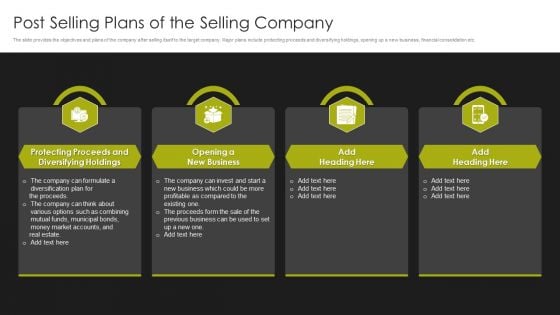
Selling Strategy And Operational Plan Post Selling Plans Of The Selling Company Ppt Professional Graphics Tutorials PDF
The slide provides the objectives and plans of the company after selling itself to the target company. Major plans include protecting proceeds and diversifying holdings, opening up a new business, financial consolidation etc. This Selling Strategy And Operational Plan Post Selling Plans Of The Selling Company Ppt Professional Graphics Tutorials PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Safety Signs To Prevent Incidences At Construction Sites Ppt PowerPoint Presentation Diagram PDF
The following slide showcases the safety signals which are important to inform workers and about the potential dangers at the construction sites. These signals shows warning for demolition work, overhead loads, Protective footwear, Danger demolition work, unauthorized personnelhard hat areas etc. Slidegeeks is here to make your presentations a breeze with Safety Signs To Prevent Incidences At Construction Sites Ppt PowerPoint Presentation Diagram PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
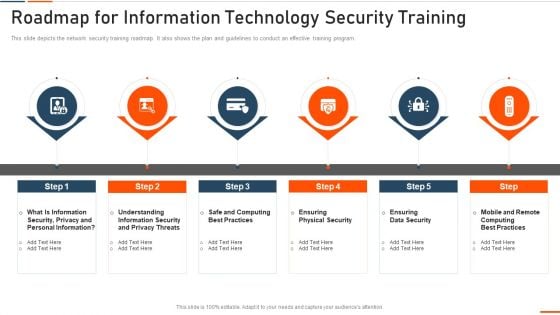
Roadmap For Information Technology Security Training Ppt Ideas Influencers PDF
This slide depicts the network security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a roadmap for roadmap for information technology security training ppt ideas influencers pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like rmation security, computing best practices, physical security, data security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
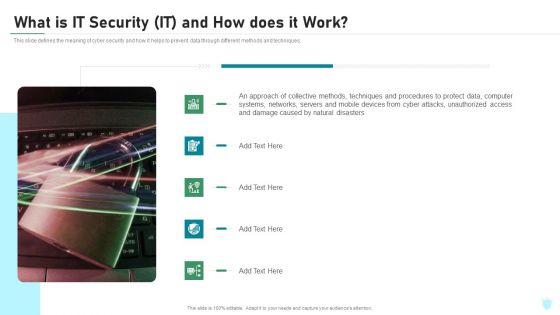
What Is IT Security IT And How Does IT Work Ppt Slides Gridlines PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. This is a what is it security it and how does it work ppt slides gridlines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like techniques, computer systems, networks, servers, mobile devices, cyber attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
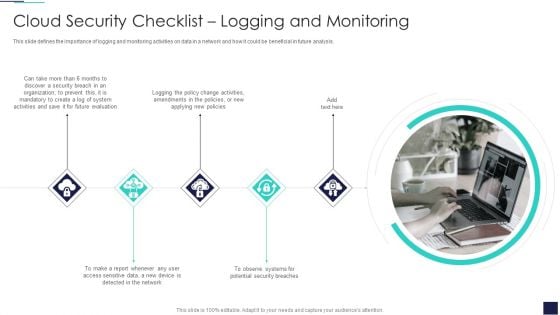
Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. Presenting Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Future Evaluation, New Policies, Potential Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
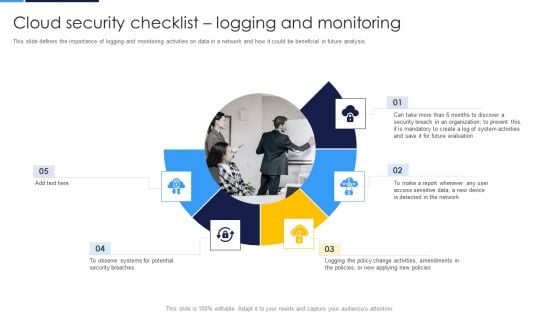
Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis.Presenting Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Breaches, Access Sensitive, System Activities In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
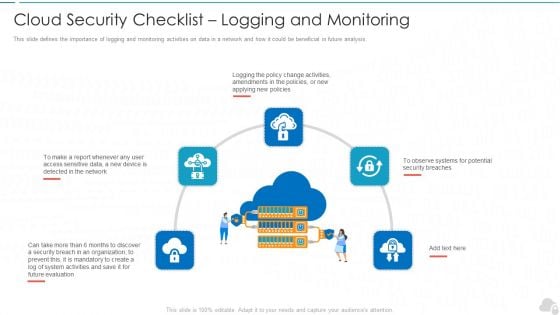
Cloud Security Checklist Logging And Monitoring Cloud Computing Security IT Ppt Show Example PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. This is a cloud security checklist logging and monitoring cloud computing security it ppt show example pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluation, organization, policies, potential, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
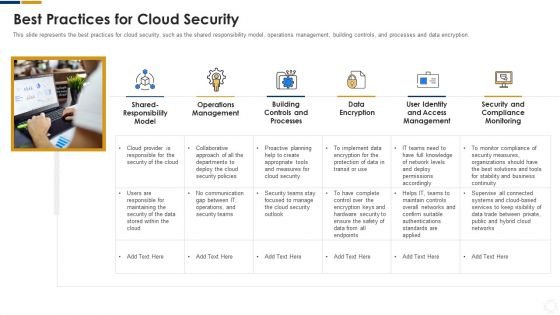
Cybersecurity Best Practices For Cloud Security Ppt Ideas Images PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting cybersecurity best practices for cloud security ppt ideas images pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like measures, security, planning, network, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Steps To Boost Home Safety And Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the process to be followed by smart homeowners to increase security. Major steps covered are determining data captured, utilizing security features, keeping networks separate, providing access to authorized people, monitoring energy usage and taking precautions. Create an editable Steps To Boost Home Safety And Security Utilizing Smart Appliances IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Steps To Boost Home Safety And Security Utilizing Smart Appliances IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides an overview of the process to be followed by smart homeowners to increase security. Major steps covered are determining data captured, utilizing security features, keeping networks separate, providing access to authorized people, monitoring energy usage and taking precautions.
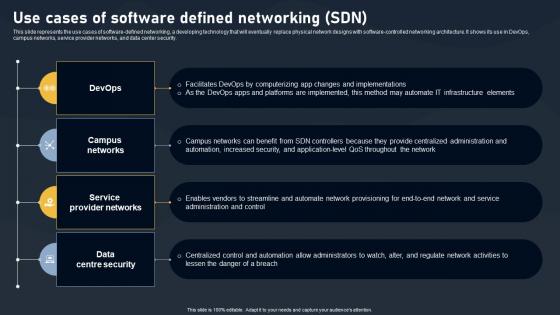
Use Cases Of Software Defined Networking SDN Building Blocks Summary Pdf
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Use Cases Of Software Defined Networking SDN Building Blocks Summary Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Use Cases Of Software Defined Networking SDN Building Blocks Summary Pdf. This slide represents the use cases of software defined networking, a developing technology that will eventually replace physical network designs with software controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security.


 Continue with Email
Continue with Email

 Home
Home


































