Data Protection

Compliance Risk Related With Dark Data Importance Of Unstructured Data Ppt Presentation
This slide highlights the compliance risk associated with dark data. Compliance obligations for dark data refer to the legal and regulatory requirements that organizations must adhere to for the protection of sensitive data. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Compliance Risk Related With Dark Data Importance Of Unstructured Data Ppt Presentation will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide highlights the compliance risk associated with dark data. Compliance obligations for dark data refer to the legal and regulatory requirements that organizations must adhere to for the protection of sensitive data.
Securing Our Data With CRM Designing And Deployment Ppt PowerPoint Presentation Icon Example File PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Deliver an awe inspiring pitch with this creative securing our data with crm designing and deployment ppt powerpoint presentation icon example file pdf bundle. Topics like crm data security, ip restriction, data storage and failover, communication protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Checklist Data Encryption Professional PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. Presenting Cloud Security Checklist Data Encryption Professional PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Protect Keys, Encrypted Data, Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
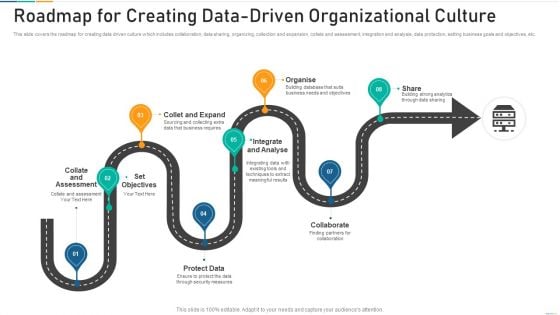
Roadmap For Creating Data Driven Organizational Culture Designs PDF
Presenting roadmap for creating data driven organizational culture designs pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including analyse, protect data, collaborat. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Breach Prevention Strategies For Users Data Breach Prevention Sample Pdf
This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Breach Prevention Strategies For Users Data Breach Prevention Sample Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the strategies to protect users from data breaches. These include use unique passwords, two-factor authentication, only submit sensitive data on HTTPS websites, software and hardware updates, encrypt hard drives, etc.

Big Data Architecture Processes Ppt PowerPoint Presentation File Portfolio PDF
This is a Big Data Architecture Processes Ppt PowerPoint Presentation File Portfolio PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Connecting To Data Sources, Data Governance, Protecting Quality Of Service, Systems Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Privacy IT 30 60 90 Days Plan For Data Privacy Guidelines PDF
This slide represents the 30 60 90 days plan for data privacy, including hiring DPO Data Protection Officer, understanding the data and requirements, analyzing the risks. This is a information privacy it 30 60 90 days plan for data privacy guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan for data privacy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security 30 60 90 Days Plan For Data Privacy Ppt PowerPoint Presentation File Gallery PDF
This slide represents the 30 60 90 days plan for data privacy, including hiring DPO Data Protection Officer, understanding the data and requirements, analyzing the risks. Create an editable Information Security 30 60 90 Days Plan For Data Privacy Ppt PowerPoint Presentation File Gallery PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Information Security 30 60 90 Days Pl is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
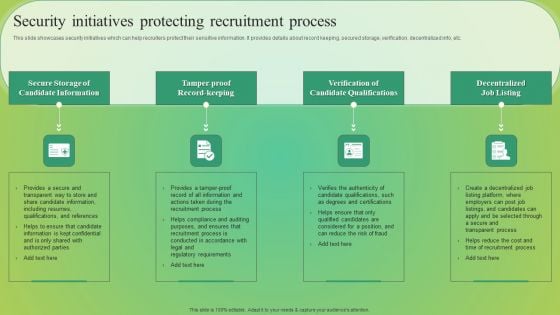
Security Initiatives Protecting Recruitment Process Elements PDF
This slide showcases security initiatives which can help recruiters protect their sensitive information. It provides details about record keeping, secured storage, verification, decentralized info, etc. Slidegeeks is here to make your presentations a breeze with Security Initiatives Protecting Recruitment Process Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Copyright Protected Music PowerPoint Template 1110
3d illustration of a pair of headphones on a chrome metallic copyright symbol on a reflective gold surface Brew your ideas in our Copyright Protected Music PowerPoint Template 1110. They will come upwith an exciting concoction.

Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses
This slide highlights the data breach mitigation measures for workers. These strategies include maintain a record of banking receipts, dont believe everything, be mindful of sharing anything on social media, secure all devices, protect individual accounts, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide highlights the data breach mitigation measures for workers. These strategies include maintain a record of banking receipts, dont believe everything, be mindful of sharing anything on social media, secure all devices, protect individual accounts, etc.

Various Methods Of Data Accuracy Preservation Elements PDF
The slide highlights methods to preserve data integrity for protecting data accuracy and validity. Various methods included are input validation, data validation and duplicate data removal. Persuade your audience using this Various Methods Of Data Accuracy Preservation Elements PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Input Validation, Data Validation, Duplicate Data Removal. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
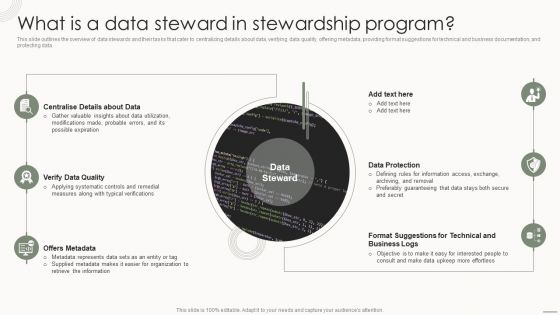
Data Governance IT What Is A Data Steward In Stewardship Program Elements PDF
This slide outlines the overview of data stewards and their tasks that cater to centralizing details about data, verifying data quality, offering metadata, providing format suggestions for technical and business documentation, and protecting data. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Data Governance IT What Is A Data Steward In Stewardship Program Elements PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Email Security Encryption And Data Loss Prevention Your Problem E Mail Security Proposal Rules PDF
This slide covers the problems that are faced by the clients. Presenting email security encryption and data loss prevention your problem e mail security proposal rules pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security confidential data, protection against malware, protection phishing scams, threat weak password. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Based Email Security Market Report Issues Faced By Companies Data Ppt Icon Templates PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Presenting cloud based email security market report issues faced by companies data ppt icon templates pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
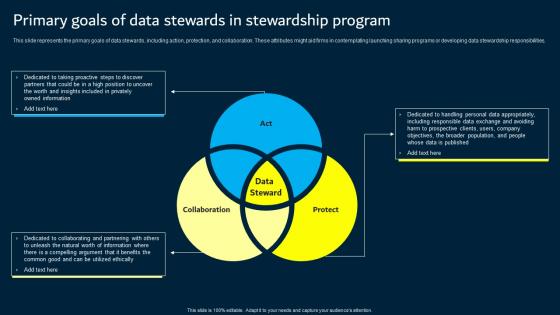
Primary Goals Of Data Stewards In Stewardship Program Data Custodianship Professional Pdf
This slide represents the primary goals of data stewards, including action, protection, and collaboration. These attributes might aid firms in contemplating launching sharing programs or developing data stewardship responsibilities. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Primary Goals Of Data Stewards In Stewardship Program Data Custodianship Professional Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Primary Goals Of Data Stewards In Stewardship Program Data Custodianship Professional Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the primary goals of data stewards, including action, protection, and collaboration. These attributes might aid firms in contemplating launching sharing programs or developing data stewardship responsibilities.
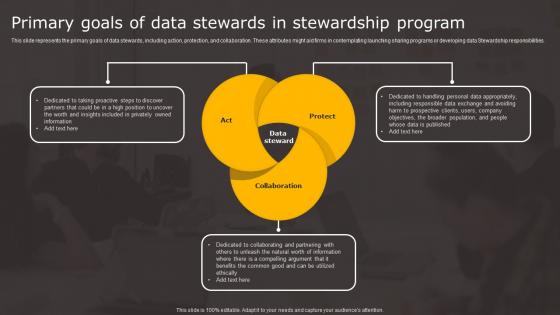
Data Stewardship In Business Processes Primary Goals Data Stewards Stewardship Inspiration Pdf
This slide represents the primary goals of data stewards, including action, protection, and collaboration. These attributes might aid firms in contemplating launching sharing programs or developing data Stewardship responsibilities. Get a simple yet stunning designed Data Stewardship In Business Processes Primary Goals Data Stewards Stewardship Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Data Stewardship In Business Processes Primary Goals Data Stewards Stewardship Inspiration Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the primary goals of data stewards, including action, protection, and collaboration. These attributes might aid firms in contemplating launching sharing programs or developing data Stewardship responsibilities.
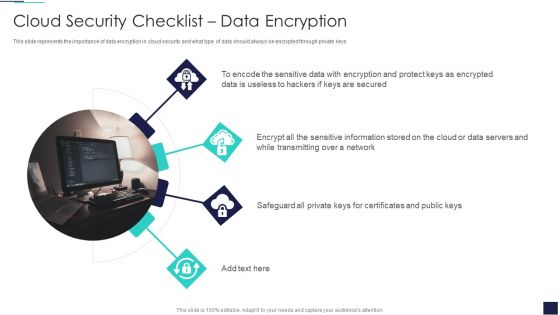
Cloud Information Security Cloud Security Checklist Data Encryption Ppt Summary Shapes PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. This is a Cloud Information Security Cloud Security Checklist Data Encryption Ppt Summary Shapes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Sensitive Data, Protect Keys, Data Servers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
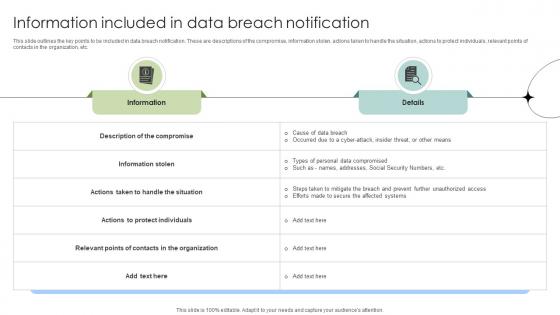
Information Included In Data Breach Notification Data Fortification Strengthening Defenses
This slide outlines the key points to be included in data breach notification. These are descriptions of the compromise, information stolen, actions taken to handle the situation, actions to protect individuals, relevant points of contacts in the organization, etc. Retrieve professionally designed Information Included In Data Breach Notification Data Fortification Strengthening Defenses to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the key points to be included in data breach notification. These are descriptions of the compromise, information stolen, actions taken to handle the situation, actions to protect individuals, relevant points of contacts in the organization, etc.

Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. The Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc.

Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low level encryption, reliance on cloud service providers for data protection, poor key management, etc. Take your projects to the next level with our ultimate collection of Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low level encryption, reliance on cloud service providers for data protection, poor key management, etc.

Benefits Of Customer Data Platform For Marketers Usability Of CDP Software Tool Summary Pdf
The following slide illustrates key advantages of CDP for marketers to boost revenue and profitability. It includes elements such as segmentation, personalization, product recommendations, conversion rate, automation, operational efficiency, data protection, agility etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Customer Data Platform For Marketers Usability Of CDP Software Tool Summary Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide illustrates key advantages of CDP for marketers to boost revenue and profitability. It includes elements such as segmentation, personalization, product recommendations, conversion rate, automation, operational efficiency, data protection, agility etc.
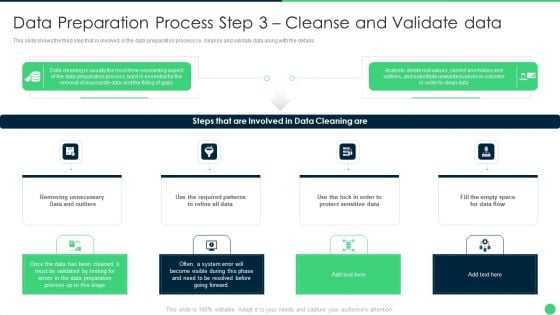
Data Preparation Process Step 3 Cleanse And Validate Data Slides PDF
This slide shows the third step that is involved in the data preparation process i.e. cleanse and validate data along with the details.Presenting Data Preparation Process Step 3 Cleanse And Validate Data Slides PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Removing Unnecessary, Protect Sensitive, Data Preparation In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
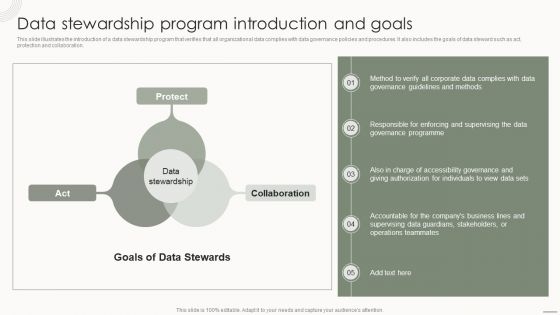
Data Governance IT Data Stewardship Program Introduction And Goals Formats PDF
This slide illustrates the introduction of a data stewardship program that verifies that all organizational data complies with data governance policies and procedures. It also includes the goals of data steward such as act, protection and collaboration. Do you know about Slidesgeeks Data Governance IT Data Stewardship Program Introduction And Goals Formats PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
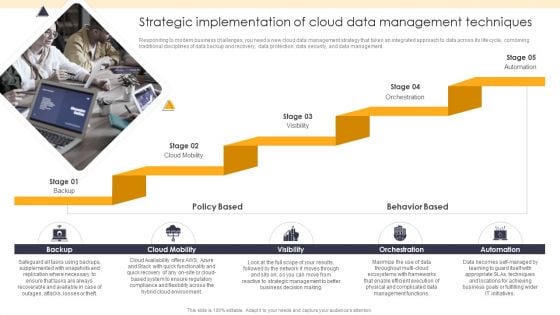
ETL Repository Strategic Implementation Of Cloud Data Management Techniques Mockup PDF
Responding to modern business challenges, you need a new cloud data management strategy that takes an integrated approach to data across its life cycle, combining traditional disciplines of data backup and recovery, data protection, data security, and data management.Presenting ETL Repository Strategic Implementation Of Cloud Data Management Techniques Mockup PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Supplemented Snapshots, Replication Necessary, Recoverable Available. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
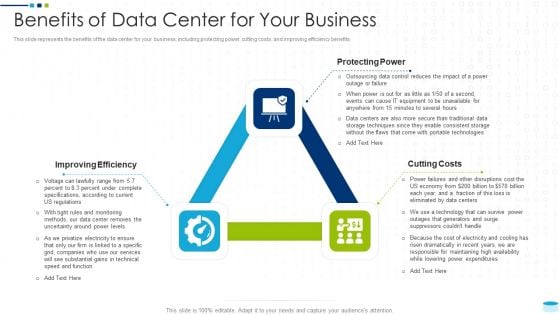
Data Center Infrastructure Management IT Benefits Of Data Center For Your Business Slides PDF
This slide represents the benefits of the data center for your business, including protecting power, cutting costs, and improving efficiency benefits. Presenting data center infrastructure management it benefits of data center for your business slides pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improving efficiency, protecting power, cutting costs. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Tips For Protecting Employee Electronic Footprint Clipart PDF
This slide lists down tips for protecting digital footprints for company employees to avoid data breach. It includes limiting data sharing, avoiding unsafe websites, not logging in with facebook and acting faster after a breach. Persuade your audience using this Tips For Protecting Employee Electronic Footprint Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Organizations, Confidential Information, Limit Data Sharing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
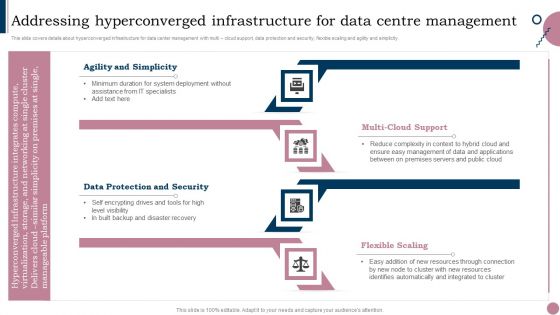
Cios Guide To Optimize Addressing Hyperconverged Infrastructure For Data Centre Information PDF
This slide covers details about hyperconverged infrastructure for data center management with multi cloud support, data protection and security, flexible scaling and agility and simplicity. Create an editable Cios Guide To Optimize Addressing Hyperconverged Infrastructure For Data Centre Information PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Cios Guide To Optimize Addressing Hyperconverged Infrastructure For Data Centre Information PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Market Trends Inspiration PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. This is a modern security observation plan to eradicate cybersecurity risk and data breach current market trends inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increasing digitization of sensitive data, outsourcing, general data protection laws. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
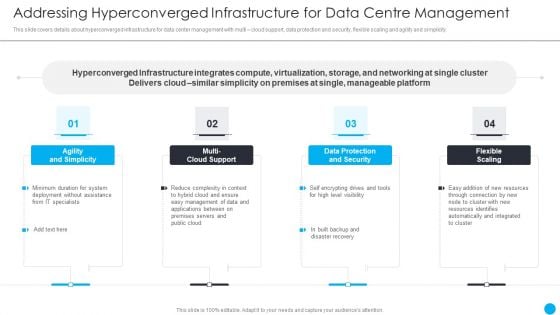
Cios Methodologies To Improve IT Spending Addressing Hyperconverged Infrastructure For Data Background PDF
This slide covers details about hyperconverged infrastructure for data center management with multi cloud support, data protection and security, flexible scaling and agility and simplicity. Presenting Cios Methodologies To Improve IT Spending Addressing Hyperconverged Infrastructure For Data Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Flexible Scaling, Agility Simplicity, Automatically Integrated In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
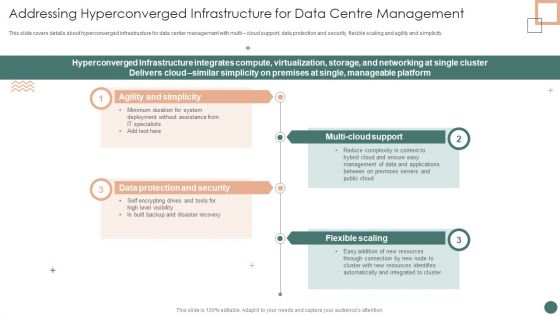
Improved Digital Expenditure Addressing Hyperconverged Infrastructure For Data Centre Management Introduction PDF
This slide covers details about hyperconverged infrastructure for data center management with multi cloud support, data protection and security, flexible scaling and agility and simplicity. Presenting Improved Digital Expenditure Addressing Hyperconverged Infrastructure For Data Centre Management Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Minimum Duration, Complexity Context, Resources Identifies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
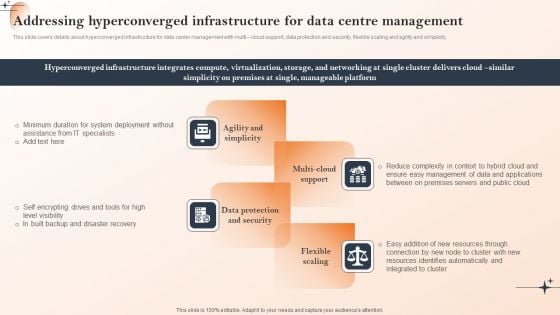
Action Of Cios To Achieve Cost Management Addressing Hyperconverged Infrastructure For Data Centre Management Themes PDF
This slide covers details about hyperconverged infrastructure for data center management with multi cloud support, data protection and security, flexible scaling and agility and simplicity. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Action Of Cios To Achieve Cost Management Addressing Hyperconverged Infrastructure For Data Centre Management Themes PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

CRM Solutions Implementation Strategy Securing Our Data With CRM Structure PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.Deliver and pitch your topic in the best possible manner with this CRM Solutions Implementation Strategy Securing Our Data With CRM Structure PDF Use them to share invaluable insights on Factor Authentication, Communication Protection, Storage And Failover and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
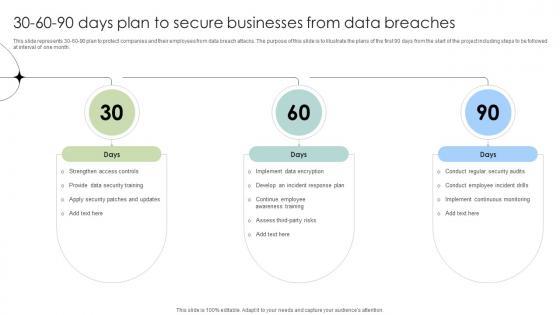
30 60 90 Days Plan To Secure Businesses From Data Breaches Data Fortification Strengthening Defenses
This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Businesses From Data Breaches Data Fortification Strengthening Defenses. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.
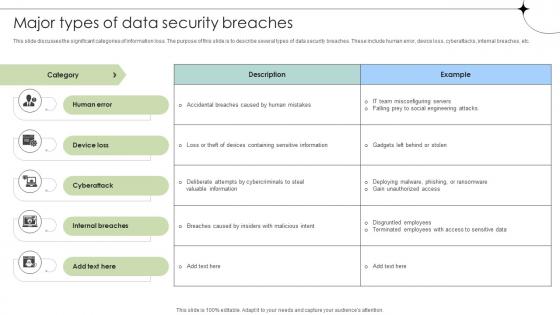
Major Types Of Data Security Breaches Data Fortification Strengthening Defenses
This slide discusses the significant categories of information loss. The purpose of this slide is to describe several types of data security breaches. These include human error, device loss, cyberattacks, internal breaches, etc. Presenting this PowerPoint presentation, titled Major Types Of Data Security Breaches Data Fortification Strengthening Defenses, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Major Types Of Data Security Breaches Data Fortification Strengthening Defenses. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Major Types Of Data Security Breaches Data Fortification Strengthening Defenses that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide discusses the significant categories of information loss. The purpose of this slide is to describe several types of data security breaches. These include human error, device loss, cyberattacks, internal breaches, etc.
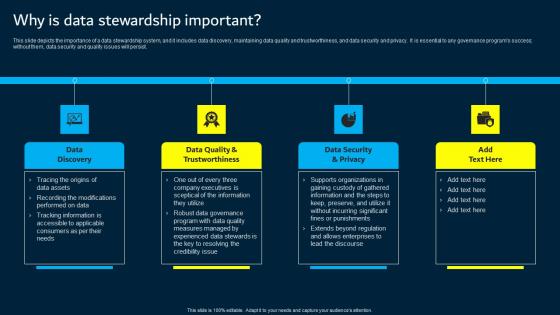
Why Is Data Stewardship Important Data Custodianship Formats Pdf
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance program s success without them, data security and quality issues will persist. Boost your pitch with our creative Why Is Data Stewardship Important Data Custodianship Formats Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance program s success without them, data security and quality issues will persist.
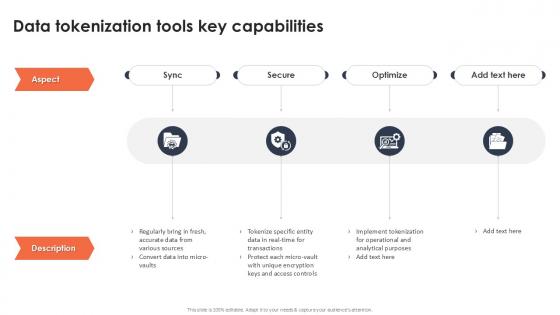
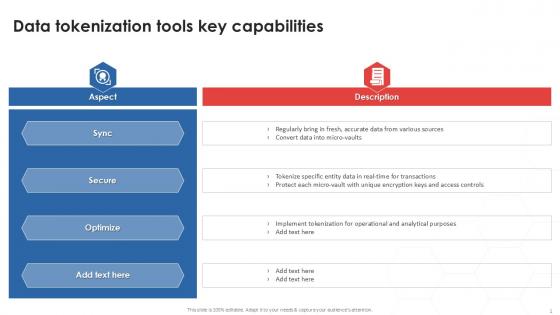
Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint
If you are looking for a format to display your unique thoughts, then the professionally designed Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Our Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Data Democratization Challenges In Product Data Analytics Ideas Pdf
This slide represents the data democratization challenges for product data analytics with relevant mitigation strategies. These challenges include challenges like complication of data analytics architecture, lack of data centralization, etc. Showcasing this set of slides titled Data Democratization Challenges In Product Data Analytics Ideas Pdf. The topics addressed in these templates are Data Privacy And Security, Data Literacy , Data Reliability And Homogeneity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the data democratization challenges for product data analytics with relevant mitigation strategies. These challenges include challenges like complication of data analytics architecture, lack of data centralization, etc.

Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses
This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. This Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc.
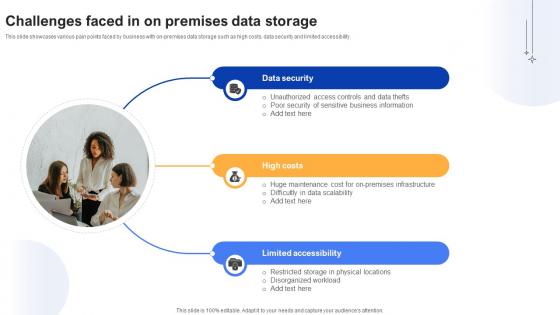
Effective Data Migration Challenges Faced In On Premises Data Storage
This slide showcases various pain points faced by business with on-premises data storage such as high costs, data security and limited accessibility. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Effective Data Migration Challenges Faced In On Premises Data Storage a try. Our experts have put a lot of knowledge and effort into creating this impeccable Effective Data Migration Challenges Faced In On Premises Data Storage. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases various pain points faced by business with on-premises data storage such as high costs, data security and limited accessibility.
Data Tokenization Tools Tokenization Strategies For Data Security PPT Template
Boost your pitch with our creative Data Tokenization Tools Tokenization Strategies For Data Security PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Data Tokenization Tools Tokenization Strategies For Data Security PPT Template are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
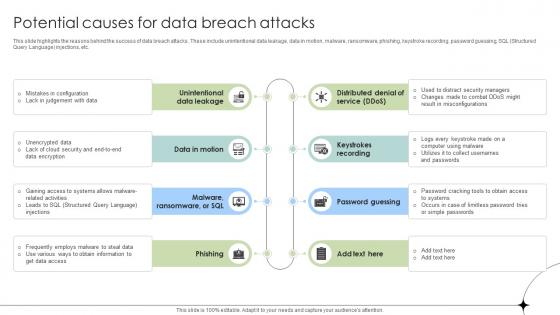
Potential Causes For Data Breach Attacks Data Fortification Strengthening Defenses
This slide highlights the reasons behind the success of data breach attacks. These include unintentional data leakage, data in motion, malware, ransomware, phishing, keystroke recording, password guessing, SQL Structured Query Language injections, etc.Find a pre-designed and impeccable Potential Causes For Data Breach Attacks Data Fortification Strengthening Defenses. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights the reasons behind the success of data breach attacks. These include unintentional data leakage, data in motion, malware, ransomware, phishing, keystroke recording, password guessing, SQL Structured Query Language injections, etc.

Main Data Security Tokenization Techniques Securing Your Data Ppt Sample
This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc. The Main Data Security Tokenization Techniques Securing Your Data Ppt Sample is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc.

Information Privacy IT Data Privacy Vs Data Security Professional PDF
This slide compares data privacy with data security, indicating that security is concerned with safeguarding data, and privacy is about responsible data usage. Presenting information privacy it data privacy vs data security professional pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like data privacy vs data security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security. If you are looking for a format to display your unique thoughts, then the professionally designed Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.

Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.

Data Breach Response Plan Fix Vulnerabilities Data Fortification Strengthening Defenses
This slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc.Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Breach Response Plan Fix Vulnerabilities Data Fortification Strengthening Defenses to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc.
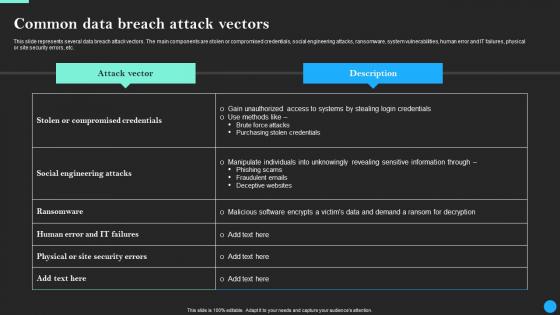
Common Data Breach Attack Vectors Data Breach Prevention Clipart Pdf
This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc. Present like a pro with Common Data Breach Attack Vectors Data Breach Prevention Clipart Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc.

Common Data Breach Attack Vectors Data Fortification Strengthening Defenses
This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc. Present like a pro with Common Data Breach Attack Vectors Data Fortification Strengthening Defenses. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc.

Data Breach Awareness Training Program Data Breach Prevention Professional Pdf
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs. Find highly impressive Data Breach Awareness Training Program Data Breach Prevention Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Breach Prevention Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.

Data Breach Awareness Training Program Data Fortification Strengthening Defenses
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.Find highly impressive Data Breach Awareness Training Program Data Fortification Strengthening Defenses on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Fortification Strengthening Defenses for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.

Data Governance IT Why Is Data Stewardship Important Formats PDF
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance programs success without them, data security and quality issues will persist. Are you searching for a Data Governance IT Why Is Data Stewardship Important Formats PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Data Governance IT Why Is Data Stewardship Important Formats PDF from Slidegeeks today.
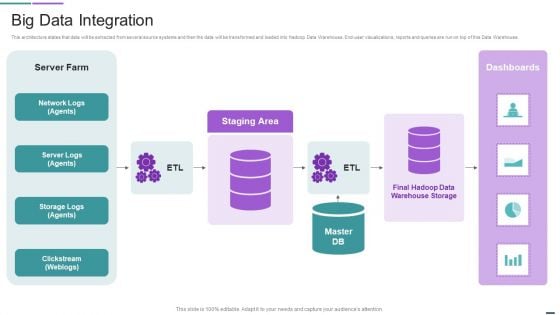
Data Management Solutions Big Data Integration Download PDF
This architecture states that data will be extracted from several source systems and then the data will be transformed and loaded into Hadoop Data Warehouse. End user visualizations, reports and queries are run on top of this Data Warehouse. Deliver and pitch your topic in the best possible manner with this Data Management Solutions Big Data Integration Download PDF. Use them to share invaluable insights on Network Logs, Storage Logs, Warehouse Storage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Warehouse Implementation Why We Need Data Warehouse Portrait PDF
This slide represents the need for a data warehouse in the organization, such as data quality, single point for all data for all users, and the complicated problems that can be solved through a data warehouse.Deliver and pitch your topic in the best possible manner with this Data Warehouse Implementation Why We Need Data Warehouse Portrait PDF. Use them to share invaluable insights on Systems Individually, Range Of Complicated, Security Considerations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
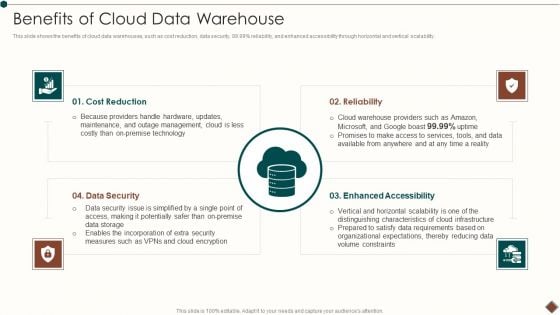
Data Warehouse Implementation Benefits Of Cloud Data Warehouse Professional PDF
This slide shows the benefits of cloud data warehouses, such as cost reduction, data security, 99.99persent reliability, and enhanced accessibility through horizontal and vertical scalability.Deliver an awe inspiring pitch with this creative Data Warehouse Implementation Benefits Of Cloud Data Warehouse Professional PDF bundle. Topics like Because Providers, Outage Management, Premise Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Data Breach Prevention Status Tracking Dashboard Data Fortification Strengthening Defenses
This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Breach Prevention Status Tracking Dashboard Data Fortification Strengthening Defenses and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the critical cyber security performance indicators for the organization. The key components include application health, encryption status, license consumption, windows defender, etc.
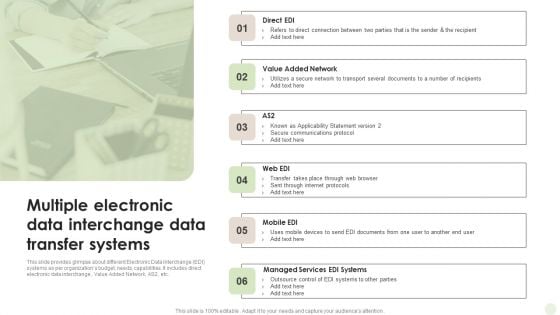
Multiple Electronic Data Interchange Data Transfer Systems Summary PDF
This slide provides glimpse about different Electronic Data Interchange EDI systems as per organizations budget, needs, capabilities. It includes direct electronic data interchange , Value Added Network, AS2, etc.Persuade your audience using this Multiple Electronic Data Interchange Data Transfer Systems Summary PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Connection Between, Transport Several, Communications Protocol. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc.
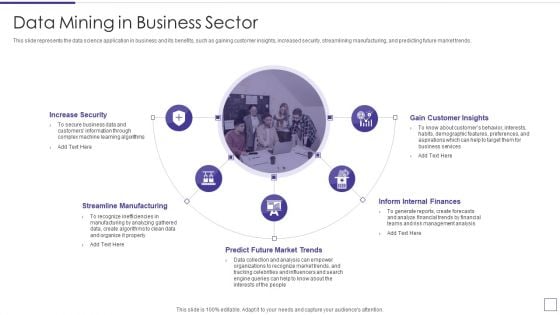
Data Mining Implementation Data Mining In Business Sector Download PDF
This slide represents the data science application in business and its benefits, such as gaining customer insights, increased security, streamlining manufacturing, and predicting future market trends.Presenting data mining implementation data mining in business sector download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like increase security, streamline manufacturing, predict future market trends In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
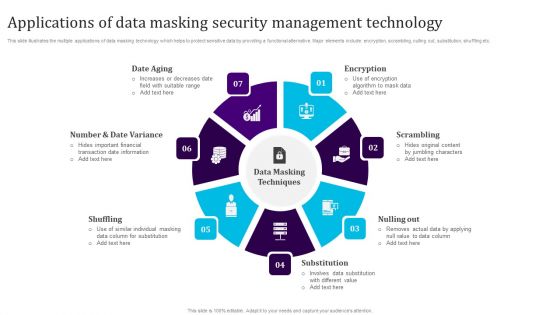
Applications Of Data Masking Security Management Technology Sample PDF
This slide illustrates the multiple applications of data masking technology which helps to protect sensitive data by providing a functional alternative. Major elements include encryption, scrambling, nulling out, substitution, shuffling etc. Persuade your audience using this Applications Of Data Masking Security Management Technology Sample PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Date Aging, Shuffling, Substitution, Nulling Out, Scrambling, Encryption. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































