Data Protection

Zero Trust Model Endpoint Initiated Zero Trust Network Topology Model
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Model Endpoint Initiated Zero Trust Network Topology Model. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.

Zero Trust Model Service Initiated Zero Trust Network Topology Model
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Model Service Initiated Zero Trust Network Topology Model for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.

Zero Trust Network Access Logical Components Of Zero Trust Architecture
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. Take your projects to the next level with our ultimate collection of Zero Trust Network Access Logical Components Of Zero Trust Architecture. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point.

Types Security Services Information Technology Ppt PowerPoint Presentation Summary Backgrounds Cpb
Presenting this set of slides with name types security services information technology ppt powerpoint presentation summary backgrounds cpb. This is an editable Powerpoint three stages graphic that deals with topics like types security services information technology to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Corporate Security And Risk Management Table Of Contents Corporate Security And Risk Download PDF
Presenting corporate security and risk management table of contents corporate security and risk download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, ensuring physical security, securing firm from natural calamity threats, handling cyber threats to secure digital assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Information Pie Donut Diagram 6 Stages Sample Of Business Proposal PowerPoint Slides
We present our information pie donut diagram 6 stages sample of business proposal PowerPoint Slides.Download and present our Circle Charts PowerPoint Templates because Your success is our commitment. Our PowerPoint Templates and Slides will ensure you reach your goal. Use our Process and Flows PowerPoint Templates because You should Throw the gauntlet with our PowerPoint Templates and Slides. They are created to take up any challenge. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let your team Walk through your plans. See their energy levels rise as you show them the way. Download and present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Download our Marketing PowerPoint Templates because You can Channelise the thoughts of your team with our PowerPoint Templates and Slides. Urge them to focus on the goals you have set.Use these PowerPoint slides for presentations relating to diagram, business, chart, market, website, network, statistics, model, document, junction, red, plan, vector, presentation, template, circle, brochure, orange, data, stock, process, marketing, management, graph, wheel, multicolored, box, pie, options, catalog, direction, design, company, navigation, financial, structure, multiple, button, goals, results. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Fact of the matter is that you have great ideas. Drive this ability home with our Information Pie Donut Diagram 6 Stages Sample Of Business Proposal PowerPoint Slides.

Desktop Security Management Minimize Administrative And Staff Privileges Download PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. This is a desktop security management minimize administrative and staff privileges download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like minimize administrative and staff privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
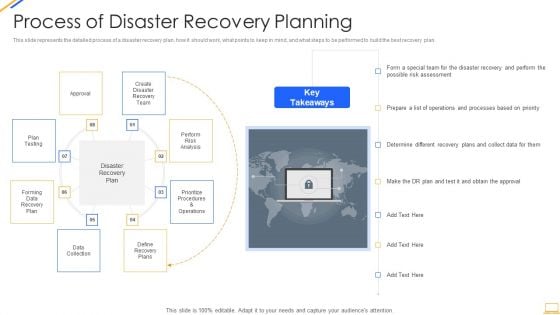
Desktop Security Management Process Of Disaster Recovery Planning Professional PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a desktop security management process of disaster recovery planning professional pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plans, team, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Server Room Layout Vector With Authentication Ppt PowerPoint Presentation Gallery Pictures PDF
Pitch your topic with ease and precision using this server room layout vector with authentication ppt powerpoint presentation gallery pictures pdf. This layout presents information on server room layout vector with authentication. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Bank Note With Watermark Authentication Stamp Ppt PowerPoint Presentation Example 2015 PDF
Presenting bank note with watermark authentication stamp ppt powerpoint presentation example 2015 pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including bank note with watermark authentication stamp. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
7 Stage Pyramid Infographics For Authentication System Ppt PowerPoint Presentation File Good PDF
Presenting 7 stage pyramid infographics for authentication system ppt powerpoint presentation file good pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including 7 stage pyramid infographics for authentication system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Customer Authentication Process Flow Of Verification Factors For Safe Access Vector Icon Infographics PDF
Showcasing this set of slides titled customer authentication process flow of verification factors for safe access vector icon infographics pdf. The topics addressed in these templates are customer authentication process flow of verification factors for safe access vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
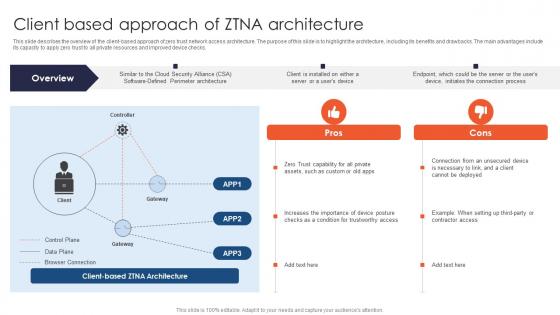
Zero Trust Network Access Client Based Approach Of ZTNA Architecture
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. This modern and well-arranged Zero Trust Network Access Client Based Approach Of ZTNA Architecture provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.
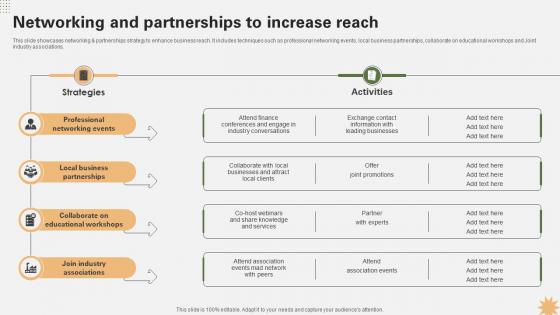
Networking And Partnerships To Increase Reach Strategy For Launching A Financial Strategy SS V
This slide showcases networking and partnerships strategy to enhance business reach. It includes techniques such as professional networking events, local business partnerships, collaborate on educational workshops and Joint industry associations. Retrieve professionally designed Networking And Partnerships To Increase Reach Strategy For Launching A Financial Strategy SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases networking and partnerships strategy to enhance business reach. It includes techniques such as professional networking events, local business partnerships, collaborate on educational workshops and Joint industry associations.
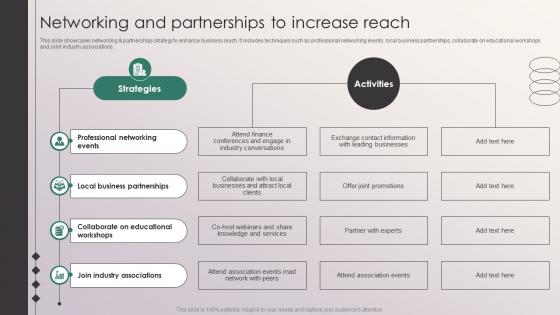
Networking And Partnerships To Increase Reach Penetrating Markets With Financial Strategy SS V
This slide showcases networking and partnerships strategy to enhance business reach. It includes techniques such as professional networking events, local business partnerships, collaborate on educational workshops and Joint industry associations. Retrieve professionally designed Networking And Partnerships To Increase Reach Penetrating Markets With Financial Strategy SS V to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases networking and partnerships strategy to enhance business reach. It includes techniques such as professional networking events, local business partnerships, collaborate on educational workshops and Joint industry associations.
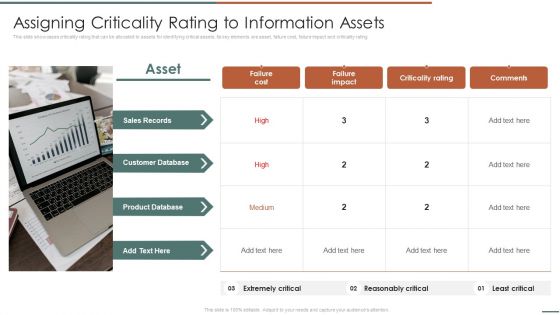
Information Security Risk Evaluation Assigning Criticality Rating To Information Assets Template PDF
This slide showcases criticality rating that can be allocated to assets for identifying critical assets. Its key elements are asset, failure cost, failure impact and criticality rating.Presenting Information Security Risk Evaluation Assigning Criticality Rating To Information Assets Template PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Customer Database, Product Database, Sales Records. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
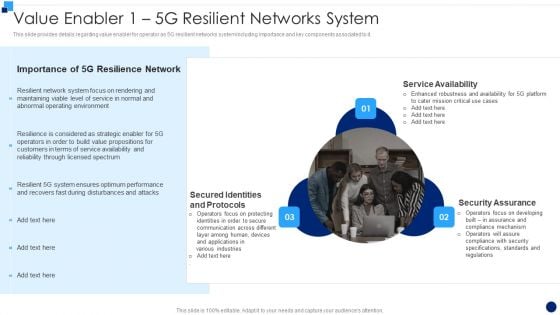
Developing 5G Wireless Cellular Network Value Enabler 1 5G Resilient Networks System Clipart PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a Developing 5G Wireless Cellular Network Value Enabler 1 5G Resilient Networks System Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Assurance, Service Availability, Protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
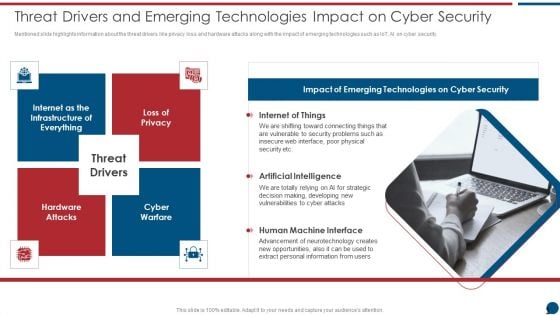
Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Presenting Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Internet Of Things, Artificial Intelligence, Human Machine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Communication Plan For Information Technology Security Based On Audience Type Demonstration PDF
This slide consists of a communication plan information technology security to be deployed by managers based on the type of audience. Key elements include communication, frequency, communication goal, owner, etc. Presenting Communication Plan For Information Technology Security Based On Audience Type Demonstration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Project Status Report, Team Standup, Task Progress Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Risk Security PowerPoint Ppt Templates Security Ppt Slides
Risk Security PowerPoint PPT templates Security PPT Slides-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Achieve success with our Risk Security PowerPoint Ppt Templates Security Ppt Slides. Download without worries with our money back guaranteee.
Icons Slide Cloud Networking Service Provider Business Model BMC SS V
Download our innovative and attention grabbing Icons Slide Cloud Networking Service Provider Business Model BMC SS V template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide Cloud Networking Service Provider Business Model BMC SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Checklist For Selecting Functional Technology Security Vendor Mockup PDF
Showcasing this set of slides titled checklist for selecting functional technology security vendor mockup pdf. The topics addressed in these templates are security, environments, technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
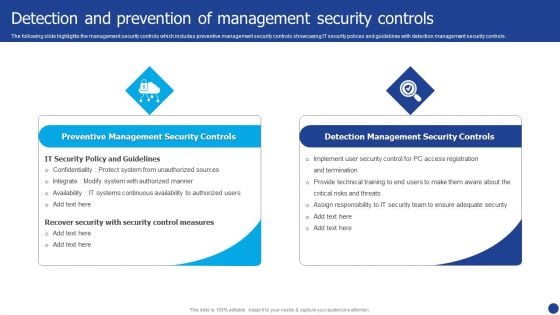
Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF
The following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Presenting Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Preventive Management Security Controls, Detection Management Security Controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
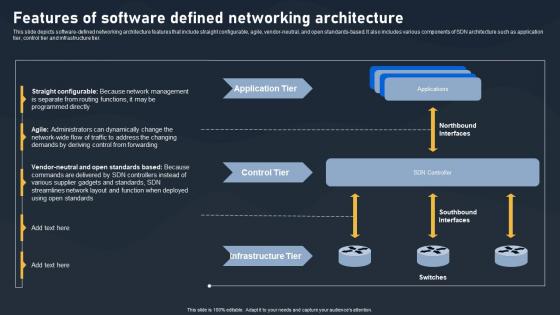
Features Of Software Defined Networking Architecture SDN Building Blocks Demonstration Pdf
This slide depicts software-defined networking architecture features that include straight configurable, agile, vendor-neutral, and open standards-based. It also includes various components of SDN architecture such as application tier, control tier and infrastructure tier.Presenting this PowerPoint presentation, titled Features Of Software Defined Networking Architecture SDN Building Blocks Demonstration Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Features Of Software Defined Networking Architecture SDN Building Blocks Demonstration Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Features Of Software Defined Networking Architecture SDN Building Blocks Demonstration Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide depicts software defined networking architecture features that include straight configurable, agile, vendor neutral, and open standards based. It also includes various components of SDN architecture such as application tier, control tier and infrastructure tier.

Satellite Communication Network Integrated With IoT Sensor IoT In Orbit Unleashing The Power IoT SS V
This slide exhibits an overview of wireless sensor and satellite communication integration to enhance IoT application capabilities across changing environments. It includes satellite network architecture with elements such as sensor networks, terminal stations, earth stations, etc. Retrieve professionally designed Satellite Communication Network Integrated With IoT Sensor IoT In Orbit Unleashing The Power IoT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide exhibits an overview of wireless sensor and satellite communication integration to enhance IoT application capabilities across changing environments. It includes satellite network architecture with elements such as sensor networks, terminal stations, earth stations, etc.

Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets.Are you searching for a Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF from Slidegeeks today.
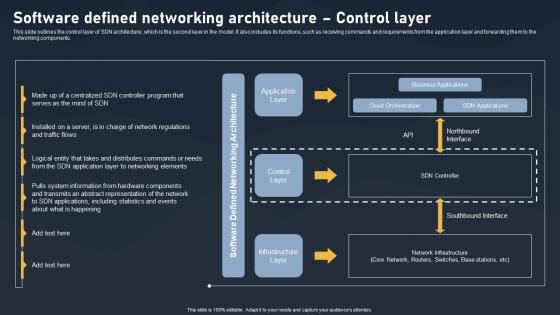
Software Defined Networking Architecture Control Layer SDN Building Blocks Portrait Pdf
This slide outlines the control layer of SDN architecture, which is the second layer in the model. It also includes its functions, such as receiving commands and requirements from the application layer and forwarding them to the networking components.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Software Defined Networking Architecture Control Layer SDN Building Blocks Portrait Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the control layer of SDN architecture, which is the second layer in the model. It also includes its functions, such as receiving commands and requirements from the application layer and forwarding them to the networking components.
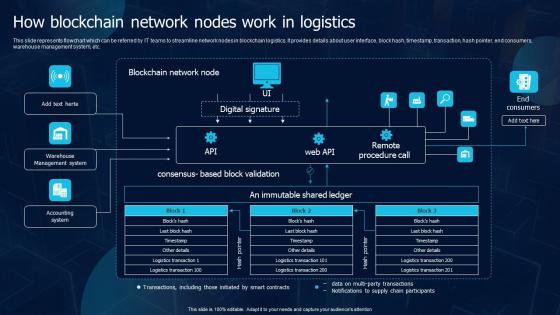
How Blockchain Network Nodes Work In Logistics Blockchain Transportation Professional Pdf
This slide represents flowchart which can be referred by IT teams to streamline network nodes in blockchain logistics. It provides details about user interface, block hash, timestamp, transaction, hash pointer, end consumers, warehouse management system, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit How Blockchain Network Nodes Work In Logistics Blockchain Transportation Professional Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents flowchart which can be referred by IT teams to streamline network nodes in blockchain logistics. It provides details about user interface, block hash, timestamp, transaction, hash pointer, end consumers, warehouse management system, etc.
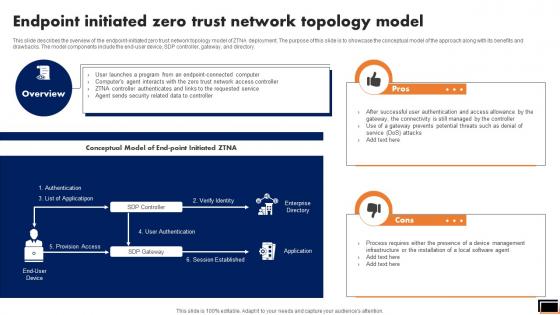
Endpoint Initiated Zero Trust Network Topology Model Software Defined Perimeter SDP
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Endpoint Initiated Zero Trust Network Topology Model Software Defined Perimeter SDP and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.

Service Initiated Zero Trust Network Topology Model Software Defined Perimeter SDP
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Find a pre-designed and impeccable Service Initiated Zero Trust Network Topology Model Software Defined Perimeter SDP. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.

Comprehensive Manual For Overview Of Private Blockchain Networks BCT SS V
This slide covers brief summary of private blockchain networks. It includes benefits such as preventing fraud by using identity to confirm membership, higher performance due to lesser nodes, private blockchain are currently more scalable, etc. along with characteristics. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Comprehensive Manual For Overview Of Private Blockchain Networks BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide covers brief summary of private blockchain networks. It includes benefits such as preventing fraud by using identity to confirm membership, higher performance due to lesser nodes, private blockchain are currently more scalable, etc. along with characteristics.
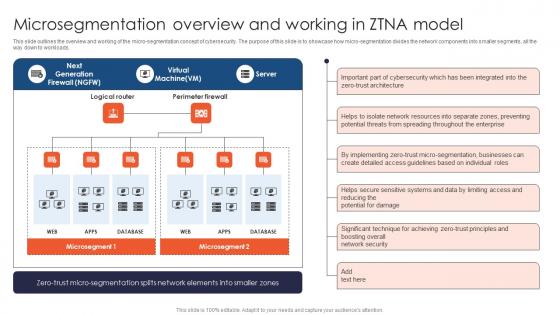
Zero Trust Network Access Microsegmentation Overview And Working In ZTNA Model
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Find a pre-designed and impeccable Zero Trust Network Access Microsegmentation Overview And Working In ZTNA Model. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.
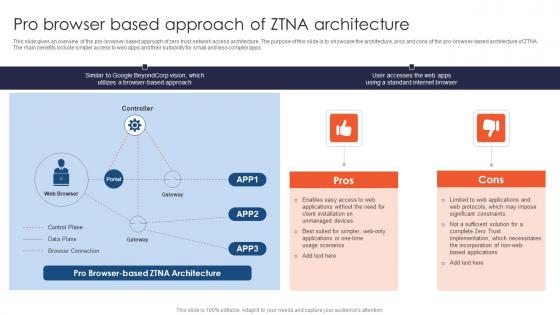
Zero Trust Network Access Pro Browser Based Approach Of ZTNA Architecture
This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. There are so many reasons you need a Zero Trust Network Access Pro Browser Based Approach Of ZTNA Architecture. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps.
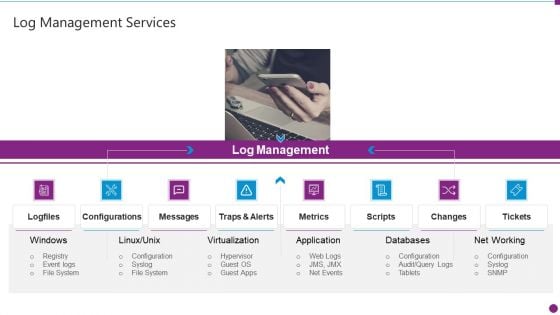
Security Information And Event Management Strategies For Financial Audit And Compliance Log Management Services Slide2 Structure PDF
This is a security information and event management strategies for financial audit and compliance log management services slide2 structure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like log management, configurations, metrics, databases, net working. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Workforce Security Realization Coaching Plan Comparison Ppt Outline Picture PDF
This is a workforce security realization coaching plan comparison ppt outline picture pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topic like comparison. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
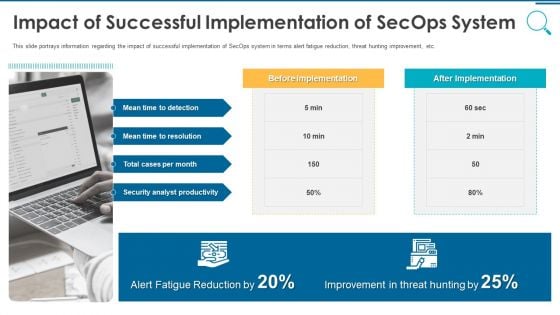
Information And Technology Security Operations Impact Of Successful Implementation Of Secops System Download PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Presenting information and technology security operations impact of successful implementation of secops system download pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, analyst, improvement, reduction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Linkedin Content Strategies Tips To Expand Business Reach Through Linkedin Marketing MKT SS V
This slide covers strategies to increase business target audience and network. The purpose of this template is to help users with techniques to expand business market. It includes elements such as staying customers radars, claim custom URL, completion of summary section, use of sponsored updates along with impacts. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Linkedin Content Strategies Tips To Expand Business Reach Through Linkedin Marketing MKT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Linkedin Content Strategies Tips To Expand Business Reach Through Linkedin Marketing MKT SS V today and make your presentation stand out from the rest This slide covers strategies to increase business target audience and network. The purpose of this template is to help users with techniques to expand business market. It includes elements such as staying customers radars, claim custom URL, completion of summary section, use of sponsored updates along with impacts.
Star Network Topology In Powerpoint And Google Slides Cpb
Introducing our well designed Star Network Topology In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Star Network Topology. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Star Network Topology In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Constraints Neural Network In Powerpoint And Google Slides Cpb
Introducing our well designed Constraints Neural Network In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Constraints Neural Network. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Constraints Neural Network In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Network Engineering Computer Science In Powerpoint And Google Slides Cpb
Introducing our well-designed Network Engineering Computer Science In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Network Engineering Computer Science. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Network Engineering Computer Science In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Blockchain In Financial Sector For Security Ppt PowerPoint Presentation File Slide Portrait PDF
Showcasing this set of slides titled blockchain in financial sector for security ppt powerpoint presentation file slide portrait pdf. The topics addressed in these templates are security, digital transactions, authentication of users. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
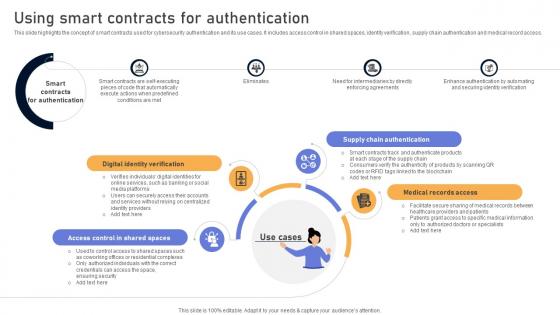
Comprehensive Look At Blockchain Using Smart Contracts For Authentication BCT SS V
This slide highlights the concept of smart contracts used for cybersecurity authentication and its use cases. It includes access control in shared spaces, identity verification, supply chain authentication and medical record access. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Comprehensive Look At Blockchain Using Smart Contracts For Authentication BCT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Comprehensive Look At Blockchain Using Smart Contracts For Authentication BCT SS V This slide highlights the concept of smart contracts used for cybersecurity authentication and its use cases. It includes access control in shared spaces, identity verification, supply chain authentication and medical record access.
Secure Computer Database Access Icon Slides PDF
Presenting Secure Computer Database Access Icon Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Secure, Computer, Database Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cloud Computing Security Architecture Icon Slides PDF
Presenting Cloud Computing Security Architecture Icon Slides PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Computing, Security Architecture Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
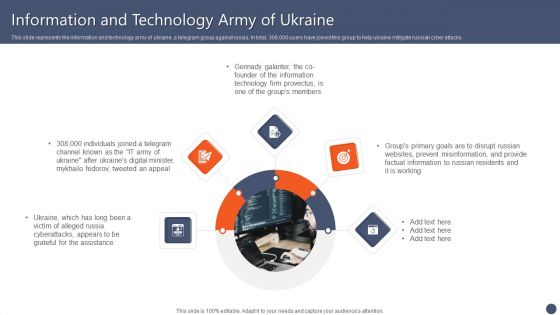
Series Of Cyber Security Attacks Against Ukraine 2022 Information And Technology Army Of Ukraine Diagrams PDF
This slide represents the information and technology army of ukraine, a telegram group against russia. In total, 308,000 users have joined this group to help ukraine mitigate russian cyber attacks. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Series Of Cyber Security Attacks Against Ukraine 2022 Information And Technology Army Of Ukraine Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Series Of Cyber Security Attacks Against Ukraine 2022 Information And Technology Army Of Ukraine Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Prevention Of Information Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre-designed and impeccable Prevention Of Information Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Functional Technology Security Challenges And Solutions To Overcome Topics PDF
Presenting functional technology security challenges and solutions to overcome topics pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including challenges, solutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
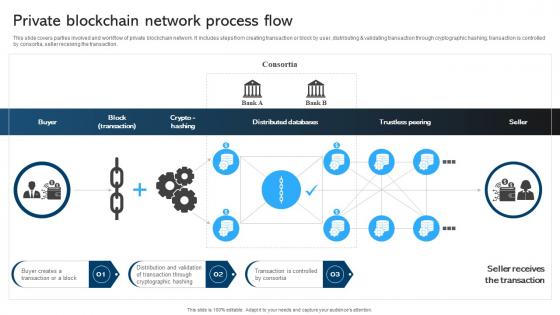
Comprehensive Manual For Blockchain Private Blockchain Network Process BCT SS V
This slide covers parties involved and workflow of private blockchain network. It includes steps from creating transaction or block by user, distributing and validating transaction through cryptographic hashing, transaction is controlled by consortia, seller receiving the transaction. Retrieve professionally designed Comprehensive Manual For Blockchain Private Blockchain Network Process BCT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide covers parties involved and workflow of private blockchain network. It includes steps from creating transaction or block by user, distributing and validating transaction through cryptographic hashing, transaction is controlled by consortia, seller receiving the transaction.

Increasing Business Awareness Overview Of Linked In Networking To Promote Strategy SS V
This slide presents an overview of linked-in networking to promote the insurance business online. It includes bets practices for influencing existence on linked din and goals such as, providing education, generate high-quality leads and improving presence in search results. Present like a pro with Increasing Business Awareness Overview Of Linked In Networking To Promote Strategy SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide presents an overview of linked-in networking to promote the insurance business online. It includes bets practices for influencing existence on linked din and goals such as, providing education, generate high-quality leads and improving presence in search results.

Multi Level Network Marketing Revenue Download Pdf
The following slide provides the working model of network marketing strategy which helps business in creating effective product promotion. Key components are lead generation, recruitment, training and development. Showcasing this set of slides titled Multi Level Network Marketing Revenue Download Pdf. The topics addressed in these templates are Affiliate Marketing, Levels Of Sales, Commission. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide provides the working model of network marketing strategy which helps business in creating effective product promotion. Key components are lead generation, recruitment, training and development.
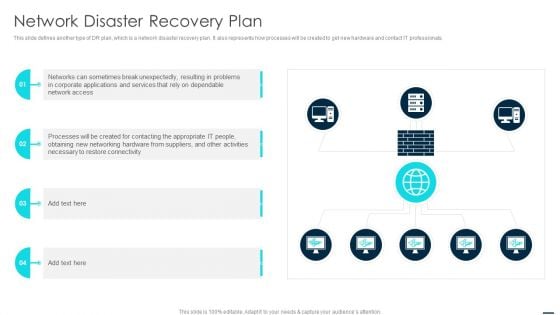
Technology Disaster Recovery Plan Network Disaster Recovery Plan Diagrams PDF
This slide defines another type of DR plan, which is a network disaster recovery plan. It also represents how processes will be created to get new hardware and contact IT professionals. Presenting Technology Disaster Recovery Plan Network Disaster Recovery Plan Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Networking, Services, Corporate Applications. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Business PowerPoint Templates Download Process Chiropractic Plan
We present our business powerpoint templates download process chiropractic plan.Download and present our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Use our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Download our Shapes PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level. Use our Metaphors-Visual Concepts PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan.Use these PowerPoint slides for presentations relating to business, chart, collaborate, colorful, colors, commerce, concept, data, development, direction, economic, forward, graph, graphics, growing, growth, illustration, improvement, interaction, lead, leadership, line, manage, management, networking, object, organization, organize, performance, race, relation, relationship, resources, results, sales, same, staff, team, together. The prominent colors used in the PowerPoint template are Yellow, Green, Blue. We assure you our business powerpoint templates download process chiropractic plan will help them to explain complicated concepts. People tell us our collaborate PowerPoint templates and PPT Slides will make you look like a winner. Customers tell us our business powerpoint templates download process chiropractic plan will make the presenter successul in his career/life. Presenters tell us our collaborate PowerPoint templates and PPT Slides will impress their bosses and teams. People tell us our business powerpoint templates download process chiropractic plan are the best it can get when it comes to presenting. We assure you our colors PowerPoint templates and PPT Slides will impress their bosses and teams. Remove confusionswith our Business PowerPoint Templates Download Process Chiropractic Plan. You'll deliver your best presentation yet.

Uniformed Security Our Equipments Used For Security Guard Services Proposal Template PDF
Deliver an awe inspiring pitch with this creative uniformed security our equipments used for security guard services proposal template pdf bundle. Topics like surveillance technology and software, security trailers, vehicles, cameras, mobile phones can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
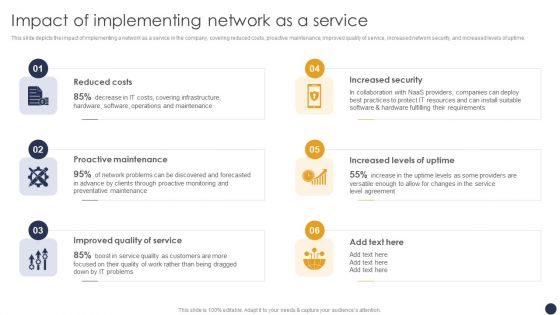
Integrating Naas Service Model Impact Of Implementing Network As A Service Ppt Slides Ideas PDF
This slide depicts the impact of implementing a network as a service in the company, covering reduced costs, proactive maintenance, improved quality of service, increased network security, and increased levels of uptime. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integrating Naas Service Model Impact Of Implementing Network As A Service Ppt Slides Ideas PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Essential Ethics Related To Network Marketing Industry Multi Level Marketing Mockup Pdf
This slide represents key ethics to be followed during network marketing by members and organizations. It includes no promotion of multiple MLM, no cross recruitment, use of clean tactics and flow of same information. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Essential Ethics Related To Network Marketing Industry Multi Level Marketing Mockup Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Essential Ethics Related To Network Marketing Industry Multi Level Marketing Mockup Pdf This slide represents key ethics to be followed during network marketing by members and organizations. It includes no promotion of multiple MLM, no cross recruitment, use of clean tactics and flow of same information.
Ppt Yellow Animated Text Cycle Network Diagram PowerPoint Template Templates
PPT yellow animated text cycle network diagram powerpoint template Templates-Use this Circular diagram to show activities that are related to the business plan metrics and monitor the results to determine if the business plan is proceeding as planned.-PPT yellow animated text cycle network diagram powerpoint template Templates-Abstract, Blank, Business, Chart, Circular, Circulation, Cycle, Design, Diagram, Empty, Executive, Icon, Illustration, Management, Model, Numbers, Organization, Procedure, Process Recognize your calling with our Ppt Yellow Animated Text Cycle Network Diagram PowerPoint Template Templates. Download without worries with our money back guaranteee.
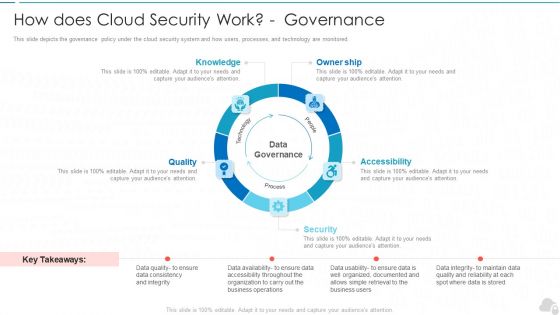
How Does Cloud Security Work Governance Cloud Computing Security IT Ppt Layouts Structure PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a how does cloud security work governance cloud computing security it ppt layouts structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like knowledge, owner ship, quality, security, accessibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
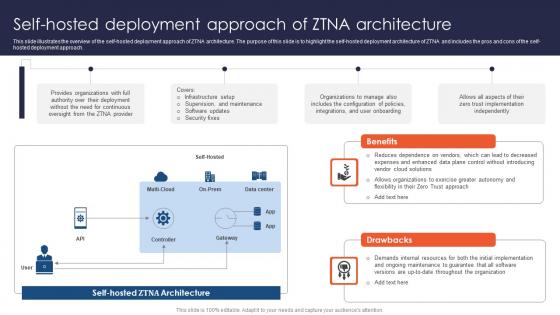
Zero Trust Network Access Self Hosted Deployment Approach Of ZTNA Architecture
This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach. Present like a pro with Zero Trust Network Access Self Hosted Deployment Approach Of ZTNA Architecture. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach.

Business Model Canvas Cloud Networking Service Provider Business Model BMC SS V
This slide provides the business model canvas of the company. It involves key partners, key activities, USP, customer relationships, customer segments, channels, revenue streams, channels, key resources, cost structure. Find a pre-designed and impeccable Business Model Canvas Cloud Networking Service Provider Business Model BMC SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides the business model canvas of the company. It involves key partners, key activities, USP, customer relationships, customer segments, channels, revenue streams, channels, key resources, cost structure.
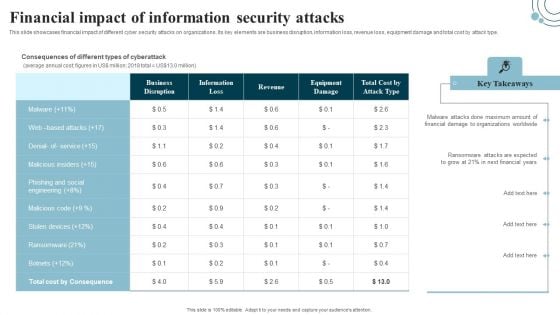
Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Boost your pitch with our creative Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.


 Continue with Email
Continue with Email

 Home
Home


































