Data Risk Management
Cyber Security Implementation Framework Determining Roles And Responsibilities For Risk Handling Icons PDF
Presenting this set of slides with name cyber security implementation framework determining roles and responsibilities for risk handling icons pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
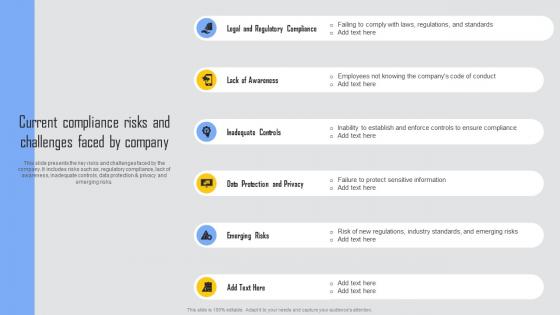
Current Compliance Risks Managing Risks And Establishing Trust Through Efficient Demonstration Pdf
This slide presents the key risks and challenges faced by the company. It includes risks such as, regulatory compliance, lack of awareness, inadequate controls, data protection and privacy and emerging risks. The Current Compliance Risks Managing Risks And Establishing Trust Through Efficient Demonstration Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide presents the key risks and challenges faced by the company. It includes risks such as, regulatory compliance, lack of awareness, inadequate controls, data protection and privacy and emerging risks.
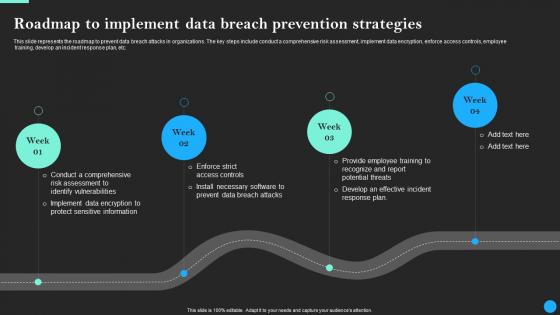
Roadmap To Implement Data Breach Prevention Strategies Rules Pdf
Create an editable Roadmap To Implement Data Breach Prevention Strategies Rules Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Roadmap To Implement Data Breach Prevention Strategies Rules Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the roadmap to prevent data breach attacks in organizations. The key steps include conduct a comprehensive risk assessment, implement data encryption, enforce access controls, employee training, develop an incident response plan, etc.
Security Risk Assessment Icon With Magnifying Glass Ppt PowerPoint Presentation File Templates PDF
Presenting this set of slides with name security risk assessment icon with magnifying glass ppt powerpoint presentation file templates pdf. This is a three stage process. The stages in this process are security risk assessment icon with magnifying glass. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icon Of Macroeconomic Analysis Illustrating Risk Reduction In Economy Formats PDF
Presenting Icon Of Macroeconomic Analysis Illustrating Risk Reduction In Economy Formats PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Icon Of Macroeconomic Analysis Illustrating Risk Reduction In Economy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Identifying Risk In Business Bar Graph Vector Icon Ppt PowerPoint Presentation Icon Show PDF
Presenting this set of slides with name identifying risk in business bar graph vector icon ppt powerpoint presentation icon show pdf. This is a three stage process. The stages in this process are identifying risk in business bar graph vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Practices In Consumer Risk Assessment And Rating Ppt Ideas Vector PDF
This slide showcases the best practices for customer risk assessment and rating. It includes effective and efficient risk rating models such as channel, geography, products, customer, transaction and potential external high risk. Presenting Best Practices In Consumer Risk Assessment And Rating Ppt Ideas Vector PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Customer Risk Rating, Channel, Geography. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Project Risk Identification Vector Icon Ppt PowerPoint Presentation Portfolio Picture PDF
Persuade your audience using this project risk identification vector icon ppt powerpoint presentation portfolio picture pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including project risk identification vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
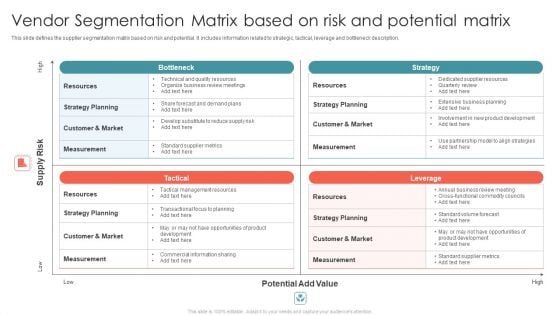
Vendor Segmentation Matrix Based On Risk And Potential Matrix Ppt Model Slide PDF
This slide defines the supplier segmentation matrix based on risk and potential. It includes information related to strategic, tactical, leverage and bottleneck description. Presenting Vendor Segmentation Matrix Based On Risk And Potential Matrix Ppt Model Slide PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Supply Risk, Potential Add Value, High. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Macroeconomic Analysis Icon Depicting Risk Impact On National Business Infographics PDF
Presenting Macroeconomic Analysis Icon Depicting Risk Impact On National Business Infographics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Macroeconomic Analysis Icon Depicting Risk Impact On National Business. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Software Risk Assessment Report Icon Ppt PowerPoint Presentation File Outfit PDF
Presenting Software Risk Assessment Report Icon Ppt PowerPoint Presentation File Outfit PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Software Risk Assessment Report Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
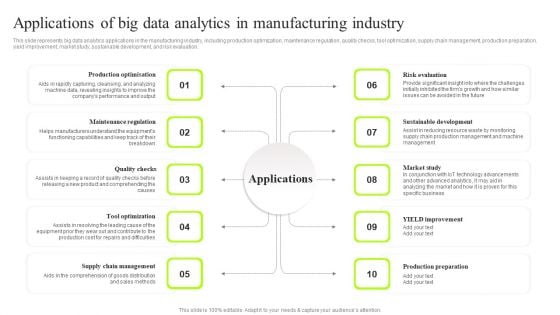
Applications Of Big Data Analytics In Manufacturing Industry Sample PDF
This slide represents big data analytics applications in the manufacturing industry, including production optimization, maintenance regulation, quality checks, tool optimization, supply chain management, production preparation, yield improvement, market study, sustainable development, and risk evaluation. This modern and well-arranged Applications Of Big Data Analytics In Manufacturing Industry Sample PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
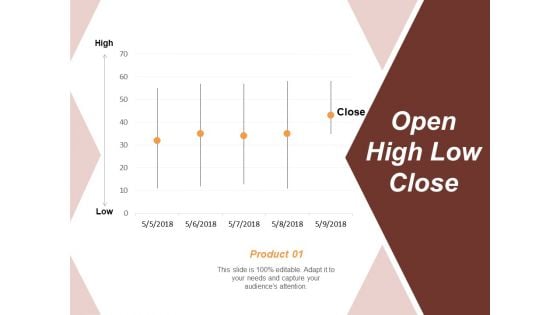
Open High Low Close Risk Estimator Ppt PowerPoint Presentation Infographics Vector
This is a open high low close risk estimator ppt powerpoint presentation infographics vector. This is a five stage process. The stages in this process are business, management, strategy, analysis, marketing.
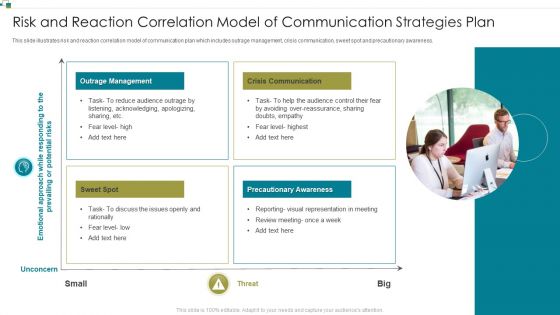
Risk And Reaction Correlation Model Of Communication Strategies Plan Information PDF
This slide illustrates risk and reaction correlation model of communication plan which includes outrage management, crisis communication, sweet spot and precautionary awareness. Presenting Risk And Reaction Correlation Model Of Communication Strategies Plan Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Outrage Management, Crisis Communication, Precautionary Awareness. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
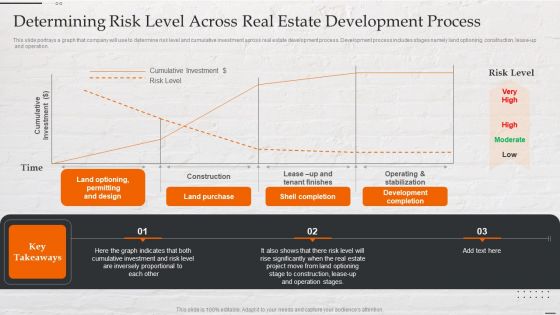
Capital Investment Options Determining Risk Level Across Real Estate Development Formats PDF
This slide portrays a graph that company will use to determine risk level and cumulative investment across real estate development process. Development process includes stages namely land optioning, construction, lease-up and operation. Presenting Capital Investment Options Determining Risk Level Across Real Estate Development Formats PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cumulative Investment, Risk Level, Construction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Impact And Probability Analysis Template 1 Ppt PowerPoint Presentation Infographics Templates
This is a risk impact and probability analysis template 1 ppt powerpoint presentation infographics templates. This is a three stage process. The stages in this process are low, medium, high, cost, time, quality.
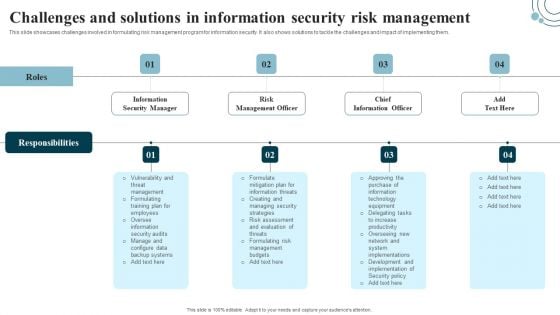
Developing IT Security Strategy Challenges And Solutions In Information Security Risk Pictures PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. Welcome to our selection of the Developing IT Security Strategy Challenges And Solutions In Information Security Risk Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
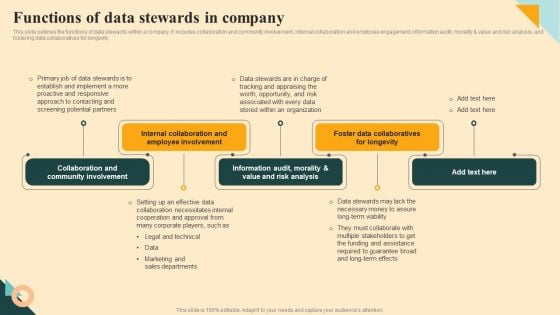
Functions Of Data Stewards In Company Themes PDF
This slide outlines the functions of data stewards within a company. It includes collaboration and community involvement, internal collaboration and employee engagement, information audit, morality and value and risk analysis, and fostering data collaboratives for longevity. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Functions Of Data Stewards In Company Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Functions Of Data Stewards In Company Themes PDF.
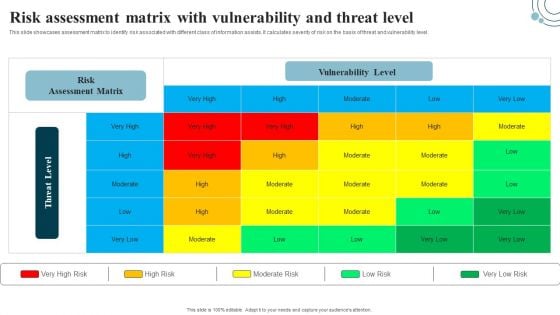
Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF
This slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. This Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
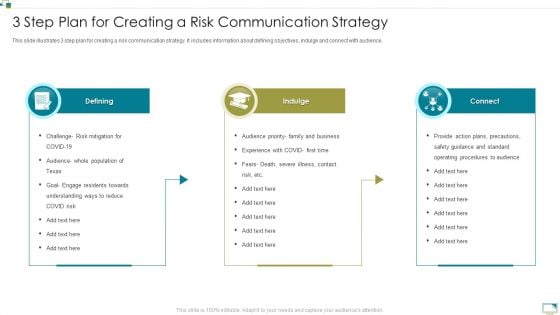
3 Step Plan For Creating A Risk Communication Strategy Demonstration PDF
This slide illustrates 3 step plan for creating a risk communication strategy. It includes information about defining objectives, indulge and connect with audience. Presenting 3 Step Plan For Creating A Risk Communication Strategy Demonstration PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Defining, Indulge, Connect. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
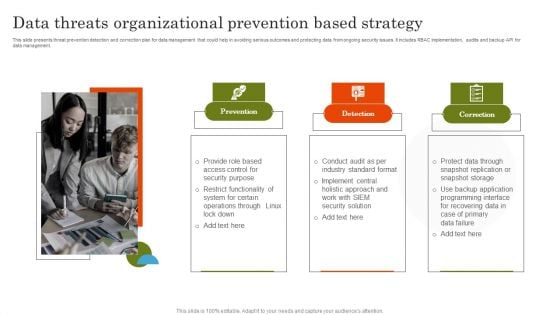
Data Threats Organizational Prevention Based Strategy Infographics PDF
This slide presents threat prevention detection and correction plan for data management that could help in avoiding serious outcomes and protecting data from ongoing security issues. It includes RBAC implementation, audits and backup API for data management. Increase audience engagement and knowledge by dispensing information using Data Threats Organizational Prevention Based Strategy Infographics PDF. This template helps you present information on three stages. You can also present information on Prevention, Detection, Correction using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
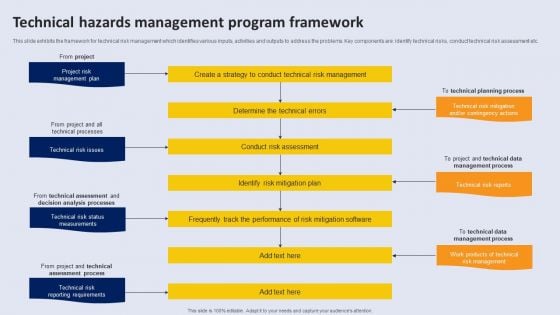
Technical Hazards Management Program Framework Themes PDF
This slide exhibits the framework for technical risk management which identifies various inputs, activities and outputs to address the problems. Key components are identify technical risks, conduct technical risk assessment etc.Pitch your topic with ease and precision using this Technical Hazards Management Program Framework Themes PDF. This layout presents information on Project Risk Management Plan, Determine The Technical Errors. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Exit Strategy Big Data Analytics Investor Funding Elevator Pitch Deck
This slide displays the exit strategy of the organization which helps in reducing risk. These strategies include merger and acquisition, management buyout, and initial public offering. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Exit Strategy Big Data Analytics Investor Funding Elevator Pitch Deck will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide displays the exit strategy of the organization which helps in reducing risk. These strategies include merger and acquisition, management buyout, and initial public offering.
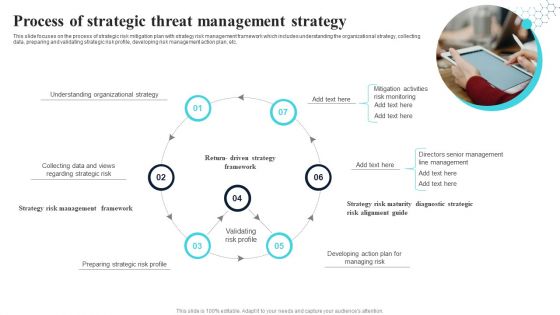
Process Of Strategic Threat Management Strategy Themes PDF
This slide focuses on the process of strategic risk mitigation plan with strategy risk management framework which includes understanding the organizational strategy, collecting data, preparing and validating strategic risk profile, developing risk management action plan, etc. Presenting Process Of Strategic Threat Management Strategy Themes PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Risk Alignment Guide, Strategy Risk Management Framework, Strategy Risk Maturity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
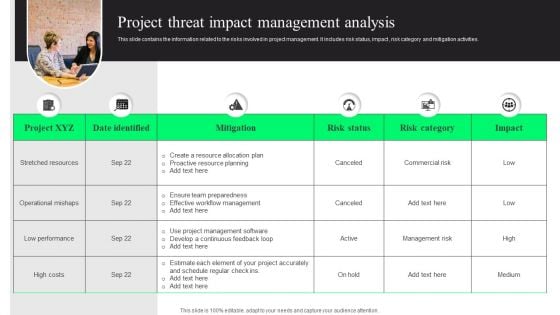
Project Threat Impact Management Analysis Portrait PDF
This slide contains the information related to the risks involved in project management. It includes risk status, impact , risk category and mitigation activities. Persuade your audience using this Project Threat Impact Management Analysis Portrait PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Low Performance, Stretched Resources, Risk Category. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
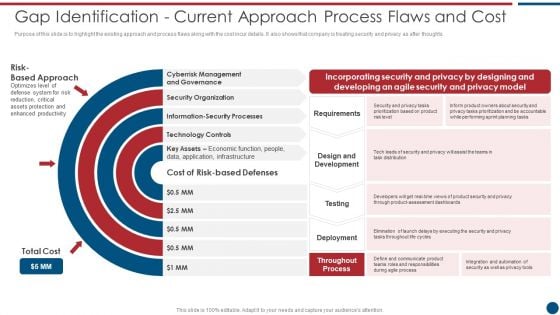
Gap Identification Current Approach Process Flaws And Cost Risk Based Procedures To IT Security Topics PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. This is a Gap Identification Current Approach Process Flaws And Cost Risk Based Procedures To IT Security Topics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cyberrisk Management, Security Organization, Formation Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Plan And Frame Problem Collect The Data Ppt Sample
This is a plan and frame problem collect the data ppt sample. This is a four stage process. The stages in this process are business, marketing, success.

Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. This is a Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Major Components, Criticality Rating, Failure Cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
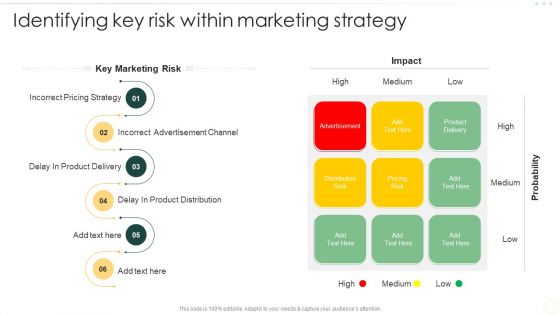
Effective Organizational B2B And B2C Identifying Key Risk Within Marketing Strategy Inspiration PDF
This Effective Organizational B2B And B2C Identifying Key Risk Within Marketing Strategy Inspiration PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Table Of Contents For Big Data Engineer Brochure PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For Big Data Engineer Brochure PDF. Use them to share invaluable insights on Provider Company, Management Problems, Technologies Strategies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
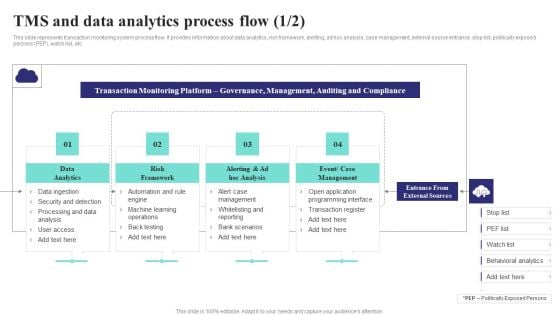
Formulating Money Laundering Tms And Data Analytics Process Flow Sample PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Formulating Money Laundering Tms And Data Analytics Process Flow Sample PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Formulating Money Laundering Tms And Data Analytics Process Flow Sample PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Deploying Banking Transaction Tms And Data Analytics Process Flow Designs PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. Get a simple yet stunning designed Deploying Banking Transaction Tms And Data Analytics Process Flow Designs PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Deploying Banking Transaction Tms And Data Analytics Process Flow Designs PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
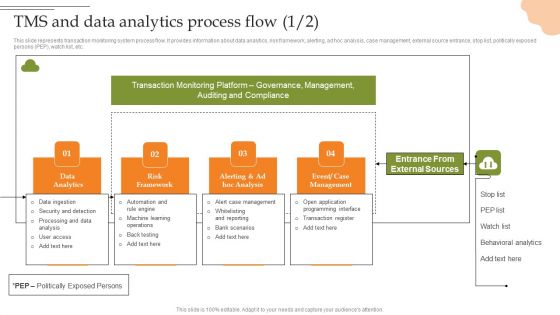
Creating Transaction Monitoring TMS And Data Analytics Process Flow Elements PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. Create an editable Creating Transaction Monitoring TMS And Data Analytics Process Flow Elements PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Creating Transaction Monitoring TMS And Data Analytics Process Flow Elements PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
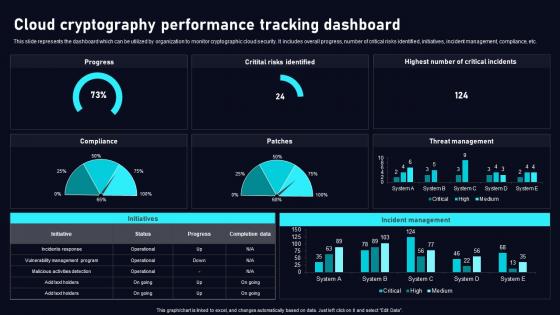
Cloud Cryptography Performance Cloud Data Security Using Cryptography Sample Pdf
This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Cloud Cryptography Performance Cloud Data Security Using Cryptography Sample Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc.
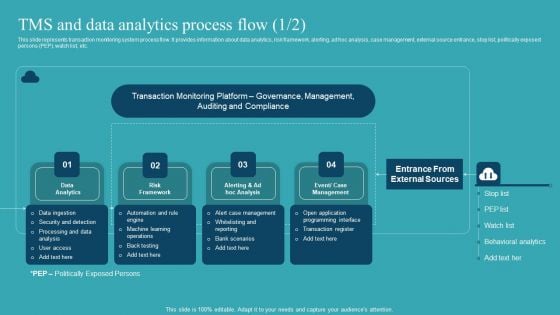
Integrating AML And Transaction Tms And Data Analytics Process Flow Designs PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Integrating AML And Transaction Tms And Data Analytics Process Flow Designs PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
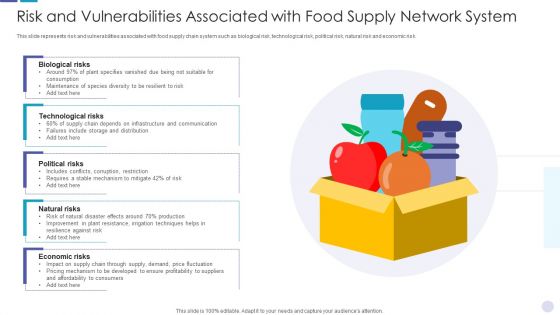
Risk And Vulnerabilities Associated With Food Supply Network System Information PDF
This slide represents risk and vulnerabilities associated with food supply chain system such as biological risk, technological risk, political risk, natural risk and economic risk. Presenting risk and vulnerabilities associated with food supply network system information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including biological risks, technological risks, political risks, natural risks, economic risks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Steps Of Project Risk Assessment With Icons Ppt PowerPoint Presentation Show Information PDF
Presenting steps of project risk assessment with icons ppt powerpoint presentation show information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identify risk, risk analysis, risk evaluation, risk treatment, risk review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
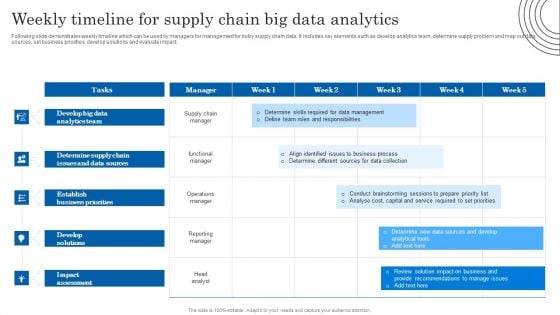
Weekly Timeline For Supply Chain Big Data Analytics Introduction PDF
Following slide demonstrates weekly timeline which can be used by managers for management for bulky supply chain data. It includes key elements such as develop analytics team, determine supply problem and map out data sources, set business priorities, develop solutions and evaluate impact. Pitch your topic with ease and precision using this Weekly Timeline For Supply Chain Big Data Analytics Introduction PDF. This layout presents information on Determine Supply Chain, Data Sources, Analytics Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Six Step Data Analytic Strategy For Business Transformation Download PDF
This slide covers role of data analytics in six steps for transformation of business. It includes acquire customers, transform financial process, create business models, optimize operations, manage risks and maximise insights. Persuade your audience using this Six Step Data Analytic Strategy For Business Transformation Download PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Transform Financial Process, Acquire Customers, Create Business Models. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
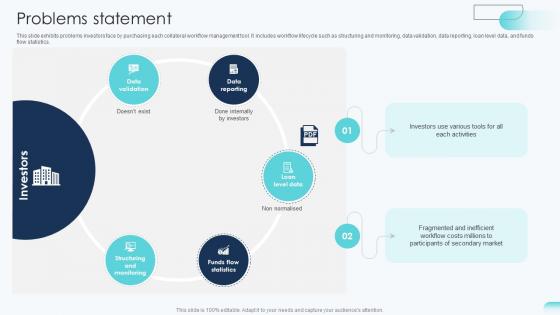
Problems Statement Big Data Analytics Investor Funding Elevator Pitch Deck
This slide exhibits problems investors face by purchasing each collateral workflow management tool. It includes workflow lifecycle such as structuring and monitoring, data validation, data reporting, loan level data, and funds flow statistics. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problems Statement Big Data Analytics Investor Funding Elevator Pitch Deck was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problems Statement Big Data Analytics Investor Funding Elevator Pitch Deck. This slide exhibits problems investors face by purchasing each collateral workflow management tool. It includes workflow lifecycle such as structuring and monitoring, data validation, data reporting, loan level data, and funds flow statistics.
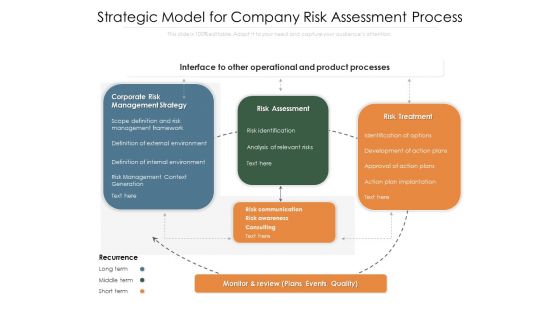
Strategic Model For Company Risk Assessment Process Ppt PowerPoint Presentation Inspiration Maker PDF
Presenting strategic model for company risk assessment process ppt powerpoint presentation inspiration maker pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including corporate risk management strategy, risk assessment, risk treatment, risk communication, recurrence, monitor and review, plans, events, quality. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Privacy IT Data Privacy In Healthcare Designs PDF
This slide represents data privacy in the healthcare industry, decreasing risks and keeping the business operations functioning. This is a information privacy it data privacy in healthcare designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data privacy in healthcare. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Computer Security Incident Handling Determining Roles And Responsibilities For Risk Handling Mockup PDF
Presenting this set of slides with name computer security incident handling determining roles and responsibilities for risk handling mockup pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Issues Which Leads To Insolvency Risk Identification In Bankruptcy Guidelines PDF
Presenting this set of slides with name issues which leads to insolvency risk identification in bankruptcy guidelines pdf. This is a four stage process. The stages in this process are market risk, credit risk, liquidity risk, employee layoff. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
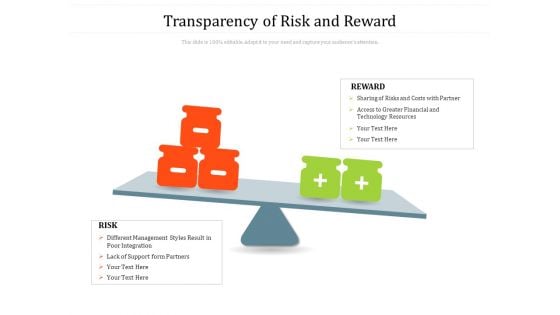
Transparency Of Risk And Reward Ppt PowerPoint Presentation Infographics Skills PDF
Presenting this set of slides with name transparency of risk and reward ppt powerpoint presentation infographics skills pdf. This is a two stage process. The stages in this process are risk, reward, different management styles result in poor integration, lack of support form partners, sharing of risks and costs with partner, access to greater financial and technology resources. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
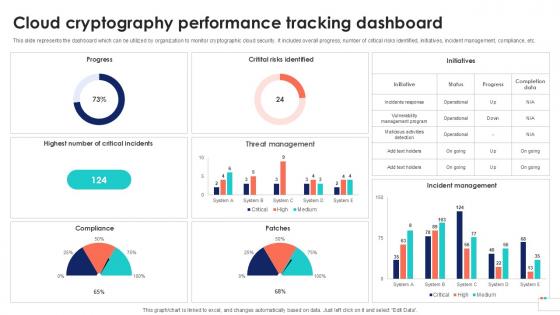
Cloud Cryptography Performance Data Security In Cloud Computing Ppt Presentation
This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Cloud Cryptography Performance Data Security In Cloud Computing Ppt Presentation is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cloud Cryptography Performance Data Security In Cloud Computing Ppt Presentation and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc.
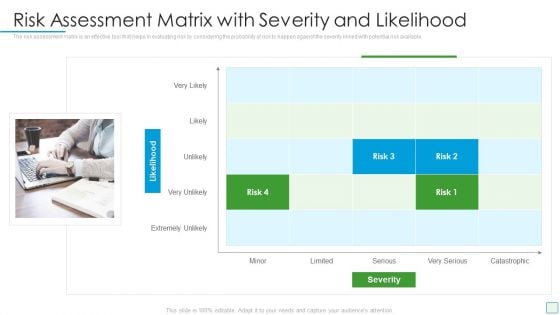
Developing Firm Security Strategy Plan Risk Assessment Matrix With Severity And Likelihood Portrait PDF
The risk assessment matrix is an effective tool that helps in evaluating risk by considering the probability of risk to happen against the severity linked with potential risk available. This is a developing firm security strategy plan risk assessment matrix with severity and likelihood portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment matrix with severity and likelihood. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
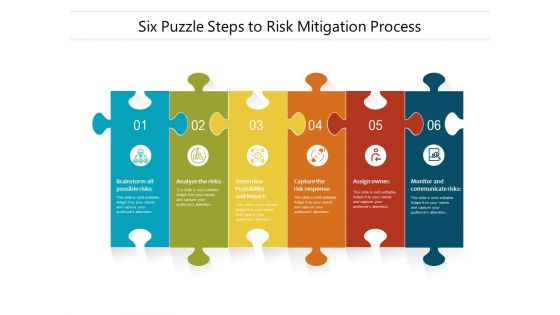
Six Puzzle Steps To Risk Mitigation Process Ppt PowerPoint Presentation File Example PDF
Presenting six puzzle steps to risk mitigation process ppt powerpoint presentation file example pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including brainstorm all possible risks, analyze the risks, determine probability, capture the risk response, assign owner, monitor and communicate risks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security For Your Organization Determining Roles And Responsibilities For Risk Handling Ppt Outline Example PDF
Presenting this set of slides with name cyber security for your organization determining roles and responsibilities for risk handling ppt outline example pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management, executive, line management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Data Encryption Performance Tracking Client Side Encryption PPT Presentation
This slide represents the dashboard which can be utilized by organization to monitor cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Data Encryption Performance Tracking Client Side Encryption PPT Presentation is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Encryption Performance Tracking Client Side Encryption PPT Presentation and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the dashboard which can be utilized by organization to monitor cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, patches, highest number of critical incidents, etc.

Workplace Portable Device Monitoring And Administration Determining Roles And Responsibilities For Risk Handling Designs PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. This modern and well arranged Workplace Portable Device Monitoring And Administration Determining Roles And Responsibilities For Risk Handling Designs PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide
This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc. Find highly impressive Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc.

Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf
This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi tenancy, cloud provider vulnerability, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi tenancy, cloud provider vulnerability, etc.
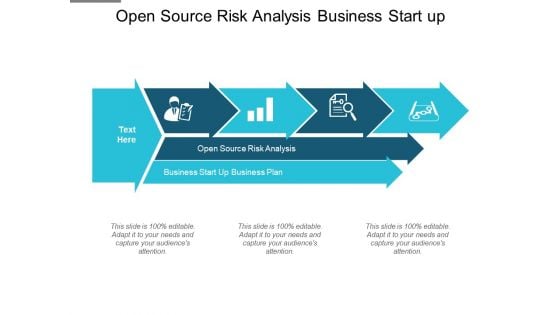
Open Source Risk Analysis Business Start Up Business Plan Ppt PowerPoint Presentation Styles Elements
This is a open source risk analysis business start up business plan ppt powerpoint presentation styles elements. This is a four stage process. The stages in this process are open source risk analysis, business start up business plan.

Staff Opinion Survey Risk Asset Allocation Security Development Ppt PowerPoint Presentation Model Design Ideas
This is a staff opinion survey risk asset allocation security development ppt powerpoint presentation model design ideas. This is a four stage process. The stages in this process are staff opinion survey, risk asset allocation, security development.
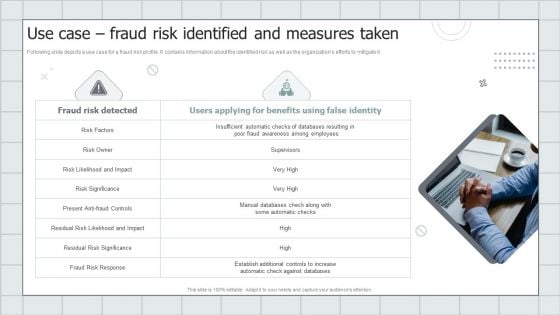
Fraud Avoidance Playbook Use Case Fraud Risk Identified And Measures Taken Infographics PDF
Following slide depicts a use case for a fraud risk profile. It contains information about the identified risk as well as the organizations efforts to mitigate it. Presenting Fraud Avoidance Playbook Use Case Fraud Risk Identified And Measures Taken Infographics PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Risk Owner, Risk Significance, Awareness. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Risk Identification And Assessment Process With Icons Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting risk identification and assessment process with icons ppt powerpoint presentation gallery graphics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including risk mitigation, implementing, risk strategy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
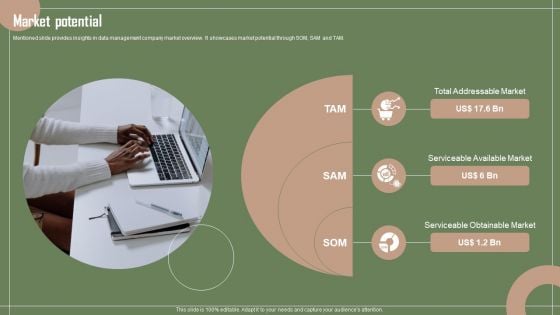
Data Automation Solution Investor Funding Presentation Market Potential Formats PDF
Mentioned slide provides insights in data management company market overview. It showcases market potential through SOM, SAM and TAM. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Data Automation Solution Investor Funding Presentation Market Potential Formats PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
Analyzing Business Risk With Statistical Graph Icon Ppt PowerPoint Presentation Outline Portfolio PDF
Presenting this set of slides with name analyzing business risk with statistical graph icon ppt powerpoint presentation outline portfolio pdf. This is a one stage process. The stage in this process is analyzing business risk with statistical graph icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
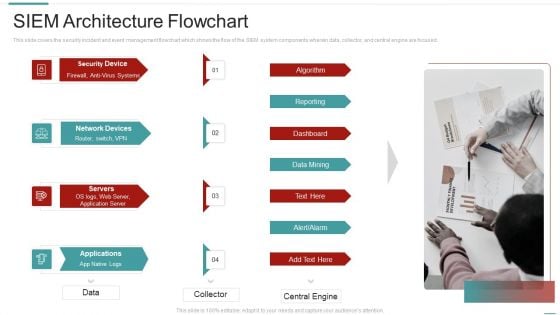
Risk Recognition Automation Siem Architecture Flowchart Ppt Summary Example File PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Presenting risk recognition automation siem architecture flowchart ppt summary example file pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reporting, dashboard, data mining, algorithm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































