Data Security And Protection
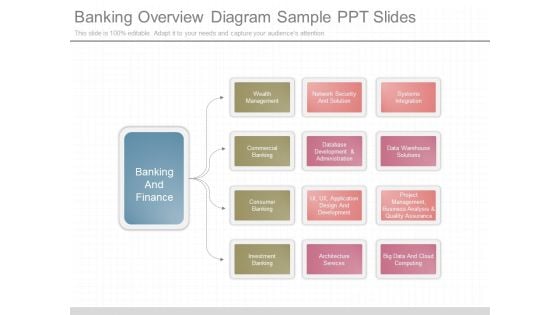
Banking Overview Diagram Sample Ppt Slides
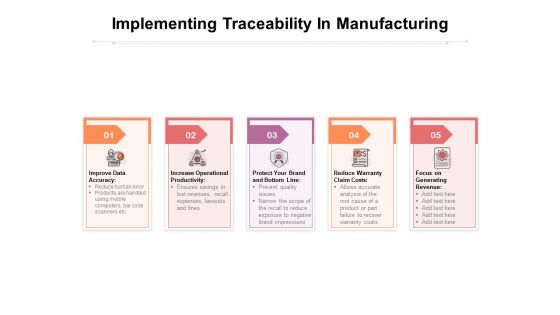
Implementing Traceability In Manufacturing Ppt PowerPoint Presentation Inspiration Example Topics PDF
Presenting this set of slides with name implementing traceability in manufacturing ppt powerpoint presentation inspiration example topics pdf. This is a five stage process. The stages in this process are improve data accuracy, increase operational productivity, protect your brand and bottom line reduce warranty claim costs, focus on generating revenue. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
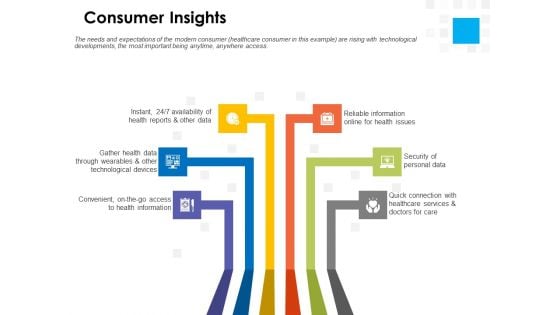
Digital Transformation Strategy Roadmap Consumer Insights Ppt PowerPoint Presentation Layouts Design Inspiration PDF
Presenting this set of slides with name digital transformation strategy roadmap consumer insights ppt powerpoint presentation layouts design inspiration pdf. This is a six stage process. The stages in this process are convenient access, health information, quick connection, healthcare services, security personal data, reliable information online health issues, health reports, gather health data through wearables, technological devices. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
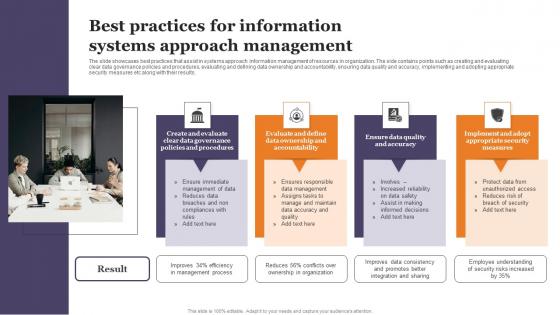
Best Practices For Information Systems Approach Management Professional Pdf
The slide showcases best practices that assist in systems approach information management of resources in organization. The side contains points such as creating and evaluating clear data governance policies and procedures, evaluating and defining data ownership and accountability, ensuring data quality and accuracy, implementing and adopting appropriate security measures etc along with their results. Showcasing this set of slides titled Best Practices For Information Systems Approach Management Professional Pdf The topics addressed in these templates are Policies And Procedures, Ownership And Accountability, Security Measures All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases best practices that assist in systems approach information management of resources in organization. The side contains points such as creating and evaluating clear data governance policies and procedures, evaluating and defining data ownership and accountability, ensuring data quality and accuracy, implementing and adopting appropriate security measures etc along with their results.
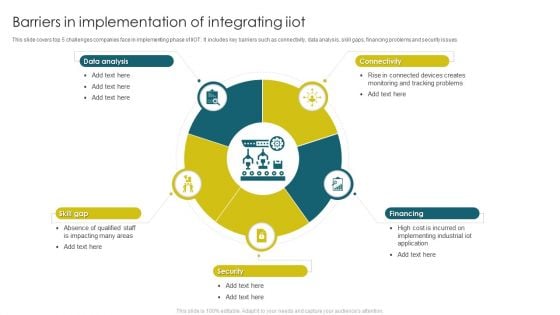
Barriers In Implementation Of Integrating Iiot Infographics PDF
This slide covers top 5 challenges companies face in implementing phase of IIOT. It includes key barriers such as connectivity, data analysis, skill gaps, financing problems and security issues. Presenting Barriers In Implementation Of Integrating Iiot Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Data Analysis, Connectivity, Financing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Six Steps Of Concept Of Risk Management Framework Introduction Professional PDF
Presenting Six Steps Of Concept Of Risk Management Framework Introduction Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Information System Categorization, Security Control Selection, Security Control Implementation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
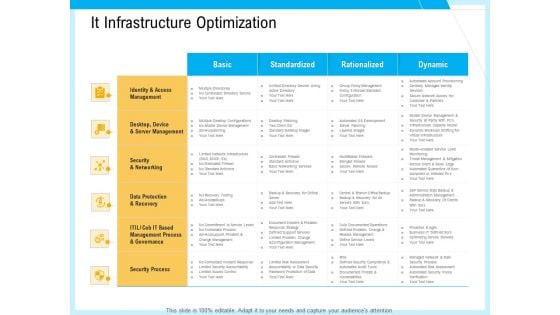
IT And Cloud Facilities Management It Infrastructure Optimization Ppt Model Slide PDF
Deliver an awe-inspiring pitch with this creative it and cloud facilities management it infrastructure optimization ppt model slide pdf bundle. Topics like standardized, rationalized, dynamic, identity and access management, security and networking, security process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
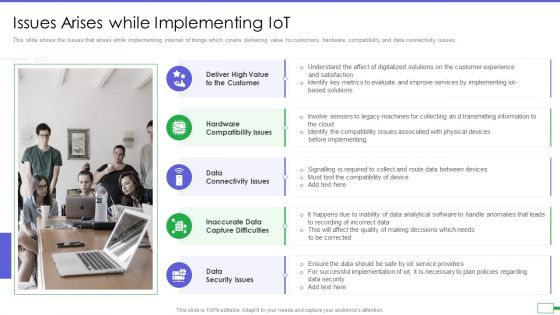
Iot And Digital Twin To Reduce Costs Post Covid Issues Arises While Implementing Iot Themes PDF
This slide shows the issues that arises while implementing internet of things which covers delivering value to customers, hardware compatibility and data connectivity issues. Presenting iot and digital twin to reduce costs post covid issues arises while implementing iot themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like high value to the customer, hardware compatibility issues, data connectivity issues, inaccurate data capture difficulties, data security issues. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
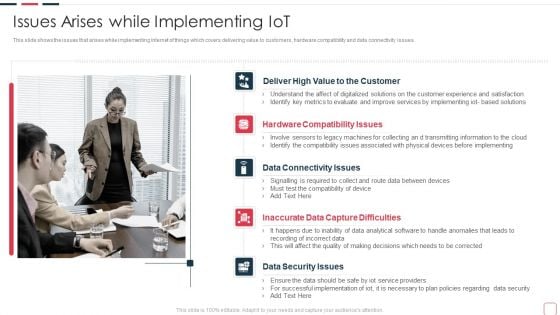
Price Benefit Internet Things Digital Twins Execution After Covid Issues Arises While Implementing Slides PDF
This slide shows the issues that arises while implementing internet of things which covers delivering value to customers, hardware compatibility and data connectivity issues. This is a price benefit internet things digital twins execution after covid issues arises while implementing slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data connectivity issues, inaccurate data capture difficulties, data security issues. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
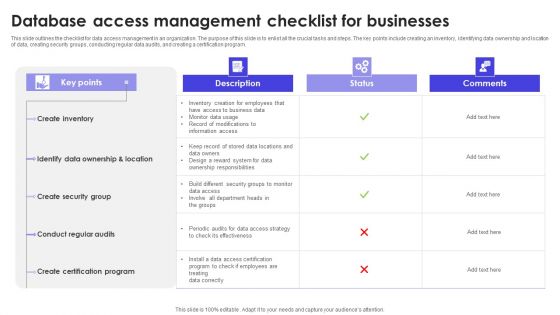
Database Access Management Checklist For Businesses Formats PDF
This slide outlines the checklist for data access management in an organization. The purpose of this slide is to enlist all the crucial tasks and steps. The key points include creating an inventory, identifying data ownership and location of data, creating security groups, conducting regular data audits, and creating a certification program. Showcasing this set of slides titled Database Access Management Checklist For Businesses Formats PDF. The topics addressed in these templates are Description, Status, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
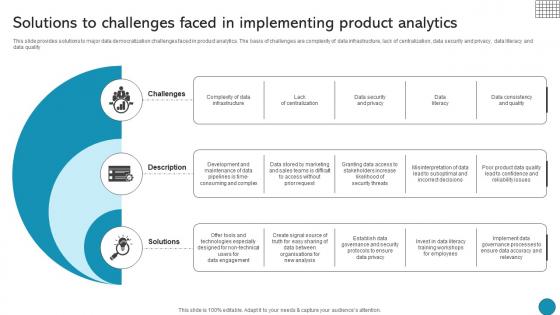
Solutions To Challenges Faced In Implementing Product Driving Business Success Integrating Product
This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality If you are looking for a format to display your unique thoughts, then the professionally designed Solutions To Challenges Faced In Implementing Product Driving Business Success Integrating Product is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Solutions To Challenges Faced In Implementing Product Driving Business Success Integrating Product and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality

Zero Trust Network Access User Flow Overview Ppt File Deck
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. The Zero Trust Network Access User Flow Overview Ppt File Deck is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
Business Diagram Magnifying Glass With Puzzle Pieces Slide Presentation Template
This business plan power point template has been designed with graphic of lock which is made by puzzles pieces and with one missing puzzle. This PPT contains the concept of security and solution development. Add this PPT in your presentations and display solution and security related topics.
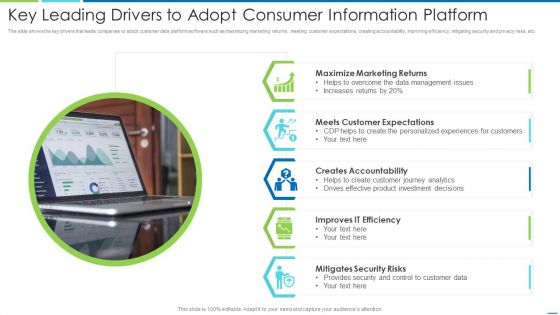
Key Leading Drivers To Adopt Consumer Information Platform Information PDF
This slide shows the key drivers that leads companies to adopt customer data platform software such as maximizing marketing returns, ,meeting customer expectations, creating accountability, improving efficiency, mitigating security and privacy risks, etc. Presenting key leading drivers to adopt consumer information platform information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including maximize marketing returns, meets customer expectations, creates accountability, improves it efficiency, mitigates security risks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
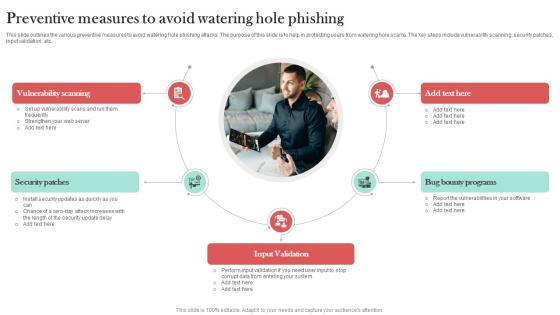
Preventive Measures To Avoid Watering Man In The Middle Phishing IT
This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc. Present like a pro with Preventive Measures To Avoid Watering Man In The Middle Phishing IT. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc.
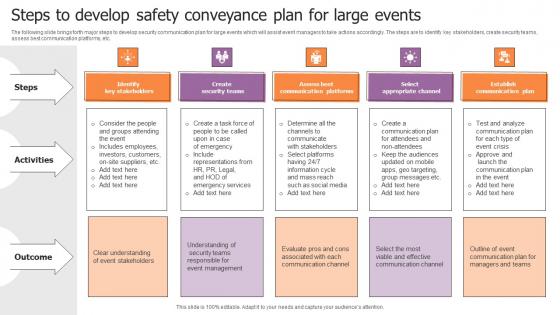
Steps To Develop Safety Conveyance Plan For Large Events Designs Pdf
The following slide brings forth major steps to develop security communication plan for large events which will assist event managers to take actions accordingly. The steps are to identify key stakeholders, create security teams, assess best communication platforms, etc. Showcasing this set of slides titled Steps To Develop Safety Conveyance Plan For Large Events Designs Pdf. The topics addressed in these templates are Identify Key Stakeholders, Create Security Teams, Select Appropriate Channel. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide brings forth major steps to develop security communication plan for large events which will assist event managers to take actions accordingly. The steps are to identify key stakeholders, create security teams, assess best communication platforms, etc.
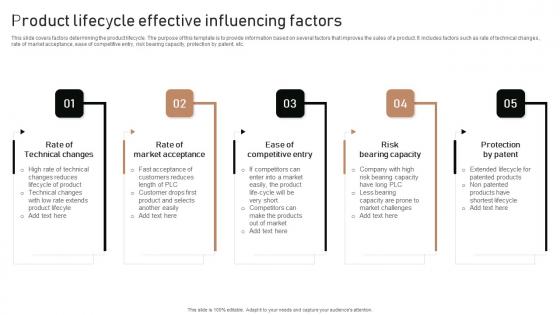
Execution Of Product Lifecycle Product Lifecycle Effective Influencing Factors Guidelines Pdf
This slide covers factors determining the product lifecycle. The purpose of this template is to provide information based on several factors that improves the sales of a product. It includes factors such as rate of technical changes, rate of market acceptance, ease of competitive entry, risk bearing capacity, protection by patent, etc. The Execution Of Product Lifecycle Product Lifecycle Effective Influencing Factors Guidelines Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide covers factors determining the product lifecycle. The purpose of this template is to provide information based on several factors that improves the sales of a product. It includes factors such as rate of technical changes, rate of market acceptance, ease of competitive entry, risk bearing capacity, protection by patent, etc.
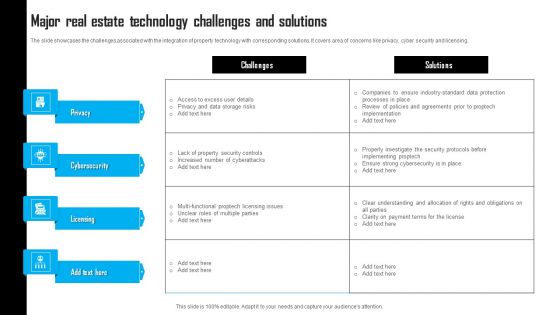
Major Real Estate Technology Challenges And Solutions Template PDF
The slide showcases the challenges associated with the integration of property technology with corresponding solutions. It covers area of concerns like privacy, cyber security and licensing. Pitch your topic with ease and precision using this Major Real Estate Technology Challenges And Solutions Template PDF. This layout presents information on Data Storage Risks, Property Security Controls, Payment Terms. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
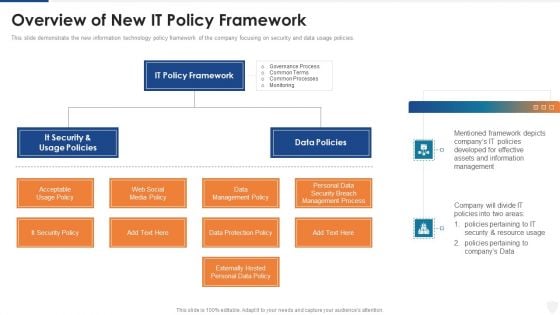
Overview Of New IT Policy Framework Ppt Summary Format Ideas PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting overview of new it policy framework ppt summary format ideas pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like management policy, security breach, information, resource. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Playbook For Enterprise Transformation Administration Digital Transformation Trends We Can Adopt Professional PDF
The following slide displays the key trends that can be adopted by the organization, these trends can impact the transformation journey can help in achieving operational excellence. These trends can be usage of Hyper automation, cyber security tools, usage of AI etc. This is a Playbook For Enterprise Transformation Administration Digital Transformation Trends We Can Adopt Professional PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Deconstruction, Security Tools, Organizations Operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
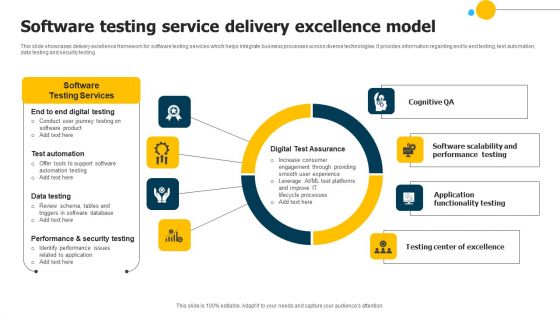
Software Testing Service Delivery Excellence Model Mockup PDF
This slide showcases delivery excellence framework for software testing services which helps integrate business processes across diverse technologies. It provides information regarding end to end testing, test automation, data testing and security testing. Showcasing this set of slides titled Software Testing Service Delivery Excellence Model Mockup PDF. The topics addressed in these templates are Performance Testing, Digital Test Assurance, Security Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
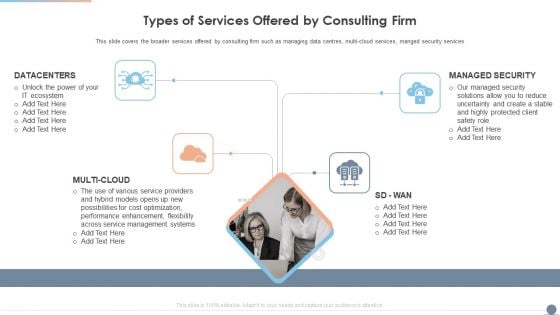
Multi Cloud Complexity Management Types Of Services Offered By Consulting Firm Ideas PDF
This slide covers the broader services offered by consulting firm such as managing data centres, multi cloud services, manged security services. Presenting Multi Cloud Complexity Management Types Of Services Offered By Consulting Firm Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Datacenters, Managed Security, Management Systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
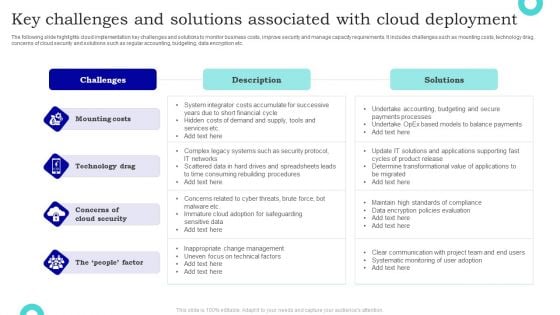
Key Challenges And Solutions Associated With Cloud Deployment Introduction PDF
The following slide highlights cloud implementation key challenges and solutions to monitor business costs, improve security and manage capacity requirements. It includes challenges such as mounting costs, technology drag, concerns of cloud security and solutions such as regular accounting, budgeting, data encryption etc. Pitch your topic with ease and precision using this Key Challenges And Solutions Associated With Cloud Deployment Introduction PDF. This layout presents information on Challenges, Description, Solutions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
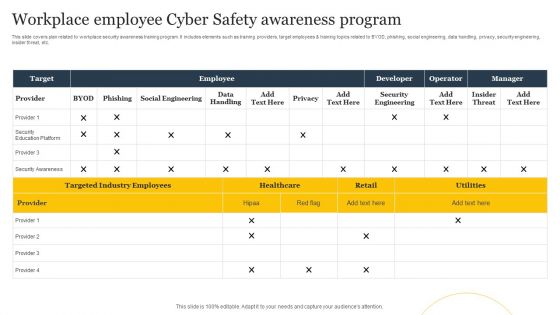
Workplace Employee Cyber Safety Awareness Program Ppt Layouts Slide Portrait PDF
This slide covers plan related to workplace security awareness training program. It includes elements such as training providers, target employees and training topics related to BYOD, phishing, social engineering, data handling, privacy, security engineering, insider threat, etc. Pitch your topic with ease and precision using this Workplace Employee Cyber Safety Awareness Program Ppt Layouts Slide Portrait PDF. This layout presents information on Employee, Target, Developer. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
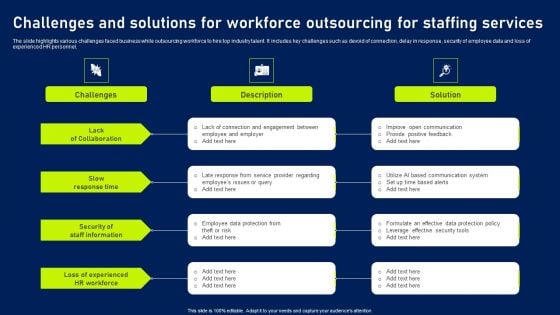
Challenges And Solutions For Workforce Outsourcing For Staffing Services Diagrams PDF
The slide highlights various challenges faced business while outsourcing workforce to hire top industry talent. It includes key challenges such as devoid of connection, delay in response, security of employee data and loss of experienced HR personnel. Presenting Challenges And Solutions For Workforce Outsourcing For Staffing Services Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Lack Collaboration, Slow Response Time, Security Staff Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
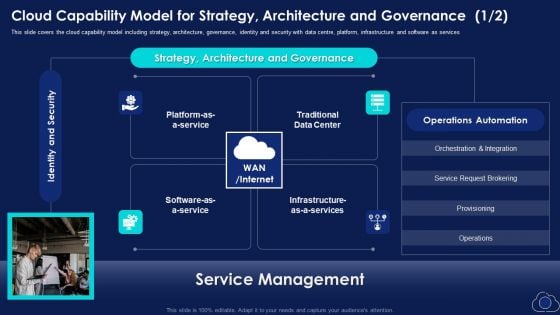
Cloud Capability Model For Strategy Architecture And Governance Elements PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services This is a Cloud Capability Model For Strategy Architecture And Governance Elements PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Request Brokering, Strategy, Identity And Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
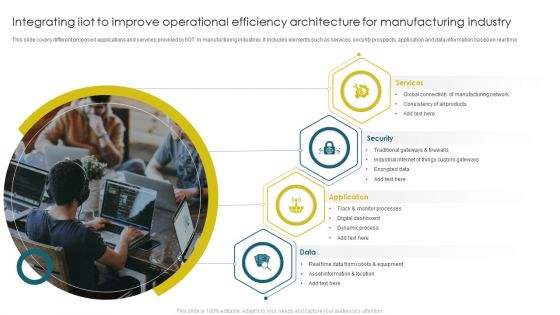
Integrating Iiot To Improve Operational Efficiency Architecture For Manufacturing Industry Microsoft PDF
This slide covers different proposed applications and services provided by IIOT in manufacturing industries. It includes elements such as services, security prospects, application and data information based on real time. Presenting Integrating Iiot To Improve Operational Efficiency Architecture For Manufacturing Industry Microsoft PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security, Services, Application. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
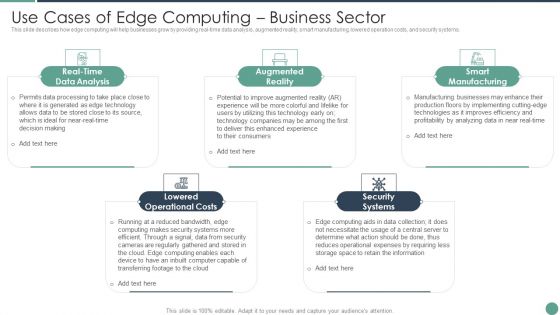
Distributed Computing Use Cases Of Edge Computing Business Sector Themes PDF
This slide describes how edge computing will help businesses grow by providing real-time data analysis, augmented reality, smart manufacturing, lowered operation costs, and security systems.This is a Distributed Computing Use Cases Of Edge Computing Business Sector Themes PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Augmented Reality, Smart Manufacturing, Security Systems You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
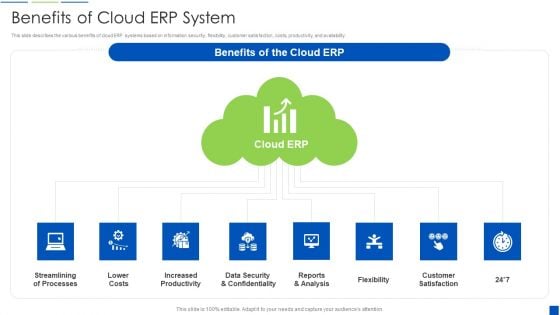
Corporate Resource Planning Benefits Of Cloud ERP System Topics PDF
This slide describes the various benefits of cloud ERP systems based on information security, flexibility, customer satisfaction, costs, productivity, and availability. This is a Corporate Resource Planning Benefits Of Cloud ERP System Topics PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Streamlining Of Processes, Increased Productivity, Data Security And Confidentiality You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Insurance Sales Cycle To Boost Stand Alone Penetration Topics PDF
The following slide highlights insurance sales cycle for cyber security to improve market penetration and reduce security risks and data thefts. It includes components such as attractive price offers or buyers, improve value proposition, training and development and upgrade agent or broker support. Presenting Cyber Insurance Sales Cycle To Boost Stand Alone Penetration Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Broker Support, Development, Proposition. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
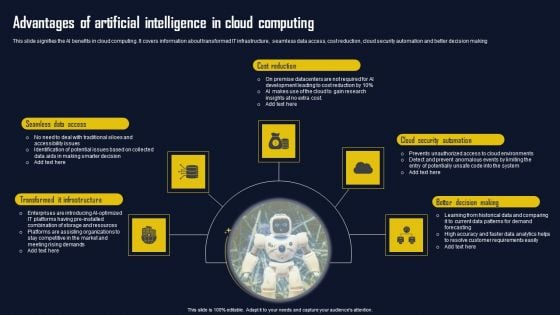
Advantages Of Artificial Intelligence In Cloud Computing Summary PDF
This slide signifies the AI benefits in cloud computing. It covers information about transformed IT infrastructure, seamless data access, cost reduction, cloud security automation and better decision making Persuade your audience using this Advantages Of Artificial Intelligence In Cloud Computing Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cost Reduction, Cloud Security Automation, Better Decision Making. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
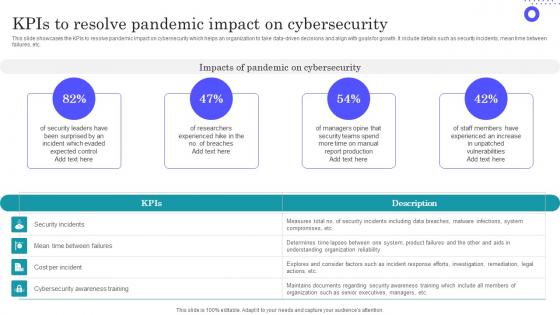
KPIs To Resolve Pandemic Impact On Cybersecurity Microsoft Pdf
Pitch your topic with ease and precision using this KPIs To Resolve Pandemic Impact On Cybersecurity Microsoft Pdf This layout presents information on Understanding Organization, Security Incidents, Malware Infections It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the KPIs to resolve pandemic impact on cybersecurity which helps an organization to take data driven decisions and align with goals for growth. It include details such as security incidents, mean time between failures, etc.
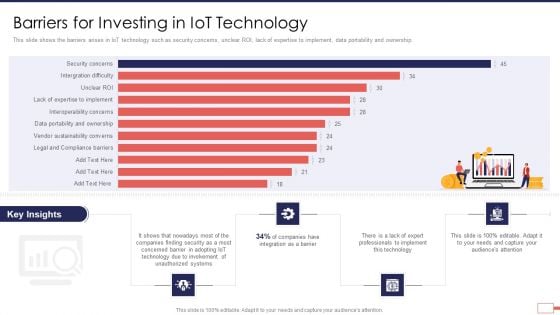
Iot Digital Twin Technology Post Covid Expenditure Management Barriers For Investing In Iot Technology Download PDF
This slide shows the barriers arises in IoT technology such as security concerns, unclear ROI, lack of expertise to implement, data portability and ownership. Deliver and pitch your topic in the best possible manner with this iot digital twin technology post covid expenditure management barriers for investing in iot technology download pdf Use them to share invaluable insights on security, companies, involvement, unauthorized, technology, barrier and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Use Cases Of Concurrent Computing Business Sector Ppt Infographic Template Graphic Tips PDF
This slide describes how edge computing will help businesses grow by providing real time data analysis, augmented reality, smart manufacturing, lowered operation costs, and security systems. Presenting use cases of concurrent computing business sector ppt infographic template graphic tips pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like analysis, manufacturing, security, systems, operational. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organization Impact Metrics Strategic Themes PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission.Presenting organization impact metrics strategic themes pdf. to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like data loss incidents, infected computers, total number of computers currently corrupted. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
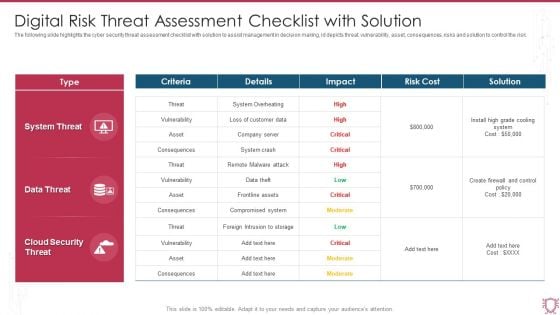
Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF
The following slide highlights the cyber security threat assessment checklist with solution to assist management in decision making, id depicts threat, vulnerability, asset, consequences, risks and solution to control the risk. Showcasing this set of slides titled Digital Risk Threat Assessment Checklist With Solution Ppt File Display PDF. The topics addressed in these templates are System Threat, Data Threat, Cloud Security Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
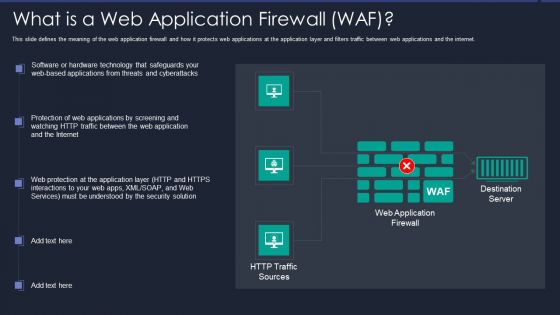
Web App Firewall Services IT What Is A Web Application Firewall WAF Graphics PDF
This slide defines the meaning of the web application firewall and how it protects web applications at the application layer and filters traffic between web applications and the internet. This slide defines the meaning of the web application firewall and how it protects web applications at the application layer and filters traffic between web applications and the internet. Deliver and pitch your topic in the best possible manner with this web app firewall services it what is a web application firewall waf graphics pdf. Use them to share invaluable insights on applications, technology, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
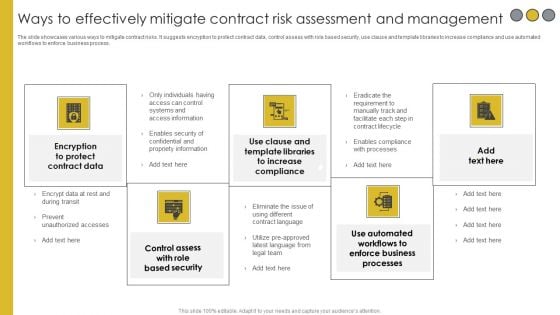
Ways To Effectively Mitigate Contract Risk Assessment And Management Download PDF
The slide showcases various ways to mitigate contract risks. It suggests encryption to protect contract data, control assess with role based security, use clause and template libraries to increase compliance and use automated workflows to enforce business process. Presenting Ways To Effectively Mitigate Contract Risk Assessment And Management Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Encryption Protect, Control Assess Role, Use Clause Template Libraries. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Zero Trust Model Technologies Used In Zero Trust Network Access
This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Model Technologies Used In Zero Trust Network Access. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Model Technologies Used In Zero Trust Network Access today and make your presentation stand out from the rest This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer.

Technologies Used In Zero Trust Network Access Software Defined Perimeter SDP
This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Technologies Used In Zero Trust Network Access Software Defined Perimeter SDP. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Technologies Used In Zero Trust Network Access Software Defined Perimeter SDP today and make your presentation stand out from the rest. This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer.

Industry Laws And Regulations Licensing And Intellectual Property Maritime Shipping Industry IR SS V
The slide highlights industry laws and regulations in shipping industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Industry Laws And Regulations Licensing And Intellectual Property Maritime Shipping Industry IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Industry Laws And Regulations Licensing And Intellectual Property Maritime Shipping Industry IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The slide highlights industry laws and regulations in shipping industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory.
Product Lifecycle Effective Influencing Factors Comprehensive Guide To Product Lifecycle Icons Pdf
This slide covers factors determining the product lifecycle. The purpose of this template is to provide information based on several factors that improves the sales of a product. It includes factors such as rate of technical changes, rate of market acceptance, ease of competitive entry, risk bearing capacity, protection by patent, etc. Are you searching for a Product Lifecycle Effective Influencing Factors Comprehensive Guide To Product Lifecycle Icons Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Product Lifecycle Effective Influencing Factors Comprehensive Guide To Product Lifecycle Icons Pdf from Slidegeeks today. This slide covers factors determining the product lifecycle. The purpose of this template is to provide information based on several factors that improves the sales of a product. It includes factors such as rate of technical changes, rate of market acceptance, ease of competitive entry, risk bearing capacity, protection by patent, etc.
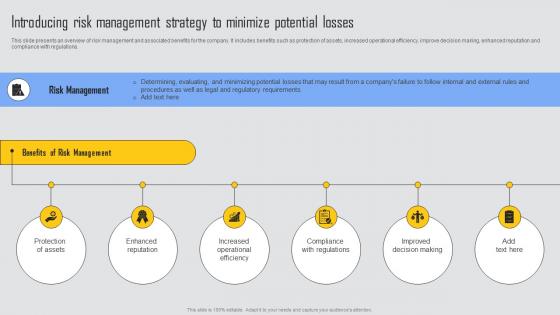
Introducing Risk Management Managing Risks And Establishing Trust Through Efficient Infographics Pdf
This slide presents an overview of risk management and associated benefits for the company. It includes benefits such as protection of assets, increased operational efficiency, improve decision making, enhanced reputation and compliance with regulations. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Introducing Risk Management Managing Risks And Establishing Trust Through Efficient Infographics Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Introducing Risk Management Managing Risks And Establishing Trust Through Efficient Infographics Pdf This slide presents an overview of risk management and associated benefits for the company. It includes benefits such as protection of assets, increased operational efficiency, improve decision making, enhanced reputation and compliance with regulations.
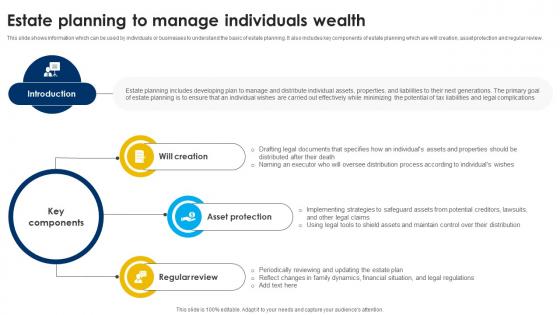
Estate Planning To Manage Individuals Wealth Strategic Wealth Management And Financial Fin SS V
This slide shows information which can be used by individuals or businesses to understand the basic of estate planning. It also includes key components of estate planning which are will creation, asset protection and regular review. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Estate Planning To Manage Individuals Wealth Strategic Wealth Management And Financial Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Estate Planning To Manage Individuals Wealth Strategic Wealth Management And Financial Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide shows information which can be used by individuals or businesses to understand the basic of estate planning. It also includes key components of estate planning which are will creation, asset protection and regular review.
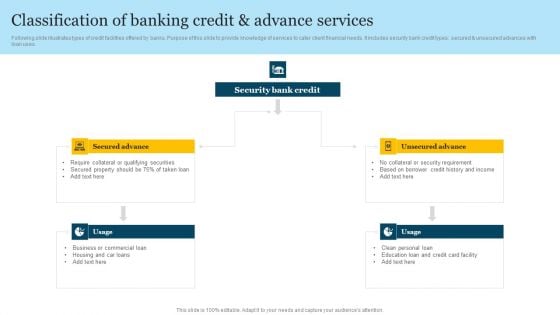
Classification Of Banking Credit And Advance Services Summary PDF
Following slide illustrates types of credit facilities offered by banks. Purpose of this slide to provide knowledge of services to cater client financial needs. It includes security bank credit types secured and unsecured advances with loan uses. Presenting Classification Of Banking Credit And Advance Services Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Bank Credit, Security Requirement, Education Loan This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Prevention Of Information Assessment Test To Measure Effectiveness Of Training Plan Inspiration PDF
The purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Create an editable Prevention Of Information Assessment Test To Measure Effectiveness Of Training Plan Inspiration PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Prevention Of Information Assessment Test To Measure Effectiveness Of Training Plan Inspiration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
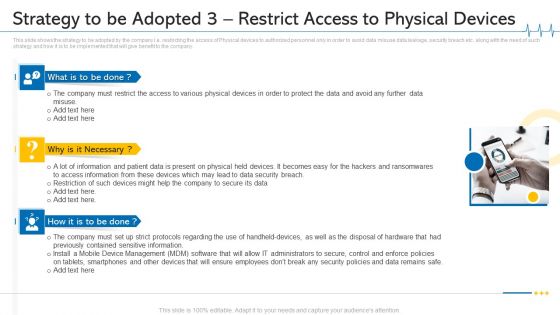
Minimize Cloud Risks Medical Care Business Case Competition Strategy To Be Adopted 3 Restrict Access To Physical Devices Ideas PDF
This slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. This is a minimize cloud risks medical care business case competition strategy to be adopted 3 restrict access to physical devices ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like mobile device management, data security breach, physical devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
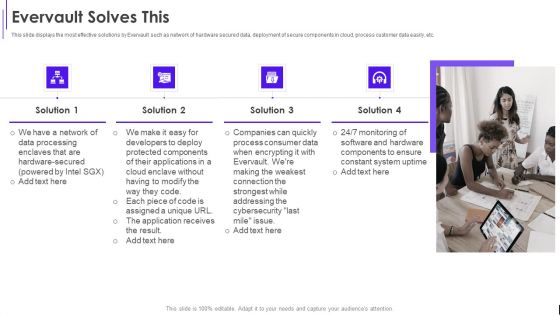
Fundraising Pitch Deck For Evervault Evervault Solves This Ppt Gallery Grid PDF
This slide displays the most effective solutions by Evervault such as network of hardware secured data, deployment of secure components in cloud, process customer data easily, etc. Presenting Fundraising Pitch Deck For Evervault Evervault Solves This Ppt Gallery Grid PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Processing, Protected Components, Monitoring Software. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Table Of Contents Risk Management For Organization Essential Assets Brochure PDF
Presenting table of contents risk management for organization essential assets brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, secure digital assets, natural calamity threats, ensuring physical security, security against workplace. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Implementing Cybersecurity Awareness Program To Prevent Attacks Assessment Test To Measure Brochure PDF
The purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Want to ace your presentation in front of a live audience Our Implementing Cybersecurity Awareness Program To Prevent Attacks Assessment Test To Measure Brochure PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Incident Response Techniques Deployement Impact Of Cybersecurity Incidents On Organization Clipart PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
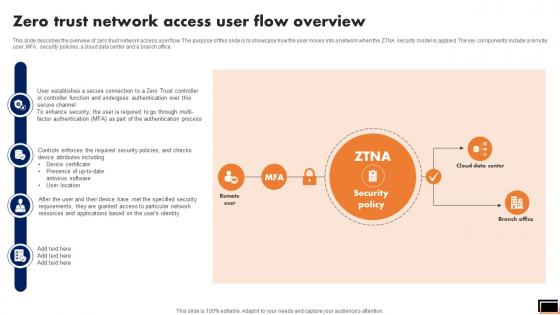
Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Role IT Team Digital Transformation It Professional Upskilling For Cybersecurity Introduction PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a role it team digital transformation it professional upskilling for cybersecurity introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
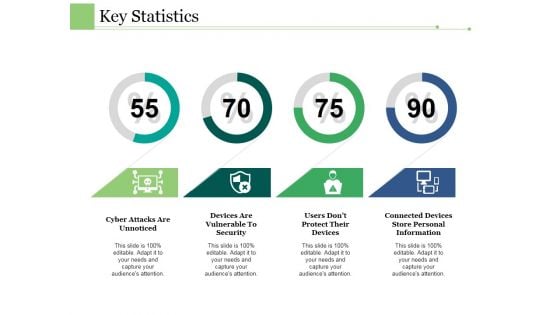
Key Statistics Ppt PowerPoint Presentation Show Sample
This is a key statistics ppt powerpoint presentation show sample. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, users do not protect their devices, connected devices store personal information.
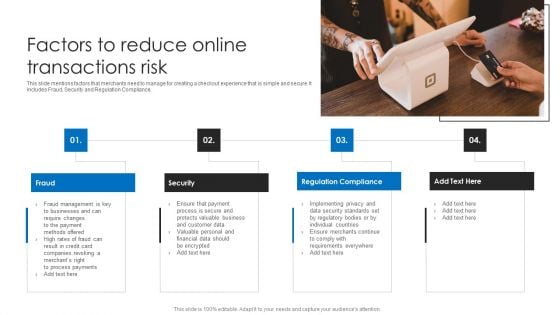
Factors To Reduce Online Transactions Risk Ppt Ideas Graphics Design PDF
This slide mentions factors that merchants need to manage for creating a checkout experience that is simple and secure. It includes Fraud, Security and Regulation Compliance. Presenting Factors To Reduce Online Transactions Risk Ppt Ideas Graphics Design PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Fraud, Security, Regulation Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
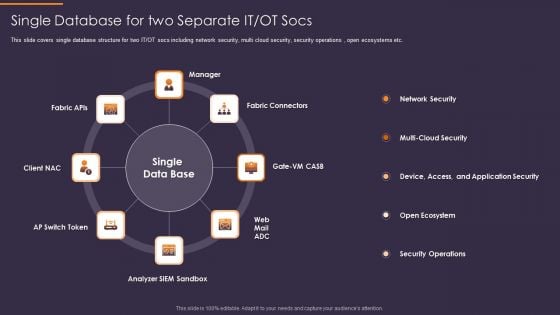
Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Fabric Connectors, Analyzer SIEM Sandbox, AP Switch Token, Client NAC, Fabric APIs. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
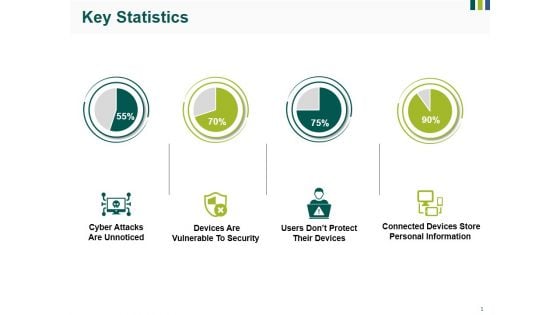
Key Statistics Ppt PowerPoint Presentation Gallery Format Ideas
This is a key statistics ppt powerpoint presentation gallery format ideas. This is a four stage process. The stages in this process are cyber attacks are unnoticed, devices are vulnerable to security, users dont protect their devices, connected devices store personal information.
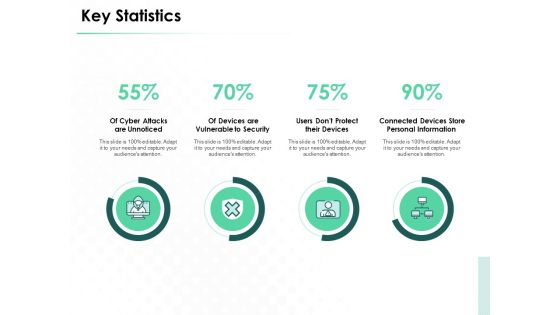
Market Approach To Business Valuation Key Statistics Summary PDF
Presenting this set of slides with name market approach to business valuation key statistics summary pdf. This is a four stage process. The stages in this process are cyber attacks unnoticed, devices vulnerable security, users dont protect devices, connected devices store personal information. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
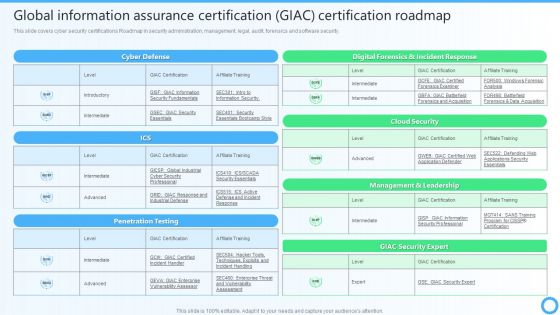
Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security.This Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.


 Continue with Email
Continue with Email

 Home
Home


































