Data Security And Protection
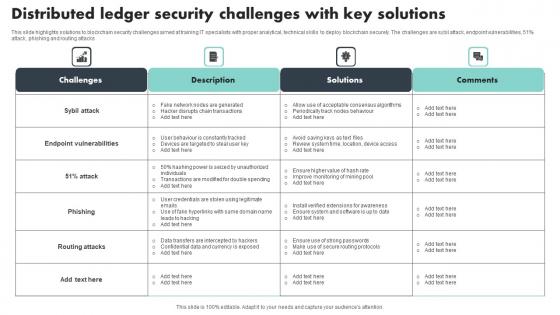
Distributed Ledger Security Challenges With Key Solutions Introduction Pdf
This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51percent attack, phishing and routing attacks Showcasing this set of slides titled Distributed Ledger Security Challenges With Key Solutions Introduction Pdf The topics addressed in these templates are Endpoint Vulnerabilities, Routing Attacks, Phishing All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51 percent attack, phishing and routing attacks

Serverless Computing Security Role Serverless Computing Modern Technology Ideas Pdf
The purpose of this slide is to outline the security challenges and risks of serverless computing. These problems are vulnerable configuration, permissions for too powerful functions, infusion of event data, insufficient function recording and monitoring, etc. This modern and well arranged Serverless Computing Security Role Serverless Computing Modern Technology Ideas Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The purpose of this slide is to outline the security challenges and risks of serverless computing. These problems are vulnerable configuration, permissions for too powerful functions, infusion of event data, insufficient function recording and monitoring, etc.
Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf
Showcasing this set of slides titled Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf The topics addressed in these templates are Ecommerce Payment Security, Distributed Ledger, Technology Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Complete Guide To Launch Website Security Management Strategic Plan
Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Slidegeeks has constructed Complete Guide To Launch Website Security Management Strategic Plan after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc.

Information Technology Security Gap Analysis With Risk Level Information PDF
The following slide highlights the gaps in the IT security system to determine the opportunities for improvement. It also reflects the level of risk low, moderate, high and extreme if the gap are not fulfilled. Pitch your topic with ease and precision using this Information Technology Security Gap Analysis With Risk Level Information PDF. This layout presents information on Organize Security, Regularly Analyze, Gap Assessment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
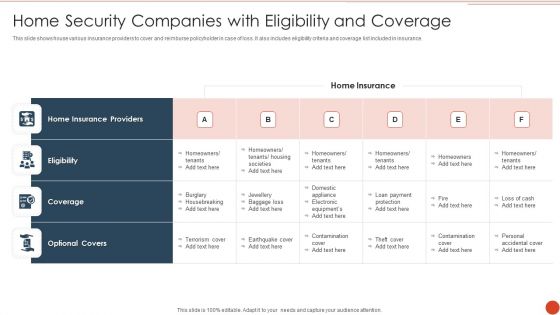
Home Security Companies With Eligibility And Coverage Infographics PDF
This slide shows house various insurance providers to cover and reimburse policyholder in case of loss. It also includes eligibility criteria and coverage list included in insurance. Showcasing this set of slides titled Home Security Companies With Eligibility And Coverage Infographics PDF. The topics addressed in these templates are Home Insurance Providers, Home Insurance, Loan Payment Protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
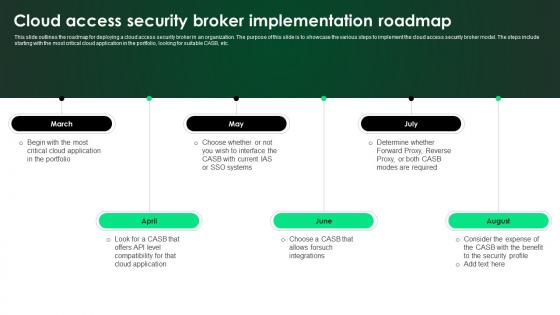
CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Welcome to our selection of the CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc.
Smart Phone Security Key Aspects For Growing Revenue Icons PDF
This slide shows every aspect of phone security model that should be considered while framing security policy for organization. It include aspects such as compliance security, product security and infrastructure security etc. Presenting Smart Phone Security Key Aspects For Growing Revenue Icons PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Compliance Security, Product Security, Infrastructure Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Information Technology Security Assurance And Analysis Icon Professional PDF
Presenting Information Technology Security Assurance And Analysis Icon Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Information Technology Security, Assurance And Analysis Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Incident Response Communication Plan Icon Professional Pdf
Showcasing this set of slides titled Security Incident Response Communication Plan Icon Professional Pdf The topics addressed in these templates are Security Incident, Response Communication, Plan Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Security Incident Response Communication Plan Icon Professional Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Strategic Agenda For Hotels Icon Professional Pdf
Showcasing this set of slides titled Security Strategic Agenda For Hotels Icon Professional Pdf. The topics addressed in these templates are Security Strategic, Agenda For Hotels. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Security Strategic Agenda For Hotels Icon Professional Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Email Phishing And Internet Security Icon Microsoft Pdf
Showcasing this set of slides titled Email Phishing And Internet Security Icon Microsoft Pdf The topics addressed in these templates are Email Phishing, Internet Security Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Email Phishing And Internet Security Icon Microsoft Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
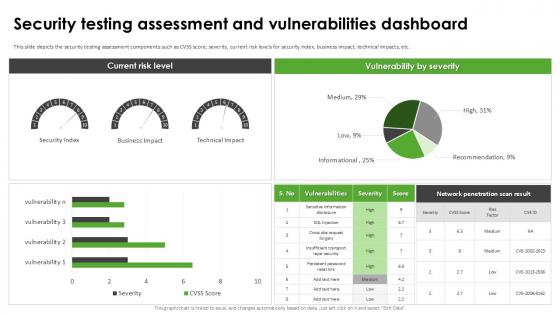
Security Testing Assessment Harnessing The World Of Ethical Ppt Example
This slide depicts the security testing assessment components such as CVSS score, severity, current risk levels for security index, business impact, technical impacts, etc. This Security Testing Assessment Harnessing The World Of Ethical Ppt Example is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security Testing Assessment Harnessing The World Of Ethical Ppt Example features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the security testing assessment components such as CVSS score, severity, current risk levels for security index, business impact, technical impacts, etc.
Internet Of Things Security Icon For Software Management Template Pdf
Showcasing this set of slides titled Internet Of Things Security Icon For Software Management Template Pdf The topics addressed in these templates are Internet Of Things Security, Icon For Software, Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Internet Of Things Security Icon For Software Management Template Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf
Showcasing this set of slides titled Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf The topics addressed in these templates are Cyber Security Breach, Icon Sending Malicious Emails All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Wireless In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Wireless In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Wireless that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Wireless In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Employee Incentives Icon For Healthcare And Financial Security Designs Pdf
Showcasing this set of slides titled Employee Incentives Icon For Healthcare And Financial Security Designs Pdf The topics addressed in these templates are Employee Incentives, Icon For Healthcare, Financial Security All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Employee Incentives Icon For Healthcare And Financial Security Designs Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Wifi Systems Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Wifi Systems Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Wifi Systems Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Wifi Systems Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Computer Personal Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Computer Personal Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Computer Personal Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Computer Personal Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Gate Icon In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Gate Icon In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Gate Icon that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Gate Icon In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Application Security Testing Tools Reference Model Ppt Powerpoint Ideas
This slide showcases the application security testing tools reference model along with the workflow. Get a simple yet stunning designed Application Security Testing Tools Reference Model Ppt Powerpoint Ideas. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Application Security Testing Tools Reference Model Ppt Powerpoint Ideas can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases the application security testing tools reference model along with the workflow.
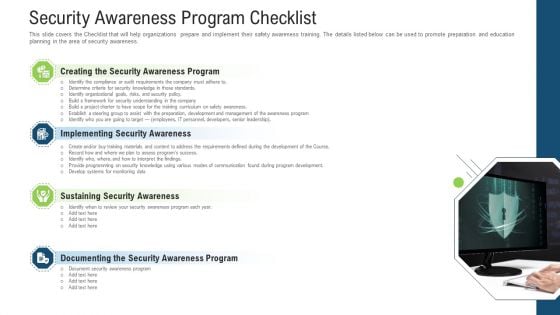
Security Awareness Program Checklist Ppt Layouts Microsoft PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. This is a security awareness program checklist ppt layouts microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sustaining security awareness, implementing security awareness, creating the security awareness program, documenting the security awareness program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Existing It Security Infrastructure Constituents Corrective Regression Testing Ppt Slides
This slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are vulnerability scanners, improper functioning, functional disrupt, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Existing It Security Infrastructure Constituents Corrective Regression Testing Ppt Slides will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are vulnerability scanners, improper functioning, functional disrupt, and so on.
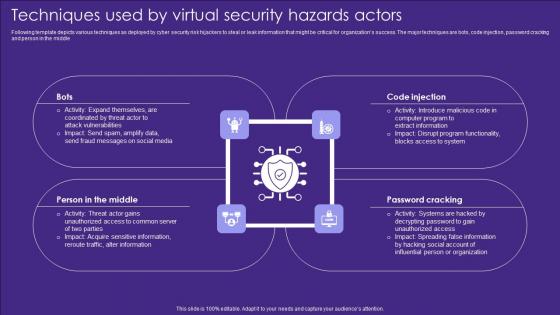
Techniques Used By Virtual Security Hazards Actors Professional Pdf
Following template depicts various techniques as deployed by cyber security risk hijackers to steal or leak information that might be critical for organizations success. The major techniques are bots, code injection, password cracking and person in the middle Pitch your topic with ease and precision using this Techniques Used By Virtual Security Hazards Actors Professional Pdf. This layout presents information on Code Injection, Password Cracking, Middle. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following template depicts various techniques as deployed by cyber security risk hijackers to steal or leak information that might be critical for organizations success. The major techniques are bots, code injection, password cracking and person in the middle
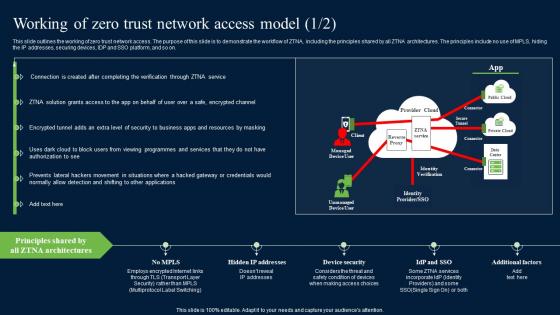
Working Of Zero Trust Network Access Model Security Pictures Pdf
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Working Of Zero Trust Network Access Model Security Pictures Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Table Of Contents For Cloud Security Firewall Proposal
Take your presentations to the next level with our Table Of Contents For Cloud Security Firewall Proposal template. With its sleek design and seamless editing features, this single-slide PPT template is a game-changer for professionals who want to make an impact. Impress your audience with stunning visuals and engaging content that will capture their attention from start to finish. Get your hands on our template and elevate your presentations to new heights. Our Table Of Contents For Cloud Security Firewall Proposal are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
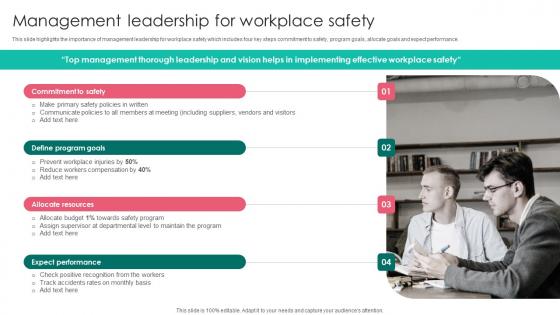
Management Leadership Workplace Safety Protocol And Security Practices Sample Pdf
This slide highlights the importance of management leadership for workplace safety which includes four key steps commitment to safety, program goals, allocate goals and expect performance. The Management Leadership Workplace Safety Protocol And Security Practices Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide highlights the importance of management leadership for workplace safety which includes four key steps commitment to safety, program goals, allocate goals and expect performance.
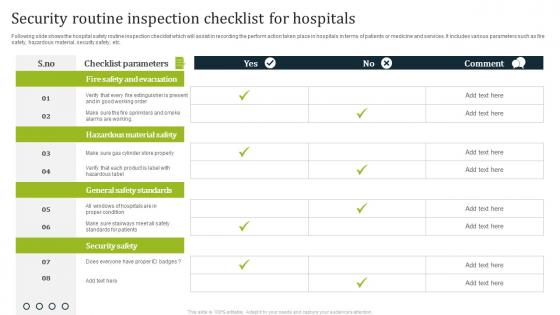
Security Routine Inspection Checklist For Hospitals Diagrams Pdf
Following slide shows the hospital safety routine inspection checklist which will assist in recording the perform action taken place in hospitals in terms of patients or medicine and services. It includes various parameters such as fire safety, hazardous material, security safety, etc. Showcasing this set of slides titled Security Routine Inspection Checklist For Hospitals Diagrams Pdf. The topics addressed in these templates are Checklist Parameters, Comment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the hospital safety routine inspection checklist which will assist in recording the perform action taken place in hospitals in terms of patients or medicine and services. It includes various parameters such as fire safety, hazardous material, security safety, etc.

Teamwork Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Teamwork Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Teamwork Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Teamwork Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Endpoint Security Checklist In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Endpoint Security Checklist In Powerpoint And Google Slides Cpb This completely editable PowerPoint graphic exhibits Endpoint Security Checklist that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Endpoint Security Checklist In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
National Security Budget In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled National Security Budget In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits National Security Budget that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our National Security Budget In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Information Technology Security KPI Icon With Shield Inspiration PDF
Presenting Information Technology Security KPI Icon With Shield Inspiration PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Information Technology, Security KPI, Icon With Shield. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Information Technology Security Risk Mitigation Strategies Icon Mockup PDF
Presenting Information Technology Security Risk Mitigation Strategies Icon Mockup PDF to dispense important information. This template comprises Three stages. It also presents valuable insights into the topics including Information Technology, Security Risk, Mitigation Strategies . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Information Technology Operations Security Management Icon Designs PDF
Presenting Information Technology Operations Security Management Icon Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Information Technology Operations, Security Management Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
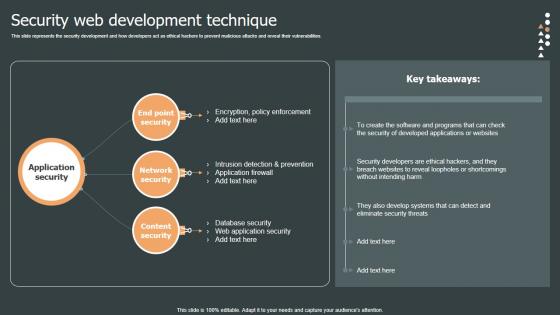
Security Web Development Role Web Designing User Engagement Topics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Are you searching for a Security Web Development Role Web Designing User Engagement Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Web Development Role Web Designing User Engagement Topics PDF from Slidegeeks today. This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.
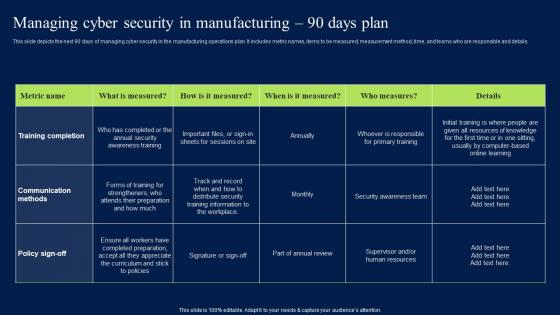
Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, andteams who are responsible and details. Slidegeeks has constructed Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.
Information Technology Security Assessment Report Icon Demonstration PDF
Presenting Information Technology Security Assessment Report Icon Demonstration PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Information Technology Security, Assessment Report Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Information Technology Security Key Strategies Icon Slides PDF
Persuade your audience using this Information Technology Security Key Strategies Icon Slides PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Information Technology Security, Key Strategies Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Operations Training Department Program Chart Infographics PDF
This slide covers employees training in organizations based on different security operations. It includes training based on security policy, incident management, security audit, cybersecurity, malware analysis, etc. Showcasing this set of slides titled Information Security Operations Training Department Program Chart Infographics PDF. The topics addressed in these templates are Induction Complete, Company Security Policy, Incident Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
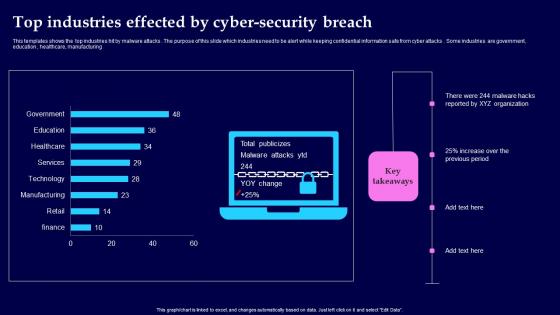
Top Industries Effected By Cyber Security Breach Background Pdf
This templates shows the top industries hit by malware attacks. The purpose of this slide which industries need to be alert while keeping confidential information safe from cyber attacks. Some industries are government, education, healthcare, manufacturing Showcasing this set of slides titled Top Industries Effected By Cyber Security Breach Background Pdf The topics addressed in these templates are Top Industries Effected, Cyber Security Breach All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the top industries hit by malware attacks. The purpose of this slide which industries need to be alert while keeping confidential information safe from cyber attacks. Some industries are government, education, healthcare, manufacturing
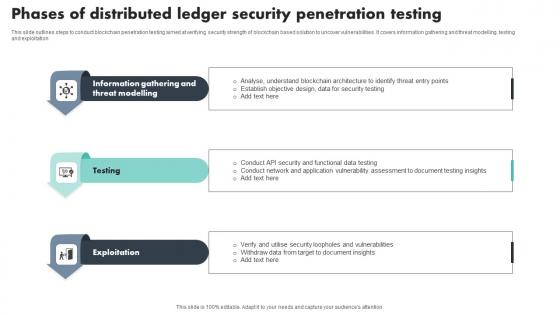
Phases Of Distributed Ledger Security Penetration Testing Download Pdf
This slide outlines steps to conduct blockchain penetration testing aimed at verifying security strength of blockchain based solution to uncover vulnerabilities. It covers information gathering and threat modelling, testing and exploitation Showcasing this set of slides titled Phases Of Distributed Ledger Security Penetration Testing Download Pdf The topics addressed in these templates are Information Gathering, Threat Modelling, Exploitation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide outlines steps to conduct blockchain penetration testing aimed at verifying security strength of blockchain based solution to uncover vulnerabilities. It covers information gathering and threat modelling, testing and exploitation

Top Countries Effect By Cyber Security Breach Background Pdf
This templates shows the top countries impacted by malware attacks. The purpose of this slide which country is most effected by malware attack what precaution they should take to reduce the numbers of attacks in futures. it includes various countries such as sweden, japan , china, etc. Pitch your topic with ease and precision using this Top Countries Effect By Cyber Security Breach Background Pdf This layout presents information on Malware Attack, Countries Effect, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the top countries impacted by malware attacks. The purpose of this slide which country is most effected by malware attack what precaution they should take to reduce the numbers of attacks in futures. it includes various countries such as sweden, japan , china, etc.
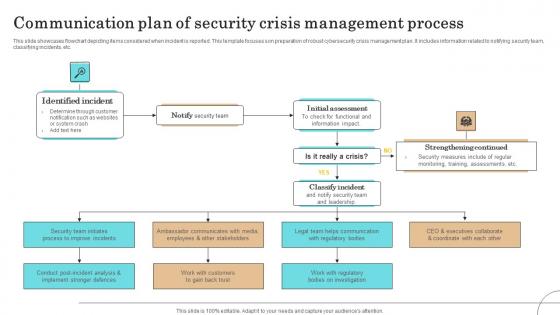
Communication Plan Of Security Crisis Management Process Pictures Pdf
This slide showcases flowchart depicting items considered when incident is reported. This template focuses son preparation of robust cybersecurity crisis management plan. It includes information related to notifying security team, classifying incidents, etc.Pitch your topic with ease and precision using this Communication Plan Of Security Crisis Management Process Pictures Pdf This layout presents information on Identified Incident, Initial Assessment, Strengthening Continued It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases flowchart depicting items considered when incident is reported. This template focuses son preparation of robust cybersecurity crisis management plan. It includes information related to notifying security team, classifying incidents, etc.
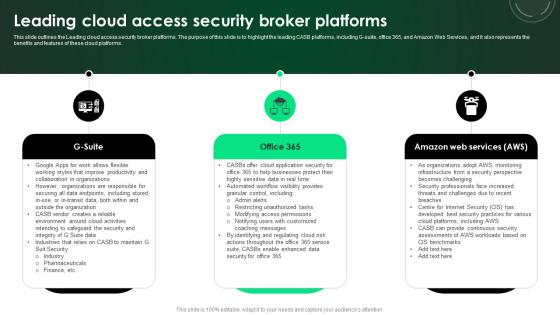
CASB 2 0 IT Leading Cloud Access Security Broker Platforms
This slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. There are so many reasons you need a CASB 2 0 IT Leading Cloud Access Security Broker Platforms. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms.
Security Icon In Powerpoint And Google Slides Cpb
Introducing our well designed Security Icon In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Icon. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Icon In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Lifeshield Security Projects Johannesburg In Powerpoint And Google Slides Cpb
Introducing our well-designed Lifeshield Security Projects Johannesburg In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Lifeshield Security Projects Johannesburg. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Lifeshield Security Projects Johannesburg In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
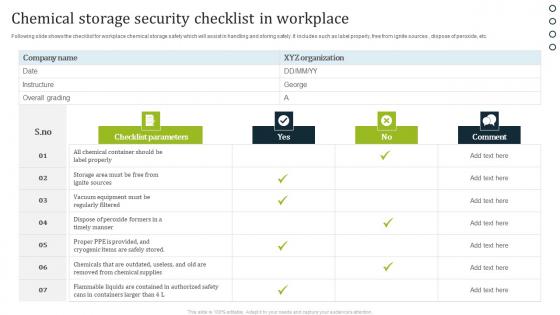
Chemical Storage Security Checklist In Workplace Brochure Pdf
Following slide shows the checklist for workplace chemical storage safety which will assist in handling and storing safely. It includes such as label properly, free from ignite sources , dispose of peroxide, etc. Pitch your topic with ease and precision using this Chemical Storage Security Checklist In Workplace Brochure Pdf. This layout presents information on Checklist Parameters, Comment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide shows the checklist for workplace chemical storage safety which will assist in handling and storing safely. It includes such as label properly, free from ignite sources , dispose of peroxide, etc.
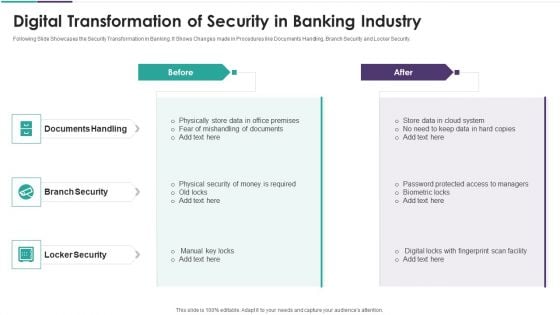
Digital Transformation Of Security In Banking Industry Elements PDF
Following Slide Showcases the Security Transformation in Banking. It Shows Changes made in Procedures like Documents Handling, Branch Security and Locker Security. Presenting digital transformation of security in banking industry elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including documents handling, branch security, locker security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
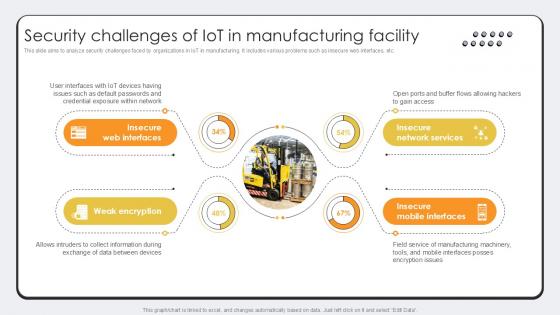
Security Challenges Of IoT In Revolutionizing Production IoT Ppt Example
This slide aims to analyze security challenges faced by organizations in IoT in manufacturing. It includes various problems such as insecure web interfaces, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Security Challenges Of IoT In Revolutionizing Production IoT Ppt Example to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Security Challenges Of IoT In Revolutionizing Production IoT Ppt Example. This slide aims to analyze security challenges faced by organizations in IoT in manufacturing. It includes various problems such as insecure web interfaces, etc.
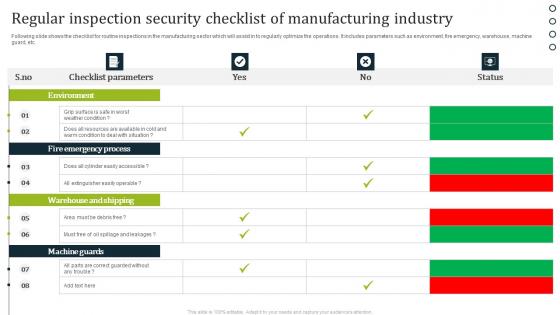
Regular Inspection Security Checklist Of Manufacturing Industry Demonstration Pdf
Following slide shows the checklist for routine inspections in the manufacturing sector which will assist in to regularly optimize the operations. It includes parameters such as environment, fire emergency, warehouse, machine guard, etc. Pitch your topic with ease and precision using this Regular Inspection Security Checklist Of Manufacturing Industry Demonstration Pdf. This layout presents information on Checklist Parameters, Status. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide shows the checklist for routine inspections in the manufacturing sector which will assist in to regularly optimize the operations. It includes parameters such as environment, fire emergency, warehouse, machine guard, etc.
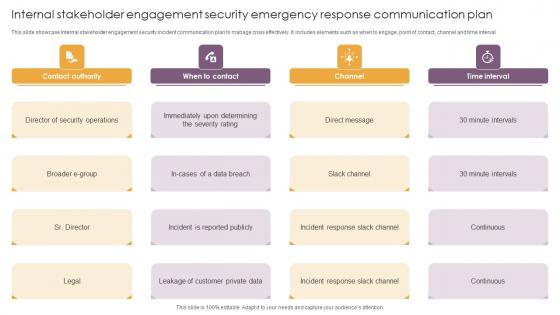
Internal Stakeholder Engagement Security Emergency Response Communication Plan Introduction Pdf
This slide showcase Internal stakeholder engagement security incident communication plan to manage crisis effectively. It includes elements such as when to engage, point of contact, channel and time interval Showcasing this set of slides titled Internal Stakeholder Engagement Security Emergency Response Communication Plan Introduction Pdf The topics addressed in these templates are Contact Authority, Time Interval, Director Of Security Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase Internal stakeholder engagement security incident communication plan to manage crisis effectively. It includes elements such as when to engage, point of contact, channel and time interval
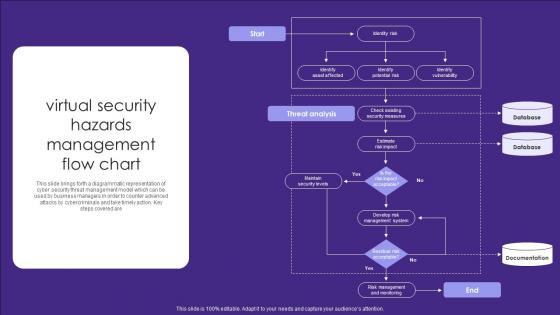
Virtual Security Hazards Management Flow Chart Infographics Pdf
This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are Showcasing this set of slides titled Virtual Security Hazards Management Flow Chart Infographics Pdf. The topics addressed in these templates are Security Measures, Database, Documentation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are
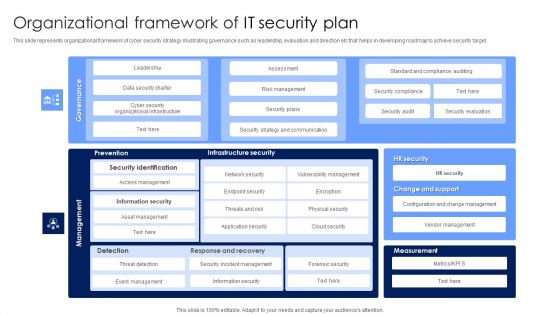
Organizational Framework Of IT Security Plan Microsoft PDF
This slide represents organizational framework of cyber security strategy illustrating governance such as leadership, evaluation and direction etc that helps in developing roadmap to achieve security target. Showcasing this set of slides titled Organizational Framework Of IT Security Plan Microsoft PDF. The topics addressed in these templates are Infrastructure Security, Management, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icons Slide For Zero Trust Security Template Pdf
Introducing our well designed Icons Slide For Zero Trust Security Template Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Zero Trust Security Template Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Major Target Areas Of Virtual Security Hazards Summary Pdf
The following slide consists of major target points of cyber security attacks aimed at accessing, changing, or destroying sensitive information extorting money from users or interrupting normal business processes. The major targets are electronic devices, critical information, financial resources and public opinion Pitch your topic with ease and precision using this Major Target Areas Of Virtual Security Hazards Summary Pdf. This layout presents information on Financial Resources, Public Opinion, Electronic Devices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide consists of major target points of cyber security attacks aimed at accessing, changing, or destroying sensitive information extorting money from users or interrupting normal business processes. The major targets are electronic devices, critical information, financial resources and public opinion
Information Security Tool Ppt PowerPoint Presentation Summary Portrait Cpb
This is a information security tool ppt powerpoint presentation summary portrait cpb. This is a three stage process. The stages in this process are information security tool.
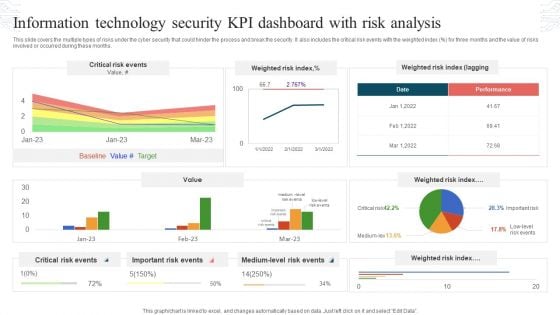
Information Technology Security KPI Dashboard With Risk Analysis Topics PDF
This slide covers the multiple types of risks under the cyber security that could hinder the process and break the security. It also includes the critical risk events with the weighted index percent for three months and the value of risks involved or occurred during these months. Showcasing this set of slides titled Information Technology Security KPI Dashboard With Risk Analysis Topics PDF. The topics addressed in these templates are Critical Risk Events, Weighted Risk Index, Important Risk Events. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
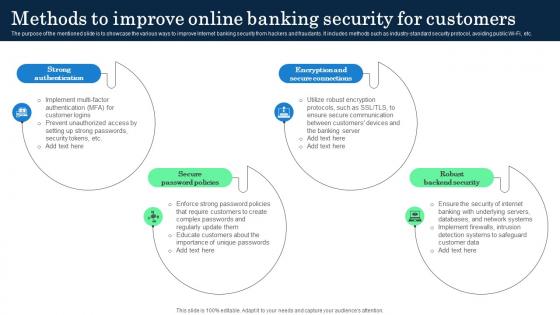
Methods To Improve Online Banking Security Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc. Do you know about Slidesgeeks Methods To Improve Online Banking Security Incorporating Banking Operational Growth These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc.
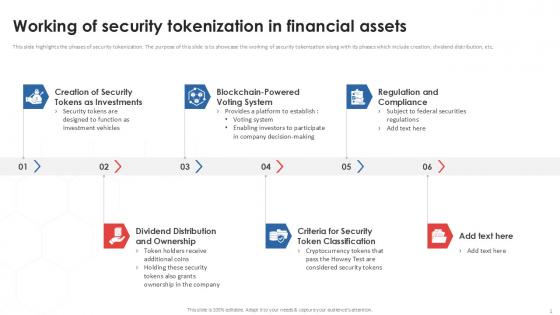
Working Of Security Tokenization In Financial Assets PPT Powerpoint
This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc. Find a pre-designed and impeccable Working Of Security Tokenization In Financial Assets PPT Powerpoint. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc.

Email Security Industry Report In Powerpoint And Google Slides Cpb
Introducing our well-designed Email Security Industry Report In Powerpoint And Google Slides Cpb This PowerPoint design presents information on topics like Email Security Industry Report As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Email Security Industry Report In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































