Data Security And Protection
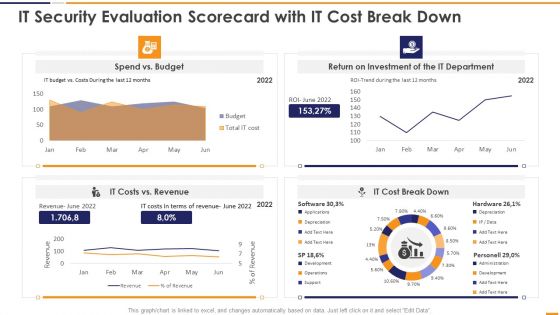
IT Security Evaluation Scorecard With It Cost Break Down Ppt Infographics Slideshow PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With It Cost Break Down Ppt Infographics Slideshow PDF bundle. Topics like Spend Vs Budget, Return On Investment, IT Department Revenue, IT Costs Vs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective IT Risk Management Process Information Security Risk Assessment Formats PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Deliver and pitch your topic in the best possible manner with this NAMEEEEEE. Use them to share invaluable insights on system failure, potential, vulnerability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Landscape Architecture Planning And Management 4 Dimensions Of Infrastructure Security Sample PDF
Deliver an awe inspiring pitch with this creative landscape architecture planning and management 4 dimensions of infrastructure security sample pdf bundle. Topics like people, data, applications, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents Information Security Ppt PowerPoint Presentation Diagram Graph Charts PDF
Find highly impressive Table Of Contents Information Security Ppt PowerPoint Presentation Diagram Graph Charts PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents Information Security Ppt PowerPoint Presentation Diagram Graph Charts PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
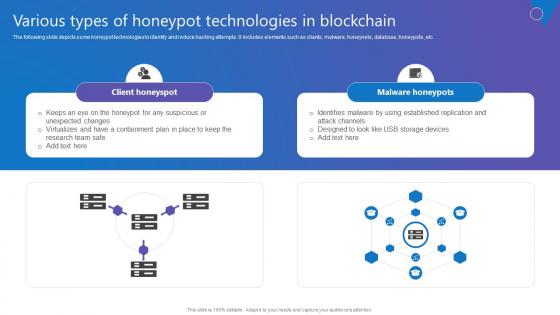
Various Types Of Honeypot Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Various Types Of Honeypot Comprehensive Guide To Blockchain Digital Security Information Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc.
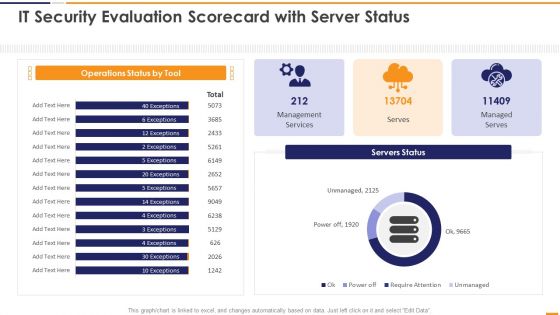
IT Security Evaluation Scorecard With Server Status Ppt Professional Images PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Server Status Ppt Professional Images PDF bundle. Topics like Operations Status Tool, Management Services Managed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
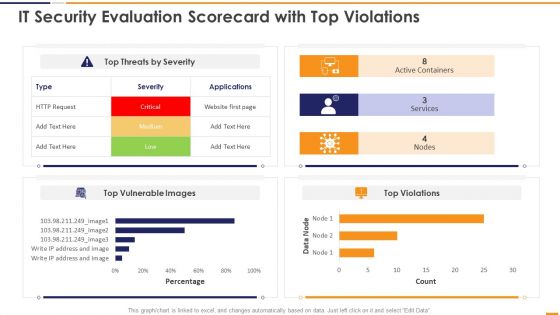
IT Security Evaluation Scorecard With Top Violations Ppt Portfolio Deck PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Top Violations Ppt Portfolio Deck PDF bundle. Topics like Top Threats Severity, Active Containers Services, Top Vulnerable Images can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
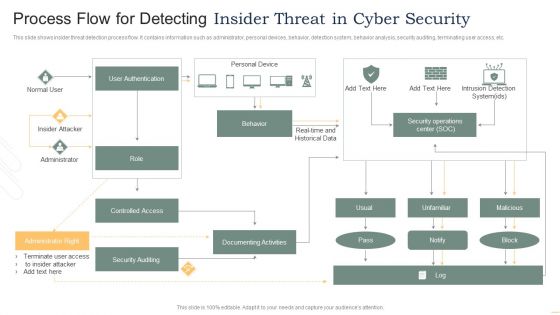
Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Proposal For Security Guard Services Table Of Contents One Pager Sample Example Document
Presenting you an exemplary Proposal For Security Guard Services Table Of Contents One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Security Guard Services Table Of Contents One Pager Sample Example Document brilliant piece now.

Table Of Contents Security Services Proposal One Pager Sample Example Document
Presenting you an exemplary Table Of Contents Security Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents Security Services Proposal One Pager Sample Example Document brilliant piece now.

Table Of Contents Security And Safety System Proposal One Pager Sample Example Document
Presenting you an exemplary Table Of Contents Security And Safety System Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents Security And Safety System Proposal One Pager Sample Example Document brilliant piece now.
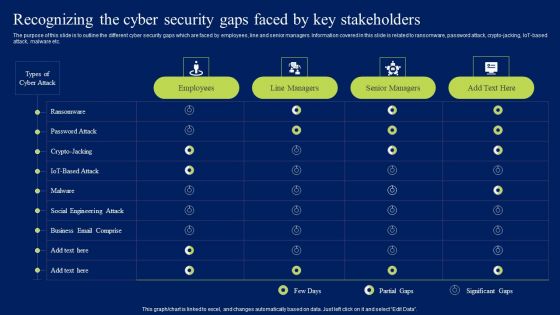
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Get a simple yet stunning designed Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Laptop And Help Button Security PowerPoint Templates And PowerPoint Backgrounds 0711
Microsoft PowerPoint Template and Background with laptop and help button to resolve the customer problem Give a fillip to your campaign. Give it a fitting finale with our Laptop And Help Button Security PowerPoint Templates And PowerPoint Backgrounds 0711.

Organizing Security Awareness In House Training Schedule We Will Implement Background PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and iot-based attack. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Organizing Security Awareness In House Training Schedule We Will Implement Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Organizing Security Awareness In House Training Schedule We Will Implement Background PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
Icon For Managed Cyber Cloud Security Service Ppt Outline Graphic Tips PDF
Persuade your audience using this Icon For Managed Cyber Cloud Security Service Ppt Outline Graphic Tips PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Icon, Cloud Security, Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
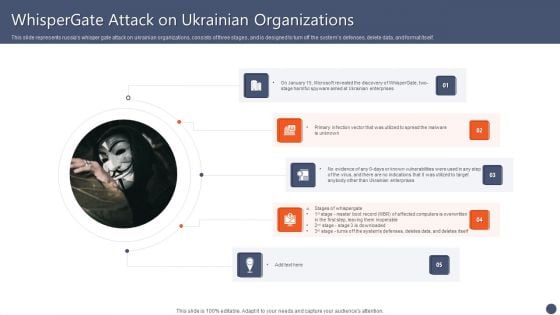
Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF
This slide represents russias whisper gate attack on ukrainian organizations, consists of three stages, and is designed to turn off the systems defenses, delete data, and format itself. Are you searching for a Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF from Slidegeeks today.

Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF
This slide represents types of e banking security threats. It includes brute force, phishing, pharming, cross site scripting and trojan horse. The Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
IT Security Evaluation Scorecard With Server Uptime And Downtime Icons PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Server Uptime And Downtime Icons PDF bundle. Topics like IT Support Employee, Per Thousand End, user Over Time, Uptime And Downtime can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
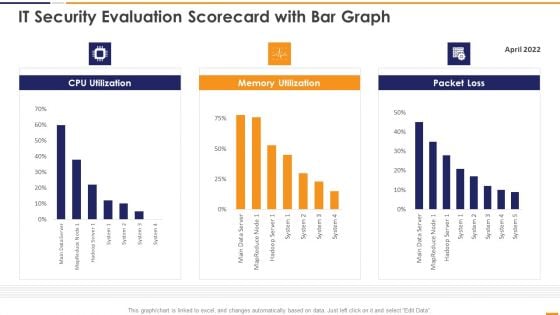
IT Security Evaluation Scorecard With Bar Graph Ppt Gallery Design Templates PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Bar Graph Ppt Gallery Design Templates PDF. Use them to share invaluable insights on CPU Utilization Memory, Utilization Packet Loss and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
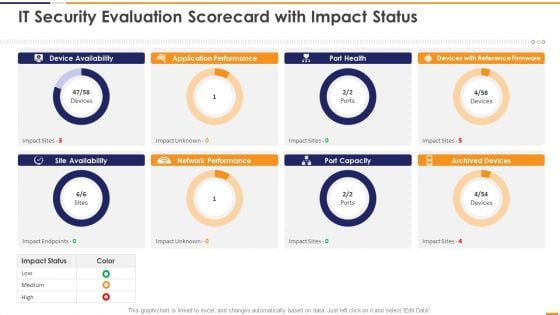
IT Security Evaluation Scorecard With Impact Status Ppt Portfolio Guidelines PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Impact Status Ppt Portfolio Guidelines PDF. Use them to share invaluable insights on Device Availability Application, Performance Port Health, Devices Reference Firmware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
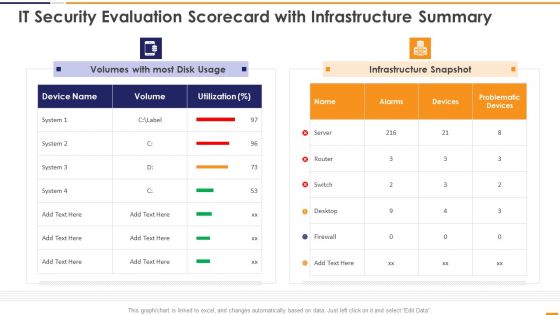
IT Security Evaluation Scorecard With Infrastructure Summary Ppt Slides Portrait PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Infrastructure Summary Ppt Slides Portrait PDF bundle. Topics like Volumes Most Disk, Usage Infrastructure Snapshot can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
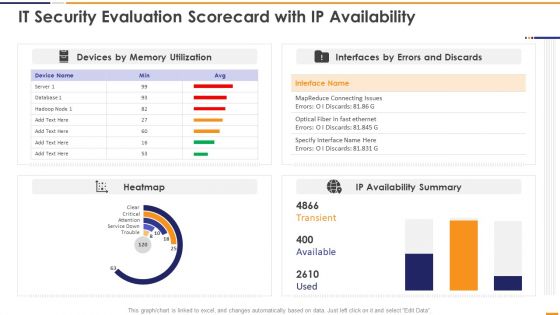
IT Security Evaluation Scorecard With Ip Availability Ppt Pictures Portrait PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Ip Availability Ppt Pictures Portrait PDF. Use them to share invaluable insights on Devices Memory Utilization, Interfaces Errors Discards, IP Availability Summary and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
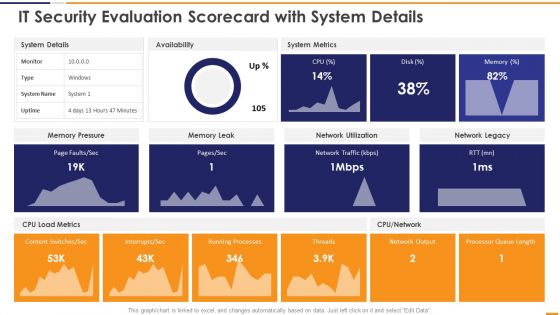
IT Security Evaluation Scorecard With System Details Ppt Inspiration Vector PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With System Details Ppt Inspiration Vector PDF. Use them to share invaluable insights on System Details Availability, System Metrics Memory, Pressure Memory Leak and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
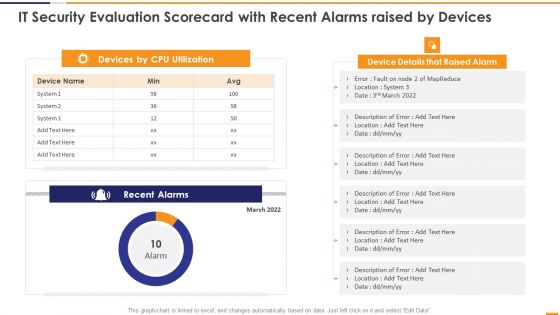
IT Security Evaluation Scorecard With Recent Alarms Raised By Devices Guidelines PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Recent Alarms Raised By Devices Guidelines PDF bundle. Topics like Devices CPU Utilization, Device Details Raised can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Evaluation Scorecard With Response Time And Availability Brochure PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard With Response Time And Availability Brochure PDF. Use them to share invaluable insights on Response Time 2022, Disk Utilization Availability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Security Technology Trends Ppt PowerPoint Presentation Model Graphics Download Cpb
Presenting this set of slides with name cyber security technology trends ppt powerpoint presentation model graphics download cpb. This is an editable Powerpoint four stages graphic that deals with topics like cyber security technology trends to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Operational Technology Cyber Security Ppt PowerPoint Presentation Inspiration File Formats Cpb
Presenting this set of slides with name operational technology cyber security ppt powerpoint presentation inspiration file formats cpb. This is an editable Powerpoint four stages graphic that deals with topics like operational technology cyber security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Technology Overview Cloud Access Security Ppt PowerPoint Presentation Model Ideas Cpb Pdf
Presenting this set of slides with name technology overview cloud access security ppt powerpoint presentation model ideas cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like technology overview cloud access security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
New Technology Handle Cyber Security Ppt PowerPoint Presentation Infographics Graphics Pictures Cpb
Presenting this set of slides with name new technology handle cyber security ppt powerpoint presentation infographics graphics pictures cpb. This is an editable Powerpoint three stages graphic that deals with topics like new technology handle cyber security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Table Of Contents For One Page Yearly Report For Internet Security Company One Pager Documents
Presenting you an exemplary Table Of Contents For One Page Yearly Report For Internet Security Company One Pager Documents. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents For One Page Yearly Report For Internet Security Company One Pager Documents brilliant piece now.

Proposal For Enterprise Security System Table Of Contents One Pager Sample Example Document
Presenting you an exemplary Proposal For Enterprise Security System Table Of Contents One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Table Of Contents One Pager Sample Example Document brilliant piece now.

Proposal For House Security Devices Installation Table Of Contents One Pager Sample Example Document
Presenting you an exemplary Proposal For House Security Devices Installation Table Of Contents One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For House Security Devices Installation Table Of Contents One Pager Sample Example Document brilliant piece now.

Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF
This slide covers quarterly cyber security planning roadmap by management to reduce risk with program maturity and cost .It consist secure , defend, contain, manage and anticipate. Persuade your audience using this Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Management, Level Risk Reduction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
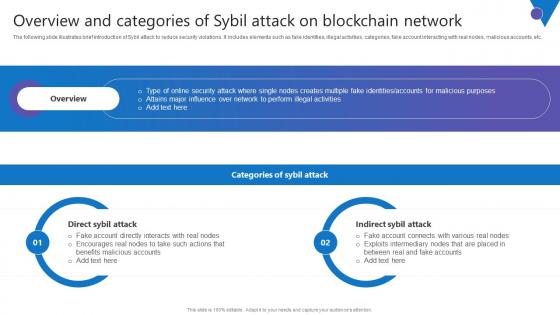
Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf
The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. Are you searching for a Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf from Slidegeeks today. The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc.
Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF bundle. Topics like Gap Analysis, Environmental Trends, Business Strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Smart Phone Device With Security Lock Placed On Table Ppt Professional Inspiration PDF
Persuade your audience using this smart phone device with security lock placed on table ppt professional inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including smart phone device with security lock placed on table. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Case Competition Overpower The Obstacle Of Cyber Security In Medicare Post It Sample PDF
Presenting case competition overpower the obstacle of cyber security in medicare post it sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like post it. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
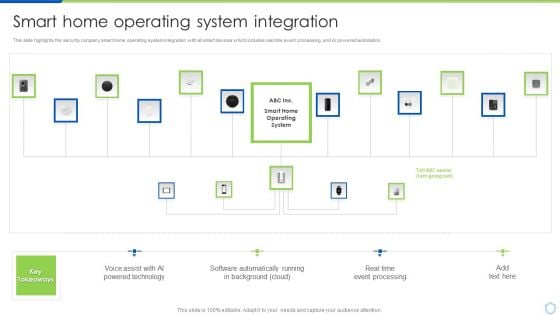
Security And Surveillance Company Profile Smart Home Operating System Integration Clipart PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Smart Home Operating System Integration Clipart PDF bundle. Topics like Powered Technology, Software Automatically, Event Processing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
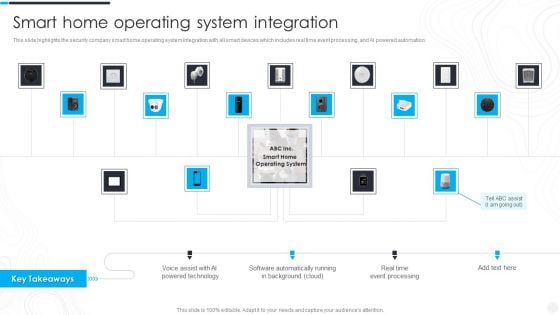
Security Camera System Company Profile Smart Home Operating System Integration Background PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Smart Home Operating System Integration Background PDF bundle. Topics like Powered Technology, Software Automatically, Event Processing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
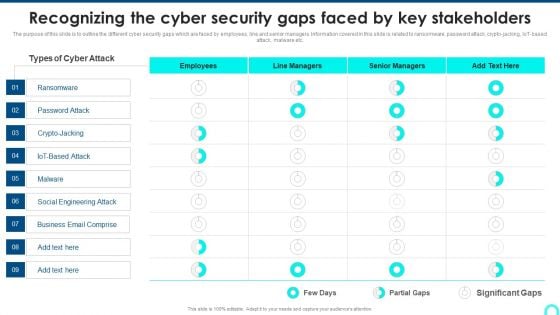
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Deliver and pitch your topic in the best possible manner with this Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF. Use them to share invaluable insights on Ransomware, Engineering Attack, Email Comprise and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Prevention Of Information Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre-designed and impeccable Prevention Of Information Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
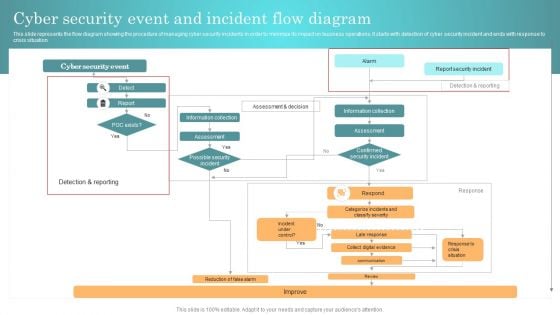
Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
Five Horizontal Steps With Security Analysis Ppt PowerPoint Presentation Gallery Background Image PDF
Persuade your audience using this five horizontal steps with security analysis ppt powerpoint presentation gallery background image pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including segment offering, security, analysis. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
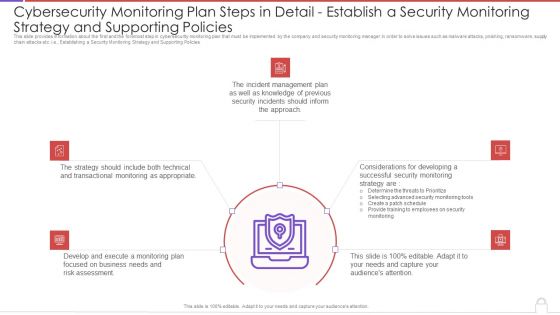
Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Pictures PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Establishing a Security Monitoring Strategy and Supporting Policies. This is a cybersecurity monitoring plan steps in detail establish a security monitoring strategy and pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident management, transactional monitoring, monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Eight Steps Of Portfolio Management With Security Analysis Ppt PowerPoint Presentation Gallery Deck PDF
Persuade your audience using this eight steps of portfolio management with security analysis ppt powerpoint presentation gallery deck pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including security analysis, portfolio analysis, portfolio evaluation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Checklist Of Security Risk Analysis Vector Icon Ppt PowerPoint Presentation File Elements PDF
Persuade your audience using this checklist of security risk analysis vector icon ppt powerpoint presentation file elements pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including checklist of security risk analysis vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
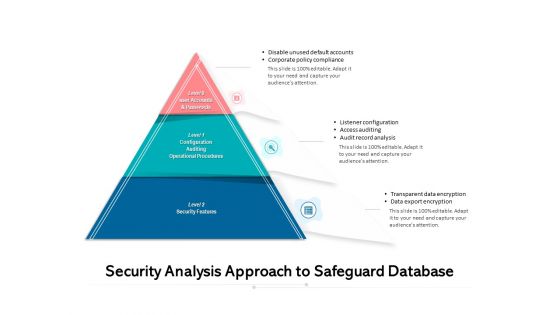
Security Analysis Approach To Safeguard Database Ppt PowerPoint Presentation Show Designs PDF
Persuade your audience using this security analysis approach to safeguard database ppt powerpoint presentation show designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including analysis, corporate policy compliance, operational procedures, security features. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Dsl Is A Best Security Option PowerPoint Templates Ppt Backgrounds For Slides 0713
Give them a dose of your ability. It will go down well with our DSL Is A Best Security Option PowerPoint Templates PPT Backgrounds For Slides. Connect the dots with our People PowerPoint Templates. Watch the whole picture clearly emerge. Dot your thoughts with our Globe PowerPoint Templates. Give your demeanour that Propah look. Make the play with our Dsl Is A Best Security Option PowerPoint Templates Ppt Backgrounds For Slides 0713. Achieve the goals you have set.
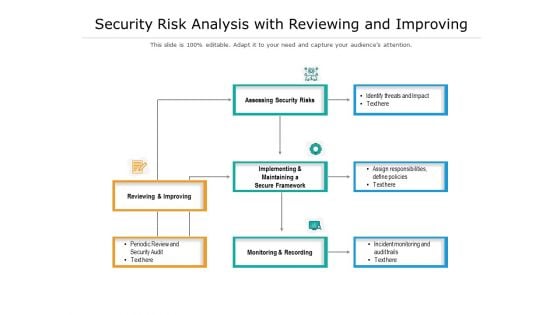
Security Risk Analysis With Reviewing And Improving Ppt PowerPoint Presentation Professional Graphics Download PDF
Persuade your audience using this security risk analysis with reviewing and improving ppt powerpoint presentation professional graphics download pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including assessing security risks, reviewing and improving, monitoring and recording. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Highest Number Of Malware Attacks On Departments Hacking Prevention Awareness Training For IT Security Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this highest number of malware attacks on departments hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on r and d department, it department, accounts department, sales department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Functional Analysis Of Business Operations 4 Dimensions Of Infrastructure Security Designs PDF
Presenting this set of slides with name functional analysis of business operations 4 dimensions of infrastructure security designs pdf. The topics discussed in these slides are employees, infrastructure, data, mobile, cloud. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Threat Analysis Ppt PowerPoint Presentation Infographics Clipart Images Cpb
Presenting this set of slides with name cyber security threat analysis ppt powerpoint presentation infographics clipart images cpb. This is an editable Powerpoint three stages graphic that deals with topics like cyber security threat analysis to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
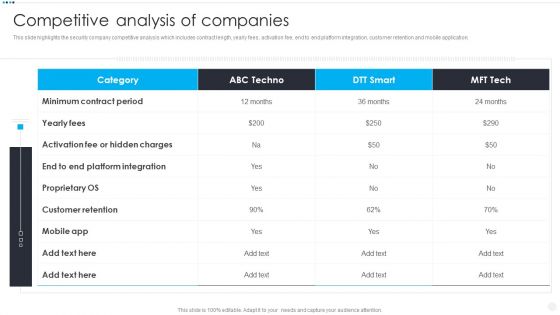
Smart Home Security Solutions Company Profile Competitive Analysis Of Companies Ideas PDF
This slide highlights the security company competitive analysis which includes contract length, yearly fees, activation fee, end to end platform integration, customer retention and mobile application. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Competitive Analysis Of Companies Ideas PDF bundle. Topics like Minimum Contract Period, Activation Fee Hidden, Customer Retention Mobile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
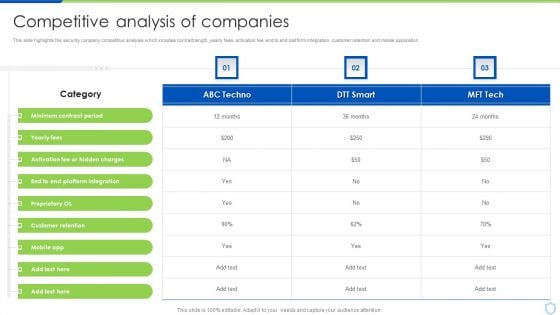
Security And Surveillance Company Profile Competitive Analysis Of Companies Brochure PDF
This slide highlights the security company competitive analysis which includes contract length, yearly fees, activation fee, end to end platform integration, customer retention and mobile application.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Competitive Analysis Of Companies Brochure PDF. Use them to share invaluable insights on Customer Retention, Platform Integration, Minimum Contract and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
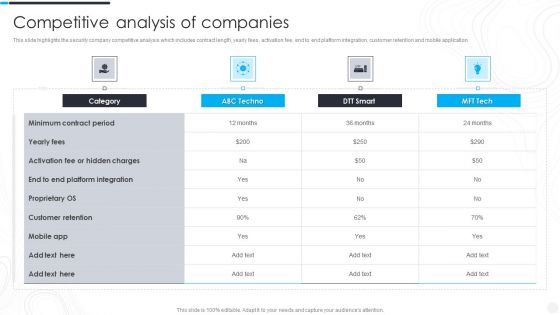
Security Camera System Company Profile Competitive Analysis Of Companies Mockup PDF
This slide highlights the security company competitive analysis which includes contract length, yearly fees, activation fee, end to end platform integration, customer retention and mobile application.Deliver and pitch your topic in the best possible manner with this Security Camera System Company Profile Competitive Analysis Of Companies Mockup PDF. Use them to share invaluable insights on Customer Retention, Hidden Charges, Minimum Contract and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
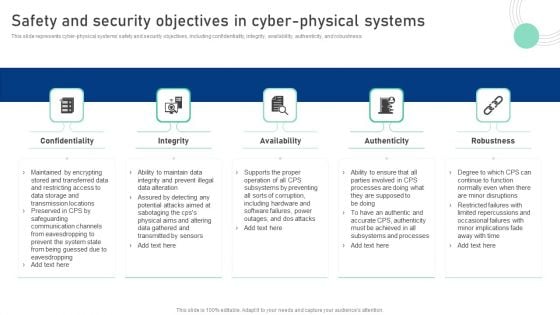
Cyber Physical System To Enhance Safety And Security Objectives In Cyber Physical Systems Information PDF
This slide represents cyber-physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Present like a pro with Cyber Physical System To Enhance Safety And Security Objectives In Cyber Physical Systems Information PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
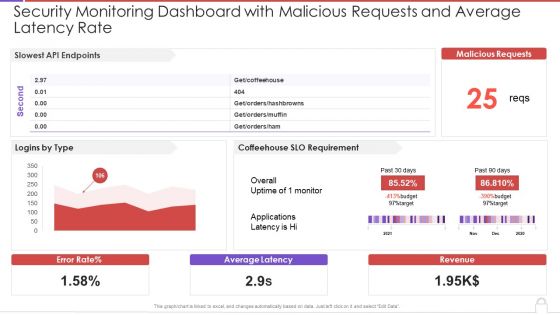
Security Monitoring Dashboard With Malicious Requests And Average Latency Rate Topics PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative security monitoring dashboard with malicious requests and average latency rate topics pdf bundle. Topics like slowest api endpoints, malicious requests, coffeehouse slo can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Vector For Cloud Computing And Security Model Icon Ppt PowerPoint Presentation Icon Samples PDF
Persuade your audience using this vector for cloud computing and security model icon ppt powerpoint presentation icon samples pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector for cloud computing and security model icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Hacker Icon For Online Security Ppt PowerPoint Presentation Styles Example PDF
Persuade your audience using this hacker icon for online security ppt powerpoint presentation styles example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including hacker icon for online security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































