Data Security And Protection

Investment Securities Research Diagram Ppt Slides
This is a investment securities research diagram ppt slides. This is a four stage process. The stages in this process are investment objectives, economic analysis, market analysis, construct portfolio, implement review.
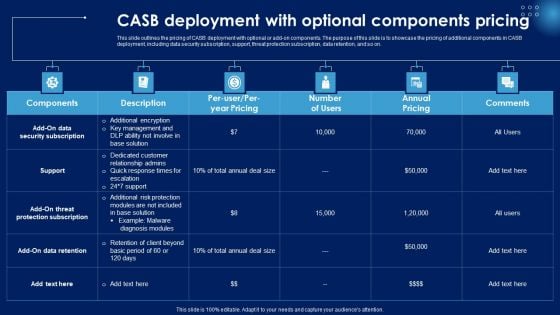
CASB Deployment With Optional Components Pricing Ppt PowerPoint Presentation Diagram Templates PDF
This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Do you know about Slidesgeeks CASB Deployment With Optional Components Pricing Ppt PowerPoint Presentation Diagram Templates PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Cloud Intelligence Framework For Application Consumption Major Cybersecurity Challenges With Required Actions Mockup PDF
The slide provides the key cybersecurity challenges information security, protecting infrastructure, protecting privacy and sensitive data etc. along with the critical actions required from the organization to resolve those challenges. Deliver and pitch your topic in the best possible manner with this cloud intelligence framework for application consumption major cybersecurity challenges with required actions mockup pdf. Use them to share invaluable insights on cybersecurity strategy, performing effective oversight, protecting cyber critical infrastructure, telecommunications, management challenges and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
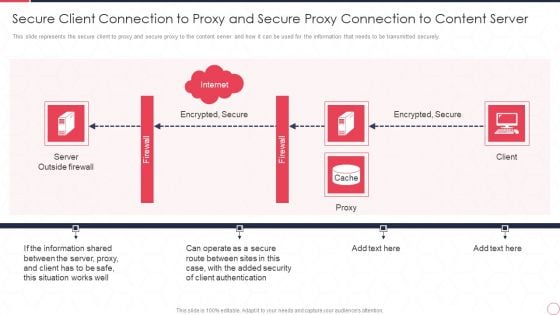
Reverse Proxy Server IT Secure Client Connection To Proxy And Secure Proxy Connection Ppt Infographic Template Design Inspiration PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. This is a reverse proxy server it secure client connection to proxy and secure proxy connection ppt infographic template design inspiration pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like server outside firewall, encrypted, secure, proxy, client. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
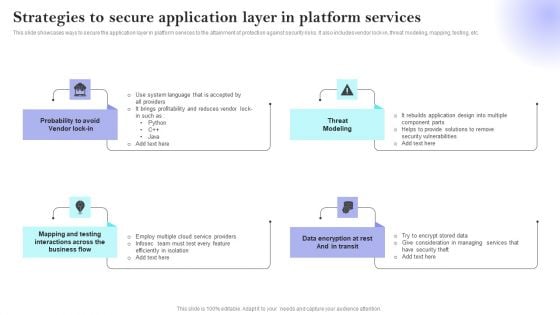
Strategies To Secure Application Layer In Platform Services Topics PDF
This slide showcases ways to secure the application layer in platform services to the attainment of protection against security risks. It also includes vendor lock-in, threat modeling, mapping, testing, etc. Presenting Strategies To Secure Application Layer In Platform Services Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Probability, Threat Modeling, Data Encryption Rest Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
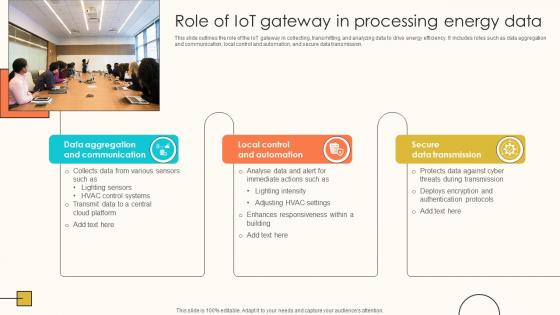
Role Of IoT Gateway In Processing Energy Data Internet Of Things Solutions To Enhance Energy IoT SS V
This slide outlines the role of the IoT gateway in collecting, transmitting, and analyzing data to drive energy efficiency. It includes roles such as data aggregation and communication, local control and automation, and secure data transmission. Do you know about Slidesgeeks Role Of IoT Gateway In Processing Energy Data Internet Of Things Solutions To Enhance Energy IoT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the role of the IoT gateway in collecting, transmitting, and analyzing data to drive energy efficiency. It includes roles such as data aggregation and communication, local control and automation, and secure data transmission.

Web Access Control Solution Relationship Between Secure Access Service Edge And Secure Web Gateway
This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc. Boost your pitch with our creative Web Access Control Solution Relationship Between Secure Access Service Edge And Secure Web Gateway. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc.

Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Business Risk Related To Cloud Computing Data Diagrams PDF
Presenting mesh computing technology hybrid private public iaas paas saas workplan business risk related to cloud computing data diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like financial, data security, technology, operational, vendor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Reverse Proxy Web Server Secure Client Connection To Proxy And Secure Proxy Icons PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. Slidegeeks has constructed Reverse Proxy Web Server Secure Client Connection To Proxy And Secure Proxy Icons PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
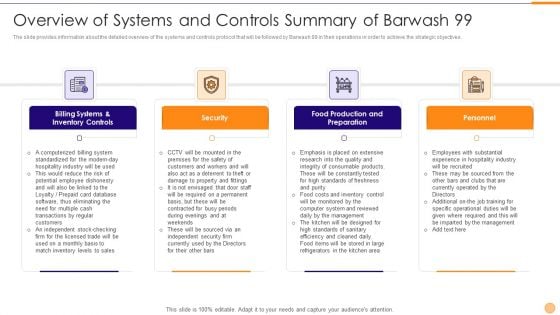
Classified Data Memo Record With Strategic Goals Overview Of Systems And Controls Summary Of Barwash 99 Rules PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. Presenting classified data memo record with strategic goals overview of systems and controls summary of barwash 99 rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like billing systems and inventory controls, security, food production and preparation, personnel. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
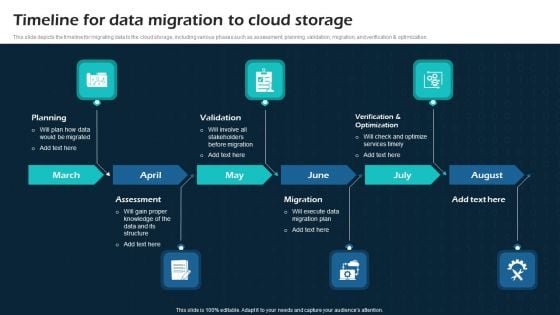
Timeline For Data Migration To Cloud Storage Virtual Cloud Network IT Ppt Visual Aids Example 2015 PDF
This slide depicts the timeline for migrating data to the cloud storage, including various phases such as assessment, planning, validation, migration, and verification and optimization. Presenting this PowerPoint presentation, titled Timeline For Data Migration To Cloud Storage Virtual Cloud Network IT Ppt Visual Aids Example 2015 PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Timeline For Data Migration To Cloud Storage Virtual Cloud Network IT Ppt Visual Aids Example 2015 PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Timeline For Data Migration To Cloud Storage Virtual Cloud Network IT Ppt Visual Aids Example 2015 PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
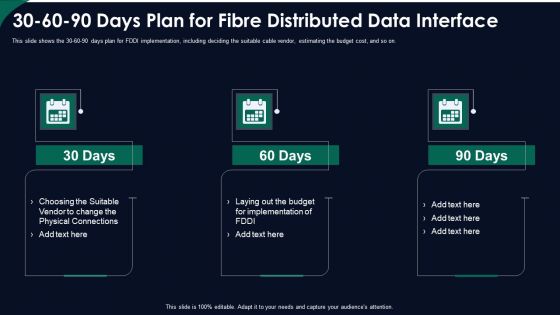
FDDI Network Standard IT 30 60 90 Days Plan For Fibre Distributed Data Interface Ppt Inspiration Diagrams PDF
This slide shows the 30 60 90 days plan for FDDI implementation, including deciding the suitable cable vendor, estimating the budget cost, and so on. This is a fddi network standard it 30 60 90 days plan for fibre distributed data interface ppt inspiration diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan for fibre distributed data interface. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Secured Money Finance PowerPoint Templates And PowerPoint Themes 1112
We present our Secured Money Finance PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because,To strive to give true form to your great dream. Use our Success PowerPoint Templates because, Highlight your ideas broad- based on strong fundamentals and illustrate how they step by step acheive the set growth factor. Use our Signs PowerPoint Templates because, Develop your marketing strategy and communicate your ethusiasm and motivation to raise the bar. Use our Money PowerPoint Templates because, Anticipate the doubts and questions in the minds of your colleagues and enlighten them with your inspired strategy to garner desired success. Use our Business PowerPoint Templates because,Marketing Strategy Business Template:- Maximising sales of your product is the intended destination.Use these PowerPoint slides for presentations relating to Protection of money, security, success, money, signs, business. The prominent colors used in the PowerPoint template are Blue navy, Black, Yellow Make a great career call with our Secured Money Finance PowerPoint Templates And PowerPoint Themes 1112. Put your ideas across emphatically.

Data Center Migration For Information Technology Systems Assessment And To Create Resilient Network Ppt PowerPoint Presentation Complete Deck
Executing a project plan for a business need Here is a top-notch solution for you to carry out the required tasks with complete precision and consistency. Deploy this easy-to-use Data Center Migration For Information Technology Systems Assessment And To Create Resilient Network Ppt PowerPoint Presentation Complete Deck to list the number of activities to be executed, key deliverables, and project phases to bring clarity for your team members. Grab this well-crafted fourty four slide complete deck to deliver a quality project within your deadline. The presentation template is also equipped to do this with its 100 precent editable and customizable capability. Download now.
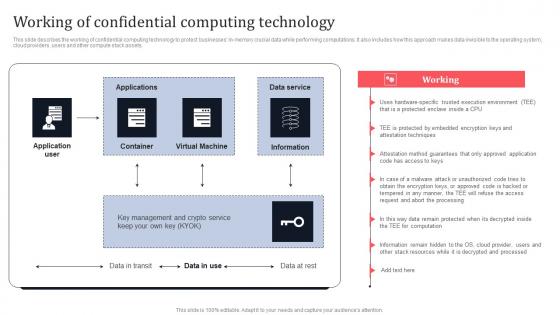
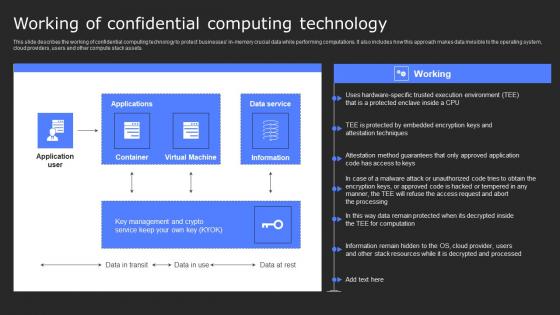
Working Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Confidential Computing Technology Secure Multi Party Information Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Slidegeeks is here to make your presentations a breeze with Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Presenting this PowerPoint presentation, titled Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.

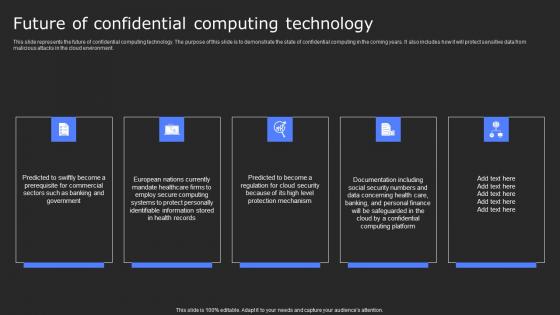
Future Of Confidential Computing Technology Secure Multi Party Rules Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Slidegeeks has constructed Future Of Confidential Computing Technology Secure Multi Party Rules Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.

Secure Email Technology PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Secure Email Technology PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Technology PowerPoint Templates because Your audience will believe you are the cats whiskers. Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Present our Communication PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download and present our Signs PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium.Use these PowerPoint slides for presentations relating to Illustration of envelope and email sign protect with padloc, security, communication, technology, business, signs. The prominent colors used in the PowerPoint template are Red, Gray, Yellow. Deal a decisive blow with our Secure Email Technology PowerPoint Templates Ppt Backgrounds For Slides 0413. Get clearlyahead in a critical event.
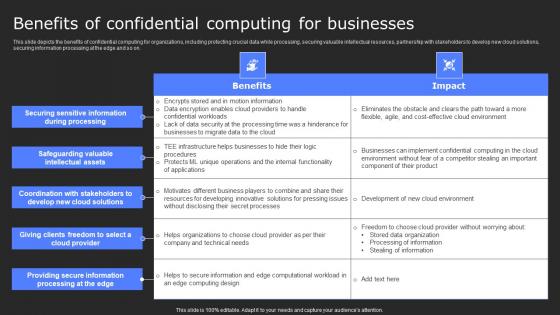
Benefits Of Confidential Computing For Secure Computing Framework Microsoft Pdf
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Confidential Computing For Secure Computing Framework Microsoft Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on.
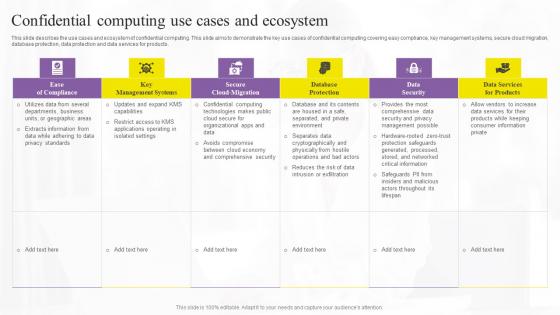
Confidential Computing Use Cases Confidential Computing Technologies Portrait Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Slidegeeks has constructed Confidential Computing Use Cases Confidential Computing Technologies Portrait Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
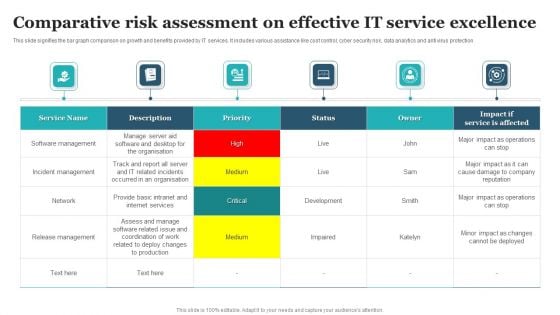
Comparative Risk Assessment On Effective IT Service Excellence Designs PDF
This slide signifies the bar graph comparison on growth and benefits provided by IT services. It includes various assistance like cost control, cyber security risk, data analytics and anti virus protection. Showcasing this set of slides titled Comparative Risk Assessment On Effective IT Service Excellence Designs PDF. The topics addressed in these templates are Software Management, Incident Management, Release Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
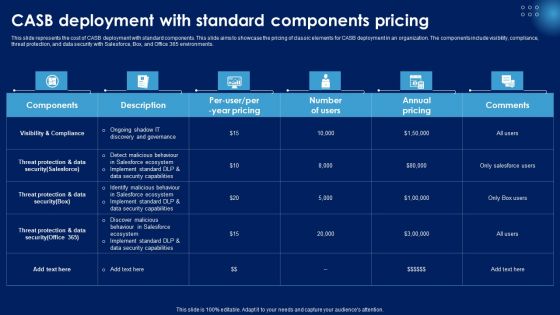
CASB Deployment With Standard Components Pricing Ppt PowerPoint Presentation File Example File PDF
This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. There are so many reasons you need a CASB Deployment With Standard Components Pricing Ppt PowerPoint Presentation File Example File PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
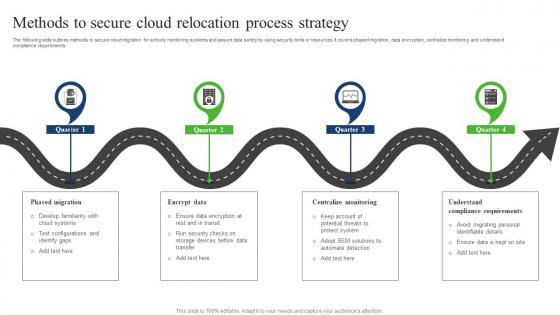
Methods To Secure Cloud Relocation Process Strategy Sample Pdf
The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements. Showcasing this set of slides titled Methods To Secure Cloud Relocation Process Strategy Sample Pdf. The topics addressed in these templates are Centralize Monitoring, Understand Compliance Requirements, Phased Migration, Encrypt Data . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements.
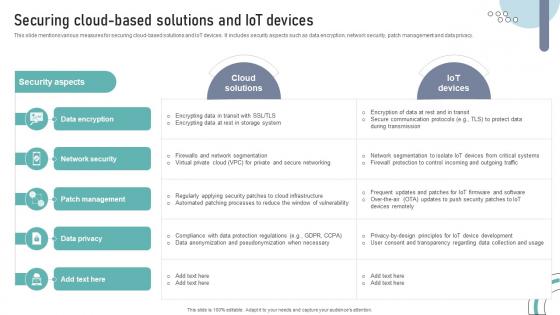
Securing Cloud Based Solutions And IOT Devices DT SS V
This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy. Slidegeeks has constructed Securing Cloud Based Solutions And IOT Devices DT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy.
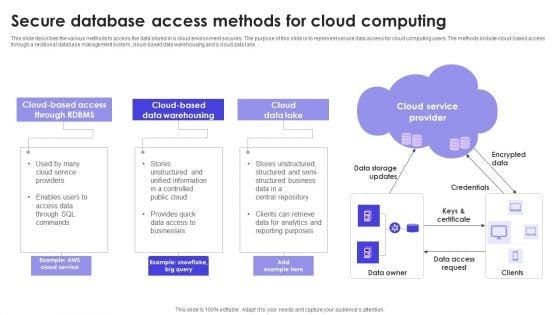
Secure Database Access Methods For Cloud Computing Formats PDF
This slide describes the various methods to access the data stored in a cloud environment securely. The purpose of this slide is to represent secure data access for cloud computing users. The methods include cloud-based access through a relational database management system, cloud-based data warehousing and a cloud data lake. Persuade your audience using this Secure Database Access Methods For Cloud Computing Formats PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Data Lake, Data Warehousing, Cloud Service Provider. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cryptocurrency Ledger Is Blockchain Technology Secure Slides PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Deliver an awe inspiring pitch with this creative Cryptocurrency Ledger Is Blockchain Technology Secure Slides PDF bundle. Topics like Digital Data, Blockchain Networks, Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
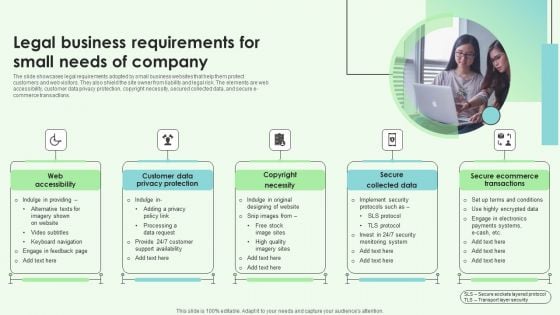
Legal Business Requirements For Small Needs Of Company Inspiration PDF
The slide showcases legal requirements adopted by small business websites that help them protect customers and web visitors. They also shield the site owner from liability and legal risk. The elements are web accessibility, customer data privacy protection, copyright necessity, secured collected data, and secure e-commerce transactions. Presenting Legal Business Requirements For Small Needs Of Company Inspiration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Copyright Necessity, Secure Collected Data, Secure Ecommerce Transactions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
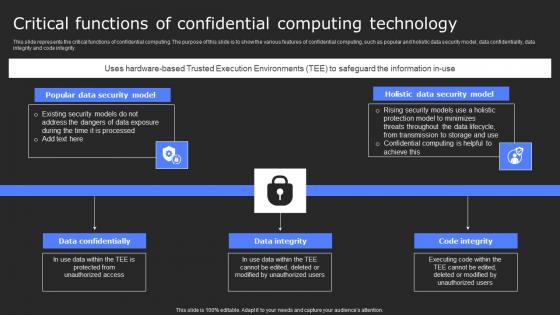
Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Are you searching for a Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf from Slidegeeks today. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
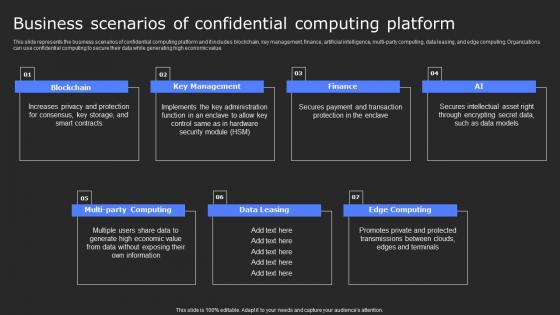
Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. There are so many reasons you need a Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
Hacker Trying To Steal Secured Virtual Identity Sample PDF
Persuade your audience using this hacker trying to steal secured virtual identity sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including hacker trying to steal secured virtual identity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Secured Internet Connections PowerPoint Templates Ppt Backgrounds For Slides 0813
Get the doers into action. Activate them with our Secured Internet Connections PowerPoint Templates PPT Backgrounds For Slides. Put your money on our Technology PowerPoint Templates. Your ideas will rake in the dollars. Put in a dollop of our Security PowerPoint Templates. Give your thoughts a distinctive flavour.

Secure Internet Browser PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Secure Internet Browser PowerPoint Templates PPT Backgrounds For Slides 0313.Use our Network diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Download our Technology PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script.Use these PowerPoint slides for presentations relating to Secure Internet Browser, network diagrams, security, technology, signs, shapes. The prominent colors used in the PowerPoint template are Gray, Yellow, Black. Take flight with our Secure Internet Browser PowerPoint Templates Ppt Backgrounds For Slides 0313. Just download, type and present.

Secure Access Lock Clipart Ppt PowerPoint Presentation Summary File Formats
This is a secure access lock clipart ppt powerpoint presentation summary file formats. This is a four stage process. The stages in this process are computer software, operating system, open source.
Practices For Secure Online Transactions Processing Ppt Icon Themes PDF
This slide mentions practices for online transactions processing to ensure secure checkout process. It includes matching IP and billing address, Encrypt data and use payment tokenization method. Persuade your audience using this Practices For Secure Online Transactions Processing Ppt Icon Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Encrypt Data, Use Payment Tokenization, IP And Billing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
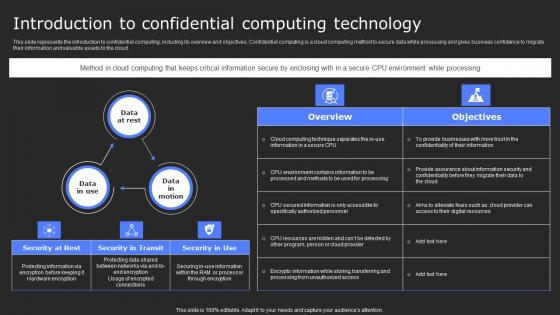
Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Boost your pitch with our creative Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.

Secured Laptop Technology PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Secured Laptop Technology PowerPoint Templates PPT Backgrounds For Slides 0213.Use our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Present our Business PowerPoint Templates because They will bring a lot to the table. Their alluring flavours will make your audience salivate. Present our Signs PowerPoint Templates because You can Hit the nail on the head with our PowerPoint Templates and Slides. Embed your ideas in the minds of your audience. Download and present our Security PowerPoint Templates because You aspire to touch the sky with glory. Let our PowerPoint Templates and Slides provide the fuel for your ascent. Use our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides team portray an attitude of elegance. Personify this quality by using them regularly.Use these PowerPoint slides for presentations relating to Notebook Lockable, technology, business, security, signs, shapes. The prominent colors used in the PowerPoint template are Red, Gray, Yellow. Get all factions to act together. Our Secured Laptop Technology PowerPoint Templates Ppt Backgrounds For Slides 0213 can help achieve a common cause.

Secured Internet Connection PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Secured Internet Connection PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Security PowerPoint Templates because You should Throw the gauntlet with our PowerPoint Templates and Slides. They are created to take up any challenge. Present our Technology PowerPoint Templates because you can Break through with our PowerPoint Templates and Slides. Bring down the mental barriers of your audience. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process. Download and present our Shapes PowerPoint Templates because You will get more than you ever bargained for. Use our Signs PowerPoint Templates because Our PowerPoint Templates and Slides are focused like a searchlight beam. They highlight your ideas for your target audience.Use these PowerPoint slides for presentations relating to Browser window with a Key, security, business, technology, signs, shapes. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Advertise your expertise with our Secured Internet Connection PowerPoint Templates Ppt Backgrounds For Slides 0313. Establish your undeniable command over the subject.

Secure Your Money PowerPoint Templates Ppt Backgrounds For Slides 0413
Our Secure Your Money PowerPoint Templates PPT Backgrounds For Slides 0413 allow you to do it with ease. Just like picking the low hanging fruit. Boil the ocean with your thoughts. Our Secure Your Money PowerPoint Templates PPT Backgrounds For Slides 0413 will help create waves. Communicate goals with our Secure Your Money PowerPoint Templates Ppt Backgrounds For Slides 0413. Download without worries with our money back guaranteee.

Secure Folders Computer PowerPoint Templates And PowerPoint Themes 1012
Secure Folders Computer PowerPoint Templates And PowerPoint Themes 1012-Microsoft Powerpoint Templates and Background with computer folder with key-Secure Folders Computer PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Computer folder with key, security, success, computer, business, shapes Our Secure Folders Computer PowerPoint Templates And PowerPoint Themes 1012 have a high degree of quality. Every element gets close attention.

Secure Internet Browser Computer PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with transparent internet browser with a lock padlock intersecting it List your core competencies with our Secure Internet Browser Computer PowerPoint Templates And PowerPoint Backgrounds 0811. They will make you look good.

Secure Internet Browser Computer PowerPoint Themes And PowerPoint Slides 0811
Microsoft PowerPoint Theme and Slide with transparent internet browser with a lock padlock intersecting it Our Secure Internet Browser Computer PowerPoint Themes And PowerPoint Slides 0811 have amazing characteristics. They educate and entertain on your command.

Secure Folders Computer PowerPoint Templates And PowerPoint Themes 0812
Secure Folders Computer PowerPoint Templates And PowerPoint Themes 0812-Microsoft Powerpoint Templates and Background with computer folder with key Kill doubts with our Secure Folders Computer PowerPoint Templates And PowerPoint Themes 0812. You will come out on top.
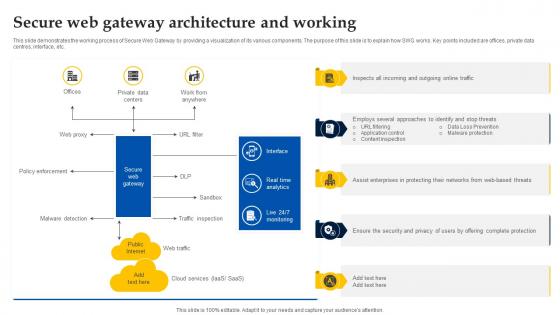
Web Access Control Solution Secure Web Gateway Architecture And Working
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Web Access Control Solution Secure Web Gateway Architecture And Working for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc.

Stock Photo Business Strategy Innovation Make Secure Folder Images
Our stock photo business strategy innovation make secure folder stock photo images Powerpoint Templates Heighten Concentration. Your Audience Will Be On The Edge. Get An Edge With Our Security Powerpoint Templates. They Give You Advantage Plus.
Blockchain Technology Framework IT Is Blockchain Technology Secure Demonstration PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. This is a blockchain technology framework it is blockchain technology secure demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like expensive, systems, blockchain network, operations database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
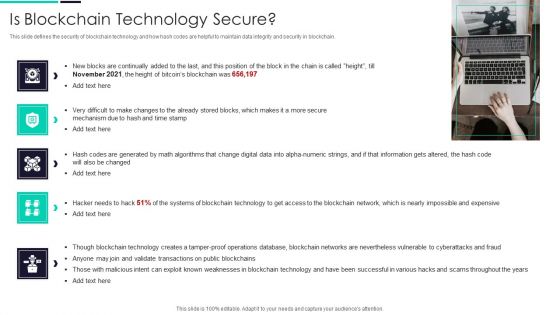
Blockchain And DLT Framework Is Blockchain Technology Secure Ideas PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. This is a Blockchain And DLT Framework Is Blockchain Technology Secure Ideas PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Time Stamp, Blockchain Technology, Weaknesses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Secure Digital Mail Internet PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface Our Secure Digital Mail Internet PowerPoint Presentation Slides C need no exaggeration. They are an advertisement for themselves.

Secure Digital Mail Internet PowerPoint Presentation Slides Cc
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface No matter how far you have to go. Our Secure Digital Mail Internet PowerPoint Presentation Slides Cc have the drive to get you there.

Secure Digital Mail Internet PowerPoint Presentation Slides F
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface Delight your audience with our Secure Digital Mail Internet PowerPoint Presentation Slides F. You will come out on top.

Secure Digital Mail Internet PowerPoint Presentation Slides R
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface Our Secure Digital Mail Internet PowerPoint Presentation Slides R will be your lucky charm. They will deliver for you on your fateful day.

Secure Digital Mail Internet PowerPoint Presentation Slides S
Microsoft PowerPoint Slides and Backgrounds with illustration of a chromeate mail symbol surrounded by aring of glowing green binary digits with a heavy metallic pad lock attached toit on a dark gray reflective surface With our Secure Digital Mail Internet PowerPoint Presentation Slides S you will get far ahead. Let your competitors play catch up.

Secure Internet Access Computer PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with transparent internet browser with a large chrome key protruding out from the window Recognize your calling with our Secure Internet Access Computer PowerPoint Templates And PowerPoint Backgrounds 0811. Download without worries with our money back guaranteee.

Secure Internet Access Computer PowerPoint Themes And PowerPoint Slides 0811
Microsoft PowerPoint Theme and Slide with transparent internet browser with a large chrome key protruding out from the window Fight off critics with our Secure Internet Access Computer PowerPoint Themes And PowerPoint Slides 0811. Be confident and convinced of your assessment.

DLT Technology Is Blockchain Technology Secure Pictures PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download DLT Technology Is Blockchain Technology Secure Pictures PDF from Slidegeeks and deliver a wonderful presentation.

Secured World PowerPoint Templates Ppt Backgrounds For Slides 0713
Double your chances with our Secured World PowerPoint Templates PPT Backgrounds For Slides. The value of your thoughts will increase two-fold. Charm the audience with your thoughts. Add our security PowerPoint Templates and they will be dotty for you. Double up our umbrellas PowerPoint Templates with your thoughts. They will make an awesome pair. Achievements flow from our Secured World PowerPoint Templates Ppt Backgrounds For Slides 0713. They encourage affirmative action.
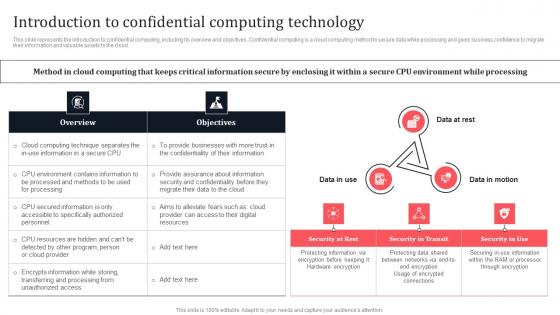
Introduction To Confidential Computing Technology Secure Multi Party Download Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Do you know about Slidesgeeks Introduction To Confidential Computing Technology Secure Multi Party Download Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
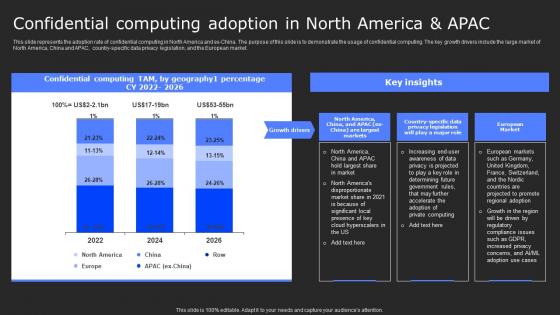
Confidential Computing Adoption In North Secure Computing Framework Template Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Adoption In North Secure Computing Framework Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Adoption In North Secure Computing Framework Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.

Securing Investor Funding The DocuSign Elevator Pitch Deck Ppt Template

Secure Web Gateway SWG Functional Components Ppt Infographics Picture PDF
This slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Secure Web Gateway SWG Functional Components Ppt Infographics Picture PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.


 Continue with Email
Continue with Email

 Home
Home


































