Editing
Strategies To Build Meaningful Comparative Analysis Of Ai Powered Meeting Assistant Apps Structure PDF
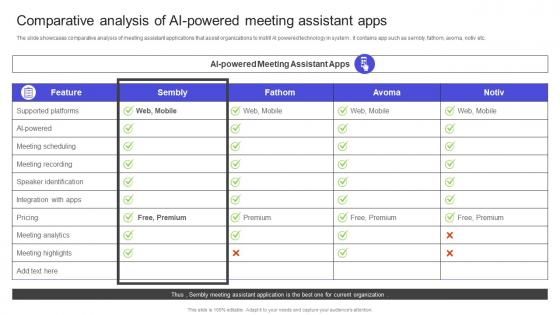
The slide showcases comparative analysis of meeting assistant applications that assist organizations to instill AI powered technology in system . it contains app such as sembly, fathom, avoma, notiv etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Strategies To Build Meaningful Comparative Analysis Of Ai Powered Meeting Assistant Apps Structure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Strategies To Build Meaningful Comparative Analysis Of Ai Powered Meeting Assistant Apps Structure PDF You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The slide showcases comparative analysis of meeting assistant applications that assist organizations to instill AI powered technology in system . it contains app such as sembly, fathom, avoma, notiv etc.
Strategies To Build Meaningful Effective Team Relationship Management Skills Template PDF
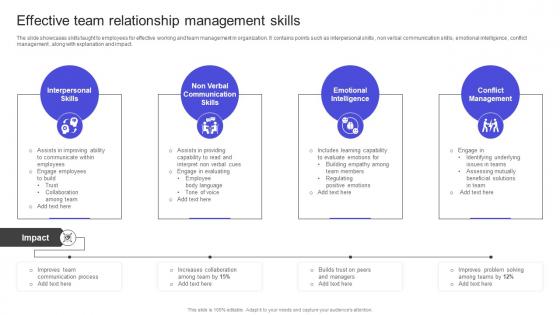
The slide showcases skills taught to employees for effective working and team management in organization. It contains points such as interpersonal skills , non verbal communication skills , emotional intelligence , conflict management , along with explanation and impact. Get a simple yet stunning designed Strategies To Build Meaningful Effective Team Relationship Management Skills Template PDF It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Strategies To Build Meaningful Effective Team Relationship Management Skills Template PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide showcases skills taught to employees for effective working and team management in organization. It contains points such as interpersonal skills , non verbal communication skills , emotional intelligence , conflict management , along with explanation and impact.
Strategies To Build Meaningful Elimination Of Problems In Team Relationship Management Structure PDF
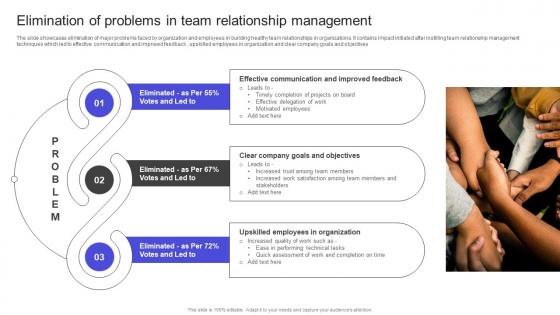
The slide showcases elimination of major problems faced by organization and employees in building healthy team relationships in organizations. It contains impact initiated after instilling team relationship management techniques which led to effective communication and improved feedback , upskilled employees in organization and clear company goals and objectives From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Strategies To Build Meaningful Elimination Of Problems In Team Relationship Management Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The slide showcases elimination of major problems faced by organization and employees in building healthy team relationships in organizations. It contains impact initiated after instilling team relationship management techniques which led to effective communication and improved feedback , upskilled employees in organization and clear company goals and objectives
Strategies To Build Meaningful Employee Rewards Management And Recognition Framework Diagrams PDF
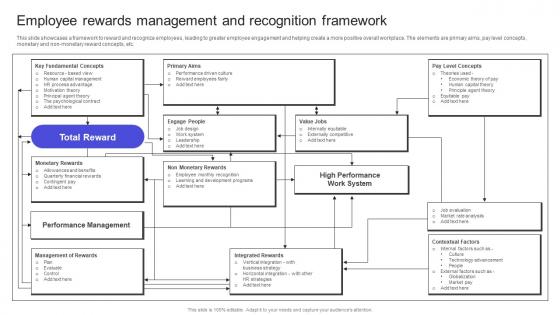
This slide showcases a framework to reward andrecognize employees, leading to greater employee engagement and helping create a more positive overall workplace. The elements are primary aims, pay level concepts, monetary and non-monetary reward concepts, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Strategies To Build Meaningful Employee Rewards Management And Recognition Framework Diagrams PDF can be your best option for delivering a presentation. Represent everything in detail using Strategies To Build Meaningful Employee Rewards Management And Recognition Framework Diagrams PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases a framework to reward andrecognize employees, leading to greater employee engagement and helping create a more positive overall workplace. The elements are primary aims, pay level concepts, monetary and non-monetary reward concepts, etc.

Strategies To Build Meaningful Key Communication Techniques For Better Team Relationships Mockup PDF
The slide showcases techniques used by manager in organizations for effective communication in teams and better understanding work to be done . It contains points such as feedback method, social media based technique , two way communication , osmotic communication etc. Welcome to our selection of the Strategies To Build Meaningful Key Communication Techniques For Better Team Relationships Mockup PDF These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today The slide showcases techniques used by manager in organizations for effective communication in teams and better understanding work to be done . It contains points such as feedback method, social media based technique , two way communication , osmotic communication etc.
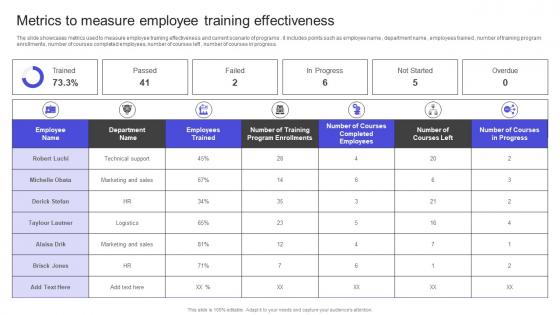
Strategies To Build Meaningful Metrics To Measure Employee Training Effectiveness Sample PDF
The slide showcases metrics used to measure employee training effectiveness and current scenario of programs . it includes points such as employee name , department name , employees trained , number of training program enrollments , number of courses completed employees, number of courses left , number of courses in progress. Explore a selection of the finest Strategies To Build Meaningful Metrics To Measure Employee Training Effectiveness Sample PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Strategies To Build Meaningful Metrics To Measure Employee Training Effectiveness Sample PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The slide showcases metrics used to measure employee training effectiveness and current scenario of programs . it includes points such as employee name , department name , employees trained , number of training program enrollments , number of courses completed employees, number of courses left , number of courses in progress.
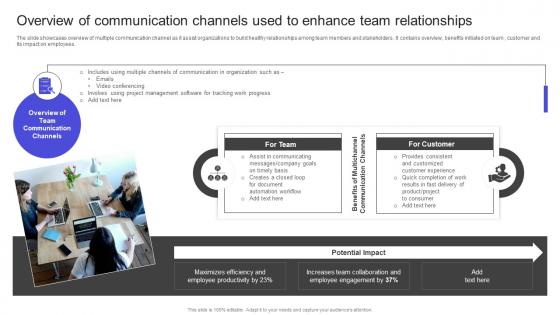
Strategies To Build Meaningful Overview Of Communication Channels Used To Enhance Team Slides PDF
The slide showcases overview of multiple communication channel as it assist organizations to build healthy relationships among team members and stakeholders . It contains overview, benefits initiated on team , customer and its impact on employees. Are you searching for a Strategies To Build Meaningful Overview Of Communication Channels Used To Enhance Team Slides PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Strategies To Build Meaningful Overview Of Communication Channels Used To Enhance Team Slides PDF from Slidegeeks today. The slide showcases overview of multiple communication channel as it assist organizations to build healthy relationships among team members and stakeholders . It contains overview, benefits initiated on team , customer and its impact on employees.
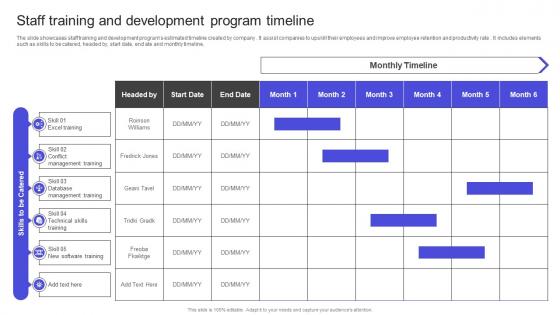
Strategies To Build Meaningful Staff Training And Development Program Timeline Graphics PDF
The slide showcases staff training and development programs estimated timeline created by company . It assist companies to upskill their employees and improve employee retention and productivity rate . It includes elements such as skills to be catered, headed by, start date, end ate and monthly timeline, Do you know about Slidesgeeks Strategies To Build Meaningful Staff Training And Development Program Timeline Graphics PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The slide showcases staff training and development programs estimated timeline created by company . It assist companies to upskill their employees and improve employee retention and productivity rate . It includes elements such as skills to be catered, headed by, start date, end ate and monthly timeline,
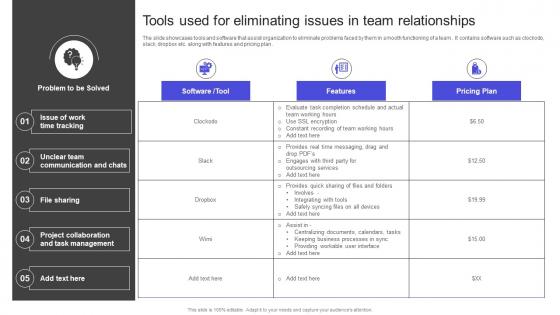
Strategies To Build Meaningful Tools Used For Eliminating Issues In Team Relationships Introduction PDF
The slide showcases tools and software that assist organization to eliminate problems faced by them in smooth functioning of a team . It contains software such as clockodo, slack, dropbox etc. along with features and pricing plan . Get a simple yet stunning designed Strategies To Build Meaningful Tools Used For Eliminating Issues In Team Relationships Introduction PDF It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Strategies To Build Meaningful Tools Used For Eliminating Issues In Team Relationships Introduction PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide showcases tools and software that assist organization to eliminate problems faced by them in smooth functioning of a team . It contains software such as clockodo, slack, dropbox etc. along with features and pricing plan .
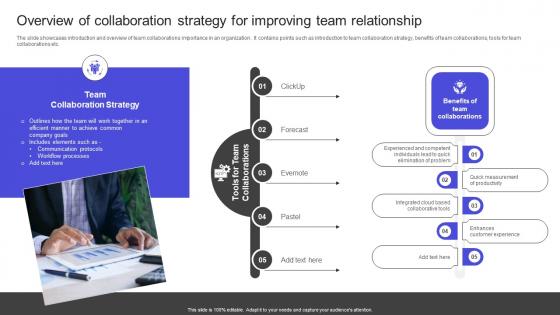
Strategies To Build Meaningful Overview Of Collaboration Strategy For Improving Team Themes Pdf
The slide showcases introduction and overview of team collaborations importance in an organization . It contains points such as introduction to team collaboration strategy, benefits of team collaborations, tools for team collaborations etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Strategies To Build Meaningful Overview Of Collaboration Strategy For Improving Team Themes Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Strategies To Build Meaningful Overview Of Collaboration Strategy For Improving Team Themes Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The slide showcases introduction and overview of team collaborations importance in an organization . It contains points such as introduction to team collaboration strategy, benefits of team collaborations, tools for team collaborations etc.
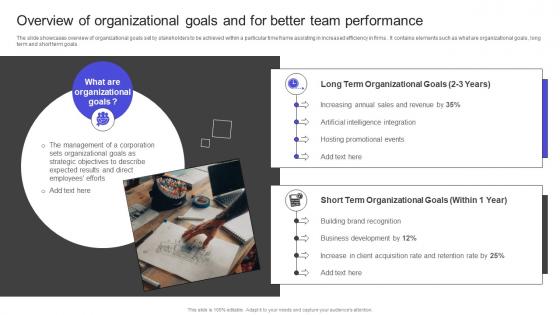
Strategies To Build Meaningful Overview Of Organizational Goals And For Better Team Guidelines Pdf
The slide showcases overview of organizational goals set by stakeholders to be achieved within a particular time frame assisting in increased efficiency in firms . It contains elements such as what are organizational goals , long term and short term goals . Get a simple yet stunning designed Strategies To Build Meaningful Overview Of Organizational Goals And For Better Team Guidelines Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Strategies To Build Meaningful Overview Of Organizational Goals And For Better Team Guidelines Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide showcases overview of organizational goals set by stakeholders to be achieved within a particular time frame assisting in increased efficiency in firms . It contains elements such as what are organizational goals , long term and short term goals .
Strategies To Build Meaningful Strategies Opted By Managers For Tracking Employee Performance Demonstration Pdf
The slide showcases strategies opted by managers in organizations that assist them tracking employee performance . it contains points such as set achievable goals , enhance leadership skills , employee monitoring software , gain 360 degree feedback , perform appraisals etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Strategies To Build Meaningful Strategies Opted By Managers For Tracking Employee Performance Demonstration Pdf can be your best option for delivering a presentation. Represent everything in detail using Strategies To Build Meaningful Strategies Opted By Managers For Tracking Employee Performance Demonstration Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The slide showcases strategies opted by managers in organizations that assist them tracking employee performance . it contains points such as set achievable goals , enhance leadership skills , employee monitoring software , gain 360 degree feedback , perform appraisals etc.

Case Study Intellectual Property Protection With Zero Trust Network Security Inspiration Pdf
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Want to ace your presentation in front of a live audience Our Case Study Intellectual Property Protection With Zero Trust Network Security Inspiration Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.
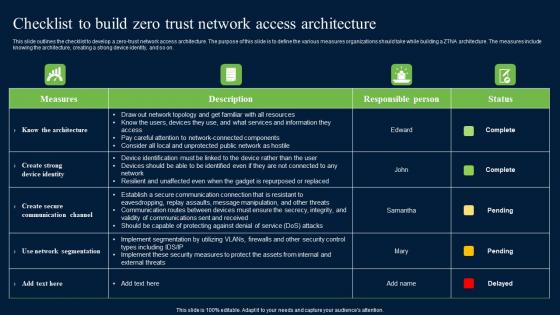
Checklist To Build Zero Trust Network Access Security Structure Pdf
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Security Structure Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Security Structure Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.
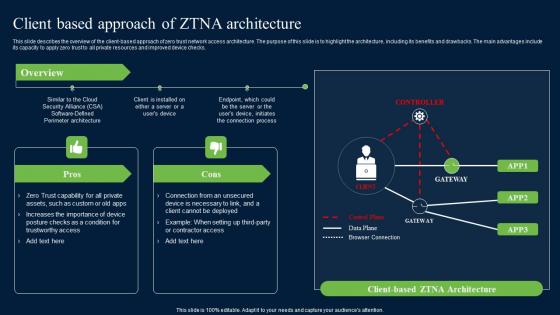
Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.
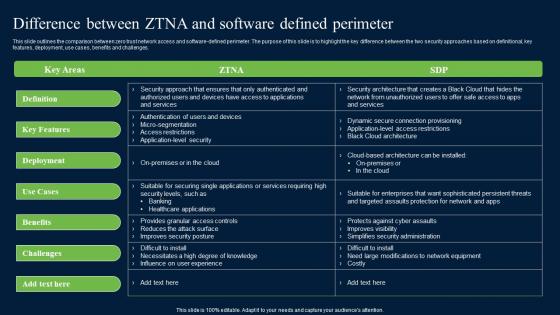
Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf can be your best option for delivering a presentation. Represent everything in detail using Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.

Main Pillars Of Zero Network Trust Access Zero Trust Network Security Professional Pdf
This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. Welcome to our selection of the Main Pillars Of Zero Network Trust Access Zero Trust Network Security Professional Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation.
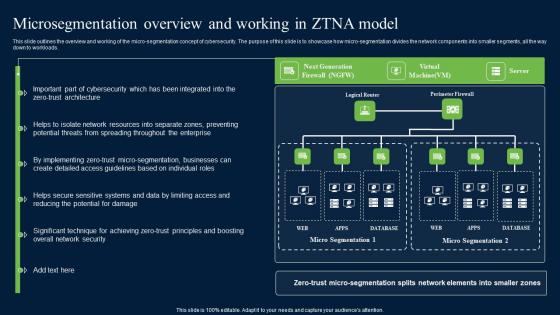
Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.
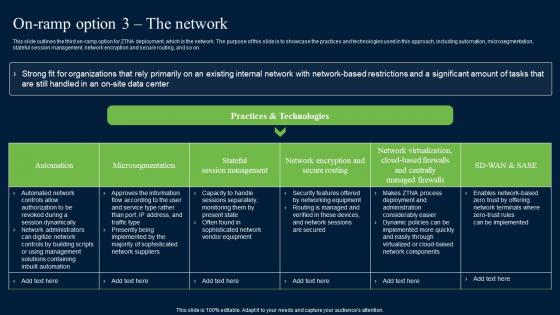
On Ramp Option 3 The Network Zero Trust Network Security Information Pdf
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Zero Trust Network Security Information Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Zero Trust Network Security Information Pdf from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
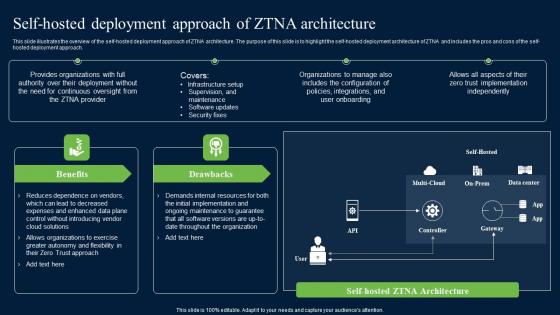
Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Network Security Graphics Pdf
This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach. Do you know about Slidesgeeks Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Network Security Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach.
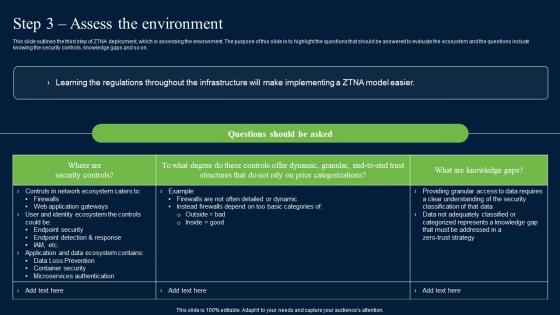
Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Want to ace your presentation in front of a live audience Our Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.

Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment.
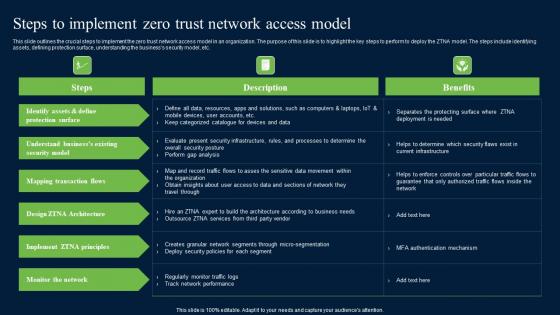
Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Get a simple yet stunning designed Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on.
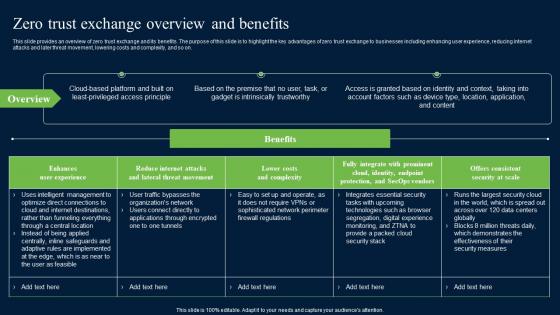
Zero Trust Exchange Overview And Benefits Zero Trust Network Security Introduction Pdf
This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on. Want to ace your presentation in front of a live audience Our Zero Trust Exchange Overview And Benefits Zero Trust Network Security Introduction Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on.
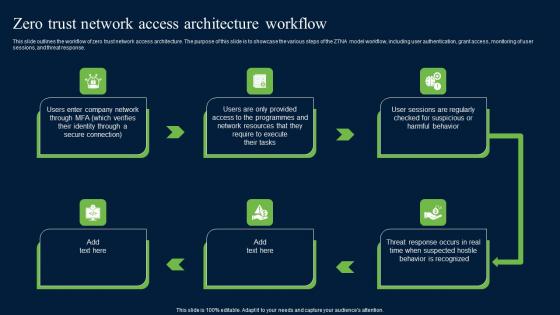
Zero Trust Network Access Architecture Workflow Themes Pdf
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Network Access Architecture Workflow Themes Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Network Access Architecture Workflow Themes Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
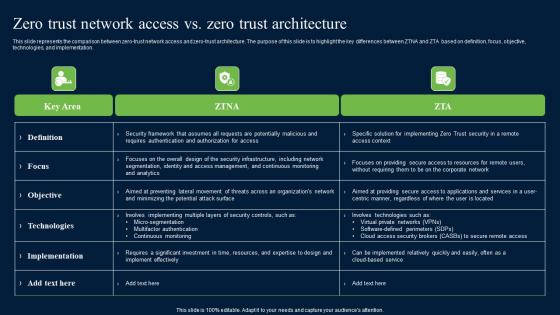
Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.
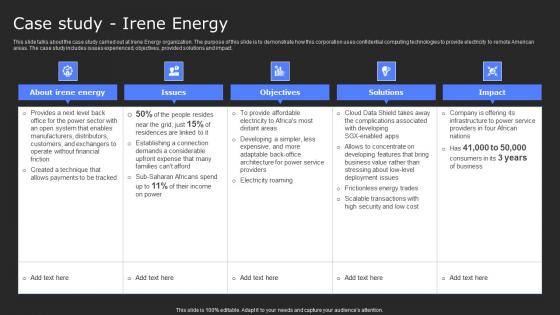
Case Study Irene Energy Secure Computing Framework Ideas Pdf
This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Case Study Irene Energy Secure Computing Framework Ideas Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Case Study Irene Energy Secure Computing Framework Ideas Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact.
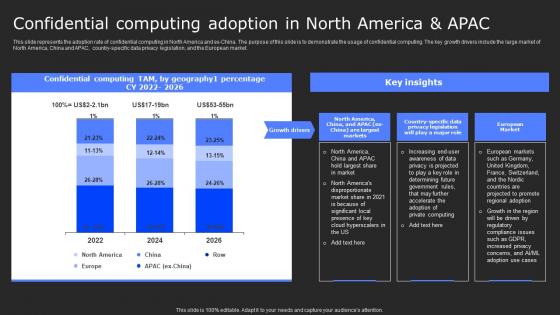
Confidential Computing Adoption In North Secure Computing Framework Template Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Adoption In North Secure Computing Framework Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Adoption In North Secure Computing Framework Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
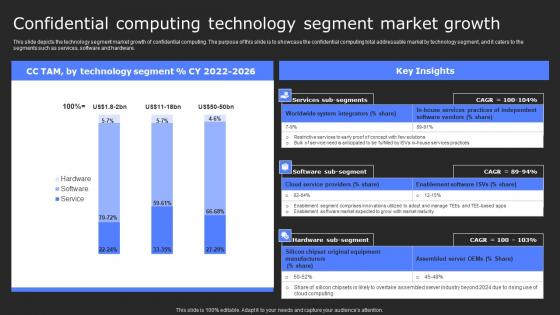
Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf
This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Explore a selection of the finest Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware.
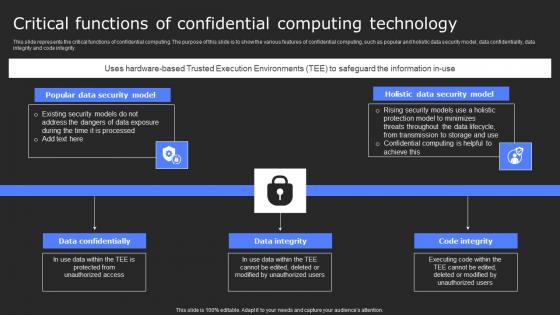
Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Are you searching for a Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf from Slidegeeks today. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
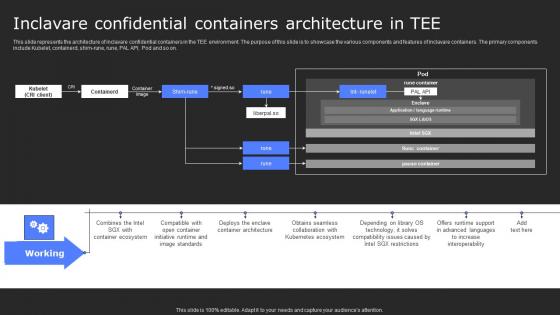
Inclavare Confidential Containers Architecture In Tee Secure Computing Framework Infographics Pdf
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Do you know about Slidesgeeks Inclavare Confidential Containers Architecture In Tee Secure Computing Framework Infographics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on.
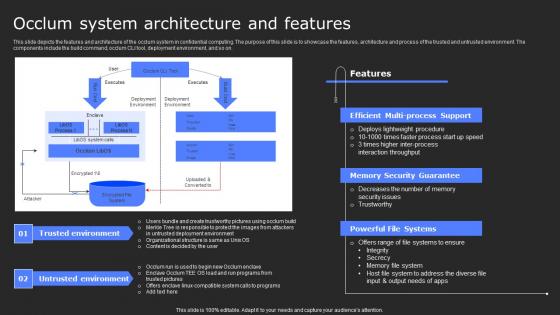
Occlum System Architecture And Features Secure Computing Framework Clipart Pdf
This slide depicts the features and architecture of the occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, occlum CLI tool, deployment environment, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Occlum System Architecture And Features Secure Computing Framework Clipart Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Occlum System Architecture And Features Secure Computing Framework Clipart Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide depicts the features and architecture of the occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, occlum CLI tool, deployment environment, and so on.
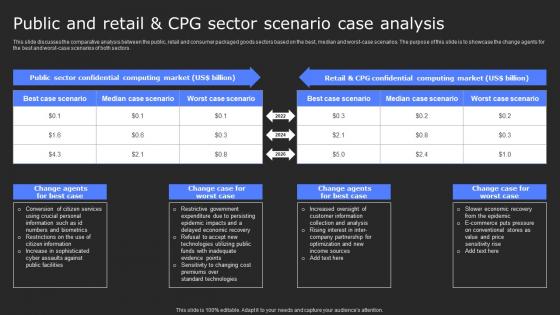
Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.
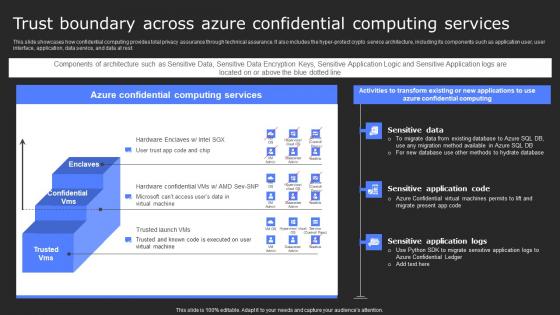
Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
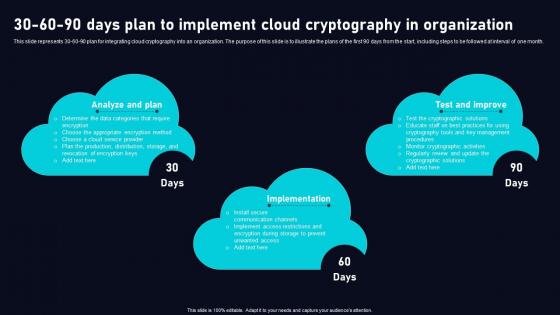
30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf
This slide represents 30 60 90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give 30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable 30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents 30 60 90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.
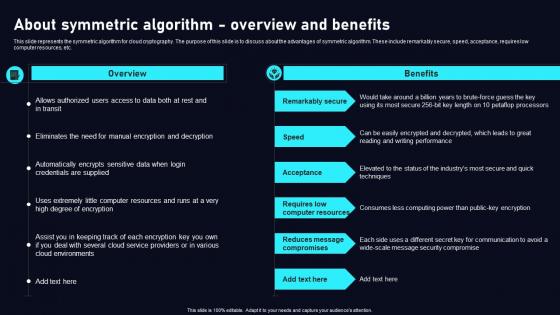
About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc.
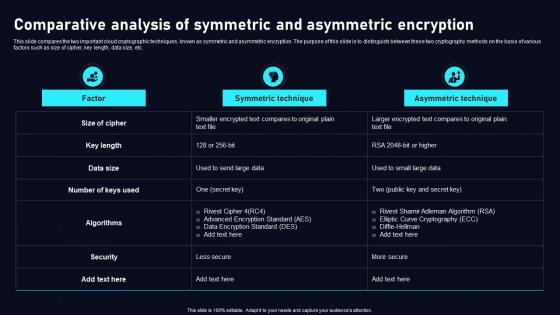
Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Explore a selection of the finest Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.
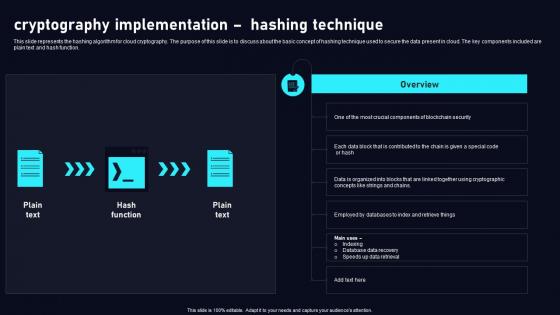
Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf
This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function. Are you searching for a Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf from Slidegeeks today. This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function.
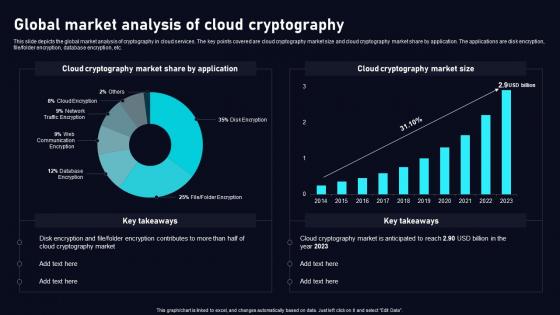
Global Market Analysis Of Cloud Data Security Using Cryptography Portrait Pdf
This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file folder encryption, database encryption, etc. Do you know about Slidesgeeks Global Market Analysis Of Cloud Data Security Using Cryptography Portrait Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file folder encryption, database encryption, etc.

Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf
The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management.
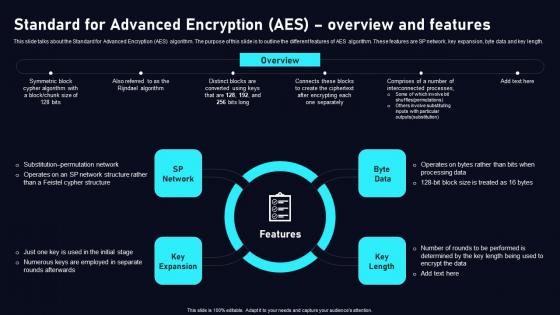
Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length.
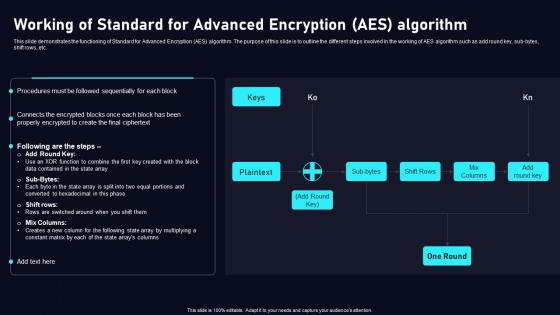
Working Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc. Create an editableWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save timeWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc.
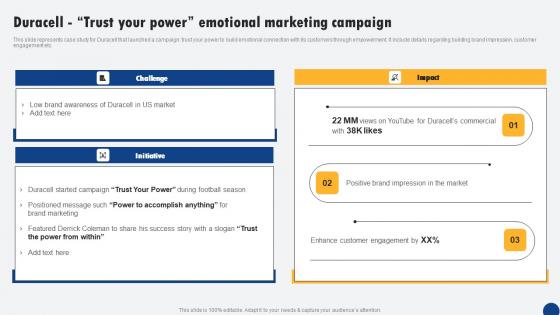
Duracell Trust Your Power Emotional Marketing Driven Digital Marketing Professional Pdf
This slide represents case study for Duracell that launched a campaign trust your power to build emotional connection with its customers through empowerment. It include details regarding building brand impression, customer engagement etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Duracell Trust Your Power Emotional Marketing Driven Digital Marketing Professional Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Duracell Trust Your Power Emotional Marketing Driven Digital Marketing Professional Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents case study for Duracell that launched a campaign trust your power to build emotional connection with its customers through empowerment. It include details regarding building brand impression, customer engagement etc.

Investment Ask Carelulu Shareholders Fund Raising Pitch Deck Download Pdf
This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance. It will utilize its finance in expanding its user base. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Investment Ask Carelulu Shareholders Fund Raising Pitch Deck Download Pdf can be your best option for delivering a presentation. Represent everything in detail using Investment Ask Carelulu Shareholders Fund Raising Pitch Deck Download Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance. It will utilize its finance in expanding its user base.
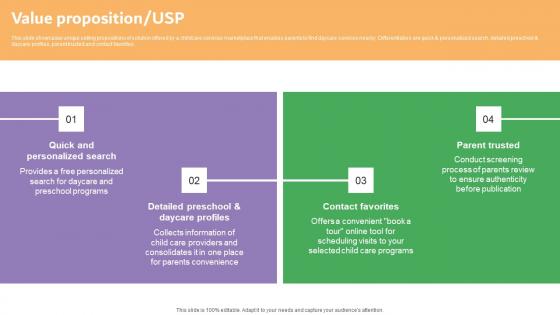
Value Proposition Usp Carelulu Shareholders Fund Raising Pitch Deck Professional Pdf
This slide showcases unique selling propositions of solution offered by a childcare services marketplace that enables parents to find daycare services nearby. Differentiators are quick and personalized search, detailed preschool and daycare profiles, parent trusted and contact favorites. Welcome to our selection of the Value Proposition Usp Carelulu Shareholders Fund Raising Pitch Deck Professional Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today This slide showcases unique selling propositions of solution offered by a childcare services marketplace that enables parents to find daycare services nearby. Differentiators are quick and personalized search, detailed preschool and daycare profiles, parent trusted and contact favorites.

Rapid Application Development Vs Waterfall Comparing RAD And Other Software Information Pdf
This slide represents the comparison between rapid application development, waterfall, and agile. The purpose of this slide is to highlight the critical difference between RAD, waterfall, and agile based on the timeframe, project size, developer team size, risks, and costs. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Rapid Application Development Vs Waterfall Comparing RAD And Other Software Information Pdf can be your best option for delivering a presentation. Represent everything in detail using Rapid Application Development Vs Waterfall Comparing RAD And Other Software Information Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the comparison between rapid application development, waterfall, and agile. The purpose of this slide is to highlight the critical difference between RAD, waterfall, and agile based on the timeframe, project size, developer team size, risks, and costs.
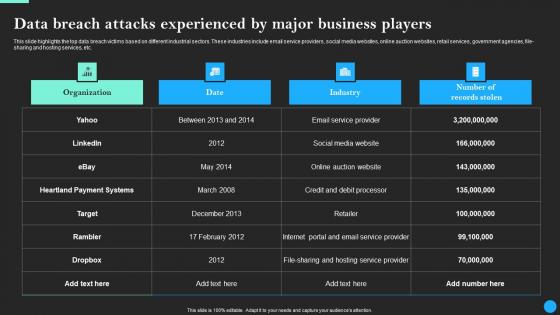
Data Breach Attacks Experienced By Major Business Data Breach Prevention Diagrams Pdf
This slide highlights the top data breach victims based on different industrial sectors. These industries include email service providers, social media websites, online auction websites, retail services, government agencies, file-sharing and hosting services, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Data Breach Attacks Experienced By Major Business Data Breach Prevention Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Data Breach Attacks Experienced By Major Business Data Breach Prevention Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the top data breach victims based on different industrial sectors. These industries include email service providers, social media websites, online auction websites, retail services, government agencies, file-sharing and hosting services, etc.

Data Breach Response Plan Secure Operations Data Breach Prevention Themes Pdf
This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. Welcome to our selection of the Data Breach Response Plan Secure Operations Data Breach Prevention Themes Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc.
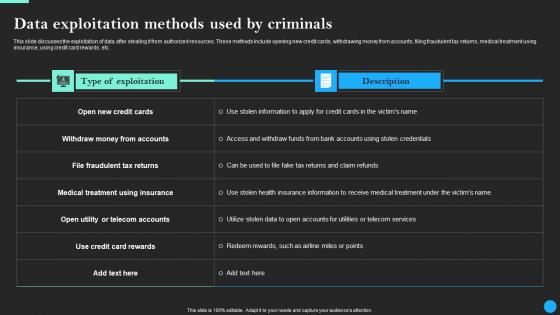
Data Exploitation Methods Used By Criminals Data Breach Prevention Portrait Pdf
This slide discusses the exploitation of data after stealing it from authorized resources. These methods include opening new credit cards, withdrawing money from accounts, filing fraudulent tax returns, medical treatment using insurance, using credit card rewards, etc. Explore a selection of the finest Data Exploitation Methods Used By Criminals Data Breach Prevention Portrait Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Data Exploitation Methods Used By Criminals Data Breach Prevention Portrait Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide discusses the exploitation of data after stealing it from authorized resources. These methods include opening new credit cards, withdrawing money from accounts, filing fraudulent tax returns, medical treatment using insurance, using credit card rewards, etc.
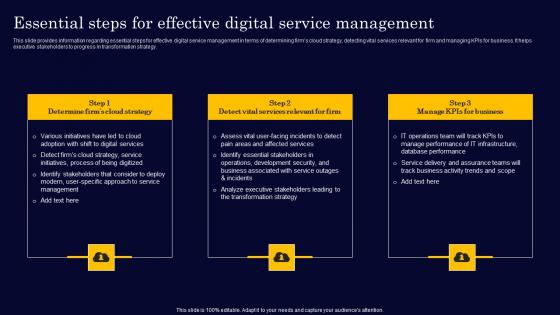
Essential Steps For Effective Digital Service Gen Tech Stack Playbook Microsoft Pdf
This slide provides information regarding essential steps for effective digital service management in terms of determining firms cloud strategy, detecting vital services relevant for firm and managing KPIs for business. It helps executive stakeholders to progress in transformation strategy. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Essential Steps For Effective Digital Service Gen Tech Stack Playbook Microsoft Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Essential Steps For Effective Digital Service Gen Tech Stack Playbook Microsoft Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provides information regarding essential steps for effective digital service management in terms of determining firms cloud strategy, detecting vital services relevant for firm and managing KPIs for business. It helps executive stakeholders to progress in transformation strategy.
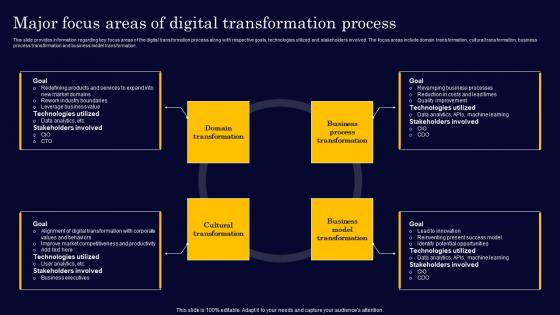
Major Focus Areas Of Digital Transformation Process Gen Tech Stack Playbook Summary Pdf
This slide provides information regarding key focus areas of the digital transformation process along with respective goals, technologies utilized and stakeholders involved. The focus areas include domain transformation, cultural transformation, business process transformation and business model transformation. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Major Focus Areas Of Digital Transformation Process Gen Tech Stack Playbook Summary Pdf can be your best option for delivering a presentation. Represent everything in detail using Major Focus Areas Of Digital Transformation Process Gen Tech Stack Playbook Summary Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide provides information regarding key focus areas of the digital transformation process along with respective goals, technologies utilized and stakeholders involved. The focus areas include domain transformation, cultural transformation, business process transformation and business model transformation.
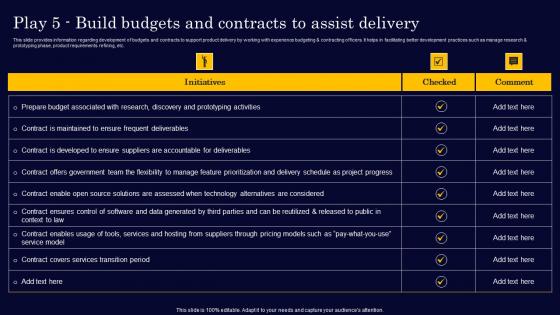
Play 5 Build Budgets And Contracts To Assist Delivery Gen Tech Stack Playbook Demonstration Pdf
This slide provides information regarding development of budgets and contracts to support product delivery by working with experience budgeting and contracting officers. It helps in facilitating better development practices such as manage research and prototyping phase, product requirements refining, etc. Welcome to our selection of the Play 5 Build Budgets And Contracts To Assist Delivery Gen Tech Stack Playbook Demonstration Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today This slide provides information regarding development of budgets and contracts to support product delivery by working with experience budgeting and contracting officers. It helps in facilitating better development practices such as manage research and prototyping phase, product requirements refining, etc.
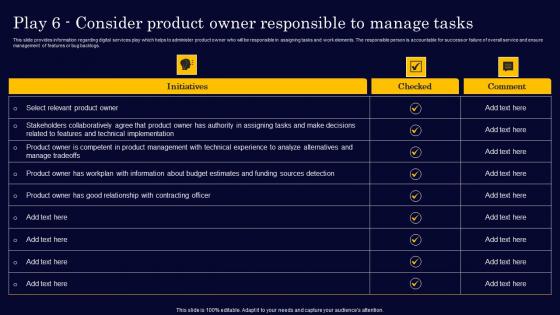
Play 6 Consider Product Owner Responsible To Manage Gen Tech Stack Playbook Slides Pdf
This slide provides information regarding digital services play which helps to administer product owner who will be responsible in assigning tasks and work elements. The responsible person is accountable for success or failure of overall service and ensure management of features or bug backlogs. Explore a selection of the finest Play 6 Consider Product Owner Responsible To Manage Gen Tech Stack Playbook Slides Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Play 6 Consider Product Owner Responsible To Manage Gen Tech Stack Playbook Slides Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide provides information regarding digital services play which helps to administer product owner who will be responsible in assigning tasks and work elements. The responsible person is accountable for success or failure of overall service and ensure management of features or bug backlogs.
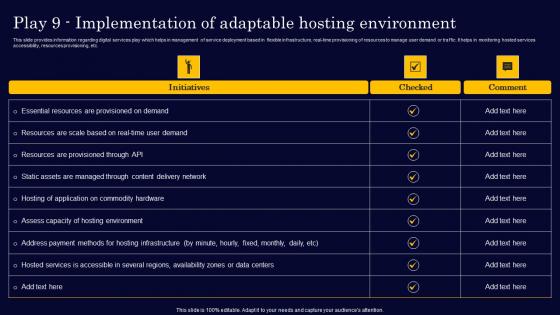
Play 9 Implementation Of Adaptable Hosting Gen Tech Stack Playbook Sample Pdf
This slide provides information regarding digital services play which helps in management of service deployment based in flexible infrastructure, real-time provisioning of resources to manage user demand or traffic. It helps in monitoring hosted services accessibility, resources provisioning, etc. Are you searching for a Play 9 Implementation Of Adaptable Hosting Gen Tech Stack Playbook Sample Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Play 9 Implementation Of Adaptable Hosting Gen Tech Stack Playbook Sample Pdf from Slidegeeks today. This slide provides information regarding digital services play which helps in management of service deployment based in flexible infrastructure, real-time provisioning of resources to manage user demand or traffic. It helps in monitoring hosted services accessibility, resources provisioning, etc.
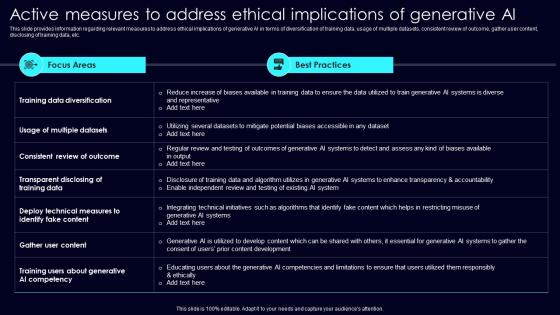
Active Measures To Address Exploring Rise Of Generative AI In Artificial Intelligence Inspiration Pdf
This slide provides information regarding relevant measures to address ethical implications of generative AI in terms of diversification of training data, usage of multiple datasets, consistent review of outcome, gather user content, disclosing of training data, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Active Measures To Address Exploring Rise Of Generative AI In Artificial Intelligence Inspiration Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Active Measures To Address Exploring Rise Of Generative AI In Artificial Intelligence Inspiration Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provides information regarding relevant measures to address ethical implications of generative AI in terms of diversification of training data, usage of multiple datasets, consistent review of outcome, gather user content, disclosing of training data, etc.
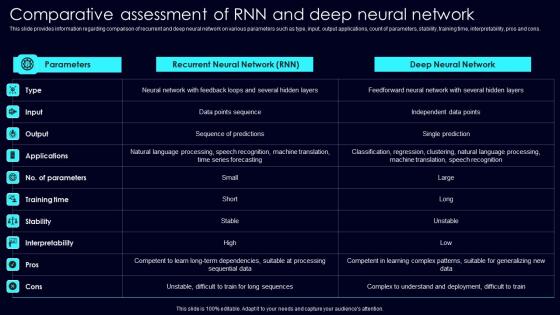
Comparative Assessment Exploring Rise Of Generative AI In Artificial Intelligence Topics Pdf
This slide provides information regarding comparison of recurrent and deep neural network on various parameters such as type, input, output applications, count of parameters, stability, training time, interpretability, pros and cons. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Comparative Assessment Exploring Rise Of Generative AI In Artificial Intelligence Topics Pdf can be your best option for delivering a presentation. Represent everything in detail using Comparative Assessment Exploring Rise Of Generative AI In Artificial Intelligence Topics Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide provides information regarding comparison of recurrent and deep neural network on various parameters such as type, input, output applications, count of parameters, stability, training time, interpretability, pros and cons.

Generative Adversarial Networks Exploring Rise Of Generative AI In Artificial Intelligence Download Pdf
This slide provides information regarding generative adversarial networks GANs that are type of generative models to create new data samples that replicates assigned dataset by learning data distribution. It also highlights it key components, pros and cons. Welcome to our selection of the Generative Adversarial Networks Exploring Rise Of Generative AI In Artificial Intelligence Download Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today This slide provides information regarding generative adversarial networks GANs that are type of generative models to create new data samples that replicates assigned dataset by learning data distribution. It also highlights it key components, pros and cons.

Generative AI Architecture Deployment Exploring Rise Of Generative AI In Artificial Intelligence Rules Pdf
This slide provides information regarding the deployment and integration layers associated with generative AI architecture. This layer comprises of several elements. It also highlights about the key steps associated with the layer. Explore a selection of the finest Generative AI Architecture Deployment Exploring Rise Of Generative AI In Artificial Intelligence Rules Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Generative AI Architecture Deployment Exploring Rise Of Generative AI In Artificial Intelligence Rules Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide provides information regarding the deployment and integration layers associated with generative AI architecture. This layer comprises of several elements. It also highlights about the key steps associated with the layer.

Major Components Of ChatGpt Exploring Rise Of Generative AI In Artificial Intelligence Inspiration Pdf
This slide provides information regarding key elements of ChatGPT architecture which is based on a neural network, including input layer, embedding layer and transformer blocks. Each transformer block caters multi head attention mechanism and feed forward neural network. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Major Components Of ChatGpt Exploring Rise Of Generative AI In Artificial Intelligence Inspiration Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Major Components Of ChatGpt Exploring Rise Of Generative AI In Artificial Intelligence Inspiration Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provides information regarding key elements of ChatGPT architecture which is based on a neural network, including input layer, embedding layer and transformer blocks. Each transformer block caters multi head attention mechanism and feed forward neural network.


 Continue with Email
Continue with Email

 Home
Home


































