Email Strategy
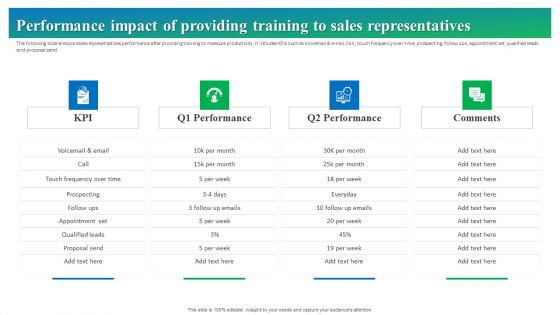
Process Enhancement Plan To Boost Sales Performance Performance Impact Of Providing Training To Sales Representatives Ideas PDF
The following slide analyze sales representatives performance after providing training to measure productivity. It includes KPIs such as Voicemail and email, Call , touch frequency over time, prospecting, follow ups, appointment set, qualified leads and proposal send. Want to ace your presentation in front of a live audience Our Process Enhancement Plan To Boost Sales Performance Performance Impact Of Providing Training To Sales Representatives Ideas PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Training Plan For Managed Cyber Security Solutions Service Ppt Summary Guide PDF
The following slide outlines a comprehensive training plan for managed security service and awareness for employees. It provides information about the training subject, trainer name, training hours, status and learning outcome. Pitch your topic with ease and precision using this Training Plan For Managed Cyber Security Solutions Service Ppt Summary Guide PDF. This layout presents information on Training Plan, Managed Cyber Security, Solutions Service. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
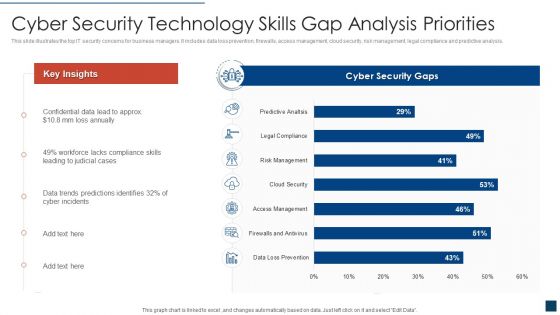
Cyber Security Technology Skills Gap Analysis Priorities Clipart PDF
This slide illustrates the top IT security concerns for business managers. It includes data loss prevention, firewalls, access management, cloud security, risk management, legal compliance and predictive analysis. Showcasing this set of slides titled cyber security technology skills gap analysis priorities clipart pdf. The topics addressed in these templates are cyber security technology skills gap analysis priorities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
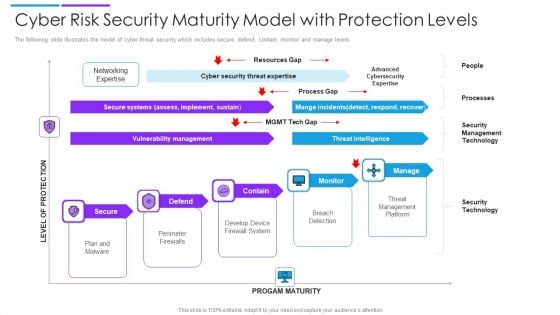
Cyber Risk Security Maturity Model With Protection Levels Mockup PDF
The following slide illustrates the model of cyber threat security which includes secure, defend, contain, monitor and manage levels. Persuade your audience using this cyber risk security maturity model with protection levels mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including secure systems, vulnerability management, threat intelligence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
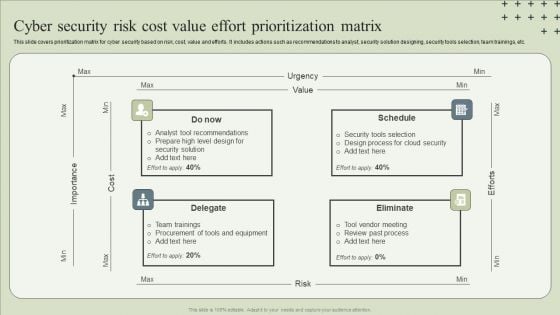
Cyber Security Risk Cost Value Effort Prioritization Matrix Guidelines PDF
This slide covers prioritization matrix for cyber security based on risk, cost, value and efforts. It includes actions such as recommendations to analyst, security solution designing, security tools selection, team trainings, etc.Presenting Cyber Security Risk Cost Value Effort Prioritization Matrix Guidelines PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Tool Recommendations, Design Process, Team Trainings. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
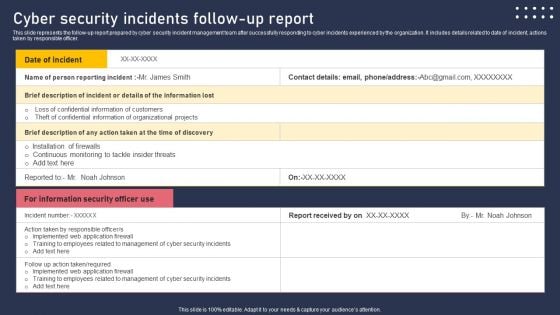
Cyber Security Incidents Follow Up Report Summary PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. Take your projects to the next level with our ultimate collection of Cyber Security Incidents Follow Up Report Summary PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
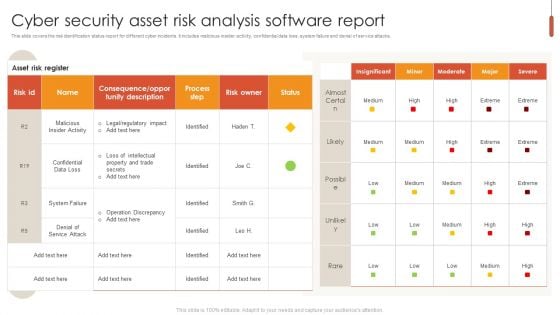
Cyber Security Asset Risk Analysis Software Report Pictures PDF
This slide covers the risk identification status report for different cyber incidents. It includes malicious insider activity, confidential data loss, system failure and denial of service attacks. Pitch your topic with ease and precision using this Cyber Security Asset Risk Analysis Software Report Pictures PDF. This layout presents information on Cyber Security Asset Risk, Analysis Software Report. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
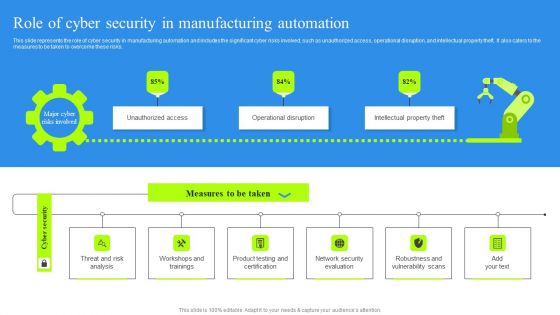
Role Of Cyber Security In Manufacturing Automation Portrait PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Find highly impressive Role Of Cyber Security In Manufacturing Automation Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Cyber Security In Manufacturing Automation Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
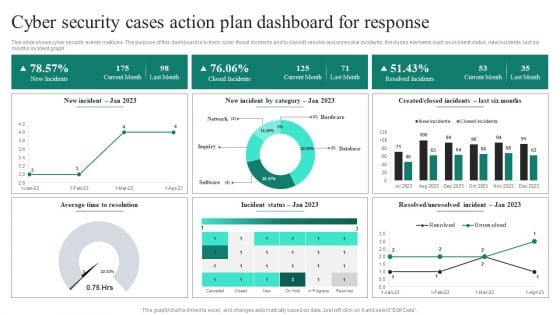
Cyber Security Cases Action Plan Dashboard For Response Ppt PowerPoint Presentation File Deck PDF
This slide shows cyber security events matrices. The purpose of this dashboard is to track cyber threat incidents and to classify resolve and unresolve incidents. It includes elements such as incident status, new incidents, last six months incident graph. Showcasing this set of slides titled Cyber Security Cases Action Plan Dashboard For Response Ppt PowerPoint Presentation File Deck PDF. The topics addressed in these templates are Current Month, Closed Incidents, Last Month, Resolved Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
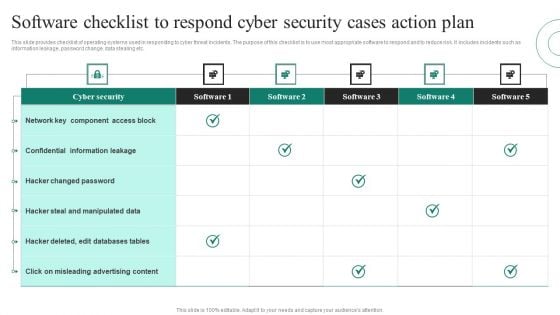
Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF
This slide provides checklist of operating systems used in responding to cyber threat incidents. The purpose of this checklist is to use most appropriate software to respond and to reduce risk. It includes incidents such as information leakage, password change, data stealing etc. Pitch your topic with ease and precision using this Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF. This layout presents information on Cyber Security, Confidential Information Leakage, Hacker Changed Password. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Project Evaluation Plan To Safeguard Business Operation Designs PDF
This slide signifies the cyber security project evaluation plan for safeguarding organisation operations. It covers information regarding to the stages like initiation, planning, execution, implement and monitor. Persuade your audience using this Cyber Security Project Evaluation Plan To Safeguard Business Operation Designs PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Planning, Execution, Implement, Initiation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Operating Designs PDF
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard operating designs pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
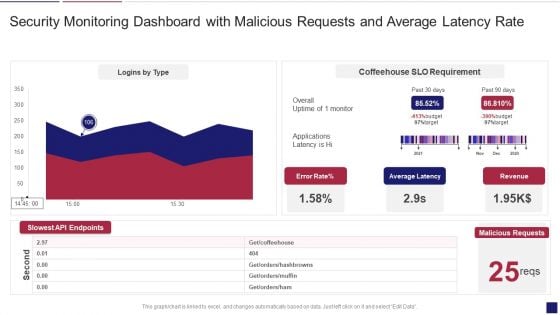
Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Rate Summary PDF
Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks security monitoring dashboard rate summary pdf. Use them to share invaluable insights on security monitoring dashboard with malicious requests and average latency rate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

cyber security administration in organization threat management action plan introduction pdf
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber security administration in organization threat management action plan introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like responsibilities, manager, assessment, manager . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
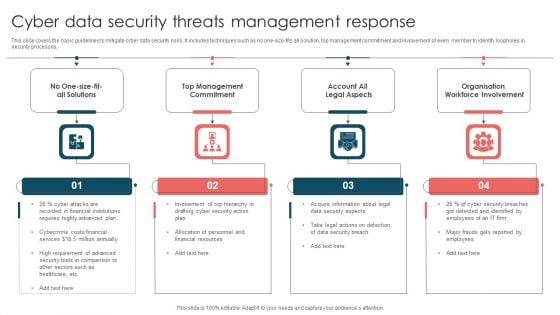
Cyber Data Security Threats Management Response Ppt Summary Skills PDF
This slide covers the basic guidelines to mitigate cyber data security risks. It includes techniques such as no one-size-fits all solution, top management commitment and involvement of every member to identify loopholes in security processes. Presenting Cyber Data Security Threats Management Response Ppt Summary Skills PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Organisation Workforce Involvement, Account Legal Aspects, Top Management Commitment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
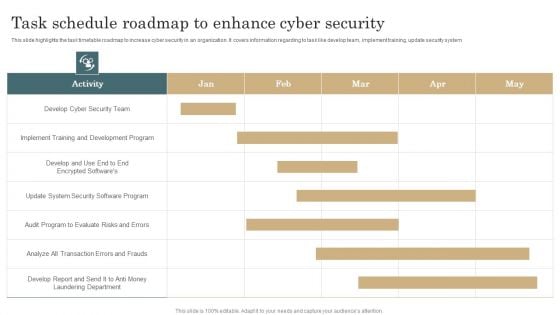
Task Schedule Roadmap To Enhance Cyber Security Template PDF
This slide highlights the task timetable roadmap to increase cyber security in an organization. It covers information regarding to task like develop team, implement training, update security system. Pitch your topic with ease and precision using this Task Schedule Roadmap To Enhance Cyber Security Template PDF. This layout presents information on Development Program, Implement Training, Evaluate Risks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
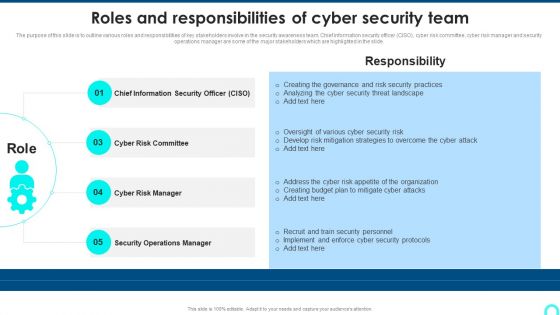
Roles And Responsibilities Of Cyber Security Team Designs PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide.This is a Roles And Responsibilities Of Cyber Security Team Designs PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Chief Information, Operations Manager, Risk Manager . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
5 Year Action Plan And Advantage Roadmap For Cyber Security Icons
We present our 5 year action plan and advantage roadmap for cyber security icons. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 5 year action plan and advantage roadmap for cyber security icons in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

IT System Risk Management Guide Prioritized Cyber Security Threats With Risk Mitigation Plan Ideas PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Welcome to our selection of the IT System Risk Management Guide Prioritized Cyber Security Threats With Risk Mitigation Plan Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
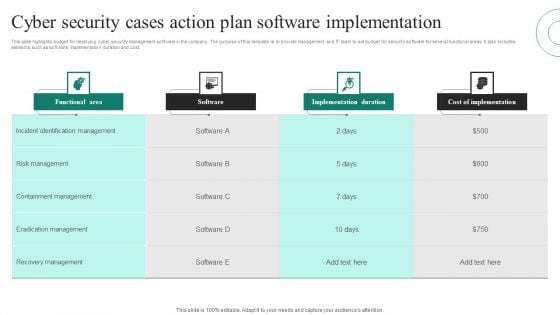
Cyber Security Cases Action Plan Software Implementation Ppt PowerPoint Presentation File Grid PDF
This slide highlights budget for deploying cyber security management software in the company. The purpose of this template is to provide management and IT team to set budget for security software for several functional areas. It also includes elements such as software, implementation duration and cost. Pitch your topic with ease and precision using this Cyber Security Cases Action Plan Software Implementation Ppt PowerPoint Presentation File Grid PDF. This layout presents information on Functional Area, Software, Implementation Duration, Cost Implementation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF
This slide outlines the business plan for managed security service which includes services such as antivirus, anti-malware, anti-spam etc. it also provides information about the total cost of services, status of purchase, security goal, etc. Pitch your topic with ease and precision using this Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF. This layout presents information on Revenue, Security Goal, IT Security Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
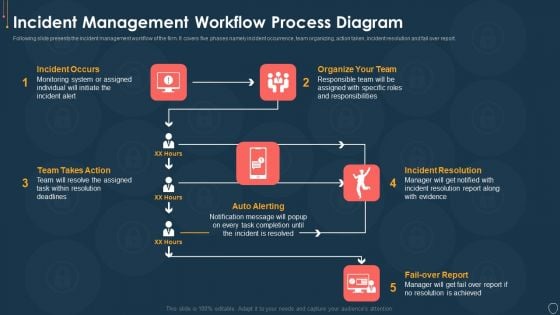
Cyber Security Risk Management Plan Incident Management Workflow Process Diagram Infographics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting cyber security risk management plan incident management workflow process diagram infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like fail over report, incident resolution, organize your team, incident occurs, team takes action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
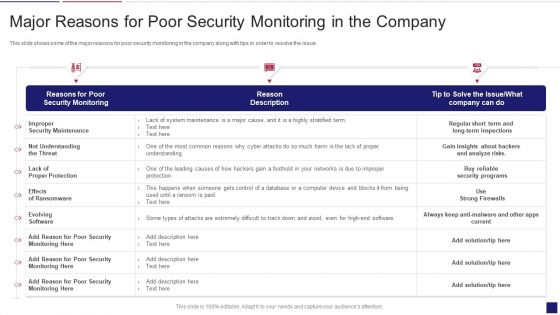
Continuous Development Evaluation Plan Eliminate Cyber Attacks Major Reasons For Poor Security Topics PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks major reasons for poor security topics pdf bundle. Topics like improper security maintenance, evolving software, effects of ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Implementation Framework 30 60 90 Days Plan Ppt PowerPoint Presentation Summary Background Image PDF
Presenting this set of slides with name cyber security implementation framework 30 60 90 days plan ppt powerpoint presentation summary background image pdf. This is a three stage process. The stages in this process are 30 60 90 days plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
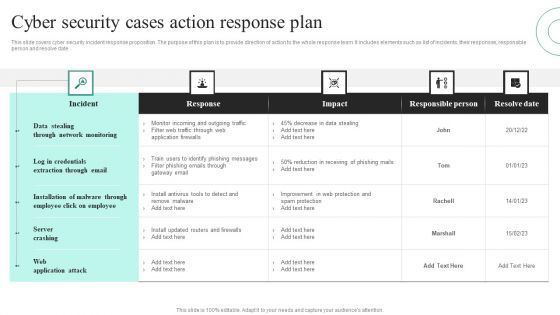
Cyber Security Cases Action Response Plan Ppt PowerPoint Presentation File Visuals PDF
This slide covers cyber security incident response proposition. The purpose of this plan is to provide direction of action to the whole response team. It includes elements such as list of incidents, their responses, responsible person and resolve date. Showcasing this set of slides titled Cyber Security Cases Action Response Plan Ppt PowerPoint Presentation File Visuals PDF. The topics addressed in these templates are Data Stealing Through, Network Monitoring, Server Crashing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
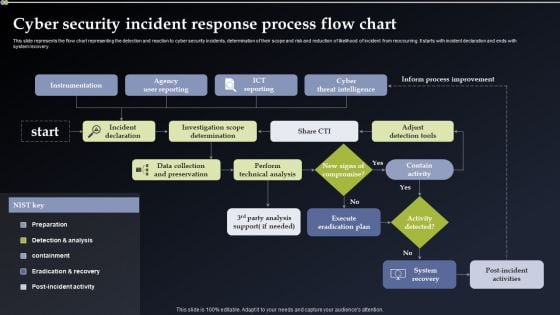
Cyber Security Incident Response Process Flow Chart Information PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Process Flow Chart Information PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Process Flow Chart Information PDF.
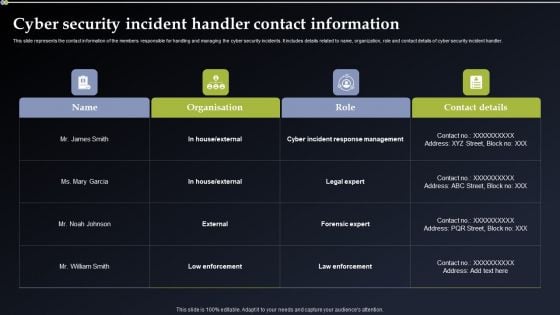
Cyber Security Incident Handler Contact Information Summary PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. This Cyber Security Incident Handler Contact Information Summary PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
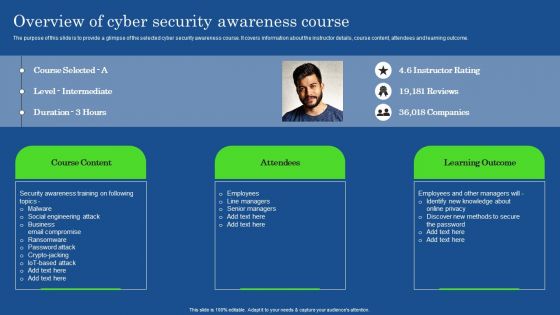
Overview Of Cyber Security Awareness Course Brochure PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Of Cyber Security Awareness Course Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Of Cyber Security Awareness Course Brochure PDF.
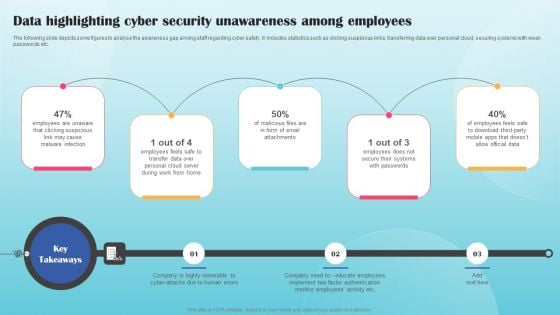
Data Highlighting Cyber Security Unawareness Among Employees Summary PDF
The following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Create an editable Data Highlighting Cyber Security Unawareness Among Employees Summary PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Data Highlighting Cyber Security Unawareness Among Employees Summary PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
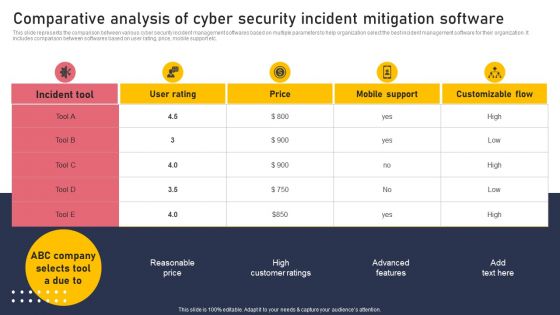
Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Cyber Security Event And Incident Flow Diagram Icons PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Event And Incident Flow Diagram Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
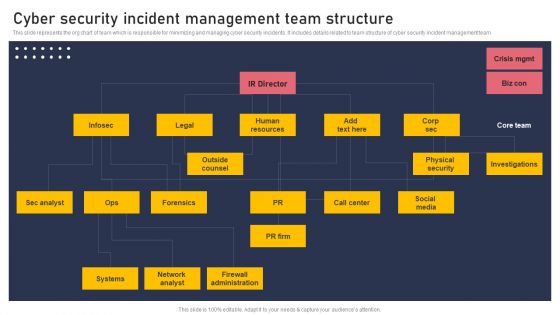
Cyber Security Incident Management Team Structure Pictures PDF
This slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team Retrieve professionally designed Cyber Security Incident Management Team Structure Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
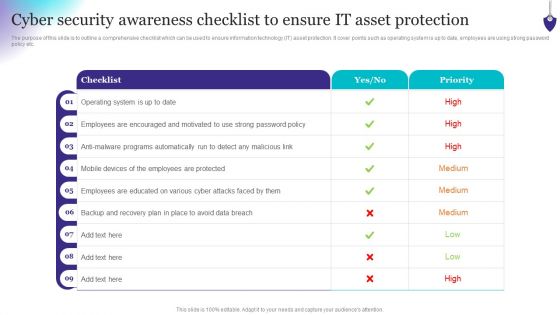
Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
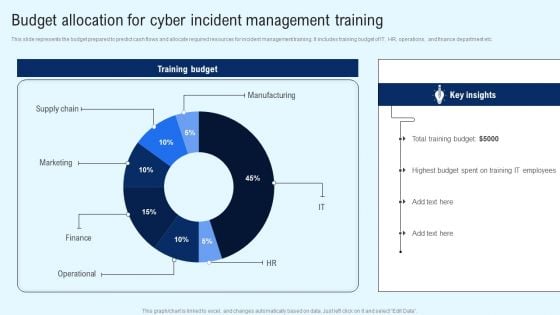
Implementing Cyber Security Incident Budget Allocation For Cyber Incident Portrait PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Find a pre designed and impeccable Implementing Cyber Security Incident Budget Allocation For Cyber Incident Portrait PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
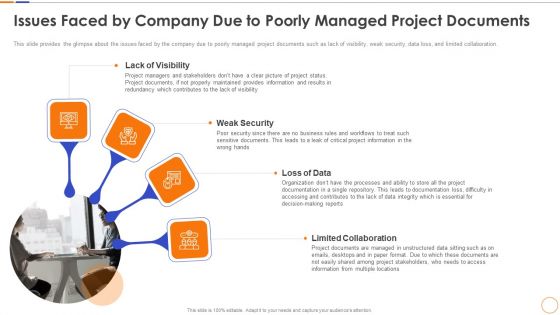
Issues Faced By Company Due To Poorly Managed Project Documents Themes PDF
This slide provides the glimpse about the issues faced by the company due to poorly managed project documents such as lack of visibility, weak security, data loss, and limited collaboration. This is a issues faced by company due to poorly managed project documents themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project information, documents, security, organization, emails. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
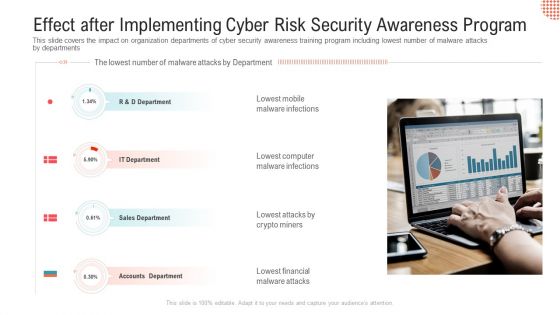
Effect After Implementing Cyber Risk Security Awareness Program Professional PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments.This is a effect after implementing cyber risk security awareness program professional pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like lowest mobile malware infections, lowest computer malware infections. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
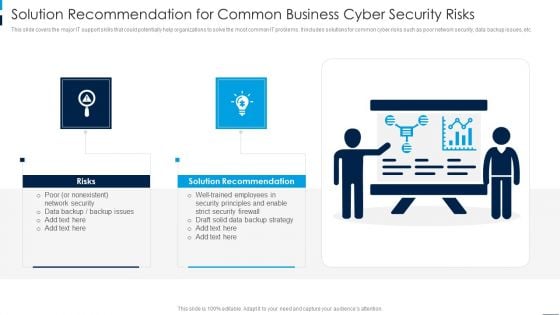
Solution Recommendation For Common Business Cyber Security Risks Rules PDF
This slide covers the major IT support skills that could potentially help organizations to solve the most common IT problems. It includes solutions for common cyber risks such as poor network security, data backup issues, etc. Persuade your audience using this Solution Recommendation For Common Business Cyber Security Risks Rules PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Solution Recommendation, Risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
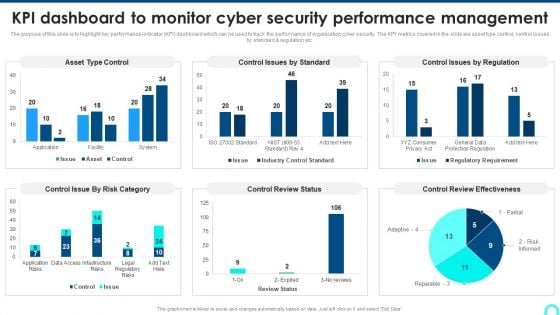
KPI Dashboard To Monitor Cyber Security Performance Management Background PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc.Deliver and pitch your topic in the best possible manner with this KPI Dashboard To Monitor Cyber Security Performance Management Background PDF. Use them to share invaluable insights on Control Issue, Control Review, Review Effectiveness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
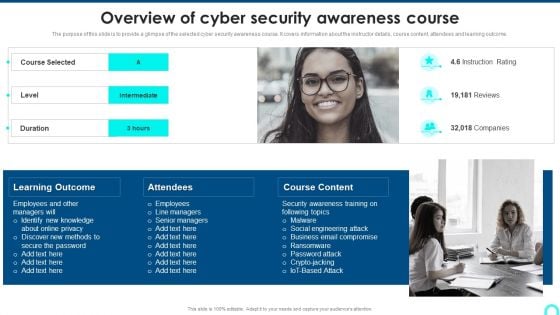
Overview Of Cyber Security Awareness Course Clipart PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This is a Overview Of Cyber Security Awareness Course Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Learning Outcome, Attendees, Course Content. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
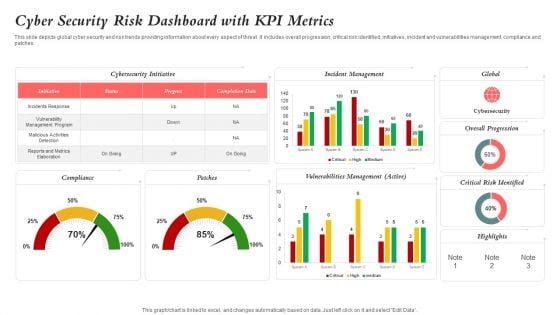
Cyber Security Risk Dashboard With KPI Metrics Elements PDF
This slide depicts global cyber security and risk trends providing information about every aspect of threat. It includes overall progression, critical risk identified, initiatives, incident and vulnerabilities management, compliance and patches. Showcasing this set of slides titled Cyber Security Risk Dashboard With KPI Metrics Elements PDF. The topics addressed in these templates are Vulnerability Management Program, Reports And Metrics Elaboration, Critical Risk Identified. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Five Steps For Cyber IT Security Risk Analysis Graphics PDF
This slide covers the steps for analysis of risk occurring in cyber security to reduce errors and system hacks so that the information of clients remain safe. It includes finding assets, identifying consequences, threats and assessing risk. Presenting Five Steps For Cyber IT Security Risk Analysis Graphics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Find Valuable Assets, Assess Risk, Identify Potential Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
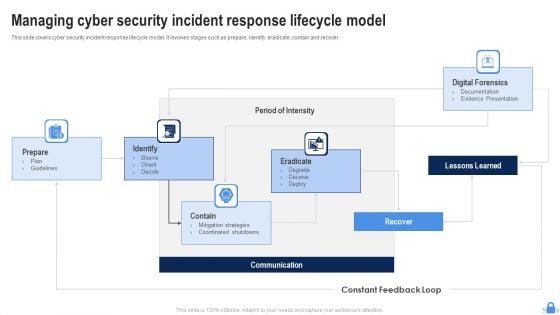
Managing Cyber Security Incident Response Lifecycle Model Ppt Graphics PDF
This slide covers cyber security incident response lifecycle model. It involves stages such as prepare, identify, eradicate, contain and recover. Persuade your audience using this Managing Cyber Security Incident Response Lifecycle Model Ppt Graphics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare, Identify, Contain, Communication, Eradicate, Lessons Learned. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
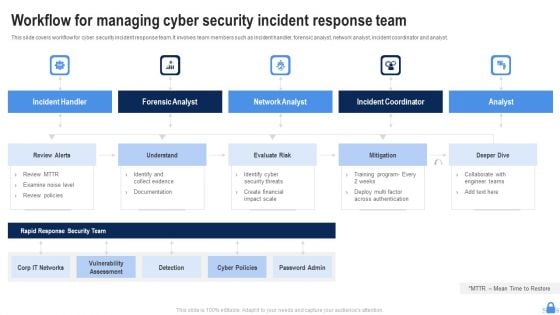
Workflow For Managing Cyber Security Incident Response Team Brochure PDF
This slide covers workflow for cyber security incident response team. It involves team members such as incident handler, forensic analyst, network analyst, incident coordinator and analyst. Presenting Workflow For Managing Cyber Security Incident Response Team Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Incident Handler, Forensic Analyst, Network Analyst, Incident Coordinator. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
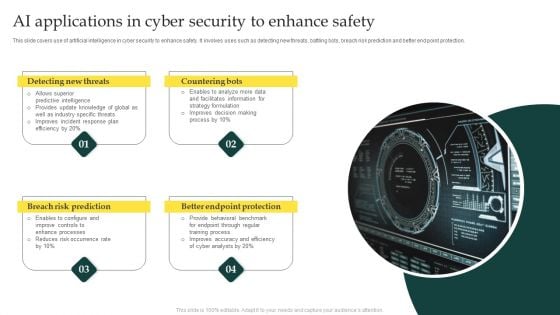
AI Applications In Cyber Security To Enhance Safety Elements PDF
This slide covers use of artificial intelligence in cyber security to enhance safety. It involves uses such as detecting new threats, battling bots, breach risk prediction and better end point protection.Persuade your audience using this AI Applications In Cyber Security To Enhance Safety Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Prediction, Endpoint Protection, Countering Bots. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
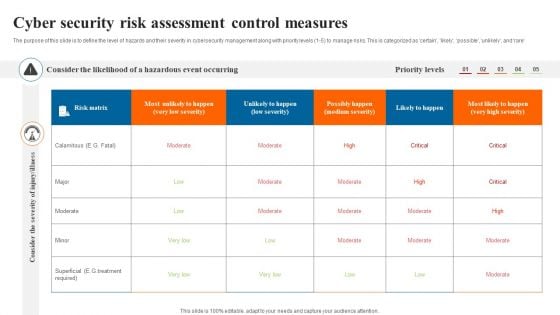
Cyber Security Risk Assessment Control Measures Slides PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management along with priority levels 1 to 5 to manage risks. This is categorized as certain likely possible unlikely and rare. Showcasing this set of slides titled Cyber Security Risk Assessment Control Measures Slides PDF. The topics addressed in these templates are Cyber Security Risk, Assessment Control Measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Standards Compliance Traceability Matrix Information PDF
This slide represents the cyber security standards compliance matrix. The purpose of this slide is to demonstrate the various cybersecurity standards and their compliance requirements for businesses. The primary standards include ISO27001, PCI DSS, HIPPA, FINRA and GDPR. Showcasing this set of slides titled Cyber Security Standards Compliance Traceability Matrix Information PDF. The topics addressed in these templates are Standards, Requirements, Risk Level. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
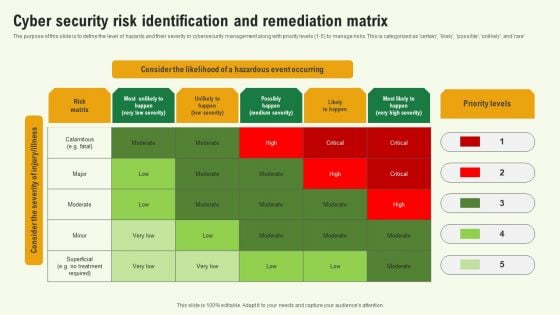
Cyber Security Risk Identification And Remediation Matrix Background PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management along with priority levels 1 to 5 to manage risks. This is categorized as certain, likely, possible, unlikel, and rare. Showcasing this set of slides titled Cyber Security Risk Identification And Remediation Matrix Background PDF. The topics addressed in these templates are Cyber Security Risk Identification, Remediation Matrix. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
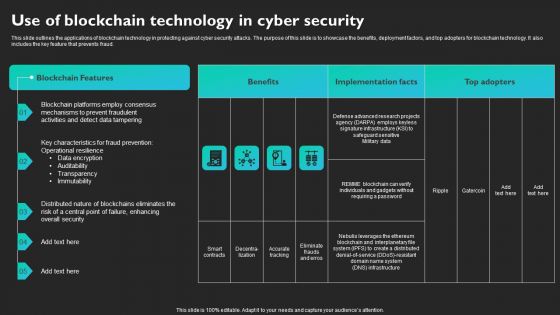
Use Of Blockchain Technology In Cyber Security Slides PDF
This slide outlines the applications of blockchain technology in protecting against cyber security attacks. The purpose of this slide is to showcase the benefits, deployment factors, and top adopters for blockchain technology. It also includes the key feature that prevents fraud. Find a pre-designed and impeccable Use Of Blockchain Technology In Cyber Security Slides PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
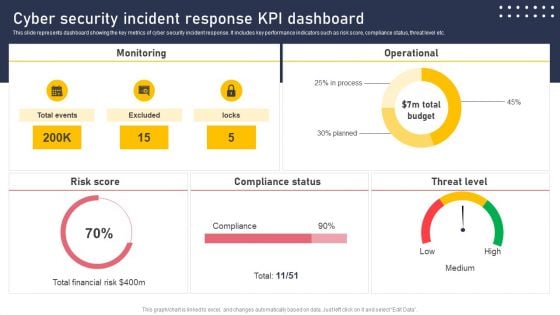
Cyber Security Incident Response KPI Dashboard Microsoft PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Slidegeeks has constructed Cyber Security Incident Response KPI Dashboard Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
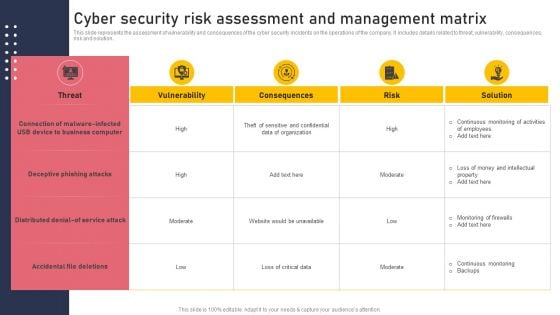
Cyber Security Risk Assessment And Management Matrix Inspiration PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Find a pre designed and impeccable Cyber Security Risk Assessment And Management Matrix Inspiration PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
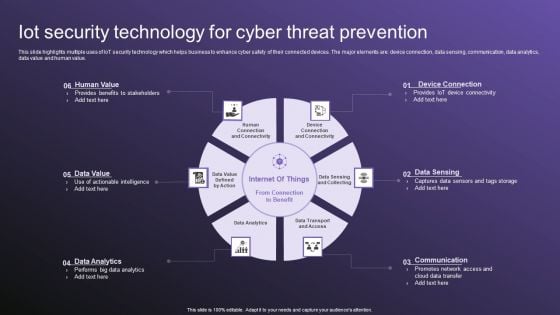
Iot Security Technology For Cyber Threat Prevention Clipart PDF
This slide highlights multiple uses of IoT security technology which helps business to enhance cyber safety of their connected devices. The major elements are device connection, data sensing, communication, data analytics, data value and human value. Persuade your audience using this Iot Security Technology For Cyber Threat Prevention Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Human Value, Data Value, Data Analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Qualitative Risk Analysis Matrix Background PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management. This is categorized as certain, likely, possible, unlikely, and rare. Pitch your topic with ease and precision using this Cyber Security Qualitative Risk Analysis Matrix Background PDF. This layout presents information on Risk Matrix, High Severity, Cyber Security Qualitative. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Corporate Communications Consulting Methods That Are Considered For Creating Stakeholders Group Clipart PDF
This template covers the stakeholders groups and consulting methods. Stakeholders groups are government officials , neighboring communities, vulnerable groups, employees and managers, NGOs and conservations organizations etc. Consulting methods are phone, emails, text messaging, one on one interviews, radio announcements etc. If you are looking for a format to display your unique thoughts, then the professionally designed Corporate Communications Consulting Methods That Are Considered For Creating Stakeholders Group Clipart PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Corporate Communications Consulting Methods That Are Considered For Creating Stakeholders Group Clipart PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
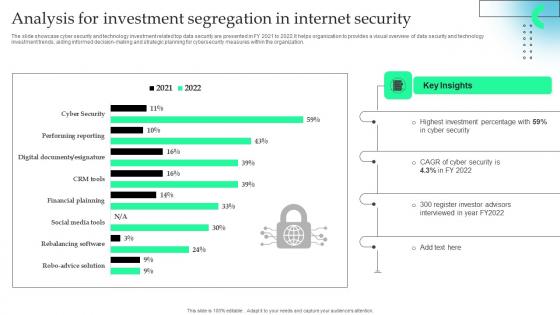
Analysis For Investment Segregation In Internet Security Formats Pdf
The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.Pitch your topic with ease and precision using this Analysis For Investment Segregation In Internet Security Formats Pdf This layout presents information on Highest Investment, Register Investor Advisors, Key Insights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.
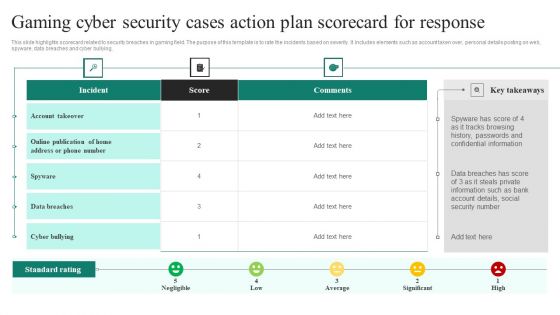
Gaming Cyber Security Cases Action Plan Scorecard For Response Ppt PowerPoint Presentation File Styles PDF
This slide highlights scorecard related to security breaches in gaming field. The purpose of this template is to rate the incidents based on severity. It includes elements such as account taken over, personal details posting on web, spyware, data breaches and cyber bullying. Showcasing this set of slides titled Gaming Cyber Security Cases Action Plan Scorecard For Response Ppt PowerPoint Presentation File Styles PDF. The topics addressed in these templates are Incident, Score, Data Breaches, Low, High. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security For Your Organization Backup Maintenance Recovery Budget Planning Ppt Inspiration Slide Portrait PDF
Presenting this set of slides with name cyber security for your organization backup maintenance recovery budget planning ppt inspiration slide portrait pdf. The topics discussed in these slides are vendor costs, hardware costs, software costs, travel shipping costs, labor contractor costs, testing costs, supply costs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Implementation Framework Cybersecurity Contingency Plan Business Impact Analysis Icons PDF
Presenting this set of slides with name cyber security implementation framework cybersecurity contingency plan business impact analysis icons pdf. The topics discussed in these slides are assign recovery priorities, determining vital it resources, determining issues impacts and acceptable outage time, vital resources, recovery priorities. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
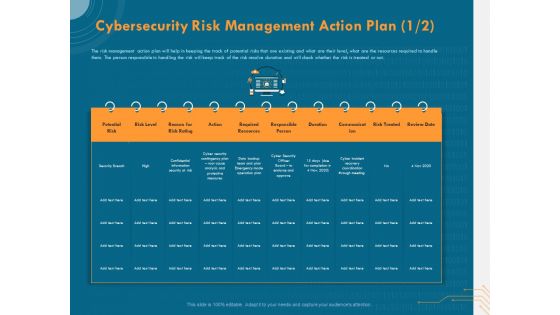
Cyber Security Implementation Framework Cybersecurity Risk Management Action Plan Potential Diagrams PDF
Presenting this set of slides with name cyber security implementation framework cybersecurity risk management action plan potential diagrams pdf. The topics discussed in these slides are potential risk, risk level, reason risk rating, action, required resources, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
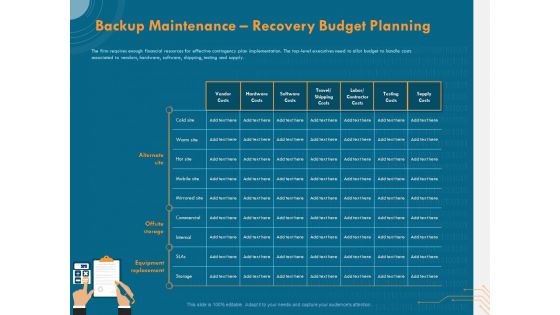
Cyber Security Implementation Framework Backup Maintenance Recovery Budget Planning Clipart PDF
Presenting this set of slides with name cyber security implementation framework backup maintenance recovery budget planning clipart pdf. The topics discussed in these slides are vendor costs, hardware costs, software costs, testing costs, supply costs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
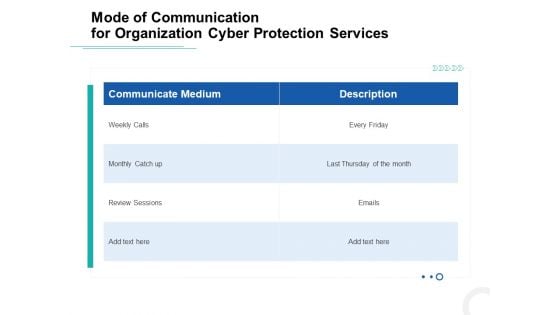
Develop Corporate Cyber Security Risk Mitigation Plan Mode Communication Organization Protection Services Introduction PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan mode communication organization protection services introduction pdf bundle. Topics like communicate medium, weekly calls, monthly catch up, review sessions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































