Email Template

Introduction To Natural Language Processing Technology AI Content Creation It Ppt Powerpoint
This slide gives an Introduction to Natural Language Processing technology. The purpose of this slide is to represent the NLP overview, its various techniques, working stages, and use cases in different domains, including translation applications, fake news detection, classifying emails, and so on. Are you searching for a Introduction To Natural Language Processing Technology AI Content Creation It Ppt Powerpoint that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Introduction To Natural Language Processing Technology AI Content Creation It Ppt Powerpoint from Slidegeeks today. This slide gives an Introduction to Natural Language Processing technology. The purpose of this slide is to represent the NLP overview, its various techniques, working stages, and use cases in different domains, including translation applications, fake news detection, classifying emails, and so on.
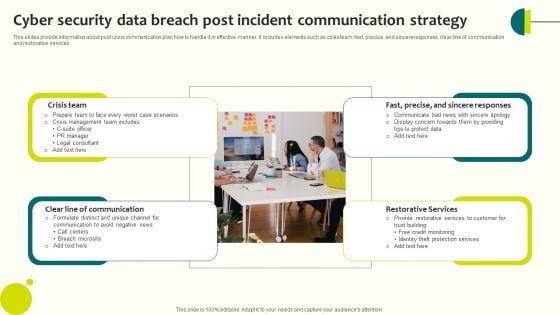
Cyber Security Data Breach Post Incident Communication Strategy Slides PDF
This slides provide information about post crisis communication plan how to handle it in effective manner. It includes elements such as crisis team, fast, precise, and sincereresponses, clear line of communication and restorative services Presenting Cyber Security Data Breach Post Incident Communication Strategy Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Crisis Team, Communication, Restorative Services. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Roadmap For Electronic Information Security Training Ppt Layouts Model PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Presenting cybersecurity roadmap for electronic information security training ppt layouts model pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
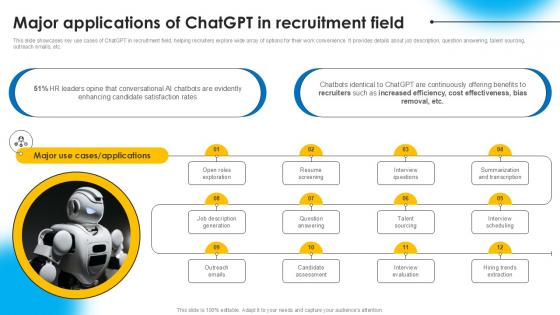
Major Applications Of ChatGPT AI Powered Recruitment Enhancing Ppt Sample AI SS V
This slide showcases key use cases of ChatGPT in recruitment field, helping recruiters explore wide array of options for their work convenience. It provides details about job description, question answering, talent sourcing, outreach emails, etc.Are you searching for a Major Applications Of ChatGPT AI Powered Recruitment Enhancing Ppt Sample AI SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Major Applications Of ChatGPT AI Powered Recruitment Enhancing Ppt Sample AI SS V from Slidegeeks today. This slide showcases key use cases of ChatGPT in recruitment field, helping recruiters explore wide array of options for their work convenience. It provides details about job description, question answering, talent sourcing, outreach emails, etc.
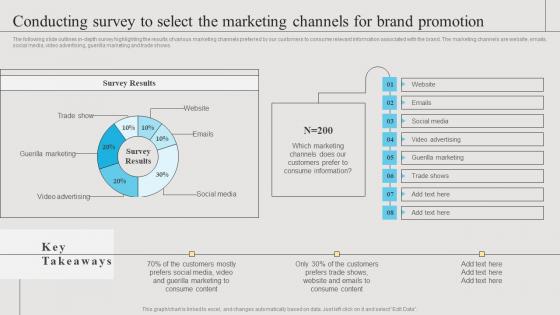
Conducting Survey To Select The Branding Strategies To Get Competitive Demonstration Pdf
The following slide outlines in-depth survey highlighting the results of various marketing channels preferred by our customers to consume relevant information associated with the brand. The marketing channels are website, emails, social media, video advertising, guerilla marketing and trade shows.Get a simple yet stunning designed Conducting Survey To Select The Branding Strategies To Get Competitive Demonstration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Conducting Survey To Select The Branding Strategies To Get Competitive Demonstration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide outlines in depth survey highlighting the results of various marketing channels preferred by our customers to consume relevant information associated with the brand. The marketing channels are website, emails, social media, video advertising, guerilla marketing and trade shows.
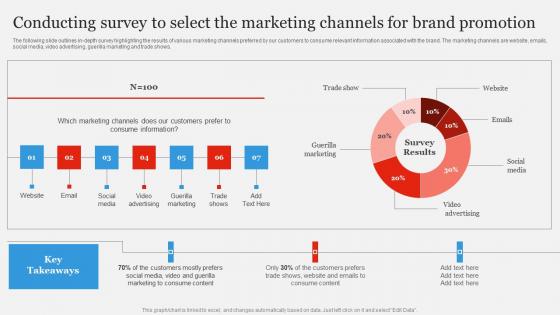
Conducting Survey Select The Marketing Branding Strategy To Gain Competitive Edge Clipart Pdf
The following slide outlines in depth survey highlighting the results of various marketing channels preferred by our customers to consume relevant information associated with the brand. The marketing channels are website, emails, social media, video advertising, guerilla marketing and trade shows. Get a simple yet stunning designed Conducting Survey Select The Marketing Branding Strategy To Gain Competitive Edge Clipart Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Conducting Survey Select The Marketing Branding Strategy To Gain Competitive Edge Clipart Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide outlines in depth survey highlighting the results of various marketing channels preferred by our customers to consume relevant information associated with the brand. The marketing channels are website, emails, social media, video advertising, guerilla marketing and trade shows.
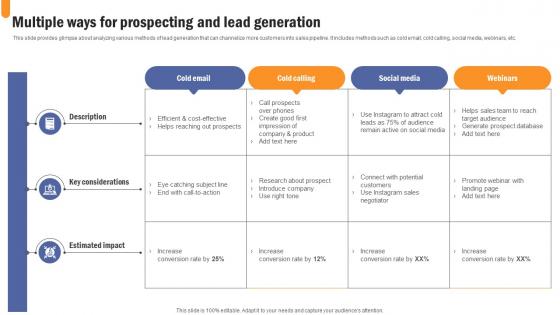
Multiple Ways For Prospecting And Lead Developing Extensive Sales And Operations Strategy Summary Pdf
This slide provides glimpse about analyzing various methods of lead generation that can channelize more customers into sales pipeline. It includes methods such as cold email, cold calling, social media, webinars, etc. Are you searching for a Multiple Ways For Prospecting And Lead Developing Extensive Sales And Operations Strategy Summary Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Multiple Ways For Prospecting And Lead Developing Extensive Sales And Operations Strategy Summary Pdf from Slidegeeks today. This slide provides glimpse about analyzing various methods of lead generation that can channelize more customers into sales pipeline. It includes methods such as cold email, cold calling, social media, webinars, etc.
Table Of Contents For IT Security IT Cont Tracking Ppt Infographics Graphics Example PDF
Presenting table of contents for it security it cont tracking ppt infographics graphics example pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cyber security, implementation, communication, administrative, training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
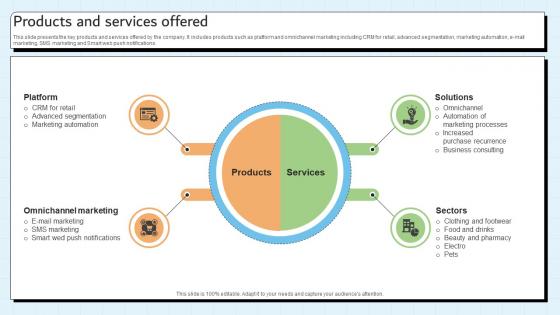
Products And Services Offered Customer Relationship Management Platform Pitch Deck
This slide presents the key products and services offered by the company. It includes products such as platform and omnichannel marketing including CRM for retail, advanced segmentation, marketing automation, e-mail marketing, SMS marketing and Smart web push notifications. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Customer Relationship Management Platform Pitch Deck to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide presents the key products and services offered by the company. It includes products such as platform and omnichannel marketing including CRM for retail, advanced segmentation, marketing automation, e-mail marketing, SMS marketing and Smart web push notifications.
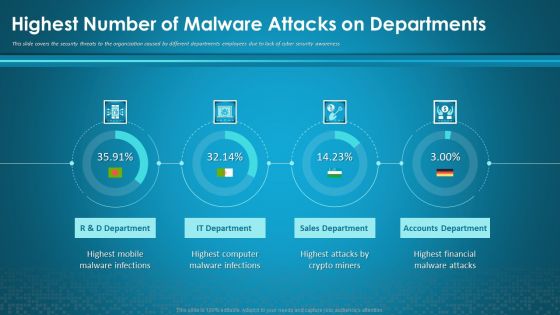
Organizational Network Security Awareness Staff Learning Highest Number Of Malware Attacks On Departments Information PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning highest number of malware attacks on departments information pdf. Use them to share invaluable insights on sales department, accounts department, financial, computer, mobile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
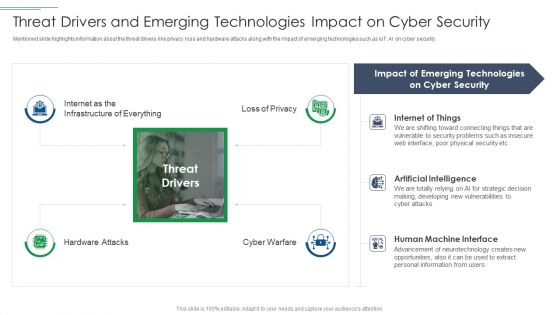
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Introduction To Natural Language Processing Technology Natural Language Automation
This slide gives an Introduction to Natural Language Processing technology. The purpose of this slide is to represent the NLP overview, its various techniques, working stages, and use cases in different domains, including translation applications, fake news detection, classifying emails, and so on. The Introduction To Natural Language Processing Technology Natural Language Automation is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide gives an Introduction to Natural Language Processing technology. The purpose of this slide is to represent the NLP overview, its various techniques, working stages, and use cases in different domains, including translation applications, fake news detection, classifying emails, and so on.
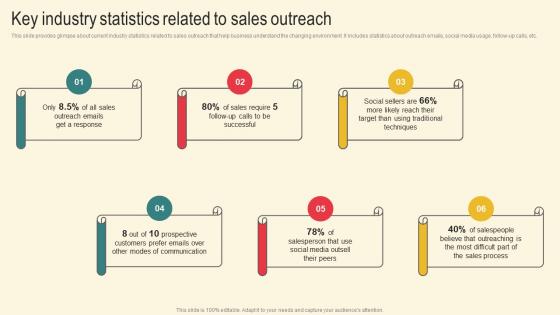
Key Industry Statistics Related Marketing Plan For Boosting Client Retention In Retail Banking Sample Pdf
This slide provides glimpse about current industry statistics related to sales outreach that help business understand the changing environment. It includes statistics about outreach emails, social media usage, follow up calls, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Key Industry Statistics Related Marketing Plan For Boosting Client Retention In Retail Banking Sample Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide provides glimpse about current industry statistics related to sales outreach that help business understand the changing environment. It includes statistics about outreach emails, social media usage, follow up calls, etc.
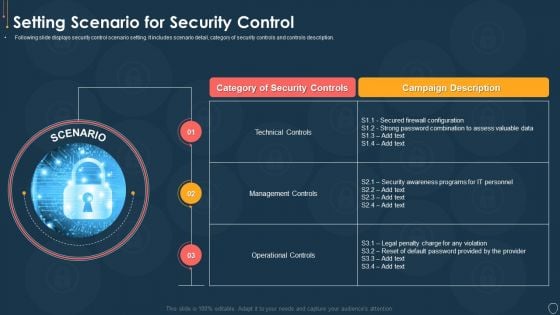
Cyber Security Risk Management Plan Setting Scenario For Security Control Microsoft PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. This is a cyber security risk management plan setting scenario for security control microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like category of security controls, campaign description, technical controls, management controls, operational controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Data Safety Initiatives For Effective IT Security Threats Administration Summary PDF
Presenting table of contents data safety initiatives for effective it security threats administration summary pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like overcoming identified gaps, improved incident reporting, communication plan cyber breaches, ensuring effective risk governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
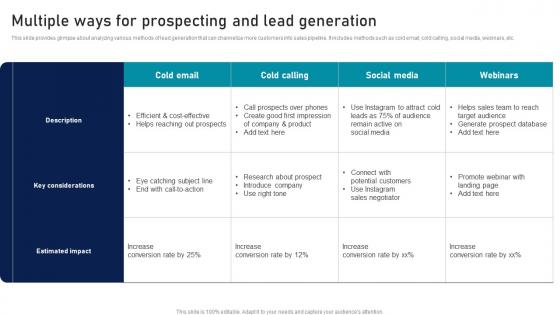
Multiple Ways For Prospecting And Lead Generation Strategic Sales Plan To Enhance Rules Pdf
This slide provides glimpse about analyzing various methods of lead generation that can channelize more customers into sales pipeline. It includes methods such as cold email, cold calling, social media, webinars, etc. Are you searching for a Multiple Ways For Prospecting And Lead Generation Strategic Sales Plan To Enhance Rules Pdf that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Multiple Ways For Prospecting And Lead Generation Strategic Sales Plan To Enhance Rules Pdf from Slidegeeks today. This slide provides glimpse about analyzing various methods of lead generation that can channelize more customers into sales pipeline. It includes methods such as cold email, cold calling, social media, webinars, etc.
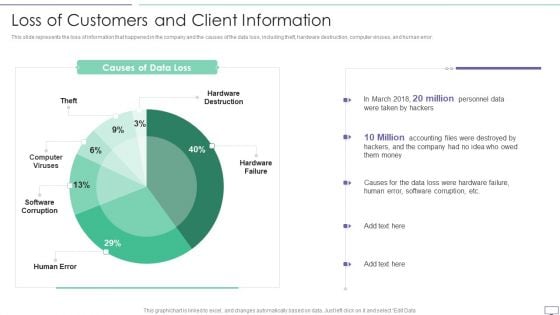
IT Security Hacker Loss Of Customers And Client Information Pictures PDF
This slide represents the loss of information that happened in the company and the causes of the data loss, including theft, hardware destruction, computer viruses, and human error.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Loss Due To Different Cyber Attacks Rules PDF. Use them to share invaluable insights on Hardware Destruction, Computer Viruses, Software Corruption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
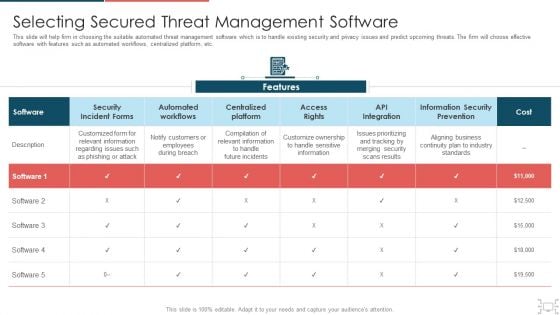
Cyber Security Administration In Organization Selecting Secured Threat Management Software Themes PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization selecting secured threat management software themes pdf. Use them to share invaluable insights on selecting secured threat management software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
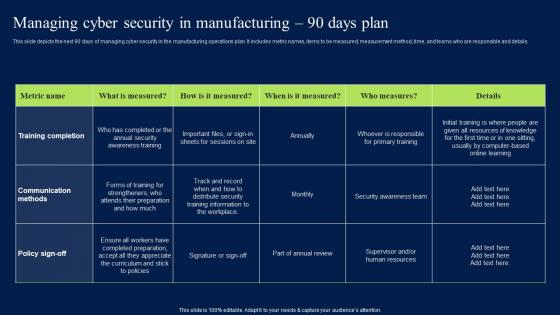
Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, andteams who are responsible and details. Slidegeeks has constructed Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.

Social Media Marketing To Boost Direct Response Marketing Introduction Demonstration Pdf
This slide provides an overview of direct response marketing that aims to persuade the audience to take quick action on the offer made. It further includes strategies and channels that are direct mail, email, social media, podcasts and referrals. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Social Media Marketing To Boost Direct Response Marketing Introduction Demonstration Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide provides an overview of direct response marketing that aims to persuade the audience to take quick action on the offer made. It further includes strategies and channels that are direct mail, email, social media, podcasts and referrals.

Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
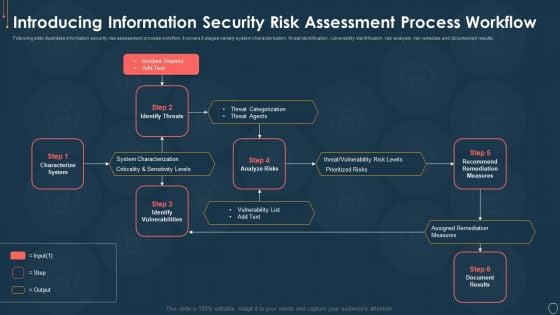
Cyber Security Risk Management Plan Introducing Information Security Risk Assessment Process Workflow Elements PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a cyber security risk management plan introducing information security risk assessment process workflow elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like characterize system, identify vulnerabilities, identify threats, recommend remediation measures, analyze risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
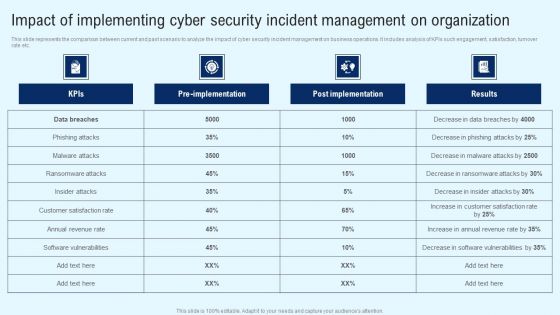
Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
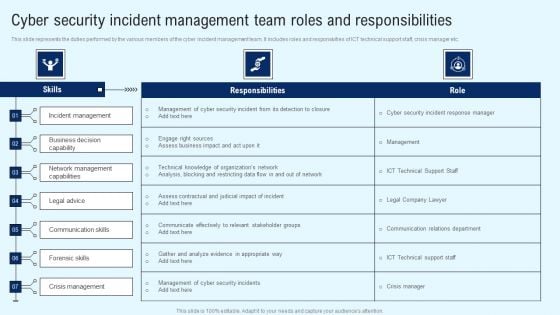
Implementing Cyber Security Incident Cyber Security Incident Team Roles Summary PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cyber Security Incident Cyber Security Incident Team Roles Summary PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cyber Security Incident Cyber Security Incident Team Roles Summary PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
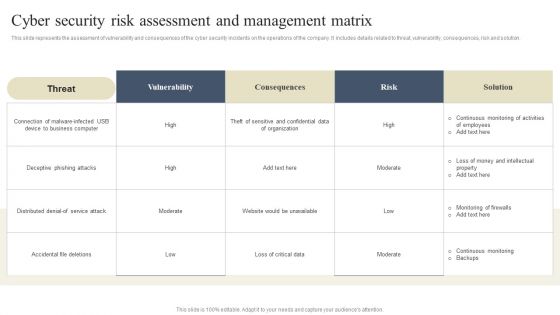
CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Welcome to our selection of the CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
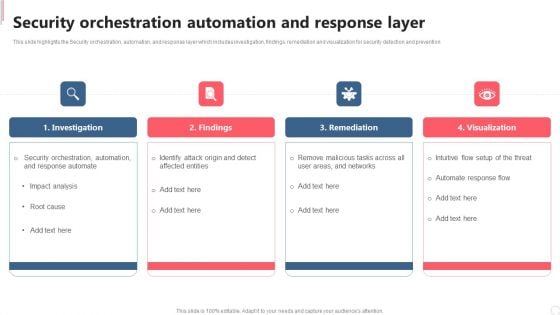
Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. Get a simple yet stunning designed Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
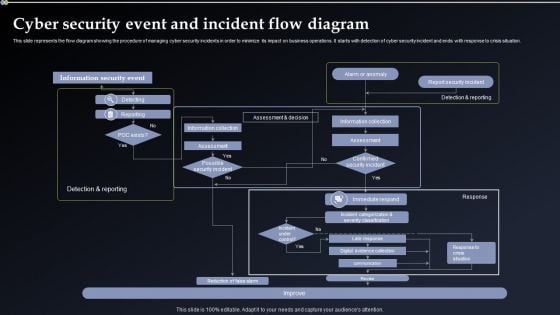
Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Welcome to our selection of the Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
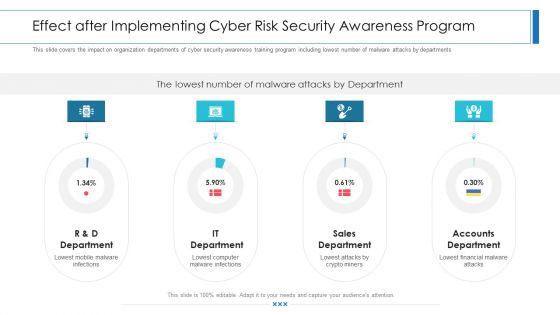
Workforce Security Realization Coaching Plan Effect After Implementing Cyber Risk Security Awareness Program Structure PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments. Presenting workforce security realization coaching plan effect after implementing cyber risk security awareness program structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like it department, sales department, accounts department. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
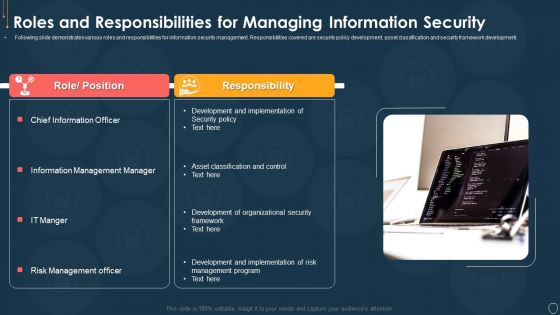
Cyber Security Risk Management Plan Roles And Responsibilities For Managing Information Security Mockup PDF
Following slide demonstrates various roles and responsibilities for information security management. Responsibilities covered are security policy development, asset classification and security framework development. Presenting cyber security risk management plan roles and responsibilities for managing information security mockup pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like role or position, responsibility. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
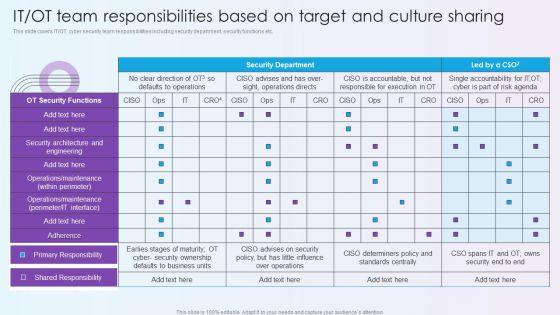
Digitalization Of Operative Enterprises IT OT Team Responsibilities Based On Target And Culture Sharing Microsoft PDF
This slide covers IT or OT cyber security team responsibilities including security department, security functions etc. Deliver and pitch your topic in the best possible manner with this Digitalization Of Operative Enterprises IT OT Team Responsibilities Based On Target And Culture Sharing Microsoft PDF. Use them to share invaluable insights on Security Functions, Security Ownership, Determiners and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
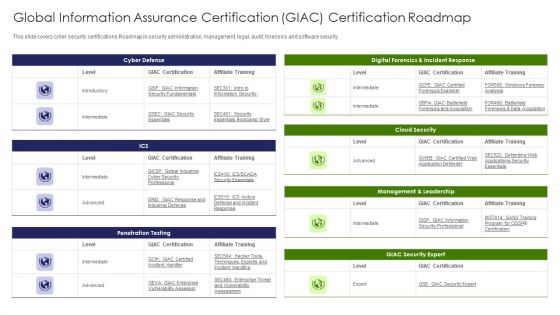
IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF. Use them to share invaluable insights on Cloud Security, Management, Security Expert and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Defining Categories Of Information Security Threats Structure PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures. This is a cyber security risk management plan defining categories of information security threats structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like human error, natural disaster, environmental control failures, deliberate software attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
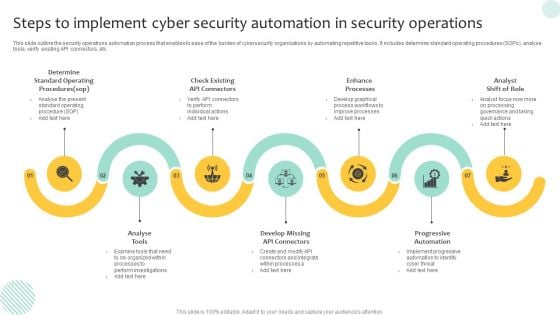
Steps To Implement Cyber Security Automation In Security Operations Demonstration PDF
This slide outline the security operations automation process that enables to ease of the burden of cybersecurity organizations by automating repetitive tasks. It includes determine standard operating procedures SOPs, analyse tools, verify existing API connectors, etc. Presenting Steps To Implement Cyber Security Automation In Security Operations Demonstration PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Progressive Automation, Enhance Processes, Analyse Tools. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
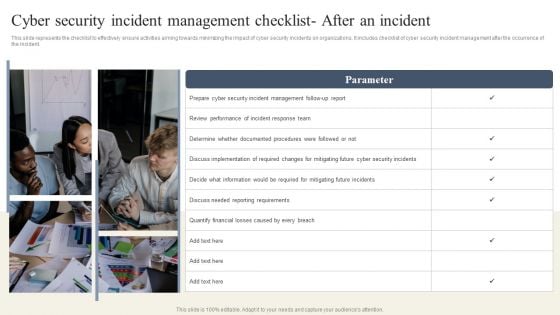
CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF can be your best option for delivering a presentation. Represent everything in detail using CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels
Explore a selection of the finest Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents Cybersecurity Risk Assessment Program Dashboard to effectively track cyber security risk levels. This will provide a structured approach for organizations to review and mitigate cyber threats. It includes multiple threat agents, attack methods, and preventive controls implemented with detailed insights, and it shows critical metrics including risk scores, the number of infected systems, and detected vulnerabilities.
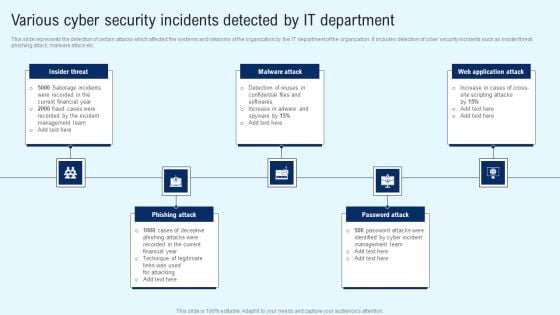
Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Electronic Voting System Electoral Process Registering The Voters Brochure PDF
This slide represents the registering process of voters, including through mails, forms from a local registrar, in-person visits to the office, and even on the election day itself.Presenting Electronic Voting System Electoral Process Registering The Voters Brochure PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Appropriate Public, Appropriate Government, Registration Laws. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault How To Prevent Ddos Attacks In The Company Inspiration PDF
This slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc.Presenting cyber terrorism assault how to prevent ddos attacks in the company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like service providers bandwidth capacity, network monitoring, update security components In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CYBER Security Breache Response Strategy Strategies To Analyze Cyber Security Incidents Inspiration PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Do you know about Slidesgeeks CYBER Security Breache Response Strategy Strategies To Analyze Cyber Security Incidents Inspiration PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
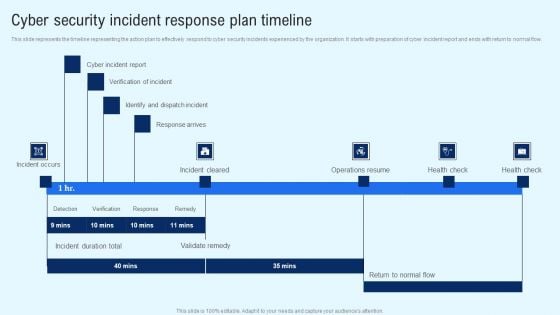
Implementing Cyber Security Incident Cyber Security Incident Response Plan Timeline Download PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Welcome to our selection of the Implementing Cyber Security Incident Cyber Security Incident Response Plan Timeline Download PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cybersecurity Detail Impact Electronic Information Ppt Portfolio Rules PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this cybersecurity detail impact electronic information ppt portfolio rules pdf. Use them to share invaluable insights on detail impact electronic information security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
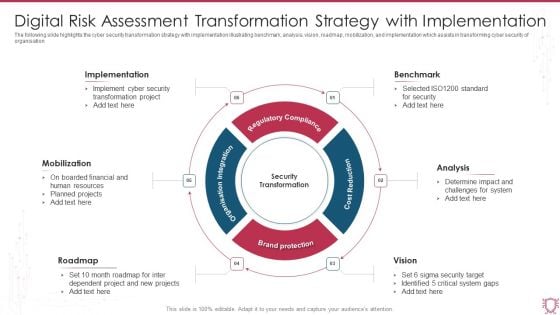
Digital Risk Assessment Transformation Strategy With Implementation Slides PDF
The following slide highlights the cyber security transformation strategy with implementation illustrating benchmark, analysis, vision, roadmap, mobilization, and implementation which assists in transforming cyber security of organisation. Presenting Digital Risk Assessment Transformation Strategy With Implementation Slides PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Implementation, Benchmark, Analysis, Vision. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

AI Applications In Banking And Financial Services Formats PDF
This slide covers use of artificial intelligence in banking and financial services. It involves applications such as customer engagement, predictive analytics, cyber security and credit scoring.Presenting AI Applications In Banking And Financial Services Formats PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Customer Engagement, Predictive Analytics, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

AI Applications Use To Improve Business Operations Diagrams PDF
This slide signifies the artificial intelligence software used to increase organisation operations. It covers information about hiring, market prediction, customer analysis and cyber security Presenting AI Applications Use To Improve Business Operations Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Market Prediction, Customer Analysis, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
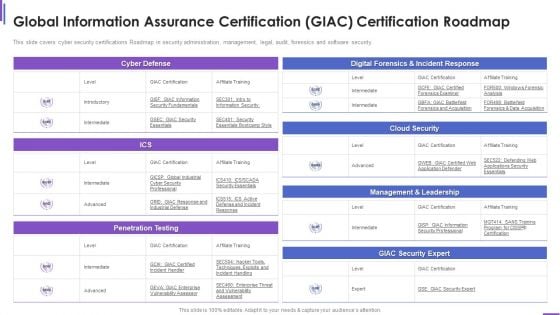
Collection Of Information Technology Certifications Global Information Assurance Designs PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this collection of information technology certifications global information assurance designs pdf. Use them to share invaluable insights on global information assurance certification giac certification roadmap and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Diverging 11 Factors Round Manner Ppt Cycle Flow Chart PowerPoint Slides
We present our diverging 11 factors round manner ppt Cycle Flow Chart PowerPoint Slides.Use our Circle Charts PowerPoint Templates because you have played a stellar role and have a few ideas. Use our Arrows PowerPoint Templates because you can see clearly through to the bigger bowl ahead. Time your jump to perfection and hit the nail on the head. Use our Business PowerPoint Templates because spell out your advertising plans to increase market share. The feedback has been positive and productive. Download and present our Shapes PowerPoint Templates because this one depicts the popular chart. Use our Flow Charts PowerPoint Templates because like your thoughts arrows are inherently precise and true.Use these PowerPoint slides for presentations relating to amazement, application, arrow, background, black, circle, devolution, direction, direction-giving, email, glamour, help, icon, insert, internet, joy, manners, reflex, roundly, scalable, search, searching, solution, support, universal, vector, visible, way, website, white. The prominent colors used in the PowerPoint template are Yellow, Green, Blue. Customers tell us our diverging 11 factors round manner ppt Cycle Flow Chart PowerPoint Slides are Fashionable. PowerPoint presentation experts tell us our devolution PowerPoint templates and PPT Slides are Ritzy. People tell us our diverging 11 factors round manner ppt Cycle Flow Chart PowerPoint Slides are Glamorous. People tell us our arrow PowerPoint templates and PPT Slides will make you look like a winner. Customers tell us our diverging 11 factors round manner ppt Cycle Flow Chart PowerPoint Slides are Bold. People tell us our arrow PowerPoint templates and PPT Slides are One-of-a-kind. With our Diverging 11 Factors Round Manner Ppt Cycle Flow Chart PowerPoint Slides you won't be ambivalent. Decide on a definite direction to follow.

Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF
This slide covers the roadmap for various courses in security awareness programs. It includes cyber system management, password security program, insider threats program, e mail security program.Presenting Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Security Program, Threats Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
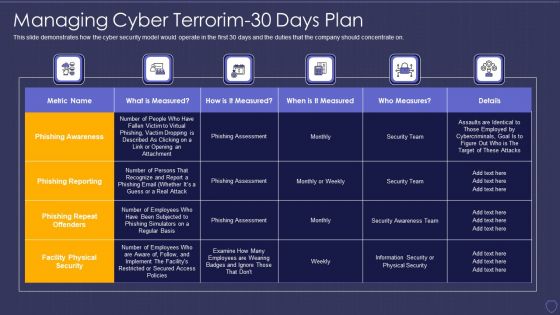
Global Cyber Terrorism Incidents On The Rise IT Managing Cyber Terrorim 30 Days Plan Information PDF
This slide demonstrates how the cyber security model would operate in the first 30 days and the duties that the company should concentrate on. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it managing cyber terrorim 30 days plan information pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
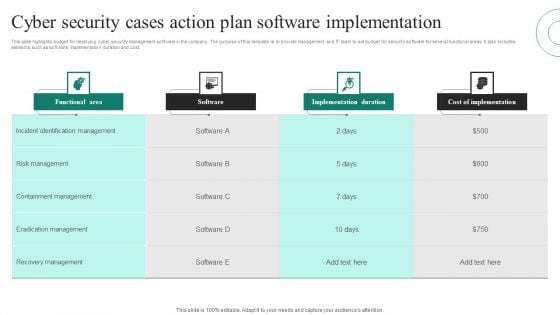
Cyber Security Cases Action Plan Software Implementation Ppt PowerPoint Presentation File Grid PDF
This slide highlights budget for deploying cyber security management software in the company. The purpose of this template is to provide management and IT team to set budget for security software for several functional areas. It also includes elements such as software, implementation duration and cost. Pitch your topic with ease and precision using this Cyber Security Cases Action Plan Software Implementation Ppt PowerPoint Presentation File Grid PDF. This layout presents information on Functional Area, Software, Implementation Duration, Cost Implementation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
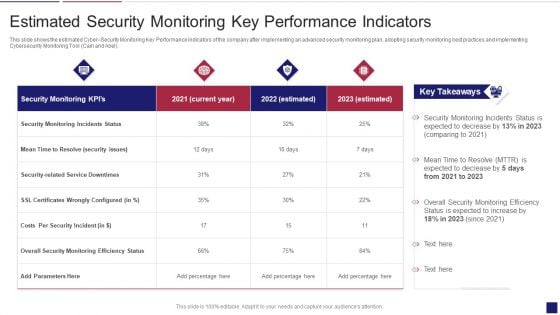
Continuous Development Evaluation Plan Eliminate Cyber Attacks Estimated Security Monitoring Designs PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks estimated security monitoring designs pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
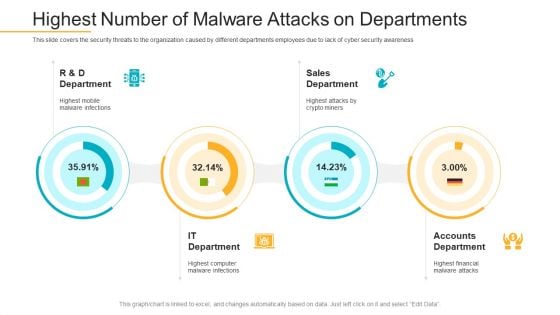
Data Breach Prevention Recognition Highest Number Of Malware Attacks On Departments Pictures PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition highest number of malware attacks on departments pictures pdf. Use them to share invaluable insights on sales department, accounts department, it department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
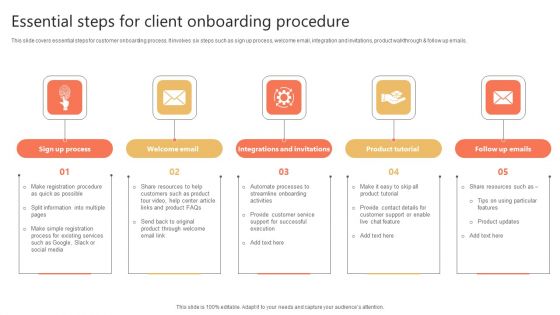
Essential Steps For Client Onboarding Procedure Ppt Slides Infographics PDF
This slide covers essential steps for customer onboarding process. It involves six steps such as sign up process, welcome email, integration and invitations, product walkthrough and follow up emails. Persuade your audience using this Essential Steps For Client Onboarding Procedure Ppt Slides Infographics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Sign Up Process, Welcome Email, Integrations And Invitations, Product Tutorial. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Administration In Organization Determine Several Threat Actors Profile Sample PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization determine several threat actors profile sample pdf. Use them to share invaluable insights on determine several threat actors profile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Risk Management Approach Introduction Communication Plan For Cyber Breaches Pictures PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Communication Plan For Cyber Breaches Pictures PDF. Use them to share invaluable insights on Sprint Report, Product Report, Delivery Method and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
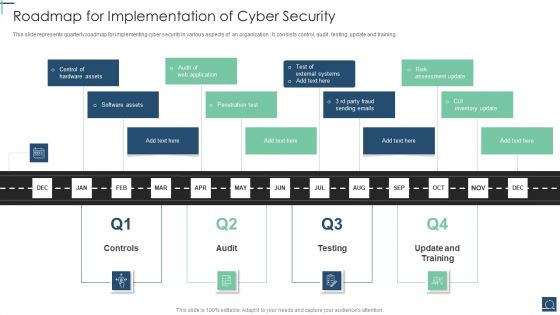
Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF
This slide represents quarterly roadmap for implementing cyber security in various aspects of an organization . It consists control, audit , testing, update and training. Presenting Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Penetration Test, Software Assets, Control Hardware Assets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
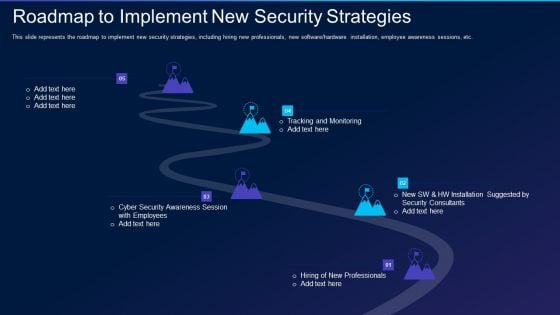
Cyber Exploitation IT Roadmap To Implement New Security Strategies Information PDF
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. This is a cyber exploitation it roadmap to implement new security strategies information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like tracking and monitoring, security consultants, cyber security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era Information Security Program Values To Business Ppt Slides Background Designs PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. This is a handling cyber threats digital era information security program values to business ppt slides background designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security program values to business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Risk Management Plan Asset Criticality Of Identified System Components Mockup PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan asset criticality of identified system components mockup pdf. Use them to share invaluable insights on system name, component used, impact rating, criticality rating, failure cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
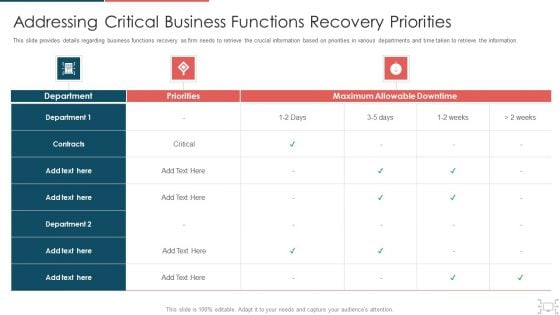
Cyber Security Administration In Organization Addressing Critical Business Functions Recovery Download PDF
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing critical business functions recovery download pdf. Use them to share invaluable insights on addressing critical business functions recovery priorities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































