Employees Responsibility
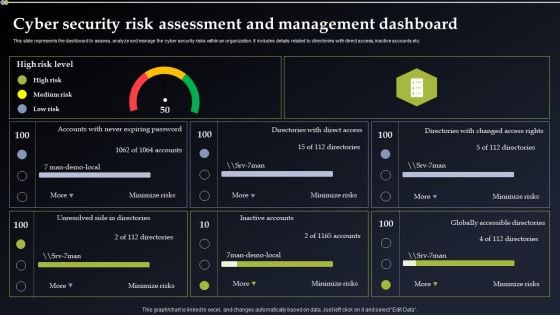
Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present like a pro with Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
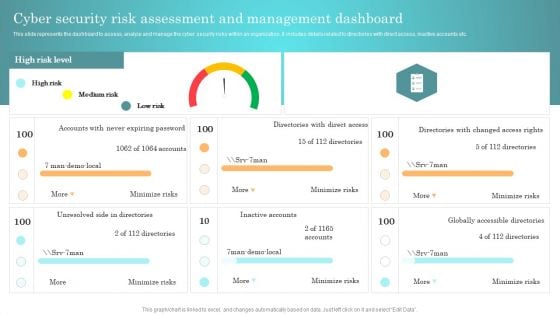
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Dashboard Themes PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present like a pro with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Dashboard Themes PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
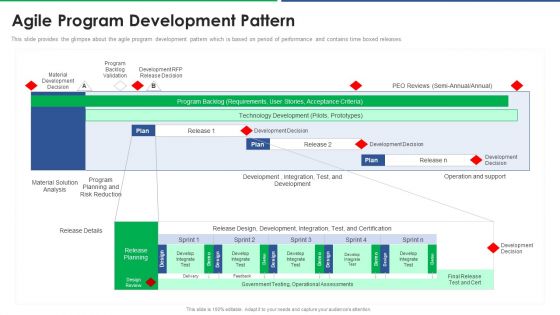
Agile Technique For Request For Proposal RFP Response Agile Program Development Pattern Structure PDF
This slide provides the glimpse about the agile program development pattern which is based on period of performance and contains time boxed releases. Deliver and pitch your topic in the best possible manner with this agile technique for request for proposal rfp response agile program development pattern structure pdf. Use them to share invaluable insights on operation and support, development decision, release details, technology development and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
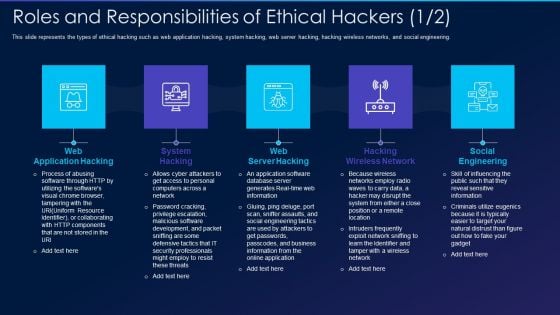
Cyber Exploitation IT Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering. Presenting cyber exploitation it roles and responsibilities of ethical hackers pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like web application hacking, system hacking, web server hacking, hacking wireless network, social engineering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
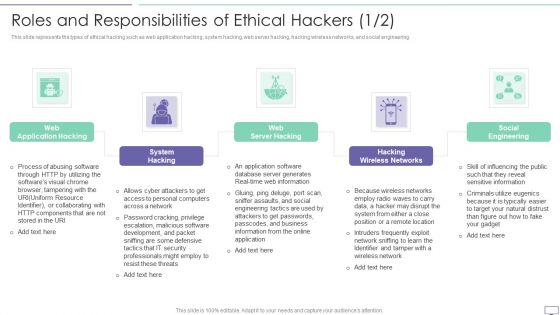
IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering.Presenting IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Application Hacking, System Hacking, Wireless Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Approaches To Make Mobile Website Responsive Search Engine Optimization Services To Minimize Elements PDF
The purpose of this slide is to outline various approaches which will assist the marketer to optimize website design. It provides information about scaling the images for mobile users, blocking popup notifications etc. Take your projects to the next level with our ultimate collection of Approaches To Make Mobile Website Responsive Search Engine Optimization Services To Minimize Elements PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they all make your projects stand out from the rest.
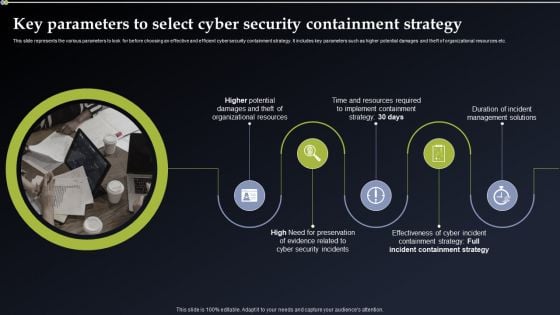
Deploying Cyber Security Incident Response Administration Key Parameters To Select Cyber Security Infographics PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Deploying Cyber Security Incident Response Administration Key Parameters To Select Cyber Security Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF

Incident Response Techniques Deployement Benefits Of Implementing Web Application Firewall Brochure PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Find a pre designed and impeccable Incident Response Techniques Deployement Benefits Of Implementing Web Application Firewall Brochure PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
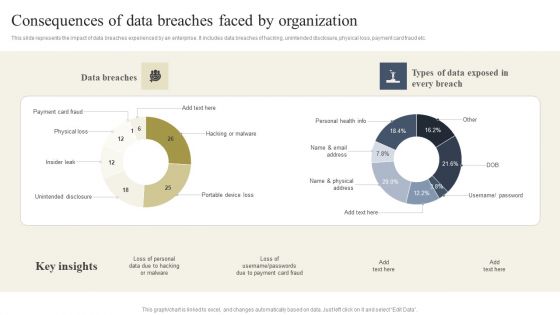
Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Boost your pitch with our creative Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

CYBER Security Breache Response Strategy Benefits Of Implementing Web Application Firewall Portrait PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Find a pre designed and impeccable CYBER Security Breache Response Strategy Benefits Of Implementing Web Application Firewall Portrait PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

CYBER Security Breache Response Strategy Comparative Analysis Of Web Application Firewall Products Slides PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. There are so many reasons you need a CYBER Security Breache Response Strategy Comparative Analysis Of Web Application Firewall Products Slides PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Present like a pro with Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

CYBER Security Breache Response Strategy Cyber Security Incident Communication Strategy Topics PDF
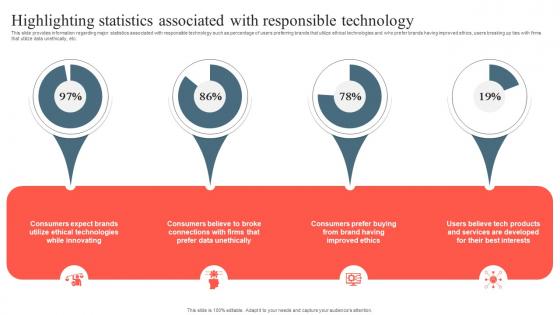
Playbook To Remediate False Highlighting Statistics Associated With Responsible Pictures Pdf
This slide provides information regarding the utilization of tarot of tech. It is considered a brainstorming exercise that allows the team to manage the long term vision of the product. The steps followed to utilize tarot cards of tech in terms of integration into smaller groups, discuss emerging queries, feedback discussion, etc. This Playbook To Remediate False Highlighting Statistics Associated With Responsible Pictures Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Playbook To Remediate False Highlighting Statistics Associated With Responsible Pictures Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides information regarding the utilization of tarot of tech. It is considered a brainstorming exercise that allows the team to manage the long term vision of the product. The steps followed to utilize tarot cards of tech in terms of integration into smaller groups, discuss emerging queries, feedback discussion, etc.

Incident Response Techniques Deployement Five Phases Of Cybersecurity Incident Management Formats PDF
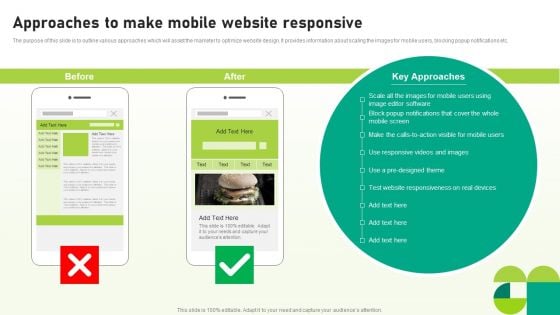
Utilizing SEO To Boost Customer Approaches To Make Mobile Website Responsive Structure PDF
The purpose of this slide is to outline various approaches which will assist the marketer to optimize website design. It provides information about scaling the images for mobile users, blocking popup notifications etc. Present like a pro with Utilizing SEO To Boost Customer Approaches To Make Mobile Website Responsive Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
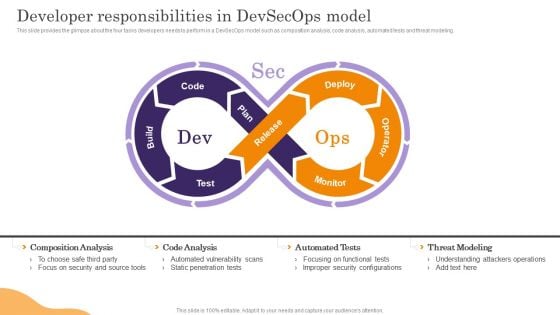
Devops App Process Administration Developer Responsibilities In Devsecops Model Guidelines PDF
This slide provides the glimpse about the four tasks developers needs to perform in a DevSecOps model such as composition analysis, code analysis, automated tests and threat modeling. Present like a pro with Devops App Process Administration Developer Responsibilities In Devsecops Model Guidelines PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
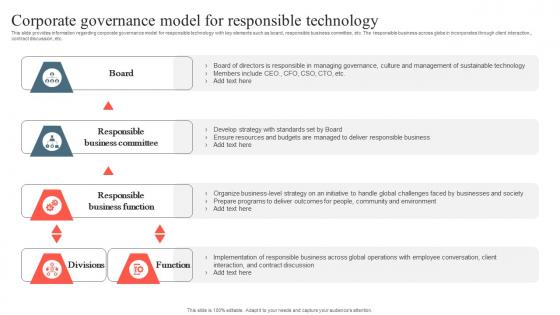
Playbook To Remediate False Corporate Governance Model For Responsible Elements Pdf
This slide provides information regarding data ethics canvas model which acts as a potential tool for data collection, sharing and utilization. It helps in detecting managing ethical issues. Key elements include data sources, reducing negative impact, etc. Present like a pro with Playbook To Remediate False Corporate Governance Model For Responsible Elements Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide provides information regarding data ethics canvas model which acts as a potential tool for data collection, sharing and utilization. It helps in detecting managing ethical issues. Key elements include data sources, reducing negative impact, etc.

Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Slidegeeks has constructed Incident Response Techniques Deployement User Awareness Training Program To Prevent Cyber Security Incidents Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
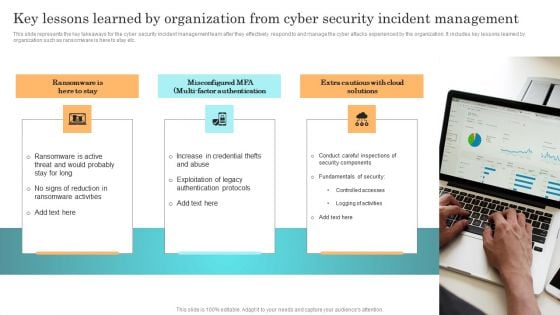
Incident Response Techniques Deployement Key Lessons Learned By Organization From Cyber Security Incident Formats PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Key Lessons Learned By Organization From Cyber Security Incident Formats PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
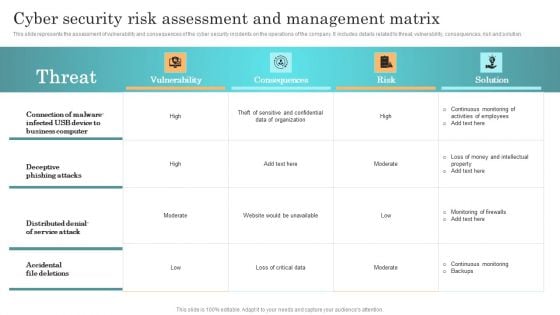
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Slidegeeks is here to make your presentations a breeze with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
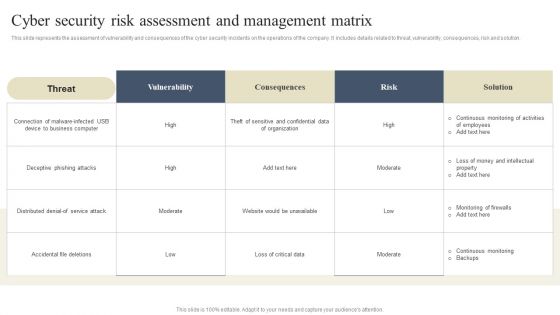
CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Welcome to our selection of the CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Responsible Technology Playbook Ethical Operating System OS Risk Mitigation Checklist Infographics PDF
This slide provides information regarding ethical operating system OS risk mitigation checklist that helps to track various risk zones such as trust, disinformation and propaganda, economic and asset inequalities, addiction and dopamine economy, etc. Do you know about Slidesgeeks Responsible Technology Playbook Ethical Operating System OS Risk Mitigation Checklist Infographics PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. The Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
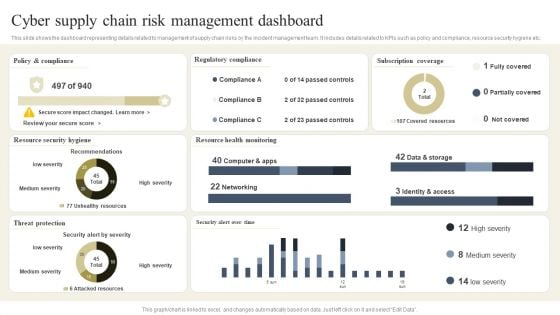
CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
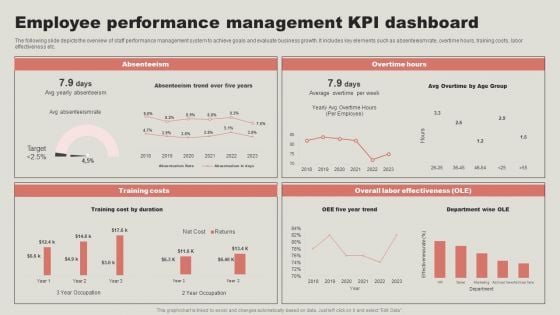
Employee Performance Management KPI Dashboard Structure PDF
The following slide depicts the overview of staff performance management system to achieve goals and evaluate business growth. It includes key elements such as absenteeism rate, overtime hours, training costs, labor effectiveness etc. Take your projects to the next level with our ultimate collection of Employee Performance Management KPI Dashboard Structure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Deploying Cyber Security Incident Response Administration Ppt PowerPoint Presentation Complete Deck With Slides
Starting a presentation on business is a decision to make. As you think about it, you realize that everything is a decision. Our Deploying Cyber Security Incident Response Administration Ppt PowerPoint Presentation Complete Deck With Slides will make all your business tasks and decisions a bit easier, with its emphasis on planning. The sixty nine slide complete deck allows you to present the daily challenges of business in your own way to your team, key stakeholders, and external vendors etc. With each slide being 100 percent editable and customizable, you may decide to fiddle around with the design or the content ready nature to arrive at your own, presentation on a topic of your choosing. Download now.
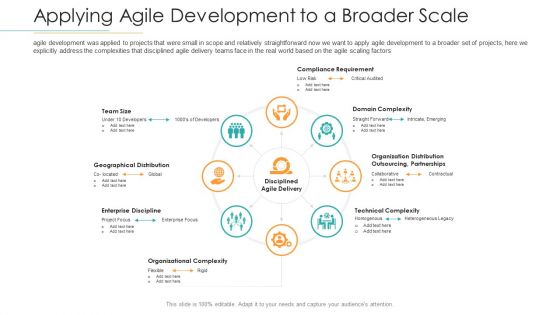
Disciplined Agile Distribution Responsibilities Applying Agile Development To A Broader Scale Formats PDF
Agile development was applied to projects that were small in scope and relatively straightforward now we want to apply agile development to a broader set of projects, here we explicitly address the complexities that disciplined agile delivery teams face in the real world based on the agile scaling factors. This is a disciplined agile distribution responsibilities applying agile development to a broader scale formats pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like geographical distribution, enterprise discipline, organizational complexity, technical complexity, domain complexity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
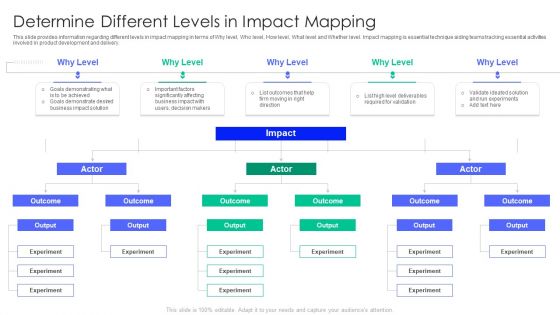
Controlling And Innovating Product Leader Responsibilities Determine Different Levels In Impact Mapping Designs Pdf
This slide provides information regarding different levels in impact mapping in terms of Why level, Who level, How level, What level and Whether level. Impact mapping is essential technique aiding teams tracking essential activities involved in product development and delivery. This is a controlling and innovating product leader responsibilities determine different levels in impact mapping designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deliverables required for validation, firm moving in right direction, decision makers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
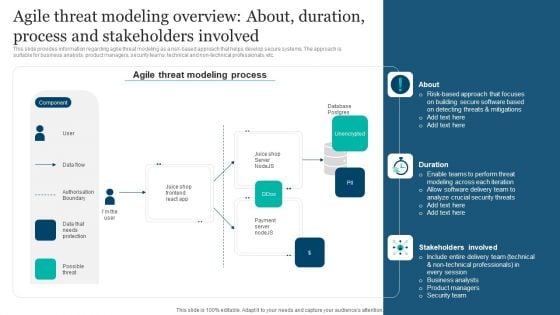
Responsible Technology Playbook Agile Threat Modeling Overview About Duration Process Elements PDF
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. This modern and well-arranged Responsible Technology Playbook Agile Threat Modeling Overview About Duration Process Elements PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Employee Internal Efficient Communication Technique Elements PDF
This slide highlights an internal communication strategy that identifies corporate objectives for staff communications and schedules the actions necessary to accomplish those objectives. The key aspects include culture and core values, growth and development, communication flow etc. Presenting Employee Internal Efficient Communication Technique Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Culture And Core Values, Growth And Development, Communication Flow, Feedback And Action Plan, Promote Transparency. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Retrieve professionally designed CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
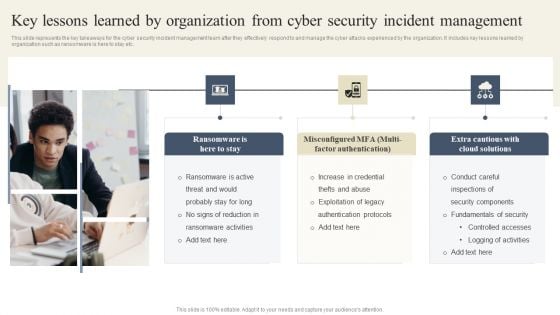
CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. This CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
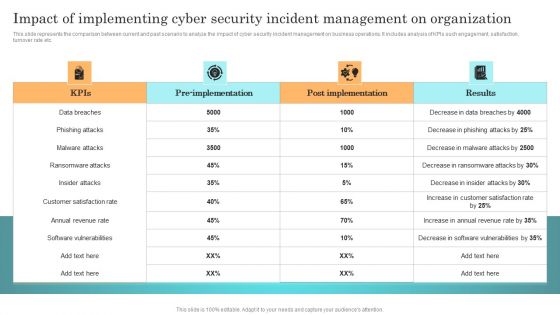
Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Retrieve professionally designed Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
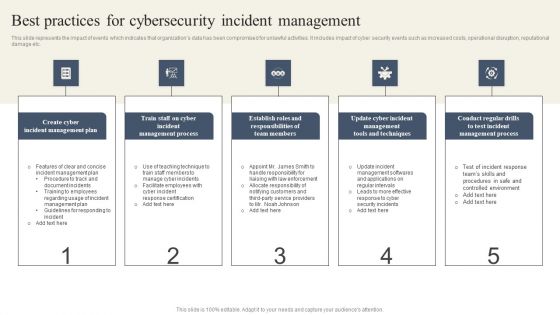
CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
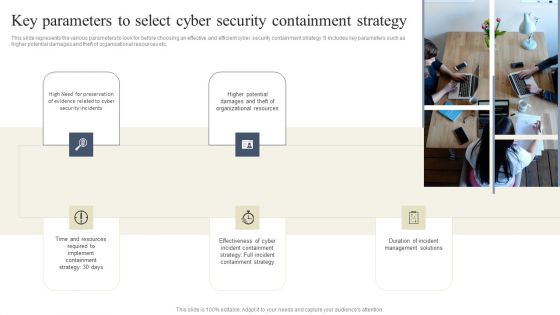
CYBER Security Breache Response Strategy Key Parameters To Select Cyber Security Containment Strategy Information PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Take your projects to the next level with our ultimate collection of CYBER Security Breache Response Strategy Key Parameters To Select Cyber Security Containment Strategy Information PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
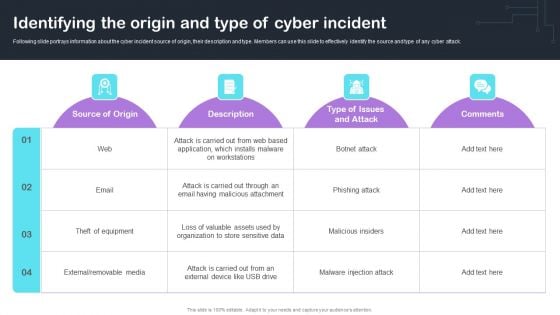
Cyber Risks And Incident Response Playbook Identifying The Origin And Type Of Cyber Incident Download PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Risks And Incident Response Playbook Identifying The Origin And Type Of Cyber Incident Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
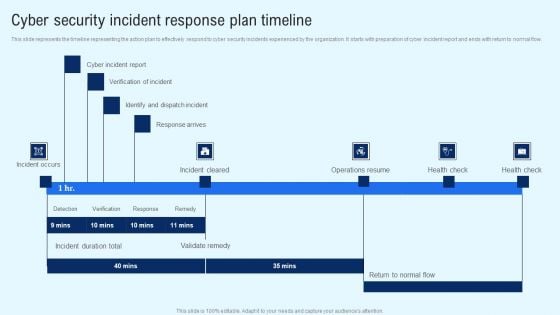
Implementing Cyber Security Incident Cyber Security Incident Response Plan Timeline Download PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Welcome to our selection of the Implementing Cyber Security Incident Cyber Security Incident Response Plan Timeline Download PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
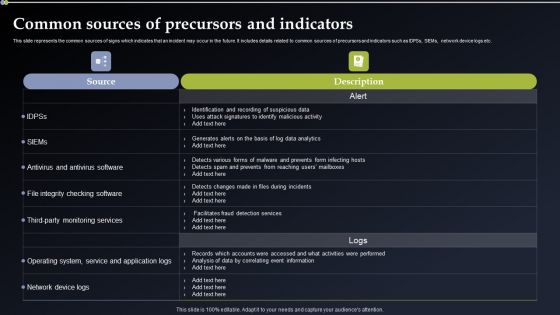
Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. This modern and well arranged Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
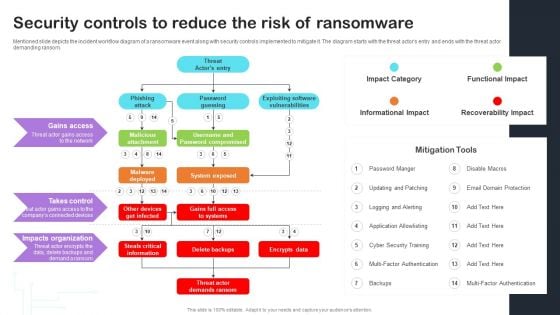
Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Take your projects to the next level with our ultimate collection of Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.

Incident Response Techniques Deployement Cyber Security Incident Management Checklist After An Incident Summary PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Incident Response Techniques Deployement Cyber Security Incident Management Checklist After An Incident Summary PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident Management before the occurrence of the incident. This modern and well arranged Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
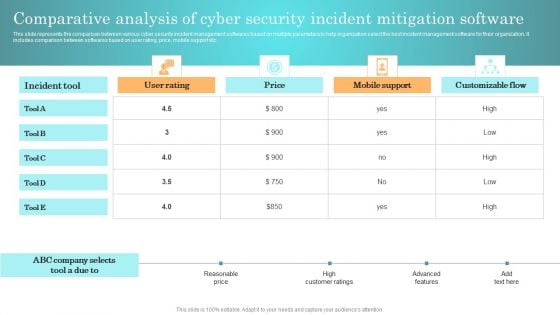
Incident Response Techniques Deployement Comparative Analysis Of Cyber Security Incident Mitigation Software Summary PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Incident Response Techniques Deployement Comparative Analysis Of Cyber Security Incident Mitigation Software Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Incident Response Techniques Deployement Comparative Analysis Of Web Application Firewall Products Infographics PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Want to ace your presentation in front of a live audience Our Incident Response Techniques Deployement Comparative Analysis Of Web Application Firewall Products Infographics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Want to ace your presentation in front of a live audience Our CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
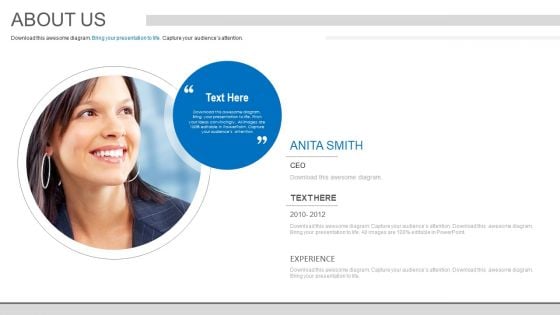
About Employee Profile And Experience Powerpoint Slides
On this template you can see image of corporate employee. This PowerPoint slide is an excellent tool for introduction of new employee. Give a detailed introduction of your team member with complete profile information.

Organizational Disaster Management Risk Checklist Information PDF
This slide depicts organizational disaster management response checklist that benefits organization in making preparations for employee safety illustrating safety checklist, employee management etc. Showcasing this set of slides titled organizational disaster management risk checklist information pdf. The topics addressed in these templates are prioritizing response checklist, employee management checklist, safety checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Organizational DRR Checklist Ppt Icon Themes PDF
This slide depicts organizational disaster management response checklist that benefits organization in making preparations for employee safety illustrating safety checklist, employee management etc. Showcasing this set of slides titled organizational drr checklist ppt icon themes pdf. The topics addressed in these templates are safety checklist, employee management checklist, prioritizing response checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
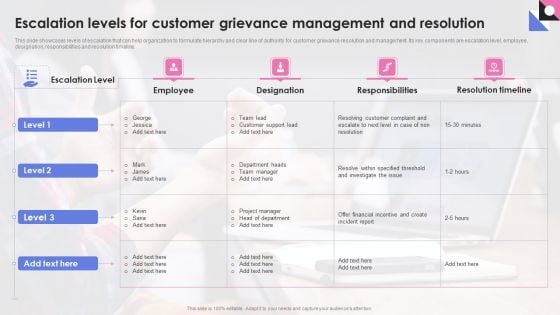
Escalation Levels For Customer Grievance Management And Resolution Inspiration PDF
This slide showcases levels of escalation that can help organization to formulate hierarchy and clear line of authority for customer grievance resolution and management. Its key components are escalation level, employee, designation, responsibilities and resolution timeline. Pitch your topic with ease and precision using this Escalation Levels For Customer Grievance Management And Resolution Inspiration PDF. This layout presents information on Customer, Team Lead, Financial Incentive. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Corporate Employee Engagement Current Employee Engagement Activities In The Organization Ppt Professional Backgrounds PDF
Presenting this set of slides with name corporate employee engagement current employee engagement activities in the organization ppt professional backgrounds pdf. The topics discussed in these slides are activity, category, description, frequency, responsibility. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies For Stabilizing Corporate RACI Matrix For Effective Financial Management
This slide exhibits the RACI matrix that helps an organization clarify employee roles and responsibilities for each task. It includes tasks such as develop financial restructuring plan, negotiation with lenders, negotiation with banks, manage merger and acquisition procedure, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Strategies For Stabilizing Corporate RACI Matrix For Effective Financial Management from Slidegeeks and deliver a wonderful presentation. This slide exhibits the RACI matrix that helps an organization clarify employee roles and responsibilities for each task. It includes tasks such as develop financial restructuring plan, negotiation with lenders, negotiation with banks, manage merger and acquisition procedure, etc.

Raci Matrix For Effective Financial Management Strategic Approaches To Corporate Financial
This slide exhibits the RACI matrix that helps an organization clarify employee roles and responsibilities for each task. It includes tasks such as develop financial restructuring plan, negotiation with lenders, negotiation with banks, manage merger and acquisition procedure, etc. The Raci Matrix For Effective Financial Management Strategic Approaches To Corporate Financial is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide exhibits the RACI matrix that helps an organization clarify employee roles and responsibilities for each task. It includes tasks such as develop financial restructuring plan, negotiation with lenders, negotiation with banks, manage merger and acquisition procedure, etc.

Timeline To Run Performance Marketing Campaign Paid Internet Marketing Strategy Graphics Pdf
This slide displays timeline that can help marketers to plan and ensure timely execution of performance marketing campaign. Key elements of this timeline are marketing activity, responsible employee and status. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline To Run Performance Marketing Campaign Paid Internet Marketing Strategy Graphics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide displays timeline that can help marketers to plan and ensure timely execution of performance marketing campaign. Key elements of this timeline are marketing activity, responsible employee and status.

Strategic Performance Marketing Campaign Timeline To Run Performance Marketing Designs Pdf
This slide displays timeline that can help marketers to plan and ensure timely execution of performance marketing campaign. Key elements of this timeline are marketing activity, responsible employee and status. Get a simple yet stunning designed Strategic Performance Marketing Campaign Timeline To Run Performance Marketing Designs Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Strategic Performance Marketing Campaign Timeline To Run Performance Marketing Designs Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide displays timeline that can help marketers to plan and ensure timely execution of performance marketing campaign. Key elements of this timeline are marketing activity, responsible employee and status.

Running Email Marketing Plan To Retain And Nurture Strategic Marketing Plan Microsoft PDF
This slide showcases email marketing plan that can help organization to retain customers after new brand launch. Its key elements are email, goal, email type, email details, expected results and responsible employee for email promotion. Get a simple yet stunning designed Running Email Marketing Plan To Retain And Nurture Strategic Marketing Plan Microsoft PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Running Email Marketing Plan To Retain And Nurture Strategic Marketing Plan Microsoft PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases email marketing plan that can help organization to retain customers after new brand launch. Its key elements are email, goal, email type, email details, expected results and responsible employee for email promotion.
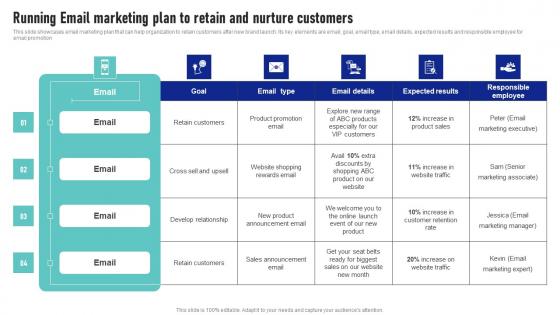
Running Email Marketing Plan To Retain And Nurture Launching New Product Brand Rules Pdf
This slide showcases email marketing plan that can help organization to retain customers after new brand launch. Its key elements are email, goal, email type, email details, expected results and responsible employee for email promotion Get a simple yet stunning designed Running Email Marketing Plan To Retain And Nurture Launching New Product Brand Rules Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Running Email Marketing Plan To Retain And Nurture Launching New Product Brand Rules Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases email marketing plan that can help organization to retain customers after new brand launch. Its key elements are email, goal, email type, email details, expected results and responsible employee for email promotion


 Continue with Email
Continue with Email

 Home
Home


































