Encryption
Information Studies Tools For Data Science SAS Designs PDF
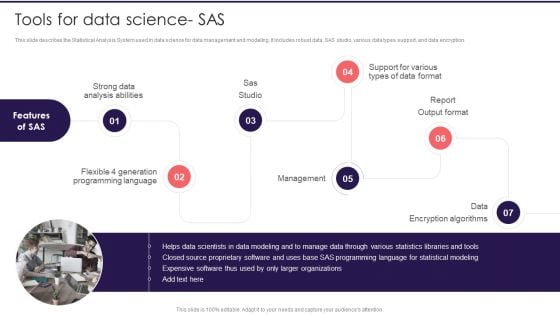
This slide describes the Statistical Analysis System used in data science for data management and modeling. It includes robust data, SAS studio, various data types support, and data encryption. Presenting Information Studies Tools For Data Science SAS Designs PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Strong Data Analysis, Data Format, Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Supply Chain Management Iot Application Pre Implementation Audit Checklist Introduction PDF
This slide shows pre implementation audit checklist for internet of things IoT application. It provides information about accuracy, system design, Wi-Fi, real time location service, Bluetooth low energy, transfer method, battery life, data encryption, etc. This is a Supply Chain Management Iot Application Pre Implementation Audit Checklist Introduction PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Parameters, Locate Packages, Iot Systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Supply Chain Management Timeline Deploying Iot Into Logistics Department Diagrams PDF
This slide depicts logistics internet of things IoT deployment timeline. It includes details such as technologies, devices, prototypes, gateways, operating system, network connections, data encryption, pallets, fleet, training, user acceptance testing, etc. Deliver and pitch your topic in the best possible manner with this Supply Chain Management Timeline Deploying Iot Into Logistics Department Diagrams PDF. Use them to share invaluable insights on Planning And Research, Evaluating Current Technologies, Choosing Operating System and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Infotech Solutions Research And Development Company Summary Case Study Software Development Summary PDF
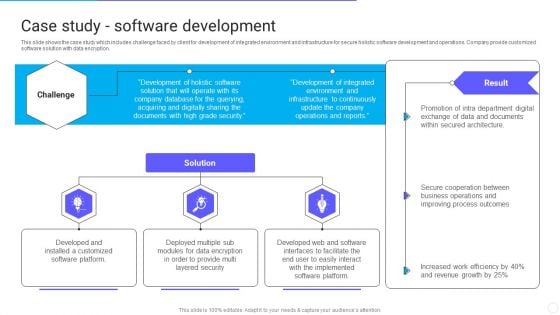
This slide shows the case study which includes challenge faced by client for development of integrated environment and infrastructure for secure holistic software development and operations. Company provide customized software solution with data encryption. Presenting Infotech Solutions Research And Development Company Summary Case Study Software Development Summary PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Challenge, Solution, Result. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Benefits Of Using A Reverse Proxy Server Reverse Proxy For Load Balancing Designs PDF
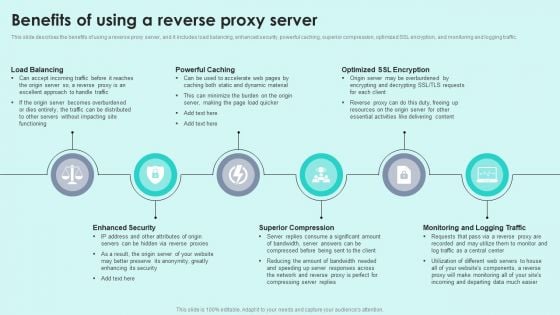
This slide describes the benefits of using a reverse proxy server, and it includes load balancing, enhanced security, powerful caching, superior compression, optimized SSL encryption, and monitoring and logging traffic.This is a Benefits Of Using A Reverse Proxy Server Reverse Proxy For Load Balancing Designs PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Load Balancing, Powerful Caching, Superior Compression. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Canva Pro Business Profile Canva Security Processes And Systems Elements PDF
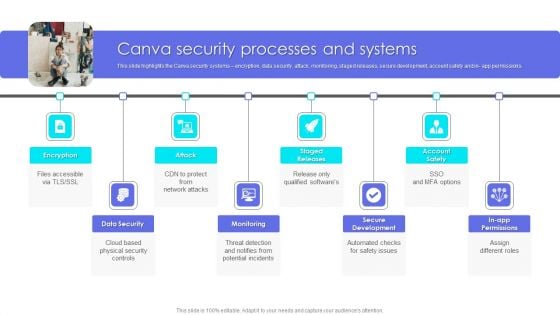
This slide highlights the Canva security systems encryption, data security, attack, monitoring, staged releases, secure development, account safety and in app permissions. Presenting Business Profile Canva Security Processes And Systems Elements PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Data Security, Monitoring, Secure Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Science Tools For Data Science Sas Ppt PowerPoint Presentation Infographics Graphic Images PDF
This slide describes the Statistical Analysis System used in data science for data management and modeling. It includes robust data, SAS studio, various data types support, and data encryption.This is a Information Science Tools For Data Science Sas Ppt PowerPoint Presentation Infographics Graphic Images PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Proprietary Software, Statistical Modeling, Data Scientists. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Application Services Company Outline Case Study Software Development Infographics PDF
This slide shows the case study which includes challenge faced by client for development of integrated environment and infrastructure for secure holistic software development and operations. Company provide customized software solution with data encryption. Presenting IT Application Services Company Outline Case Study Software Development Infographics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Layered Security, Implemented, Developed Web. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Securing Data Over Google Cloud Google Cloud Computing System Professional PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock.Presenting Securing Data Over Google Cloud Google Cloud Computing System Professional PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Management, Protect Information, Compute Engine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
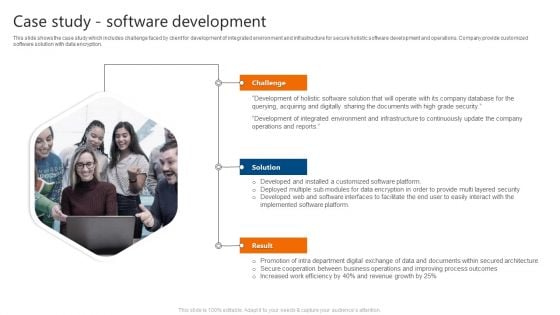
Case Study Software Development IT Software Development Company Profile Microsoft PDF
This slide shows the case study which includes challenge faced by client for development of integrated environment and infrastructure for secure holistic software development and operations. Company provide customized software solution with data encryption. Presenting Case Study Software Development IT Software Development Company Profile Microsoft PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Development, Company, Process Outcomes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
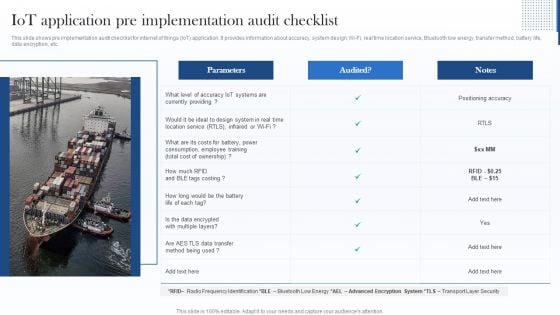
Iot Application Pre Implementation Audit Checklist Download PDF
This slide shows pre implementation audit checklist for internet of things IoT application. It provides information about accuracy, system design, Wi Fi, real time location service, Bluetooth low energy, transfer method, battery life, data encryption, etc. Deliver an awe inspiring pitch with this creative Iot Application Pre Implementation Audit Checklist Download PDF bundle. Topics like Cost Of Ownership, Design System, Method can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Iot Application Pre Implementation Audit Checklist Guidelines PDF
This slide shows pre implementation audit checklist for internet of things IoT application. It provides information about accuracy, system design, Wi Fi, real time location service, Bluetooth low energy, transfer method, battery life, data encryption, etc. Presenting Iot Application Pre Implementation Audit Checklist Guidelines PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Design System, Location Service, Positioning Accuracy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
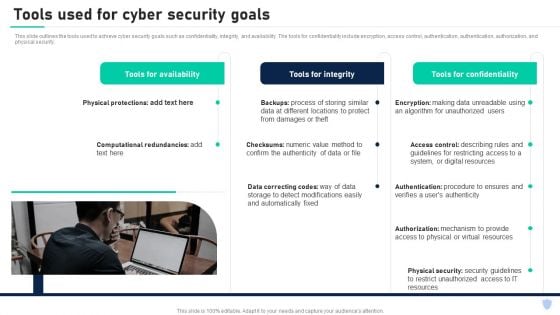
Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF
This slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
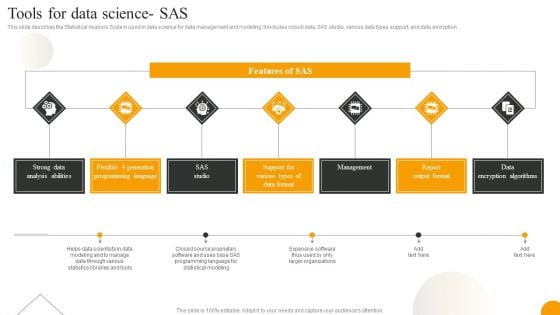
Using Data Science Technologies For Business Transformation Tools For Data Science SAS Introduction PDF
This slide describes the Statistical Analysis System used in data science for data management and modeling. It includes robust data, SAS studio, various data types support, and data encryption. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Using Data Science Technologies For Business Transformation Tools For Data Science SAS Introduction PDF from Slidegeeks and deliver a wonderful presentation.
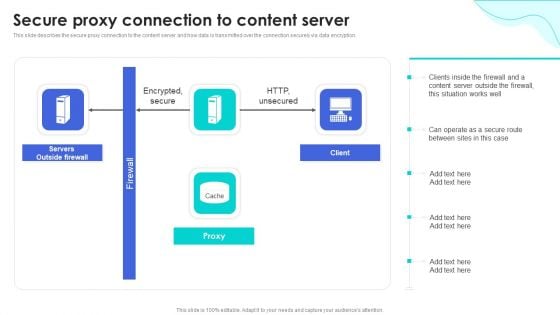
Reverse Proxy Web Server Secure Proxy Connection To Content Server Ideas PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Find a pre-designed and impeccable Reverse Proxy Web Server Secure Proxy Connection To Content Server Ideas PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF
This slide covers cybersecurity attack vector analysis for effective awareness training. It involves malware, phishing, denial of service, poor encryption, device misconfiguration and cross site scripting. Persuade your audience using this IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Attack Vector, Examples, Objective Problem Identifier. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
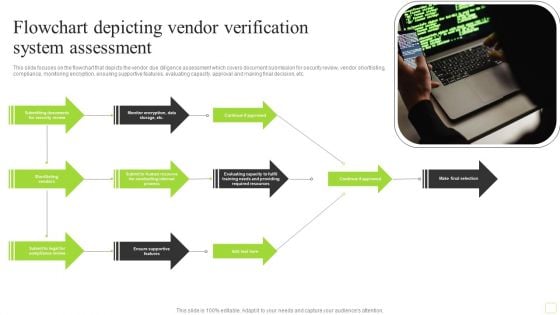
Flowchart Depicting Vendor Verification System Assessment Infographics PDF
This slide focuses on the flowchart that depicts the vendor due diligence assessment which covers document submission for security review, vendor shortlisting, compliance, monitoring encryption, ensuring supportive features, evaluating capacity, approval and making final decision, etc. Presenting Flowchart Depicting Vendor Verification System Assessment Infographics PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Required Resources, Conducting Internal Process, Security Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
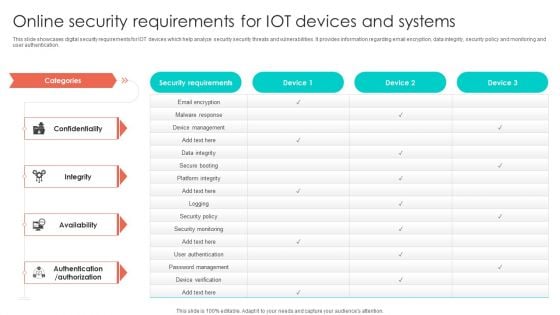
Online Security Requirements For Iot Devices And Systems Graphics PDF
This slide showcases digital security requirements for IOT devices which help analyze security security threats and vulnerabilities. It provides information regarding email encryption, data integrity, security policy and monitoring and user authentication. Pitch your topic with ease and precision using this Online Security Requirements For Iot Devices And Systems Graphics PDF. This layout presents information on Device Management, Security Policy, Security Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
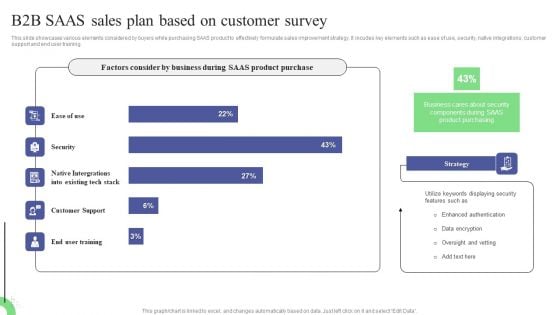
B2B SAAS Sales Plan Based On Customer Survey Demonstration PDF
This slide showcases various elements considered by buyers while purchasing SAAS product to effectively formulate sales improvement strategy. It incudes key elements such as ease of use, security, native integrations, customer support and end user training. Showcasing this set of slides titled B2B SAAS Sales Plan Based On Customer Survey Demonstration PDF. The topics addressed in these templates are Data Encryption, Displaying Security, Strategy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
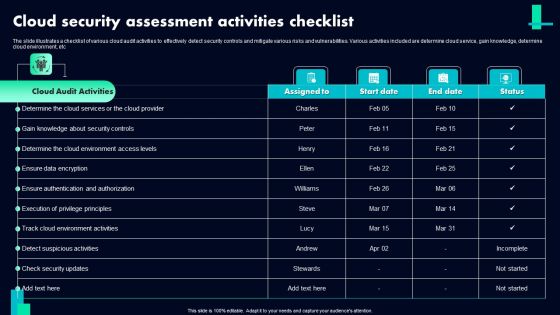
Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF
The slide illustrates a checklist of various cloud audit activities to effectively detect security controls and mitigate various risks and vulnerabilities. Various activities included are determine cloud service, gain knowledge, determine cloud environment, etc. Showcasing this set of slides titled Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF. The topics addressed in these templates are Cloud Audit Activities, Ensure Data Encryption, Detect Suspicious Activities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Iot Application Pre Implementation Audit Checklist Topics PDF
This slide shows pre implementation audit checklist for internet of things IoT application. It provides information about accuracy, system design, Wi-Fi, real time location service, Bluetooth low energy, transfer method, battery life, data encryption, etc. Create an editable Iot Application Pre Implementation Audit Checklist Topics PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Iot Application Pre Implementation Audit Checklist Topics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
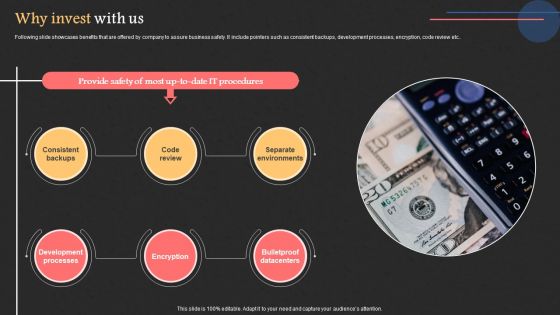
Project Management Software Capital Raising Deck Why Invest With Us Download PDF
Following slide showcases benefits that are offered by company to assure business safety. It include pointers such as consistent backups, development processes, encryption, code review etc. Slidegeeks has constructed Project Management Software Capital Raising Deck Why Invest With Us Download PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Picture Editing Company Outline Canva Security Processes And Systems Elements PDF
This slide highlights the Canva security systems encryption, data security, attack, monitoring, staged releases, secure development, account safety and in- app permissions. Welcome to our selection of the Picture Editing Company Outline Canva Security Processes And Systems Elements PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cloud Computing Application Security Architecture Audit Checklist Structure PDF
The slide shows a checklist containing number of tasks needed to be done while performing application security audit. It includes tasks like developing password policies, making multi factor confirmation mandatory, supervising SaaS license, etc. Showcasing this set of slides titled Cloud Computing Application Security Architecture Audit Checklist Structure PDF. The topics addressed in these templates are Develop Password Policies, Validate Anti Attacking Protections, Set Message Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Do you know about Slidesgeeks Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls.
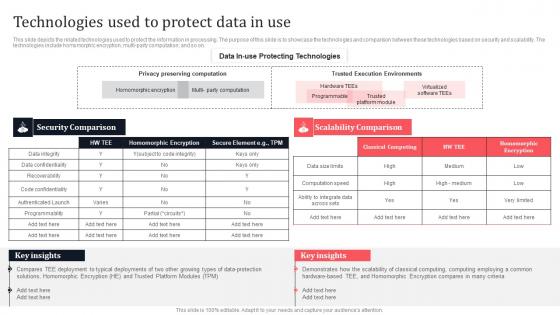
Technologies Used To Protect Data In Use Secure Multi Party Template Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Technologies Used To Protect Data In Use Secure Multi Party Template Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Technologies Used To Protect Data In Use Secure Multi Party Template Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.

Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present like a pro with Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
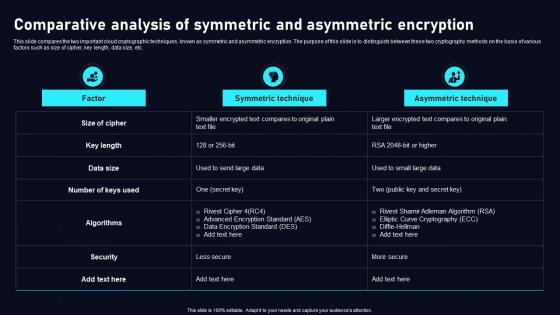
Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Explore a selection of the finest Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Comparative Analysis Of Symmetric Cloud Data Security Using Cryptography Clipart Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc.
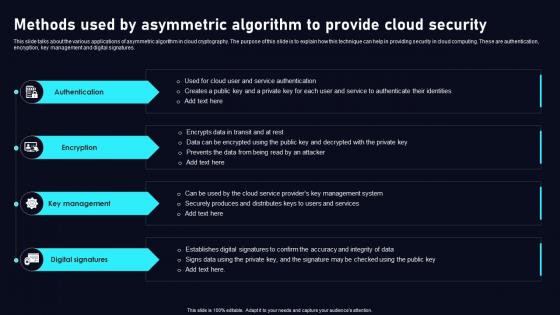
Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Get a simple yet stunning designed Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Methods Used By Asymmetric Algorithm Cloud Data Security Using Cryptography Inspiration Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.
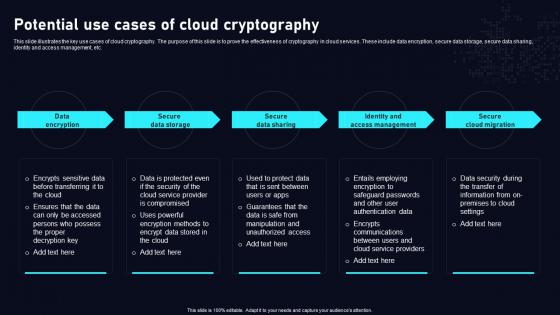
Potential Use Cases Of Cloud Cryptography Cloud Data Security Using Cryptography Information Pdf
This slide illustrates the key use cases of cloud cryptography. The purpose of this slide is to prove the effectiveness of cryptography in cloud services. These include data encryption, secure data storage, secure data sharing, identity and access management, etc. Present like a pro with Potential Use Cases Of Cloud Cryptography Cloud Data Security Using Cryptography Information Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide illustrates the key use cases of cloud cryptography. The purpose of this slide is to prove the effectiveness of cryptography in cloud services. These include data encryption, secure data storage, secure data sharing, identity and access management, etc.
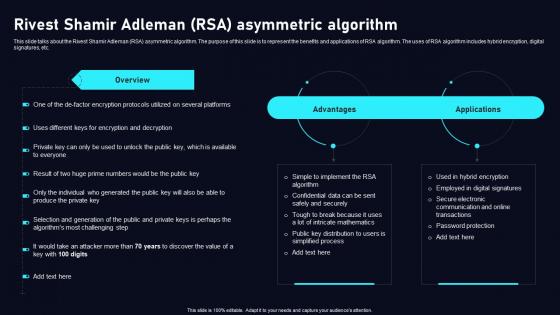
Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf
This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Slidegeeks is here to make your presentations a breeze with Rivest Shamir Adleman RSA Asymmetric Cloud Data Security Using Cryptography Slides Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc.

What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc.

Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security. If you are looking for a format to display your unique thoughts, then the professionally designed Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.
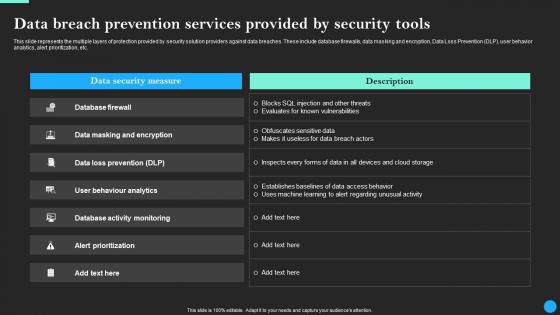
Data Breach Prevention Services Provided Data Breach Prevention Graphics Pdf
This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Breach Prevention Services Provided Data Breach Prevention Graphics Pdfand observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc.

Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.

Strategies For Reducing Cybersecurity Risks In ABS Healthcare Company Ppt Professional Mockup PDF
This slide shows strategies that can be adopted by the company in order to minimize the cybersecurity risks and increasing malware attacks. Some strategies are data encryption, proper employee training, protection of physical devices, use df latest and updated softwares etc. This is a strategies for reducing cybersecurity risks in ABS healthcare company ppt professional mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data management, operating system maintenance, financial, protect devices that can be physically accessed. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
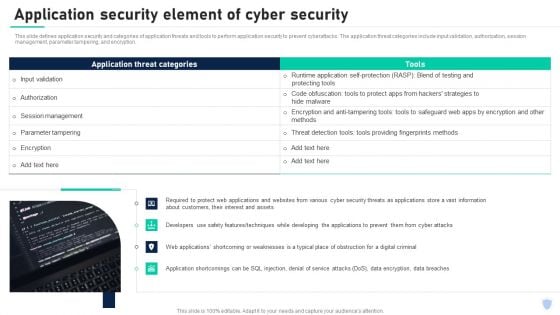
Cyber Security Components To Enhance Processes Application Security Element Of Cyber Security Infographics PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. The application threat categories include input validation, authorization, session management, parameter tampering, and encryption. Boost your pitch with our creative Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
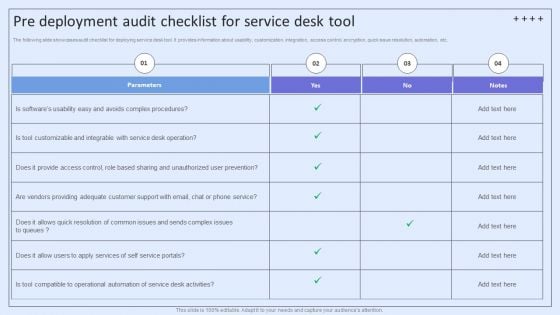
Integrating ITSM To Enhance Service Pre Deployment Audit Checklist For Service Desk Tool Summary PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. Welcome to our selection of the Integrating ITSM To Enhance Service Pre Deployment Audit Checklist For Service Desk Tool Summary PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
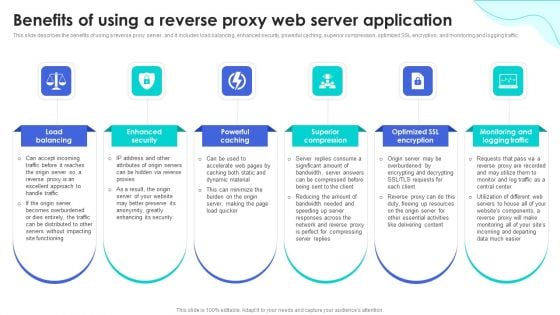
Reverse Proxy Web Server Benefits Of Using A Reverse Proxy Web Server Application Mockup PDF
This slide describes the benefits of using a reverse proxy server, and it includes load balancing, enhanced security, powerful caching, superior compression, optimized SSL encryption, and monitoring and logging traffic. Present like a pro with Reverse Proxy Web Server Benefits Of Using A Reverse Proxy Web Server Application Mockup PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
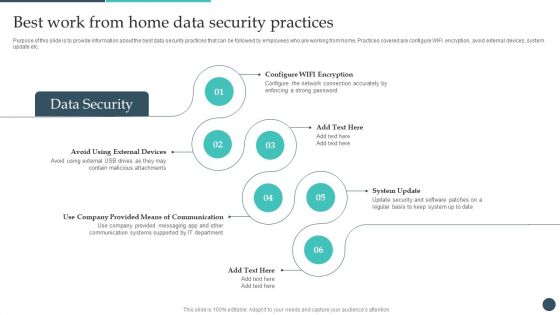
Safety Breach Response Playbook Best Work From Home Data Security Practices Topics PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Explore a selection of the finest Safety Breach Response Playbook Best Work From Home Data Security Practices Topics PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Safety Breach Response Playbook Best Work From Home Data Security Practices Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
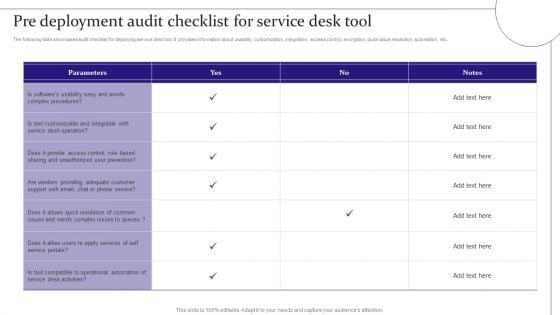
Digitalization Of Service Desk Pre Deployment Audit Checklist For Service Desk Tool Ppt Infographics Information PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. This Digitalization Of Service Desk Pre Deployment Audit Checklist For Service Desk Tool Ppt Infographics Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Digitalization Of Service Desk Pre Deployment Audit Checklist For Service Desk Tool Ppt Infographics Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Work From Home Data Security Practices Improving Cybersecurity With Incident Inspiration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
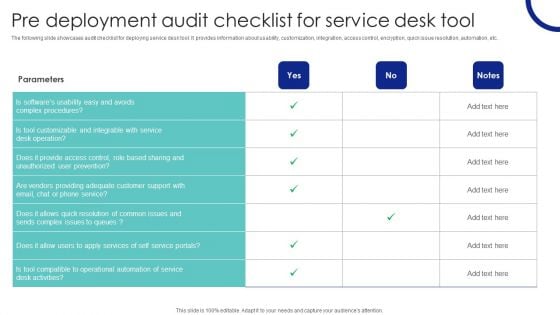
Pre Deployment Audit Checklist For Service Desk Tool Ppt PowerPoint Presentation Diagram PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. Welcome to our selection of the Pre Deployment Audit Checklist For Service Desk Tool Ppt PowerPoint Presentation Diagram PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Pre Deployment Audit Checklist For Service Desk Tool Sample PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. Welcome to our selection of the Pre Deployment Audit Checklist For Service Desk Tool Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
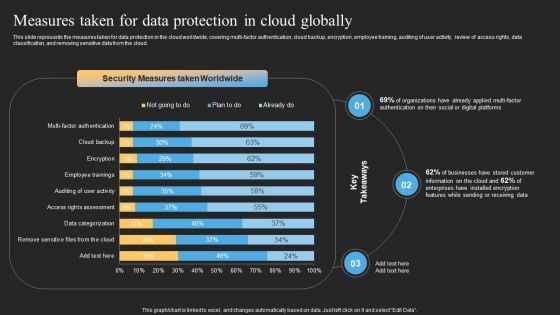
Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF
This slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud. This Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Datafy Measures Taken For Data Protection In Cloud Globally Portrait PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today
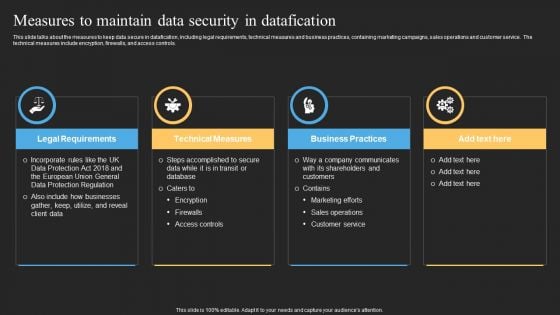
Datafy Measures To Maintain Data Security In Datafication Diagrams PDF
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Welcome to our selection of the Datafy Measures To Maintain Data Security In Datafication Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Do you have to make sure that everyone on your team knows about any specific topic. I yes, then you should give Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
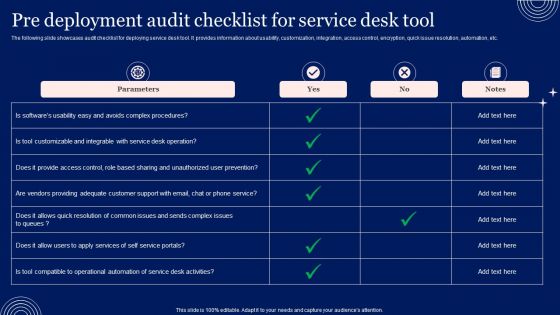
Implementing Advanced Service Help Desk Administration Program Pre Deployment Audit Checklist For Service Desk Tool Inspiration PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc.This Implementing Advanced Service Help Desk Administration Program Pre Deployment Audit Checklist For Service Desk Tool Inspiration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. TheImplementing Advanced Service Help Desk Administration Program Pre Deployment Audit Checklist For Service Desk Tool Inspiration PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today
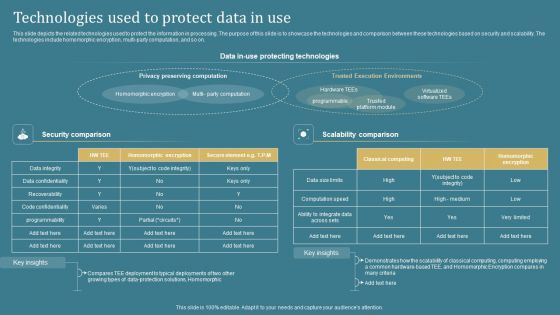
Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing System Technology Technologies Used To Protect Data In Use Inspiration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
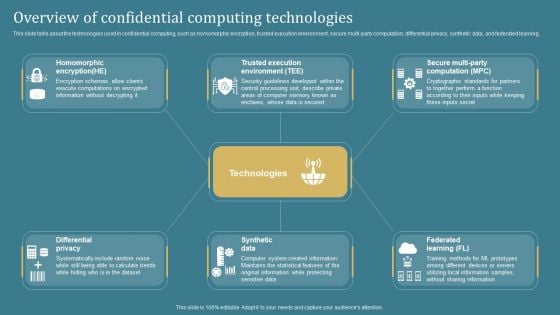
Overview Of Confidential Computing Confidential Computing System Technology Portrait PDF
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Welcome to our selection of the Overview Of Confidential Computing Confidential Computing System Technology Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
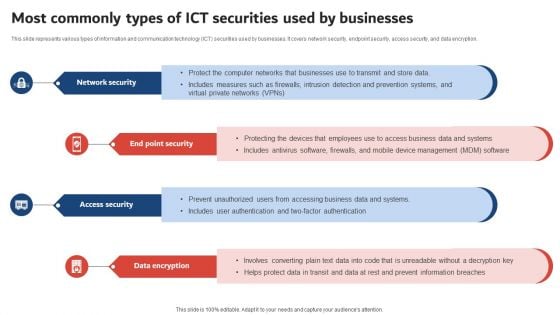
Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF
This slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Leverage Strong And Complex Password Management Ppt PowerPoint Presentation File Icon PDF
The following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi-factor authentication, conducting test etc. Do you know about Slidesgeeks Leverage Strong And Complex Password Management Ppt PowerPoint Presentation File Icon PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Increasing Consumer Engagement With Database Solutions To Overcome Database Marketing Template PDF
The purpose of this slide is to showcase multiple solutions which can be undertaken to overcome database marketing challenges. Information covered in this slide is related to updating customer data, using encryption, customer segmentation, etc. Slidegeeks is here to make your presentations a breeze with Increasing Consumer Engagement With Database Solutions To Overcome Database Marketing Template PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
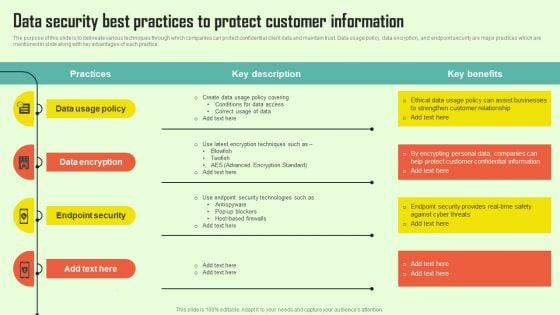
Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF
The purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Create an editable Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Zero Trust Network Access Architectural Models Diagrams PDF
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Are you searching for a Zero Trust Network Access Architectural Models Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Architectural Models Diagrams PDF from Slidegeeks today.
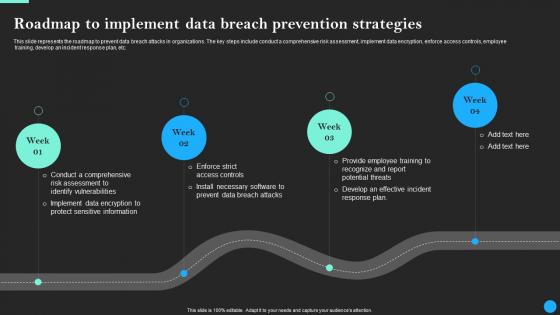
Roadmap To Implement Data Breach Prevention Strategies Rules Pdf
Create an editable Roadmap To Implement Data Breach Prevention Strategies Rules Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Roadmap To Implement Data Breach Prevention Strategies Rules Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the roadmap to prevent data breach attacks in organizations. The key steps include conduct a comprehensive risk assessment, implement data encryption, enforce access controls, employee training, develop an incident response plan, etc.
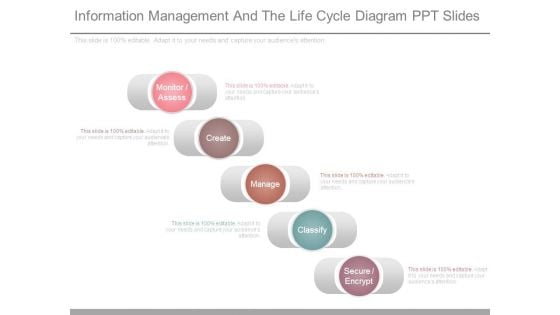
Information Management And The Life Cycle Diagram Ppt Slides
This is a information management and the life cycle diagram ppt slides. This is a five stage process. The stages in this process are monitor assess, create, manage, classify, secure encrypt.
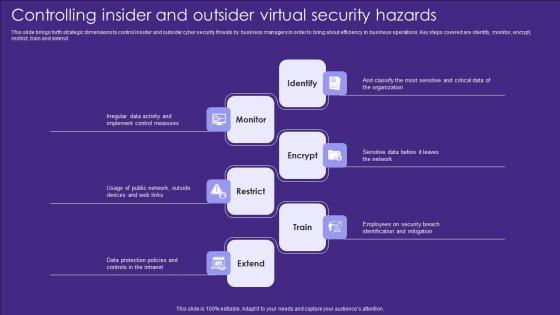
Controlling Insider And Outsider Virtual Security Hazards Designs Pdf
This slide brings forth strategic dimensions to control insider and outsider cyber security threats by business managers in order to bring about efficiency in business operations. Key steps covered are identify, monitor, encrypt, restrict, train and extend Showcasing this set of slides titled Controlling Insider And Outsider Virtual Security Hazards Designs Pdf. The topics addressed in these templates are Identify, Monitor, Encrypt. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide brings forth strategic dimensions to control insider and outsider cyber security threats by business managers in order to bring about efficiency in business operations. Key steps covered are identify, monitor, encrypt, restrict, train and extend

Deal Symbol Business Cash Credit Card Dollar Transaction Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name deal symbol business cash credit card dollar transaction ppt powerpoint presentation complete deck. The topics discussed in these slides are business cash, credit card, dollar transaction, secured and encrypted. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
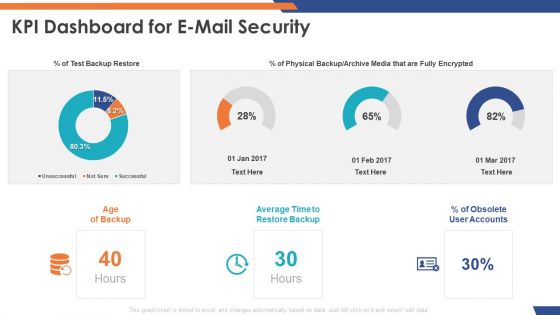
Email Security Market Research Report KPI Dashboard For E Mail Security Graphics PDF
Presenting this set of slides with name email security market research report kpi dashboard for e mail security graphics pdf. The topics discussed in these slides are test backup restore, physical backup or archive media that are fully encrypted, obsolete user accounts, average time to restore backup. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

 Home
Home