Endpoint

ITIL Strategy Service Excellence What Services Do We Offer To Clients Ppt PowerPoint Presentation Pictures Structure PDF
Presenting this set of slides with name itil strategy service excellence what services do we offer to clients ppt powerpoint presentation pictures structure pdf. The topics discussed in these slides are core offerings, server monitoring, network monitoring, backup monitoring, application monitoring, patch management, automated maintenance, performance reporting, endpoint security esm. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
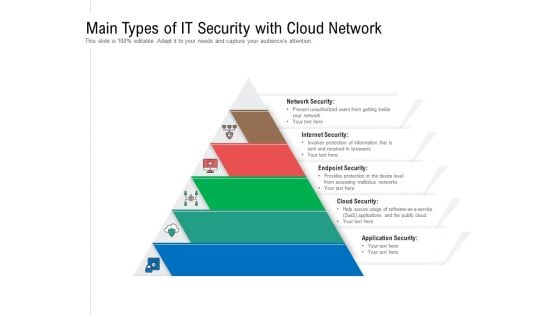
Main Types Of IT Security With Cloud Network Ppt PowerPoint Presentation Gallery Design Ideas PDF
Persuade your audience using this main types of it security with cloud network ppt powerpoint presentation gallery design ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including network security, internet security, endpoint security, cloud security, application security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
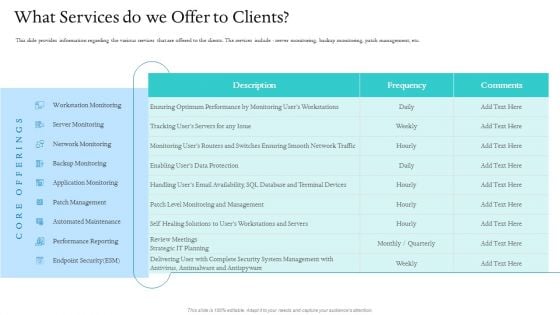
Information Technology Facilities Governance What Services Do We Offer To Clients Ppt Infographics Inspiration PDF
This slide provides information regarding the various services that are offered to the clients. The services include - server monitoring, backup monitoring, patch management, etc. Deliver an awe inspiring pitch with this creative information technology facilities governance what services do we offer to clients ppt infographics inspiration pdf bundle. Topics like performance reporting, endpoint security, network monitoring, server monitoring, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Technology Facility Maintenance And Provider What Services Do We Offer To Clients Inspiration PDF
This slide provides information regarding the various services that are offered to the clients. The services include - server monitoring, backup monitoring, patch management, etc. Deliver an awe inspiring pitch with this creative technology facility maintenance and provider what services do we offer to clients inspiration pdf bundle. Topics like server monitoring, patch management, performance reporting, automated maintenance, endpoint security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
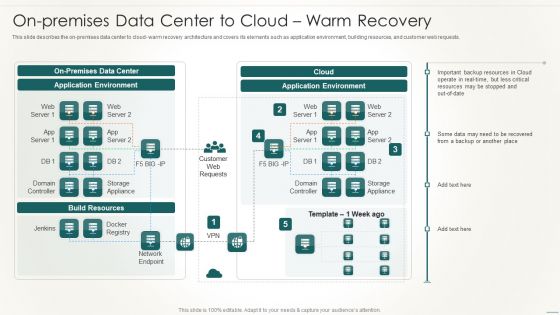
Information Technology Disaster Resilience Plan On-Premises Data Center To Cloudwarm Recovery Ideas PDF
This slide describes the on-premises data center to cloud- warm recovery architecture and covers its elements such as application environment, building resources, and customer web requests.Deliver an awe inspiring pitch with this creative Information Technology Disaster Resilience Plan On-Premises Data Center To Cloudwarm Recovery Ideas PDF bundle. Topics like Domain Controller, Storage Appliance, Network Endpoint can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

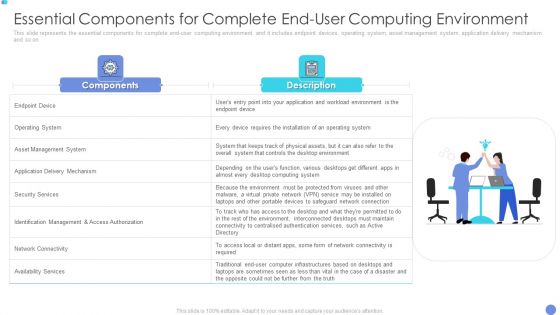
Computer Virtualization Essential Components For Complete End User Computing Environment Demonstration PDF
This slide represents the essential components for complete end-user computing environment and it includes endpoint devices, operating system, asset management system, application delivery mechanism and so on.Deliver and pitch your topic in the best possible manner with this Computer Virtualization Essential Components For Complete End User Computing Environment Demonstration PDF. Use them to share invaluable insights on Management System, Operating System, Access Authorization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
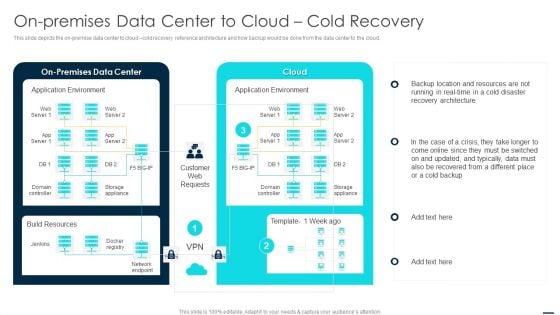
On Premises Data Center To Cloud Cold Recovery Ideas PDF
This slide depicts the on premise data center to cloud cold recovery reference architecture and how backup would be done from the data center to the cloud. Deliver an awe inspiring pitch with this creative On Premises Data Center To Cloud Cold Recovery Ideas PDF bundle. Topics like Application Environment, Build Resources, Network Endpoint can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

On Premises Data Center To Cloud Warm Recovery Background PDF
This slide describes the on premises data center to cloud warm recovery architecture and covers its elements such as application environment, building resources, and customer web requests. Deliver and pitch your topic in the best possible manner with this On Premises Data Center To Cloud Warm Recovery Background PDF. Use them to share invaluable insights on Application Environment, Build Resources, Network Endpoint and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
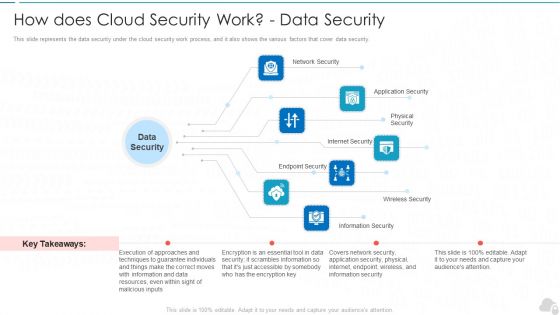
How Does Cloud Security Work Data Security Cloud Computing Security IT Ppt Ideas Slide Download PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Presenting how does cloud security work data security cloud computing security it ppt ideas slide download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network security, internet security, endpoint security, wireless security, physical security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Customer Mesh Computing IT Essential Components For Complete End User Computing Environment Guidelines PDF
This slide represents the essential components for complete end user computing environment and it includes endpoint devices, operating system, asset management system, application delivery mechanism and so on. Deliver an awe inspiring pitch with this creative customer mesh computing it essential components for complete end user computing environment guidelines pdf bundle. Topics like essential components for complete end user computing environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cloud Information Security How Does Cloud Security Work Data Security Ppt Icon Layout PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Presenting Cloud Information Security How Does Cloud Security Work Data Security Ppt Icon Layout PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Information Security, Wireless Security, Endpoint Security, Internet Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Comparative Assessment Of Data Loss Prevention Software Structure PDF
Following slide illustrates comparison of various data loss prevention softwares used in the retail industry. The comparison is drawn on the features such as detecting suspicious activity, endpoint protection platform, enforced encryption etc. Showcasing this set of slides titled Comparative Assessment Of Data Loss Prevention Software Structure PDF. The topics addressed in these templates are System Audit, Pricing, Enforced Encryption. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
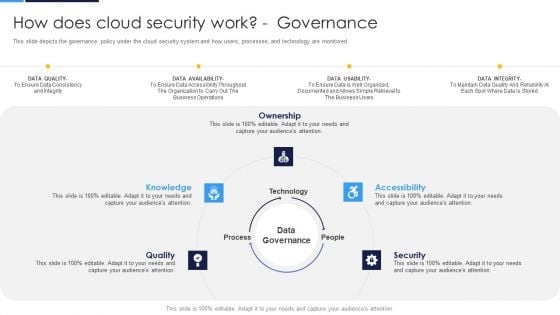
Cloud Security Assessment How Does Cloud Security Work Governance Sample PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security.This is a Cloud Security Assessment How Does Cloud Security Work Governance Sample PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Physical Security, Internet Security, Endpoint Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

VID Essential Components For Complete End-User Computing Environment Brochure PDF
This slide represents the essential components for complete end-user computing environment and it includes endpoint devices, operating system, asset management system, application delivery mechanism and so on.Presenting VID Essential Components For Complete End-User Computing Environment Brochure PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Asset Management, Delivery Mechanism, Identification Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

End User Computing Essential Components For Complete End-User Computing Environment Clipart PDF
This slide represents the essential components for complete end-user computing environment and it includes endpoint devices, operating system, asset management system, application delivery mechanism and so on.Presenting End User Computing Essential Components For Complete End-User Computing Environment Clipart PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Asset Management, Delivery Mechanism, Identification Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
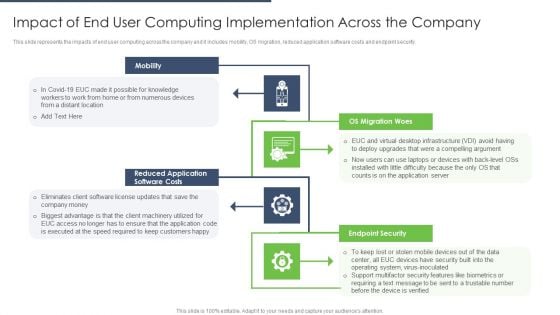
End User Computing Impact Of End User Computing Implementation Across The Company Download PDF
This slide represents the impacts of end user computing across the company and it includes mobility, OS migration, reduced application software costs and endpoint security.This is a End User Computing Impact Of End User Computing Implementation Across The Company Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Distant Location, Reduced Application, Eliminates Client. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
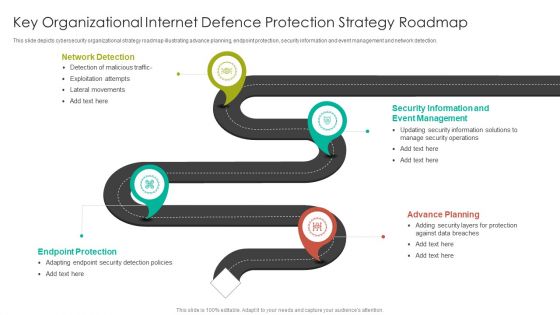
Key Organizational Internet Defence Protection Strategy Roadmap Summary PDF
This slide depicts cybersecurity organizational strategy roadmap illustrating advance planning, endpoint protection, security information and event management and network detection.Persuade your audience using this Key Organizational Internet Defence Protection Strategy Roadmap Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Detection, Event Management, Security Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
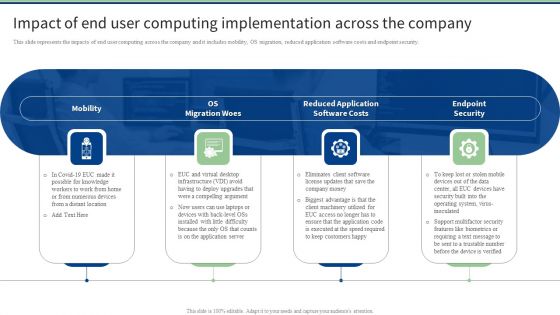
Impact Of End User Computing Implementation Across The Company Infographics PDF
This slide represents the impacts of end user computing across the company and it includes mobility, OS migration, reduced application software costs and endpoint security. Make sure to capture your audiences attention in your business displays with our gratis customizable Impact Of End User Computing Implementation Across The Company Infographics PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
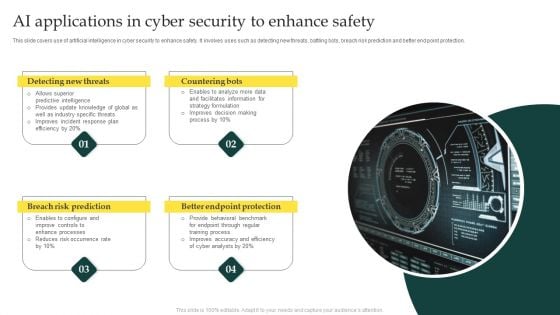
AI Applications In Cyber Security To Enhance Safety Elements PDF
This slide covers use of artificial intelligence in cyber security to enhance safety. It involves uses such as detecting new threats, battling bots, breach risk prediction and better end point protection.Persuade your audience using this AI Applications In Cyber Security To Enhance Safety Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Prediction, Endpoint Protection, Countering Bots. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Explainable Machine Learning Capabilities Of Explainable Artificial Intelligence Download PDF
This slide represents the capabilities of explainable AI, such as monitoring and explaining models, tracking and visualizing model insights, and configuring endpoint monitors. Create an editable Explainable Machine Learning Capabilities Of Explainable Artificial Intelligence Download PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Explainable Machine Learning Capabilities Of Explainable Artificial Intelligence Download PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
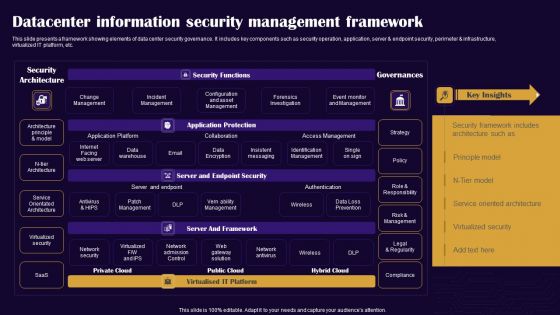
Datacenter Information Security Management Framework Professional PDF
This slide presents a framework showing elements of data center security governance. It includes key components such as security operation, application, server and endpoint security, perimeter and infrastructure, virtualized IT platform, etc. Pitch your topic with ease and precision using this Datacenter Information Security Management Framework Professional PDF. This layout presents information on Security Architecture, Security Functions, Governances. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Essential Components For Complete End User Computing Environment Rules PDF
This slide represents the essential components for complete end user computing environment and it includes endpoint devices, operating system, asset management system, application delivery mechanism and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Essential Components For Complete End User Computing Environment Rules PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
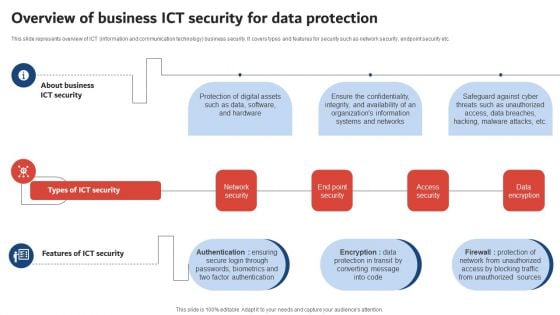
Execution Of ICT Strategic Plan Overview Of Business ICT Security For Data Protection Sample PDF
This slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Welcome to our selection of the Execution Of ICT Strategic Plan Overview Of Business ICT Security For Data Protection Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
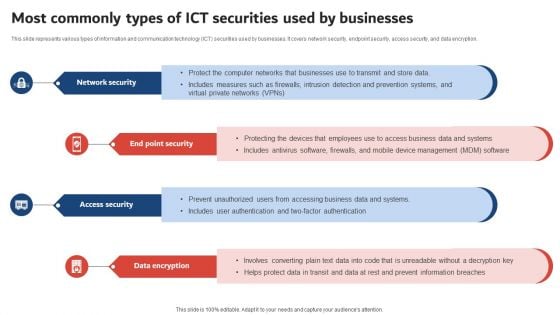
Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF
This slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
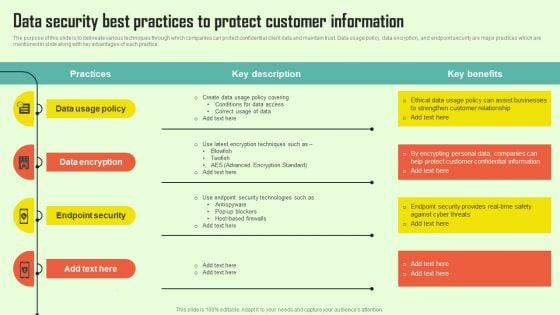
Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF
The purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Create an editable Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
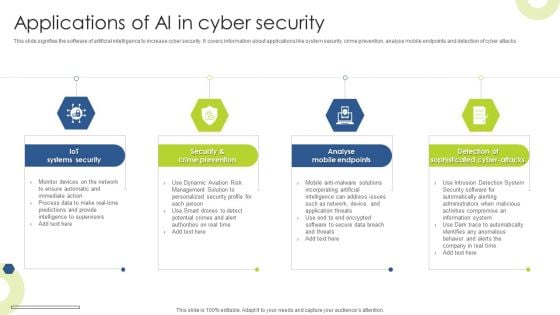
Applications Of AI In Cyber Security Infographics PDF
This slide signifies the software of artificial intelligence to increase cyber security. It covers information about applications like system security, crime prevention, analyse mobile endpoints and detection of cyber attacks Presenting Applications Of AI In Cyber Security Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Iot Systems Security, Crime Prevention, Analyse Mobile Endpoints. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
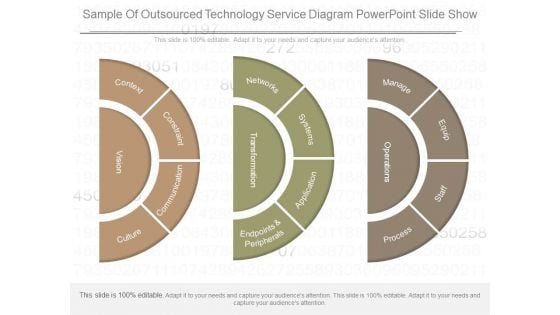
Sample Of Outsourced Technology Service Diagram Powerpoint Slide Show
This is a sample of outsourced technology service diagram powerpoint slide show. This is a three stage process. The stages in this process are vision, context, constraint, communication, culture, transformation, networks, systems, application, endpoints and peripherals, operations, manage, equip, staff, process.
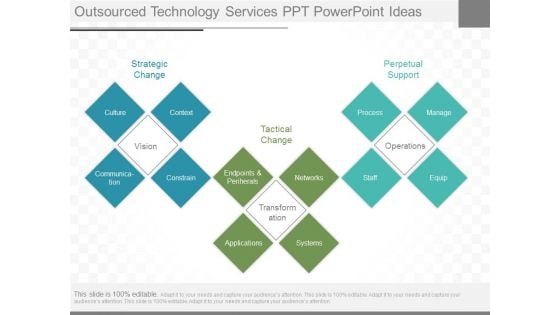
Outsourced Technology Services Ppt Powerpoint Ideas
This is a outsourced technology services ppt powerpoint ideas. This is a three stage process. The stages in this process are strategic change, context, culture, vision, constrain, communication, tactical change, endpoints and periherals, networks, transformation, applications, systems, perpetual support, process, manage, operations, staff, equip.

Threat Security Before And After Artificial Intelligence Formats PDF
This slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Showcasing this set of slides titled Threat Security Before And After Artificial Intelligence Formats PDF. The topics addressed in these templates are Malware, Distributed Denial Service, Social Engineering. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
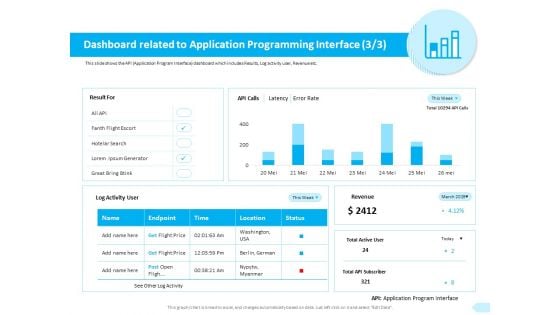
API Integration Software Development Dashboard Related To Application Sample PDF
Presenting this set of slides with name api integration software development dashboard related to application sample pdf. The topics discussed in these slides are name, endpoint, time, location, status. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
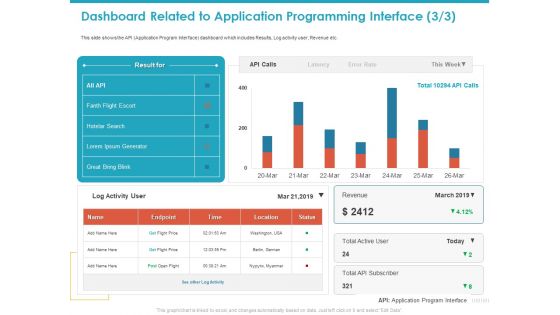
Dashboard Related To Application Programming Interface Status Slides PDF
This slide shows the API Application Program Interface dashboard which includes Results, Log activity user, Revenue etc. Deliver an awe-inspiring pitch with this creative dashboard related to application programming interface status slides pdf bundle. Topics like revenue, location, status, endpoint, time can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
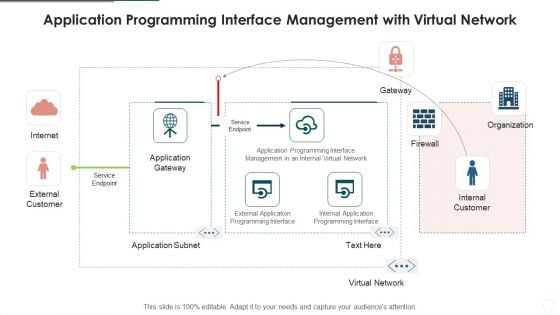
Application Programming Interface Management With Virtual Network Microsoft PDF
Showcasing this set of slides titled application programming interface management with virtual network microsoft pdf. The topics addressed in these templates are application gateway, service endpoint, external customer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Machine To Machine Communication Iot Best Practices Template PDF
The slide highlights the best IoT practices which companies should follow.Presenting machine to machine communication iot best practices template pdf. to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like understand your endpoints, consider patching and remediation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
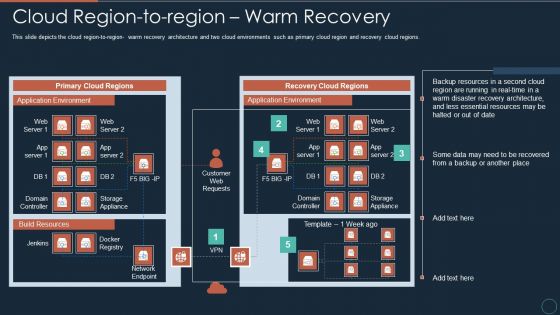
Implementing DRP IT Cloud Region To Region Warm Recovery Ppt PowerPoint Presentation Layouts Backgrounds PDF
This slide depicts the cloud region to region warm recovery architecture and two cloud environments such as primary cloud region and recovery cloud regions.Deliver and pitch your topic in the best possible manner with this implementing drp it cloud region to region warm recovery ppt powerpoint presentation layouts backgrounds pdf Use them to share invaluable insights on network endpoint, docker registry, domain controller and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
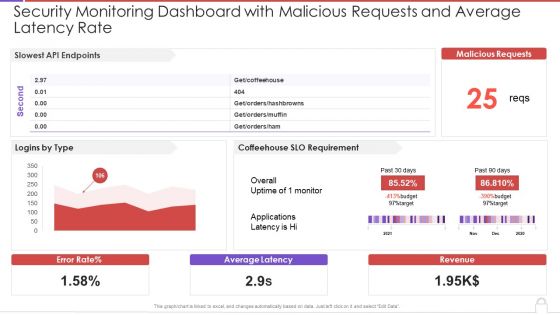
Security Monitoring Dashboard With Malicious Requests And Average Latency Rate Topics PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative security monitoring dashboard with malicious requests and average latency rate topics pdf bundle. Topics like slowest api endpoints, malicious requests, coffeehouse slo can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Machine To Machine Communication Outline Iot Best Practices Ppt Inspiration Model PDF
The slide highlights the best IoT practices which companies should follow. This is a machine to machine communication outline iot best practices ppt inspiration model pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like understand your endpoints, track and manage your devices, identify what it security cannot address, consider patching and remediation, use a risk driven strategy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Google Cloud Services Management Tools Google Cloud Computing System Infographics PDF
This slide represents the management tools service provided by Google cloud, and it includes tools such as stackdrive, monitoring, logging, error reporting, trace, debugging, and cloud shell.This is a Google Cloud Services Management Tools Google Cloud Computing System Infographics PDF template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Deployment Manager, Cloud Endpoints, Stackdriver. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
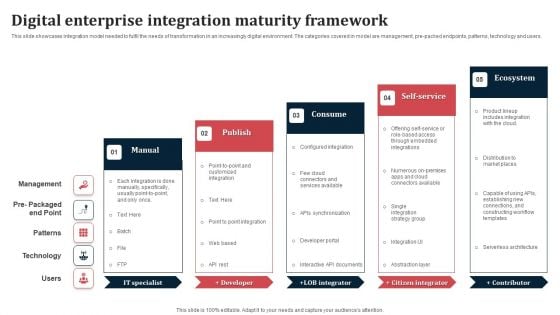
Digital Enterprise Integration Maturity Framework Ppt Infographic Template Visuals PDF
This slide showcases integration model needed to fulfil the needs of transformation in an increasingly digital environment. The categories covered in model are management, pre-packed endpoints, patterns, technology and users. Persuade your audience using this Digital Enterprise Integration Maturity Framework Ppt Infographic Template Visuals PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Manual, Publish, Consume, Ecosystem. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
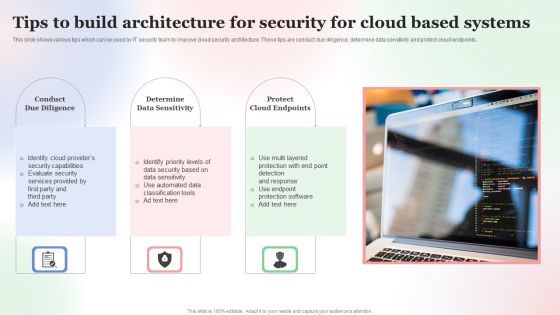
Tips To Build Architecture For Security For Cloud Based Systems Designs PDF
This slide shows various tips which can be used by IT security team to improve cloud security architecture. These tips are conduct due diligence, determine data sensitivity and protect cloud endpoints. Persuade your audience using this Tips To Build Architecture For Security For Cloud Based Systems Designs PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Tips To Build, Architecture For Security, Cloud Based Systems. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
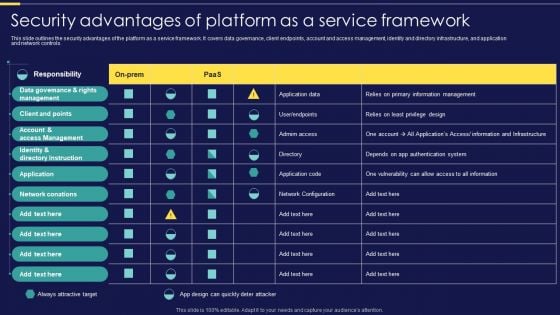
Integration Of Paas Security Advantages Of Platform As A Service Framework Elements PDF
This slide outlines the security advantages of the platform as a service framework. It covers data governance, client endpoints, account and access management, identity and directory infrastructure, and application and network controls. Make sure to capture your audiences attention in your business displays with our gratis customizable Integration Of Paas Security Advantages Of Platform As A Service Framework Elements PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
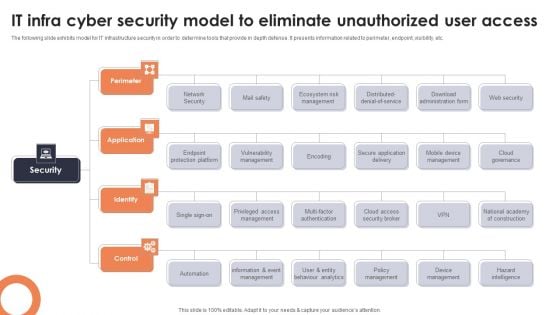
IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF
The following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defense. It presents information related to perimeter, endpoint, visibility, etc. Presenting IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Perimeter, Application, Identify. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
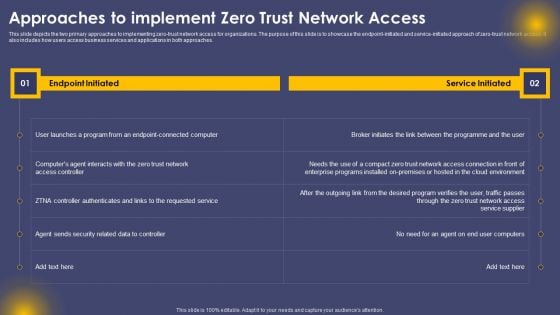
Approaches To Implement Zero Trust Network Access Ppt Layouts Shapes PDF
This slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Approaches To Implement Zero Trust Network Access Ppt Layouts Shapes PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Approaches To Implement Zero Trust Network Access Ppt Layouts Shapes PDF.
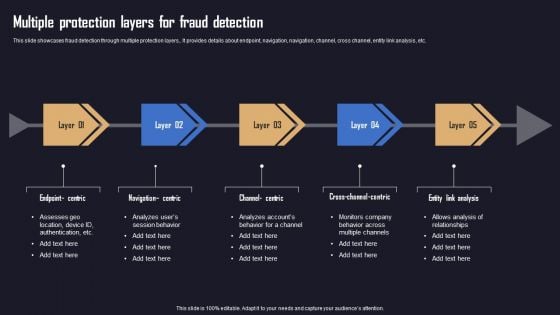
Ensuring Organizational Safety Using AML Transaction Multiple Protection Layers Professional PDF
This slide showcases fraud detection through multiple protection layers,. It provides details about endpoint, navigation, navigation, channel, cross channel, entity link analysis, etc. Explore a selection of the finest Ensuring Organizational Safety Using AML Transaction Multiple Protection Layers Professional PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Ensuring Organizational Safety Using AML Transaction Multiple Protection Layers Professional PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

 Home
Home