Ethical Compliance
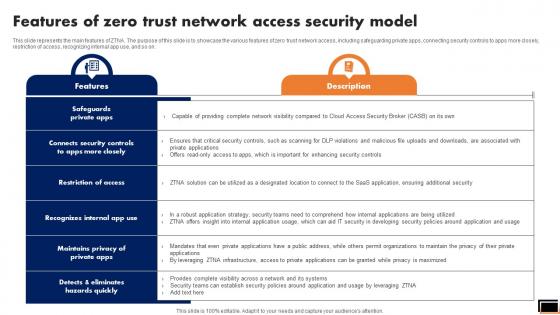
Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
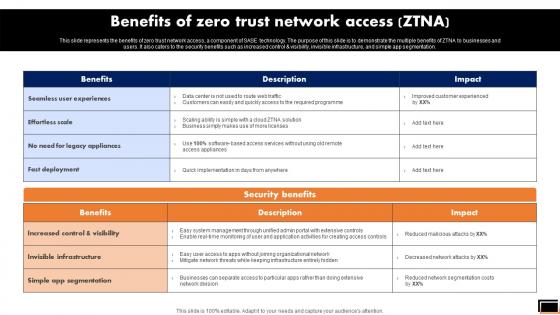
Benefits Of Zero Trust Network Access Ztna Software Defined Perimeter SDP
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Zero Trust Network Access Ztna Software Defined Perimeter SDP for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.

A51 Zero Trust Network Access Implementation Challenges
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on Want to ace your presentation in front of a live audience Our A51 Zero Trust Network Access Implementation Challenges can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on
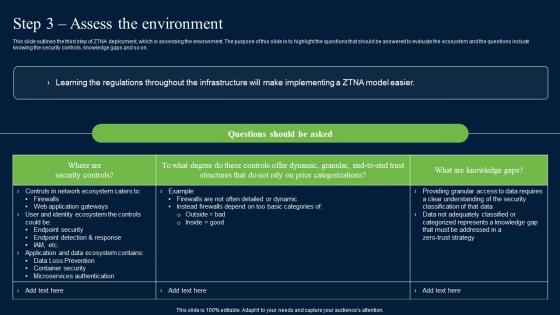
Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Want to ace your presentation in front of a live audience Our Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.

Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.

Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf
This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. Find highly impressive Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access.
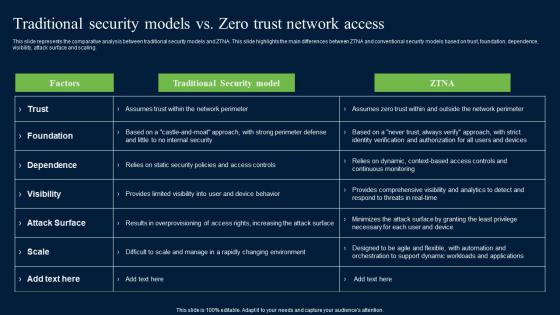
Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling.
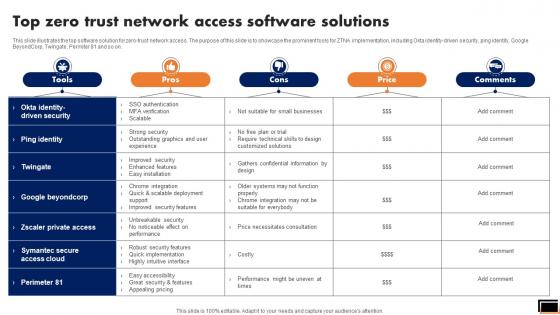
Top Zero Trust Network Access Software Solutions Software Defined Perimeter SDP
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Top Zero Trust Network Access Software Solutions Software Defined Perimeter SDP and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on.

Zero Trust Network Access Implementation Challenges Mockup Pdf
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Get a simple yet stunning designed Zero Trust Network Access Implementation Challenges Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Network Access Implementation Challenges Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.
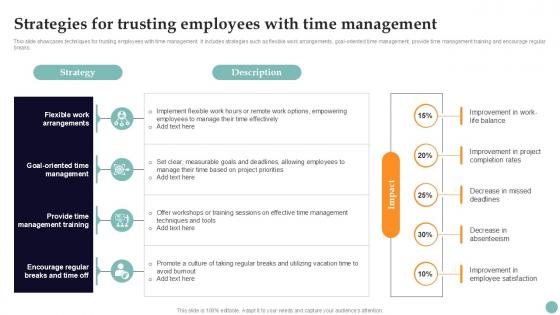
Strategies For Trusting Employees Improving Employee Performance PPT Example Strategy SS V
This slide showcases techniques for trusting employees with time management. It includes strategies such as flexible work arrangements, goal-oriented time management, provide time management training and encourage regular breaks. Take your projects to the next level with our ultimate collection of Strategies For Trusting Employees Improving Employee Performance PPT Example Strategy SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide showcases techniques for trusting employees with time management. It includes strategies such as flexible work arrangements, goal-oriented time management, provide time management training and encourage regular breaks.
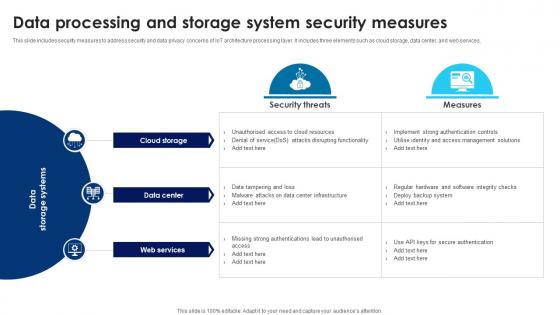
Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V
This slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services.

On Ramp Option 3 The Network Zero Trust Network Access
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than On Ramp Option 3 The Network Zero Trust Network Access. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab On Ramp Option 3 The Network Zero Trust Network Access today and make your presentation stand out from the rest This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.

Zero Trust Model On Ramp Option 3 The Network
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Presenting this PowerPoint presentation, titled Zero Trust Model On Ramp Option 3 The Network, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Model On Ramp Option 3 The Network. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Model On Ramp Option 3 The Network that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.

Zero Trust Network Access Implementation Challenges Software Defined Perimeter SDP
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Network Access Implementation Challenges Software Defined Perimeter SDP from Slidegeeks and deliver a wonderful presentation. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.

Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and acce ss management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and acce ss management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.

Building Trust With IoT Security Concerns And Solutions For Interconnected Devices IoT SS V
This slide exhibits security solution to safeguard interconnected devices against security attacks in order to enhance overall productivity. It includes devices such as smart cameras, RFID tags, Smart GPS systems, and smart home devices, smart meters. Find highly impressive Building Trust With IoT Security Concerns And Solutions For Interconnected Devices IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Building Trust With IoT Security Concerns And Solutions For Interconnected Devices IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide exhibits security solution to safeguard interconnected devices against security attacks in order to enhance overall productivity. It includes devices such as smart cameras, RFID tags, Smart GPS systems, and smart home devices, smart meters.
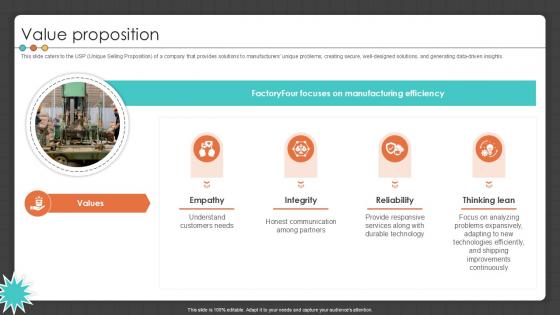
Value Proposition Manufacturing Control Software Company Investor PPT Template
This slide caters to the USP Unique Selling Proposition of a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights. Explore a selection of the finest Value Proposition Manufacturing Control Software Company Investor PPT Template here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Value Proposition Manufacturing Control Software Company Investor PPT Template to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide caters to the USP Unique Selling Proposition of a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights.

Agile Beliefs And Fundamentals Agile Marketing Onion Graphics PDF
This slide provides the glimpse about the agile marketing onion which focuses on mindset, values, principles, practices, tools and processes, etc.Deliver and pitch your topic in the best possible manner with this agile beliefs and fundamentals agile marketing onion graphics pdf Use them to share invaluable insights on focuses on learning organization, requires structural and cultural changes, control culture and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
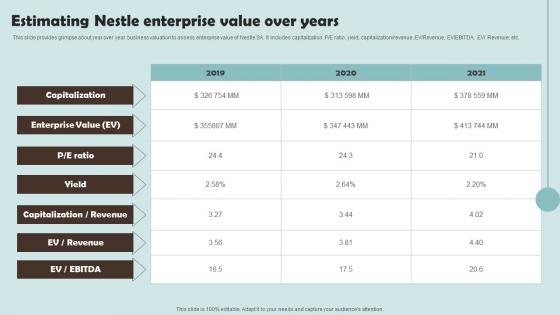
Estimating Nestle Enterprise Value Over Years Outline Of Nestle Management Template Pdf
This slide provides glimpse about year over year business valuation to assess enterprise value of Nestle SA. It includes capitalization, PorE ratio, yield, capitalizationorrevenue, EVorRevenue, EVorEBITDA, EVor Revenue, etc.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Estimating Nestle Enterprise Value Over Years Outline Of Nestle Management Template Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Estimating Nestle Enterprise Value Over Years Outline Of Nestle Management Template Pdf today and make your presentation stand out from the rest. This slide provides glimpse about year over year business valuation to assess enterprise value of Nestle SA. It includes capitalization, PorE ratio, yield, capitalizationorrevenue, EVorRevenue, EVorEBITDA, EVor Revenue, etc.

Leadership Competencies With Core Values And Beliefs Ppt PowerPoint Presentation Professional Graphics Tutorials
Presenting this set of slides with name leadership competencies with core values and beliefs ppt powerpoint presentation professional graphics tutorials. The topics discussed in these slides are effective leadership, leadership competencies, team leader. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
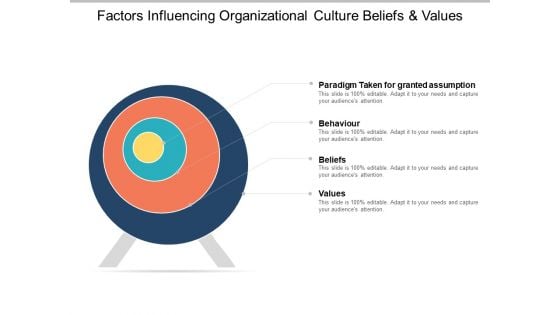
Factors Influencing Organizational Culture Beliefs And Values Ppt PowerPoint Presentation Portfolio Model
This is a factors influencing organizational culture beliefs and values ppt powerpoint presentation portfolio model. This is a four stage process. The stages in this process are company environment, culture web, companys culture.

Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.

Building Trust With IoT Security Automated Patch Management To Increase Overall Productivity IoT SS V
This slide includes an automated patch management process that ensures patch availability on devices in accordance with deployment policies. It includes steps such as scan for missing patches, collect patches from vendors, deploy patches, and report results. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Building Trust With IoT Security Automated Patch Management To Increase Overall Productivity IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide includes an automated patch management process that ensures patch availability on devices in accordance with deployment policies. It includes steps such as scan for missing patches, collect patches from vendors, deploy patches, and report results.
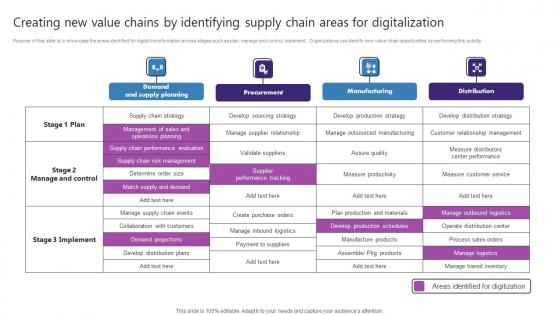
Creating New Value Chains By Identifying Supply Chain Strategic Plan For Enhancing Pictures Pdf
Purpose of this slide is to showcase the areas identified for digital transformation across stages such as plan, manage and control, implement. Organizations can identify new value chain opportunities by performing this activity. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Creating New Value Chains By Identifying Supply Chain Strategic Plan For Enhancing Pictures Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Creating New Value Chains By Identifying Supply Chain Strategic Plan For Enhancing Pictures Pdf today and make your presentation stand out from the rest. Purpose of this slide is to showcase the areas identified for digital transformation across stages such as plan, manage and control, implement. Organizations can identify new value chain opportunities by performing this activity.
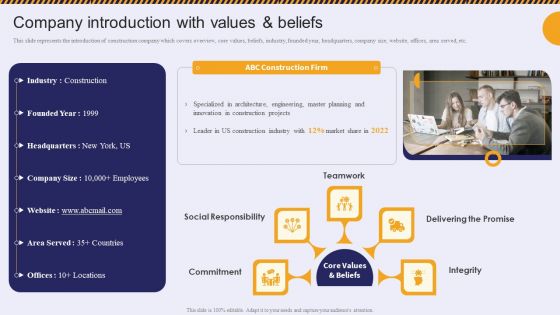
Company Introduction With Values And Beliefs Residential And Commercial Building Information PDF
This slide represents the introduction of construction company which covers overview, core values, beliefs, industry, founded year, headquarters, company size, website, offices, area served, etc.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Company Introduction With Values And Beliefs Residential And Commercial Building Information PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Client Segmentation Analysis Segmentation Beliefs Ppt Portfolio Model PDF
Presenting this set of slides with name client segmentation analysis segmentation beliefs ppt portfolio model pdf. The topics discussed in these slides are geographic, economic, political legal, cultural. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
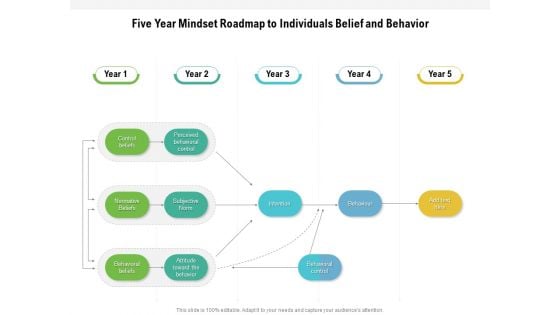
Five Year Mindset Roadmap To Individuals Belief And Behavior Microsoft
Presenting the five year mindset roadmap to individuals belief and behavior microsoft. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
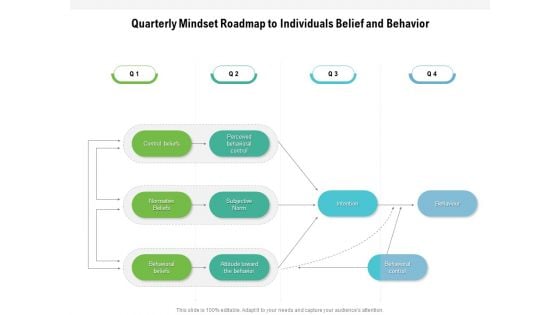
Quarterly Mindset Roadmap To Individuals Belief And Behavior Download
Presenting the quarterly mindset roadmap to individuals belief and behavior download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
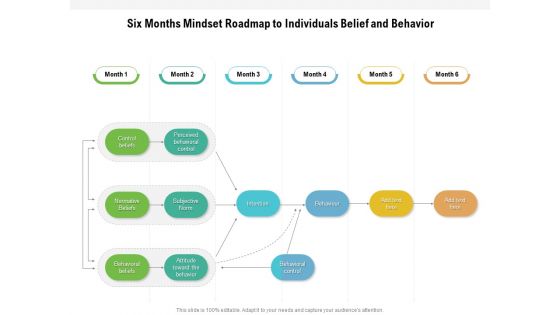
Six Months Mindset Roadmap To Individuals Belief And Behavior Demonstration
Presenting the six months mindset roadmap to individuals belief and behavior demonstration. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
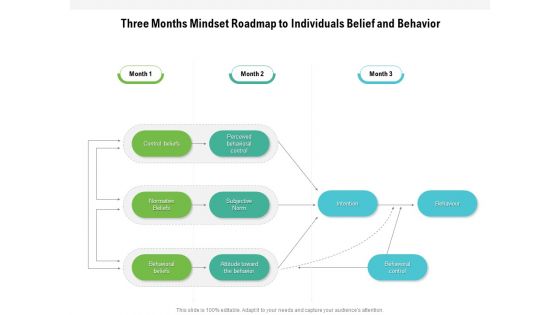
Three Months Mindset Roadmap To Individuals Belief And Behavior Designs
Presenting the three months mindset roadmap to individuals belief and behavior designs. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
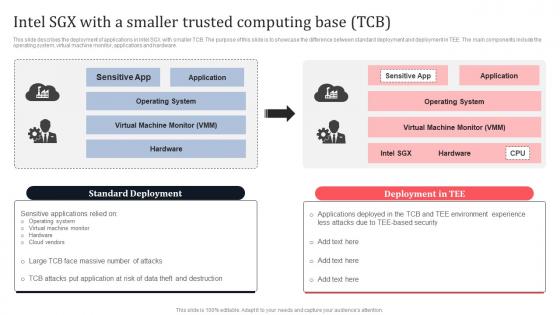
Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf
This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Take your projects to the next level with our ultimate collection of Intel SGX With A Smaller Trusted Computing Base TCB Secure Multi Party Sample Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware.
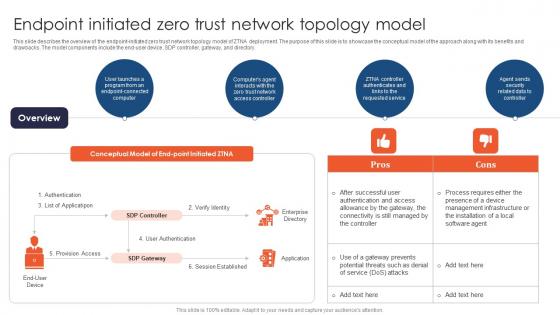
Endpoint Initiated Zero Trust Network Topology Model Zero Trust Network Access
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Endpoint Initiated Zero Trust Network Topology Model Zero Trust Network Access will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.
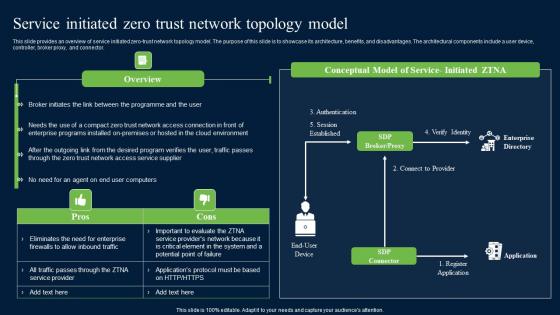
Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Find a pre-designed and impeccable Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.
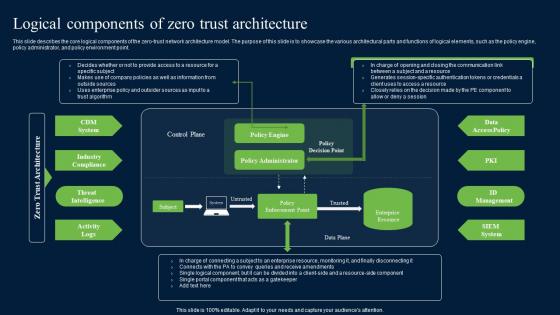
Logical Components Of Zero Trust Architecture Zero Trust Network Security Pictures Pdf
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. This Logical Components Of Zero Trust Architecture Zero Trust Network Security Pictures Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Logical Components Of Zero Trust Architecture Zero Trust Network Security Pictures Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point.
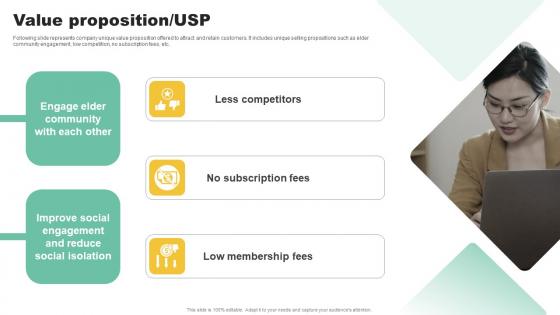
Value Proposition USP Social Community Management Solution Funding Pitch Presentation Information Pdf
Following slide represents company unique value proposition offered to attract and retain customers. It includes unique selling propositions such as elder community engagement, low competition, no subscription fees, etc. Find highly impressive Value Proposition USP Social Community Management Solution Funding Pitch Presentation Information Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Value Proposition USP Social Community Management Solution Funding Pitch Presentation Information Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Following slide represents company unique value proposition offered to attract and retain customers. It includes unique selling propositions such as elder community engagement, low competition, no subscription fees, etc.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
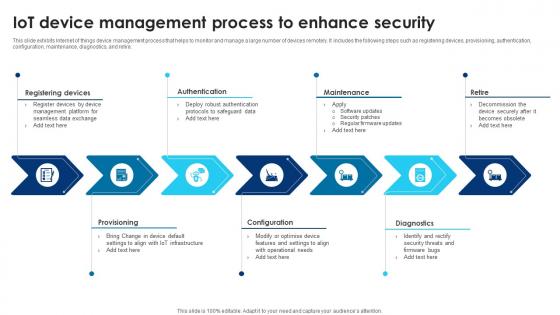
Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V
This slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire. Are you searching for a Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V from Slidegeeks today. This slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire.
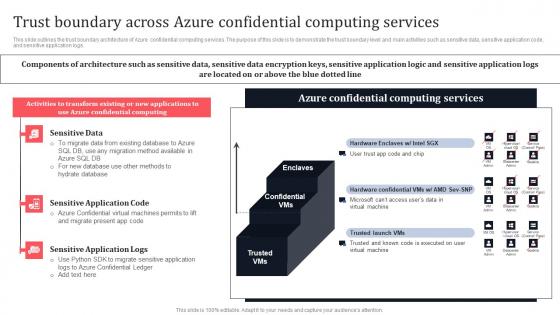
Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf
This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs.

Zero Trust Model Top Tenets Of Zero Trust Network Access Model
Find highly impressive Zero Trust Model Top Tenets Of Zero Trust Network Access Model on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Model Top Tenets Of Zero Trust Network Access Mode for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Our Zero Trust Model Top Tenets Of Zero Trust Network Access Model are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Developing Response Plan Managing Risks And Establishing Trust Through Efficient Infographics Pdf
This slide presents data breach response plan that sets out procedures and clear lines of authority. It includes steps such as identify the breach, contain the breach, assess risk and scope , notify management and stakeholders, notify affected individuals and determine affected individuals, notify law enforcement. Take your projects to the next level with our ultimate collection of Developing Response Plan Managing Risks And Establishing Trust Through Efficient Infographics Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide presents data breach response plan that sets out procedures and clear lines of authority. It includes steps such as identify the breach, contain the breach, assess risk and scope , notify management and stakeholders, notify affected individuals and determine affected individuals, notify law enforcement.

Marketing Performance Measurement Segmentation Beliefs Ppt Inspiration Sample PDF
Presenting this set of slides with name marketing performance measurement segmentation beliefs ppt inspiration sample pdf. This is a four stage process. The stages in this process are geographic, economic, political legal, cultural. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
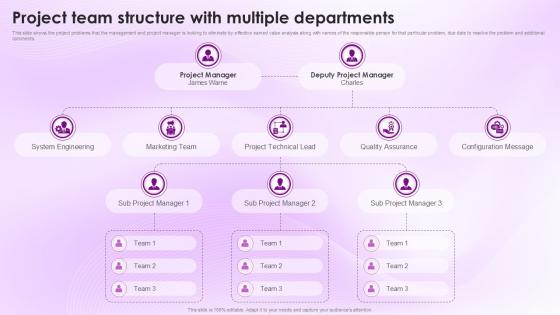
Earned Value Management To Integrate Project Team Structure With Multiple Departments
This Earned Value Management To Integrate Project Team Structure With Multiple Departments from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases project problems that the management and project manager is looking to mitigate by effective earned value analysis along with names of the responsible person for that particular challenge, due date to resolve the problem and additional comments

Cross Faith Religion PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Cross Faith Religion PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Religion PowerPoint Templates because you can come forth with the plans you have so carefully laid out. Download our Church PowerPoint Templates because if making a mark is your obsession, then let others get Obsessed with you. Download and present our Signs PowerPoint Templates because you can spread the fruits of your efforts and elaborate your ideas on the prevention, diagnosis, control and cure of prevalent diseases. Present our Shapes PowerPoint Templates because with the help of our Slides you can Illustrate the means to prevent or control them using our imaginative templates. Present our People PowerPoint Templates because you should Emphasise the process of your business or corporate growth.Use these PowerPoint slides for presentations relating to Cross faith, religion, signs, church, shapes, people. The prominent colors used in the PowerPoint template are Yellow, Orange, Tan. Customers tell us our Cross Faith Religion PowerPoint Templates PPT Backgrounds For Slides 1212 are Spiffy. Presenters tell us our PowerPoint templates and PPT Slides are Endearing. Presenters tell us our Cross Faith Religion PowerPoint Templates PPT Backgrounds For Slides 1212 will make the presenter look like a pro even if they are not computer savvy. The feedback we get is that our people PowerPoint templates and PPT Slides are Dynamic. Use our Cross Faith Religion PowerPoint Templates PPT Backgrounds For Slides 1212 are Nostalgic. You can be sure our shapes PowerPoint templates and PPT Slides are Liberated. Adopt adventure with our Cross Faith Religion PowerPoint Templates Ppt Backgrounds For Slides 1212. Discover new avenues for your thoughts.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Key Values Embedded In Organization Culture Of Nestle Outline Of Nestle Management Guidelines Pdf
This slide provides glimpse about organization cultural values of Nestle SA to understand shared beliefs, attitudes and practices that defines a company and shape its behavior. It includes values such as respect for individuals, emphasis on innovation, etc.If you are looking for a format to display your unique thoughts, then the professionally designed Key Values Embedded In Organization Culture Of Nestle Outline Of Nestle Management Guidelines Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Values Embedded In Organization Culture Of Nestle Outline Of Nestle Management Guidelines Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides glimpse about organization cultural values of Nestle SA to understand shared beliefs, attitudes and practices that defines a company and shape its behavior. It includes values such as respect for individuals, emphasis on innovation, etc.
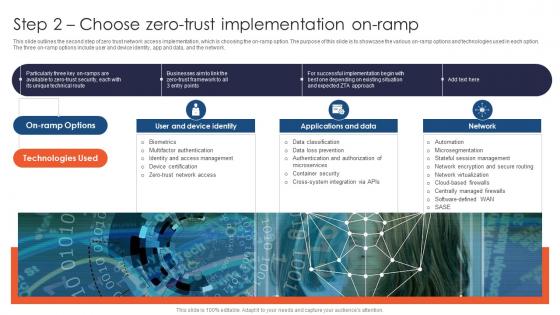
Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Find highly impressive Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.
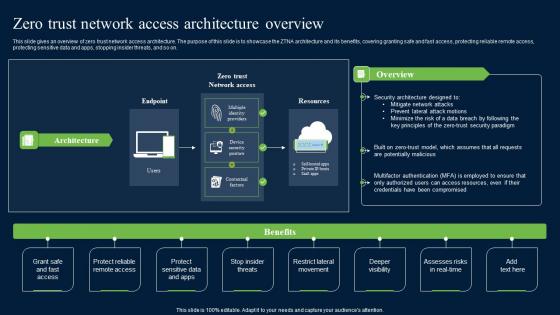
Zero Trust Network Security Access Architecture Overview Graphics Pdf
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Security Access Architecture Overview Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.

Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V
This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery. There are so many reasons you need a Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery.
Trust Monopoly In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Trust Monopoly In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Trust Monopoly that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Trust Monopoly In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
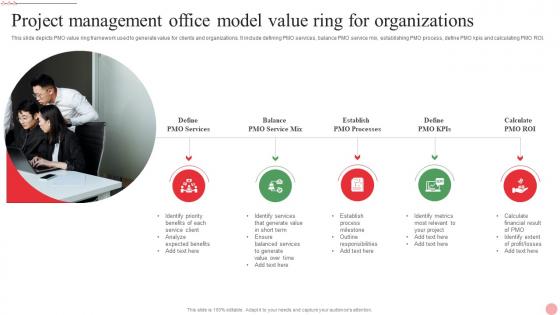
Project Management Office Model Value Ring For Organizations Inspiration Pdf
This slide depicts PMO value ring framework used to generate value for clients and organizations. It include defining PMO services, balance PMO service mix, establishing PMO process, define PMO kpis and calculating PMO ROI. Showcasing this set of slides titled Project Management Office Model Value Ring For Organizations Inspiration Pdf. The topics addressed in these templates are PMO Services, PMO Processes, Establish Process. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide depicts PMO value ring framework used to generate value for clients and organizations. It include defining PMO services, balance PMO service mix, establishing PMO process, define PMO kpis and calculating PMO ROI.
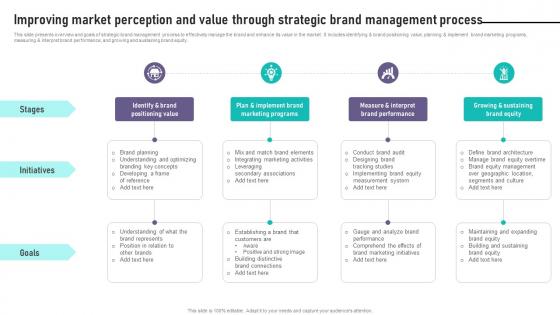
Brand Equity Management Improving Market Perception And Value Through Strategic
This slide presents overview and goals of strategic brand management process to effectively manage the brand and enhance its value in the market. It includes identifying and brand positioning value, planning and implement brand marketing programs, measuring and interpret brand performance, and growing and sustaining brand equity. Create an editable Brand Equity Management Improving Market Perception And Value Through Strategic that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Brand Equity Management Improving Market Perception And Value Through Strategic is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide presents overview and goals of strategic brand management process to effectively manage the brand and enhance its value in the market. It includes identifying and brand positioning value, planning and implement brand marketing programs, measuring and interpret brand performance, and growing and sustaining brand equity.

Value Proposition Content Management Platform Investor Funding Elevator Pitch Deck
This slide exhibits a unique selling proposition strategy that helps to differentiate company products and services and develop a competitive advantage. The company value proposition includes great talent network, streamlined content creation, and ROI tracking. Explore a selection of the finest Value Proposition Content Management Platform Investor Funding Elevator Pitch Deck here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Value Proposition Content Management Platform Investor Funding Elevator Pitch Deck to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide exhibits a unique selling proposition strategy that helps to differentiate company products and services and develop a competitive advantage. The company value proposition includes great talent network, streamlined content creation, and ROI tracking.

Zero Trust Network Access ZTNA Introduction Graphics Pdf
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Find highly impressive Zero Trust Network Access ZTNA Introduction Graphics Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Network Access ZTNA Introduction Graphics Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.
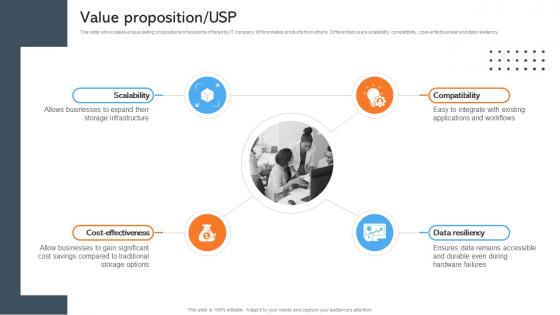
Value Proposition Usp Data Management Company Investor Funding Pitch Deck
This slide showcases unique selling propositions of solutions offered by IT company differentiates products from others. Differentiators are scalability, compatibility, cost-effectiveness and data resiliency. Explore a selection of the finest Value Proposition Usp Data Management Company Investor Funding Pitch Deck here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Value Proposition Usp Data Management Company Investor Funding Pitch Deck to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide showcases unique selling propositions of solutions offered by IT company differentiates products from others. Differentiators are scalability, compatibility, cost-effectiveness and data resiliency.

Most Trusted Supplement Brands In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Most Trusted Supplement Brands In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Most Trusted Supplement Brands that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Most Trusted Supplement Brands In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
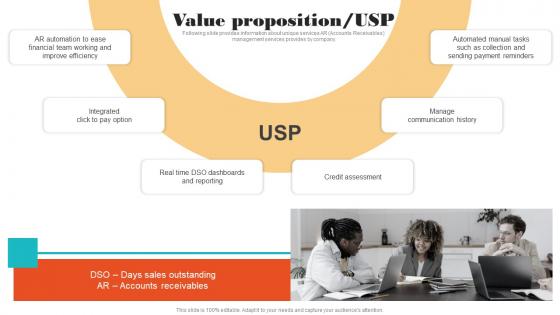
Value Proposition USP Online Financial Management Funding Elevator Microsoft Pdf
Following slide provides information about unique services AR Accounts Receivables management services provides by company. Welcome to our selection of the Value Proposition USP Online Financial Management Funding Elevator Microsoft Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today Following slide provides information about unique services AR Accounts Receivables management services provides by company.

Iot Device Management Market Value Across Major Iot Device Management Diagrams Pdf
The following slide highlights the IoT device management market size in major geographic regions. These regions include America, Europe and Asia pacific region with their current revenue distribution. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Iot Device Management Market Value Across Major Iot Device Management Diagrams Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Iot Device Management Market Value Across Major Iot Device Management Diagrams Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide highlights the IoT device management market size in major geographic regions. These regions include America, Europe and Asia pacific region with their current revenue distribution.
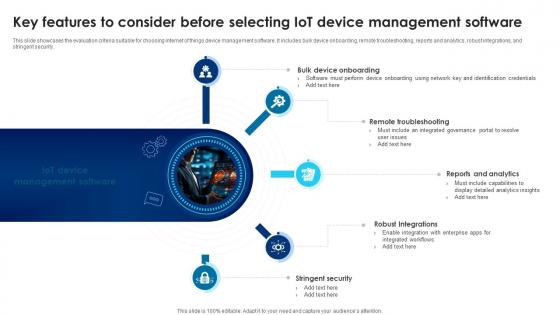
Building Trust With IoT Security Key Features To Consider Before Selecting IoT Device Management IoT SS V
This slide showcases the evaluation criteria suitable for choosing internet of things device management software. It includes bulk device onboarding, remote troubleshooting, reports and analytics, robust integrations, and stringent security. Take your projects to the next level with our ultimate collection of Building Trust With IoT Security Key Features To Consider Before Selecting IoT Device Management IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide showcases the evaluation criteria suitable for choosing internet of things device management software. It includes bulk device onboarding, remote troubleshooting, reports and analytics, robust integrations, and stringent security.
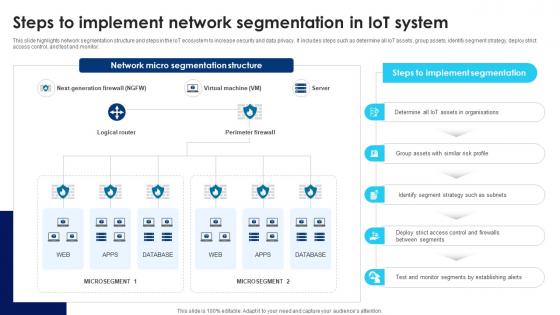
Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V
This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor. Slidegeeks is here to make your presentations a breeze with Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor.
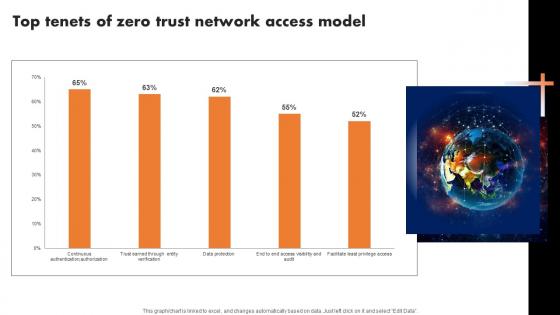
Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP
Find highly impressive Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Our Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































