Ethics

Agenda Of Agile Beliefs And Fundamentals Ideas PDF
This is a agenda of agile beliefs and fundamentals ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Icons Slide For Agile Beliefs And Fundamentals Professional PDF
Presenting our innovatively structured icons slide for agile beliefs and fundamentals professional pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.

Heaven Faith PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our Heaven Faith PowerPoint Templates PPT Backgrounds For Slides 1112.Use our Religion PowerPoint Templates because,You will be able to Highlight your ideas broad-based on strong fundamentals and illustrate how they step by step acheive the set growth factor. Use our Church PowerPoint Templates because,The Sermon on the Mount was a great presentation, it has been mankind's long standing inspiration. Use our Signs PowerPoint Templates because, this slide can help to bullet point your views. Use our Earth PowerPoint Templates because,You know that the core of any organisation is the people who work for it. Use our Future PowerPoint Templates because, Let this slide illustrates others piggyback on you to see well over the horizonUse these PowerPoint slides for presentations relating to Heaven faith, religion, church, signs, earth, future . The prominent colors used in the PowerPoint template are Blue, White, Black. Customers tell us our Heaven Faith PowerPoint Templates PPT Backgrounds For Slides 1112 are Festive. Professionals tell us our PowerPoint templates and PPT Slides are Lush. PowerPoint presentation experts tell us our Heaven Faith PowerPoint Templates PPT Backgrounds For Slides 1112 are Gorgeous. PowerPoint presentation experts tell us our earth PowerPoint templates and PPT Slides are Pleasant. Presenters tell us our Heaven Faith PowerPoint Templates PPT Backgrounds For Slides 1112 are Versatile. Professionals tell us our future PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Our Heaven Faith PowerPoint Templates Ppt Backgrounds For Slides 1112 come at a comfortable cost. They are definitely an economical choice.

Cross Faith Religion PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Cross Faith Religion PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Religion PowerPoint Templates because you can come forth with the plans you have so carefully laid out. Download our Church PowerPoint Templates because if making a mark is your obsession, then let others get Obsessed with you. Download and present our Signs PowerPoint Templates because you can spread the fruits of your efforts and elaborate your ideas on the prevention, diagnosis, control and cure of prevalent diseases. Present our Shapes PowerPoint Templates because with the help of our Slides you can Illustrate the means to prevent or control them using our imaginative templates. Present our People PowerPoint Templates because you should Emphasise the process of your business or corporate growth.Use these PowerPoint slides for presentations relating to Cross faith, religion, signs, church, shapes, people. The prominent colors used in the PowerPoint template are Yellow, Orange, Tan. Customers tell us our Cross Faith Religion PowerPoint Templates PPT Backgrounds For Slides 1212 are Spiffy. Presenters tell us our PowerPoint templates and PPT Slides are Endearing. Presenters tell us our Cross Faith Religion PowerPoint Templates PPT Backgrounds For Slides 1212 will make the presenter look like a pro even if they are not computer savvy. The feedback we get is that our people PowerPoint templates and PPT Slides are Dynamic. Use our Cross Faith Religion PowerPoint Templates PPT Backgrounds For Slides 1212 are Nostalgic. You can be sure our shapes PowerPoint templates and PPT Slides are Liberated. Adopt adventure with our Cross Faith Religion PowerPoint Templates Ppt Backgrounds For Slides 1212. Discover new avenues for your thoughts.
Faith Islam PowerPoint Slides And Ppt Diagram Templates
Faith Islam PowerPoint Slides And PPT Diagram Templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Capture success with our Faith Islam PowerPoint Slides And Ppt Diagram Templates. Download without worries with our money back guaranteee.
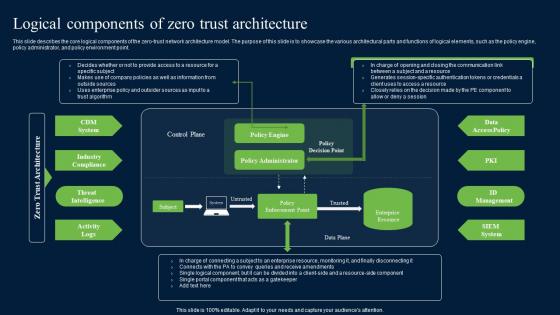
Logical Components Of Zero Trust Architecture Zero Trust Network Security Pictures Pdf
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. This Logical Components Of Zero Trust Architecture Zero Trust Network Security Pictures Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Logical Components Of Zero Trust Architecture Zero Trust Network Security Pictures Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point.
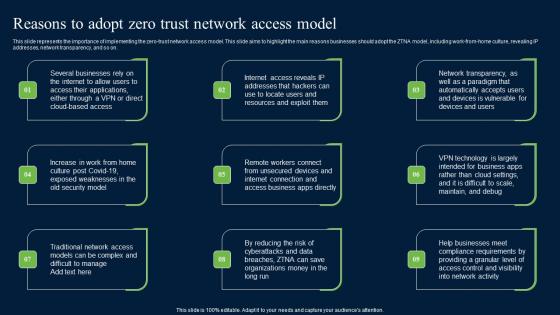
Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf. This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on.
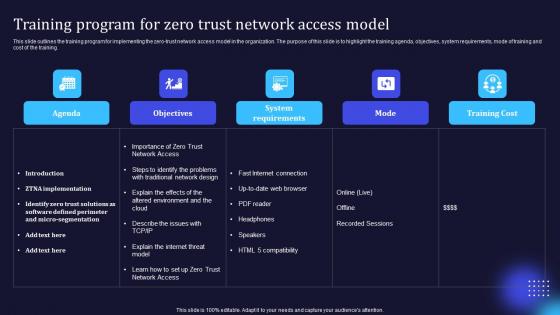
Zero Trust Model Training Program For Zero Trust Network Access Model
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Model Training Program For Zero Trust Network Access Model template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Model Training Program For Zero Trust Network Access Model that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.

Zero Trust Network Access Reasons To Adopt Zero Trust Network Access Model
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Network Access Reasons To Adopt Zero Trust Network Access Model a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Network Access Reasons To Adopt Zero Trust Network Access Model. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on.
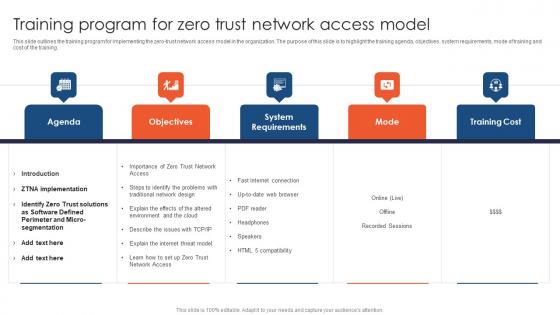
Zero Trust Network Access Training Program For Zero Trust Network Access Model
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Explore a selection of the finest Zero Trust Network Access Training Program For Zero Trust Network Access Model here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Training Program For Zero Trust Network Access Model to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.
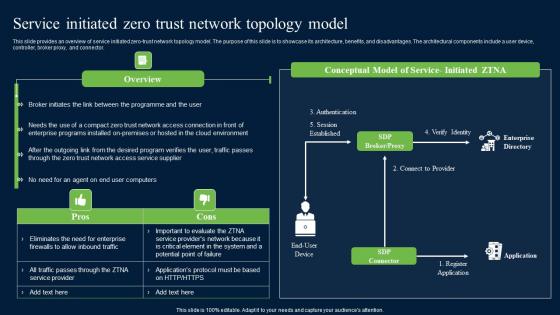
Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Find a pre-designed and impeccable Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.
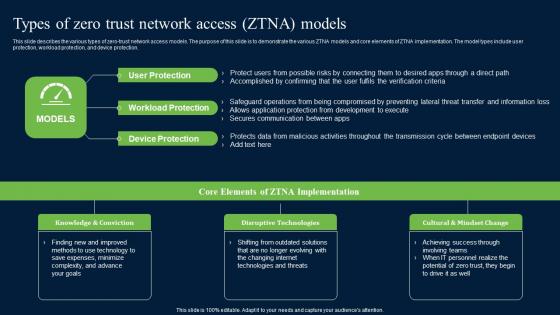
Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Boost your pitch with our creative Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.

Zero Trust Model Types Of Zero Trust Network Access ZTNA Models
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Model Types Of Zero Trust Network Access ZTNA Models. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.

Zero Trust Network Access Types Of Zero Trust Network Access ZTNA Models
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Network Access Types Of Zero Trust Network Access ZTNA Models from Slidegeeks and deliver a wonderful presentation. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.
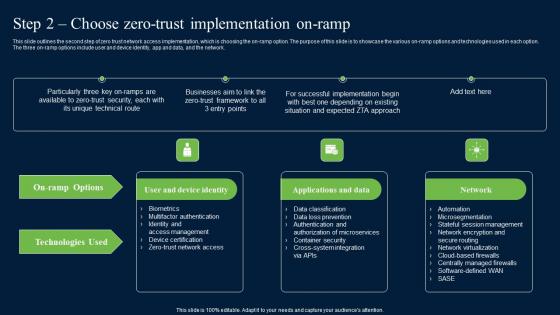
Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.

Jesus Faith Religion PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our Jesus Faith Religion PowerPoint Templates PPT Backgrounds For Slides 1112.Download and present our Religion PowerPoint Templates because it expound on why you have discarded some plans as you went along to the apex and came out with the final selection which you know will make you and your team shine. Download our Christmas PowerPoint Templates because the Christmas season brings with it cheer and goodwill. Download and present our Signs PowerPoint Templates because you will be able to Highlight your ideas broad-based on strong fundamentals and illustrate how they step by step acheive the set growth factor. Download and present our Shapes PowerPoint Templates because educate your staff on the means to provide the required support for speedy recovery. Download our Church PowerPoint Templates because our PowerPoint templates can spread the good word, be assured by all you will be keenly heard.Use these PowerPoint slides for presentations relating to Christian cross, religion, christmas, church, signs, shapes. The prominent colors used in the PowerPoint template are White, Purple, Pink. Professionals tell us our Jesus Faith Religion PowerPoint Templates PPT Backgrounds For Slides 1112 are Graceful. Presenters tell us our christmas PowerPoint templates and PPT Slides are Pleasant. We assure you our Jesus Faith Religion PowerPoint Templates PPT Backgrounds For Slides 1112 are Quaint. You can be sure our PowerPoint templates and PPT Slides are Bold. PowerPoint presentation experts tell us our Jesus Faith Religion PowerPoint Templates PPT Backgrounds For Slides 1112 are Cheerful. Use our shapes PowerPoint templates and PPT Slides are Radiant. Expand on your theory with our Jesus Faith Religion PowerPoint Templates Ppt Backgrounds For Slides 1112. Establish the cause of your confidence.

Zero Trust Model Reasons To Adopt Zero Trust Network Access Model
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Do you know about Slidesgeeks Zero Trust Model Reasons To Adopt Zero Trust Network Access Model These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on.
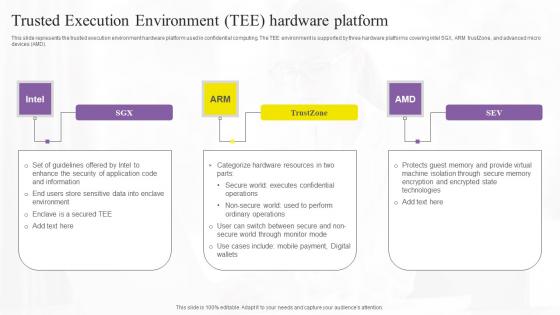
Trusted Execution Environment Tee Confidential Computing Technologies Brochure Pdf
This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering intel SGX, ARM trustZone, and advanced micro devices AMD. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Trusted Execution Environment Tee Confidential Computing Technologies Brochure Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Trusted Execution Environment Tee Confidential Computing Technologies Brochure Pdf today and make your presentation stand out from the rest This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering intel SGX, ARM trustZone, and advanced micro devices AMD.

Eid Faith Islam PowerPoint Slides And Ppt Diagram Templates
Eid Faith Islam PowerPoint Slides And PPT Diagram Templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Dont make your presetations long and boring. Make them to the point with our Eid Faith Islam PowerPoint Slides And Ppt Diagram Templates. You will be at the top of your game.
Five Year Mindset Roadmap To Individuals Belief And Behavior Microsoft
Presenting the five year mindset roadmap to individuals belief and behavior microsoft. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
Quarterly Mindset Roadmap To Individuals Belief And Behavior Download
Presenting the quarterly mindset roadmap to individuals belief and behavior download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
Six Months Mindset Roadmap To Individuals Belief And Behavior Demonstration
Presenting the six months mindset roadmap to individuals belief and behavior demonstration. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
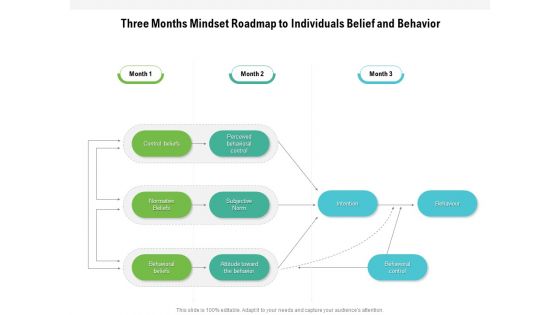
Three Months Mindset Roadmap To Individuals Belief And Behavior Designs
Presenting the three months mindset roadmap to individuals belief and behavior designs. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Agile Beliefs And Fundamentals Development Of Agile Manifesto Demonstration PDF
This slide provides the glimpse about the main factors of agile manifesto development based on their preferences such as people, product, communication and responsiveness.This is a agile beliefs and fundamentals development of agile manifesto demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like communication, responsiveness, manifesto gives preference You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Trust Monopoly In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Trust Monopoly In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Trust Monopoly that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Trust Monopoly In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
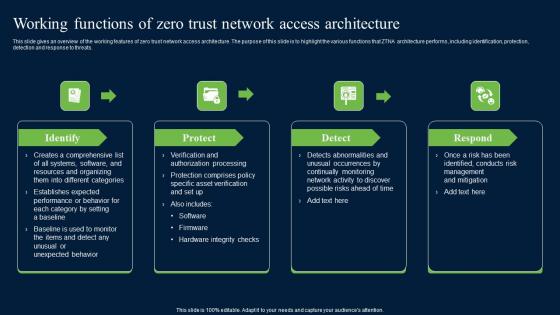
Working Functions Of Zero Trust Network Access Security Infographics Pdf
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Create an editable Working Functions Of Zero Trust Network Access Security Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Functions Of Zero Trust Network Access Security Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.

Trusted Execution Environment Tee Hardware Secure Computing Framework Graphics Pdf
This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Get a simple yet stunning designed Trusted Execution Environment Tee Hardware Secure Computing Framework Graphics Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Trusted Execution Environment Tee Hardware Secure Computing Framework Graphics Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD.
Trusted Advisor Trusted Supplier Ppt Example
This is a trusted advisor trusted supplier ppt example. This is a four stage process. The stages in this process are trusted advisor, trusted supplier, local employee, great company.
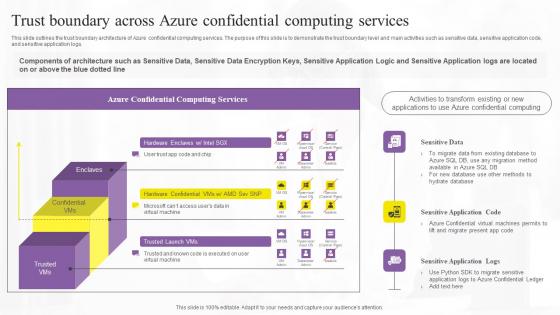
Trust Boundary Across Azure Confidential Computing Technologies Themes Pdf
This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Slidegeeks is here to make your presentations a breeze with Trust Boundary Across Azure Confidential Computing Technologies Themes Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs.
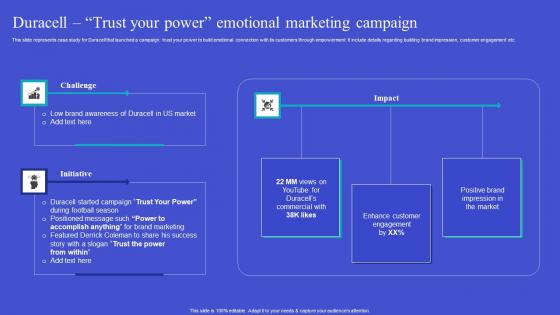
Exploring Neuromarketing Strategies Duracell Trust Your Power Ideas Pdf
This slide represents case study for Duracell that launched a campaign trust your power to build emotional connection with its customers through empowerment. It include details regarding building brand impression, customer engagement etc. There are so many reasons you need a Exploring Neuromarketing Strategies Duracell Trust Your Power Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents case study for Duracell that launched a campaign trust your power to build emotional connection with its customers through empowerment. It include details regarding building brand impression, customer engagement etc.

What Is Trusted Execution Environment Confidential Computing Technologies Microsoft Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Find a pre-designed and impeccable What Is Trusted Execution Environment Confidential Computing Technologies Microsoft Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
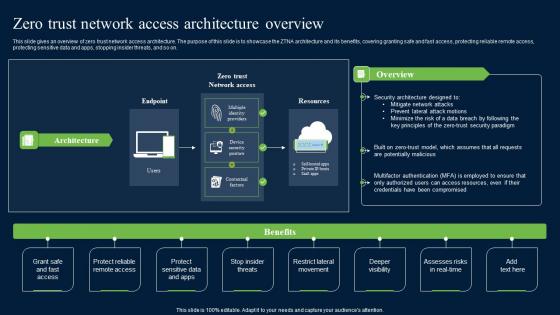
Zero Trust Network Security Access Architecture Overview Graphics Pdf
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Security Access Architecture Overview Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.

Most Trusted Supplement Brands In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Most Trusted Supplement Brands In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Most Trusted Supplement Brands that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Most Trusted Supplement Brands In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Agenda For Zero Trust Network Access Ppt Diagram Graph Charts
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Agenda For Zero Trust Network Access Ppt Diagram Graph Charts a try. Our experts have put a lot of knowledge and effort into creating this impeccable Agenda For Zero Trust Network Access Ppt Diagram Graph Charts. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today Our Agenda For Zero Trust Network Access Ppt Diagram Graph Charts are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Agenda For Zero Trust Model Ppt Powerpoint Presentation File
Boost your pitch with our creative Agenda For Zero Trust Model Ppt Powerpoint Presentation File. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Agenda For Zero Trust Model Ppt Powerpoint Presentation File are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
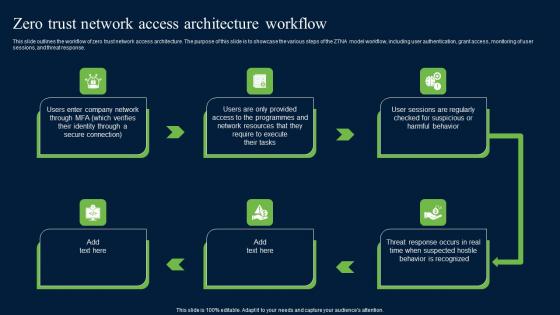
Zero Trust Network Access Architecture Workflow Themes Pdf
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Network Access Architecture Workflow Themes Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Network Access Architecture Workflow Themes Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Zero Trust Network Access ZTNA Introduction Graphics Pdf
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Find highly impressive Zero Trust Network Access ZTNA Introduction Graphics Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Network Access ZTNA Introduction Graphics Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.

Zero Trust Model Future And Emerging Trends In ZTNA Model
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. This Zero Trust Model Future And Emerging Trends In ZTNA Model is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Future And Emerging Trends In ZTNA Model features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
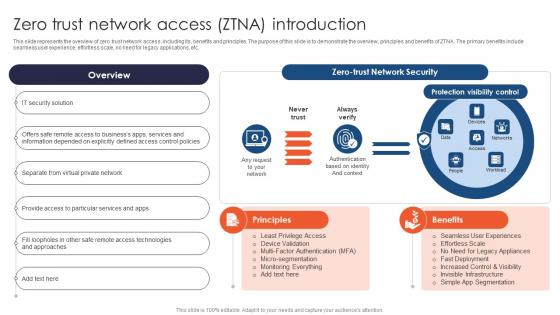
Zero Trust Network Access ZTNA Introduction Ppt File Infographic Template
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Network Access ZTNA Introduction Ppt File Infographic Template to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Network Access ZTNA Introduction Ppt File Infographic Template. This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.
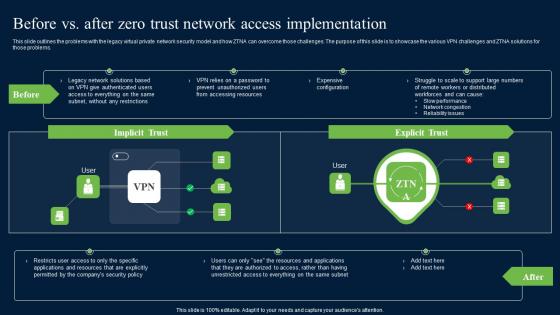
Before Vs After Zero Trust Network Access Brochure Pdf
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.
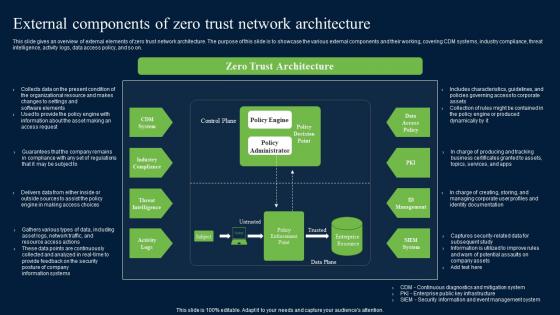
External Components Of Zero Trust Network Security Structure Pdf
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Security Structure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
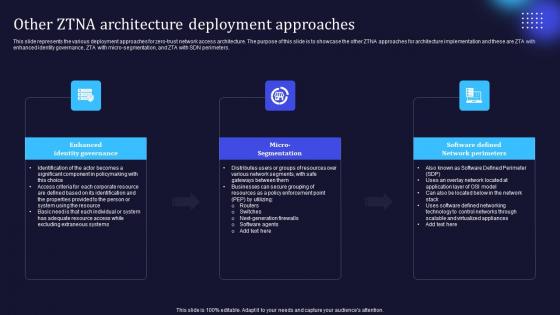
Zero Trust Model Other ZTNA Architecture Deployment Approaches
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Model Other ZTNA Architecture Deployment Approaches to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Model Other ZTNA Architecture Deployment Approaches. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.

Zero Trust Network Access Architecture Overview Software Defined Perimeter SDP
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Welcome to our selection of the Zero Trust Network Access Architecture Overview Software Defined Perimeter SDP. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.

Zero Trust Network Access User Flow Overview Ppt File Deck
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. The Zero Trust Network Access User Flow Overview Ppt File Deck is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
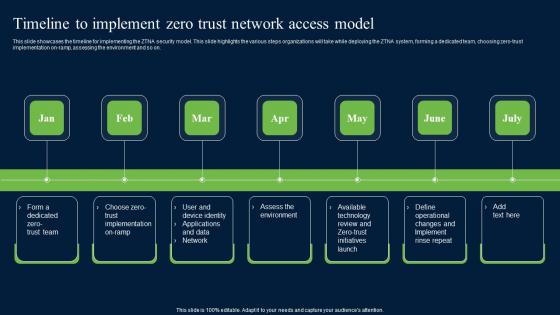
Timeline To Implement Zero Trust Network Security Themes Pdf
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Zero Trust Network Security Themes Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Zero Trust Model Case Study Intellectual Property Protection
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Model Case Study Intellectual Property Protection will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.

Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf
This slide outlines the process of using intel sgx-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing intel sgx-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf today and make your presentation stand out from the rest This slide outlines the process of using intel sgx-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing intel sgx-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing.
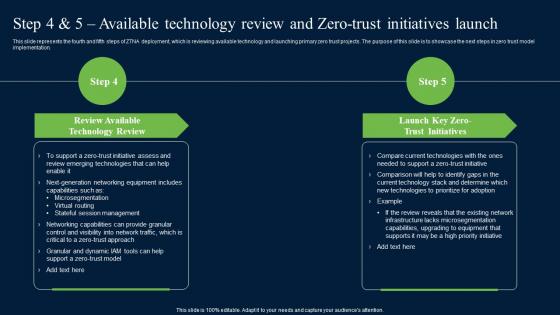
Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. There are so many reasons you need a Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.
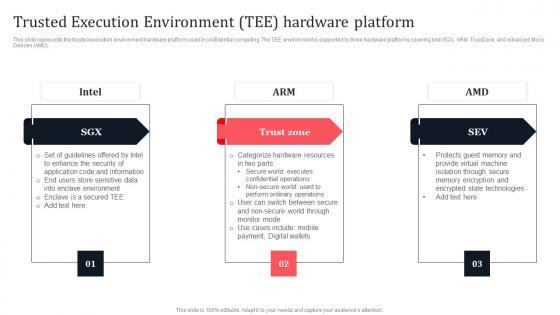
Trusted Execution Environment Tee Hardware Platform Secure Multi Party Microsoft Pdf
This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Trusted Execution Environment Tee Hardware Platform Secure Multi Party Microsoft Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Trusted Execution Environment Tee Hardware Platform Secure Multi Party Microsoft Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD.

Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.
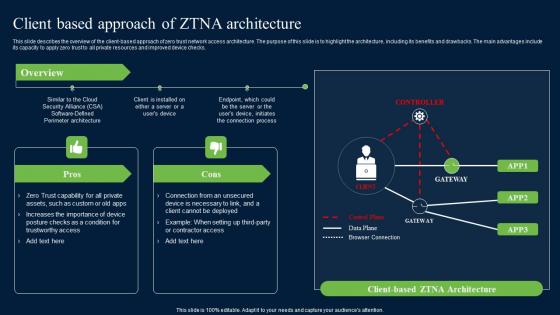
Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of ZTNA Zero Trust Network Security Demonstration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.
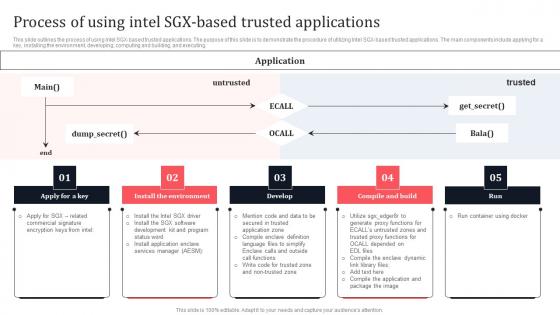
Process Of Using Intel SGX Based Trusted Applications Secure Multi Party Structure Pdf
This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Present like a pro with Process Of Using Intel SGX Based Trusted Applications Secure Multi Party Structure Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing.
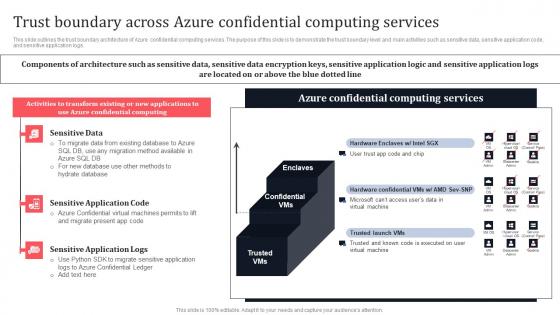
Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf
This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs.
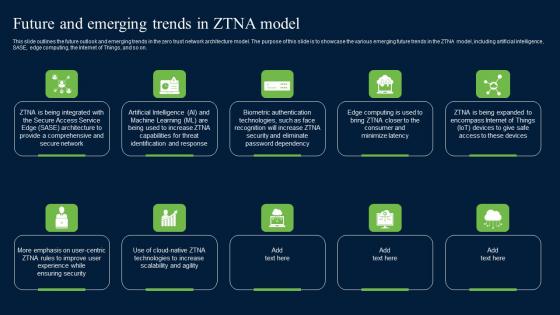
Future And Emerging Trends In ZTNA Model Zero Trust Network Security Clipart Pdf
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Future And Emerging Trends In ZTNA Model Zero Trust Network Security Clipart Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.
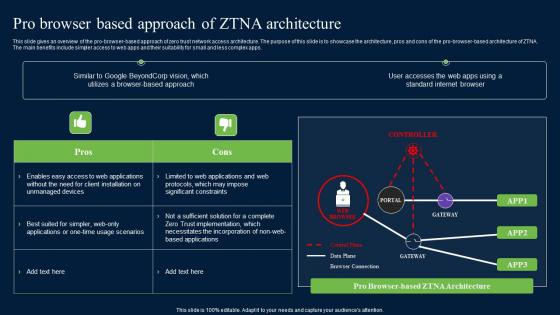
Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf
The main benefits include simpler access to web apps and their suitability for small and less complex apps. Presenting this PowerPoint presentation, titled Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The main benefits include simpler access to web apps and their suitability for small and less complex apps.
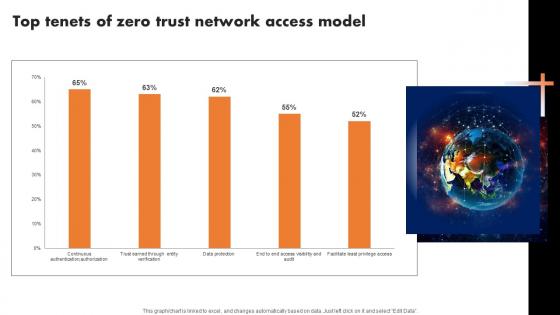
Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP
Find highly impressive Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Our Top Tenets Of Zero Trust Network Access Model Software Defined Perimeter SDP are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents For Zero Trust Network Access Ppt Diagram Lists
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Table Of Contents For Zero Trust Network Access Ppt Diagram Lists can be your best option for delivering a presentation. Represent everything in detail using Table Of Contents For Zero Trust Network Access Ppt Diagram Lists and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. Our Table Of Contents For Zero Trust Network Access Ppt Diagram Lists are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































