Executive Summary Security
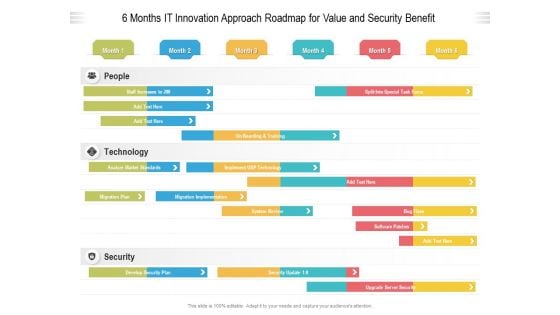
6 Months IT Innovation Approach Roadmap For Value And Security Benefit Pictures
We present our 6 months it innovation approach roadmap for value and security benefit pictures. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 6 months it innovation approach roadmap for value and security benefit pictures in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
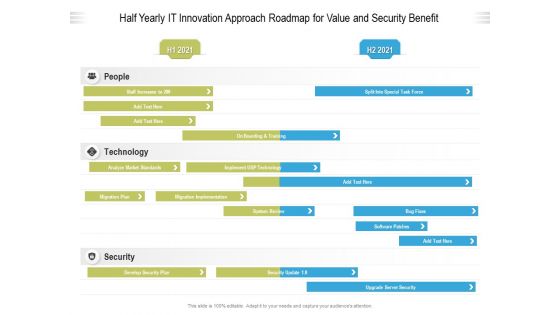
Half Yearly IT Innovation Approach Roadmap For Value And Security Benefit Professional
We present our half yearly it innovation approach roadmap for value and security benefit professional. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly it innovation approach roadmap for value and security benefit professional in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
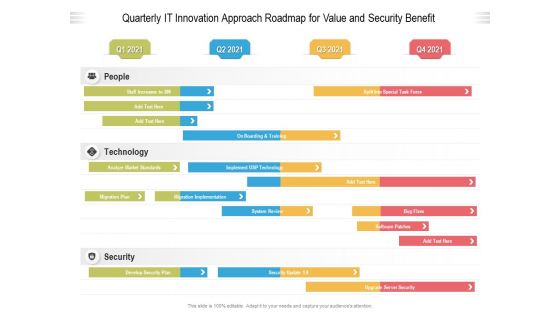
Quarterly IT Innovation Approach Roadmap For Value And Security Benefit Elements
We present our quarterly it innovation approach roadmap for value and security benefit elements. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly it innovation approach roadmap for value and security benefit elements in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
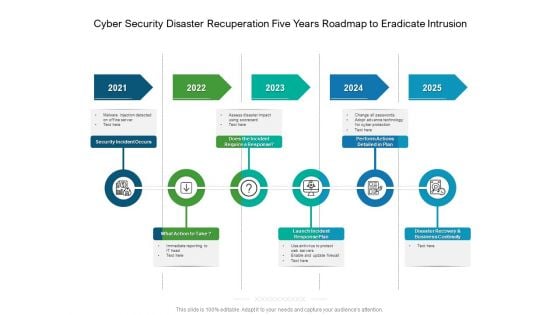
Cyber Security Disaster Recuperation Five Years Roadmap To Eradicate Intrusion Professional
We present our cyber security disaster recuperation five years roadmap to eradicate intrusion professional. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched cyber security disaster recuperation five years roadmap to eradicate intrusion professionalin different formats like PDF, PNG, and JPG to smoothly execute your business plan.
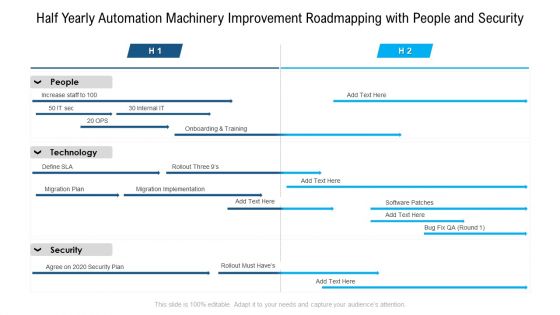
Half Yearly Automation Machinery Improvement Roadmapping With People And Security Topics
We present our half yearly automation machinery improvement roadmapping with people and security topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly automation machinery improvement roadmapping with people and security topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Six Months Enterprise IT Automation Machinery Road Mapping With Security And Compliance Professional
We present our six months enterprise it automation machinery road mapping with security and compliance professional. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months enterprise it automation machinery road mapping with security and compliance professional in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Conclusion And Recommendation Global Security Industry PPT Sample IR SS V
This slide highlights the conclusion of global Defense market. The purpose of this slide is to provide a brief insights on how the Defense market is going related to its growth. On a global scale, defense industry is a highly competitive and dynamic sector. It covers understanding of global market, diversification of products and services offered, and emerging middle class expansion. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Conclusion And Recommendation Global Security Industry PPT Sample IR SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Conclusion And Recommendation Global Security Industry PPT Sample IR SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights the conclusion of global Defense market. The purpose of this slide is to provide a brief insights on how the Defense market is going related to its growth. On a global scale, defense industry is a highly competitive and dynamic sector. It covers understanding of global market, diversification of products and services offered, and emerging middle class expansion.
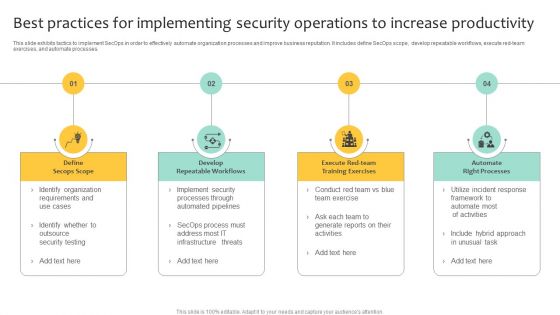
Best Practices For Implementing Security Operations To Increase Productivity Clipart PDF
This slide exhibits tactics to implement SecOps in order to effectively automate organization processes and improve business reputation. It includes define SecOps scope, develop repeatable workflows, execute red-team exercises, and automate processes. Presenting Best Practices For Implementing Security Operations To Increase Productivity Clipart PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Develop Repeatable Workflows, Automate Right Processes, Define Secops Scope. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
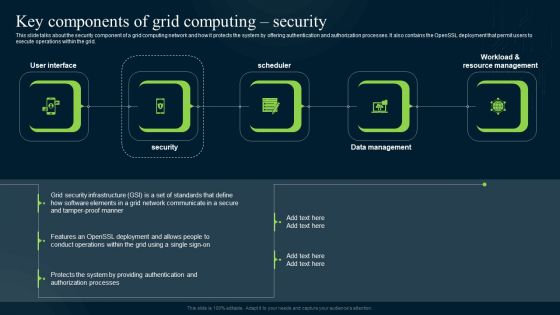
Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Explore a selection of the finest Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Grid Computing Infrastructure Key Components Of Grid Computing Security Information PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
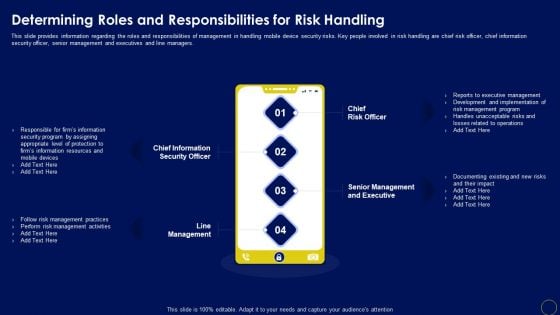
Determining Roles And Responsibilities For Risk Handling Business Mobile Device Security Management Graphics PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. Boost your pitch with our creative Determining Roles And Responsibilities For Risk Handling Business Mobile Device Security Management Graphics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Cyber Security Implementation Framework Determining Roles And Responsibilities For Risk Handling Icons PDF
Presenting this set of slides with name cyber security implementation framework determining roles and responsibilities for risk handling icons pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Determining Roles And Responsibilities For Risk Handling Mockup PDF
Presenting this set of slides with name computer security incident handling determining roles and responsibilities for risk handling mockup pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
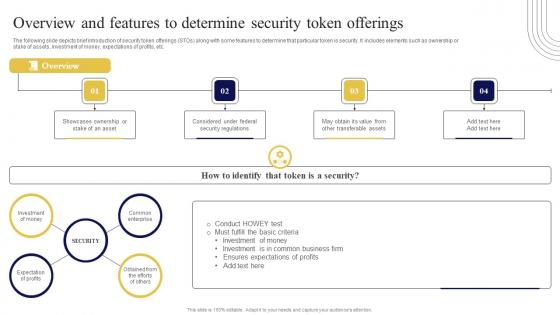
Overview And Features To Determine Security Exploring Investment Opportunities Slides Pdf
The following slide depicts brief introduction of security token offerings STOs along with some features to determine that particular token is security. It includes elements such as ownership or stake of assets, investment of money, expectations of profits, etc. Do you know about Slidesgeeks Overview And Features To Determine Security Exploring Investment Opportunities Slides Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide depicts brief introduction of security token offerings STOs along with some features to determine that particular token is security. It includes elements such as ownership or stake of assets, investment of money, expectations of profits, etc.
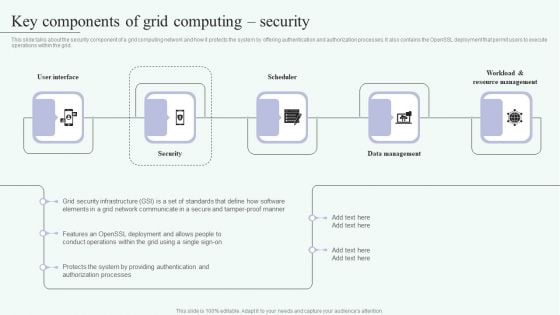
Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture
This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Get a simple yet stunning designed CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc.

Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising sixteen slides this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now. Our Big Data Security Monitoring Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security For Your Organization Determining Roles And Responsibilities For Risk Handling Ppt Outline Example PDF
Presenting this set of slides with name cyber security for your organization determining roles and responsibilities for risk handling ppt outline example pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management, executive, line management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
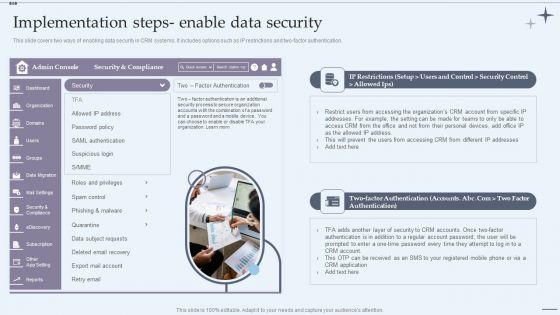
CRM System Implementation Stages Implementation Steps Enable Data Security Slides PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Presenting CRM System Implementation Stages Implementation Steps Enable Data Security Slides PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Marketing Executive, Marketing Intern, Sales Executive. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf
Are you searching for a Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf from Slidegeeks today. Our Table Of Contents Cyber Security Response Ppt Powerpoint Presentation Diagram Templates Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security Implementation Framework Business Impact Assessment Ppt PowerPoint Presentation Layouts Visuals PDF
Presenting this set of slides with name cyber security implementation framework business impact assessment ppt powerpoint presentation layouts visuals pdf. This is a three stage process. The stages in this process are department or function, executive, employees, business, strengths, weaknesses, loss impact. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Application Security Testing Tools Used In Devsecops Role Of Devsecops Ppt Sample
This slide discusses the various application security testing tools used in DevSecOps. The purpose of this slide is to explain the security testing tools these include static application security testing, software composition analysis, interactive application security testing, etc. Find a pre-designed and impeccable Application Security Testing Tools Used In Devsecops Role Of Devsecops Ppt Sample The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the various application security testing tools used in DevSecOps. The purpose of this slide is to explain the security testing tools these include static application security testing, software composition analysis, interactive application security testing, etc.
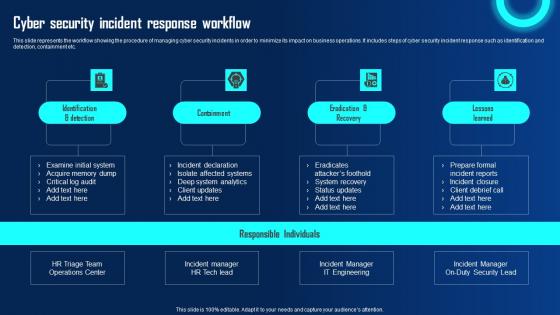
Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf
This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc. This Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc.

Strategies To Mitigate Cyber Security Risks Determining Roles And Responsibilities For Risk Handling Ideas PDF
Presenting this set of slides with name strategies to mitigate cyber security risks determining roles and responsibilities for risk handling ideas pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
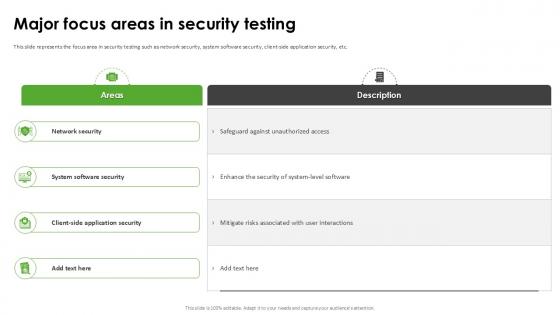
Major Focus Areas In Security Testing Harnessing The World Of Ethical Ppt Example
This slide represents the focus area in security testing such as network security, system software security, client-side application security, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Major Focus Areas In Security Testing Harnessing The World Of Ethical Ppt Example to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the focus area in security testing such as network security, system software security, client-side application security, etc.

Overview Need For Implementing Data Security Across Retail DT SS V
This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.Make sure to capture your audiences attention in your business displays with our gratis customizable Overview Need For Implementing Data Security Across Retail DT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.
Security Awareness KPI For Tracking Project Impact On Communication Plan Ideas Pdf
This slide showcases KPIs to track security awareness program. This template focuses on evaluating and measuring security awareness in organisation. It includes information related to phishing rates, cost of security breaches, audit hits, etc.Pitch your topic with ease and precision using this Security Awareness KPI For Tracking Project Impact On Communication Plan Ideas Pdf This layout presents information on Program Participation, Security Breaches, Phishing Rate It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases KPIs to track security awareness program. This template focuses on evaluating and measuring security awareness in organisation. It includes information related to phishing rates, cost of security breaches, audit hits, etc.

Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twenty eight slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking. Our Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security Response Management Ppt Powerpoint Presentation Complete Deck With Slides
Incorporate this Cyber Security Response Management Ppt Powerpoint Presentation Complete Deck With Slides to make your business idea and proposal stand out. This will also ensure that your proposal,in seventeen slides of this complete deck,is well organized and professional. You can also add variables like market opportunity,value proposition,innovative solutions,and more for any business concern or issue that you might be facing. Download this design now. The 100 percent customizable nature of the template adds to the beauty of the entire concept of the off the shelf presentation concept that we have mastered. Our Cyber Security Response Management Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Zero Trust Network Security Ppt PowerPoint Presentation Complete Deck With Slides
Use this Zero Trust Network Security Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in eighty nine slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now. Our Zero Trust Network Security Ppt PowerPoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Password Security App Two Factor Authentication In Powerpoint And Google Slides Cpb
Introducing our well designed Password Security App Two Factor Authentication In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Password Security App Two Factor Authentication. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Password Security App Two Factor Authentication In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Overview Of Website Security Check To Improve Efficiency Step By Step Guide Slides PDF
Following slide represents overview and benefits to conduct security test to assure website authenticity and eliminate potential threats. It further covers description, example, benefits such as simpler fixes, educate developers etc. Want to ace your presentation in front of a live audience Our Overview Of Website Security Check To Improve Efficiency Step By Step Guide Slides PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. Following slide represents overview and benefits to conduct security test to assure website authenticity and eliminate potential threats. It further covers description, example, benefits such as simpler fixes, educate developers etc.

Complete Guide To Launch Overview Of Website Security Check To Improve
Following slide represents overview and benefits to conduct security test to assure website authenticity and eliminate potential threats. It further covers description, example, benefits such as simpler fixes, educate developers etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Complete Guide To Launch Overview Of Website Security Check To Improve for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Following slide represents overview and benefits to conduct security test to assure website authenticity and eliminate potential threats. It further covers description, example, benefits such as simpler fixes, educate developers etc.

Various Types Of Security Testing Harnessing The World Of Ethical Ppt Sample
This slide represents the types of security testing such as penetration testing, application security testing, web application security testing, etc. Do you know about Slidesgeeks Various Types Of Security Testing Harnessing The World Of Ethical Ppt Sample These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the types of security testing such as penetration testing, application security testing, web application security testing, etc.
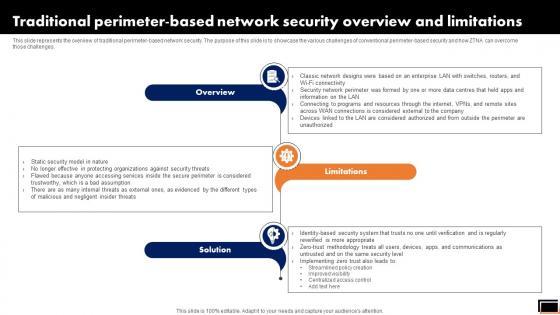
Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.
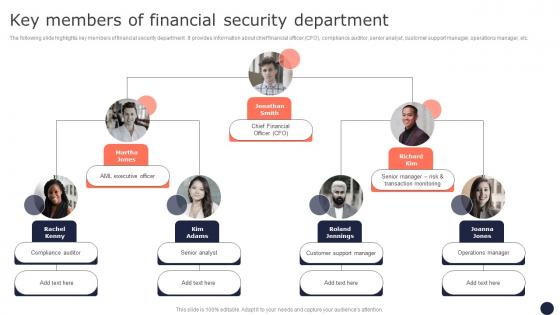
Key Members Of Financial Security Department Mitigating Corporate Scams And Robberies Designs Pdf
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This Key Members Of Financial Security Department Mitigating Corporate Scams And Robberies Designs Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Key Members Of Financial Security Department Mitigating Corporate Scams And Robberies Designs Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc.

About Cloud Cryptography Overview And Features Data Security In Cloud Computing Ppt Powerpoint
This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Cloud Cryptography Overview And Features Data Security In Cloud Computing Ppt Powerpoint for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology.

Company Introduction Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide represents the overview of Mycroft company which offers open source voice assistant and can be used in any field. It showcases industry, customer, headquarters, founded year, founders and legal name. Make sure to capture your audiences attention in your business displays with our gratis customizable Company Introduction Voice Assistance Security Platform Investor Funding Presentation Professional Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of Mycroft company which offers open source voice assistant and can be used in any field. It showcases industry, customer, headquarters, founded year, founders and legal name.

Global Data Security Industry Report Overview Of Cybersecurity Market Landscape IR SS V
The slide highlights a comprehensive overview of the cyber security industry. The purpose of the slide is to provide insights to stakeholders enabling them to make strategic decisions. The slide covers market sizing, and statistics related to cybersecurity spending, cybercrimes, and venture funding. This modern and well-arranged Global Data Security Industry Report Overview Of Cybersecurity Market Landscape IR SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide highlights a comprehensive overview of the cyber security industry. The purpose of the slide is to provide insights to stakeholders enabling them to make strategic decisions. The slide covers market sizing, and statistics related to cybersecurity spending, cybercrimes, and venture funding.

Effective Ways Of Raising It Security Awareness Communication Plan Demonstration Pdf
This slide showcases different ways to consider while planning communication to increase information security awareness which helps to create messages that match with audiences mitigates all problems. It includes information related to impact of security incidents, IT security mechanism, etc.Pitch your topic with ease and precision using this Effective Ways Of Raising It Security Awareness Communication Plan Demonstration Pdf This layout presents information on Secure Management, Prioritize Personal, Security Awareness It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases different ways to consider while planning communication to increase information security awareness which helps to create messages that match with audiences mitigates all problems. It includes information related to impact of security incidents, IT security mechanism, etc.
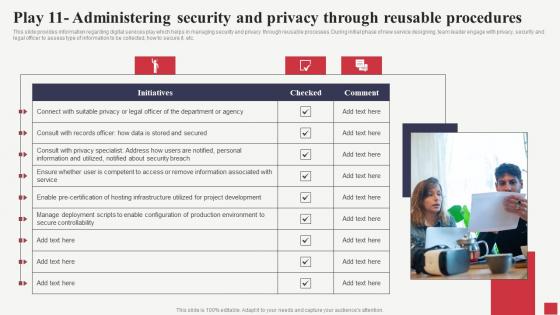
Play 11 Administering Security And Privacy Through Public Sector Digital Solutions Designs Pdf
This slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Find a pre-designed and impeccable Play 11 Administering Security And Privacy Through Public Sector Digital Solutions Designs Pdf The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc.

Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V
This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V. This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.
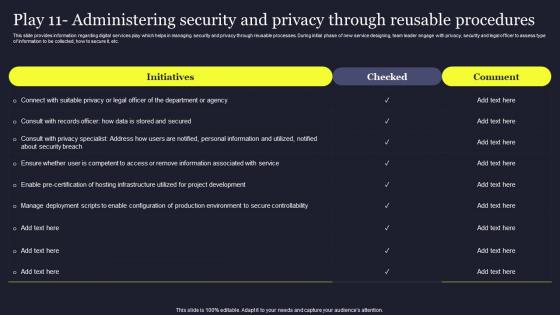
Play 11 Administering Security And Privacy Playbook For Managing Us Slides Pdf
This slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100Precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Play 11 Administering Security And Privacy Playbook For Managing Us Slides Pdf from Slidegeeks and deliver a wonderful presentation. This slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc.
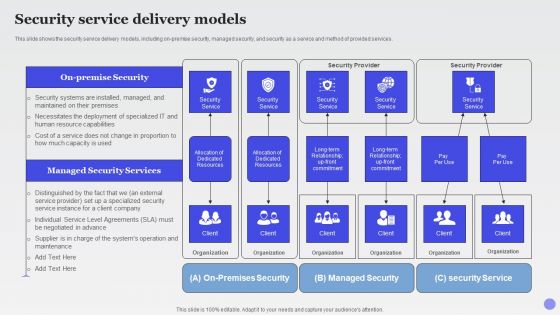
Security Service Delivery Models Xaas Cloud Computing Models Ppt PowerPoint Presentation Infographic Template Graphics PDF
This slide shows the security service delivery models, including on premise security, managed security, and security as a service and method of provided services.Deliver an awe inspiring pitch with this creative Security Service Delivery Models Xaas Cloud Computing Models Ppt PowerPoint Presentation Infographic Template Graphics PDF bundle. Topics like Dedicated Resources, Security Service, Managed Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
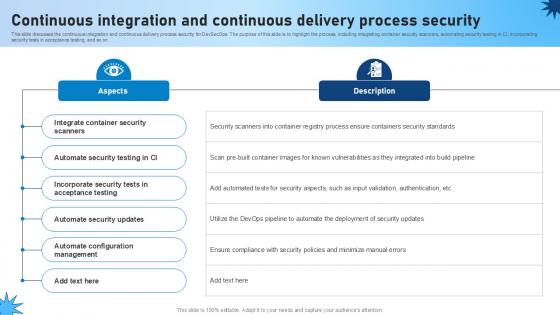
Continuous Integration And Continuous Delivery Process Security Role Of Devsecops Ppt Slide
This slide discusses the continuous integration and continuous delivery process security for DevSecOps. The purpose of this slide is to highlight the process, including integrating container security scanners, automating security testing in CI, incorporating security tests in acceptance testing, and so on. Present like a pro with Continuous Integration And Continuous Delivery Process Security Role Of Devsecops Ppt Slide Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide discusses the continuous integration and continuous delivery process security for DevSecOps. The purpose of this slide is to highlight the process, including integrating container security scanners, automating security testing in CI, incorporating security tests in acceptance testing, and so on.
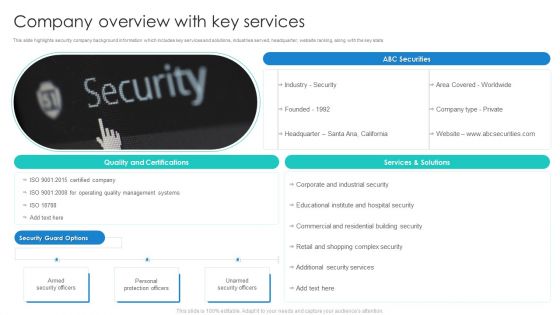
Manpower Corporate Security Business Profile Company Overview With Key Services Formats PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Company Overview With Key Services Formats PDF bundle. Topics like Armed Security Officer, Personal Protection Officers, Unarmed Security Officers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
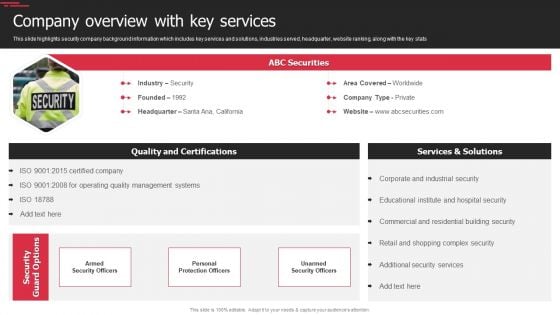
Security Agency Business Profile Company Overview With Key Services Inspiration PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Company Overview With Key Services Inspiration PDF bundle. Topics like Quality Management Systems, Industrial Security, Security Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. Create an editable About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc.

What Is The Cyber Security Role Web Designing User Engagement Rules PDF
Boost your pitch with our creative What Is The Cyber Security Role Web Designing User Engagement Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.
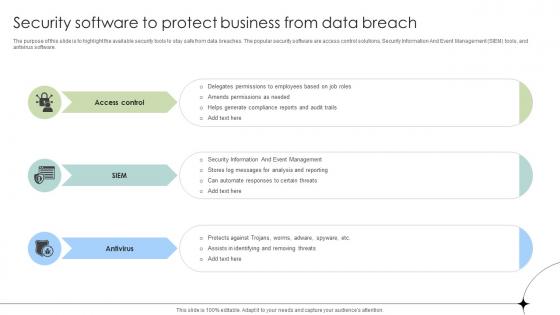
Security Software To Protect Business From Data Breach Data Fortification Strengthening Defenses
The purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Software To Protect Business From Data Breach Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software.
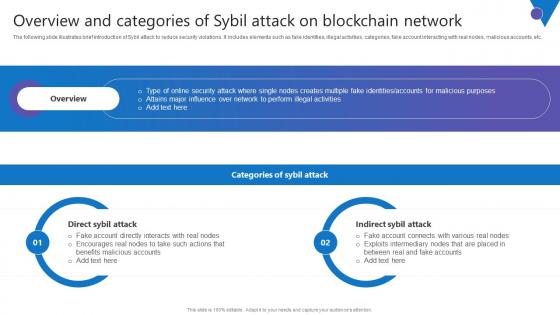
Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf
The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. Are you searching for a Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf from Slidegeeks today. The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc.

Security Testing Implementation Training Program Harnessing The World Of Ethical Ppt Slide
The purpose of this slide is to outline the security testing implementation training program such as mode, cost, agenda, and schedule for the training programs. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Security Testing Implementation Training Program Harnessing The World Of Ethical Ppt Slide from Slidegeeks and deliver a wonderful presentation. The purpose of this slide is to outline the security testing implementation training program such as mode, cost, agenda, and schedule for the training programs.

Specific Security Tool Common To All Devsecops Design Role Of Devsecops Ppt Sample
This slide discusses the specific security tool common to DevSecOps design. The purpose of this slide is to explain the various tools, including runtime defense, vulnerability, CVE service host, artifact repository, and zero trust. Get a simple yet stunning designed Specific Security Tool Common To All Devsecops Design Role Of Devsecops Ppt Sample It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Specific Security Tool Common To All Devsecops Design Role Of Devsecops Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide discusses the specific security tool common to DevSecOps design. The purpose of this slide is to explain the various tools, including runtime defense, vulnerability, CVE service host, artifact repository, and zero trust.
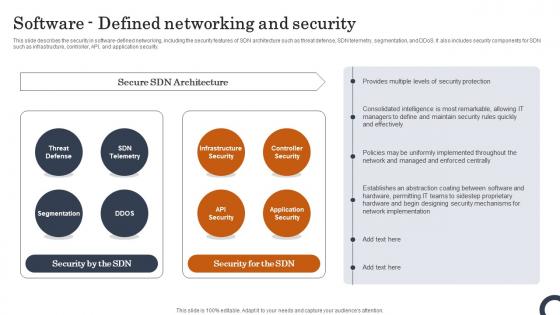
Software Defined Networking And Security Evolution Of SDN Controllers Inspiration Pdf
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Do you know about Slidesgeeks Software Defined Networking And Security Evolution Of SDN Controllers Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.
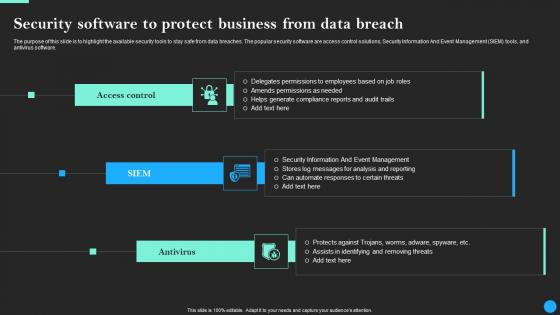
Security Software To Protect Business From Data Breach Prevention Elements Pdf
Want to ace your presentation in front of a live audience Our Security Software To Protect Business From Data Breach Prevention Elements Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software.
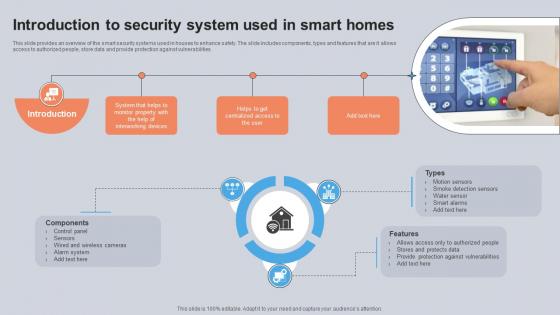
Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. Create an editable Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities.

Zero Trust Network Access Traditional Security Models Vs Zero Trust Network Access
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Welcome to our selection of the Zero Trust Network Access Traditional Security Models Vs Zero Trust Network Access. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling.
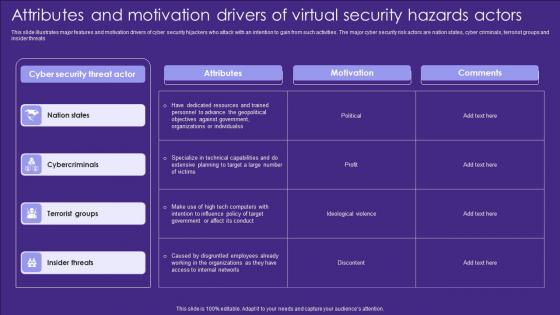
Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf
This slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats Showcasing this set of slides titled Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf. The topics addressed in these templates are Attributes, Motivation, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats

Evolution Of Security Testing Harnessing The World Of Ethical Ppt Presentation
This slide showcases the evolution of security testing from late 1960 when the inception of security testing was unclear to universal practice for all sizes. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Evolution Of Security Testing Harnessing The World Of Ethical Ppt Presentation With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Evolution Of Security Testing Harnessing The World Of Ethical Ppt Presentation today and make your presentation stand out from the rest This slide showcases the evolution of security testing from late 1960 when the inception of security testing was unclear to universal practice for all sizes.
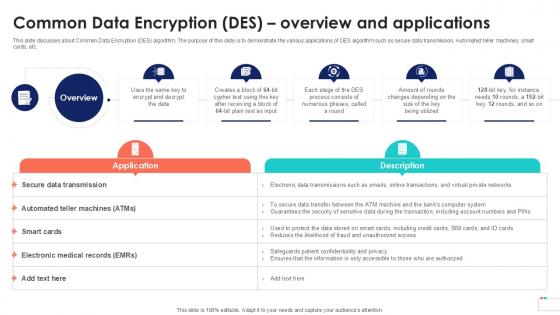
Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample
This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Common Data Encryption Des Overview Data Security In Cloud Computing Ppt Sample that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide discusses about Common Data Encryption DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc.
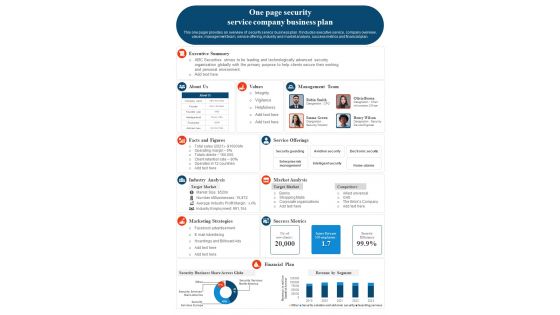
One Page Security Service Company Business Plan PDF Document PPT Template
Presenting you an exemplary One Page Security Service Company Business Plan PDF Document PPT Template. Our one-pager template comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this One Page Security Service Company Business Plan PDF Document PPT Template Download now. Our One Page Security Service Company Business Plan PDF Document PPT Template are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































