Executive Summary Security
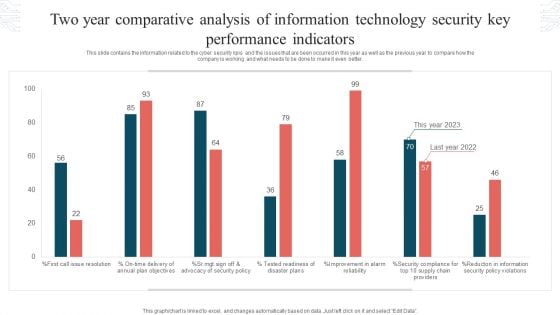
Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF
This slide contains the information related to the cyber security kpis and the issues that are been occurred in this year as well as the previous year to compare how the company is working and what needs to be done to make it even better. Showcasing this set of slides titled Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF. The topics addressed in these templates are Tested Readiness, Disaster Plans, Security Policy Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Investment And Security Analysis Portfolio Management Ppt PowerPoint Presentation Complete Deck With Slides
This is a investment and security analysis portfolio management ppt powerpoint presentation complete deck with slides. This is a one stage process. The stages in this process are planning, business, strategy, management, marketing.

Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF
This slide provide the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market etc.Persuade your audience using this Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Provided Parties, Initial Cost Investment, Comparatively Longer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Problems Cloud Computing Ppt PowerPoint Presentation Infographic Template Picture Cpb
Presenting this set of slides with name security problems cloud computing ppt powerpoint presentation infographic template picture cpb. This is an editable Powerpoint four stages graphic that deals with topics like security problems cloud computing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Transformation Cyber Security Roadmap Ppt PowerPoint Presentation Infographic Template Visual Aids Cpb Pdf
Presenting this set of slides with name transformation cyber security roadmap ppt powerpoint presentation infographic template visual aids cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like transformation cyber security roadmap to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Threat Intelligence Cyber Security Ppt PowerPoint Presentation Infographic Template Diagrams Cpb Pdf
Presenting this set of slides with name threat intelligence cyber security ppt powerpoint presentation infographic template diagrams cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like threat intelligence cyber security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Mortgage Technology Data Security Ppt PowerPoint Presentation Professional Infographic Template Cpb Pdf
Presenting this set of slides with name mortgage technology data security ppt powerpoint presentation professional infographic template cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like mortgage technology data security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Corporate Security Vendor Analysis Ppt PowerPoint Presentation Infographic Template Information Cpb Pdf
Presenting this set of slides with name corporate security vendor analysis ppt powerpoint presentation infographic template information cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like corporate security vendor analysis to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Business Firms Safety And Security Rules Vector Icon Ppt PowerPoint Presentation Gallery Maker PDF
Persuade your audience using this business firms safety and security rules vector icon ppt powerpoint presentation gallery maker pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including business firms safety and security rules vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
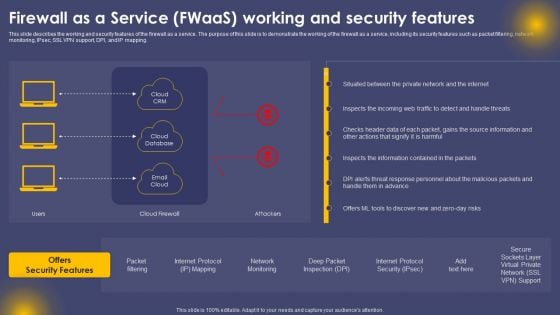
Firewall As A Service Fwaas Working And Security Features Ppt File Guidelines PDF
This slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Create an editable Firewall As A Service Fwaas Working And Security Features Ppt File Guidelines PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Firewall As A Service Fwaas Working And Security Features Ppt File Guidelines PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Security Officer Walking Down Through Escalator In Shopping Mall Ppt PowerPoint Presentation File Example File PDF
Showcasing this set of slides titled security officer walking down through escalator in shopping mall ppt powerpoint presentation file example file pdf. The topics addressed in these templates are security officer walking down through escalator in shopping mall. All the content presented in this PPT design is completely editable. Download it and make ajustments in color, background, font etc. as per your unique business setting.

Proposal For Enterprise Security System Case Study One Pager Sample Example Document
The following slide displays the case study for security system proposal, as it highlights the project description, project results, project budget and project timeline. Presenting you an exemplary Proposal For Enterprise Security System Case Study One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Case Study One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Cover Letter One Pager Sample Example Document
The following slide displays the cover slide for the security system proposal, as it highlights the key details of the client requirement. Presenting you an exemplary Proposal For Enterprise Security System Cover Letter One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Cover Letter One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Next Step One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be tem meeting ,on-site visit etc. Presenting you an exemplary Proposal For Enterprise Security System Next Step One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Next Step One Pager Sample Example Document brilliant piece now.
Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Training Timeline One Pager Sample Example Document brilliant piece now.

Proposal For Enterprise Security System Your Investment One Pager Sample Example Document
The following slide displays the investment required by the origination to implement the new security system Presenting you an exemplary Proposal For Enterprise Security System Your Investment One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Your Investment One Pager Sample Example Document brilliant piece now.
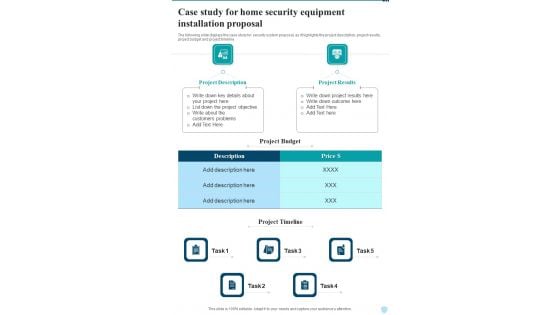
Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the case study for security system proposal, as it highlights the project description, project results, project budget and project timeline Presenting you an exemplary Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Case Study For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
Cover Letter For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the cover slide for the security system proposal, as it highlights the key details of the client requirement. Presenting you an exemplary Cover Letter For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Cover Letter For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.

Next Step For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be tem meeting ,on site visit etc. Presenting you an exemplary Next Step For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Step For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
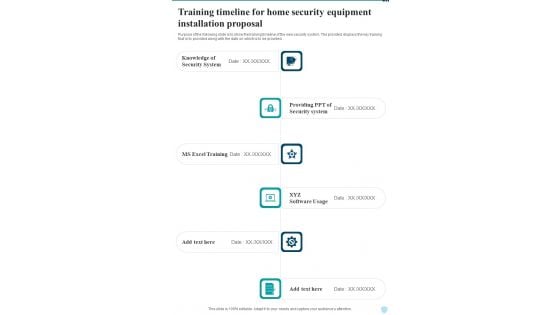
Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document
Purpose of the following slide is to show the training timeline of the new security system. The provided displays the key training that is to provided along with the date on which is to be provided. Presenting you an exemplary Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Training Timeline For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
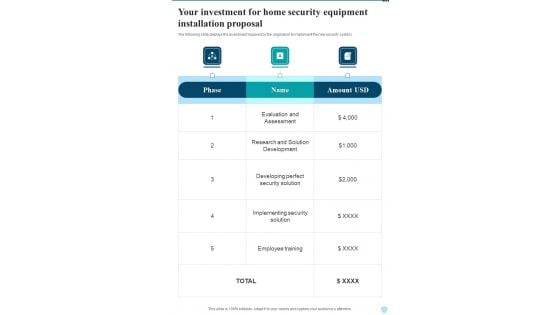
Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document
The following slide displays the investment required by the origination to implement the new security system. Presenting you an exemplary Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Your Investment For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
Six Steps Of System Development Service Delivery And Data Security Ppt PowerPoint Presentation Icon Slide Download
This is a six steps of system development service delivery and data security ppt powerpoint presentation icon slide download. This is a six stage process. The stages in this process are risk management, risk factors, risk variable.
Data Management And Security With Contract File Vector Icon Ppt PowerPoint Presentation Gallery Display PDF
Persuade your audience using this data management and security with contract file vector icon ppt powerpoint presentation gallery display pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including data management and security with contract file vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V
This slide highlights the different prospects responsible for growth of Defense market. The purpose of this slide is to cover different prospects related to growth of the industry. It covers digital and technological transformation, sustainable and climate concerns, product development innovation, and data-driven decision making. The Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide highlights the different prospects responsible for growth of Defense market. The purpose of this slide is to cover different prospects related to growth of the industry. It covers digital and technological transformation, sustainable and climate concerns, product development innovation, and data-driven decision making.
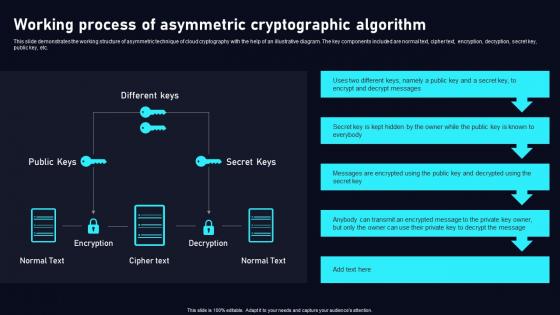
Working Process Of Asymmetric Cloud Data Security Using Cryptography Demonstration Pdf
This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulateWorking Process Of Asymmetric Cloud Data Security Using Cryptography Demonstration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc.
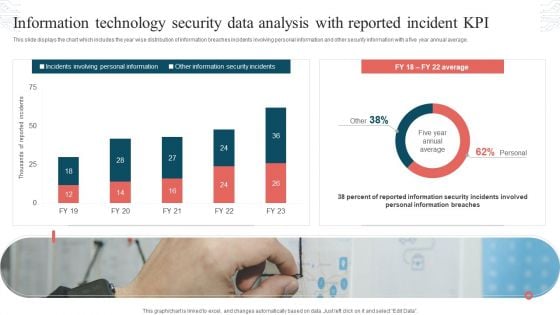
Information Technology Security Data Analysis With Reported Incident KPI Download PDF
This slide displays the chart which includes the year wise distribution of information breaches incidents involving personal information and other security information with a five year annual average. Showcasing this set of slides titled Information Technology Security Data Analysis With Reported Incident KPI Download PDF. The topics addressed in these templates are Incidents Involving, Personal Information, Other Information, Security Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Software Professional Working On Website Global Security Icon Ppt PowerPoint Presentation Infographic Template Images PDF
Persuade your audience using this software professional working on website global security icon ppt powerpoint presentation infographic template images pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including software professional working on website global security icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Three Steps For Business Security With Icons Ppt PowerPoint Presentation Infographic Template Samples PDF
Persuade your audience using this three steps for business security with icons ppt powerpoint presentation infographic template samples pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including security, feedback, profile. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
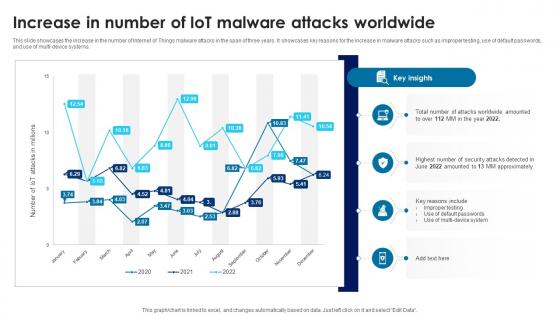
Building Trust With IoT Security Increase In Number Of IoT Malware Attacks Worldwide IoT SS V
This slide showcases the increase in the number of Internet of Things malware attacks in the span of three years. It showcases key reasons for the increase in malware attacks such as improper testing, use of default passwords, and use of multi-device systems. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Building Trust With IoT Security Increase In Number Of IoT Malware Attacks Worldwide IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases the increase in the number of Internet of Things malware attacks in the span of three years. It showcases key reasons for the increase in malware attacks such as improper testing, use of default passwords, and use of multi-device systems.

Recent Global Security Market Trends Behavior Ppt PowerPoint Presentation Styles Clipart
This is a recent global security market trends behavior ppt powerpoint presentation styles clipart. This is a six stage process. The stages in this process are management, marketing, business, strategy, planning.
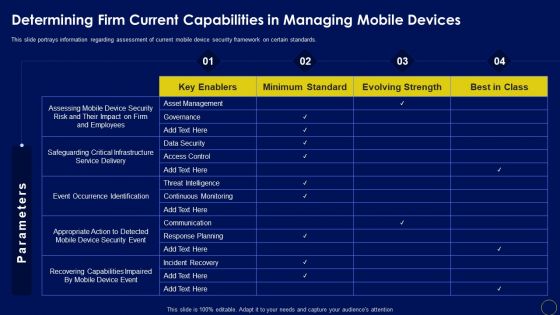
Determining Firm Current Capabilities In Managing Business Mobile Device Security Management Graphics PDF
This slide portrays information regarding assessment of current mobile device security framework on certain standards. Find a pre-designed and impeccable Determining Firm Current Capabilities In Managing Business Mobile Device Security Management Graphics PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Enterprise Content Management Security Cost And User Friendly Ppt Powerpoint Presentation Gallery Demonstration
This is a enterprise content management security cost and user friendly ppt powerpoint presentation gallery demonstration. This is a five stage process. The stages in this process are cms, content management system.
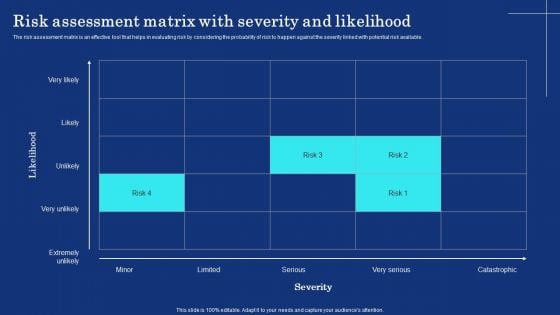
Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF
The risk assessment matrix is an effective tool that helps in evaluating risk by considering the probability of risk to happen against the severity linked with potential risk available. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF.
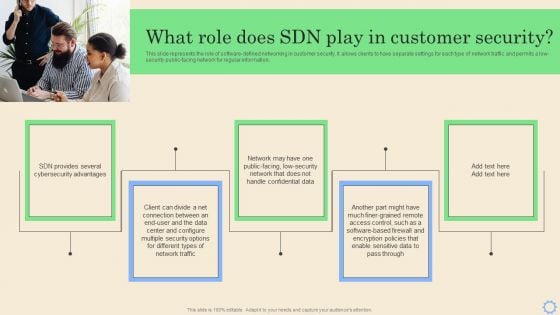
Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Security Access Control Iris Scanning System Ppt PowerPoint Presentation Show Gridlines
This is a security access control iris scanning system ppt powerpoint presentation show gridlines. This is a two stage process. The stages in this process are access rights, access management, business.
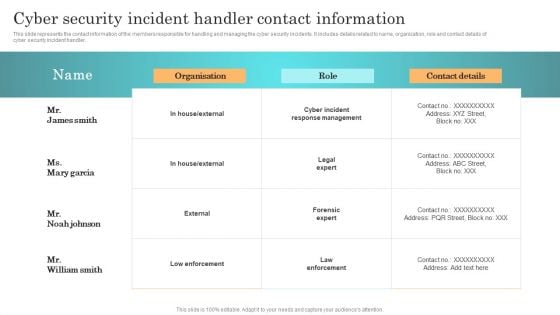
Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Get a simple yet stunning designed Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Prevention Of Information Overview Of Cyber Security Awareness Course Icons PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This Prevention Of Information Overview Of Cyber Security Awareness Course Icons PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
Icon Showcasing Information Availability Security Against Risks And Threats Designs PDF
Persuade your audience using this icon showcasing information availability security against risks and threats designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including icon showcasing information availability security against risks and threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V
The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Slidegeeks is here to make your presentations a breeze with Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks.

Building Trust With IoT Security Case Study 1 Enhancing Operational Technology By Integrating IoT SS V
This slide includes a case study of the company providing operational digital safety solutions integrating Cisco technology to enhance visibility at scale. It includes elements such as objectives of company , solutions implemented, and results. Slidegeeks is here to make your presentations a breeze with Building Trust With IoT Security Case Study 1 Enhancing Operational Technology By Integrating IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide includes a case study of the company providing operational digital safety solutions integrating Cisco technology to enhance visibility at scale. It includes elements such as objectives of company , solutions implemented, and results.
Cloud Data Storage Infrastructure And Security Ppt Powerpoint Presentation Model Show
This is a cloud data storage infrastructure and security ppt powerpoint presentation model show. This is a four stage process. The stages in this process are data management, data centre, storage system.
Clinical Testing Icon For Human Security Ppt PowerPoint Presentation Gallery Elements PDF
Persuade your audience using this clinical testing icon for human security ppt powerpoint presentation gallery elements pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including clinical testing icon for human security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Operations Compliance And Security Testing Ppt PowerPoint Presentation Slides Master Slide
This is a operations compliance and security testing ppt powerpoint presentation slides master slide. This is a three stage process. The stages in this process are quality assurance, quality analysis, qa, testing process, bugs analysis.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Template PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
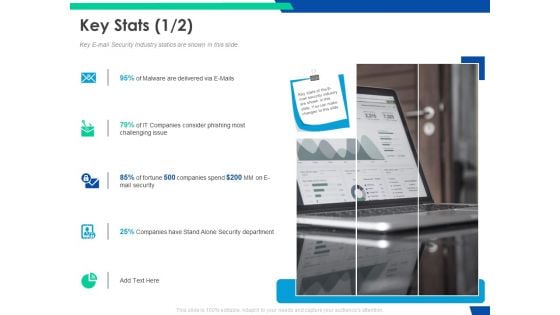
Cloud Based Email Security Market Report Key Stats Department Ppt Outline Brochure PDF
Key E mail Security Industry statics are shown in this slide. This is a cloud based email security market report key stats department ppt outline brochure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like key stats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Security Incident Alert Icon With Desktop Screen Ppt Gallery Layouts PDF
Persuade your audience using this Cyber Security Incident Alert Icon With Desktop Screen Ppt Gallery Layouts PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Incident, Alert Icon, Desktop Screen. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

United States Marine Officers Port Security Officers On Patrol 01 Ppt PowerPoint Presentation Model Good PDF
Pitch your topic with ease and precision using this united states marine officers port security officers on patrol 01 ppt powerpoint presentation model good pdf. This layout presents information on united states marine officers port security officers on patrol 01. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Five Horizontal Steps With Security Analysis Ppt PowerPoint Presentation Gallery Background Image PDF
Persuade your audience using this five horizontal steps with security analysis ppt powerpoint presentation gallery background image pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including segment offering, security, analysis. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
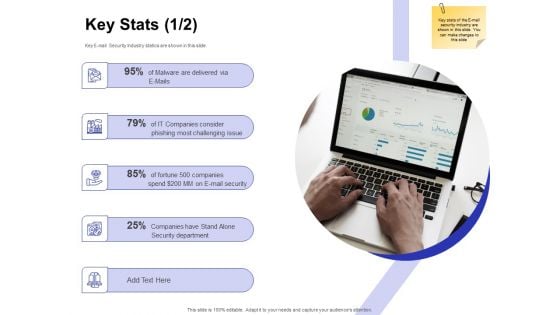
Global Cloud Based Email Security Market Key Stats Ppt Model Design Inspiration PDF
Presenting this set of slides with name global cloud based email security market key stats ppt model design inspiration pdf. This is a five stage process. The stages in this process are 25 percent companies have stand alone security department, 95 percent of malware are delivered via e mails. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Recent Global Security Market Trends Behavior Ppt PowerPoint Presentation Gallery Example
This is a recent global security market trends behavior ppt powerpoint presentation gallery example. This is a six stage process. The stages in this process are marketing, business, management.

Recent Global Security Market Trends Behavior Ppt PowerPoint Presentation Pictures Shapes
This is a recent global security market trends behavior ppt powerpoint presentation pictures shapes. This is a six stage process. The stages in this process are business, management, marketing.

Recent Global Security Market Trends Behavior Ppt PowerPoint Presentation Professional Picture
This is a recent global security market trends behavior ppt powerpoint presentation professional picture. This is a six stage process. The stages in this process are business, management, marketing.
Claims Management Security Contract Vector Icon Ppt PowerPoint Presentation Ideas Graphics Example PDF
Persuade your audience using this claims management security contract vector icon ppt powerpoint presentation ideas graphics example pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including claims management security contract vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cloud Data Security Management Vector Icon Ppt PowerPoint Presentation Gallery Vector PDF
Persuade your audience using this cloud data security management vector icon ppt powerpoint presentation gallery vector pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including cloud data security management vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Eight Steps Of Portfolio Management With Security Analysis Ppt PowerPoint Presentation Gallery Deck PDF
Persuade your audience using this eight steps of portfolio management with security analysis ppt powerpoint presentation gallery deck pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including security analysis, portfolio analysis, portfolio evaluation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
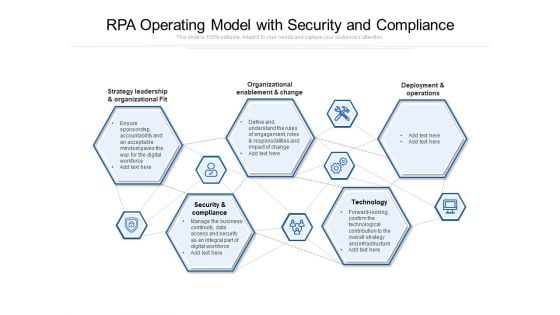
RPA Operating Model With Security And Compliance Ppt PowerPoint Presentation Model Styles PDF
Presenting rpa operating model with security and compliance ppt powerpoint presentation model styles pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including strategy leadership and organizational fit, organizational enablement and change, deployment and operations, security and compliance, technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
IT Security System Installation With Gear Wheel Vector Icon Ppt PowerPoint Presentation File Skills PDF
Presenting it security system installation with gear wheel vector icon ppt powerpoint presentation file skills pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including it security system installation with gear wheel vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Smart Phone Application Protected With IT Security Software Ppt PowerPoint Presentation File Graphic Images PDF
Persuade your audience using this smart phone application protected with it security software ppt powerpoint presentation file graphic images pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including smart phone application protected with it security software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
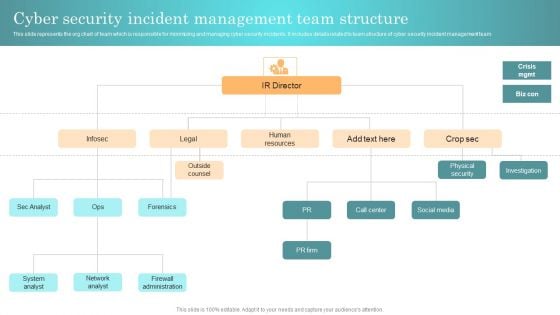
Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF
This slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Find highly impressive Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.


 Continue with Email
Continue with Email

 Home
Home


































