Executive Summary Security
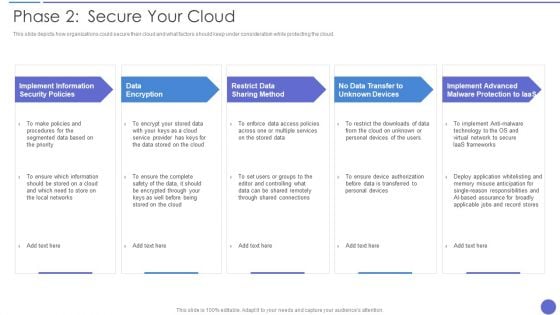
Phase 2 Secure Your Cloud Clipart PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Presenting Phase 2 Secure Your Cloud Clipart PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Encryption, Restrict Data Sharing Method, Implement Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
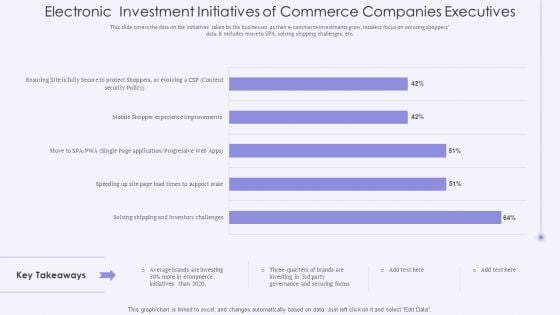
Electronic Investment Initiatives Of Commerce Companies Executives Professional PDF
This slide covers the data on the initiatives taken by the businesses as their e commerce investments grow, retailers focus on securing shoppers data. It includes move to SPA, solving shipping challenges, etc. Showcasing this set of slides titled Electronic Investment Initiatives Of Commerce Companies Executives Professional PDF. The topics addressed in these templates are Ecommerce, Investing, Average. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
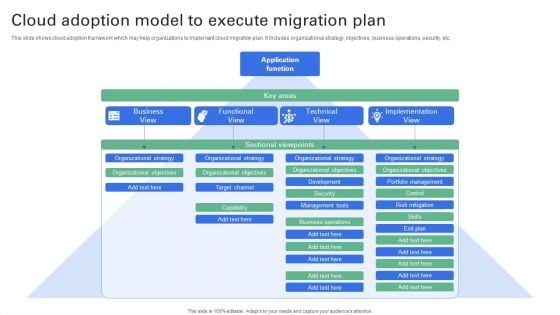
Cloud Adoption Model To Execute Migration Plan Designs PDF
This slide shows cloud adoption framework which may help organizations to implement cloud migration plan. It Includes organizational strategy, objectives, business operations, security, etc. Showcasing this set of slides titled Cloud Adoption Model To Execute Migration Plan Designs PDF. The topics addressed in these templates are Application, Business, Functional, Technical. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Application Test Execution Outcome Reporting To Improve Performance Sample PDF
This slide showcases a report presenting results of application test execution to improve performance and functionality. It includes key components such as summary, status, components, requirements, executions and passed executions. Showcasing this set of slides titled Application Test Execution Outcome Reporting To Improve Performance Sample PDF. The topics addressed in these templates are Login Attempts, Creating Confirmation, Email Requires Retesting. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
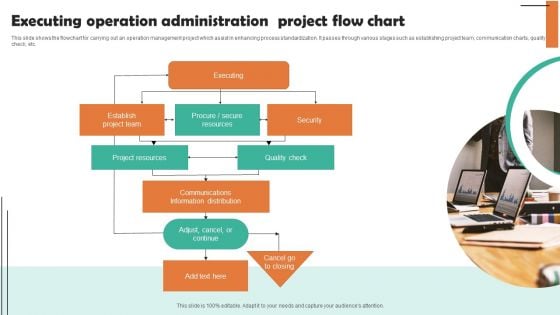
Executing Operation Administration Project Flow Chart Clipart PDF
This slide shows the flowchart for carrying out an operation management project which assist in enhancing process standardization. It passes through various stages such as establishing project team, communication charts, quality check, etc. Presenting Executing Operation Administration Project Flow Chart Clipart PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Executing Security, Establish Project Team. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

What Is Trusted Execution Environment Confidential Computing Technologies Microsoft Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Find a pre-designed and impeccable What Is Trusted Execution Environment Confidential Computing Technologies Microsoft Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.

Techniques For Executing Workflow Automation In Industry Procedures Complete Deck
This presentation deck contains fifty four professionally designed templates that eliminate the hassle of creating visually appealing presentations for you. It is your perfect option to communicate your thoughts in an easy-to-understand and effective manner. This Techniques For Executing Workflow Automation In Industry Procedures Complete Deck comes with a wide range of features like high-quality, graphics and 100 percent customizable layout. Graphs, charts, and polls are attention-grabbing visually interactive elements of this presentation bundle that will lock the eye of spectators on the screen. It also contains text styles, colors, background themes, and other design elements that perfectly complement each other and create a stunning template bundle. Take advantage of this PowerPoint Set to upgrade your presentation game and steer back your competitors. Our Techniques For Executing Workflow Automation In Industry Procedures Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cloud Network Technical Execution Plan Icon Mockup PDF
Showcasing this set of slides titled Cloud Network Technical Execution Plan Icon Mockup PDF. The topics addressed in these templates are Cloud Network, Technical, Execution Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Strategy To Execute Success Plan Business Creation PowerPoint Slides
We present our strategy to execute success plan business creation PowerPoint Slides.Download and present our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities. Download our Flow charts PowerPoint Templates because you can Organize your thoughts and illuminate your ideas accordingly. Use our Business PowerPoint Templates because project your ideas to you colleagues and complete the full picture. Present our Arrows PowerPoint Templates because it can convey all the options that present themselves. Download our Shapes PowerPoint Templates because infrastructure growth is an obvious requirement of today.inform your group on how exactly this potential is tailor made for you.Use these PowerPoint slides for presentations relating to Arrows, blank, business, chart, circular, circulation, concept, conceptual design, diagram, empty, executive, icon, idea, illustration, management, map mapping, model, numbers, organization, procedure, process, progression, resource sequence, sequential, seven, stages. The prominent colors used in the PowerPoint template are Orange, Gray, White. We assure you our strategy to execute success plan business creation PowerPoint Slides are Flirty. Use our design PowerPoint templates and PPT Slides are Classic. Use our strategy to execute success plan business creation PowerPoint Slides are Energetic. Professionals tell us our chart PowerPoint templates and PPT Slides are Endearing. Professionals tell us our strategy to execute success plan business creation PowerPoint Slides are Swanky. People tell us our circulation PowerPoint templates and PPT Slides are Luxurious. Investigate problems with our Strategy To Execute Success Plan Business Creation PowerPoint Slides. Download without worries with our money back guaranteee.
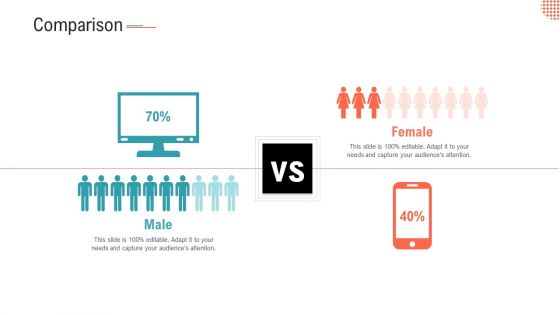
Executing A Safety Recognition Program Comparison Clipart PDF
Presenting executing a safety recognition program comparison clipart pdf. to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like male, female. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
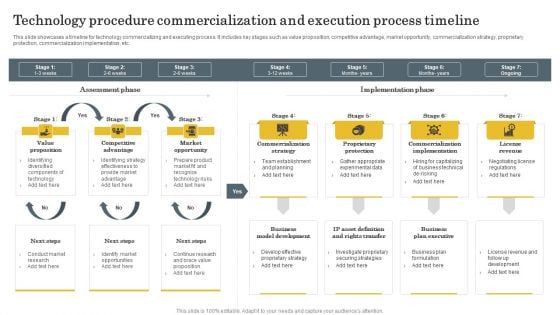
Technology Procedure Commercialization And Execution Process Timeline Information PDF
This slide showcases a timeline for technology commercializing and executing process. It includes key stages such as value proposition, competitive advantage, market opportunity, commercialization strategy, proprietary protection, commercialization implementation, etc. Pitch your topic with ease and precision using this Technology Procedure Commercialization And Execution Process Timeline Information PDF. This layout presents information on Value Proposition, Competitive Advantage, Proprietary Protection . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Executing A Safety Recognition Program Post It Notes Elements PDF
Presenting executing a safety recognition program post it notes elements pdf. to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like post it notes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
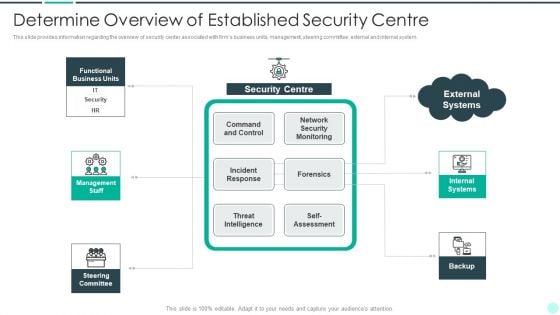
Executing Advance Data Analytics At Workspace Determine Overview Of Established Topics PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an awe inspiring pitch with this creative executing advance data analytics at workspace determine overview of established topics pdf bundle. Topics like determine overview of established security centre can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.
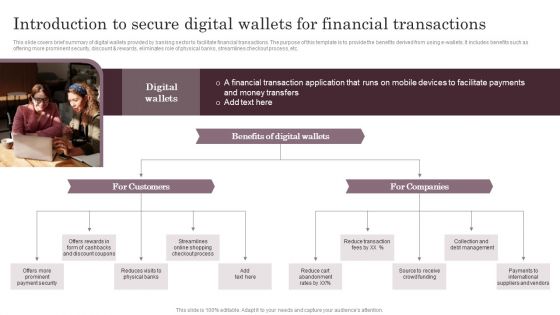
Introduction To Secure Digital Wallets For Financial Transactions Themes PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e-wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Introduction To Secure Digital Wallets For Financial Transactions Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Introduction To Secure Digital Wallets For Financial Transactions Guidelines PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Want to ace your presentation in front of a live audience Our Introduction To Secure Digital Wallets For Financial Transactions Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
Hacker Trying To Steal Secured Virtual Identity Sample PDF
Persuade your audience using this hacker trying to steal secured virtual identity sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including hacker trying to steal secured virtual identity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Business Reasons For Executing Identify And Access Management Technique Mockup PDF
This slide shows major reasons to execute IAM strategy in organization to ease complexity of management and reducing IT costs. It include reasons such as improved security system, simplifies information sharing and usability sue , etc. Persuade your audience using this Business Reasons For Executing Identify And Access Management Technique Mockup PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security System, Information Sharing, Usability Ease. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
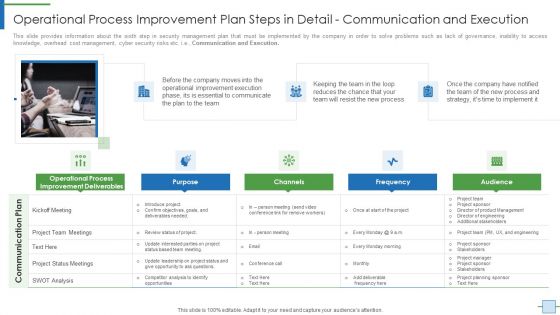
Operational Process Improvement Plan Steps In Detail Communication And Execution Information PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Communication and Execution. Presenting operational process improvement plan steps in detail communication and execution information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like communicate, team, process, reduces, strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Communication And Execution Guidelines PDF
This slide provides information about the Sixth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution. Presenting operational process improvement plan steps in detail communication and execution guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improvement, communicate, team, process, implement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
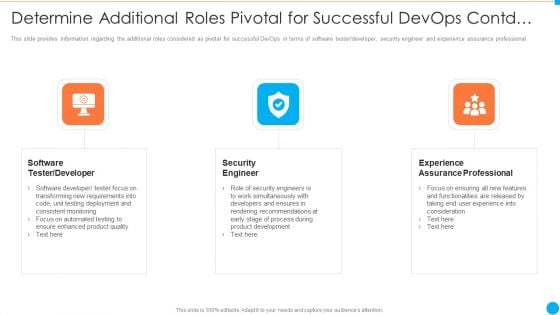
Determine Additional Roles Pivotal For Successful Devops Contd IT Infrastructure By Executing Devops Approach Elements PDF
This slide provides information regarding the additional roles considered as pivotal for successful DevOps in terms of software tester or developer, security engineer and experience assurance professional. Presenting determine additional roles pivotal for successful devops contd it infrastructure by executing devops approach elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like software tester or developer, security engineer, experience assurance professional. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
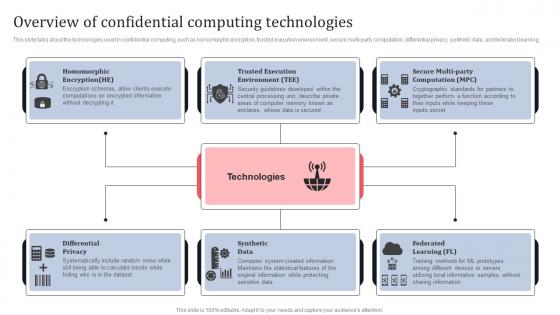
Overview Of Confidential Computing Technologies Secure Multi Party Designs Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Get a simple yet stunning designed Overview Of Confidential Computing Technologies Secure Multi Party Designs Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview Of Confidential Computing Technologies Secure Multi Party Designs Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
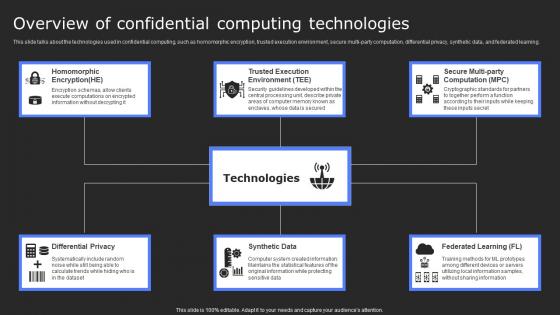
Overview Of Confidential Computing Technologies Secure Computing Framework Slides Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Present like a pro with Overview Of Confidential Computing Technologies Secure Computing Framework Slides Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
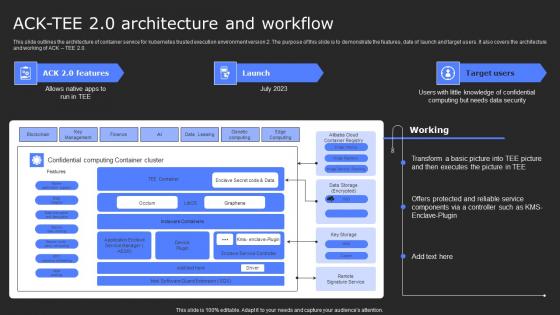
Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf
This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Boost your pitch with our creative Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.

Secure Computing Framework Confidential Computing Architecture Implementation Structure Pdf
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Secure Computing Framework Confidential Computing Architecture Implementation Structure Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.
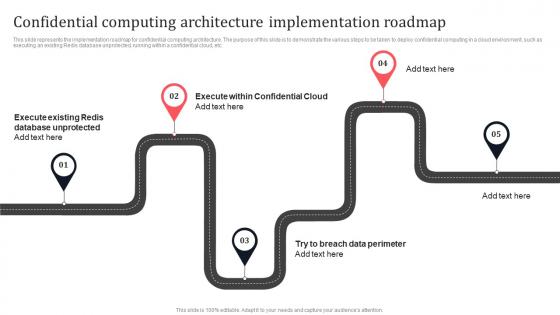
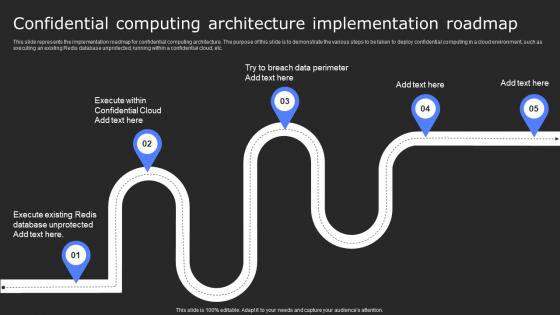
Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf
This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.
Confidential Computing Architecture Secure Computing Framework Themes Pdf
This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Confidential Computing Architecture Secure Computing Framework Themes Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.

Table Of Content For Executing A Safety Recognition Program Ppt Slides Graphics Example PDF
Presenting table of content for executing a safety recognition program ppt slides graphics example pdf. to provide visual cues and insights. Share and navigate important information on fourteen stages that need your due attention. This template can be used to pitch topics like security strategies for learning, awareness platform and cost, training formats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
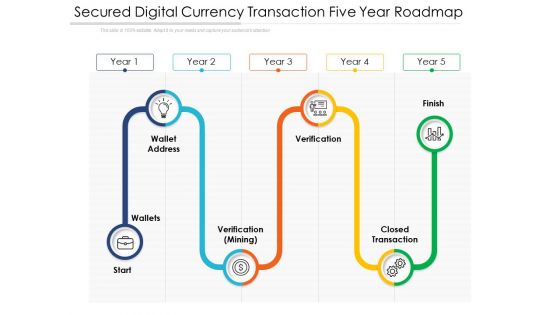
Secured Digital Currency Transaction Five Year Roadmap Themes
We present our secured digital currency transaction five year roadmap themes. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched secured digital currency transaction five year roadmap themes in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Steps Icons PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Mapping. Presenting operational efficiency execution strategy improve quality operational process improvement plan steps icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, applications, graphic software, accountability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
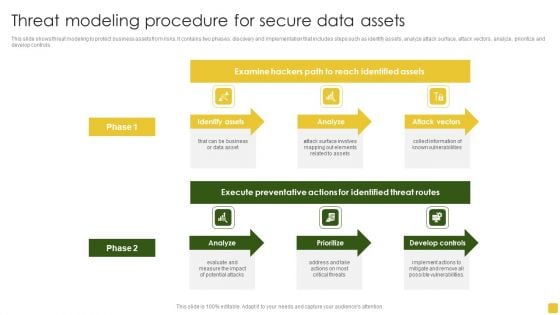
Threat Modeling Procedure For Secure Data Assets Formats PDF
This slide shows threat modeling to protect business assets from risks. It contains two phases discovery and implementation that includes steps such as identify assets, analyze attack surface, attack vectors, analyze, prioritize and develop controls. Pitch your topic with ease and precision using this Threat Modeling Procedure For Secure Data Assets Formats PDF. This layout presents information on Execute Preventative, Identified Threat, Develop Controls. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
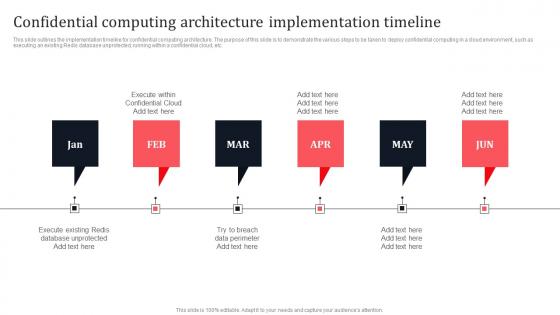
Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Find highly impressive Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.
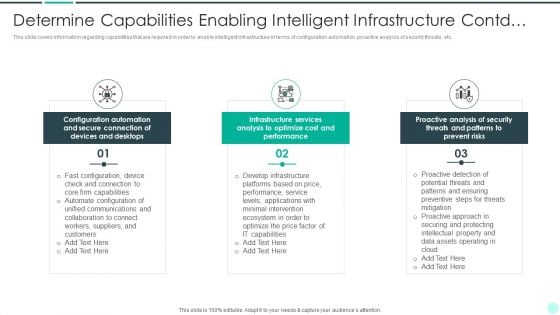
Executing Advance Data Analytics At Workspace Determine Capabilities Enabling Brochure PDF
This slide covers information regarding capabilities that are required in order to enable intelligent infrastructure in terms of configuration automation, proactive analysis of security threats, etc. Presenting executing advance data analytics at workspace determine capabilities enabling brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like secure, connection, devices, optimize. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
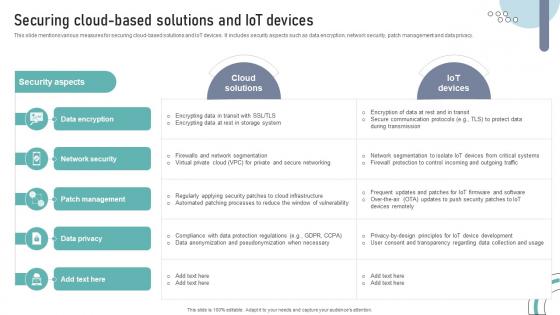
Securing Cloud Based Solutions And IOT Devices DT SS V
This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy. Slidegeeks has constructed Securing Cloud Based Solutions And IOT Devices DT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy.

Future Of Secure Web Gateway Technology Web Threat Protection System
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Future Of Secure Web Gateway Technology Web Threat Protection System and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.
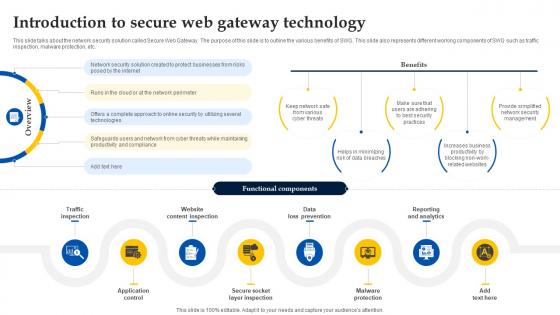
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
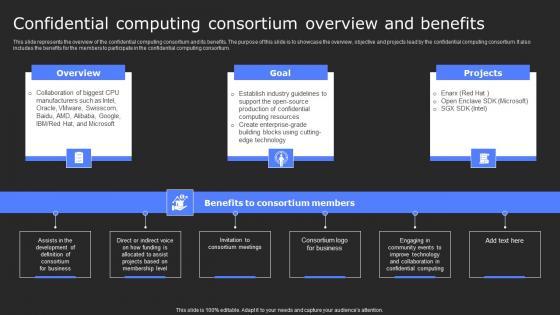
Confidential Computing Consortium Overview And Secure Computing Framework Inspiration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing Consortium Overview And Secure Computing Framework Inspiration Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
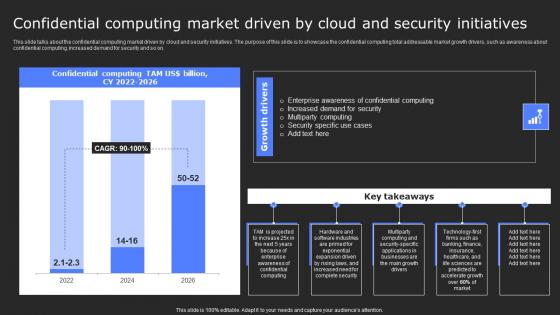
Secure Computing Framework Confidential Computing Market Driven By Mockup Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Find a pre-designed and impeccable Secure Computing Framework Confidential Computing Market Driven By Mockup Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.
Incident Management Chart Change Execution Plan Ppt PowerPoint Presentation Icon Diagrams PDF
This slide illustrates the incidents of the transition project. It covers the details such as explanation, status, priority, and resolution of the incident to ensure that technological change is successfully completed in the organization. Deliver and pitch your topic in the best possible manner with this Incident Management Chart Change Execution Plan Ppt PowerPoint Presentation Icon Diagrams PDF. Use them to share invaluable insights on Incident Status Priority, Cyber Attack Sensitive, Added Data Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Secure Computing Framework Ppt PowerPoint Presentation Complete Deck With Slides
You will save yourself your energy and hours of time when you choose to use this impactful PowerPoint Deck. This Secure Computing Framework Ppt PowerPoint Presentation Complete Deck With Slides has been tailor-made to your business needs which ensures that you will always be prepared for that next meeting. Worry can not touch you when you present in your area of expertise using this PPT Template Bundle. With a modern design and easy to follow structure, this PowerPoint Presentation has eighty three slides, which ensures that you can cover you need to without much work. Create your next presentation using this PPT Theme to deliver a memorable performance. Our Secure Computing Framework Ppt PowerPoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Executing Advance Data Analytics At Workspace How Firm Handle Variou Elements PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. Presenting executing advance data analytics at workspace how firm handle variou elements pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like employee training, coordination, implement, behavioral. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
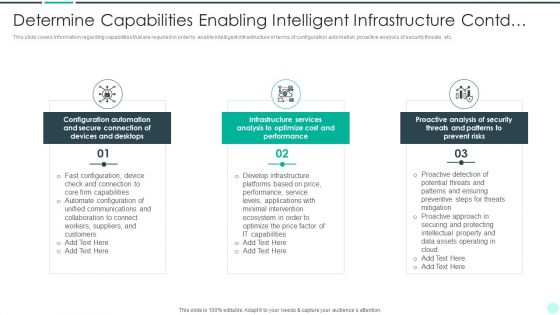
Executing Advance Data Analytics At Workspace Determine Capabilities Enabling Sample PDF
This slide covers information regarding capabilities that are required in order to enable intelligent infrastructure in terms of configuration automation, proactive analysis of security threats, etc. Presenting executing advance data analytics at workspace determine capabilities enabling sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like capabilities, connection, communications, collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Executing Advance Data Analytics At Workspace Facilities Offered By Implementation Sample PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting executing advance data analytics at workspace facilities offered by implementation sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like investigation, prevention, organization, intelligence, collaborate . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Securing Your Data with Tokenization Powerpoint Presentation Slides PPT Example
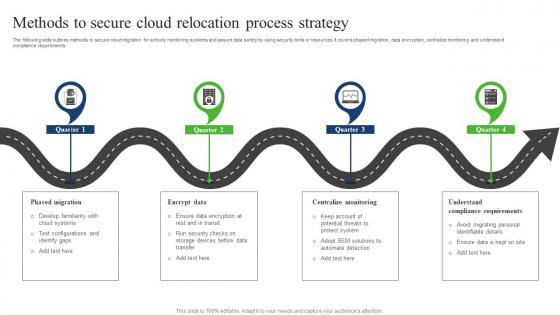
Methods To Secure Cloud Relocation Process Strategy Sample Pdf
The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements. Showcasing this set of slides titled Methods To Secure Cloud Relocation Process Strategy Sample Pdf. The topics addressed in these templates are Centralize Monitoring, Understand Compliance Requirements, Phased Migration, Encrypt Data . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements.

Zero Trust Model Comparison Between ZTNA And Secure Access Service
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Model Comparison Between ZTNA And Secure Access Service and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.
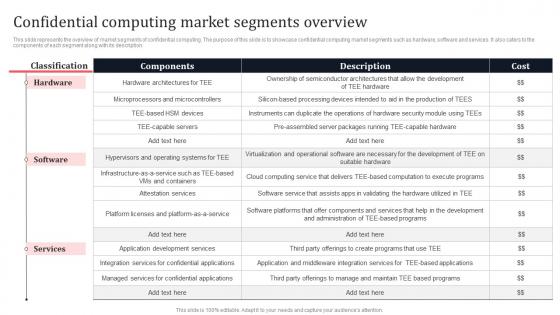
Confidential Computing Market Segments Overview Secure Multi Party Background Pdf
This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Confidential Computing Market Segments Overview Secure Multi Party Background Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Confidential Computing Market Segments Overview Secure Multi Party Background Pdf This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description.
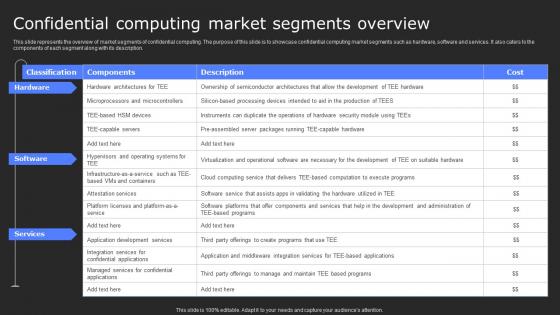
Confidential Computing Market Segments Overview Secure Computing Framework Structure Pdf
This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description. his modern and well-arranged Confidential Computing Market Segments Overview Secure Computing Framework Structure Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description.
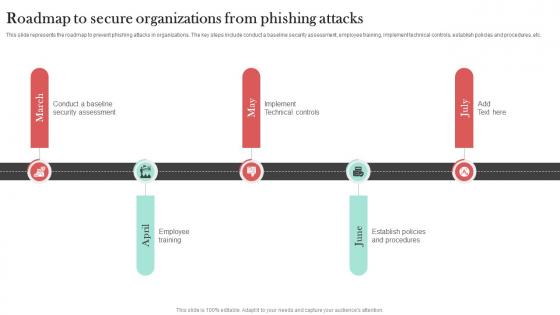
Roadmap To Secure Organizations Man In The Middle Phishing IT
This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Roadmap To Secure Organizations Man In The Middle Phishing IT and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc.

Introduction To Secure Web Gateway Technology Web Threat Protection System
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. This Introduction To Secure Web Gateway Technology Web Threat Protection System is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Introduction To Secure Web Gateway Technology Web Threat Protection System features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.

Prominent Users Of Secure Web Gateway Web Threat Protection System
This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Retrieve professionally designed Prominent Users Of Secure Web Gateway Web Threat Protection System to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.
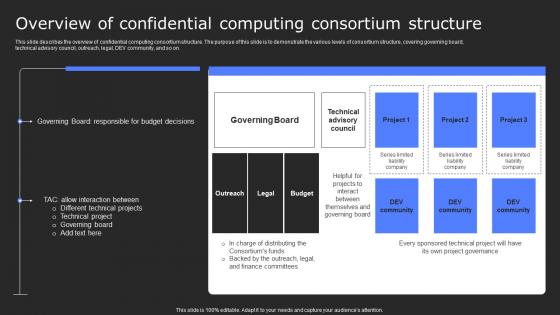
Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on.
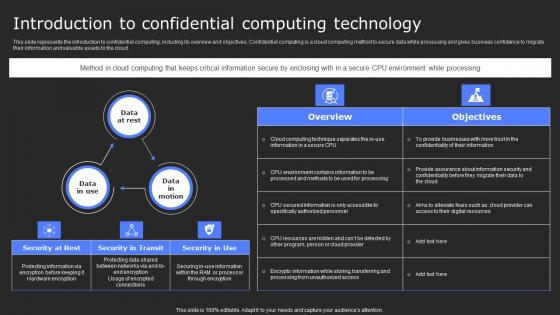
Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Boost your pitch with our creative Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
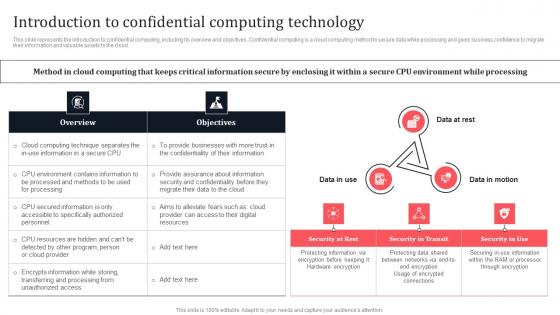
Introduction To Confidential Computing Technology Secure Multi Party Download Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Do you know about Slidesgeeks Introduction To Confidential Computing Technology Secure Multi Party Download Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
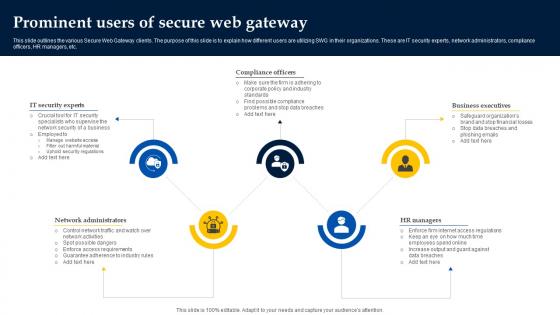
Web Access Control Solution Prominent Users Of Secure Web Gateway
Do you know about Slidesgeeks Web Access Control Solution Prominent Users Of Secure Web Gateway These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.
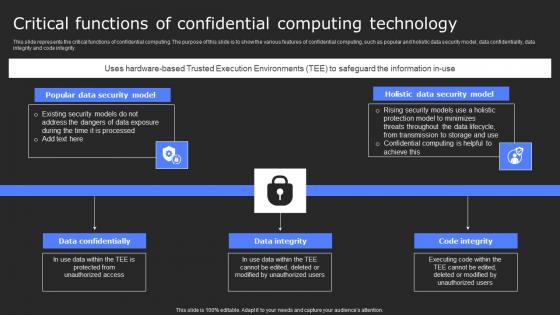
Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Are you searching for a Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf from Slidegeeks today. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
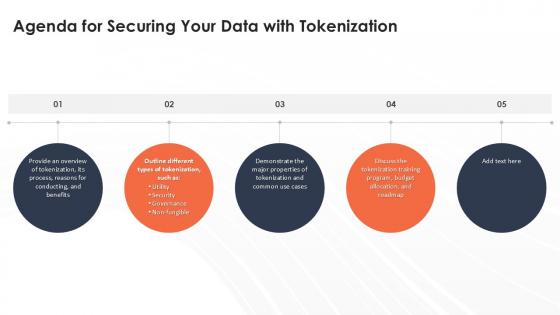
Agenda For Securing Your Data With Tokenization Ppt Template
Create an editable Agenda For Securing Your Data With Tokenization Ppt Template that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agenda For Securing Your Data With Tokenization Ppt Template is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Our Agenda For Securing Your Data With Tokenization Ppt Template are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
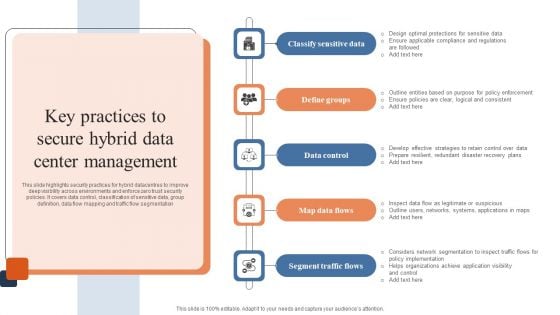
Key Practices To Secure Hybrid Data Center Management Ideas PDF
This slide highlights security practices for hybrid datacentres to improve deep visibility across environments and enforce zero trust security policies. It covers data control, classification of sensitive data, group definition, data flow mapping and traffic flow segmentation. Presenting Key Practices To Secure Hybrid Data Center Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Classify Sensitive Data, Define Groups, Data Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb
Introducing our well designed Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Sdlc Policy Template. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
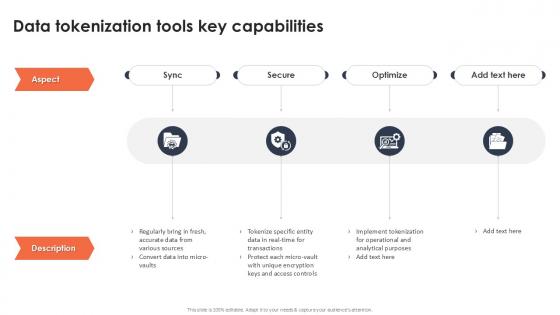
Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint
If you are looking for a format to display your unique thoughts, then the professionally designed Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Our Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.


 Continue with Email
Continue with Email

 Home
Home


































