Figures
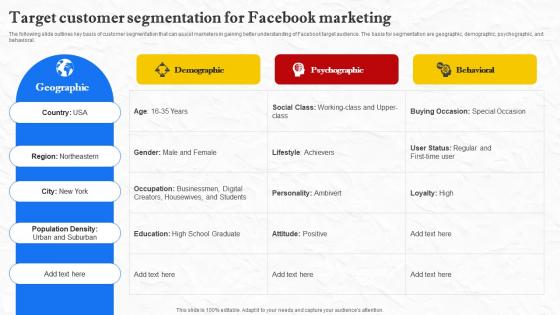
Facebook Marketing Techniques Target Customer Segmentation For Facebook Marketing Strategy SS V
The following slide outlines key basis of customer segmentation that can assist marketers in gaining better understanding of Facebook target audience. The basis for segmentation are geographic, demographic, psychographic, and behavioral. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Facebook Marketing Techniques Target Customer Segmentation For Facebook Marketing Strategy SS V can be your best option for delivering a presentation. Represent everything in detail using Facebook Marketing Techniques Target Customer Segmentation For Facebook Marketing Strategy SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide outlines key basis of customer segmentation that can assist marketers in gaining better understanding of Facebook target audience. The basis for segmentation are geographic, demographic, psychographic, and behavioral.

Facebook Marketing Techniques User Generated Content Example To Increase Customer Strategy SS V
The following slide outlines ideal user generated content which can be used by companies to build engagement, trust and community around brand. It covers information about practices such as asking for feedback, sharing customer success stories, collaborating with social media influencers, and hosting live events. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Facebook Marketing Techniques User Generated Content Example To Increase Customer Strategy SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide outlines ideal user generated content which can be used by companies to build engagement, trust and community around brand. It covers information about practices such as asking for feedback, sharing customer success stories, collaborating with social media influencers, and hosting live events.
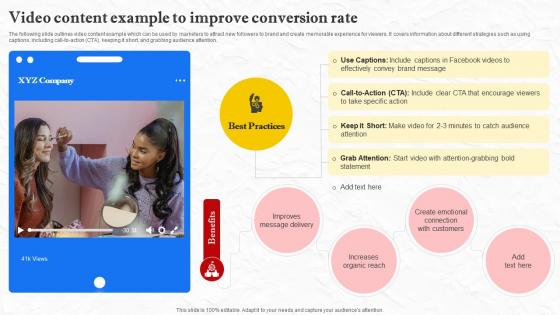
Facebook Marketing Techniques Video Content Example To Improve Conversion Rate Strategy SS V
The following slide outlines video content example which can be used by marketers to attract new followers to brand and create memorable experience for viewers. It covers information about different strategies such as using captions, including call-to-action CTA , keeping it short, and grabbing audience attention. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Facebook Marketing Techniques Video Content Example To Improve Conversion Rate Strategy SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Facebook Marketing Techniques Video Content Example To Improve Conversion Rate Strategy SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide outlines video content example which can be used by marketers to attract new followers to brand and create memorable experience for viewers. It covers information about different strategies such as using captions, including call-to-action CTA , keeping it short, and grabbing audience attention.
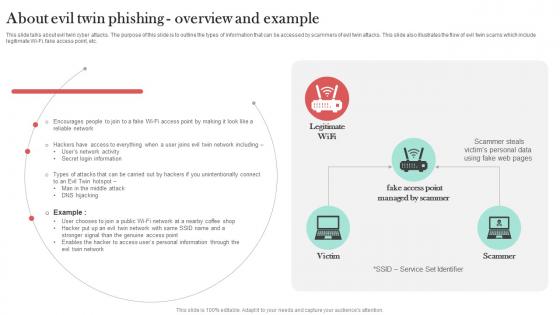
About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT
This slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc.
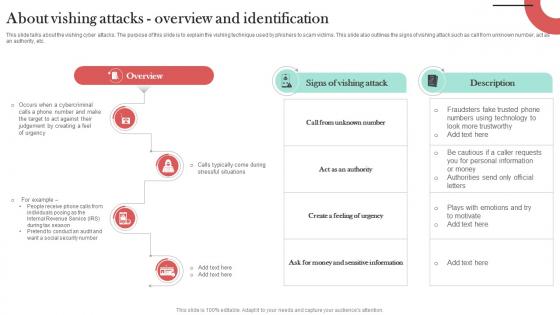
About Vishing Attacks Overview And Identification Man In The Middle Phishing IT
This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Vishing Attacks Overview And Identification Man In The Middle Phishing IT can be your best option for delivering a presentation. Represent everything in detail using About Vishing Attacks Overview And Identification Man In The Middle Phishing IT and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc.

Benefits Of Comprehensive Training Programs Man In The Middle Phishing IT
This slide outlines the benefits of comprehensive training programs in organizations. These include align with companys database, instructional library, auto-enrolment service, inform about real risks, track and evaluate and plan a year ahead. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Benefits Of Comprehensive Training Programs Man In The Middle Phishing IT and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the benefits of comprehensive training programs in organizations. These include align with companys database, instructional library, auto-enrolment service, inform about real risks, track and evaluate and plan a year ahead.
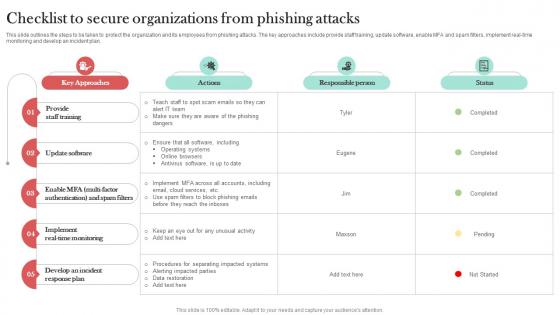
Checklist To Secure Organizations From Man In The Middle Phishing IT
This slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Checklist To Secure Organizations From Man In The Middle Phishing IT template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Checklist To Secure Organizations From Man In The Middle Phishing IT that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan.
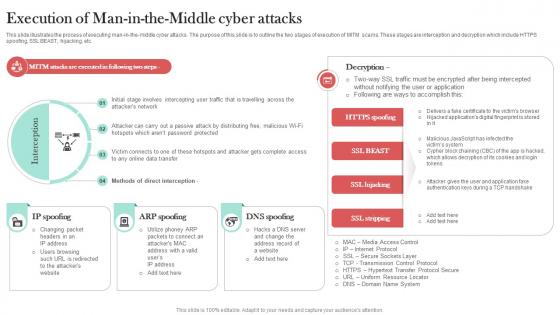
Execution Of Man In The Middle Cyber Attacks Man In The Middle Phishing IT
This slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption which include HTTPS spoofing, SSL BEAST, hijacking, etc. Welcome to our selection of the Execution Of Man In The Middle Cyber Attacks Man In The Middle Phishing IT. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption which include HTTPS spoofing, SSL BEAST, hijacking, etc.
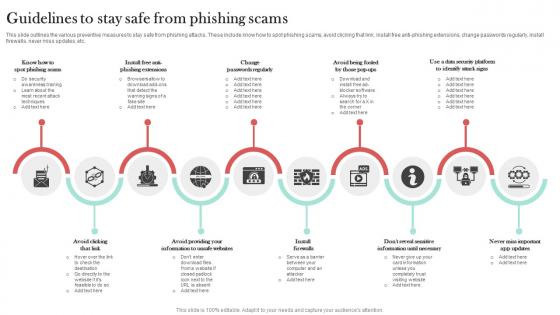
Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT
This slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link, install free anti-phishing extensions, change passwords regularly, install firewalls, never miss updates, etc. Explore a selection of the finest Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link, install free anti-phishing extensions, change passwords regularly, install firewalls, never miss updates, etc.
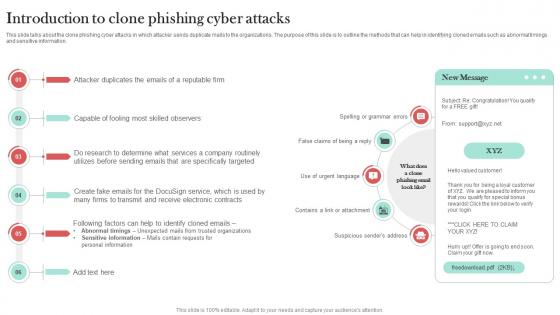
Introduction To Clone Phishing Cyber Man In The Middle Phishing IT
This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information. This Introduction To Clone Phishing Cyber Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information.

Overview Of Business Disruption Caused Man In The Middle Phishing IT
This slide discusses the impact of phishing attacks on businesses. The purpose of this slide is to outline the amount of money lost by well-reputed companies due to phishing scams. The companies included are Facebook and Google, Crelan Bank in Belgium, etc. Create an editable Overview Of Business Disruption Caused Man In The Middle Phishing IT that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Overview Of Business Disruption Caused Man In The Middle Phishing IT is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide discusses the impact of phishing attacks on businesses. The purpose of this slide is to outline the amount of money lost by well-reputed companies due to phishing scams. The companies included are Facebook and Google, Crelan Bank in Belgium, etc.
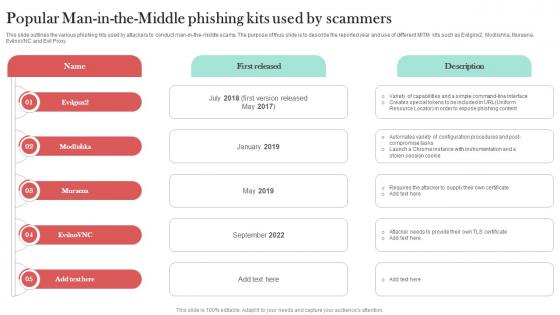
Popular Man In The Middle Phishing Kits Man In The Middle Phishing IT
This slide outlines the various phishing kits used by attackers to conduct man-in-the-middle scams. The purpose of thus slide is to describe the reported year and use of different MITM kits such as Evilginx2, Modlishka, Muraena, EvilnoVNC and Evil Proxy. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Popular Man In The Middle Phishing Kits Man In The Middle Phishing IT a try. Our experts have put a lot of knowledge and effort into creating this impeccable Popular Man In The Middle Phishing Kits Man In The Middle Phishing IT. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the various phishing kits used by attackers to conduct man-in-the-middle scams. The purpose of thus slide is to describe the reported year and use of different MITM kits such as Evilginx2, Modlishka, Muraena, EvilnoVNC and Evil Proxy.
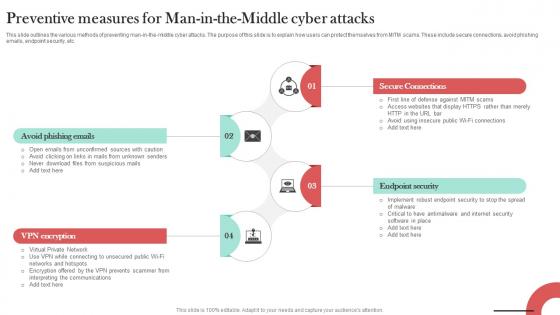
Preventive Measures For Man In The Middle Man In The Middle Phishing IT
This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Get a simple yet stunning designed Preventive Measures For Man In The Middle Man In The Middle Phishing IT. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Preventive Measures For Man In The Middle Man In The Middle Phishing IT can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc.
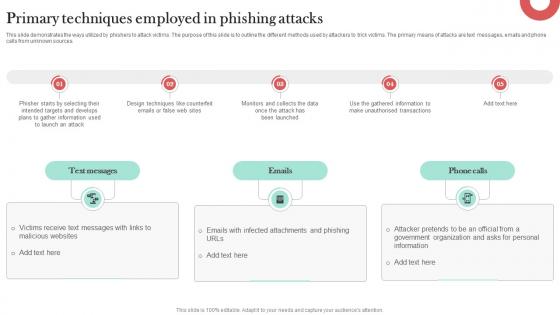
Primary Techniques Employed In Phishing Man In The Middle Phishing IT
This slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources. Slidegeeks is here to make your presentations a breeze with Primary Techniques Employed In Phishing Man In The Middle Phishing IT With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources.
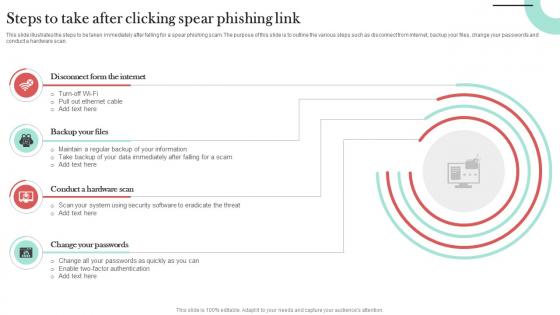
Steps To Take After Clicking Spear Phishing Link Man In The Middle Phishing IT
This slide illustrates the steps to be taken immediately after falling for a spear phishing scam. The purpose of this slide is to outline the various steps such as disconnect from internet, backup your files, change your passwords and conduct a hardware scan. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Steps To Take After Clicking Spear Phishing Link Man In The Middle Phishing IT and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide illustrates the steps to be taken immediately after falling for a spear phishing scam. The purpose of this slide is to outline the various steps such as disconnect from internet, backup your files, change your passwords and conduct a hardware scan.

Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT
This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Retrieve professionally designed Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names.
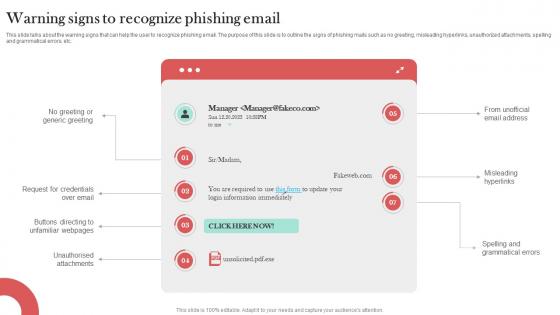
Warning Signs To Recognize Phishing Email Man In The Middle Phishing IT
This slide talks about the warning signs that can help the user to recognize phishing email. The purpose of this slide is to outline the signs of phishing mails such as no greeting, misleading hyperlinks, unauthorized attachments, spelling and grammatical errors, etc. Slidegeeks has constructed Warning Signs To Recognize Phishing Email Man In The Middle Phishing IT after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide talks about the warning signs that can help the user to recognize phishing email. The purpose of this slide is to outline the signs of phishing mails such as no greeting, misleading hyperlinks, unauthorized attachments, spelling and grammatical errors, etc.

Why Businesses Fall Victim To Phishing Man In The Middle Phishing IT
This slide outlines the various reasons responsible for businesses to fall victim to different phishing attacks. These include inadequate employee training, never evaluate the success of the training, careless browsing habits of the employees, etc. Presenting this PowerPoint presentation, titled Why Businesses Fall Victim To Phishing Man In The Middle Phishing IT, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Why Businesses Fall Victim To Phishing Man In The Middle Phishing IT. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Why Businesses Fall Victim To Phishing Man In The Middle Phishing IT that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the various reasons responsible for businesses to fall victim to different phishing attacks. These include inadequate employee training, never evaluate the success of the training, careless browsing habits of the employees, etc.

Increasing Business Awareness Establishing Effective Partnerships With Local Strategy SS V
This slide outlines a partnership program for establishing effective partnerships with local businesses to promote insurance companies and sell policies. It includes information about aspects such as partner name, partnership benefits, target audience and duration. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Increasing Business Awareness Establishing Effective Partnerships With Local Strategy SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Increasing Business Awareness Establishing Effective Partnerships With Local Strategy SS V today and make your presentation stand out from the rest This slide outlines a partnership program for establishing effective partnerships with local businesses to promote insurance companies and sell policies. It includes information about aspects such as partner name, partnership benefits, target audience and duration.

Increasing Business Awareness Implementing SEO Basics To Rank Website Higher Strategy SS V
This slide presents an outline of a strategic SEO plan to optimize websites to rank better on search engines. It includes information about SEO basics such as keyword research, content creation, on-page optimization, mobile responsiveness, site speed, and link building. This Increasing Business Awareness Implementing SEO Basics To Rank Website Higher Strategy SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Increasing Business Awareness Implementing SEO Basics To Rank Website Higher Strategy SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide presents an outline of a strategic SEO plan to optimize websites to rank better on search engines. It includes information about SEO basics such as keyword research, content creation, on-page optimization, mobile responsiveness, site speed, and link building.

Increasing Business Awareness Setting Up Unique Identity Of Brand To Create Strategy SS V
This slide presents an outline of a plan to create a unique value proposition and set a brand identity to stand out amongst the competition. It includes information about brand values, unique value propositions, logo concepts, and taglines. If you are looking for a format to display your unique thoughts, then the professionally designed Increasing Business Awareness Setting Up Unique Identity Of Brand To Create Strategy SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Increasing Business Awareness Setting Up Unique Identity Of Brand To Create Strategy SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide presents an outline of a plan to create a unique value proposition and set a brand identity to stand out amongst the competition. It includes information about brand values, unique value propositions, logo concepts, and taglines.

On Ramp Option 3 The Network Zero Trust Network Access
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than On Ramp Option 3 The Network Zero Trust Network Access. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab On Ramp Option 3 The Network Zero Trust Network Access today and make your presentation stand out from the rest This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
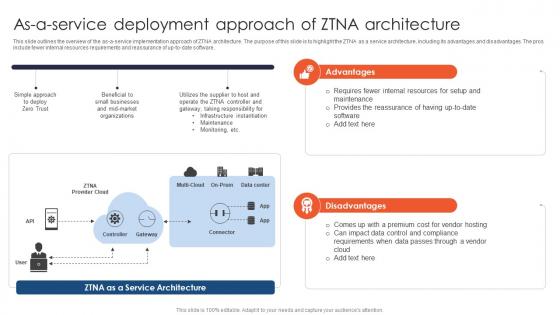
Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software.
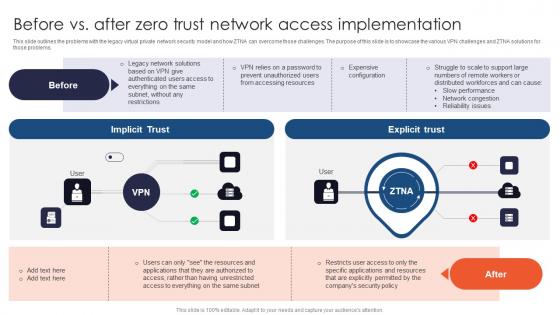
Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Network Access Challenges Of VPN Based Remote Access Solutions
This slide outlines the limitations of virtual private network-based remote access services. The purpose of this slide is to showcase the various challenges of the VPN network system and how the zero trust network model can overcome those issues. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Zero Trust Network Access Challenges Of VPN Based Remote Access Solutions was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Zero Trust Network Access Challenges Of VPN Based Remote Access Solutions. This slide outlines the limitations of virtual private network-based remote access services. The purpose of this slide is to showcase the various challenges of the VPN network system and how the zero trust network model can overcome those issues.

Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Zero Trust Network Access Future And Emerging Trends In ZTNA Model
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Future And Emerging Trends In ZTNA Model, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Future And Emerging Trends In ZTNA Model. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Future And Emerging Trends In ZTNA Model that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.

Zero Trust Network Access On Ramp Option 1 User And Device Identity
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. Boost your pitch with our creative Zero Trust Network Access On Ramp Option 1 User And Device Identity. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.

Zero Trust Network Access Roadmap To Implement Zero Trust Network Access Model
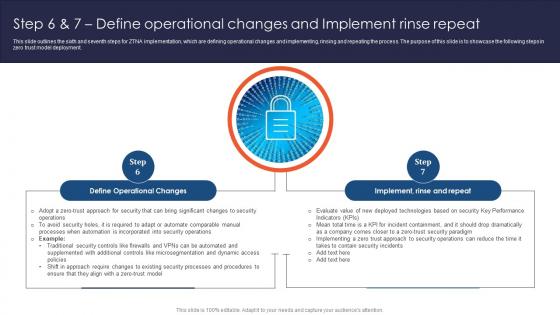
Zero Trust Network Access Step 6 And 7 Define Operational Changes And Implement Rinse Repeat
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Step 6 And 7 Define Operational Changes And Implement Rinse Repeat and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment.

Zero Trust Network Access Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Steps To Implement Zero Trust Network Access Model template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Steps To Implement Zero Trust Network Access Model that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.
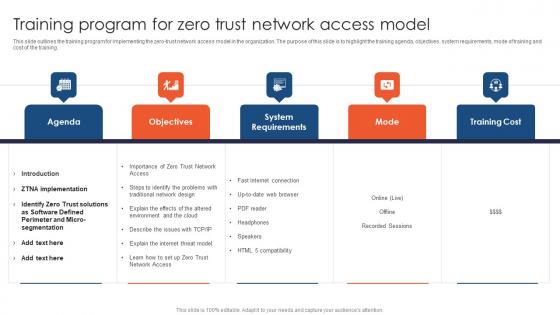
Zero Trust Network Access Training Program For Zero Trust Network Access Model
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Explore a selection of the finest Zero Trust Network Access Training Program For Zero Trust Network Access Model here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Training Program For Zero Trust Network Access Model to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.

Zero Trust Network Access Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Working Of Zero Trust Network Access Model, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Working Of Zero Trust Network Access Model. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Working Of Zero Trust Network Access Model that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

CASB 2 0 IT API Scanning CASB Deployment Model
This slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs. Want to ace your presentation in front of a live audience Our CASB 2 0 IT API Scanning CASB Deployment Model can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs.

CASB 2 0 IT CASB As A Streamline Endpoint Protection Solution
This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration. Slidegeeks is here to make your presentations a breeze with CASB 2 0 IT CASB As A Streamline Endpoint Protection Solution With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration.
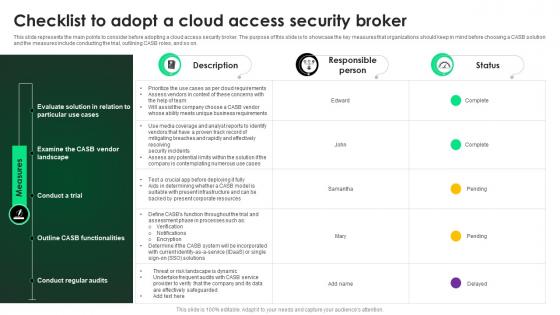
CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers. This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on.
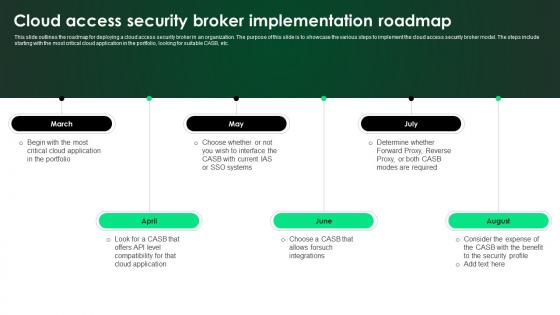
CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Welcome to our selection of the CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc.
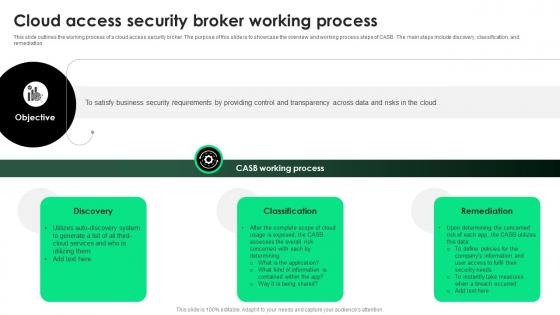
CASB 2 0 IT Cloud Access Security Broker Working Process
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download CASB 2 0 IT Cloud Access Security Broker Working Process to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the CASB 2 0 IT Cloud Access Security Broker Working Process. This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation.

CASB 2 0 IT Pros And Cons Of API Scanning CASB Deployment
This slide outlines the advantages and disadvantages of the API scanning cloud access security broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc. Slidegeeks is here to make your presentations a breeze with CASB 2 0 IT Pros And Cons Of API Scanning CASB Deployment With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the advantages and disadvantages of the API scanning cloud access security broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc.
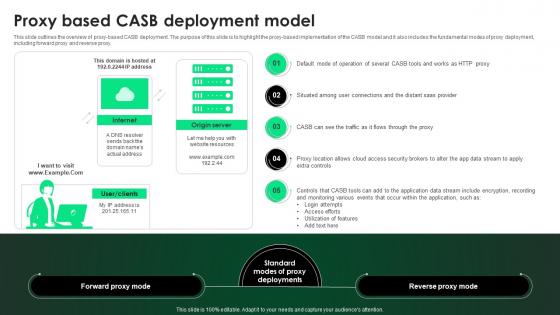
CASB 2 0 IT Proxy Based CASB Deployment Model
This slide outlines the overview of proxy-based CASB deployment. The purpose of this slide is to highlight the proxy-based implementation of the CASB model and it also includes the fundamental modes of proxy deployment, including forward proxy and reverse proxy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CASB 2 0 IT Proxy Based CASB Deployment Model. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CASB 2 0 IT Proxy Based CASB Deployment Model today and make your presentation stand out from the rest This slide outlines the overview of proxy-based CASB deployment. The purpose of this slide is to highlight the proxy-based implementation of the CASB model and it also includes the fundamental modes of proxy deployment, including forward proxy and reverse proxy.
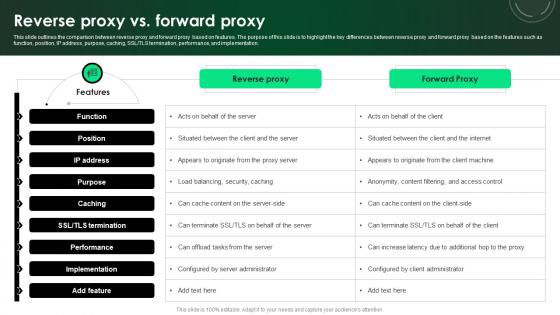
CASB 2 0 IT Reverse Proxy Vs Forward Proxy
This slide outlines the comparison between reverse proxy and forward proxy based on features. The purpose of this slide is to highlight the key differences between reverse proxy and forward proxy based on the features such as function, position, IP address, purpose, caching, SSL or TLS termination, performance, and implementation. If you are looking for a format to display your unique thoughts, then the professionally designed CASB 2 0 IT Reverse Proxy Vs Forward Proxy is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CASB 2 0 IT Reverse Proxy Vs Forward Proxy and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the comparison between reverse proxy and forward proxy based on features. The purpose of this slide is to highlight the key differences between reverse proxy and forward proxy based on the features such as function, position, IP address, purpose, caching, SSL or TLS termination, performance, and implementation.

CASB 2 0 IT Shadow It Management Lifecycle Overview
This slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download CASB 2 0 IT Shadow It Management Lifecycle Overview and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring.

CASB 2 0 IT Steps To Deploy Cloud Access Security Broker
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CASB 2 0 IT Steps To Deploy Cloud Access Security Broker template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CASB 2 0 IT Steps To Deploy Cloud Access Security Broker that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model.
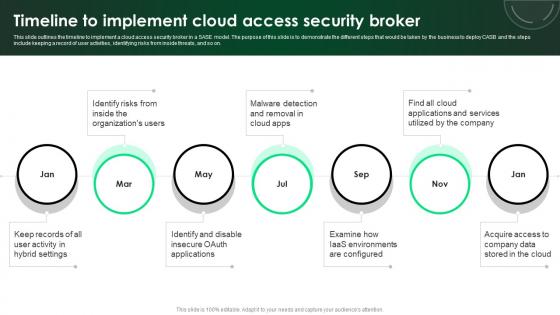
CASB 2 0 IT Timeline To Implement Cloud Access Security Broker
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Timeline To Implement Cloud Access Security Broker. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on.

CASB 2 0 IT Why CASB Is Important For Businesses
This slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the cloud access security broker model, including increased cloud adoption, better security, compliance, and cost-effective and centralized management. This CASB 2 0 IT Why CASB Is Important For Businesses is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CASB 2 0 IT Why CASB Is Important For Businesses features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the cloud access security broker model, including increased cloud adoption, better security, compliance, and cost-effective and centralized management.

About Hot Crypto Wallets Overview And Types Cryptocurrency Management With Blockchain
This slide discusses the key takeaways to keep in mind regarding Hot Wallets. This slide outlines that hot wallets which are connected to the internet and very easy to access are beginner-friendly and enable the storing, receiving, and sending of tokens.Create an editable About Hot Crypto Wallets Overview And Types Cryptocurrency Management With Blockchain that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Hot Crypto Wallets Overview And Types Cryptocurrency Management With Blockchain is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide discusses the key takeaways to keep in mind regarding Hot Wallets. This slide outlines that hot wallets which are connected to the internet and very easy to access are beginner-friendly and enable the storing, receiving, and sending of tokens.
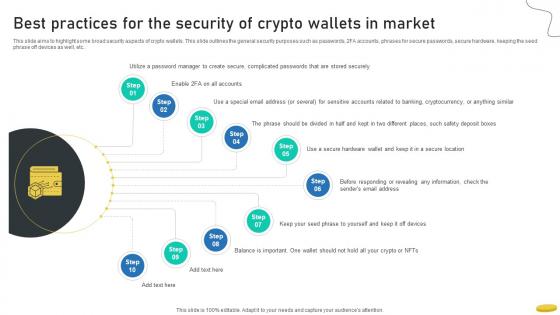
Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain
This slide aims to highlight some broad security aspects of crypto wallets. This slide outlines the general security purposes such as passwords, 2FA accounts, phrases for secure passwords, secure hardware, keeping the seed phrase off devices as well, etc.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain today and make your presentation stand out from the rest This slide aims to highlight some broad security aspects of crypto wallets. This slide outlines the general security purposes such as passwords, 2FA accounts, phrases for secure passwords, secure hardware, keeping the seed phrase off devices as well, etc.

Complete Us Crypto Tax Guide Cryptocurrency Management With Blockchain
This slide discusses the taxes in the crypto market. The purpose of this slide is to outline the crypto tax criteria used in the United States of America on Bitcoin and Crypto. It also includes the tax range for long-term and short-term capital gains.If you are looking for a format to display your unique thoughts, then the professionally designed Complete Us Crypto Tax Guide Cryptocurrency Management With Blockchain is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Complete Us Crypto Tax Guide Cryptocurrency Management With Blockchain and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide discusses the taxes in the crypto market. The purpose of this slide is to outline the crypto tax criteria used in the United States of America on Bitcoin and Crypto. It also includes the tax range for long-term and short-term capital gains.

Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain
This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.Get a simple yet stunning designed Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.

Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain
This slide highlights the overview of paper wallets in the crypto world. The purpose of this slide is to outline some basic features of a paper wallet such as present in a physical medium, having to download the code for transactions, have a unique identifiers, etc.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain can be your best option for delivering a presentation. Represent everything in detail using Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the overview of paper wallets in the crypto world. The purpose of this slide is to outline some basic features of a paper wallet such as present in a physical medium, having to download the code for transactions, have a unique identifiers, etc.
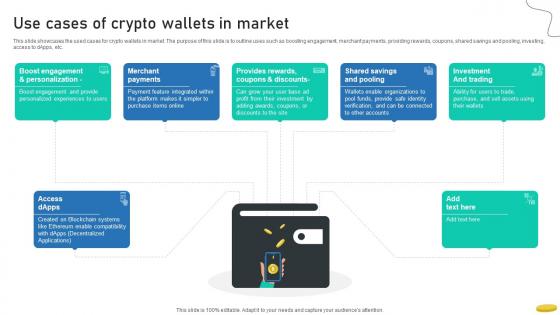
Use Cases Of Crypto Wallets In Market Cryptocurrency Management With Blockchain
This slide showcases the used cases for crypto wallets in market. The purpose of this slide is to outline uses such as boosting engagement, merchant payments, providing rewards, coupons, shared savings and pooling, investing, access to dApps, etc.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Use Cases Of Crypto Wallets In Market Cryptocurrency Management With Blockchain was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Use Cases Of Crypto Wallets In Market Cryptocurrency Management With Blockchain. This slide showcases the used cases for crypto wallets in market. The purpose of this slide is to outline uses such as boosting engagement, merchant payments, providing rewards, coupons, shared savings and pooling, investing, access to dApps, etc.
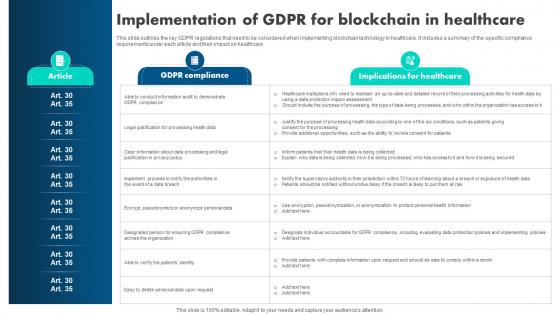
How Blockchain Is Reshaping Implementation Of GDPR For Blockchain In Healthcare BCT SS V
This slide outlines the key GDPR regulations that need to be considered when implementing blockchain technology in healthcare. It includes a summary of the specific compliance requirements under each article and their impact on healthcare. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download How Blockchain Is Reshaping Implementation Of GDPR For Blockchain In Healthcare BCT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the How Blockchain Is Reshaping Implementation Of GDPR For Blockchain In Healthcare BCT SS V. This slide outlines the key GDPR regulations that need to be considered when implementing blockchain technology in healthcare. It includes a summary of the specific compliance requirements under each article and their impact on healthcare.

Managing Technical And Non Implementation Of New Web Designing Technologies
Mentioned slide outlines checklist use to select new web design technologies to be adopted by business which are within business expenses. It includes key components such as technologies, benefits, cost and checklist. Presenting this PowerPoint presentation, titled Managing Technical And Non Implementation Of New Web Designing Technologies, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Managing Technical And Non Implementation Of New Web Designing Technologies. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Managing Technical And Non Implementation Of New Web Designing Technologies that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. Mentioned slide outlines checklist use to select new web design technologies to be adopted by business which are within business expenses. It includes key components such as technologies, benefits, cost and checklist.

Growth Drivers Of Product Analytics Market Driving Business Success Integrating Product
This slide outlines major growth drivers promoting use of product analytics at a global level to boost business reach. It covers arguments such as need to improve customer behavior, cloud-based analytics solutions, rapid changes in model and increase in adoption This Growth Drivers Of Product Analytics Market Driving Business Success Integrating Product is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Growth Drivers Of Product Analytics Market Driving Business Success Integrating Product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines major growth drivers promoting use of product analytics at a global level to boost business reach. It covers arguments such as need to improve customer behavior, cloud-based analytics solutions, rapid changes in model and increase in adoption
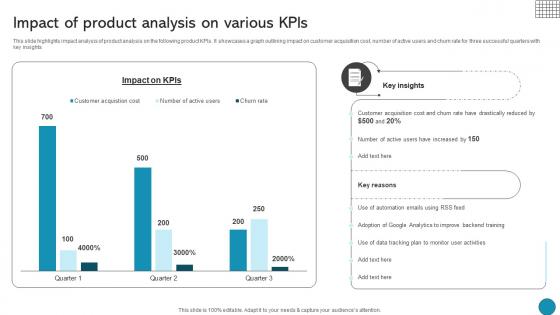
Impact Of Product Analysis On Various Kpis Driving Business Success Integrating Product
This slide highlights impact analysis of product analysis on the following product KPIs. It showcases a graph outlining impact on customer acquisition cost, number of active users and churn rate for three successful quarters with key insights Retrieve professionally designed Impact Of Product Analysis On Various Kpis Driving Business Success Integrating Product to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide highlights impact analysis of product analysis on the following product KPIs. It showcases a graph outlining impact on customer acquisition cost, number of active users and churn rate for three successful quarters with key insights
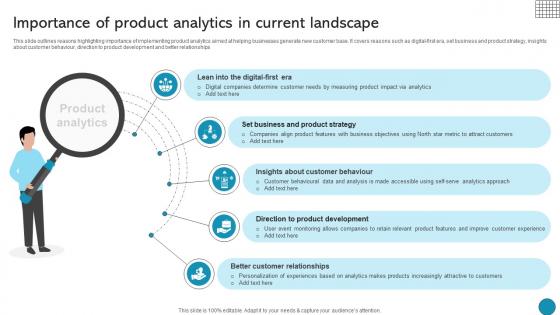
Importance Of Product Analytics In Current Landscape Driving Business Success Integrating Product
This slide outlines reasons highlighting importance of implementing product analytics aimed at helping businesses generate new customer base. It covers reasons such as digital-first era, set business and product strategy, insights about customer behaviour, direction to product development and better relationships Presenting this PowerPoint presentation, titled Importance Of Product Analytics In Current Landscape Driving Business Success Integrating Product, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Importance Of Product Analytics In Current Landscape Driving Business Success Integrating Product. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Importance Of Product Analytics In Current Landscape Driving Business Success Integrating Product that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines reasons highlighting importance of implementing product analytics aimed at helping businesses generate new customer base. It covers reasons such as digital-first era, set business and product strategy, insights about customer behaviour, direction to product development and better relationships

Product Analytics Training Plan For Employees Driving Business Success Integrating Product
This slide outlines training plan aimed at helping employees learn the basics of product analytics to streamline its usage in the business enterprises. It covers details on training module, mode of training, training time slots with trainer name Find highly impressive Product Analytics Training Plan For Employees Driving Business Success Integrating Product on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Product Analytics Training Plan For Employees Driving Business Success Integrating Product for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines training plan aimed at helping employees learn the basics of product analytics to streamline its usage in the business enterprises. It covers details on training module, mode of training, training time slots with trainer name

Steps To Build Attribution Strategy For Businesses Driving Business Success Integrating Product
This slide outlines phases to develop attribution strategy aimed at tracking, aligning and prioritizing experiences. It covers steps such as determine objectives, store information, focus on behavior, analyze interactions, choose right model and optimize attribution window This Steps To Build Attribution Strategy For Businesses Driving Business Success Integrating Product is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Steps To Build Attribution Strategy For Businesses Driving Business Success Integrating Product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines phases to develop attribution strategy aimed at tracking, aligning and prioritizing experiences. It covers steps such as determine objectives, store information, focus on behavior, analyze interactions, choose right model and optimize attribution window
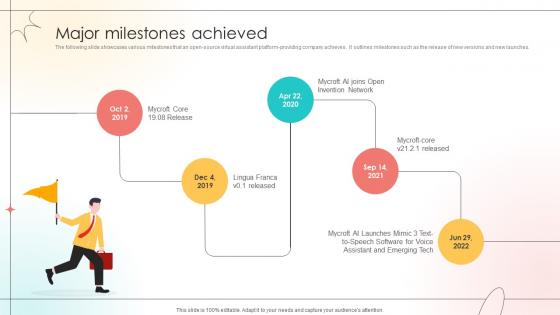
Major Milestones Achieved Open Source Solution Investor Funding Elevator Pitch Deck
The following slide showcases various milestones that an open-source virtual assistant platform-providing company achieves. It outlines milestones such as the release of new versions and new launches. If you are looking for a format to display your unique thoughts, then the professionally designed Major Milestones Achieved Open Source Solution Investor Funding Elevator Pitch Deck is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Major Milestones Achieved Open Source Solution Investor Funding Elevator Pitch Deck and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide showcases various milestones that an open-source virtual assistant platform-providing company achieves. It outlines milestones such as the release of new versions and new launches.

ChatGPT Education Use Case For Teachers Designing Applications Of ChatGPT In Education ChatGPT SS V
This slide represents details related to use of AI technology designed to understand and generate human-like texts based on received inputs, by educators for teaching purpose. It includes details related to use case of ChatGPT by educators for designing syllabus outline. Present like a pro with ChatGPT Education Use Case For Teachers Designing Applications Of ChatGPT In Education ChatGPT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents details related to use of AI technology designed to understand and generate human-like texts based on received inputs, by educators for teaching purpose. It includes details related to use case of ChatGPT by educators for designing syllabus outline.


 Continue with Email
Continue with Email

 Home
Home


































