Firewall

Primary Actions Of WAF Features Ppt Infographics Ideas PDF
This slide gives an overview of the main actions of Web Application Firewall technology. The purpose of this slide is to showcase the different actions of the Web Application Firewall system, including Allow, Block, Log, and Anomaly Score. The Primary Actions Of WAF Features Ppt Infographics Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
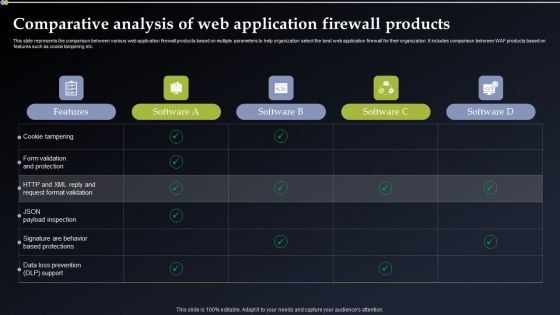
Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. This Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
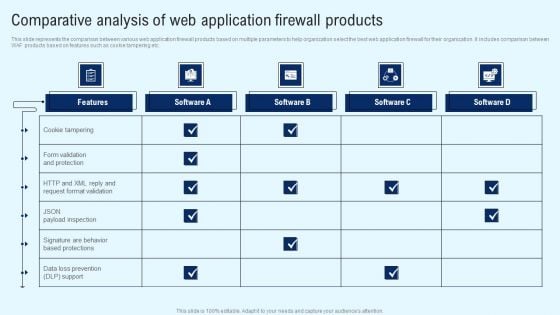
Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Boost your pitch with our creative Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
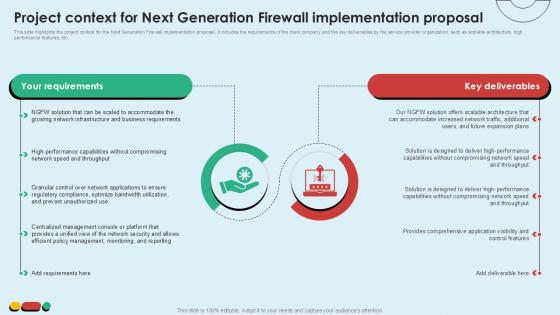
Project Context For Next Generation Intelligent Intrusion Prevention System Ppt Slide
This slide highlights the project context for the Next Generation Firewall implementation proposal. It includes the requirements of the client company and the key deliverables by the service provider organization, such as scalable architecture, high performance features, etc.If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Project Context For Next Generation Intelligent Intrusion Prevention System Ppt Slide and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide highlights the project context for the Next Generation Firewall implementation proposal. It includes the requirements of the client company and the key deliverables by the service provider organization, such as scalable architecture, high performance features, etc.
Zero Trust Network Access Performance Tracking Dashboar Slides Pdf
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Network Access Performance Tracking Dashboar Slides Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.
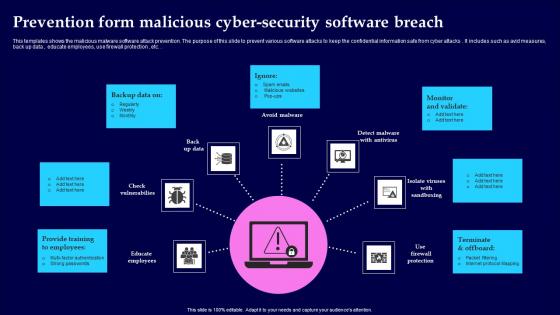
Prevention Form Malicious Cyber Security Software Breach Portrait Pdf
This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc. Showcasing this set of slides titled Prevention Form Malicious Cyber Security Software Breach Portrait Pdf The topics addressed in these templates are Provide Training, Monitor And Validate, Terminate And Offboard All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc.

A52 Zero Trust Network Access System Use Cases
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. There are so many reasons you need a A52 Zero Trust Network Access System Use Cases. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.

About Us For Our Intelligent Intrusion Prevention System Ppt Template
This slide gives an overview of the firewall solutions provider company. It includes the total number of clients, employees, successful projects, partnerships and collaborations with industry leading organizations, and history.Find a pre designed and impeccable About Us For Our Intelligent Intrusion Prevention System Ppt Template. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide gives an overview of the firewall solutions provider company. It includes the total number of clients, employees, successful projects, partnerships and collaborations with industry leading organizations, and history.
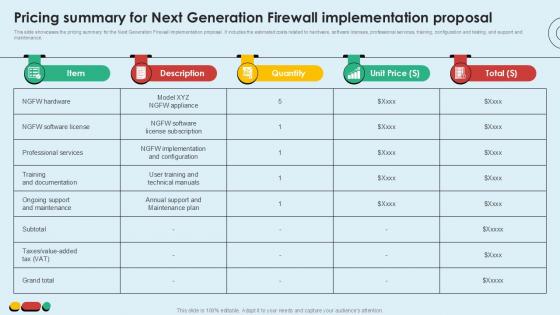
Pricing Summary For Next Generation Intelligent Intrusion Prevention System Ppt Sample
This slide showcases the pricing summary for the Next Generation Firewall implementation proposal. It includes the estimated costs related to hardware, software licenses, professional services, training, configuration and testing, and support and maintenance.Find highly impressive Pricing Summary For Next Generation Intelligent Intrusion Prevention System Ppt Sample on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Pricing Summary For Next Generation Intelligent Intrusion Prevention System Ppt Sample for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the pricing summary for the Next Generation Firewall implementation proposal. It includes the estimated costs related to hardware, software licenses, professional services, training, configuration and testing, and support and maintenance.
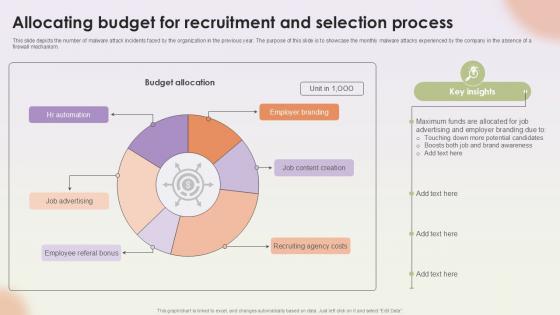
Allocating Budget For Recruitment Workforce Procurement And Aptitude Evaluation Ppt Slides
This slide depicts the number of malware attack incidents faced by the organization in the previous year. The purpose of this slide is to showcase the monthly malware attacks experienced by the company in the absence of a firewall mechanism. Boost your pitch with our creative Allocating Budget For Recruitment Workforce Procurement And Aptitude Evaluation Ppt Slides. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide depicts the number of malware attack incidents faced by the organization in the previous year. The purpose of this slide is to showcase the monthly malware attacks experienced by the company in the absence of a firewall mechanism.
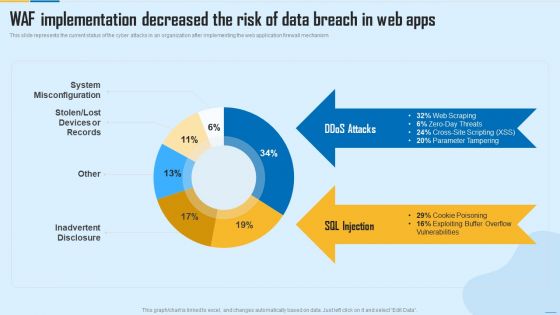
WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF. Use them to share invaluable insights on System Misconfiguration, Inadvertent Disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
WAF Platform Kpis Dashboard For Threat Tracking In WAF Demonstration PDF
This slide depicts how threat risk will be monitored and threat detection will be done in the organization through web application firewall implementation. Deliver an awe inspiring pitch with this creative WAF Platform Kpis Dashboard For Threat Tracking In WAF Demonstration PDF bundle. Topics like Current Risk Status, Threat Dashboard, Risk By Threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ITIL Strategy Service Excellence Client Standards Checklist Contd Ppt PowerPoint Presentation Styles Example PDF
Presenting this set of slides with name itil strategy service excellence client standards checklist contd ppt powerpoint presentation styles example pdf. This is a one stage process. The stages in this process are genuine anti spam solution, vendor supported server, licensed firewall between internal, secured encryption, wireless data traffic, environment, high speed internet access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
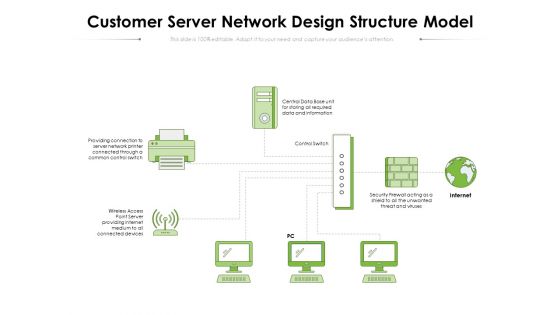
Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
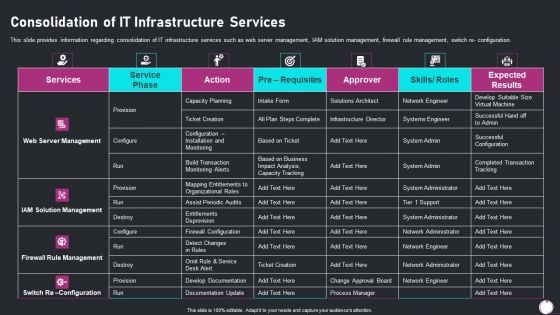
Information Technology Transformation Playbook Consolidation Of IT Infrastructure Services Graphics PDF
This slide provides information regarding consolidation of IT infrastructure services such as web server management, IAM solution management, firewall rule management, switch re- configuration. Deliver an awe inspiring pitch with this creative information technology transformation playbook consolidation of it infrastructure services graphics pdf bundle. Topics like consolidation of it infrastructure services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
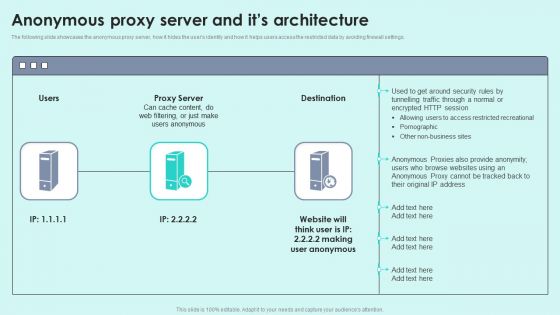
Reverse Proxy Server IT Anonymous Proxy Server And Its Architecture Ppt Infographic Template Icon PDF
The following slide showcases the anonymous proxy server, how it hides the users identity and how it helps users access the restricted data by avoiding firewall settings. Deliver an awe inspiring pitch with this creative reverse proxy server it anonymous proxy server and its architecture ppt infographic template icon pdf bundle. Topics like proxy server, access restricted recreational, pornographic can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
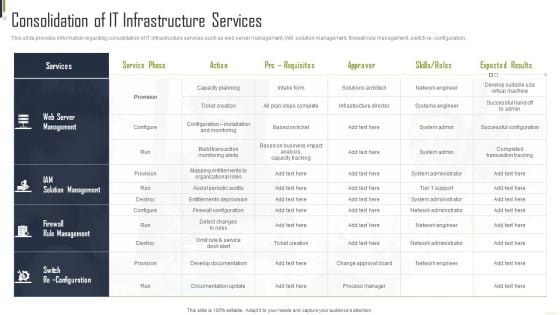
Consolidation Of IT Infrastructure Services Playbook For Information Inspiration PDF
This slide provides information regarding consolidation of IT infrastructure services such as web server management, IAM solution management, firewall rule management, switch re- configuration. Deliver and pitch your topic in the best possible manner with this Consolidation Of IT Infrastructure Services Playbook For Information Inspiration PDF. Use them to share invaluable insights on Solution Management, Rule Management, Successful Configuration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
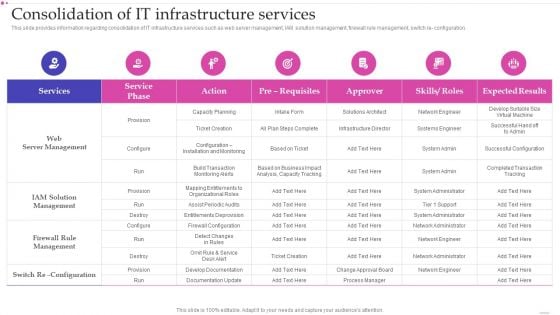
Optimizing IT Infrastructure Playbook Consolidation Of IT Infrastructure Services Structure PDF
This slide provides information regarding consolidation of IT infrastructure services such as web server management, IAM solution management, firewall rule management, switch re configuration.Deliver an awe inspiring pitch with this creative Optimizing IT Infrastructure Playbook Consolidation Of IT Infrastructure Services Structure PDF bundle. Topics like Installation Monitoring, Rule Management, Documentation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
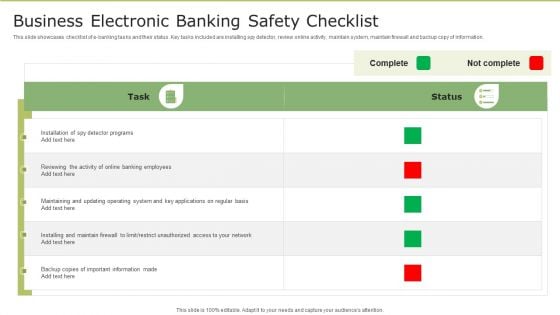
Business Electronic Banking Safety Checklist Introduction PDF
This slide showcases checklist of e banking tasks and their status. Key tasks included are installing spy detector, review online activity, maintain system, maintain firewall and backup copy of information. Showcasing this set of slides titled Business Electronic Banking Safety Checklist Introduction PDF. The topics addressed in these templates are Key Applications, Operating System, Network. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Anonymous Proxy Server And Its Architecture Reverse Proxy For Load Balancing Slides PDF
The following slide showcases the anonymous proxy server, how it hides the users identity and how it helps users access the restricted data by avoiding firewall settings.Deliver and pitch your topic in the best possible manner with this Anonymous Proxy Server And Its Architecture Reverse Proxy For Load Balancing Slides PDF. Use them to share invaluable insights on Restricted Recreational, Tunnelling Traffic, Anonymous Proxy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Deliver an awe inspiring pitch with this creative Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF bundle. Topics like Servers Outside, Encrypted Secure, Outside Firewall can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
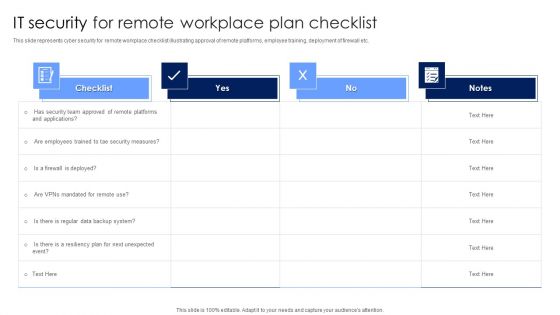
IT Security For Remote Workplace Plan Checklist Introduction PDF
This slide represents cyber security for remote workplace checklist illustrating approval of remote platforms, employee training, deployment of firewall etc. Pitch your topic with ease and precision using this IT Security For Remote Workplace Plan Checklist Introduction PDF. This layout presents information on Security Measures, Employees, Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
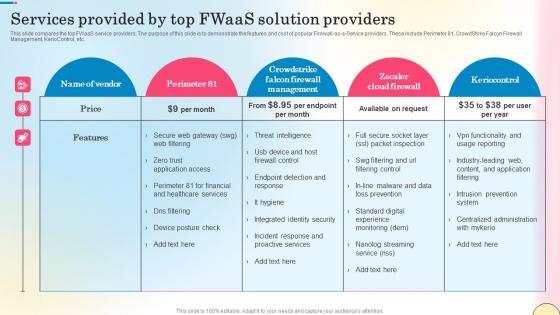
Services Provided By Top Fwaas Solution Providers Network Security Themes Pdf
This slide compares the top FWaaS service providers. The purpose of this slide is to demonstrate the features and cost of popular Firewall-as-a-Service providers. These include Perimeter 81, CrowdStrike Falcon Firewall Management, KerioControl, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Services Provided By Top Fwaas Solution Providers Network Security Themes Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Services Provided By Top Fwaas Solution Providers Network Security Themes Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide compares the top FWaaS service providers. The purpose of this slide is to demonstrate the features and cost of popular Firewall-as-a-Service providers. These include Perimeter 81, CrowdStrike Falcon Firewall Management, KerioControl, etc.
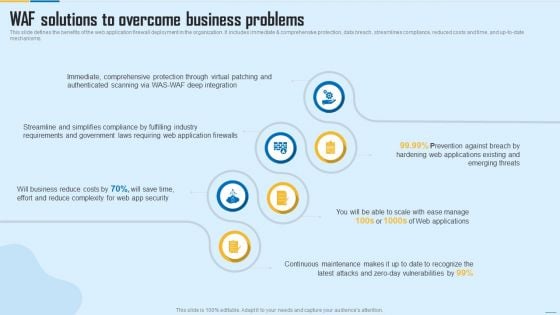
WAF Solutions To Overcome Business Problems WAF Platform Clipart PDF
This slide defines the benefits of the web application firewall deployment in the organization. It includes immediate and comprehensive protection, data breach, streamlines compliance, reduced costs and time, and up to date mechanisms. This is a WAF Solutions To Overcome Business Problems WAF Platform Clipart PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Requirements, Security, Applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Features Of WAF Protection Against Known And Unknown Attacks WAF Platform Inspiration PDF
This slide describes another web application firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. Presenting Features Of WAF Protection Against Known And Unknown Attacks WAF Platform Inspiration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Hybrid Model, Negative Model, Positive Model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT How To Protect Company From Trojan Attacks Summary PDF
This slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. This is a global cyber terrorism incidents on the rise it how to protect company from trojan attacks summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install a good antivirus programm, web application firewall waf, stick to reliable sources, avoid third party downloads. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver an awe inspiring pitch with this creative Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF bundle. Topics like Ransomware, Reduce Ransomware, Cybersecurity Awareness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti phishing add ons, using a customized web application firewall etc. Deliver and pitch your topic in the best possible manner with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF. Use them to share invaluable insights on Goal, Security System, Reduce and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Summary PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver and pitch your topic in the best possible manner with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Summary PDF. Use them to share invaluable insights on Reduce Ransomware, Reduce Distributed, Approaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
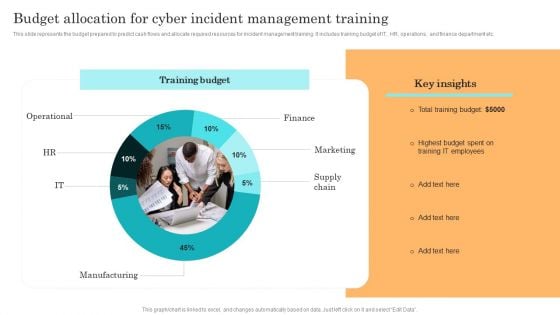
Incident Response Techniques Deployement Budget Allocation For Cyber Incident Management Training Rules PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Boost your pitch with our creative Incident Response Techniques Deployement Benefits Of Implementing Web Application Firewall Brochure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
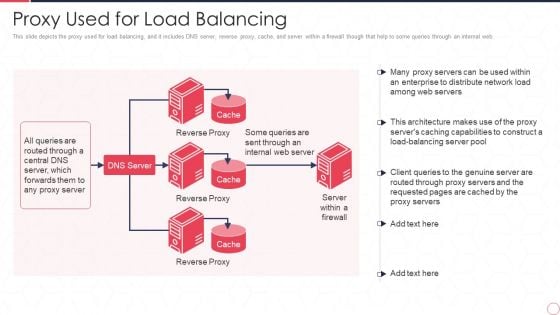
Reverse Proxy Server IT Proxy Used For Load Balancing Ppt Show Design Inspiration PDF
This slide depicts the proxy used for load balancing, and it includes DNS server, reverse proxy, cache, and server within a firewall though that help to some queries through an internal web. Presenting reverse proxy server it proxy used for load balancing ppt show design inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like reverse proxy, dns server, cache. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

5 Key Practices To Prevent Cyber Phishing Scams And Attacks Graphics PDF
Mentioned slide showcases best practices which can be implemented to prevent cyber phishing. The practices are recognizing hyperlinks attached in an email, backup system copies, secure robust HTTPs connections, installing a firewall and using anti spam tools. Presenting 5 key practices to prevent cyber phishing scams and attacks graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including secure, device, reduced. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Presenting Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Category Of Security Controls, Controls Description, Secured Firewall Configuration In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
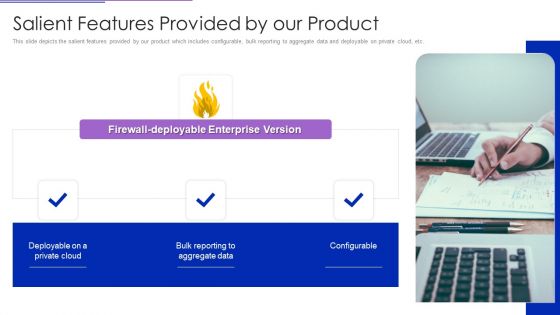
Bliss Investor Capital Raising Elevator Pitch Deck Salient Features Provided By Our Product Demonstration PDF
This slide depicts the salient features provided by our product which includes configurable, bulk reporting to aggregate data and deployable on private cloud, etc.Presenting Bliss Investor Capital Raising Elevator Pitch Deck Salient Features Provided By Our Product Demonstration PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Firewall Deployable, Enterprise Version, Aggregate Data In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
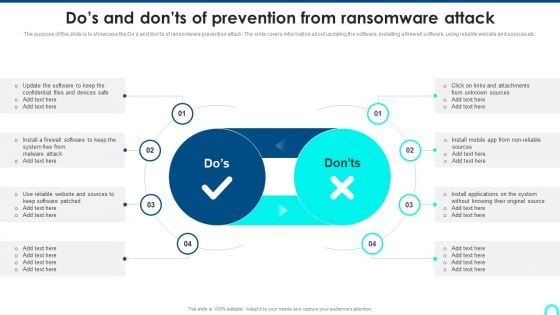
Dos And Donts Of Prevention From Ransomware Attack Summary PDF
The purpose of this slide is to showcase the Dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc.Deliver and pitch your topic in the best possible manner with this Dos And Donts Of Prevention From Ransomware Attack Summary PDF. Use them to share invaluable insights on Confidential Files, Install Applications, Keep Software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
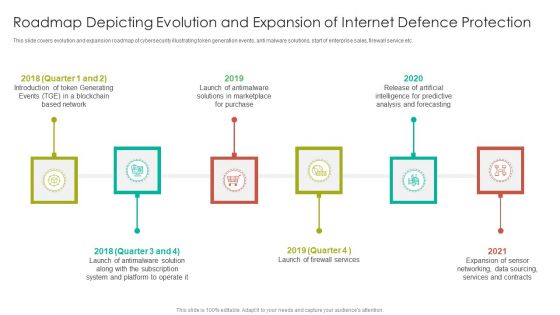
Roadmap Depicting Evolution And Expansion Of Internet Defence Protection Guidelines PDF
This slide covers evolution and expansion roadmap of cybersecurity illustrating token generation events, anti malware solutions, start of enterprise sales, firewall service etc.Persuade your audience using this Roadmap Depicting Evolution And Expansion Of Internet Defence Protection Guidelines PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Token Generating, Solutions Marketplace, Launch Antimalware. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Proxy Used For Load Balancing Reverse Proxy For Load Balancing Icons PDF
This slide depicts the proxy used for load balancing, and it includes DNS server, reverse proxy, cache, and server within a firewall though that help to some queries through an internal web.Deliver an awe inspiring pitch with this creative Proxy Used For Load Balancing Reverse Proxy For Load Balancing Icons PDF bundle. Topics like Reverse Proxy, Distribute Network, Capabilities Construct, Servers Requested can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
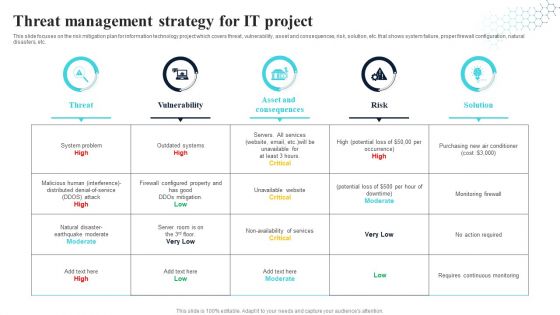
Threat Management Strategy For It Project Themes PDF
This slide focuses on the risk mitigation plan for information technology project which covers threat, vulnerability, asset and consequences, risk, solution, etc. that shows system failure, proper firewall configuration, natural disasters, etc. Pitch your topic with ease and precision using this Threat Management Strategy For It Project Themes PDF. This layout presents information on Vulnerability, Asset And Consequences, Risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Reverse Proxy Web Server Anonymous Proxy Server And Its Architecture Icons PDF
The following slide showcases the anonymous proxy server, how it hides the users identity and how it helps users access the restricted data by avoiding firewall settings. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Reverse Proxy Web Server Anonymous Proxy Server And Its Architecture Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
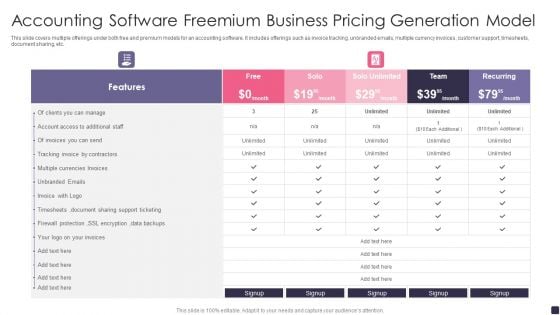
Accounting Software Freemium Business Pricing Generation Model Pictures PDF
This slide covers multiple offerings under both free and premium models for an accounting software. It includes offerings such as invoice tracking, unbranded emails, multiple currency invoices, customer support, timesheets, document sharing, etc.Showcasing this set of slides titled Accounting Software Freemium Business Pricing Generation Model Pictures PDF. The topics addressed in these templates are Tracking Invoice, Timesheets Document, Firewall Protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Dos And Donts Of Prevention From Ransomware Attack Ppt Outline Designs Download PDF
The purpose of this slide is to showcase the Dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. There are so many reasons you need a Dos And Donts Of Prevention From Ransomware Attack Ppt Outline Designs Download PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Information IT Security Communication Plan Guidelines PDF
This slide showcases an information cyber security communication plan to effectively communicate cyber incident and action plan. It includes cyber incidents such as virus, spyware, firewall hacking and phishing. Showcasing this set of slides titled Information IT Security Communication Plan Guidelines PDF. The topics addressed in these templates are Run Microsoft Defender Offline, Install Antivirus, Block Traffic Default. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Internet Security Framework For Data Security Summary Pdf
This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.Showcasing this set of slides titled Internet Security Framework For Data Security Summary Pdf The topics addressed in these templates are Policies And Standard, Data Collection, Establish Firewall All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.
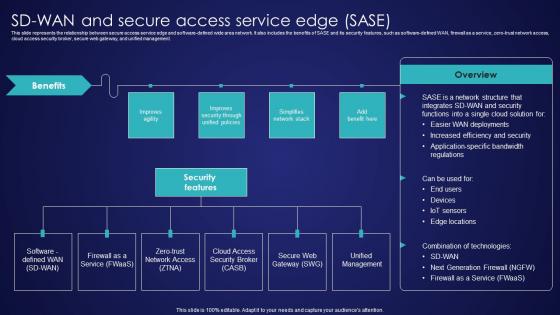
SD Wan And Secure Access Service Edge Sase Wide Area Network Services Elements Pdf
This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management. Welcome to our selection of the SD Wan And Secure Access Service Edge Sase Wide Area Network Services Elements Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management.
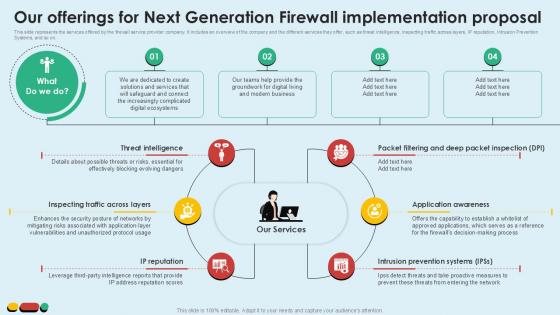
Our Offerings For Next Generation Intelligent Intrusion Prevention System Ppt Slide
This slide represents the services offered by the firewall service provider company. It includes an overview of the company and the different services they offer, such as threat intelligence, inspecting traffic across layers, IP reputation, Intrusion Prevention Systems, and so on.Present like a pro with Our Offerings For Next Generation Intelligent Intrusion Prevention System Ppt Slide. Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the services offered by the firewall service provider company. It includes an overview of the company and the different services they offer, such as threat intelligence, inspecting traffic across layers, IP reputation, Intrusion Prevention Systems, and so on.
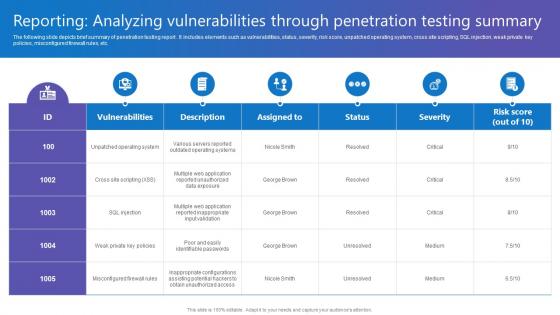
Reporting Analyzing Vulnerabilities Comprehensive Guide To Blockchain Digital Security Inspiration Pdf
The following slide depicts brief summary of penetration testing report . It includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc. Do you know about Slidesgeeks Reporting Analyzing Vulnerabilities Comprehensive Guide To Blockchain Digital Security Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide depicts brief summary of penetration testing report . It includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc.
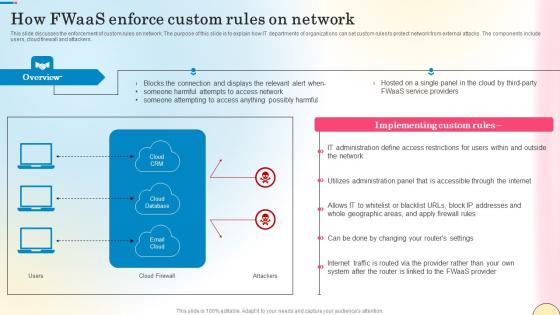
How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf
This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers. This How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers.

Zero Trust Network Access System Use Cases Software Defined Perimeter SDP
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Network Access System Use Cases Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access System Use Cases Software Defined Perimeter SDP from Slidegeeks today. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.
Our Team For Next Generation Intelligent Intrusion Prevention System Ppt Slide
This slide represents an overview of the team structure for the Next Generation Firewall implementation proposal. It highlights the names and designations of each team member in accordance with their position within the hierarchy.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Our Team For Next Generation Intelligent Intrusion Prevention System Ppt Slide can be your best option for delivering a presentation. Represent everything in detail using Our Team For Next Generation Intelligent Intrusion Prevention System Ppt Slide and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents an overview of the team structure for the Next Generation Firewall implementation proposal. It highlights the names and designations of each team member in accordance with their position within the hierarchy.
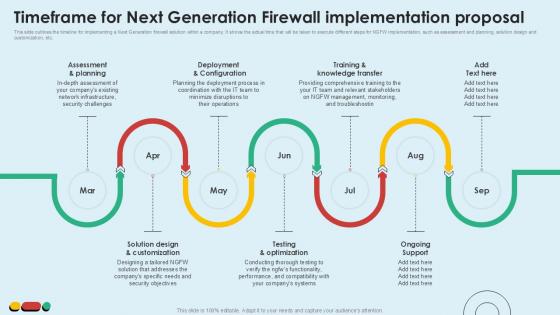
Timeframe For Next Generation Intelligent Intrusion Prevention System Ppt PowerPoint
This slide outlines the timeline for implementing a Next Generation firewall solution within a company. It shows the actual time that will be taken to execute different steps for NGFW implementation, such as assessment and planning, solution design and customization, etc.Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeframe For Next Generation Intelligent Intrusion Prevention System Ppt PowerPoint template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeframe For Next Generation Intelligent Intrusion Prevention System Ppt PowerPoint that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the timeline for implementing a Next Generation firewall solution within a company. It shows the actual time that will be taken to execute different steps for NGFW implementation, such as assessment and planning, solution design and customization, etc.
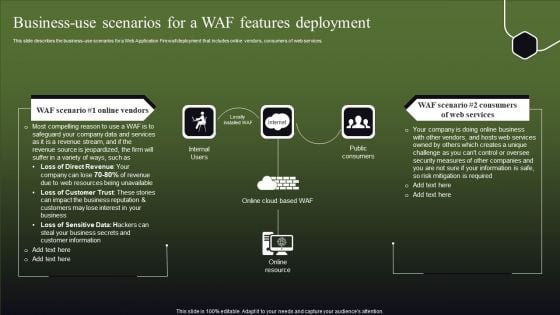
Business-Use Scenarios For A WAF Features Deployment Formats PDF
This slide describes the business-use scenarios for a Web Application Firewall deployment that includes online vendors, consumers of web services. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Business-Use Scenarios For A WAF Features Deployment Formats PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
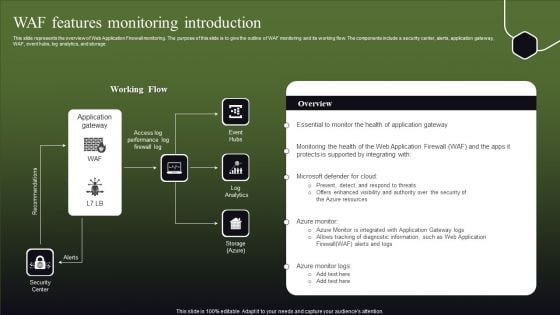
WAF Features Monitoring Introduction Ppt Outline Example Topics PDF
This slide represents the overview of Web Application Firewall monitoring. The purpose of this slide is to give the outline of WAF monitoring and its working flow. The components include a security center, alerts, application gateway, WAF, event hubs, log analytics, and storage. Presenting this PowerPoint presentation, titled WAF Features Monitoring Introduction Ppt Outline Example Topics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this WAF Features Monitoring Introduction Ppt Outline Example Topics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable WAF Features Monitoring Introduction Ppt Outline Example Topics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

WAF Features And Capabilities Ppt Pictures Designs Download PDF
This slide represents the capabilities and characteristics of a Web Application Firewall security solution. This slide aims to showcase the various features of WAF, including AI-powered traffic patterns, attack signature databases, application profiling, customization, correlation engines, and so on. Slidegeeks has constructed WAF Features And Capabilities Ppt Pictures Designs Download PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
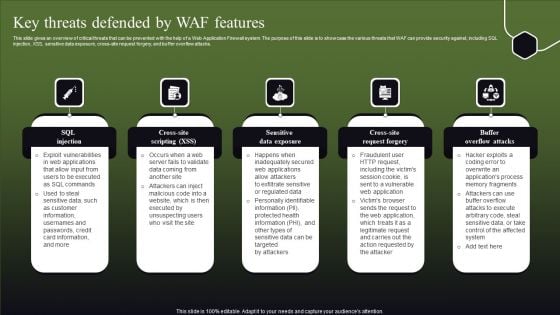
Key Threats Defended By WAF Features Ppt Pictures Elements PDF
This slide gives an overview of critical threats that can be prevented with the help of a Web Application Firewall system. The purpose of this slide is to showcase the various threats that WAF can provide security against, including SQL injection, XSS, sensitive data exposure, cross-site request forgery, and buffer overflow attacks. Explore a selection of the finest Key Threats Defended By WAF Features Ppt Pictures Elements PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Threats Defended By WAF Features Ppt Pictures Elements PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
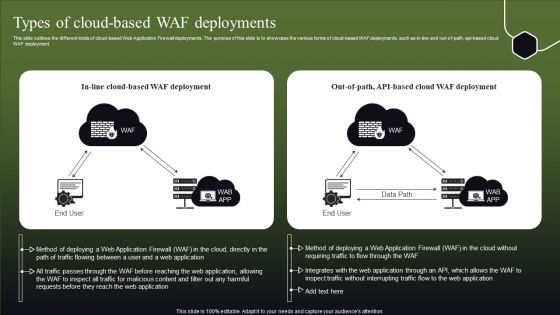
Types Of Cloud Based WAF Deployments Ppt Guide PDF
This slide outlines the different kinds of cloud-based Web Application Firewall deployments. The purpose of this slide is to showcase the various forms of cloud-based WAF deployments, such as in-line and out-of-path, api-based cloud WAF deployment. Retrieve professionally designed Types Of Cloud Based WAF Deployments Ppt Guide PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
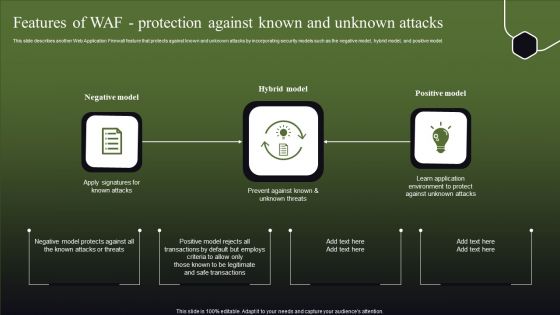
Features Of WAF Protection Against Known And Unknown Attacks Graphics PDF
This slide describes another Web Application Firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. This modern and well-arranged Features Of WAF Protection Against Known And Unknown Attacks Graphics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
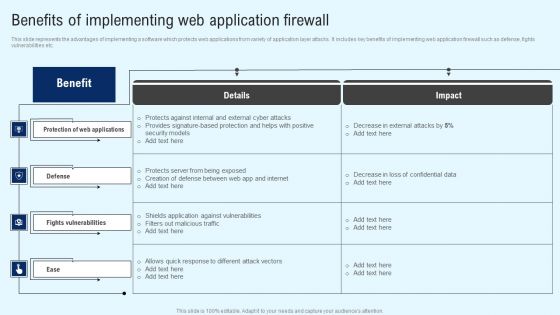
Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cyber Security Incident Benefits Of Implementing Web Application Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

IT Infrastructure Library Procedure Management Playbook Consolidation Of IT Infrastructure Services Ideas PDF
This slide provides information regarding consolidation of IT infrastructure services such as web server management, IAM solution management, firewall rule management, switch re configuration. If you are looking for a format to display your unique thoughts, then the professionally designed IT Infrastructure Library Procedure Management Playbook Consolidation Of IT Infrastructure Services Ideas PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download IT Infrastructure Library Procedure Management Playbook Consolidation Of IT Infrastructure Services Ideas PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
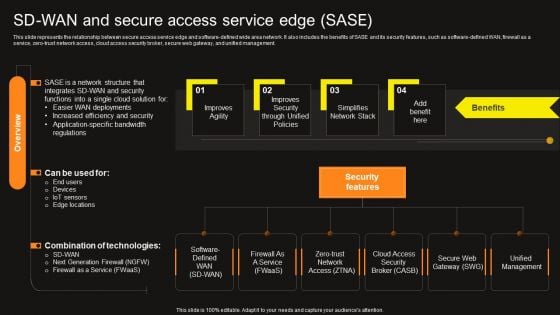
Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF
This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF today and make your presentation stand out from the rest.


 Continue with Email
Continue with Email

 Home
Home


































