Food Security
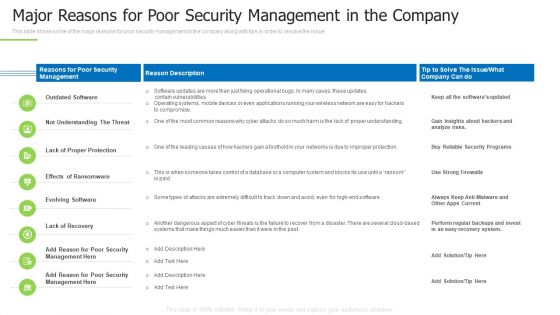
Techniques And Strategies To Reduce Security Management Risks Major Reasons For Poor Security Guidelines PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue.Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks major reasons for poor security guidelines pdf bundle. Topics like outdated software, lack of proper protection, another dangerous aspect can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Addressing Performance Indicators To Determine Security Standards Structure PDF
This slide provides information about performance indicators in order to determine security standards at workplace in terms of incidents, offender management, risk assessments. Deliver an awe inspiring pitch with this creative developing firm security strategy plan addressing performance indicators to determine security standards structure pdf bundle. Topics like incidents, offender management, risk assessments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
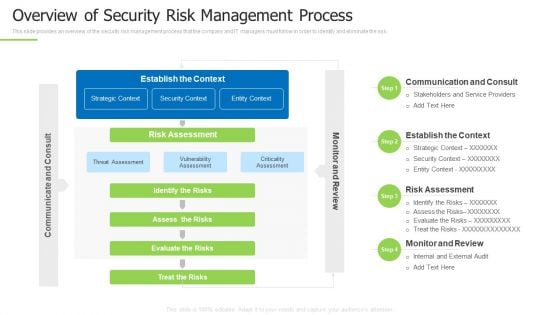
Techniques And Strategies To Reduce Security Management Risks Overview Of Security Risk Background PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks overview of security risk background pdf bundle. Topics like identify the risks, strategic context, vulnerability assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
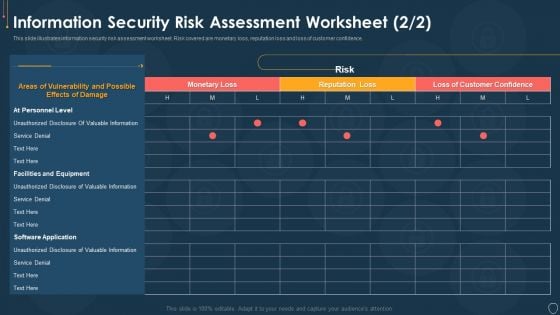
Cyber Security Risk Management Plan Information Security Risk Assessment Worksheet Service Graphics PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan information security risk assessment worksheet service graphics pdf. Use them to share invaluable insights on monetary loss, reputation loss, loss of customer confidence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
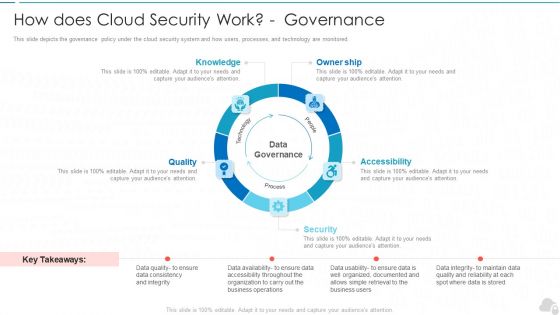
How Does Cloud Security Work Governance Cloud Computing Security IT Ppt Layouts Structure PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a how does cloud security work governance cloud computing security it ppt layouts structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like knowledge, owner ship, quality, security, accessibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Surveillance Company Profile Security Company Executive Summary Microsoft PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Security Company Executive Summary Microsoft PDF. Use them to share invaluable insights on Monitory Services, Company Shareholding, Extensive Customization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Camera System Company Profile Security Company Business Model Mockup PDF
This slide highlights the business model of home security company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Security Company Business Model Mockup PDF bundle. Topics like Revenue Stream, Customer Relationship, Customer Segments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Information Security Risk Assessment Worksheet Infographics PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Information Security Risk Assessment Worksheet Infographics PDF. Use them to share invaluable insights on Facilities And Equipment, Software Application, At Personnel Level, Monetary Loss, Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
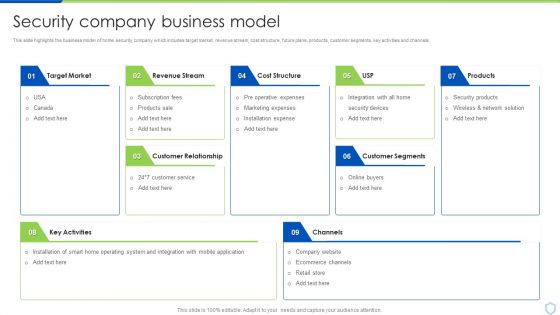
Security And Surveillance Company Profile Security Company Business Model Designs PDF
This slide highlights the business model of home security company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Security Company Business Model Designs PDF bundle. Topics like Target Market, Revenue Stream, Cost Structure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
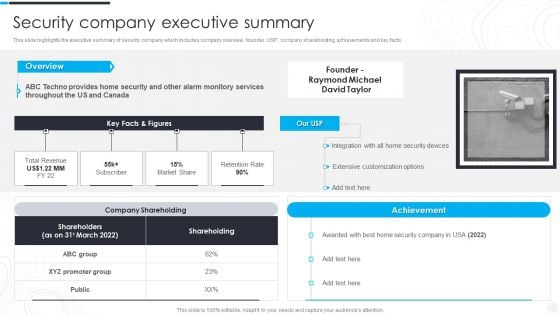
Security Camera System Company Profile Security Company Executive Summary Formats PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Security Company Executive Summary Formats PDF bundle. Topics like Company Shareholding, Customization Options, Raymond Michael can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
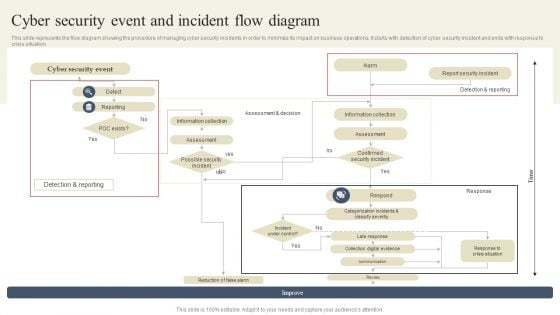
CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Elements Of Information Technology Security Application Security Ppt Portfolio Inspiration PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Presenting elements of information technology security application security ppt portfolio inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like required, information, customers, interest, assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
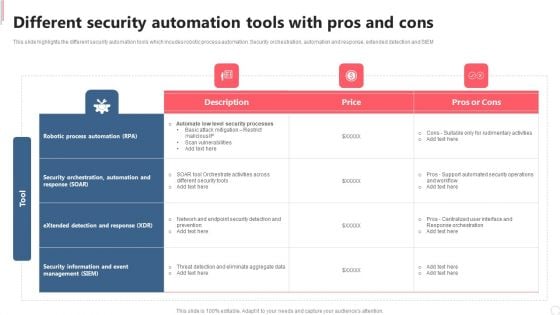
Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
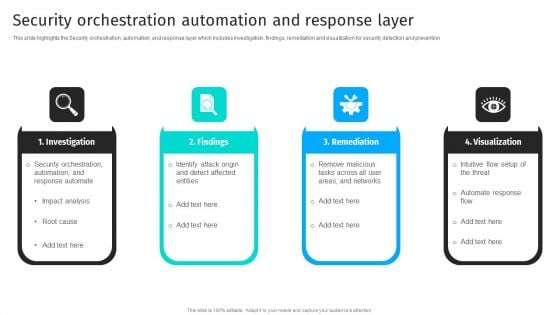
Security Automation To Analyze And Mitigate Cyberthreats Security Orchestration Automation Ideas PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. Welcome to our selection of the Security Automation To Analyze And Mitigate Cyberthreats Security Orchestration Automation Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
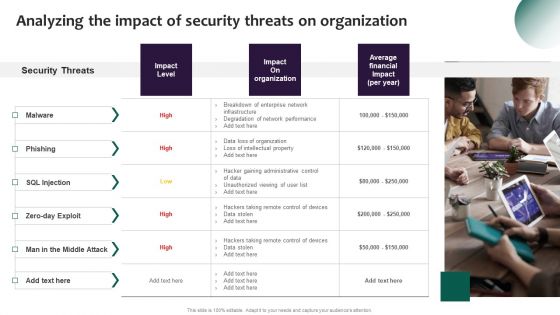
Information Systems Security And Risk Management Plan Analyzing The Impact Of Security Threats On Demonstration PDF
Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information Systems Security And Risk Management Plan Analyzing The Impact Of Security Threats On Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information Systems Security And Risk Management Plan Analyzing The Impact Of Security Threats On Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
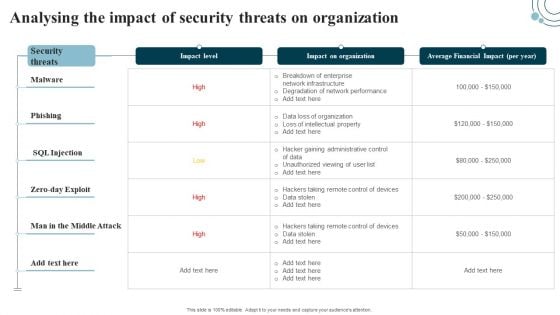
Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Developing IT Security Strategy Analysing The Impact Of Security Threats On Organization Ideas PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Uniformed Security Project Summary For Security Guard Services Proposal Slides PDF
Deliver an awe inspiring pitch with this creative uniformed security project summary for security guard services proposal slides pdf bundle. Topics like relationship philosophy, organizational abilities, competitive advantages, customer service tools, innovative programs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
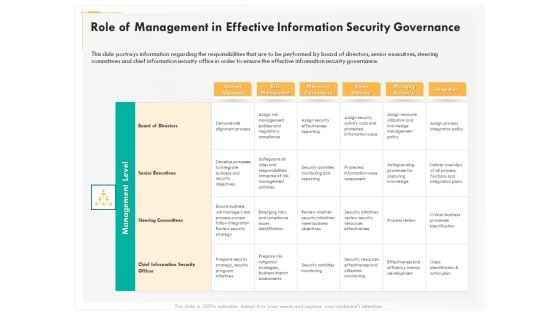
Computer Security Incident Handling Role Of Management In Effective Information Security Governance Portrait PDF
Presenting this set of slides with name computer security incident handling role of management in effective information security governance portrait pdf. The topics discussed in these slides are strategic alignment, risk management, measuring performance, value delivery, managing resource, integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icons Slide For Uniformed Security Proposal For Security Guard Services Brochure PDF
Introducing our well designed icons slide for uniformed security proposal for security guard services brochure pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Techniques And Strategies To Reduce Security Management Risks Security Detail System Maintenance And Monitoring Mockup PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. This is a techniques and strategies to reduce security management risks security detail system maintenance and monitoring mockup pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perfective maintenance, corrective maintenance, perfective maintenance You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
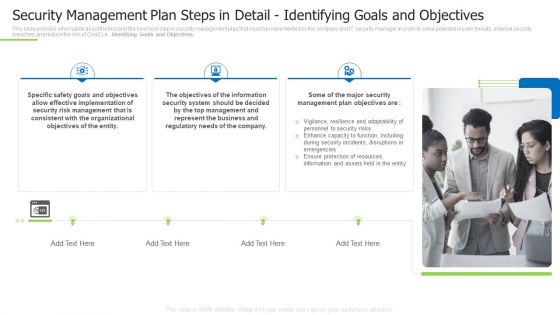
Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps In Detail Inspiration PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a techniques and strategies to reduce security management risks security management plan steps in detail inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like effective implementation, consistent with the organizational, represent the business You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
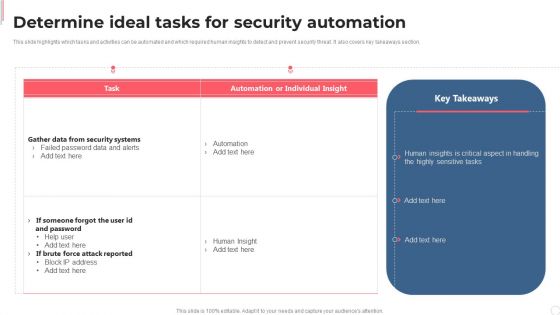
Cyber Security Automation Framework Determine Ideal Tasks For Security Automation Demonstration PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Security Automation Framework Determine Ideal Tasks For Security Automation Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Security Automation Framework Determine Ideal Tasks For Security Automation Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
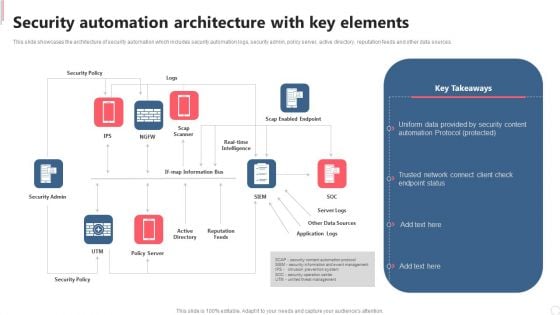
Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. This modern and well arranged Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
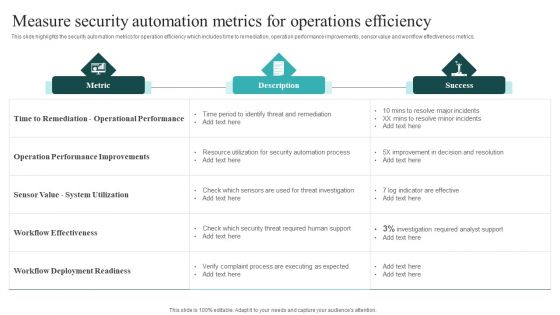
IT Security Automation Systems Guide Measure Security Automation Metrics For Operations Efficiency Mockup PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IT Security Automation Systems Guide Measure Security Automation Metrics For Operations Efficiency Mockup PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IT Security Automation Systems Guide Measure Security Automation Metrics For Operations Efficiency Mockup PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
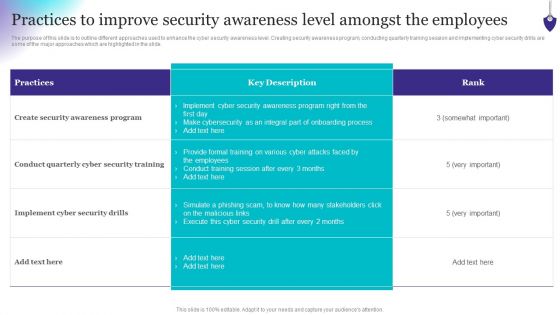
Organizing Security Awareness Practices To Improve Security Awareness Level Amongst Demonstration PDF
The purpose of this slide is to outline different approaches used to enhance the cyber security awareness level. Creating security awareness program, conducting quarterly training session and implementing cyber security drills are some of the major approaches which are highlighted in the slide. This Organizing Security Awareness Practices To Improve Security Awareness Level Amongst Demonstration PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
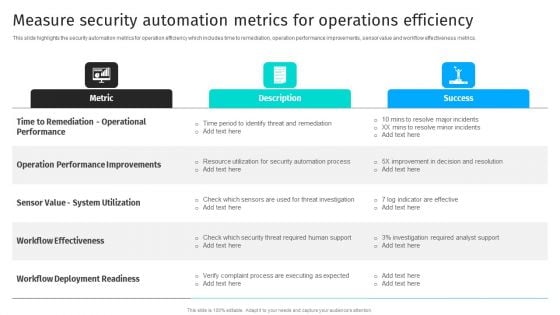
Security Automation To Analyze And Mitigate Cyberthreats Measure Security Automation Metrics Summary PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security Automation To Analyze And Mitigate Cyberthreats Measure Security Automation Metrics Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security Automation To Analyze And Mitigate Cyberthreats Measure Security Automation Metrics Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
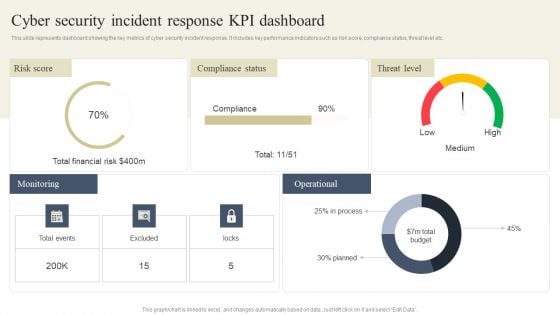
CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
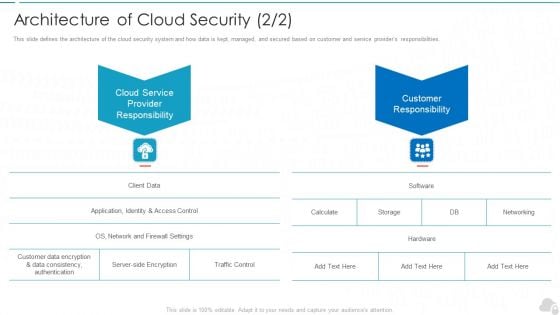
Architecture Of Cloud Security Service Cloud Computing Security IT Ppt Professional Information PDF
This slide defines the architecture of the cloud security system and how data is kept, managed, and secured based on customer and service providers responsibilities. This is a architecture of cloud security service cloud computing security it ppt professional information pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cloud service provider responsibility, customer responsibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
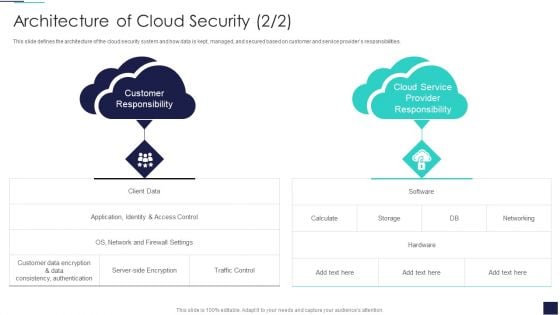
Architecture Of Cloud Security Cloud Information Security Ppt Inspiration Samples PDF
This slide defines the architecture of the cloud security system and how data is kept, managed, and secured based on customer and service providers responsibilities. This is a Architecture Of Cloud Security Cloud Information Security Ppt Inspiration Samples PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Responsibility, Cloud Service, Provider Responsibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
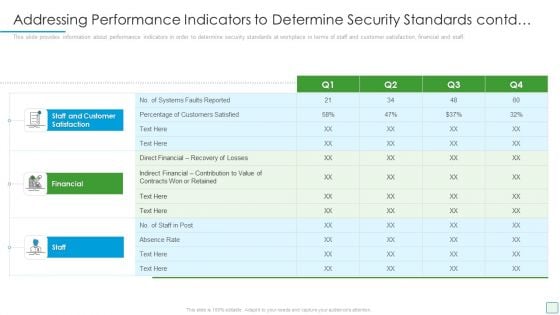
Developing Firm Security Strategy Plan Addressing Performance Indicators To Determine Security Standards Contd Themes PDF
This slide provides information about performance indicators in order to determine security standards at workplace in terms of staff and customer satisfaction, financial and staff. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan addressing performance indicators to determine security standards contd themes pdf. Use them to share invaluable insights on staff and customer satisfaction, financial, staff and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
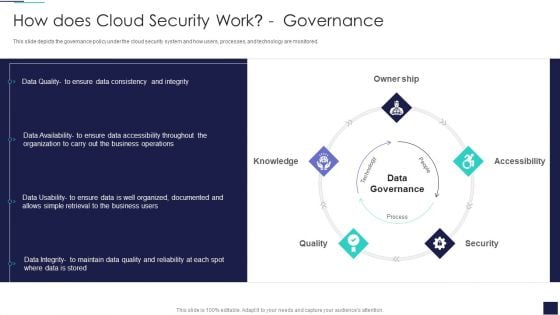
Cloud Information Security How Does Cloud Security Work Governance Ppt Show Slide Portrait PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a Cloud Information Security How Does Cloud Security Work Governance Ppt Show Slide Portrait PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Owner Ship, Accessibility Knowledge, Data Governance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Contd Brochure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Presenting developing firm security strategy plan information security process to manage firms sensitive data contd brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like firewall audit checklist, vpn configuration, penetrating testing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Contd Graphics PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Deliver and pitch your topic in the best possible manner with this project security administration it information security process to manage firms sensitive data contd graphics pdf. Use them to share invaluable insights on firewall audit checklist, vpn configuration, penetrating testing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
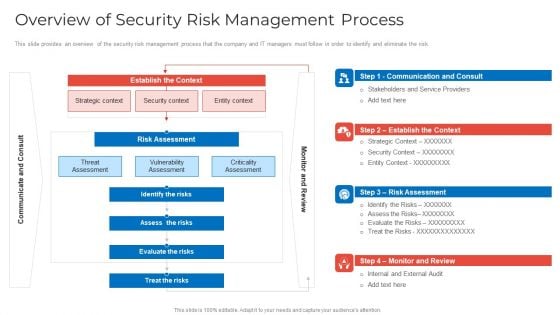
Implementing Security Management Strategy To Mitigate Risk Overview Of Security Risk Management Process Pictures PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative implementing security management strategy to mitigate risk overview of security risk management process pictures pdf bundle. Topics like identify the risks, assess the risks, evaluate the risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Developing Firm Security Strategy Plan Security Incidents Tracking Dashboard Alerts Graphics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Presenting developing firm security strategy plan security incidents tracking dashboard alerts graphics pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like application whitelisting, patch applications, patch operating systems, restrict admin privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Home Security Solutions Company Profile Security Company Business Model Infographics PDF
This slide highlights the business model of home security company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Security Company Business Model Infographics PDF bundle. Topics like Target Market Revenue, Stream Cost Structure, Customer Relationship Products, Customer Segments Key can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
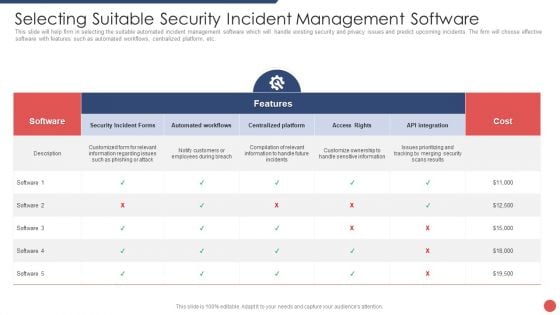
Security Functioning Centre Selecting Suitable Security Incident Management Software Introduction PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative security functioning centre selecting suitable security incident management software introduction pdf bundle. Topics like prioritizing, customers, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
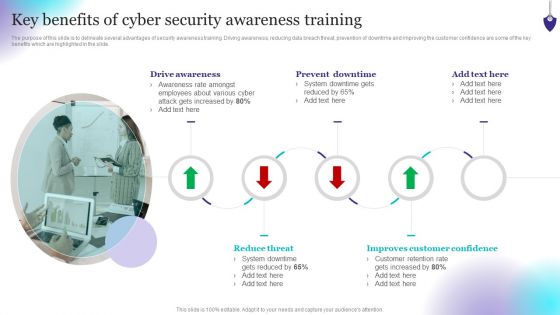
Organizing Security Awareness Key Benefits Of Cyber Security Awareness Training Rules PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Make sure to capture your audiences attention in your business displays with our gratis customizable Organizing Security Awareness Key Benefits Of Cyber Security Awareness Training Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

How Does Cloud Security Work Legal Compliance Cloud Computing Security IT Ppt Model Maker PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. This is a how does cloud security work legal compliance cloud computing security it ppt model maker pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like governance, regulations, transparency, policies, rules. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Revenue Losses Cloud Computing Security IT Ppt Ideas Rules PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. This is a cloud security threats revenue losses cloud computing security it ppt ideas rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizations, cyber threats, revenue. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Threats End User Control Ppt Summary Ideas PDF
This slide represents the end-user threat in cloud security and how an organization needs to control user access and be aware of potential threats. This is a Cloud Information Security Cloud Security Threats End User Control Ppt Summary Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer List, Rival Organizations, Could Upload. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Threats Revenue Losses Ppt Model Themes PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. Presenting Cloud Information Security Cloud Security Threats Revenue Losses Ppt Model Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cyber Threats, Organizations Could, Drastic Decrease. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Regulations Transparency, Standards Policies, Requirements Governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
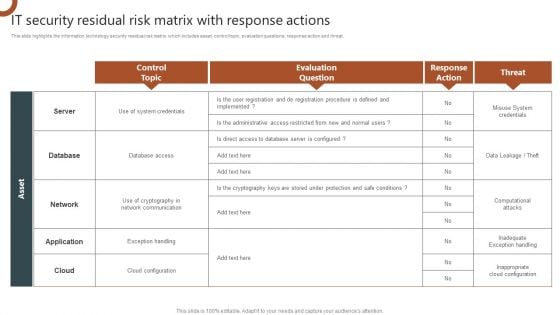
IT Security Residual Risk Matrix With Response Actions Organizations Risk Management And IT Security Professional PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Residual Risk Matrix With Response Actions Organizations Risk Management And IT Security Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

KYC Transaction Monitoring System Business Security Key Members Of Financial Security Department Pictures PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Want to ace your presentation in front of a live audience Our KYC Transaction Monitoring System Business Security Key Members Of Financial Security Department Pictures PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
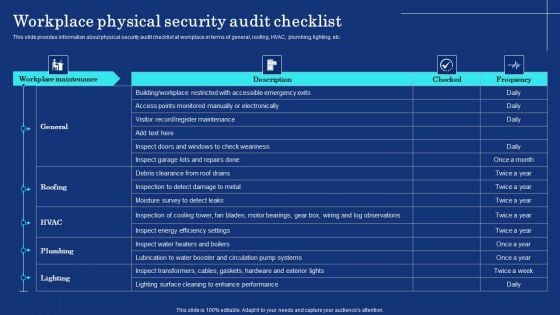
Organizational Assets Security Management Strategy Workplace Physical Security Audit Checklist Guidelines PDF
This slide provides information about physical security audit checklist at workplace in terms of general, roofing, HVAC, plumbing, lighting, etc. This Organizational Assets Security Management Strategy Workplace Physical Security Audit Checklist Guidelines PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Make sure to capture your audiences attention in your business displays with our gratis customizable CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
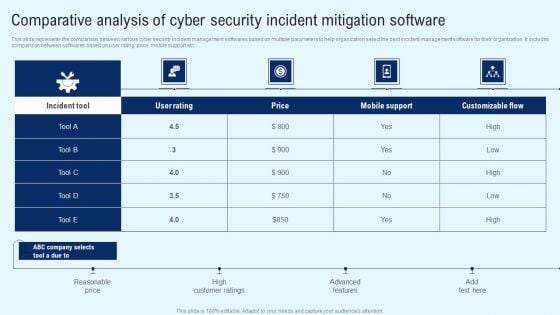
Implementing Cyber Security Incident Comparative Analysis Of Cyber Security Background PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cyber Security Incident Comparative Analysis Of Cyber Security Background PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
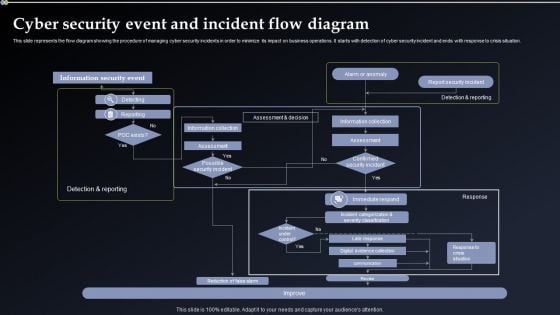
Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Welcome to our selection of the Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
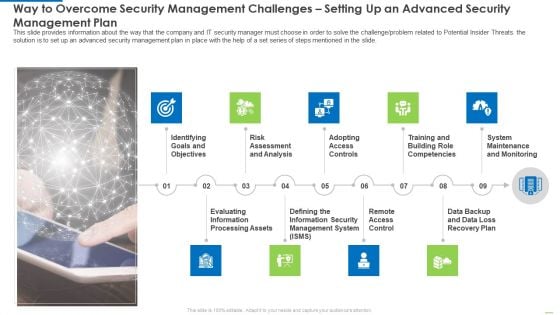
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Introduction PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.This is a way to overcome security management challenges setting up an advanced security management plan introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment and analysis, adopting access controls, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
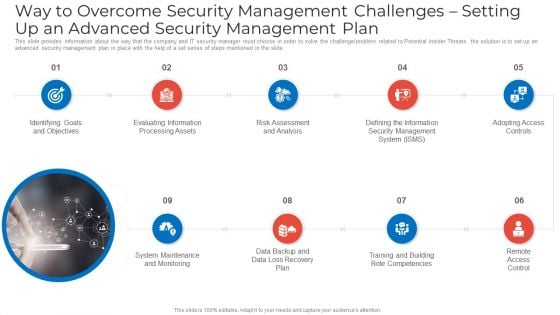
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Microsoft PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide. Presenting way to overcome security management challenges setting up an advanced security management plan microsoft pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, evaluating information processing assets, risk assessment and analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
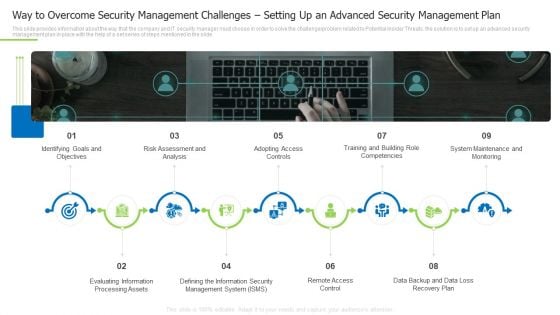
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Rules PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.This is a way to overcome security management challenges setting up an advanced security management plan rules pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identifying goals and objectives, risk assessment and analysis, adopting access controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
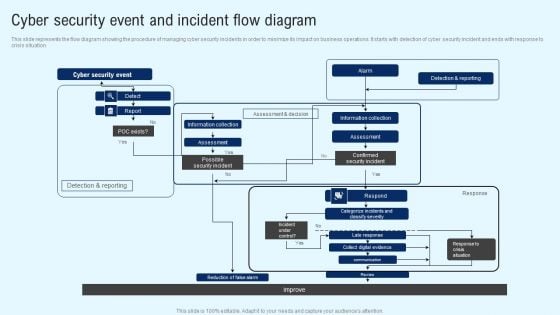
Implementing Cyber Security Incident Cyber Security Event And Incident Flow Diagram Download PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cyber Security Incident Cyber Security Event And Incident Flow Diagram Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Information Systems Security And Risk Management Plan Process For Information Security Risk Assessment Formats PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. This modern and well arranged Information Systems Security And Risk Management Plan Process For Information Security Risk Assessment Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
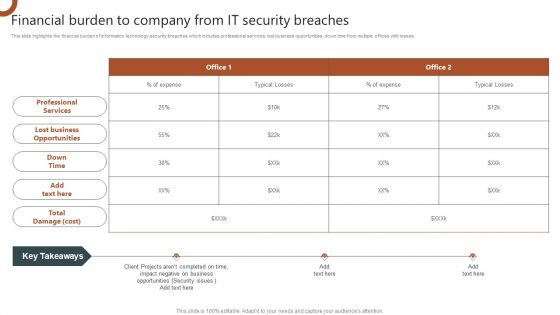
Organizations Risk Management And IT Security Financial Burden To Company From IT Security Breaches Brochure PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Welcome to our selection of the Organizations Risk Management And IT Security Financial Burden To Company From IT Security Breaches Brochure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Organizing Security Awareness KPI Dashboard To Monitor Cyber Security Performance Ideas PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. This modern and well-arranged Organizing Security Awareness KPI Dashboard To Monitor Cyber Security Performance Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Challenges And Solutions In Information Security Risk Management Information Security Risk Administration Template PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them.This Challenges And Solutions In Information Security Risk Management Information Security Risk Administration Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
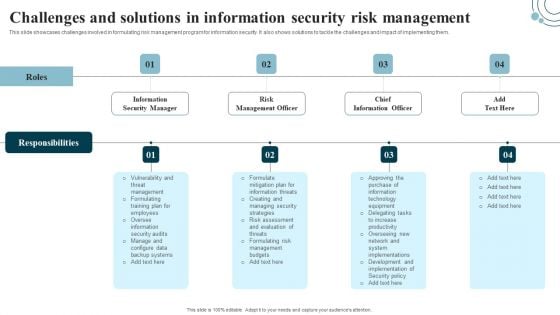
Developing IT Security Strategy Challenges And Solutions In Information Security Risk Pictures PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. Welcome to our selection of the Developing IT Security Strategy Challenges And Solutions In Information Security Risk Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
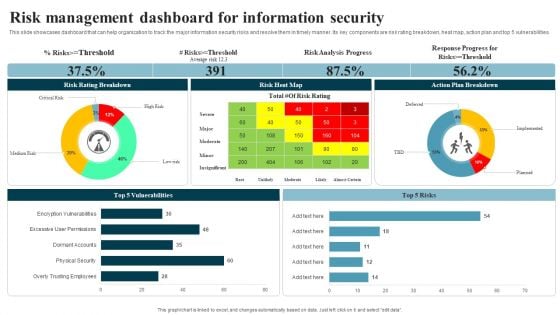
Developing IT Security Strategy Risk Management Dashboard For Information Security Mockup PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. Welcome to our selection of the Developing IT Security Strategy Risk Management Dashboard For Information Security Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.


 Continue with Email
Continue with Email

 Home
Home


































