Gap Analysis Of Security
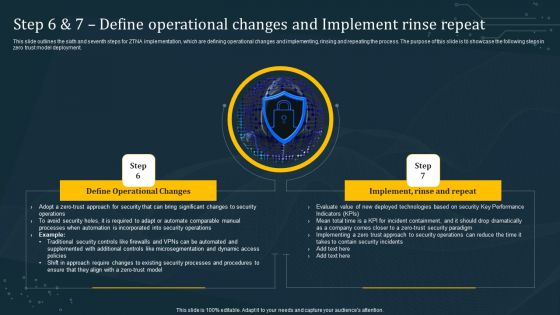
Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Professional PDF
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Find highly impressive Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Professional PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Professional PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Stop The Wars Global PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with wars constantly destroying our home planet Cross the chasm with our Stop The Wars Global PowerPoint Templates And PowerPoint Backgrounds 0211. You will come out on top.

Protect Your Global Business PowerPoint Templates Ppt Backgrounds For Slides 0513
Put yourself in a dominant position. Our Protect Your Global Business PowerPoint Templates PPT Backgrounds For Slides will confirm your superiority. Dominate proceedings with your ideas. Our Umbrellas PowerPoint Templates will empower your thoughts. Our Business PowerPoint Templates have a domino effect. Your ideas will generate one after another. Cross the chasm with our Protect Your Global Business PowerPoint Templates Ppt Backgrounds For Slides 0513. You will come out on top.

Homes Ownership Real Estate PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with symbol of a successful real estate business Develop plans with our Homes Ownership Real Estate PowerPoint Presentation Slides C. Download without worries with our money back guaranteee.
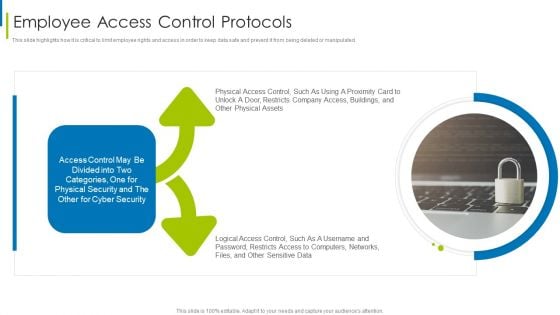
Cyber Terrorism Assault Employee Access Control Protocols Diagrams PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated.This is a cyber terrorism assault employee access control protocols diagrams pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Distributed Denial Of Service DDOS As Cyber Terrorism Tool You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Characteristics Of Modern ZTNA Solution Portrait PDF
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Are you searching for a Key Characteristics Of Modern ZTNA Solution Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Key Characteristics Of Modern ZTNA Solution Portrait PDF from Slidegeeks today.

Mitigating Cybersecurity Threats And Vulnerabilities Table Of Contents Infographics PDF
Presenting mitigating cybersecurity threats and vulnerabilities table of contents infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like leveraging workforce, budget assessment, dashboard, impact assessment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
PowerPoint Slide Teamwork Chains Process Ppt Theme
PowerPoint Slide Teamwork chains process PPT Theme-These Fabulous PowerPoint slides and PowerPoint templates have been delicately designed by our professional team to leave long-lasting impressions on your audiences Make the break with our PowerPoint Slide Teamwork Chains Process Ppt Theme. Your thoughts will create a breakthrough.
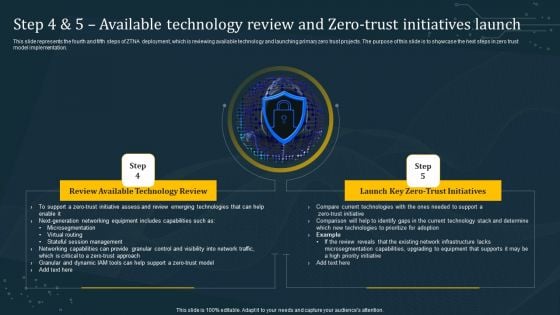
Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Formats PDF
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Formats PDF can be your best option for delivering a presentation. Represent everything in detail using Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Formats PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Stock Photo 3d Yellow Travel Bag PowerPoint Slide
This image slide displays 3d yellow travel bag. This image slide has been designed with graphic of yellow colored travel bag with text space. This image slide depicts travelling. You can change size, color and orientation of icons to your liking. Use this image, in your presentations to express views on travel, vacations, holidays and tourism. This image slide may also be used in presentations to exhibit fashion and luxury. This image slide will add charm to your presentations.
Stock Photo Two Blue Travel Bags PowerPoint Slide
This image slide displays two blue travel bags. This image slide has been designed with graphic of blue colored travel bag with text space. This image slide depicts travelling. You can change size, color and orientation of icons to your liking. Use this image, in your presentations to express views on travel, vacations, holidays and tourism. This image slide may also be used in presentations to exhibit fashion and luxury. This image slide will add charm to your presentations.

Opportunities For Business Growth PowerPoint Templates Ppt Backgrounds For Slides 0513
Our Opportunities For Business Growth PowerPoint Templates PPT Backgrounds For Slides 0513 help to make a draft. They give you a good place to start. Break the deadlock with our Puzzles or jigsaws PowerPoint Templates. Let the words start to flow. Assert your capability with our People PowerPoint Templates. Give your thoughts that decisive touch. Take a blind date with our Opportunities For Business Growth PowerPoint Templates Ppt Backgrounds For Slides 0513. You will be charmed to the core.
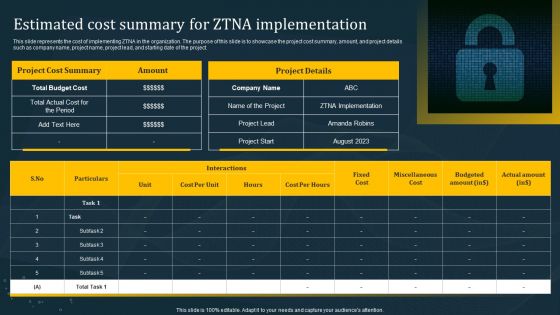
Estimated Cost Summary For ZTNA Implementation Formats PDF
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. This Estimated Cost Summary For ZTNA Implementation Formats PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Estimated Cost Summary For ZTNA Implementation Formats PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Problem Solution Payment Gateway Provider Startup GTM Strategy GTM SS V
The following slide showcases various gaps addressed in market along with desired state through the launch of ABC digital payment provider startup. It includes gaps such as security concerns and fraud risks, lacks responsive support team, etc.The following slide showcases various gaps addressed in market along with desired state through the launch of ABC digital payment provider startup. It includes gaps such as security concerns and fraud risks, lacks responsive support team, etc.This Problem Solution Payment Gateway Provider Startup GTM Strategy GTM SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Problem Solution Payment Gateway Provider Startup GTM Strategy GTM SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide showcases various gaps addressed in market along with desired state through the launch of ABC digital payment provider startup. It includes gaps such as security concerns and fraud risks, lacks responsive support team, etc.

Top To Down Approach For Business Information Protection Demonstration PDF
This slide covers top to down approach for business security which includes security leadership, program, policies and management. Further, it includes user management and information asset security.Pitch your topic with ease and precision using this Top To Down Approach For Business Information Protection Demonstration PDF. This layout presents information on Security Leadership, Security Program, Security Policies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API.
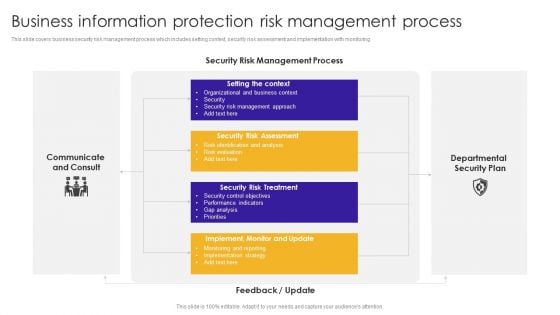
Business Information Protection Risk Management Process Structure PDF
This slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Pitch your topic with ease and precision using this Business Information Protection Risk Management Process Structure PDF. This layout presents information on Organizational Business, Security Risk Assessment, Performance Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
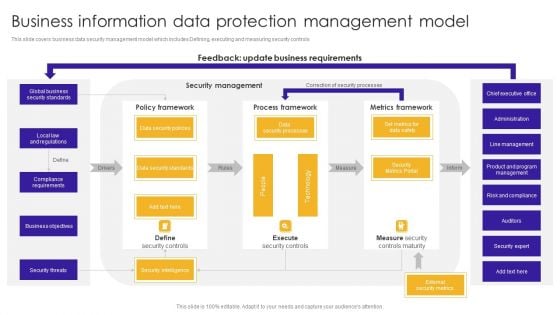
Business Information Data Protection Management Model Structure PDF
This slide covers business data security management model which includes Defining, executing and measuring security controls.Pitch your topic with ease and precision using this Business Information Data Protection Management Model Structure PDF. This layout presents information on Compliance Requirements, Security Standards, Controls Maturity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
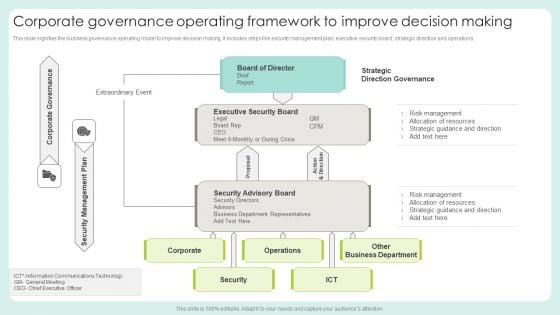
Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF
This slide signifies the business governance operating model to improve decision making. It includes steps like security management plan, executive security board, strategic direction and operations.Pitch your topic with ease and precision using this Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF. This layout presents information on Executive Security, Direction Governance, Communications Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
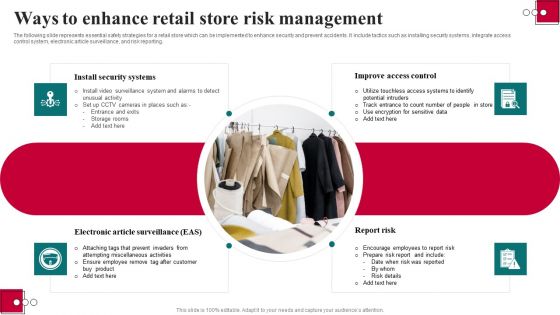
Ways To Enhance Retail Store Risk Management Introduction PDF
The following slide represents essential safety strategies for a retail store which can be implemented to enhance security and prevent accidents. It include tactics such as installing security systems, integrate access control system, electronic article surveillance, and risk reporting. Pitch your topic with ease and precision using this Ways To Enhance Retail Store Risk Management Introduction PDF. This layout presents information on Electronic Article Surveillance, Report Risk, Install Security Systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
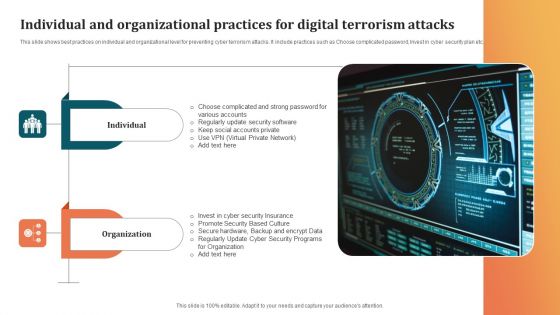
Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF
This slide shows best practices on individual and organizational level for preventing cyber terrorism attacks. It include practices such as Choose complicated password, Invest in cyber security plan etc. Pitch your topic with ease and precision using this Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF. This layout presents information on Organization, Promote Security, Security Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
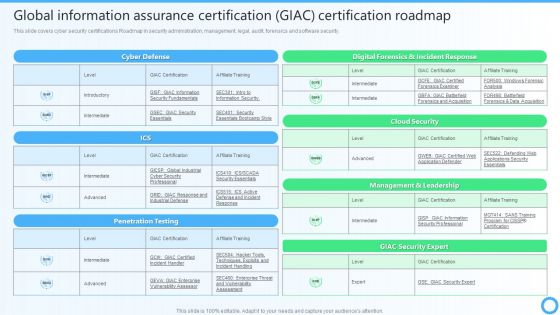
Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security.This Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
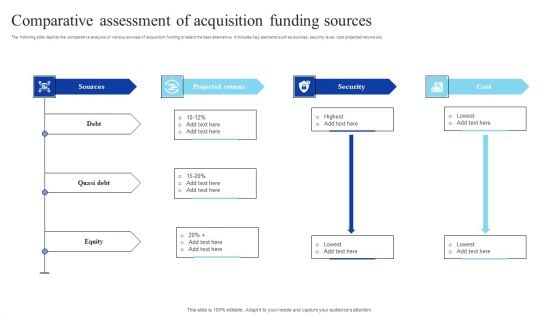
Comparative Assessment Of Acquisition Funding Sources Graphics PDF
The following slide depicts the comparative analysis of various sources of acquisition funding to select the best alternative. It includes key elements such as sources, security level, cost projected returns etc. Showcasing this set of slides titled Comparative Assessment Of Acquisition Funding Sources Graphics PDF. The topics addressed in these templates are Sources, Projected Returns, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Architecture At Scale How To Execute A Cloud Infrastructure Evaluation Determining Ideal Future State Background PDF
This slide emphasize on reviewing current status if company found any gaps in the internal cloud infrastructure and prioritizing approaches to those gaps based on security issues. Presenting cloud architecture at scale how to execute a cloud infrastructure evaluation determining ideal future state background pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud infrastructure, security issues, operational risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Web Consulting Business Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Consulting Business Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.

Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.
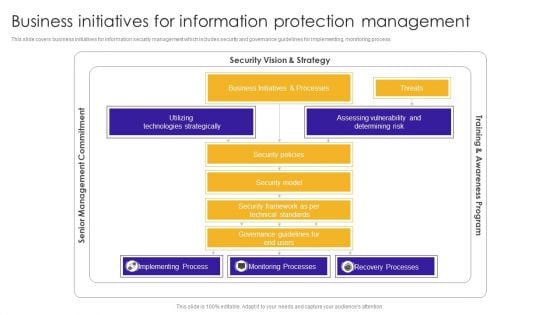
Business Initiatives For Information Protection Management Designs PDF
This slide covers business initiatives for information security management which includes security and governance guidelines for implementing, monitoring process. Pitch your topic with ease and precision using this Business Initiatives For Information Protection Management Designs PDF. This layout presents information on Technologies Strategically, Assessing Vulnerability, Implementing Process. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
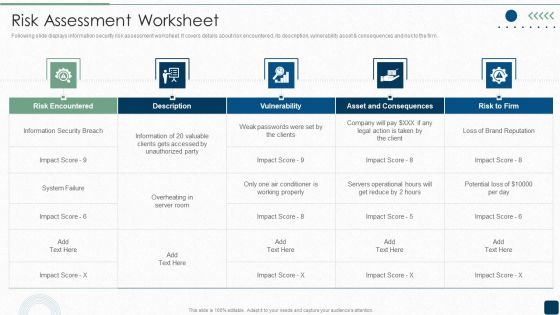
ISO 27001 Certification Procedure Risk Assessment Worksheet Diagrams PDF
Following slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset consequences and risk to the firm.Deliver an awe inspiring pitch with this creative ISO 27001 Certification Procedure Risk Assessment Worksheet Diagrams PDF bundle. Topics like Risk Encountered, Asset And Consequences, Information Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

NIST Cybersecurity Framework Successful Implementation Guide Rules PDF
The slide showcases a guide for the implementation of Nist cyber security framework that help in improving existing capacity of the system or develop a new one. It includes steps like prioritizing and defining scope, identifying and determining a current profile, risk evaluation, target determining, analyzing gaps and implementation stage. Showcasing this set of slides titled NIST Cybersecurity Framework Successful Implementation Guide Rules PDF. The topics addressed in these templates are Define Scope, Current Profile, Risk Evaluation . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
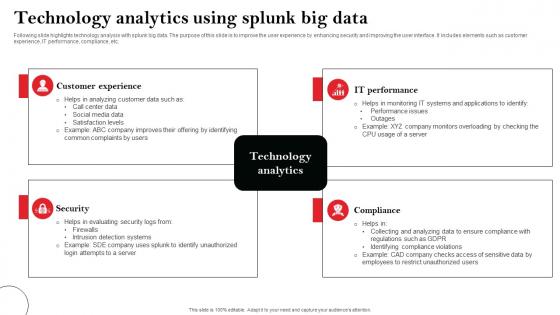
Technology Analytics Using Splunk Big Data Microsoft Pdf
Following slide highlights technology analysis with splunk big data. The purpose of this slide is to improve the user experience by enhancing security and improving the user interface. It includes elements such as customer experience, IT performance, compliance, etc. Pitch your topic with ease and precision using this Technology Analytics Using Splunk Big Data Microsoft Pdf This layout presents information on Customer Experience, Security, Compliance It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide highlights technology analysis with splunk big data. The purpose of this slide is to improve the user experience by enhancing security and improving the user interface. It includes elements such as customer experience, IT performance, compliance, etc.

Key Challenges Faced By Businesses During B2B Payments B2B Digital Commerce Themes Pdf
This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Key Challenges Faced By Businesses During B2B Payments B2B Digital Commerce Themes Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking.
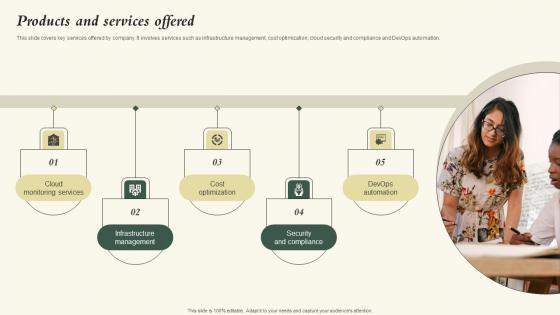
Products And Services Offered Nubity Capital Funding Pitch Deck Guidelines Pdf
This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Nubity Capital Funding Pitch Deck Guidelines Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation.

Cryptocurrencies Available For Trading On Complete Roadmap To Blockchain BCT SS V
This slide covers types of coins available for trading on Kraken crypto exchange platforms. It includes coins such as bitcoins, Ethereum, XRP, Cardano, Solana, Dogecoin, Polkadot, Polygon, TRON, etc along with ratings for Kraken based on trading, advanced trading features, security and storage, crypto wallets, staking, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cryptocurrencies Available For Trading On Complete Roadmap To Blockchain BCT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide covers types of coins available for trading on Kraken crypto exchange platforms. It includes coins such as bitcoins, Ethereum, XRP, Cardano, Solana, Dogecoin, Polkadot, Polygon, TRON, etc along with ratings for Kraken based on trading, advanced trading features, security and storage, crypto wallets, staking, etc.
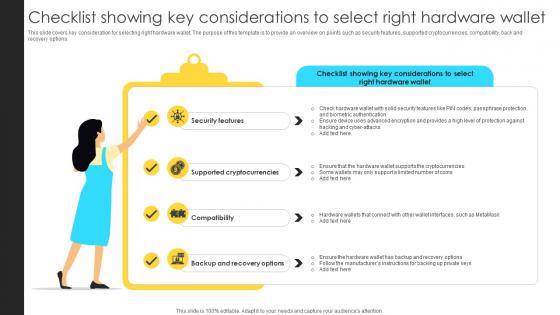
Mastering Blockchain Wallets Checklist Showing Key Considerations To Select Right BCT SS V
This slide covers key consideration for selecting right hardware wallet. The purpose of this template is to provide an overview on points such as security features, supported cryptocurrencies, compatibility, back and recovery options. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Mastering Blockchain Wallets Checklist Showing Key Considerations To Select Right BCT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide covers key consideration for selecting right hardware wallet. The purpose of this template is to provide an overview on points such as security features, supported cryptocurrencies, compatibility, back and recovery options.
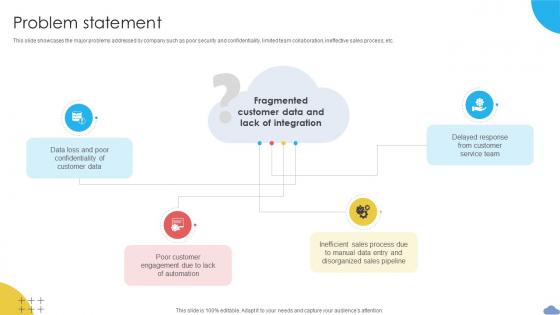
Problem Statement Cloud Based CRM Business Model BMC SS V
This slide showcases the major problems addressed by company such as poor security and confidentiality, limited team collaboration, ineffective sales process, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Problem Statement Cloud Based CRM Business Model BMC SS V can be your best option for delivering a presentation. Represent everything in detail using Problem Statement Cloud Based CRM Business Model BMC SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the major problems addressed by company such as poor security and confidentiality, limited team collaboration, ineffective sales process, etc.

Legal Considerations Payment Gateway Provider Startup GTM Strategy GTM SS V
The following slide showcases legal compliance and considerations for digital payment technology provider startup. It includes elements such as payment card industry data security standard, anti-money laundering, data protection laws, etc.The following slide showcases legal compliance and considerations for digital payment technology provider startup. It includes elements such as payment card industry data security standard, anti-money laundering, data protection laws, etc.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Legal Considerations Payment Gateway Provider Startup GTM Strategy GTM SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide showcases legal compliance and considerations for digital payment technology provider startup. It includes elements such as payment card industry data security standard, anti-money laundering, data protection laws, etc.

Industry Pain Points Powerpoint Ppt Template Bundles
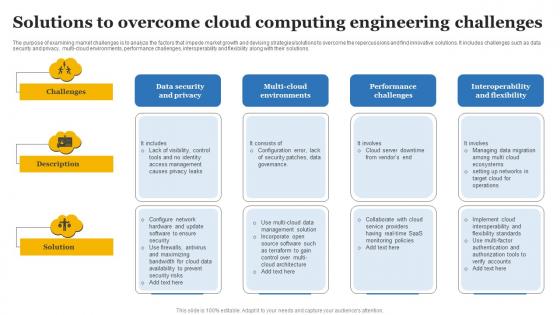
Solutions To Overcome Cloud Computing Engineering Challenges Background Pdf
The purpose of examining market challenges is to analyze the factors that impede market growth and devising strategies solutions to overcome the repercussions and find innovative solutions. It includes challenges such as data security and privacy, multi-cloud environments, performance challenges, interoperability and flexibility along with their solutions. Pitch your topic with ease and precision using this Solutions To Overcome Cloud Computing Engineering Challenges Background Pdf This layout presents information on Data Security And Privacy, Multi Cloud Environments It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of examining market challenges is to analyze the factors that impede market growth and devising strategies solutions to overcome the repercussions and find innovative solutions. It includes challenges such as data security and privacy, multi-cloud environments, performance challenges, interoperability and flexibility along with their solutions.
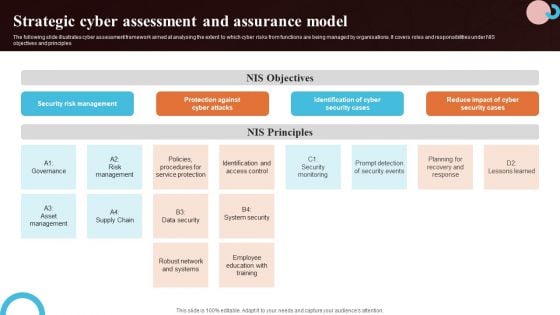
Strategic Cyber Assessment And Assurance Model Microsoft PDF
The following slide illustrates cyber assessment framework aimed at analysing the extent to which cyber risks from functions are being managed by organisations. It covers roles and responsibilities under NIS objectives and principles. Showcasing this set of slides titled Strategic Cyber Assessment And Assurance Model Microsoft PDF. The topics addressed in these templates are Security Cases, System Security, Network And Systems. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Solution Offered Delivery Service Provider Business Model BMC SS V
This slide showcases solutions such as a delivery management system, live tracking, security and reliability, and responsive customer support. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Offered Delivery Service Provider Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases solutions such as a delivery management system, live tracking, security and reliability, and responsive customer support.
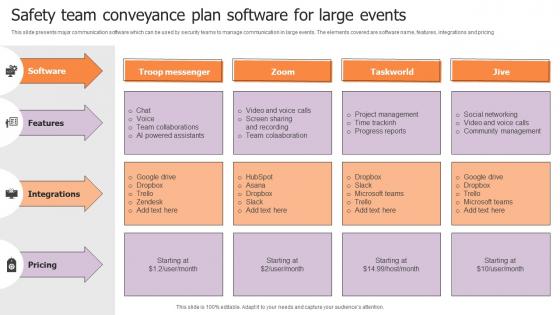
Safety Team Conveyance Plan Software For Large Events Structure Pdf
This slide presents major communication software which can be used by security teams to manage communication in large events. The elements covered are software name, features, integrations and pricing. Pitch your topic with ease and precision using this Safety Team Conveyance Plan Software For Large Events Structure Pdf. This layout presents information on Software, Features, Integrations. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents major communication software which can be used by security teams to manage communication in large events. The elements covered are software name, features, integrations and pricing.
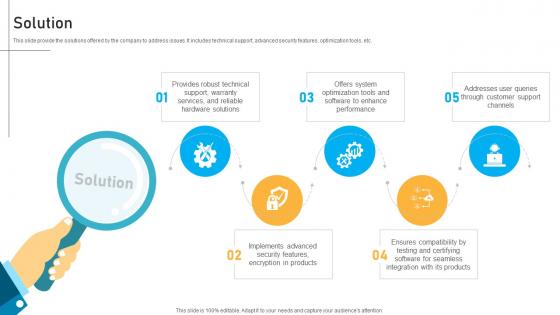
Solution IT Infrastructure Service Provider Business Models BMC SS V
This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution IT Infrastructure Service Provider Business Models BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc.

Implementing Cybersecurity Awareness Program To Prevent Attacks How Much Employees Are Aware Elements PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Implementing Cybersecurity Awareness Program To Prevent Attacks How Much Employees Are Aware Elements PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
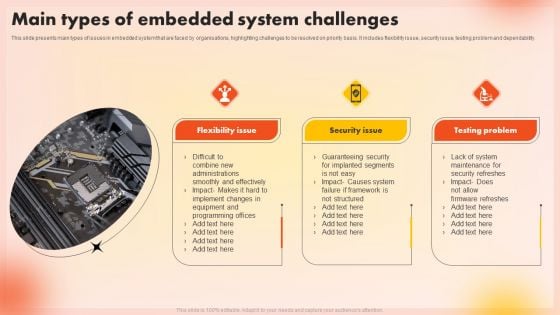
Main Types Of Embedded System Challenges Download PDF
This slide presents main types of issues in embedded system that are faced by organisations, highlighting challenges to be resolved on priority basis. It includes flexibility issue, security issue, testing problem and dependability. Showcasing this set of slides titled Main Types Of Embedded System Challenges Download PDF. The topics addressed in these templates are Flexibility Issue, Security Issue, Testing Problem. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

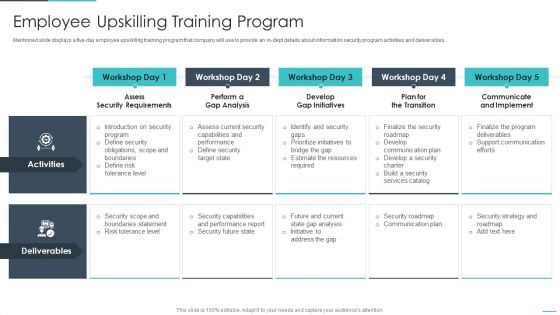
Data Safety Initiatives Employee Upskilling Training Program Portrait PDF
Mentioned slide displays a five-day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. Deliver and pitch your topic in the best possible manner with this data safety initiatives employee upskilling training program portrait pdf. Use them to share invaluable insights on assess security requirements, perform gap analysis, develop gap initiatives, plan transition, communicate and implement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Handling Cyber Threats Digital Era Employee Upskilling Training Program Ppt Professional Master Slide
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. This is a handling cyber threats digital era employee upskilling training program ppt professional master slide template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assess security requirements, perform a gap analysis, develop gap initiatives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
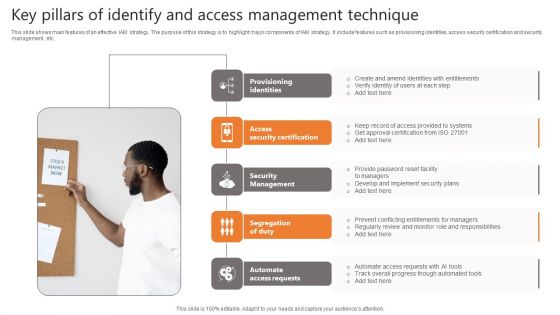
Key Pillars Of Identify And Access Management Technique Topics PDF
This slide shows main features of an effective IAM strategy. The purpose of this strategy is to highlight major components of IAM strategy. It include features such as provisioning identities, access security certification and security management , etc. Presenting Key Pillars Of Identify And Access Management Technique Topics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Provisioning Identities, Security Certification, Security Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Step 3 Assess The Environment Elements PDF
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Step 3 Assess The Environment Elements PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Step 3 Assess The Environment Elements PDF today and make your presentation stand out from the rest

Table Of Contents For Upgrading Total Project Safety IT Graphics PDF
Deliver an awe inspiring pitch with this creative table of contents for upgrading total project safety it graphics pdf bundle. Topics like security centre implementation, project safety management, dashboard analysis, budget assessment, project management team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
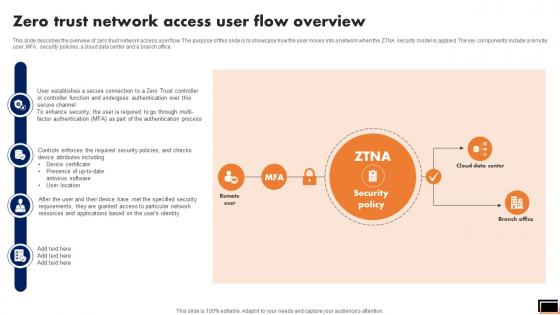
Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
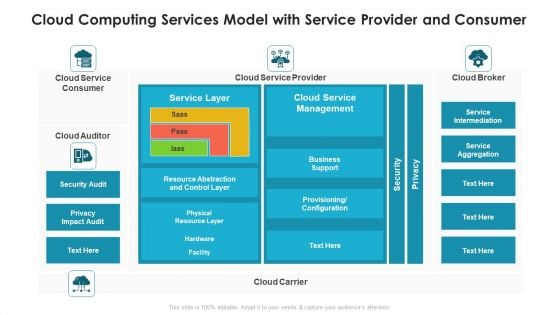
Cloud Computing Services Model With Service Provider And Consumer Ppt PowerPoint Presentation Gallery Mockup PDF
Pitch your topic with ease and precision using this cloud computing services model with service provider and consumer ppt powerpoint presentation gallery mockup pdf. This layout presents information on security audit, management, service aggregation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
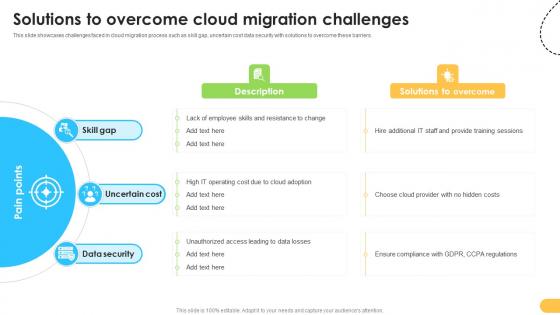
Solutions To Overcome Cloud Migration Challenges Data Migration From On Premises
This slide showcases challenges faced in cloud migration process such as skill gap, uncertain cost data security with solutions to overcome these barriers. Slidegeeks has constructed Solutions To Overcome Cloud Migration Challenges Data Migration From On Premises after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases challenges faced in cloud migration process such as skill gap, uncertain cost data security with solutions to overcome these barriers.

Online Promotion Playbook Interest Based And Safety Net Of Prospecting Slides PDF
This template depicts that majority of prospective audiences are lookalikes. If any target customer falls between the gap of the sales funnel, then they will be captured in the broad interest based audience. Deliver an awe inspiring pitch with this creative online promotion playbook interest based and safety net of prospecting slides pdf bundle. Topics like browsing information, interests, purchasing devices, location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Social Media Brand Promotion Instructions Playbook Interest Based And Safety Net Of Prospecting Clipart PDF
This template depicts that majority of prospective audiences are lookalikes. If any target customer falls between the gap of the sales funnel, then they will be captured in the broad interest based audience.Deliver an awe inspiring pitch with this creative Social Media Brand Promotion Instructions Playbook Interest Based And Safety Net Of Prospecting Clipart PDF bundle. Topics like Browsing Information, Shopping Behavior, Purchasing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
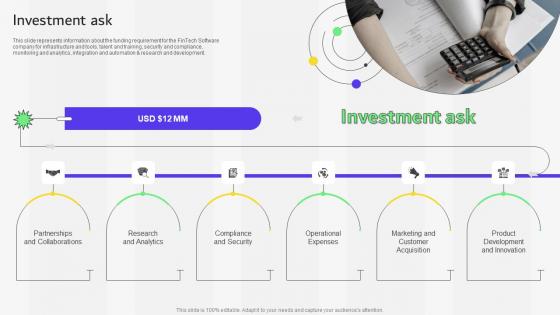
Investment Ask Financial Services Provider Investor Funding Elevator Pitch Deck
This slide represents information about the funding requirement for the FinTech Software company for infrastructure and tools, talent and training, security and compliance, monitoring and analytics, integration and automation and research and development. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Investment Ask Financial Services Provider Investor Funding Elevator Pitch Deck can be your best option for delivering a presentation. Represent everything in detail using Investment Ask Financial Services Provider Investor Funding Elevator Pitch Deck and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents information about the funding requirement for the FinTech Software company for infrastructure and tools, talent and training, security and compliance, monitoring and analytics, integration and automation and research and development.

Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Implementation Software Defined Perimeter SDP is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.
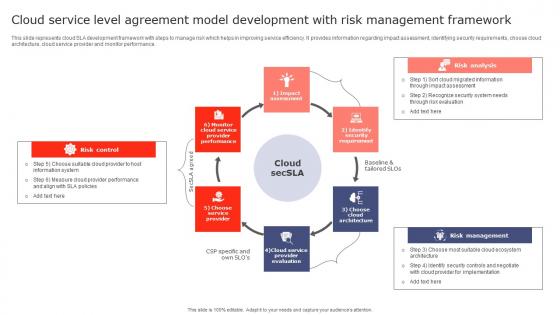
Cloud Service Level Agreement Model Development With Risk Management Framework Inspiration Pdf
This slide represents cloud SLA development framework with steps to manage risk which helps in improving service efficiency. It provides information regarding impact assessment, identifying security requirements, choose cloud architecture, cloud service provider and monitor performance. Showcasing this set of slides titled Cloud Service Level Agreement Model Development With Risk Management Framework Inspiration Pdf. The topics addressed in these templates are Risk Control, Risk Analysis, Risk Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents cloud SLA development framework with steps to manage risk which helps in improving service efficiency. It provides information regarding impact assessment, identifying security requirements, choose cloud architecture, cloud service provider and monitor performance.

Project Change Management Team Org Chart Digital Project Management Strategies
This slide represents details related to org chart of project change management team. It includes details related to steering committee, sponsor, project security officer, etc. Get a simple yet stunning designed Project Change Management Team Org Chart Digital Project Management Strategies. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Project Change Management Team Org Chart Digital Project Management Strategies can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents details related to org chart of project change management team. It includes details related to steering committee, sponsor, project security officer, etc.
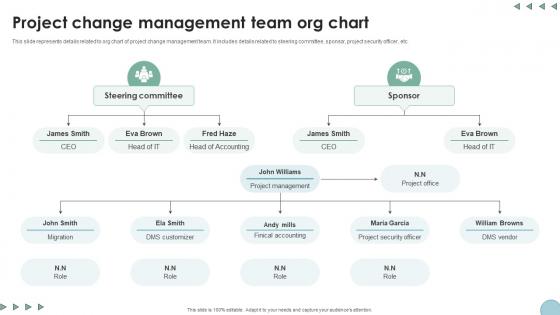
Project Change Management Team Org Chart Digital Transformation In Project Management
This slide represents details related to org chart of project change management team. It includes details related to steering committee, sponsor, project security officer, etc. Presenting this PowerPoint presentation, titled Project Change Management Team Org Chart Digital Transformation In Project Management, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Project Change Management Team Org Chart Digital Transformation In Project Management. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Project Change Management Team Org Chart Digital Transformation In Project Management that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents details related to org chart of project change management team. It includes details related to steering committee, sponsor, project security officer, etc.


 Continue with Email
Continue with Email

 Home
Home


































