Gap Analysis Of Security
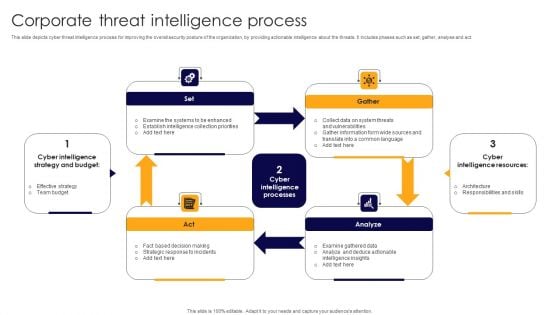
Corporate Threat Intelligence Process Demonstration PDF
This slide depicts cyber threat intelligence process for improving the overall security posture of the organization, by providing actionable intelligence about the threats. It includes phases such as set, gather, analyse and act. Presenting Corporate Threat Intelligence Process Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Fact Based Decision Making, Strategic Response Incidents, Collect Data System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Infographics PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. This is a global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats infographics pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
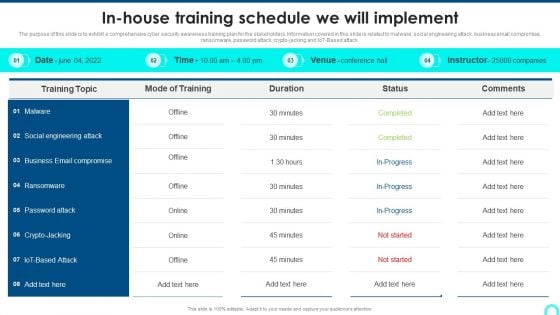
In House Training Schedule We Will Implement Icons PDF

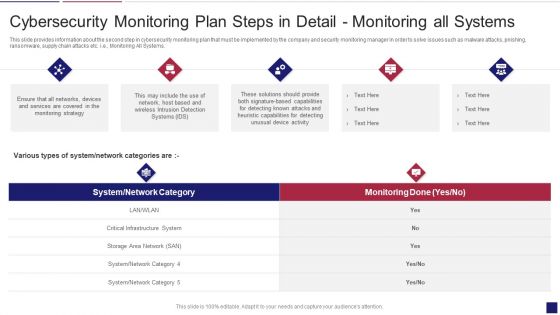
Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems Introduction PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring all systems introduction pdf bundle. Topics like system network category, monitoring done can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

New Website Launch Strategy Web Bug Testing For Improving Virtual Sales Clipart PDF
Mentioned slide provides insights into various testing strategies which can be implemented by web developers to deploy bug free applications. It includes testing strategies such as cross browser, accessibility, HTML and CSS, web security login, performance, and beta testing. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. New Website Launch Strategy Web Bug Testing For Improving Virtual Sales Clipart PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Next Step Infrastructure Maintenance Upkeep Services Proposal One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be tem meeting ,on-site visit etc. Presenting you an exemplary Next Step Infrastructure Maintenance Upkeep Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Step Infrastructure Maintenance Upkeep Services Proposal One Pager Sample Example Document brilliant piece now.

ESO System Center Best Practices Ppt PowerPoint Presentation File Structure PDF
This slide covers enterprise security operation center best practices. It involves practices such as setting up right time, align strategy with business goals, leverage best tools and continuously monitor network. Presenting ESO System Center Best Practices Ppt PowerPoint Presentation File Structure PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Practices, Leverage Best Tools, Continuously Monitor Network. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Contractual Risk Reduction Plan For Construction Firm Sample PDF
Mentioned slide provides insight about risk management plan which can be used by business to improve customer satisfaction. It includes risks such as financial risk, project risk, project implementation risk and security risk Presenting Contractual Risk Reduction Plan For Construction Firm Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Risk Category, Description, Risk Manager. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Systems Graphics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring All Systems. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring systems graphics pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Monitoring Plan Steps In Detail Monitoring User Activity Guidelines PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring User Activity. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring user activity guidelines pdf bundle. Topics like action information, user information, monitoring capability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Key Strategies For Enhancing ESO System Ppt PowerPoint Presentation Icon Outline PDF
This slide covers key strategies for enhancing enterprise security operations. It involves strategies such as detect endpoint threats, leverage advanced analytics and automate incident response. Presenting Key Strategies For Enhancing ESO System Ppt PowerPoint Presentation Icon Outline PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Detect Endpoint Threats, Leverage Advanced Analytics, Automate Incident Response. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Next Step For Post Real Estate Cleaning Proposal One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be teem meeting ,on-site visit etc. Presenting you an exemplary Next Step For Post Real Estate Cleaning Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Step For Post Real Estate Cleaning Proposal One Pager Sample Example Document brilliant piece now.

Proposal For Installing Radio Frequency Identification Next Step One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be tem meeting ,on-site visit etc. Presenting you an exemplary Proposal For Installing Radio Frequency Identification Next Step One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Installing Radio Frequency Identification Next Step One Pager Sample Example Document brilliant piece now.
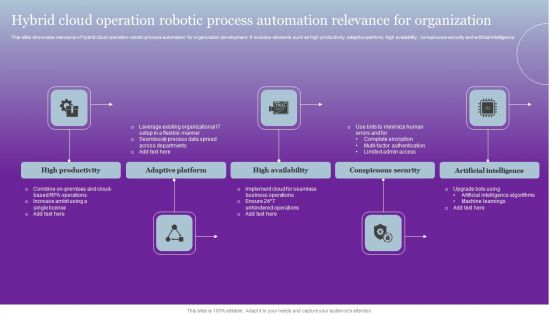
Hybrid Cloud Operation Robotic Process Automation Relevance For Organization Pictures PDF
This slide showcase relevance of hybrid cloud operation robotic process automation for organization development. It includes elements such as high productivity, adaptive platform, high availability, conspicuous security and artificial intelligence. Presenting Hybrid Cloud Operation Robotic Process Automation Relevance For Organization Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including High Productivity, Adaptive Platform, High Availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
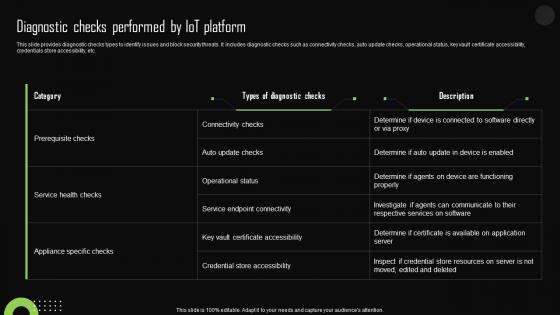
Diagnostic Checks Performed By Iot Platform Iot Device Management Topics Pdf
This slide provides diagnostic checks types to identify issues and block security threats. It includes diagnostic checks such as connectivity checks, auto update checks, operational status, key vault certificate accessibility, credentials store accessibility, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Diagnostic Checks Performed By Iot Platform Iot Device Management Topics Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide provides diagnostic checks types to identify issues and block security threats. It includes diagnostic checks such as connectivity checks, auto update checks, operational status, key vault certificate accessibility, credentials store accessibility, etc.
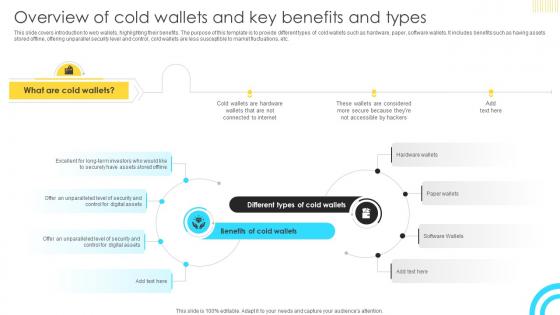
Mastering Blockchain Wallets Overview Of Cold Wallets And Key Benefits BCT SS V
This slide covers introduction to web wallets, highlighting their benefits. The purpose of this template is to provide different types of cold wallets such as hardware, paper, software wallets. It includes benefits such as having assets stored offline, offering unparallel security level and control, cold wallets are less susceptible to market fluctuations, etc. Slidegeeks is here to make your presentations a breeze with Mastering Blockchain Wallets Overview Of Cold Wallets And Key Benefits BCT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers introduction to web wallets, highlighting their benefits. The purpose of this template is to provide different types of cold wallets such as hardware, paper, software wallets. It includes benefits such as having assets stored offline, offering unparallel security level and control, cold wallets are less susceptible to market fluctuations, etc.

The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V
This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. Take your projects to the next level with our ultimate collection of The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc.
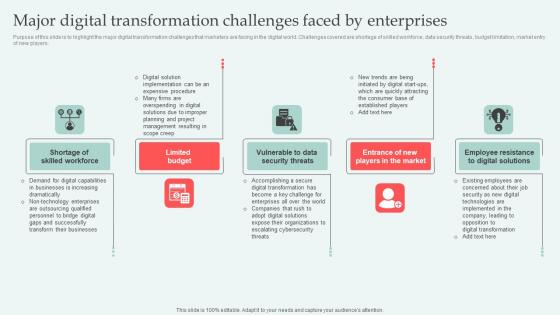
Major Digital Transformation Digital Approaches To Increase Business Growth Formats Pdf
Purpose of this slide is to highlight the major digital transformation challenges that marketers are facing in the digital world. Challenges covered are shortage of skilled workforce, data security threats, budget limitation, market entry of new players. If you are looking for a format to display your unique thoughts, then the professionally designed Major Digital Transformation Digital Approaches To Increase Business Growth Formats Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Major Digital Transformation Digital Approaches To Increase Business Growth Formats Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Purpose of this slide is to highlight the major digital transformation challenges that marketers are facing in the digital world. Challenges covered are shortage of skilled workforce, data security threats, budget limitation, market entry of new players.
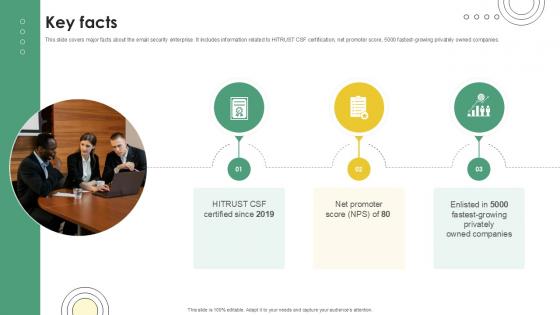
Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint
This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies. If you are looking for a format to display your unique thoughts, then the professionally designed Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies.

Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution. If you are looking for a format to display your unique thoughts, then the professionally designed Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution.

Data Integration Implementation Challenges And Solutions Data Integration Strategies For Business
This slide highlights various limitations of data integration. The purpose of this slide is to discuss the solutions to different challenges associated with data integration. These include security risks, delays in data delivery, resource-constrained, and their solutions. If you are looking for a format to display your unique thoughts, then the professionally designed Data Integration Implementation Challenges And Solutions Data Integration Strategies For Business is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Integration Implementation Challenges And Solutions Data Integration Strategies For Business and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide highlights various limitations of data integration. The purpose of this slide is to discuss the solutions to different challenges associated with data integration. These include security risks, delays in data delivery, resource-constrained, and their solutions.

Customer Data Platform Safety And Privacy Usability Of CDP Software Tool Professional Pdf
The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc. If you are looking for a format to display your unique thoughts, then the professionally designed Customer Data Platform Safety And Privacy Usability Of CDP Software Tool Professional Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Customer Data Platform Safety And Privacy Usability Of CDP Software Tool Professional Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc.
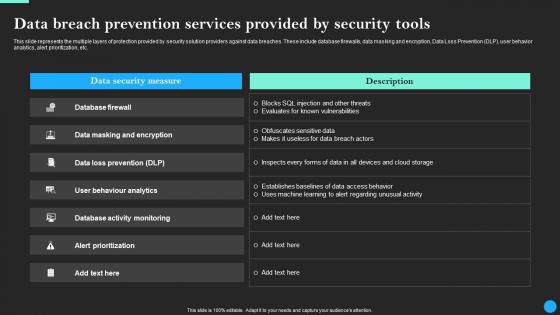
Data Breach Prevention Services Provided Data Breach Prevention Graphics Pdf
This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Breach Prevention Services Provided Data Breach Prevention Graphics Pdfand observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc.
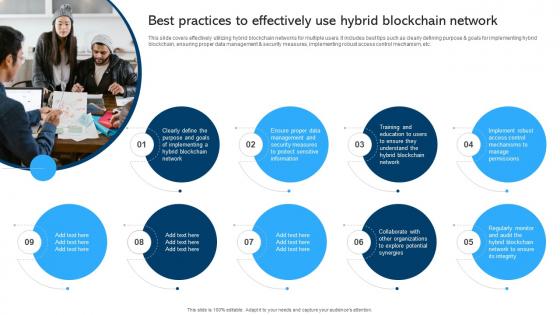
Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V
This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc. Welcome to our selection of the Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc.

Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Are you searching for a Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V from Slidegeeks today. This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.

Zero Trust Model Timeline To Implement Zero Trust Network Access
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Model Timeline To Implement Zero Trust Network Access can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Model Timeline To Implement Zero Trust Network Access and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.
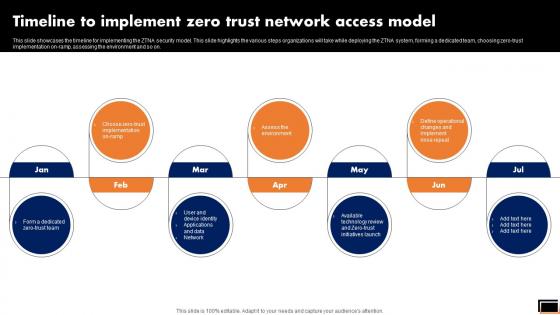
Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.
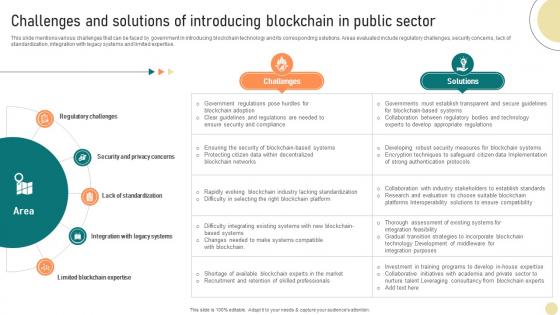
Visionary Guide To Blockchain Challenges And Solutions Of Introducing Blockchain BCT SS V
This slide mentions various challenges that can be faced by government in introducing blockchain technology and its corresponding solutions. Areas evaluated include regulatory challenges, security concerns, lack of standardization, integration with legacy systems and limited expertise. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Visionary Guide To Blockchain Challenges And Solutions Of Introducing Blockchain BCT SS V can be your best option for delivering a presentation. Represent everything in detail using Visionary Guide To Blockchain Challenges And Solutions Of Introducing Blockchain BCT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide mentions various challenges that can be faced by government in introducing blockchain technology and its corresponding solutions. Areas evaluated include regulatory challenges, security concerns, lack of standardization, integration with legacy systems and limited expertise.
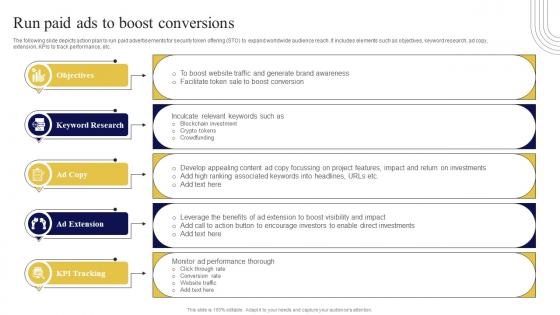
Run Paid Ads To Boost Conversions Exploring Investment Opportunities Diagrams Pdf
The following slide depicts action plan to run paid advertisements for security token offering STO to expand worldwide audience reach. It includes elements such as objectives, keyword research, ad copy, extension, KPIs to track performance, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Run Paid Ads To Boost Conversions Exploring Investment Opportunities Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Run Paid Ads To Boost Conversions Exploring Investment Opportunities Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide depicts action plan to run paid advertisements for security token offering STO to expand worldwide audience reach. It includes elements such as objectives, keyword research, ad copy, extension, KPIs to track performance, etc.
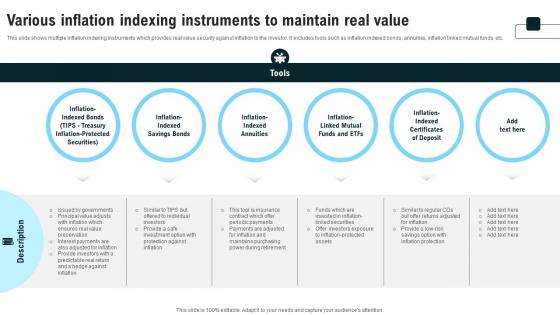
Various Inflation Indexing Instruments To Maintain Real Value Strategies For Inflation A Tactical Guide Fin SS V
This slide shows multiple inflation indexing instruments which provides real value security against inflation to the investor. It includes tools such as inflation indexed bonds, annuities, inflation linked mutual funds, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Various Inflation Indexing Instruments To Maintain Real Value Strategies For Inflation A Tactical Guide Fin SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide shows multiple inflation indexing instruments which provides real value security against inflation to the investor. It includes tools such as inflation indexed bonds, annuities, inflation linked mutual funds, etc.
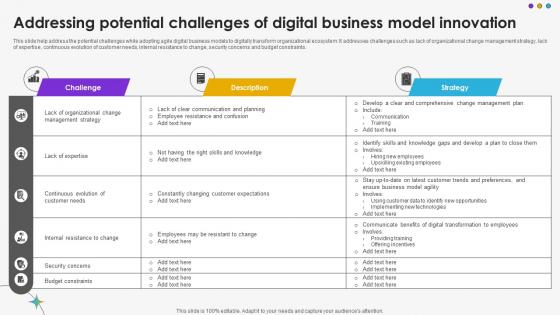
Addressing Potential Challenges Of Digital Business Model Innovation DT SS V
This slide help address the potential challenges while adopting agile digital business models to digitally transform organizational ecosystem. It addresses challenges such as lack of organizational change management strategy, lack of expertise, continuous evolution of customer needs, internal resistance to change, security concerns and budget constraints.Boost your pitch with our creative Addressing Potential Challenges Of Digital Business Model Innovation DT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide help address the potential challenges while adopting agile digital business models to digitally transform organizational ecosystem. It addresses challenges such as lack of organizational change management strategy, lack of expertise, continuous evolution of customer needs, internal resistance to change, security concerns and budget constraints.
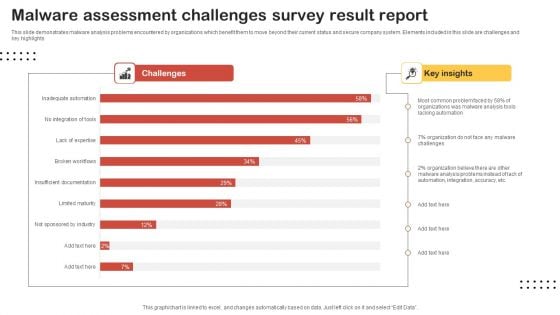
Malware Assessment Challenges Survey Result Report Slides PDF
This slide demonstrates malware analysis problems encountered by organizations which benefit them to move beyond their current status and secure company system. Elements included in this slide are challenges and key highlights. Showcasing this set of slides titled Malware Assessment Challenges Survey Result Report Slides PDF. The topics addressed in these templates are Most Common Problem, Organization, Malware Challenges. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IoT Device Management Fundamentals IoT Device Update Management Process IoT Ss V
This slide exhibits IoT device management and maintenance process in order to avoid security threats. It includes steps such as analyse IoT fleet, Create backup, Test updates, schedule plan, divide fleet into groups, execute updates, and collect feedback. Find highly impressive IoT Device Management Fundamentals IoT Device Update Management Process IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download IoT Device Management Fundamentals IoT Device Update Management Process IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide exhibits IoT device management and maintenance process in order to avoid security threats. It includes steps such as analyse IoT fleet, Create backup, Test updates, schedule plan, divide fleet into groups, execute updates, and collect feedback.
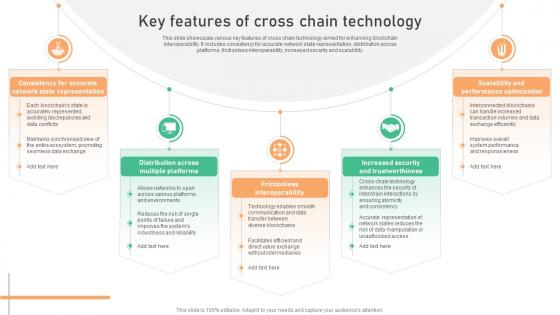
Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Are you searching for a Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V from Slidegeeks today. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.
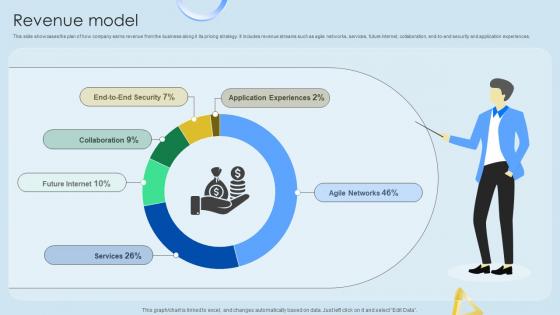
Revenue Model Cloud Networking Service Provider Business Model BMC SS V
This slide showcases the plan of how company earns revenue from the business along it its pricing strategy. It includes revenue streams such as agile networks, services, future internet, collaboration, end-to-end security and application experiences. Find highly impressive Revenue Model Cloud Networking Service Provider Business Model BMC SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Revenue Model Cloud Networking Service Provider Business Model BMC SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the plan of how company earns revenue from the business along it its pricing strategy. It includes revenue streams such as agile networks, services, future internet, collaboration, end-to-end security and application experiences.

Healthcare Information Technology Healthcare Information Tech Enhance Medical Facilities Professional Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Healthcare Information Technology Healthcare Information Tech Enhance Medical Facilities Professional Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.
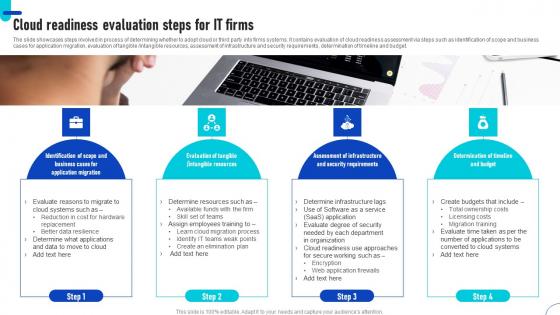
Cloud Readiness Evaluation Steps For IT Firms Ppt Outline Files Pdf
The slide showcases steps involved in process of determining whether to adopt cloud or third party into firms systems. It contains evaluation of cloud readiness assessment via steps such as identification of scope and business cases for application migration, evaluation of tangible intangible resources, assessment of infrastructure and security requirements, determination of timeline and budget. Pitch your topic with ease and precision using this Cloud Readiness Evaluation Steps For IT Firms Ppt Outline Files Pdf. This layout presents information on Determine Resources, Assign Employees Training, Determine Applications. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcases steps involved in process of determining whether to adopt cloud or third party into firms systems. It contains evaluation of cloud readiness assessment via steps such as identification of scope and business cases for application migration, evaluation of tangible intangible resources, assessment of infrastructure and security requirements, determination of timeline and budget.
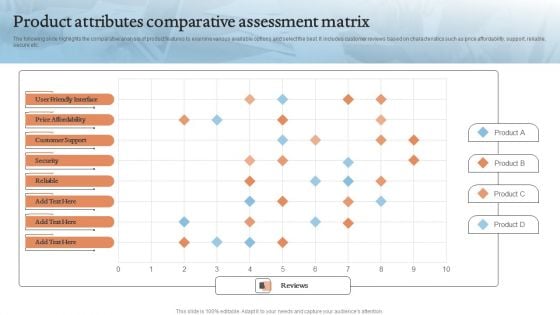
Product Attributes Comparative Assessment Matrix Introduction PDF
The following slide highlights the comparative analysis of product features to examine various available options and select the best. It includes customer reviews based on characteristics such as price affordability, support, reliable, secure etc.Showcasing this set of slides titled Product Attributes Comparative Assessment Matrix Introduction PDF. The topics addressed in these templates are Customer Support, Price Affordability, Friendly Interface. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
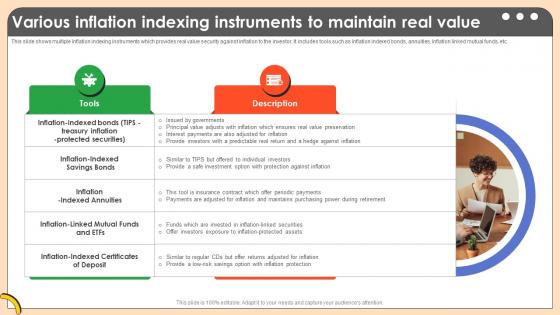
Various Inflation Indexing Instruments To Comprehensive Guide On Inflation Control CM SS V
This slide shows multiple inflation indexing instruments which provides real value security against inflation to the investor. It includes tools such as inflation indexed bonds, annuities, inflation linked mutual funds, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Various Inflation Indexing Instruments To Comprehensive Guide On Inflation Control CM SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Various Inflation Indexing Instruments To Comprehensive Guide On Inflation Control CM SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows multiple inflation indexing instruments which provides real value security against inflation to the investor. It includes tools such as inflation indexed bonds, annuities, inflation linked mutual funds, etc.
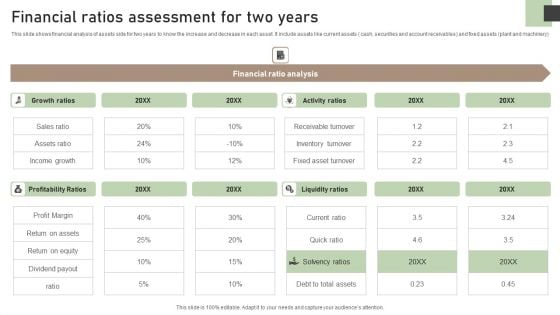
Financial Ratios Assessment For Two Years Designs PDF
This slide shows financial analysis of assets side for two years to know the increase and decrease in each asset. It include assets like current assets cash, securities and account receivables and fixed assets plant and machinery. Showcasing this set of slides titled Financial Ratios Assessment For Two Years Designs PDF. The topics addressed in these templates are Growth Ratios, Profitability Ratios, Liquidity Ratios. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
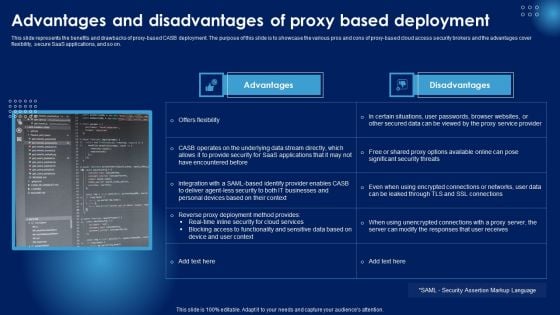
Advantages And Disadvantages Of Proxy Based Deployment Ppt PowerPoint Presentation Diagram Images PDF
This slide represents the benefits and drawbacks of proxy-based CASB deployment. The purpose of this slide is to showcase the various pros and cons of proxy-based cloud access security brokers and the advantages cover flexibility, secure SaaS applications, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Advantages And Disadvantages Of Proxy Based Deployment Ppt PowerPoint Presentation Diagram Images PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Advantages And Disadvantages Of Proxy Based Deployment Ppt PowerPoint Presentation Diagram Images PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
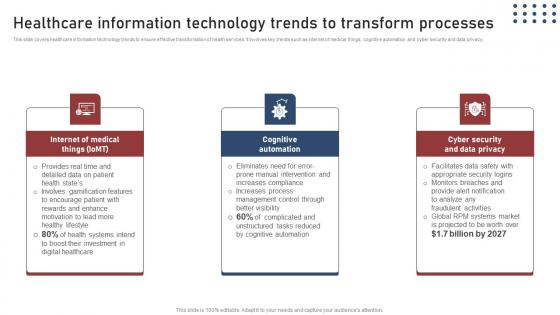
Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. If you are looking for a format to display your unique thoughts, then the professionally designed Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.
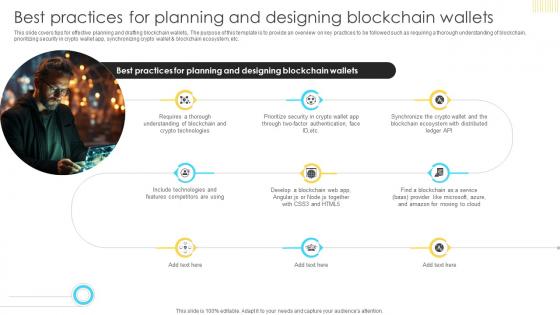
Mastering Blockchain Wallets Best Practices For Planning And Designing Blockchain BCT SS V
This slide covers tips for effective planning and drafting blockchain wallets,. The purpose of this template is to provide an overview on key practices to be followed such as requiring a thorough understanding of blockchain, prioritizing security in crypto wallet app, synchronizing crypto wallet and blockchain ecosystem, etc. Want to ace your presentation in front of a live audience Our Mastering Blockchain Wallets Best Practices For Planning And Designing Blockchain BCT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide covers tips for effective planning and drafting blockchain wallets,. The purpose of this template is to provide an overview on key practices to be followed such as requiring a thorough understanding of blockchain, prioritizing security in crypto wallet app, synchronizing crypto wallet and blockchain ecosystem, etc.
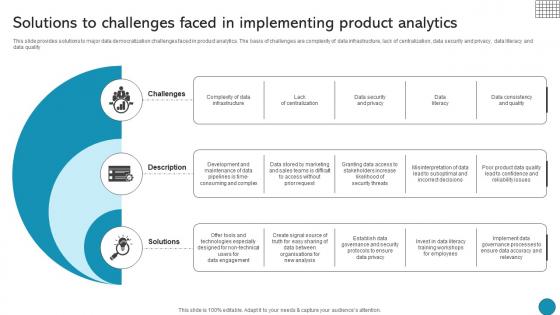
Solutions To Challenges Faced In Implementing Product Driving Business Success Integrating Product
This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality If you are looking for a format to display your unique thoughts, then the professionally designed Solutions To Challenges Faced In Implementing Product Driving Business Success Integrating Product is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Solutions To Challenges Faced In Implementing Product Driving Business Success Integrating Product and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides solutions to major data democratization challenges faced in product analytics. The basis of challenges are complexity of data infrastructure, lack of centralization, data security and privacy, data literacy and data quality

Iot Device Update Management Process Iot Device Management Background Pdf
This slide exhibits IoT device management and maintenance process in order to avoid security threats. It includes steps such as analyse IoT fleet, Create backup, Test updates, schedule plan, divide fleet into groups, execute updates, and collect feedback. This Iot Device Update Management Process Iot Device Management Background Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide exhibits IoT device management and maintenance process in order to avoid security threats. It includes steps such as analyse IoT fleet, Create backup, Test updates, schedule plan, divide fleet into groups, execute updates, and collect feedback.
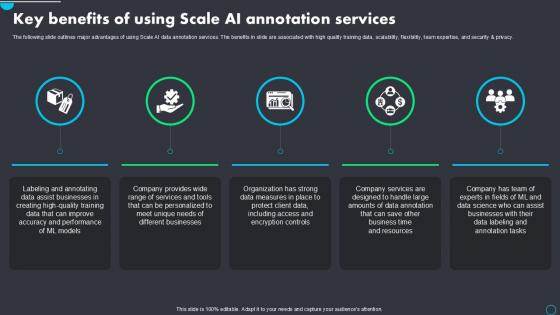
Key Benefits Of Using Implementing Scale AI PPT Presentation AI SS V
The following slide outlines major advantages of using Scale AI data annotation services. The benefits in slide are associated with high quality training data, scalability, flexibility, team expertise, and security and privacy. If you are looking for a format to display your unique thoughts, then the professionally designed Key Benefits Of Using Implementing Scale AI PPT Presentation AI SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Benefits Of Using Implementing Scale AI PPT Presentation AI SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide outlines major advantages of using Scale AI data annotation services. The benefits in slide are associated with high quality training data, scalability, flexibility, team expertise, and security and privacy.
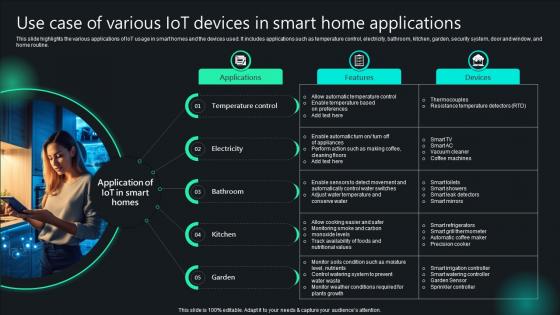
Unlocking Potential IoTs Application Use Case Of Various IoT Devices In Smart Home Applications IoT SS V
This slide highlights the various applications of IoT usage in smart homes and the devices used. It includes applications such as temperature control, electricity, bathroom, kitchen, garden, security system, door and window, and home routine. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Unlocking Potential IoTs Application Use Case Of Various IoT Devices In Smart Home Applications IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide highlights the various applications of IoT usage in smart homes and the devices used. It includes applications such as temperature control, electricity, bathroom, kitchen, garden, security system, door and window, and home routine.
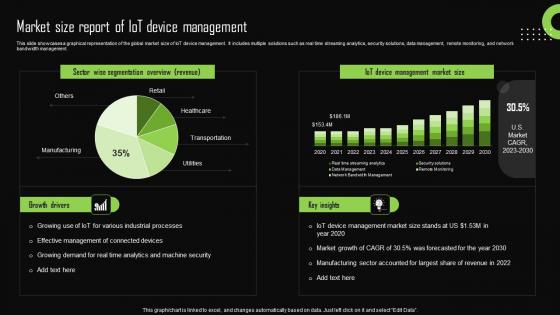
Market Size Report Of Iot Device Management Iot Device Management Demonstration Pdf
This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management. If you are looking for a format to display your unique thoughts, then the professionally designed Market Size Report Of Iot Device Management Iot Device Management Demonstration Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Market Size Report Of Iot Device Management Iot Device Management Demonstration Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management.

Zero Trust Model Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Get a simple yet stunning designed Zero Trust Model Benefits Of Zero Trust Network Access ZTNA. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Benefits Of Zero Trust Network Access ZTNA can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.
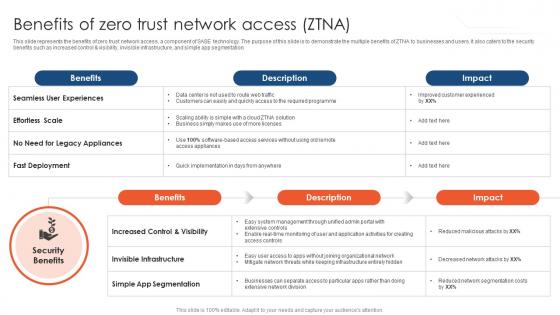
Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.

Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF
This slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
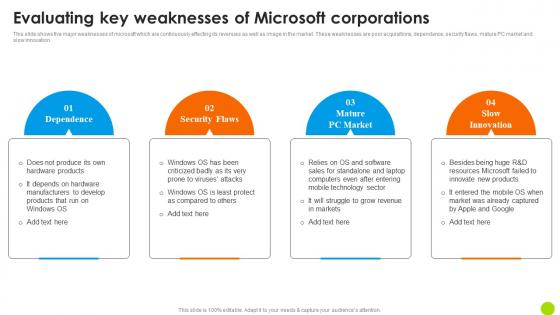
Evaluating Key Weaknesses Of Microsoft Corporations Microsoft Long Term Business Guidelines PDF
This slide shows five major weaknesses of microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation. If you are looking for a format to display your unique thoughts, then the professionally designed Evaluating Key Weaknesses Of Microsoft Corporations Microsoft Long Term Business Guidelines PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Evaluating Key Weaknesses Of Microsoft Corporations Microsoft Long Term Business Guidelines PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows five major weaknesses of microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation.
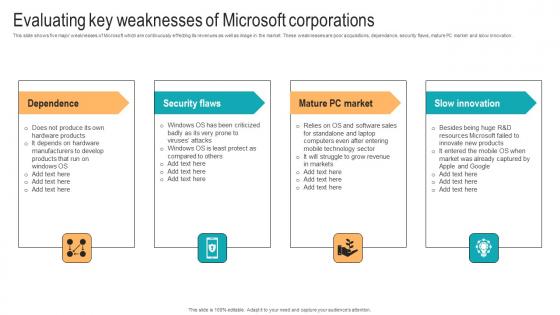
Evaluating Key Weaknesses Of Microsoft Strategic Advancements By Microsofts Microsoft Pdf
This slide shows five major weaknesses of Microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation. If you are looking for a format to display your unique thoughts, then the professionally designed Evaluating Key Weaknesses Of Microsoft Strategic Advancements By Microsofts Microsoft Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Evaluating Key Weaknesses Of Microsoft Strategic Advancements By Microsofts Microsoft Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows five major weaknesses of Microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation.
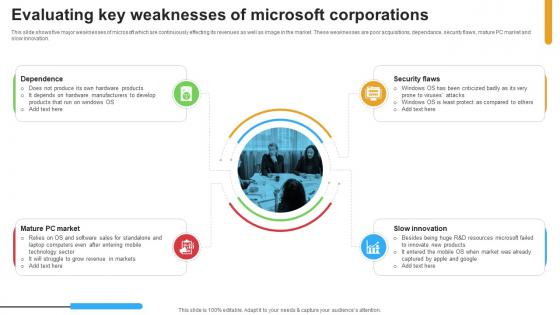
Micosoft Intensive Growth Evaluating Key Weaknesses Of Microsoft Corporations Strategy SS V
This slide shows five major weaknesses of microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation. If you are looking for a format to display your unique thoughts, then the professionally designed Micosoft Intensive Growth Evaluating Key Weaknesses Of Microsoft Corporations Strategy SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Micosoft Intensive Growth Evaluating Key Weaknesses Of Microsoft Corporations Strategy SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows five major weaknesses of microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation.
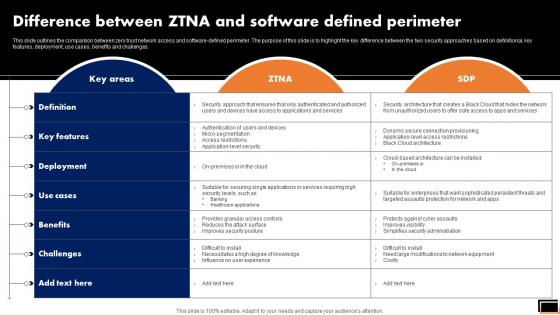
Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.

Zero Trust Model Difference Between ZTNA And Software Defined Perimeter
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Difference Between ZTNA And Software Defined Perimeter and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
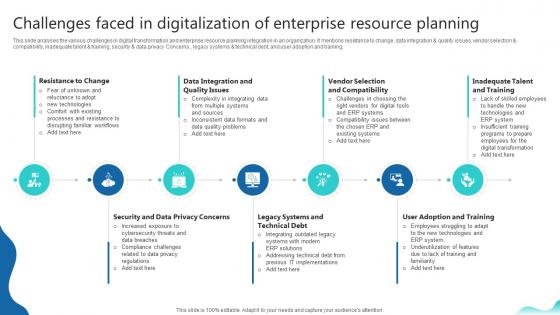
Challenges Faced In Digitalization Of Enterprise Erp And Digital Transformation For Maximizing DT SS V
This slide analyses the various challenges in digital transformation and enterprise resource planning integration in an organization. It mentions resistance to change, data integration and quality issues, vendor selection and compatibility, inadequate talent and training, security and data privacy Concerns , legacy systems and technical debt, and user adoption and training.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Challenges Faced In Digitalization Of Enterprise Erp And Digital Transformation For Maximizing DT SS V can be your best option for delivering a presentation. Represent everything in detail using Challenges Faced In Digitalization Of Enterprise Erp And Digital Transformation For Maximizing DT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide analyses the various challenges in digital transformation and enterprise resource planning integration in an organization. It mentions resistance to change, data integration and quality issues, vendor selection and compatibility, inadequate talent and training, security and data privacy Concerns , legacy systems and technical debt, and user adoption and training.

Major Focus Of White Box Testing Gray Box Testing Best Practices
This slide represents the area of focus for white box testing in software development. The purpose of this slide is to highlight the primary emphasis of white box testing which include path checking, output validation, security testing, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Major Focus Of White Box Testing Gray Box Testing Best Practices and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the area of focus for white box testing in software development. The purpose of this slide is to highlight the primary emphasis of white box testing which include path checking, output validation, security testing, and so on.
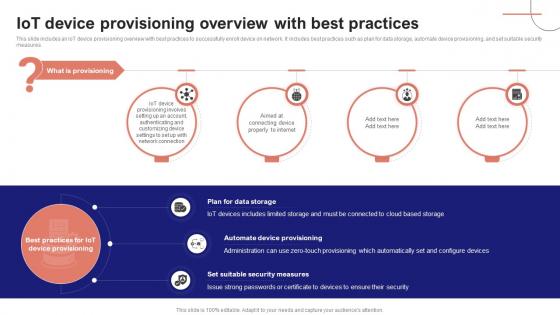
IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT Ss V
This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT SS V can be your best option for delivering a presentation. Represent everything in detail using IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures.


 Continue with Email
Continue with Email

 Home
Home


































