Growth Strategy
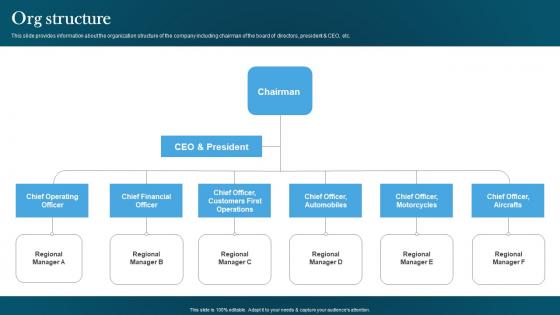
Org Structure Automotive Designing Company Investor Funding Pitch Deck Portrait Pdf
This slide provides information about the organization structure of the company including chairman of the board of directors, president and CEO, etc.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforwardOrg Structure Automotive Designing Company Investor Funding Pitch Deck Portrait Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Org Structure Automotive Designing Company Investor Funding Pitch Deck Portrait Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide provides information about the organization structure of the company including chairman of the board of directors, president and CEO, etc.

Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.
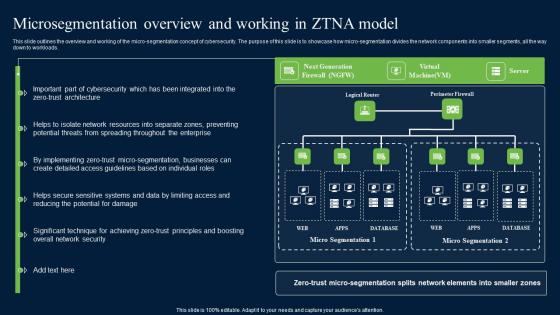
Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.
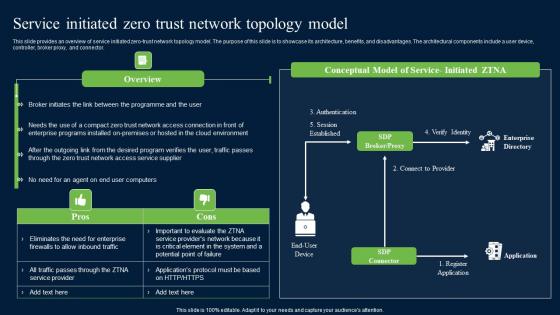
Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Find a pre-designed and impeccable Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.
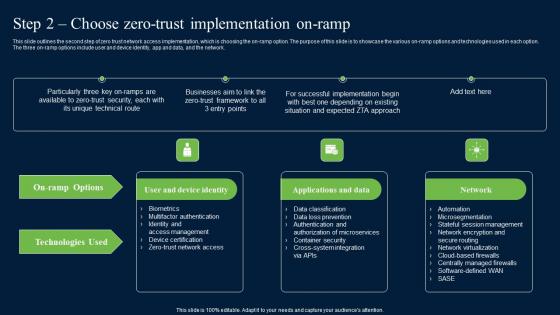
Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.
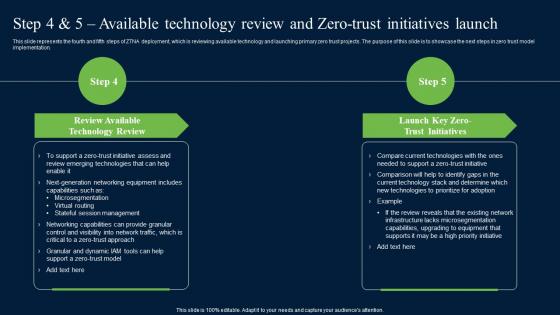
Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. There are so many reasons you need a Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.

Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment.
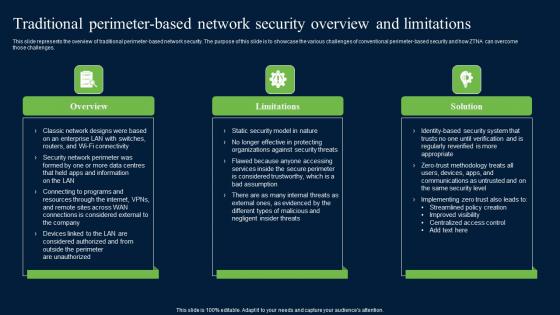
Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. Find highly impressive Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.

Zero Trust Network Access ZTNA Introduction Graphics Pdf
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Find highly impressive Zero Trust Network Access ZTNA Introduction Graphics Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Network Access ZTNA Introduction Graphics Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc.
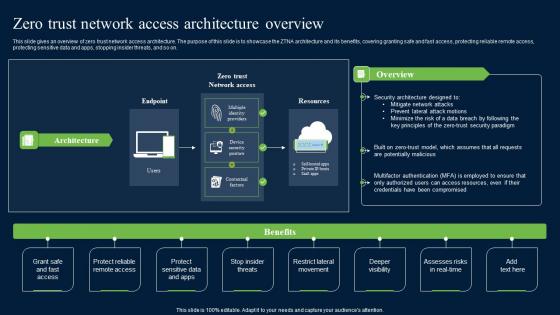
Zero Trust Network Security Access Architecture Overview Graphics Pdf
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Security Access Architecture Overview Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.
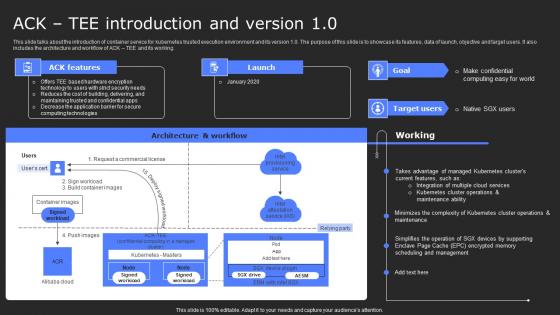
ACK Tee Introduction And Version 10 Secure Computing Framework Slides Pdf
This slide talks about the introduction of container service for kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. Find a pre-designed and impeccable ACK Tee Introduction And Version 10 Secure Computing Framework Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the introduction of container service for kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
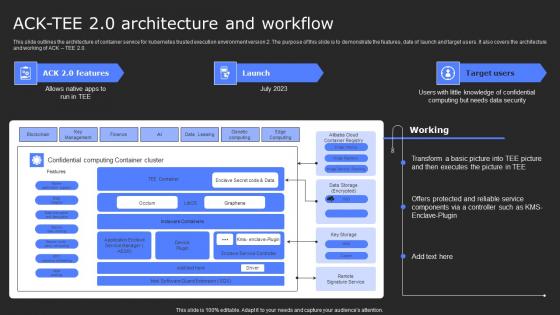
Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf
This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Boost your pitch with our creative Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.
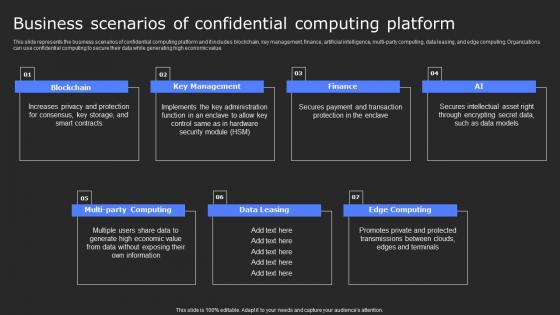
Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. There are so many reasons you need a Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
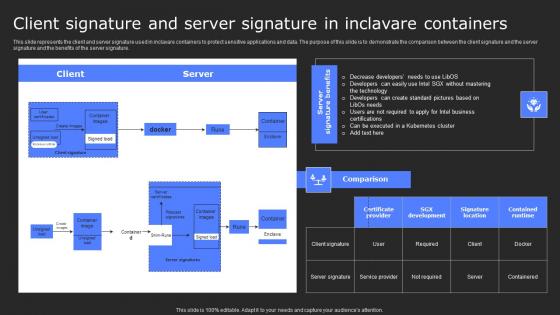
Client Signature And Server Signature In Secure Computing Framework Themes Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Client Signature And Server Signature In Secure Computing Framework Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature.
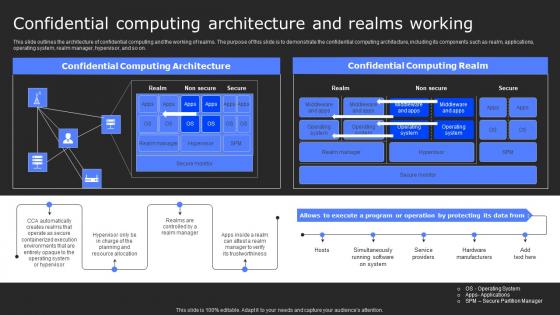
Confidential Computing Architecture And Secure Computing Framework Graphics Pdf
This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Confidential Computing Architecture And Secure Computing Framework Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on.
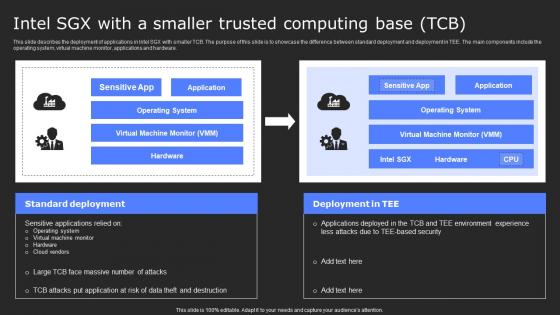
Intel Sgx With A Smaller Trusted Computing Base Tcb Secure Computing Framework Slides Pdf
This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Find a pre-designed and impeccable Intel Sgx With A Smaller Trusted Computing Base Tcb Secure Computing Framework Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware.
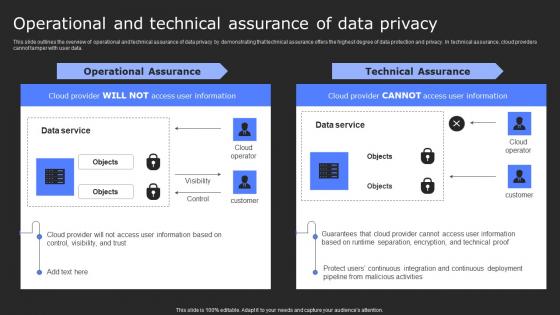
Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. Get a simple yet stunning designed Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data.
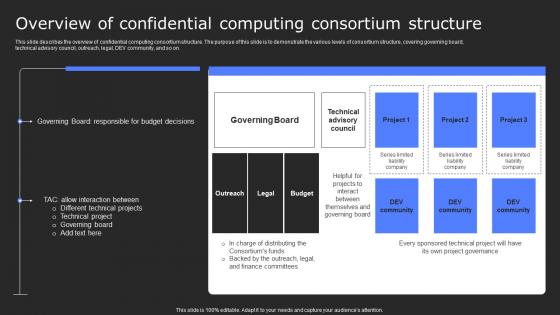
Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on.

Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf
This slide outlines the process of using intel sgx-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing intel sgx-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf today and make your presentation stand out from the rest This slide outlines the process of using intel sgx-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing intel sgx-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing.
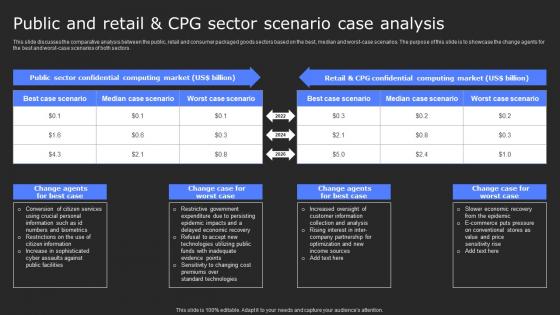
Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.
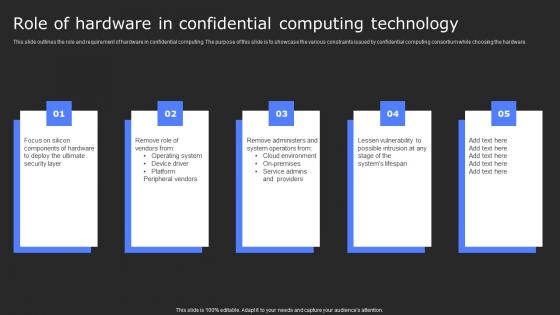
Role Of Hardware In Confidential Computing Secure Computing Framework Brochure Pdf
This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Find highly impressive Role Of Hardware In Confidential Computing Secure Computing Framework Brochure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Hardware In Confidential Computing Secure Computing Framework Brochure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware.

Secure Computing Framework Confidential Computing Architecture Implementation Structure Pdf
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Secure Computing Framework Confidential Computing Architecture Implementation Structure Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.
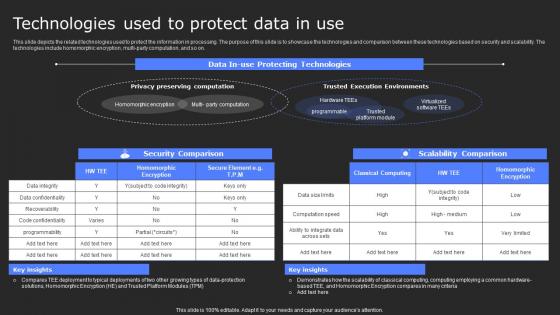
Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. There are so many reasons you need a Technologies Used To Protect Data In Use Secure Computing Framework Diagrams Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
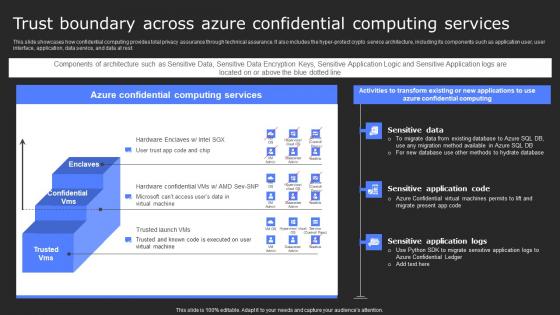
Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
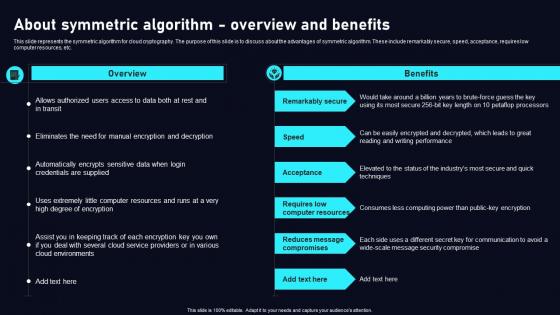
About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc.
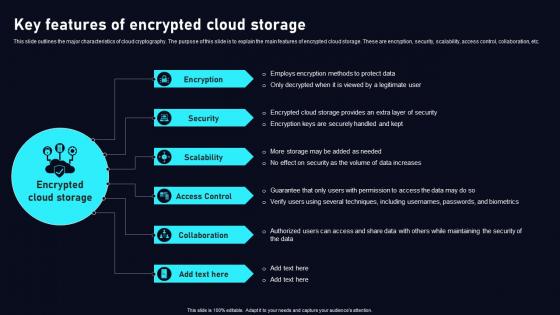
Key Features Of Encrypted Cloud Storage Cloud Data Security Using Cryptography Portrait Pdf
This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Key Features Of Encrypted Cloud Storage Cloud Data Security Using Cryptography Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc.
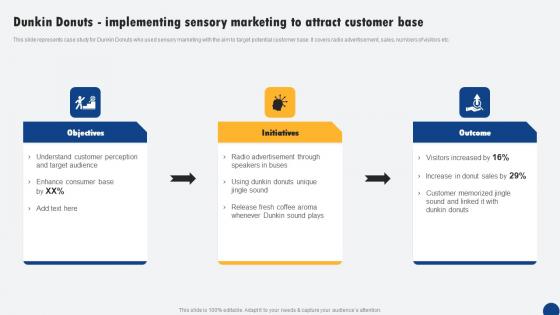
Dunkin Donuts Implementing Sensory Marketing To Driven Digital Marketing Inspiration Pdf
This slide represents case study for Dunkin Donuts who used sensory marketing with the aim to target potential customer base. It covers radio advertisement, sales, numbers of visitors etc. There are so many reasons you need a Dunkin Donuts Implementing Sensory Marketing To Driven Digital Marketing Inspiration Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents case study for Dunkin Donuts who used sensory marketing with the aim to target potential customer base. It covers radio advertisement, sales, numbers of visitors etc.
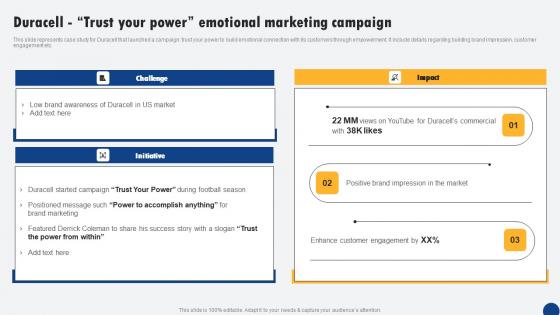
Duracell Trust Your Power Emotional Marketing Driven Digital Marketing Professional Pdf
This slide represents case study for Duracell that launched a campaign trust your power to build emotional connection with its customers through empowerment. It include details regarding building brand impression, customer engagement etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Duracell Trust Your Power Emotional Marketing Driven Digital Marketing Professional Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Duracell Trust Your Power Emotional Marketing Driven Digital Marketing Professional Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents case study for Duracell that launched a campaign trust your power to build emotional connection with its customers through empowerment. It include details regarding building brand impression, customer engagement etc.

How Neuromarketing Enable Effective Product Driven Digital Marketing Elements Pdf
This slide represents role of neuromarketing in product packaging and designing that helps marketers to attract customers in market. It covers customer purchase decision, consumer perception etc. Find highly impressive How Neuromarketing Enable Effective Product Driven Digital Marketing Elements Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download How Neuromarketing Enable Effective Product Driven Digital Marketing Elements Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents role of neuromarketing in product packaging and designing that helps marketers to attract customers in market. It covers customer purchase decision, consumer perception etc.
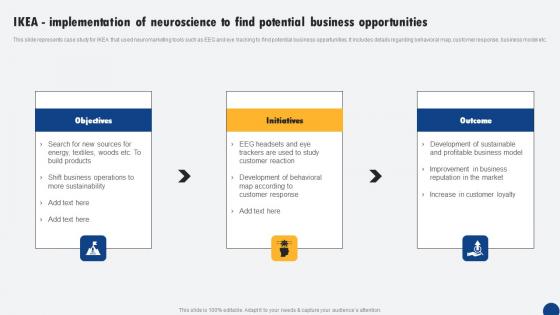
IKEA Implementation Of Neuroscience To Find Potential Driven Digital Marketing Topics Pdf
This slide represents case study for IKEA that used neuromarketing tools such as EEG and eye tracking to find potential business opportunities. It includes details regarding behavioral map, customer response, business model etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IKEA Implementation Of Neuroscience To Find Potential Driven Digital Marketing Topics Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IKEA Implementation Of Neuroscience To Find Potential Driven Digital Marketing Topics Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents case study for IKEA that used neuromarketing tools such as EEG and eye tracking to find potential business opportunities. It includes details regarding behavioral map, customer response, business model etc.
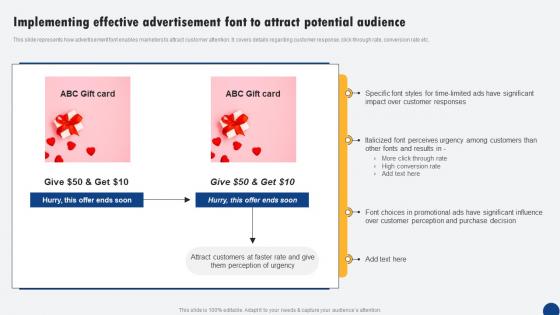
Implementing Effective Advertisement Font To Attract Driven Digital Marketing Inspiration Pdf
This slide represents how advertisement font enables marketers to attract customer attention. It covers details regarding customer response, click-through rate, conversion rate etc. This modern and well-arranged Implementing Effective Advertisement Font To Attract Driven Digital Marketing Inspiration Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents how advertisement font enables marketers to attract customer attention. It covers details regarding customer response, click-through rate, conversion rate etc.
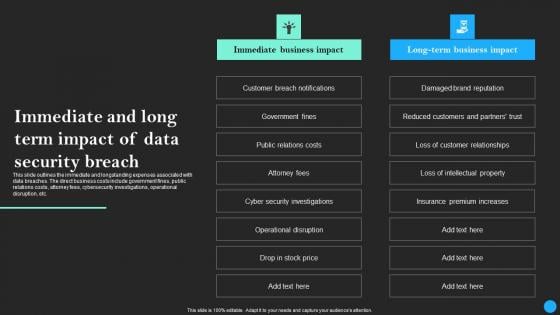
Immediate And Long Term Impact Of Data Security Breach Data Breach Prevention Topics Pdf
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Retrieve professionally designed Immediate And Long Term Impact Of Data Security Breach Data Breach Prevention Topics Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc.
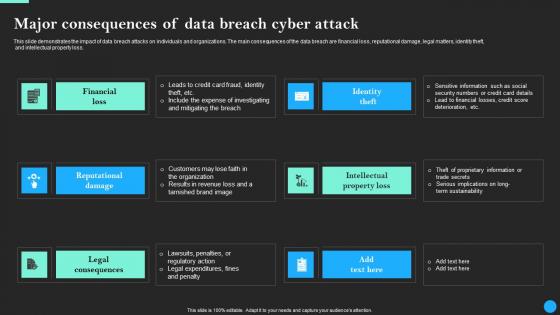
Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf
This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Presenting this PowerPoint presentation, titled Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss.
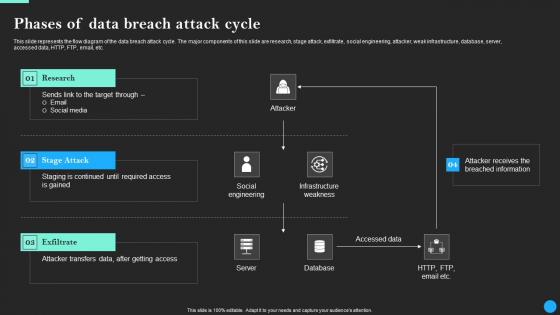
Phases Of Data Breach Attack Cycle Data Breach Prevention Template Pdf
Find a pre-designed and impeccable Phases Of Data Breach Attack Cycle Data Breach Prevention Template Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents the flow diagram of the data breach attack cycle. The major components of this slide are research, stage attack, exfiltrate, social engineering, attacker, weak infrastructure, database, server, accessed data, HTTP, FTP, email, etc.
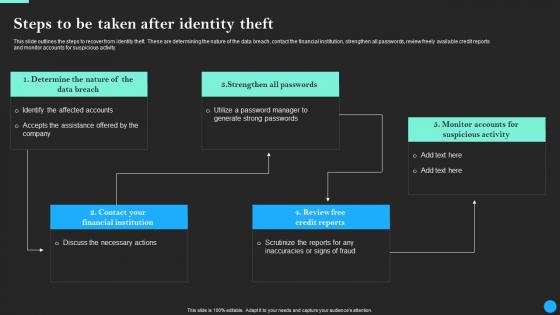
Steps To Be Taken After Identity Theft Data Breach Prevention Microsoft Pdf
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Steps To Be Taken After Identity Theft Data Breach Prevention Microsoft Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Steps To Be Taken After Identity Theft Data Breach Prevention Microsoft Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the steps to recover from identity theft. These are determining the nature of the data breach, contact the financial institution, strengthen all passwords, review freely available credit reports and monitor accounts for suspicious activity.
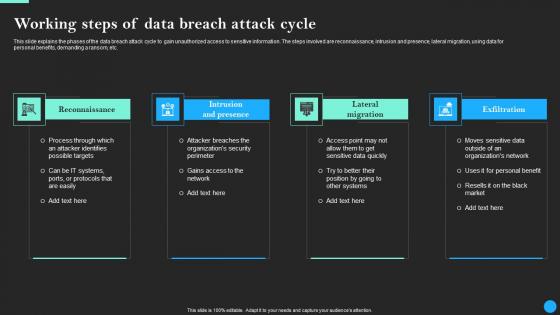
Working Steps Of Data Breach Attack Cycle Data Breach Prevention Infographics Pdf
This slide explains the phases of the data breach attack cycle to gain unauthorized access to sensitive information. The steps involved are reconnaissance, intrusion and presence, lateral migration, using data for personal benefits, demanding a ransom, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Working Steps Of Data Breach Attack Cycle Data Breach Prevention Infographics Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Working Steps Of Data Breach Attack Cycle Data Breach Prevention Infographics Pdf today and make your presentation stand out from the rest This slide explains the phases of the data breach attack cycle to gain unauthorized access to sensitive information. The steps involved are reconnaissance, intrusion and presence, lateral migration, using data for personal benefits, demanding a ransom, etc.

Guiding Principles For Successful Digital Gen Tech Stack Playbook Formats Pdf
This slide provides information regarding guiding principles for successful digital transformation. The stages include value defining, launch and acceleration and scaling up. Key principles include management of senior management commitment, investment tracking, hire potential launch team, capabilities development, etc. Get a simple yet stunning designed Guiding Principles For Successful Digital Gen Tech Stack Playbook Formats Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Guiding Principles For Successful Digital Gen Tech Stack Playbook Formats Pdfcan be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide provides information regarding guiding principles for successful digital transformation. The stages include value defining, launch and acceleration and scaling up. Key principles include management of senior management commitment, investment tracking, hire potential launch team, capabilities development, etc.

Omnichannel Payment Solution Minimizing Customer Transaction Vulnerabilities Professional Pdf
The following slide showcases omni channel payment solution to mitigate risks. It provides details about unwavering controls, configurable workflows, virtual cards, managed services, industry standards, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Omnichannel Payment Solution Minimizing Customer Transaction Vulnerabilities Professional Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide showcases omni channel payment solution to mitigate risks. It provides details about unwavering controls, configurable workflows, virtual cards, managed services, industry standards, etc.

Our Solution Circuit Designing Company Investor Fund Raising Pitch Deck Introduction Pdf
The slide mentions the solutions provided by the company to its customers. Various solutions offered are world class computational software for designing aspects of electronic systems, AI driven verification, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Our Solution Circuit Designing Company Investor Fund Raising Pitch Deck Introduction Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The slide mentions the solutions provided by the company to its customers. Various solutions offered are world class computational software for designing aspects of electronic systems, AI driven verification, etc.

Chat Bots Use Cases In B2B Digital Platform Administration For B2B Ecommerce Background Pdf
This slide represents use cases for chatbots in b2b ecommerce website with their key benefits. It covers answering customer queries, collection of customer complains, advertising alerts etc. Find highly impressive Chat Bots Use Cases In B2B Digital Platform Administration For B2B Ecommerce Background Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Chat Bots Use Cases In B2B Digital Platform Administration For B2B Ecommerce Background Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents use cases for chatbots in b2b ecommerce website with their key benefits. It covers answering customer queries, collection of customer complains, advertising alerts etc.

Myths And Facts Regarding B2B Digital Platform Administration For B2B Ecommerce Microsoft Pdf
This slide represents major common misconceptions regarding b2b ecommerce with key facts. It includes b2b ecommerce is uncommon, no demand for b2b in market, ecommerce is for small orders and no custom pricing. Find a pre designed and impeccable Myths And Facts Regarding B2B Digital Platform Administration For B2B Ecommerce Microsoft Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents major common misconceptions regarding b2b ecommerce with key facts. It includes b2b ecommerce is uncommon, no demand for b2b in market, ecommerce is for small orders and no custom pricing.
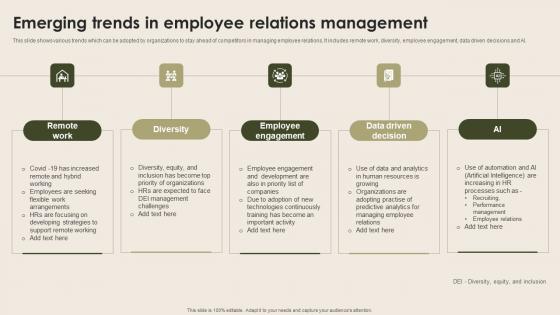
Emerging Trends In Employee Relations Nurturing Positive Work Culture Demonstration Pdf
This slide shows various trends which can be adopted by organizations to stay ahead of competitors in managing employee relations. It includes remote work, diversity, employee engagement, data driven decisions and AI. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Emerging Trends In Employee Relations Nurturing Positive Work Culture Demonstration Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Emerging Trends In Employee Relations Nurturing Positive Work Culture Demonstration Pdf today and make your presentation stand out from the rest This slide shows various trends which can be adopted by organizations to stay ahead of competitors in managing employee relations. It includes remote work, diversity, employee engagement, data driven decisions and AI.

Five Elements Of Employee Relations Management Positive Work Culture Slides Pdf
This slide shows five pillars which can be used by organizations to establish or manage employee relations. It includes organizational culture, employee engagement, conflict resolution, workplace investigations and disciplinary actions. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Five Elements Of Employee Relations Management Positive Work Culture Slides Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide shows five pillars which can be used by organizations to establish or manage employee relations. It includes organizational culture, employee engagement, conflict resolution, workplace investigations and disciplinary actions.

Comparison Between Fwaas And Cloud Firewalls Network Security Portrait Pdf
This slide illustrates the concept of cloud firewalls and Firewall-as-a-Service. The purpose of this slide is to explain if cloud firewalls, and Firewall-as-Service are same or not. This slide also talks about the correlation of both the terms with each other. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Comparison Between Fwaas And Cloud Firewalls Network Security Portrait Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide illustrates the concept of cloud firewalls and Firewall-as-a-Service. The purpose of this slide is to explain if cloud firewalls, and Firewall-as-Service are same or not. This slide also talks about the correlation of both the terms with each other.
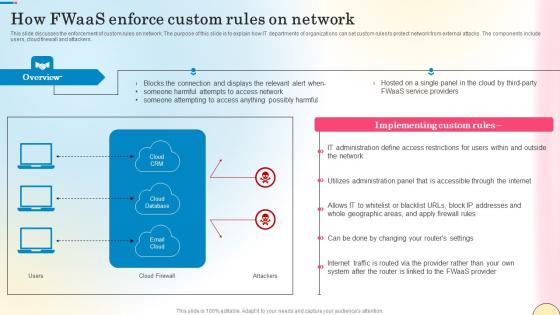
How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf
This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers. This How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers.

Overview Of Secure Access Service Edge Network Security Download Pdf
This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc. Boost your pitch with our creative Overview Of Secure Access Service Edge Network Security Download Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Overview Of Secure Access Service Edge Network Security Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Top Firewall As A Service Technology Trends Network Security Mockup Pdf
This slide outlines the top Firewall-as-a-Service trends. The purpose of this slide is to briefly explain the top current FWaaS trends. These include firewalls remain important, zero trust in the cloud, isolation of security from the underlying infrastructure, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Top Firewall As A Service Technology Trends Network Security Mockup Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Top Firewall As A Service Technology Trends Network Security Mockup Pdf today and make your presentation stand out from the rest This slide outlines the top Firewall-as-a-Service trends. The purpose of this slide is to briefly explain the top current FWaaS trends. These include firewalls remain important, zero trust in the cloud, isolation of security from the underlying infrastructure, etc.
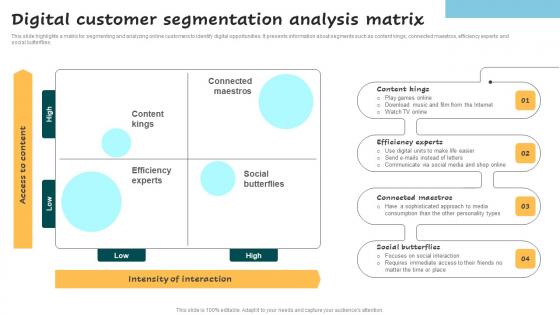
Digital Customer Segmentation Analysis Matrix Successful Guide For Market Segmentation Elements Pdf
This slide highlights a matrix for segmenting and analyzing online customers to identify digital opportunities. It presents information about segments such as content kings, connected maestros, efficiency experts and social butterflies. Find highly impressive Digital Customer Segmentation Analysis Matrix Successful Guide For Market Segmentation Elements Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Digital Customer Segmentation Analysis Matrix Successful Guide For Market Segmentation Elements Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide highlights a matrix for segmenting and analyzing online customers to identify digital opportunities. It presents information about segments such as content kings, connected maestros, efficiency experts and social butterflies.
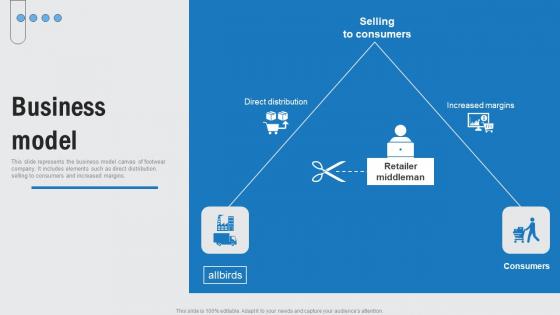
Business Model Footwear Company Funding Elevator Pitch Deck Microsoft Pdf
This slide represents the business model canvas of footwear company. It includes elements such as direct distribution, selling to consumers and increased margins. Boost your pitch with our creative Business Model Footwear Company Funding Elevator Pitch Deck Microsoft Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the business model canvas of footwear company. It includes elements such as direct distribution, selling to consumers and increased margins.
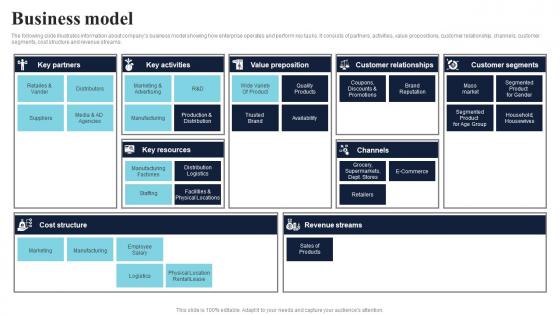
Business Model Healthcare Product Company Fund Raising Pitch Deck Introduction Pdf
The following slide illustrates information about companys business model showing how enterprise operates and perform key tasks. It consists of partners, activities, value propositions, customer relationship, channels, customer segments, cost structure and revenue streams. The Business Model Healthcare Product Company Fund Raising Pitch Deck Introduction Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The following slide illustrates information about companys business model showing how enterprise operates and perform key tasks. It consists of partners, activities, value propositions, customer relationship, channels, customer segments, cost structure and revenue streams.
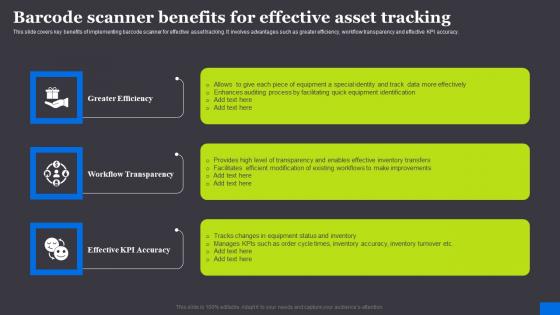
Barcode Scanner Benefits For Effective Asset RFID Solutions For Asset Traceability Portrait Pdf
This slide covers key benefits of implementing barcode scanner for effective asset tracking. It involves advantages such as greater efficiency, workflow transparency and effective KPI accuracy. There are so many reasons you need a Barcode Scanner Benefits For Effective Asset RFID Solutions For Asset Traceability Portrait Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide covers key benefits of implementing barcode scanner for effective asset tracking. It involves advantages such as greater efficiency, workflow transparency and effective KPI accuracy.
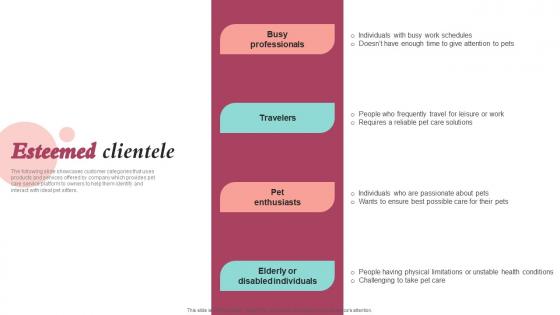
Esteemed Clientele Pet Care Company Investor Funding Elevator Pitch Deck Portrait Pdf
The following slide showcases customer categories that uses products and services offered by company which provides pet care service platform to owners to help them identify and interact with ideal pet sitters. Get a simple yet stunning designed Esteemed Clientele Pet Care Company Investor Funding Elevator Pitch Deck Portrait Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Esteemed Clientele Pet Care Company Investor Funding Elevator Pitch Deck Portrait Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide showcases customer categories that uses products and services offered by company which provides pet care service platform to owners to help them identify and interact with ideal pet sitters.
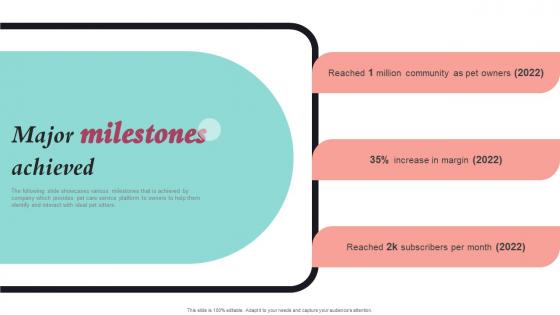
Major Milestones Achieved Pet Care Company Investor Funding Elevator Pitch Deck Slide Pdf
The following slide showcases various milestones that is achieved by company which provides pet care service platform to owners to help them identify and interact with ideal pet sitters. This Major Milestones Achieved Pet Care Company Investor Funding Elevator Pitch Deck Slide Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Major Milestones Achieved Pet Care Company Investor Funding Elevator Pitch Deck Slide Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide showcases various milestones that is achieved by company which provides pet care service platform to owners to help them identify and interact with ideal pet sitters.

Products And Services Offered Pet Care Company Investor Funding Elevator Pitch Deck grids Pdf
This slide shows products services provided by a company which provides pet care service platform to owners to help them identify and interact with ideal pet sitters. It consists of care with host family, care in your own home, daily visit and dog walking. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Products And Services Offered Pet Care Company Investor Funding Elevator Pitch Deck grids Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide shows products services provided by a company which provides pet care service platform to owners to help them identify and interact with ideal pet sitters. It consists of care with host family, care in your own home, daily visit and dog walking.
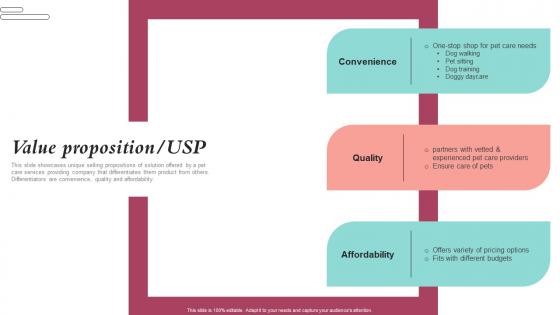
Value Proposition USP Pet Care Company Investor Funding Elevator Pitch Deck Slides Pdf
This slide showcases unique selling propositions of solution offered by a pet care services providing company that differentiates them product from others. Differentiators are convenience, quality and affordability. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Value Proposition USP Pet Care Company Investor Funding Elevator Pitch Deck Slides Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases unique selling propositions of solution offered by a pet care services providing company that differentiates them product from others. Differentiators are convenience, quality and affordability.
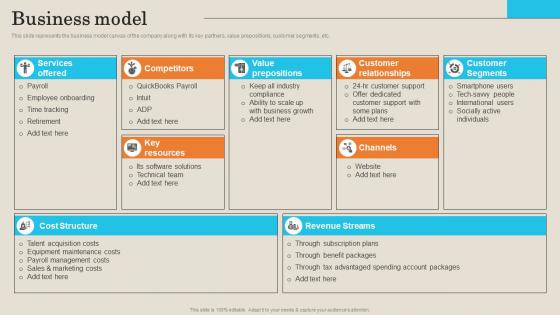
Business Model Employee Management Platform Investor Funding Presentation Introduction Pdf
This slide represents the business model canvas of the company along with its key partners, value prepositions, customer segments, etc. Boost your pitch with our creative Business Model Employee Management Platform Investor Funding Presentation Introduction Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the business model canvas of the company along with its key partners, value prepositions, customer segments, etc.
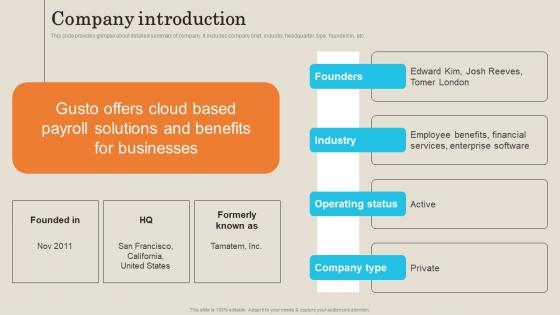
Company Introduction Employee Management Platform Investor Funding Presentation Sample Pdf
This slide provides glimpse about detailed summary of company. It includes company brief, industry, headquarter, type, founded in, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Company Introduction Employee Management Platform Investor Funding Presentation Sample Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides glimpse about detailed summary of company. It includes company brief, industry, headquarter, type, founded in, etc.
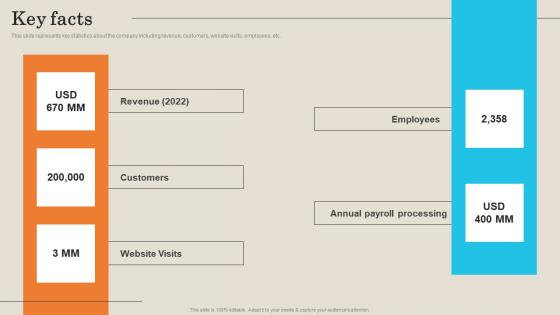
Key Facts Employee Management Platform Investor Funding Presentation Diagrams Pdf
This slide represents key statistics about the company including revenue, customers, website visits, employees, etc. Find highly impressive Key Facts Employee Management Platform Investor Funding Presentation Diagrams Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Key Facts Employee Management Platform Investor Funding Presentation Diagrams Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents key statistics about the company including revenue, customers, website visits, employees, etc.

Major Milestones Employee Management Platform Investor Funding Presentation Infographics Pdf
This slide provides glimpse about aspirations achieved by the company including best overall payroll software, best dependable payroll, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Major Milestones Employee Management Platform Investor Funding Presentation Infographics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provides glimpse about aspirations achieved by the company including best overall payroll software, best dependable payroll, etc.
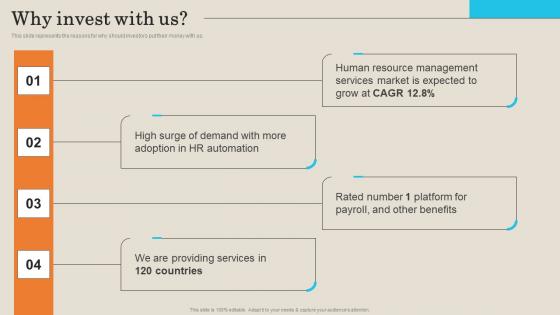
Why Invest With Us Employee Management Platform Investor Funding Presentation Graphics Pdf
This slide represents the reasons for why should investors put their money with us. Explore a selection of the finest Why Invest With Us Employee Management Platform Investor Funding Presentation Graphics Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Why Invest With Us Employee Management Platform Investor Funding Presentation Graphics Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the reasons for why should investors put their money with us.


 Continue with Email
Continue with Email

 Home
Home


































