Identity Access Management
Identity Access Management Challenges Ppt PowerPoint Presentation Show Graphic Tips Cpb
Presenting this set of slides with name identity access management challenges ppt powerpoint presentation show graphic tips cpb. This is an editable Powerpoint four stages graphic that deals with topics like identity access management challenges to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Enterprise Identity Access Management Ppt PowerPoint Presentation Infographic Template Templates Cpb
Presenting this set of slides with name enterprise identity access management ppt powerpoint presentation infographic template templates cpb. This is an editable Powerpoint four stages graphic that deals with topics like enterprise identity access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
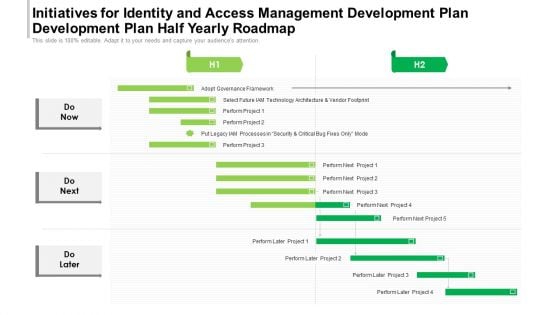
Initiatives For Identity And Access Management Development Plan Development Plan Half Yearly Roadmap Rules
Presenting our innovatively-structured initiatives for identity and access management development plan development plan half yearly roadmap rules Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
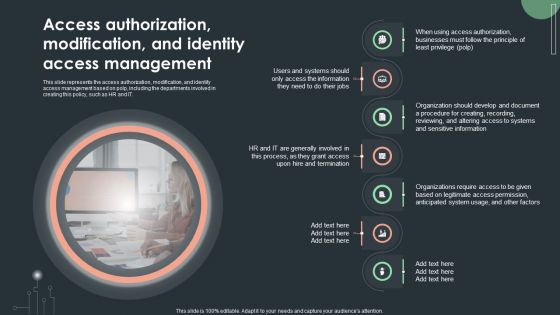
Cybersecurity Guidelines IT Access Authorization Modification And Identity Access Inspiration PDF
This slide represents the access authorization, modification, and identity access management based on polp, including the departments involved in creating this policy, such as HR and IT. Boost your pitch with our creative Cybersecurity Guidelines IT Access Authorization Modification And Identity Access Inspiration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Identity Card Employee Access Ppt PowerPoint Presentation Complete Deck
This identity card employee access ppt powerpoint presentation complete deck acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twelve slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this identity card employee access ppt powerpoint presentation complete deck PPT slideshow.

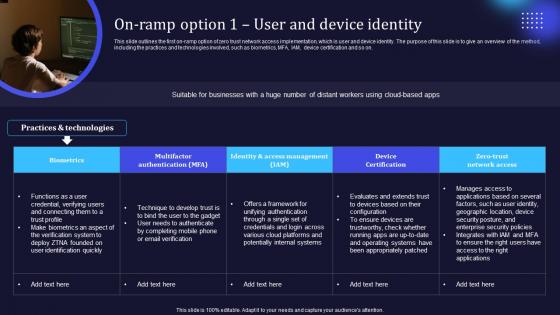
Zero Trust Network Access On Ramp Option 1 User And Device Identity
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. Boost your pitch with our creative Zero Trust Network Access On Ramp Option 1 User And Device Identity. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.
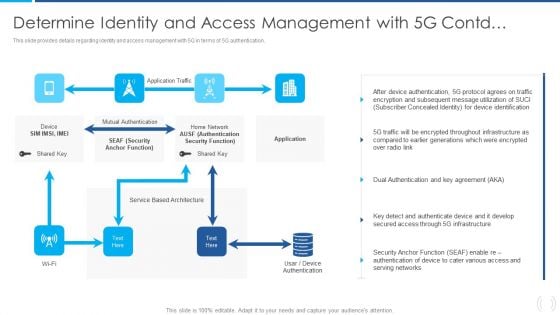
Proactive Method For 5G Deployment By Telecom Companies Determine Identity And Acces Microsoft PDF Structure PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver and pitch your topic in the best possible manner with this Proactive Method For 5G Deployment By Telecom Companies Determine Identity And Acces Microsoft PDF Structure PDF Use them to share invaluable insights on Mutual Authentication, Authentication Security, Service Based and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Client Identity Services In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Client Identity Services In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Client Identity Services that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Client Identity Services In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Anonymous Identity Protection In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Anonymous Identity Protection In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Anonymous Identity Protection that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Anonymous Identity Protection In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Symptoms Dissociative Identity Disorder In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Symptoms Dissociative Identity Disorder In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Symptoms Dissociative Identity Disorder that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Symptoms Dissociative Identity Disorder In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Social Identity Psychology In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Social Identity Psychology In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Social Identity Psychology that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Social Identity Psychology In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
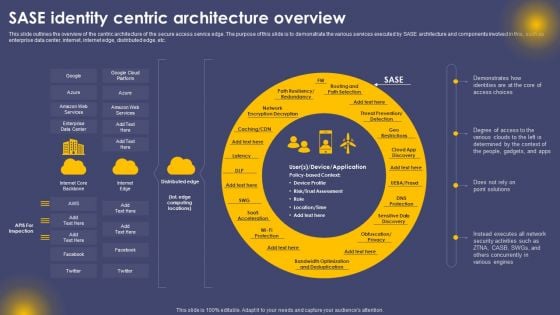
SASE Identity Centric Architecture Overview Ppt Pictures Layouts PDF
This slide outlines the overview of the centric architecture of the secure access service edge. The purpose of this slide is to demonstrate the various services executed by SASE architecture and components involved in this, such as enterprise data center, internet, internet edge, distributed edge, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward SASE Identity Centric Architecture Overview Ppt Pictures Layouts PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal SASE Identity Centric Architecture Overview Ppt Pictures Layouts PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
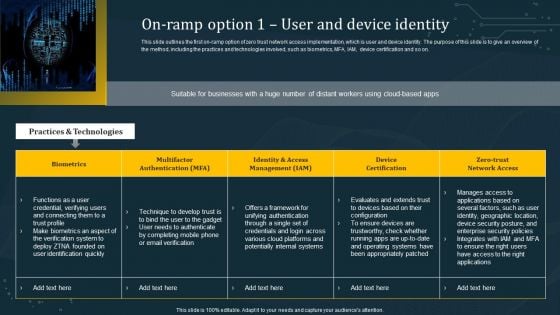
On Ramp Option 1 User And Device Identity Themes PDF
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. This On Ramp Option 1 User And Device Identity Themes PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Google Cloud Service Models Identity And Security Services On Google Cloud Platform Clipart PDF
This slide depicts the security services on the google cloud platform. The purpose of this slide is to show the various security services available on the google cloud platform. The main components include a cloud resource manager, cloud identity and access management, cloud security scanner, and cloud platform security. Welcome to our selection of the Google Cloud Service Models Identity And Security Services On Google Cloud Platform Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
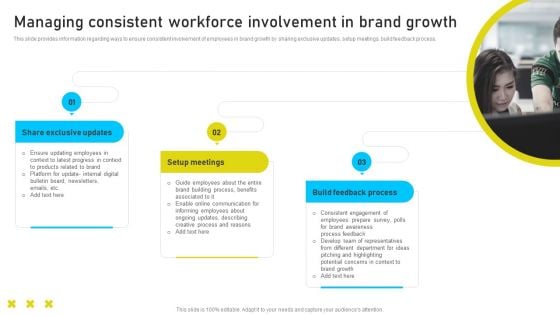
Brand Identity Management Toolkit Managing Consistent Workforce Involvement In Brand Themes PDF
This slide provides information regarding ways to ensure consistent involvement of employees in brand growth by sharing exclusive updates, setup meetings, build feedback process. Retrieve professionally designed Brand Identity Management Toolkit Managing Consistent Workforce Involvement In Brand Themes PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
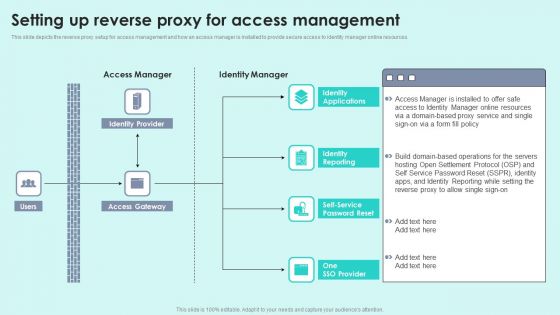
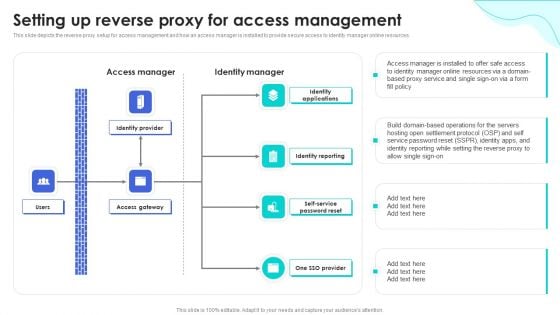
Setting Up Reverse Proxy For Access Management Reverse Proxy For Load Balancing Elements PDF
This slide depicts the reverse proxy setup for access management and how an access manager is installed to provide secure access to identity manager online resources.Deliver an awe inspiring pitch with this creative Setting Up Reverse Proxy For Access Management Reverse Proxy For Load Balancing Elements PDF bundle. Topics like Access Manager, Identity Manager, Identity Provider can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparative Assessment Of Identification Lifecycle Management Software For Identity Provisioning Rules PDF
This slide depicts identity provision and lifecycle management software with comparative analysis. It provides information about HR driven provisioning, manage access requests, regular review of access rights, streamline and automate business procedures, etc.Persuade your audience using this comparative assessment of identification lifecycle management software for identity provisioning rules pdf This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including manage access requests, regular review of access rights, streamline and automate Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
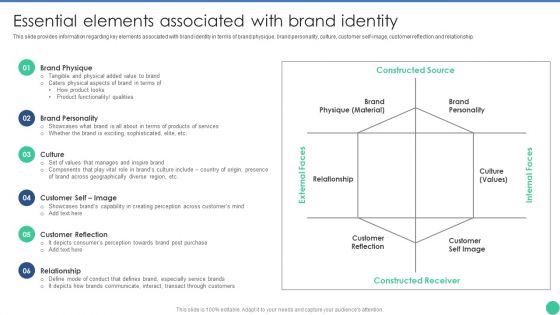
Brand Management To Enhance Essential Elements Associated With Brand Identity Structure PDF
This slide provides information regarding key elements associated with brand identity in terms of brand physique, brand personality, culture, customer self-image, customer reflection and relationship. Retrieve professionally designed Brand Management To Enhance Essential Elements Associated With Brand Identity Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
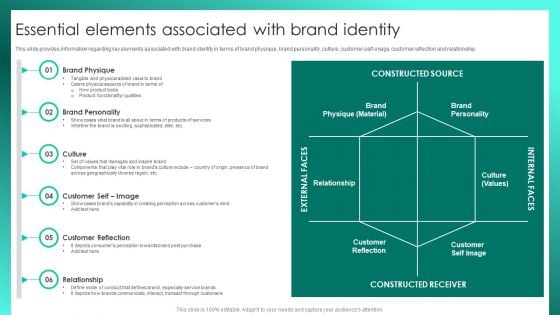
Successful Brand Management Essential Elements Associated With Brand Identity Diagrams PDF
This slide provides information regarding key elements associated with brand identity in terms of brand physique, brand personality, culture, customer self-image, customer reflection and relationship. Retrieve professionally designed Successful Brand Management Essential Elements Associated With Brand Identity Diagrams PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
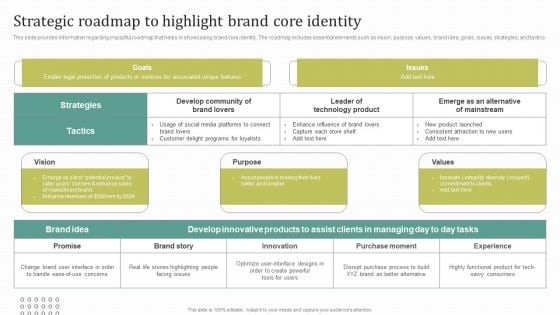
Instructions For Brand Performance Management Team Strategic Roadmap To Highlight Brand Core Identity Slides PDF
This slide provides information regarding impactful roadmap that helps in showcasing brand core identity. The roadmap includes essential elements such as vision, purpose, values, brand idea, goals, issues, strategies, and tactics. Retrieve professionally designed Instructions For Brand Performance Management Team Strategic Roadmap To Highlight Brand Core Identity Slides PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
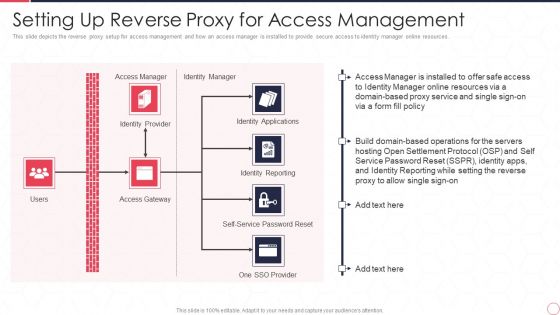
Reverse Proxy Server IT Setting Up Reverse Proxy For Access Management Ppt Ideas Guide PDF
This slide depicts the reverse proxy setup for access management and how an access manager is installed to provide secure access to identity manager online resources. Presenting reverse proxy server it setting up reverse proxy for access management ppt ideas guide pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like access manager, identity manager, identity applications, identity reporting, access gateway, identity provider. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
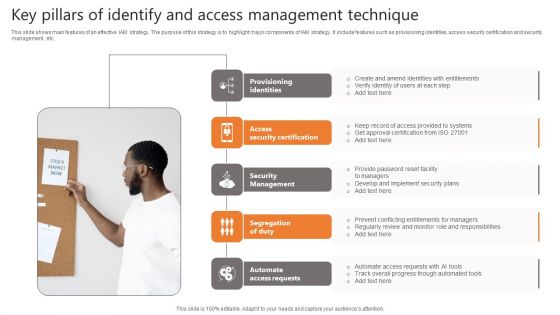
Key Pillars Of Identify And Access Management Technique Topics PDF
This slide shows main features of an effective IAM strategy. The purpose of this strategy is to highlight major components of IAM strategy. It include features such as provisioning identities, access security certification and security management , etc. Presenting Key Pillars Of Identify And Access Management Technique Topics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Provisioning Identities, Security Certification, Security Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Zero Trust Network Access Overview Of Zero Trust Solution Categories
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Network Access Overview Of Zero Trust Solution Categories for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.
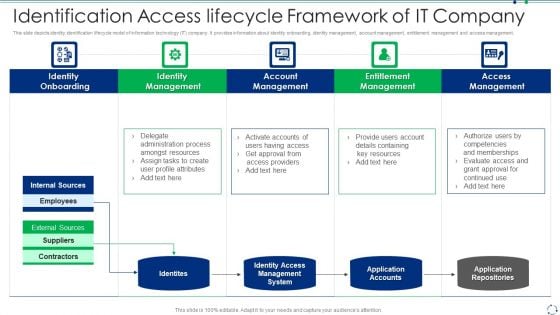
Identification Access Lifecycle Framework Of IT Company Portrait PDF
This slide depicts identity identification lifecycle model of information technology IT company. It provides information about identity onboarding, identity management, account management, entitlement management and access management.Persuade your audience using this identification access lifecycle framework of it company portrait pdf This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including identity onboarding, identity management, account management Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Reverse Proxy Web Server Setting Up Reverse Proxy For Access Management Download PDF
This slide depicts the reverse proxy setup for access management and how an access manager is installed to provide secure access to identity manager online resources. Create an editable Reverse Proxy Web Server Setting Up Reverse Proxy For Access Management Download PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Reverse Proxy Web Server Setting Up Reverse Proxy For Access Management Download PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Zero Trust Model On Ramp Option 1 User And Device Identity
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. Retrieve professionally designed Zero Trust Model On Ramp Option 1 User And Device Identity to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.

On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.
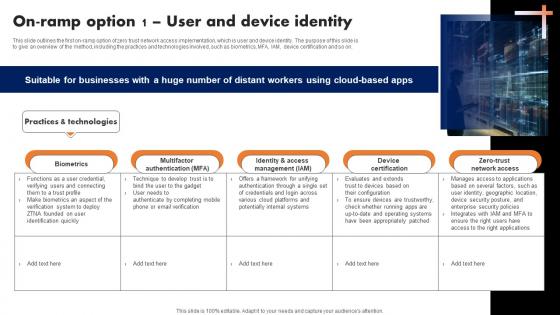
On Ramp Option 1 User And Device Identity Software Defined Perimeter SDP
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download On Ramp Option 1 User And Device Identity Software Defined Perimeter SDP from Slidegeeks and deliver a wonderful presentation. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.
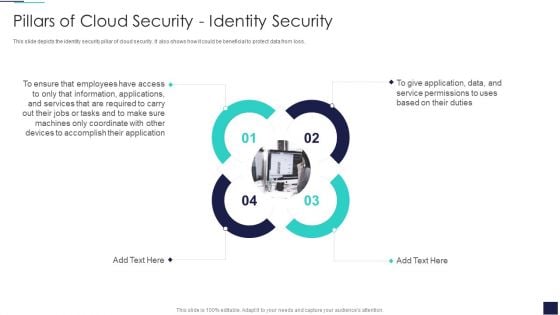
Cloud Information Security Pillars Of Cloud Security Identity Security Ppt Layouts Graphics Example PDF
This slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss. This is a Cloud Information Security Pillars Of Cloud Security Identity Security Ppt Layouts Graphics Example PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Advanced Authentication, Cloud Access, Eliminate Malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Aspects Of Information System Access Control Security Auditing Diagrams PDF
The following slide highlights the aspects of information system access control security audit illustrating key headings which incudes data access control, authentication privacy, user identity, user management, password management, network access control, and login Presenting Aspects Of Information System Access Control Security Auditing Diagrams PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Management, Data Access Control, Network Access Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

A48 Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Boost your pitch with our creative A48 Zero Trust Network Access Architectural Models. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
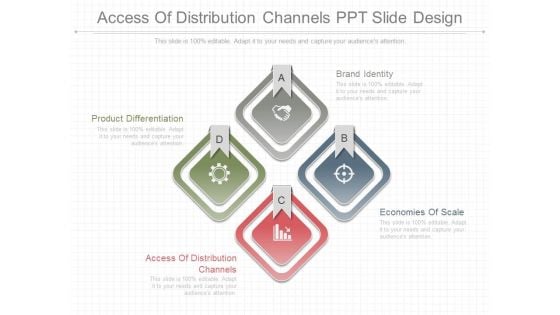
Access Of Distribution Channels Ppt Slide Design
This is a access of distribution channels ppt slide design. This is a four stage process. The stages in this process are brand identity, economies of scale, access of distribution channels, product differentiation.
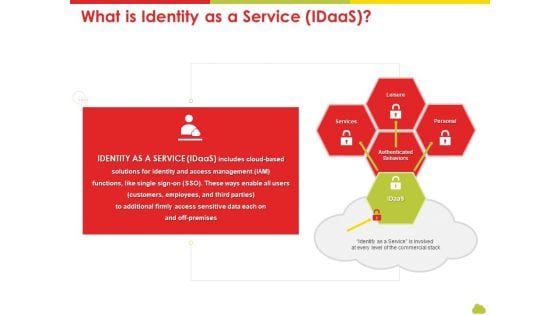
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan What Is Identity As A Service Idaas Designs PDF
This is a mesh computing technology hybrid private public iaas paas saas workplan what is identity as a service idaas designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like services, access, management, commercial stack. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.
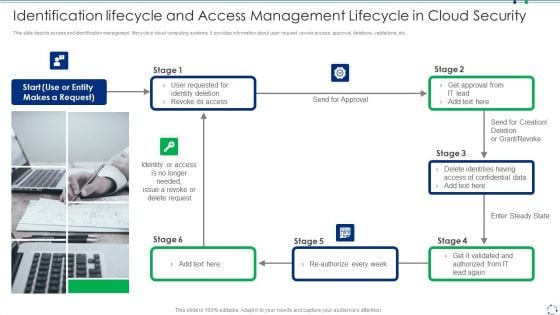
Identification Lifecycle And Access Management Lifecycle In Cloud Security Guidelines PDF
This slide depicts access and identification management lifecycle in cloud computing systems. It provides information about user request, revoke access, approval, deletions, validations, etc.Presenting identification lifecycle and access management lifecycle in cloud security guidelines pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including identity deletion, revoke its access, identity or access This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Zero Trust Network Access Architectural Models Diagrams PDF
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Are you searching for a Zero Trust Network Access Architectural Models Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Architectural Models Diagrams PDF from Slidegeeks today.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
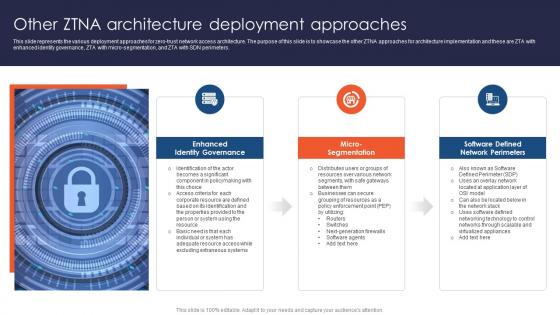
Zero Trust Network Access Other ZTNA Architecture Deployment Approaches
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Create an editable Zero Trust Network Access Other ZTNA Architecture Deployment Approaches that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Zero Trust Network Access Other ZTNA Architecture Deployment Approaches is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.
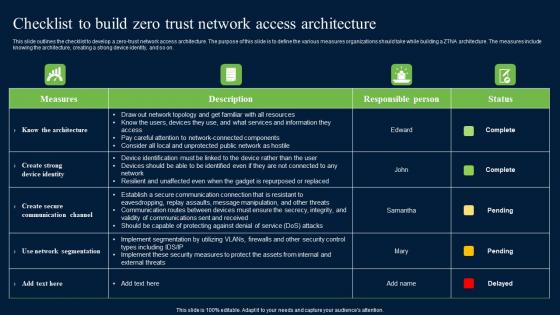
Checklist To Build Zero Trust Network Access Security Structure Pdf
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Security Structure Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Security Structure Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Zero Trust Model Checklist To Build Zero Trust Network Access
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Checklist To Build Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.
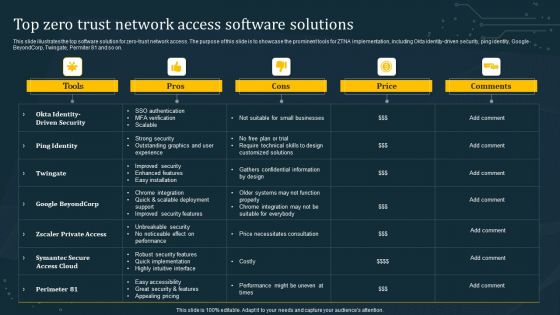
Top Zero Trust Network Access Software Solutions Microsoft PDF
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Top Zero Trust Network Access Software Solutions Microsoft PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Top Zero Trust Network Access Software Solutions Microsoft PDF.

Secure Access Service Edge Architecture Characteristics Ppt Summary Portfolio PDF
This slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity-driven, cloud-native, support for all edges, and global distribution. Make sure to capture your audiences attention in your business displays with our gratis customizable Secure Access Service Edge Architecture Characteristics Ppt Summary Portfolio PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
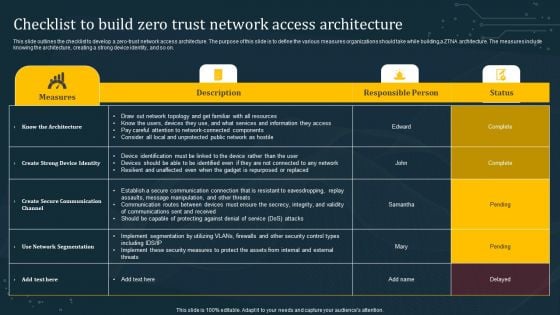
Checklist To Build Zero Trust Network Access Architecture Diagrams PDF
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Checklist To Build Zero Trust Network Access Architecture Diagrams PDF can be your best option for delivering a presentation. Represent everything in detail using Checklist To Build Zero Trust Network Access Architecture Diagrams PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Construction Engineering And Industrial Facility Management IT Infrastructure Optimization Download PDF
Deliver and pitch your topic in the best possible manner with thisconstruction engineering and industrial facility management it infrastructure optimization download pdf. Use them to share invaluable insights on desktop device and server management, identity and access management, data protection and recovery and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
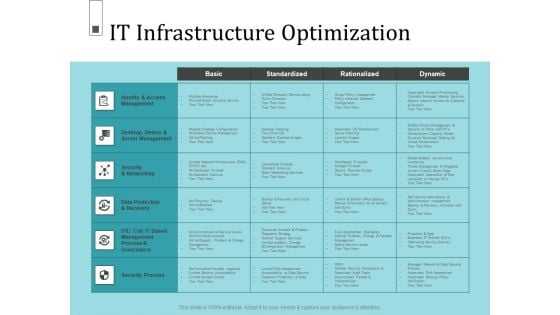
Infrastructure Project Management In Construction It Infrastructure Optimization Background PDF
Deliver and pitch your topic in the best possible manner with this infrastructure project management in construction it infrastructure optimization background pdf. Use them to share invaluable insights on standardized, rationalized, dynamic, identity and access management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
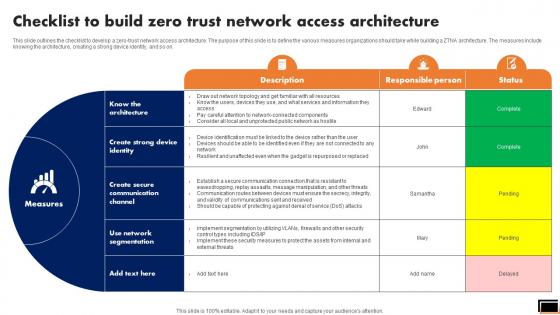
Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.
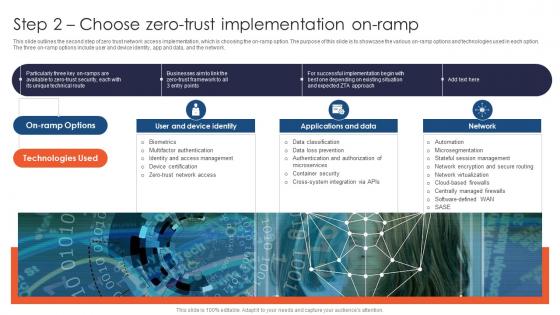
Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Find highly impressive Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.

Cloud Information Security Cloud Security Checklist Access Control Ppt Inspiration Professional PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. This is a Cloud Information Security Cloud Security Checklist Access Control Ppt Inspiration Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Control Identity, Security Breaches, Data Servers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
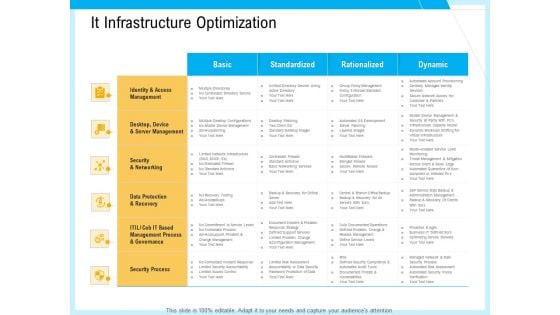
IT And Cloud Facilities Management It Infrastructure Optimization Ppt Model Slide PDF
Deliver an awe-inspiring pitch with this creative it and cloud facilities management it infrastructure optimization ppt model slide pdf bundle. Topics like standardized, rationalized, dynamic, identity and access management, security and networking, security process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
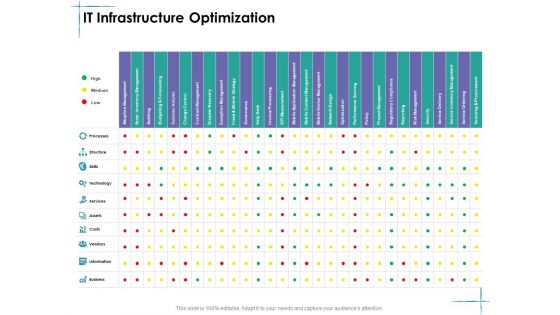
Facility Management IT Infrastructure Optimization Technology Ppt Slides Graphics Download PDF
Deliver an awe inspiring pitch with this creative facility management it infrastructure optimization technology ppt slides graphics download pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
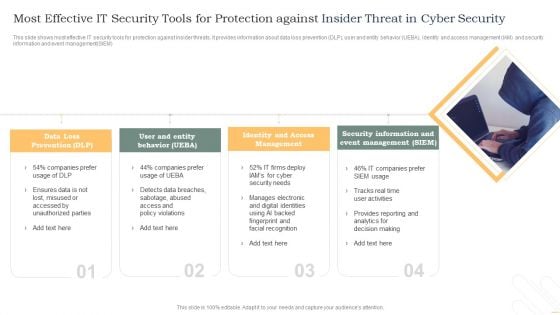
Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
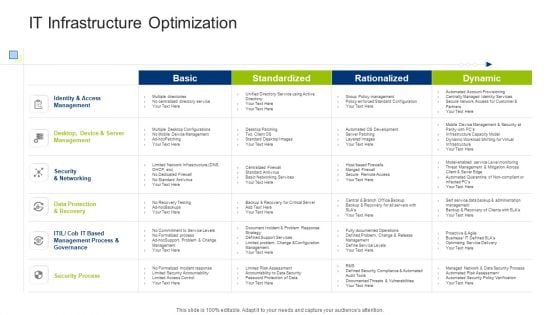
Infrastructure Building Administration IT Infrastructure Optimization Formats PDF
Deliver and pitch your topic in the best possible manner with this infrastructure building administration it infrastructure optimization formats pdf. Use them to share invaluable insights on identity and access management, security and networking, data protection and recovery and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Smart Phone Security Tools For Preventing Threats Topics PDF
This slide shows latest security tools for managing phone security model. The purpose of this slide is to highlight various tools names with description for selecting most suitable tool. It include tools such as data loss prevention, identify and access management, etc. Presenting Smart Phone Security Tools For Preventing Threats Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Loss Prevention, Identity Access Management, Security Event Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
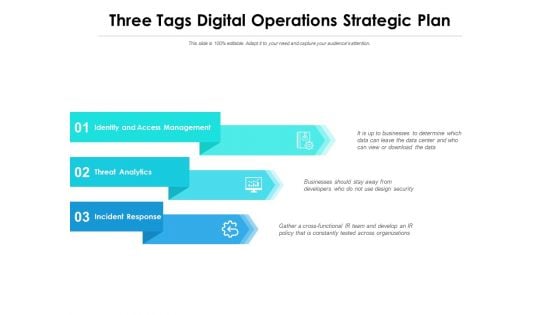
Three Tags Digital Operations Strategic Plan Ppt PowerPoint Presentation File Elements
Presenting this set of slides with name three tags digital operations strategic plan ppt powerpoint presentation file elements. This is a three stage process. The stages in this process are identity and access management, threat analytics, incident response. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
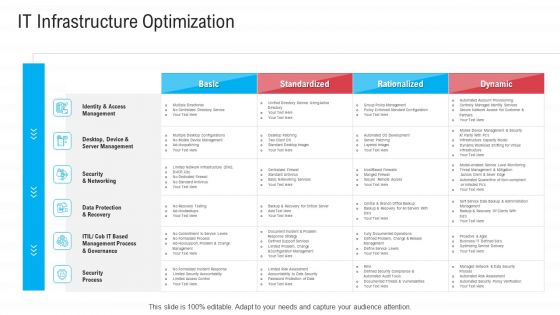
Infrastructure Designing And Administration IT Infrastructure Optimization Portrait PDF
Deliver an awe inspiring pitch with this creative infrastructure designing and administration it infrastructure optimization portrait pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
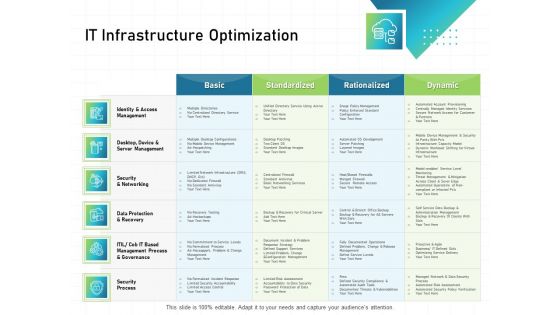
IT Infrastructure Administration IT Infrastructure Optimization Ppt Summary Example File PDF
Deliver an awe inspiring pitch with this creative it infrastructure administration it infrastructure optimization ppt summary example file pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
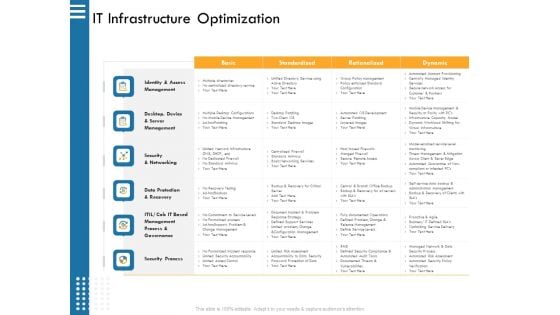
IT Infrastructure Governance IT Infrastructure Optimization Ppt Model Structure PDF
Deliver an awe inspiring pitch with this creative it infrastructure governance it infrastructure optimization ppt model structure pdf. bundle. Topics like standardized, rationalized, dynamic, identity and access management desktop, device, and server management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Infrastructure Strategies IT Infrastructure Optimization Ppt Icon Information PDF
Deliver an awe inspiring pitch with this creative infrastructure strategies it infrastructure optimization ppt icon information pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































