Implementation

Business Growth With Quality Management Ppt Slides
This is a business growth with quality management ppt slides. This is a eight stage process. The stages in this process are plan, implement, identify requirements, lessons learned, continuous impalement, monitor, measure, assess, implement, quality management.
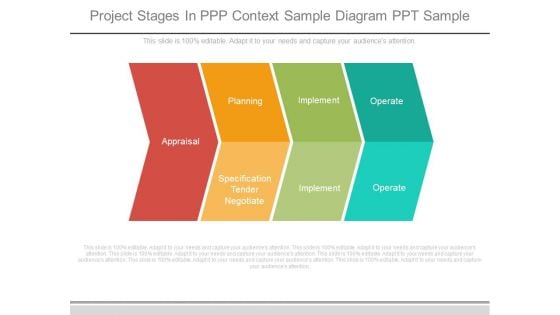
Project Stages In Ppp Context Sample Diagram Ppt Sample
This is a project stages in ppp context sample diagram ppt sample. This is a four stage process. The stages in this process are appraisal, planning, implement, operate, implement, specification tender negotiate.
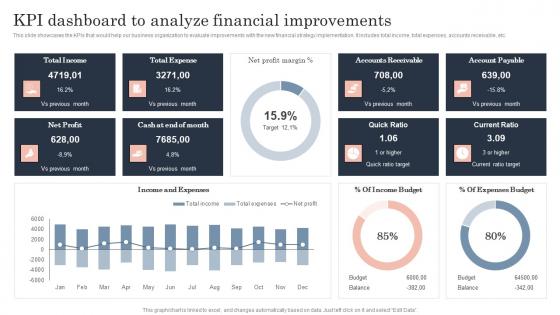
Kpi Dashboard To Analyze Financial Guide To Corporate Financial Growth Plan Designs Pdf
This slide showcases the KPIs that would help our business organization to evaluate improvements with the new financial strategy implementation. It includes total income, total expenses, accounts receivable, etc.Presenting this PowerPoint presentation, titled Kpi Dashboard To Analyze Financial Guide To Corporate Financial Growth Plan Designs Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Kpi Dashboard To Analyze Financial Guide To Corporate Financial Growth Plan Designs Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Kpi Dashboard To Analyze Financial Guide To Corporate Financial Growth Plan Designs Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide showcases the KPIs that would help our business organization to evaluate improvements with the new financial strategy implementation. It includes total income, total expenses, accounts receivable, etc.
Asset Tracking Technologies With Working Principle Tech Asset Management Introduction Pdf
This slide covers asset tracking technologies and its working principle to select suitable one for effective implementation. It involves technology such as RFID, Wi-Fi, ultra wide band, GPS and satellite.Presenting this PowerPoint presentation, titled Asset Tracking Technologies With Working Principle Tech Asset Management Introduction Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Asset Tracking Technologies With Working Principle Tech Asset Management Introduction Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Asset Tracking Technologies With Working Principle Tech Asset Management Introduction Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide covers asset tracking technologies and its working principle to select suitable one for effective implementation. It involves technology such as RFID, Wi-Fi, ultra wide band, GPS and satellite.
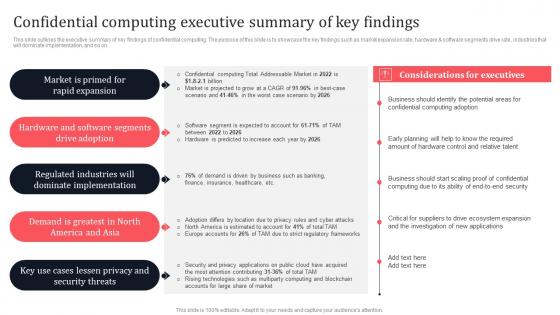
Confidential Computing Executive Summary Of Key Findings Secure Multi Party Topics Pdf
This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Confidential Computing Executive Summary Of Key Findings Secure Multi Party Topics Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on.

Checklist To Select Best SMS Text Message Advertising Solutions Enhancing Mockup Pdf
This slide represents the checklist highlighting the things to be kept in mind by marketers at the time of selecting SMS marketing software. It includes details related to parameters such as ease of implementation, compliance management etc. Slidegeeks is here to make your presentations a breeze with Checklist To Select Best SMS Text Message Advertising Solutions Enhancing Mockup Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the checklist highlighting the things to be kept in mind by marketers at the time of selecting SMS marketing software. It includes details related to parameters such as ease of implementation, compliance management etc.
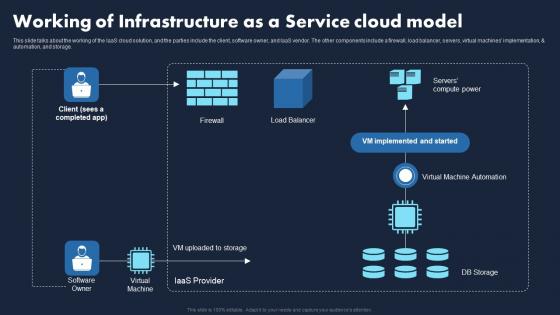
Working Of Infrastructure As A Service Cloud Transforming Business With IaaS Elements Pdf
This slide talks about the working of the IaaS cloud solution, and the parties include the client, software owner, and laaS vendor. The other components include a firewall, load balancer, servers, virtual machines implementation, and automation, and storage. If you are looking for a format to display your unique thoughts, then the professionally designed Working Of Infrastructure As A Service Cloud Transforming Business With IaaS Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Working Of Infrastructure As A Service Cloud Transforming Business With IaaS Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the working of the IaaS cloud solution, and the parties include the client, software owner, and laaS vendor. The other components include a firewall, load balancer, servers, virtual machines implementation, and automation, and storage.
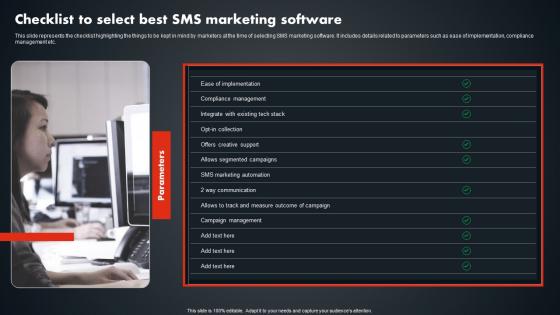
Checklist To Select Best SMS Marketing Software SMS Promotional Tactics Infographics PDF
This slide represents the checklist highlighting the things to be kept in mind by marketers at the time of selecting SMS marketing software. It includes details related to parameters such as ease of implementation, compliance management etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Select Best SMS Marketing Software SMS Promotional Tactics Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Select Best SMS Marketing Software SMS Promotional Tactics Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the checklist highlighting the things to be kept in mind by marketers at the time of selecting SMS marketing software. It includes details related to parameters such as ease of implementation, compliance management etc.
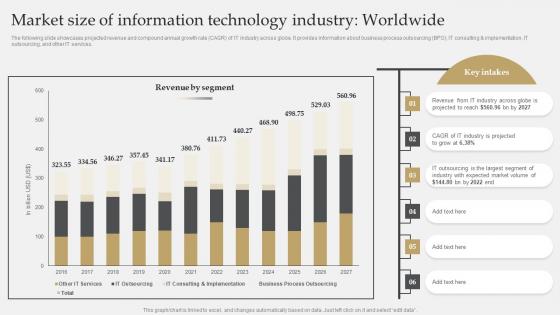
Market Size Of Information Technology Industry Worldwide IT Industry Market Research Template Pdf
The following slide showcases projected revenue and compound annual growth rate CAGR of IT industry across globe. It provides information about business process outsourcing BPO, IT consulting and implementation, IT outsourcing, and other IT services. If you are looking for a format to display your unique thoughts, then the professionally designed Market Size Of Information Technology Industry Worldwide IT Industry Market Research Template Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download IT Industry Market Research Market Size Of Information Technology Industry Worldwide Template Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide showcases projected revenue and compound annual growth rate CAGR of IT industry across globe. It provides information about business process outsourcing BPO, IT consulting and implementation, IT outsourcing, and other IT services.
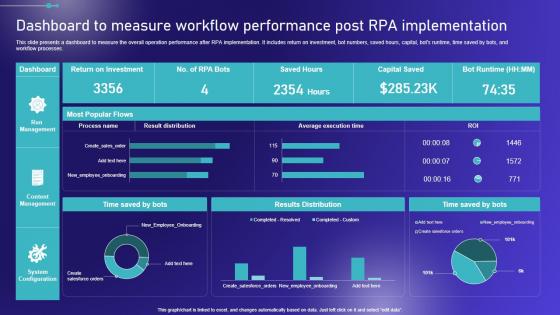
Dashboard To Measure Workflow Performance Post Embracing Robotic Process Portrait PDF
This slide presents a dashboard to measure the overall operation performance after RPA implementation. It includes return on investment, bot numbers, saved hours, capital, bots runtime, time saved by bots, and workflow processes. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Dashboard To Measure Workflow Performance Post Embracing Robotic Process Portrait PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide presents a dashboard to measure the overall operation performance after RPA implementation. It includes return on investment, bot numbers, saved hours, capital, bots runtime, time saved by bots, and workflow processes.
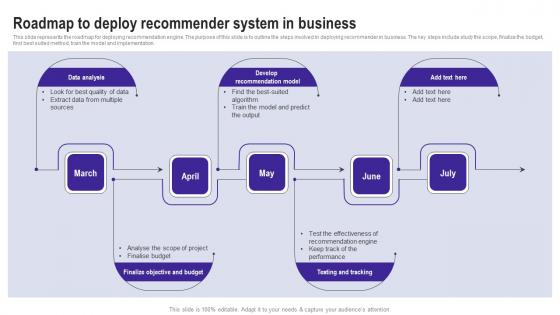
Roadmap To Deploy Recommender System In Business Use Cases Of Filtering Methods Download Pdf
This slide represents the roadmap for deploying recommendation engine. The purpose of this slide is to outline the steps involved in deploying recommender in business. The key steps include study the scope, finalize the budget, find best suited method, train the model and implementation. Slidegeeks is here to make your presentations a breeze with Roadmap To Deploy Recommender System In Business Use Cases Of Filtering Methods Download Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the roadmap for deploying recommendation engine. The purpose of this slide is to outline the steps involved in deploying recommender in business. The key steps include study the scope, finalize the budget, find best suited method, train the model and implementation.

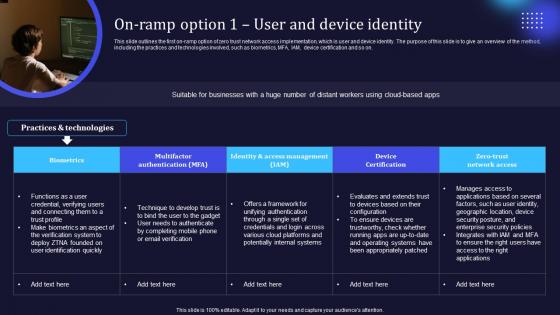
On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download On Ramp Option 1 User And Device Identity Zero Trust Network Security Mockup Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.

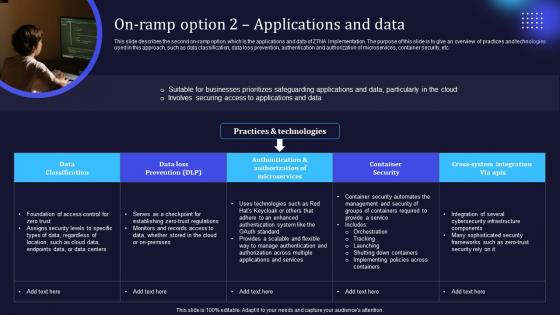
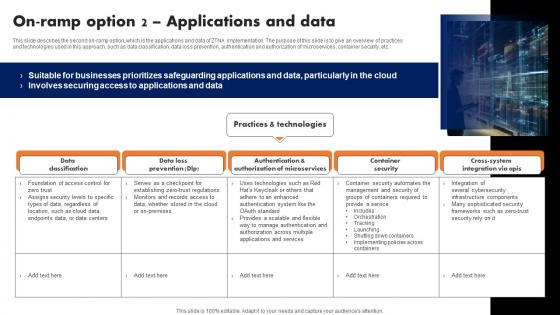
On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.

Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf
This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members. Create an editable Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Step 1 Form A Dedicated Zero Trust Team Zero Trust Network Security Portrait Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members.

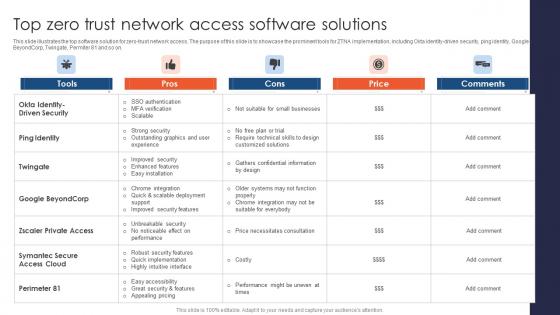
Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using Top Zero Trust Network Access Software Solutions Zero Trust Network Security Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on.
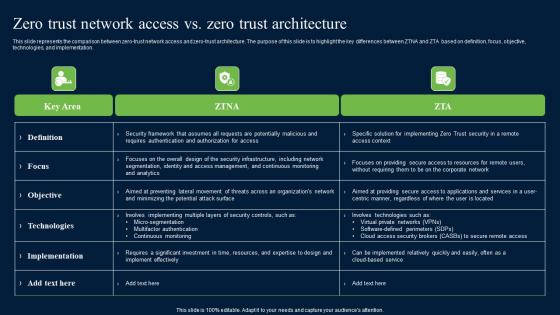
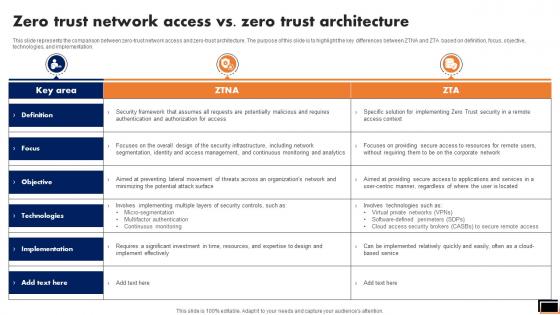
Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.
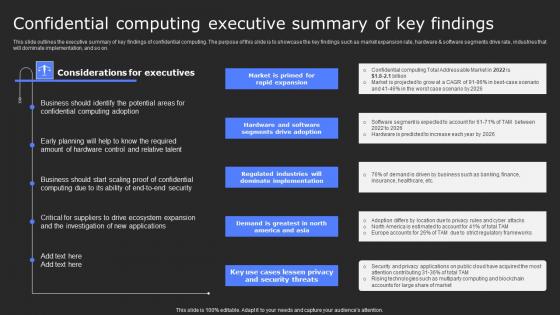
Confidential Computing Executive Summary Of Key Secure Computing Framework Guidelines Pdf
This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Confidential Computing Executive Summary Of Key Secure Computing Framework Guidelines Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Confidential Computing Executive Summary Of Key Secure Computing Framework Guidelines Pdf This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on.

Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc.
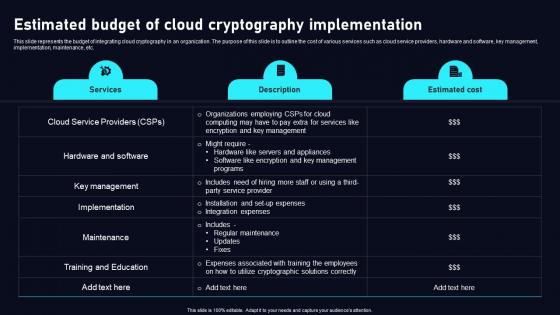
Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. This Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc.
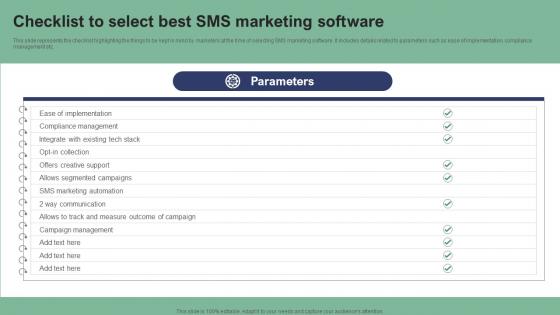
Checklist To Select Best SMS Marketing Software Text Message Marketing Strategies Introduction Pdf
This slide represents the checklist highlighting the things to be kept in mind by marketers at the time of selecting SMS marketing software. It includes details related to parameters such as ease of implementation, compliance management etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Select Best SMS Marketing Software Text Message Marketing Strategies Introduction Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Select Best SMS Marketing Software Text Message Marketing Strategies Introduction Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. This slide represents the checklist highlighting the things to be kept in mind by marketers at the time of selecting SMS marketing software. It includes details related to parameters such as ease of implementation, compliance management etc.
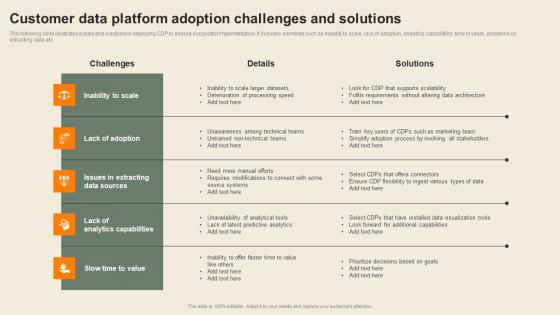
Customer Data Platform Adoption Challenges Usability Of CDP Software Tool Guidelines Pdf
The following slide illustrates issues and solutions in deploying CDP to ensure successful implementation. It includes elements such as inability to scale, lack of adoption, analytics capabilities, time to value, problems on extracting data etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Customer Data Platform Adoption Challenges Usability Of CDP Software Tool Guidelines Pdf can be your best option for delivering a presentation. Represent everything in detail using Customer Data Platform Adoption Challenges Usability Of CDP Software Tool Guidelines Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide illustrates issues and solutions in deploying CDP to ensure successful implementation. It includes elements such as inability to scale, lack of adoption, analytics capabilities, time to value, problems on extracting data etc.
Zero Trust Model On Ramp Option 1 User And Device Identity
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. Retrieve professionally designed Zero Trust Model On Ramp Option 1 User And Device Identity to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.
Zero Trust Model On Ramp Option 2 Applications And Data
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Slidegeeks has constructed Zero Trust Model On Ramp Option 2 Applications And Data after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.

Zero Trust Model Zero Trust Network Access Vs Zero Trust Architecture
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Presenting this PowerPoint presentation, titled Zero Trust Model Zero Trust Network Access Vs Zero Trust Architecture, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Model Zero Trust Network Access Vs Zero Trust Architecture. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Model Zero Trust Network Access Vs Zero Trust Architecture that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.
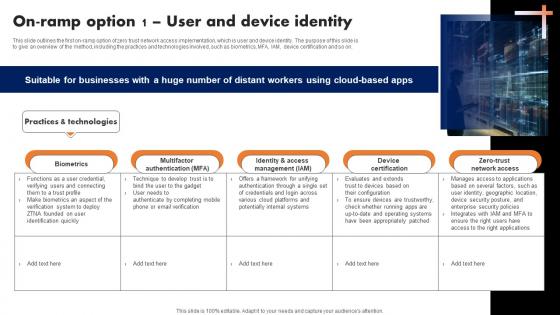
On Ramp Option 1 User And Device Identity Software Defined Perimeter SDP
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download On Ramp Option 1 User And Device Identity Software Defined Perimeter SDP from Slidegeeks and deliver a wonderful presentation. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.
On Ramp Option 2 Applications And Data Software Defined Perimeter SDP
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.

Step 1 Form A Dedicated Zero Trust Team Software Defined Perimeter SDP
This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Step 1 Form A Dedicated Zero Trust Team Software Defined Perimeter SDP for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members.

Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Software Defined Perimeter SDP
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Software Defined Perimeter SDP a try. Our experts have put a lot of knowledge and effort into creating this impeccable Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Software Defined Perimeter SDP. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.
Zero Trust Network Access Vs Zero Trust Architecture Software Defined Perimeter SDP
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Presenting this PowerPoint presentation, titled Zero Trust Network Access Vs Zero Trust Architecture Software Defined Perimeter SDP, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Vs. Zero Trust Architecture Software Defined Perimeter SDP. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Vs. Zero Trust Architecture Software Defined Perimeter SDP that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.

Creating A Comprehensive Digital Transformation Roadmap Erp And Digital Transformation For Maximizing DT SS V
This slide presents a digital transformation roadmap to optimize ERP implementation. It includes current digital strategy, deficiency in digital strategy, digital strategy formulation, digital operating model, digital strategy execution, and digital transformation. Find highly impressive Creating A Comprehensive Digital Transformation Roadmap Erp And Digital Transformation For Maximizing DT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Creating A Comprehensive Digital Transformation Roadmap Erp And Digital Transformation For Maximizing DT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide presents a digital transformation roadmap to optimize ERP implementation. It includes current digital strategy, deficiency in digital strategy, digital strategy formulation, digital operating model, digital strategy execution, and digital transformation.

Comprehensive Manual For Blockchain List Of Public Blockchain Network Platforms BCT SS V
This slide covers different platforms related to public blockchain network along with description. It includes platforms such as bitcoin, Ethereum, ripple, cardano and polkadot. It also includes key components of public blockchain network along with cost of implementation. This Comprehensive Manual For Blockchain List Of Public Blockchain Network Platforms BCT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Comprehensive Manual For Blockchain List Of Public Blockchain Network Platforms BCT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide covers different platforms related to public blockchain network along with description. It includes platforms such as bitcoin, Ethereum, ripple, cardano and polkadot. It also includes key components of public blockchain network along with cost of implementation.

On Ramp Option 2 Applications And Data Zero Trust Network Access
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Slidegeeks is here to make your presentations a breeze with On Ramp Option 2 Applications And Data Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.

Zero Trust Network Access On Ramp Option 1 User And Device Identity
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. Boost your pitch with our creative Zero Trust Network Access On Ramp Option 1 User And Device Identity. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.

Zero Trust Network Access Step 1 Form A Dedicated Zero Trust Team
This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Network Access Step 1 Form A Dedicated Zero Trust Team can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Network Access Step 1 Form A Dedicated Zero Trust Team and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members.

Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.
Zero Trust Network Access Top Zero Trust Network Access Software Solutions
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. This modern and well-arranged Zero Trust Network Access Top Zero Trust Network Access Software Solutions provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on.

Zero Trust Network Access Vs Zero Trust Architecture Ppt File Infographic Template
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Retrieve professionally designed Zero Trust Network Access Vs Zero Trust Architecture Ppt File Infographic Template to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.
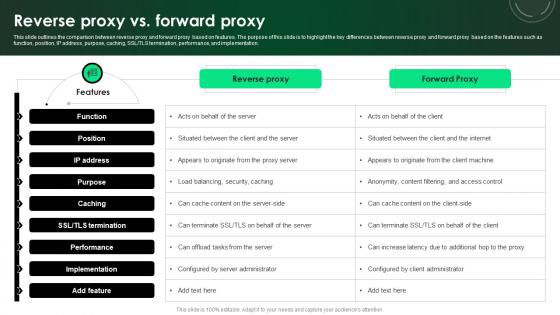
CASB 2 0 IT Reverse Proxy Vs Forward Proxy
This slide outlines the comparison between reverse proxy and forward proxy based on features. The purpose of this slide is to highlight the key differences between reverse proxy and forward proxy based on the features such as function, position, IP address, purpose, caching, SSL or TLS termination, performance, and implementation. If you are looking for a format to display your unique thoughts, then the professionally designed CASB 2 0 IT Reverse Proxy Vs Forward Proxy is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CASB 2 0 IT Reverse Proxy Vs Forward Proxy and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the comparison between reverse proxy and forward proxy based on features. The purpose of this slide is to highlight the key differences between reverse proxy and forward proxy based on the features such as function, position, IP address, purpose, caching, SSL or TLS termination, performance, and implementation.
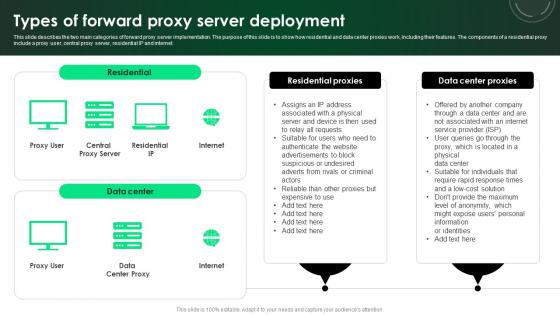
CASB 2 0 IT Types Of Forward Proxy Server Deployment
This slide describes the two main categories of forward proxy server implementation. The purpose of this slide is to show how residential and data center proxies work, including their features. The components of a residential proxy include a proxy user, central proxy server, residential IP and internet. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CASB 2 0 IT Types Of Forward Proxy Server Deployment to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the two main categories of forward proxy server implementation. The purpose of this slide is to show how residential and data center proxies work, including their features. The components of a residential proxy include a proxy user, central proxy server, residential IP and internet.
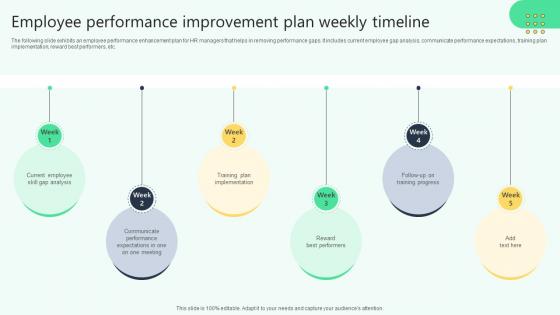
Employee Performance Improvement Plan Weekly Analysing Hr Data For Effective Decision Making
The following slide exhibits an employee performance enhancement plan for HR managers that helps in removing performance gaps. It includes current employee gap analysis, communicate performance expectations, training plan implementation, reward best performers, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Employee Performance Improvement Plan Weekly Analysing Hr Data For Effective Decision Making to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The following slide exhibits an employee performance enhancement plan for HR managers that helps in removing performance gaps. It includes current employee gap analysis, communicate performance expectations, training plan implementation, reward best performers, etc.
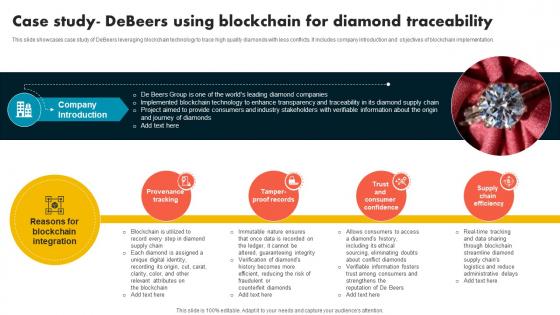
Case Study Debeers Using Blockchain For Diamond Supply Chain Evolution Harnessing The Power BCT SS V
This slide showcases case study of DeBeers leveraging blockchain technology to trace high quality diamonds with less conflicts. It includes company introduction and objectives of blockchain implementation. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Case Study Debeers Using Blockchain For Diamond Supply Chain Evolution Harnessing The Power BCT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Case Study Debeers Using Blockchain For Diamond Supply Chain Evolution Harnessing The Power BCT SS V. This slide showcases case study of DeBeers leveraging blockchain technology to trace high quality diamonds with less conflicts. It includes company introduction and objectives of blockchain implementation.
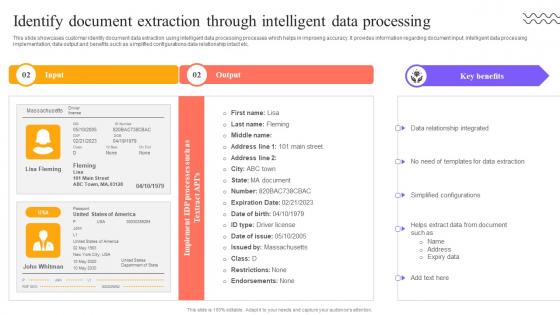
Digital Approach To Client Identify Document Extraction Through Intelligent Data Processing
This slide showcases customer identity document data extraction using intelligent data processing processes which helps in improving accuracy. It provides information regarding document input, intelligent data processing implementation, data output and benefits such as simplified configurations data relationship intact etc. Retrieve professionally designed Digital Approach To Client Identify Document Extraction Through Intelligent Data Processing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases customer identity document data extraction using intelligent data processing processes which helps in improving accuracy. It provides information regarding document input, intelligent data processing implementation, data output and benefits such as simplified configurations data relationship intact etc.
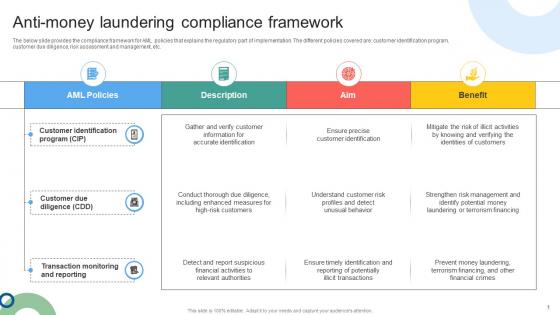
Anti Money Laundering Compliance Framework Mapping Out The Anti Money Fin SS V
The below slide provides the compliance framework for AML policies that explains the regulatory part of implementation. The different policies covered are customer identification program, customer due diligence, risk assessment and management, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Anti Money Laundering Compliance Framework Mapping Out The Anti Money Fin SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Anti Money Laundering Compliance Framework Mapping Out The Anti Money Fin SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The below slide provides the compliance framework for AML policies that explains the regulatory part of implementation. The different policies covered are customer identification program, customer due diligence, risk assessment and management, etc.
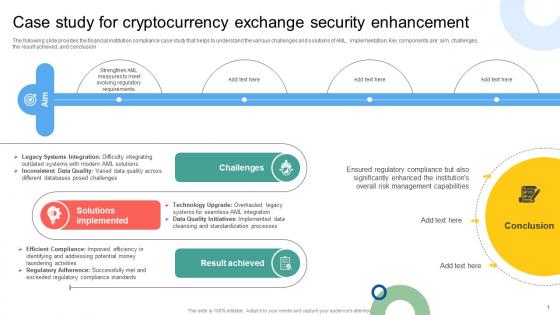
Case Study For Cryptocurrency Exchange Security Mapping Out The Anti Money Fin SS V
The following slide provides the financial institution compliance case study that helps to understand the various challenges and solutions of AML implementation. Key components are aim, challenges, the result achieved, and conclusion. Find highly impressive Case Study For Cryptocurrency Exchange Security Mapping Out The Anti Money Fin SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Case Study For Cryptocurrency Exchange Security Mapping Out The Anti Money Fin SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide provides the financial institution compliance case study that helps to understand the various challenges and solutions of AML implementation. Key components are aim, challenges, the result achieved, and conclusion.

Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template
This slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, codecommit, build test, deploy, and monitor. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template can be your best option for delivering a presentation. Represent everything in detail using Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, codecommit, build test, deploy, and monitor.

Devsecops Pipeline Development Pre Commit Stage Role Of Devsecops Ppt Slide
This slide discusses the development pre-commit stage of the DevSecOps pipeline. The purpose of this slide is to explain the pre-commit phase that includes initial defense on developer laptops, early security implementation, and Git pre-commit hooks for feedback. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Devsecops Pipeline Development Pre Commit Stage Role Of Devsecops Ppt Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Devsecops Pipeline Development Pre Commit Stage Role Of Devsecops Ppt Slide This slide discusses the development pre-commit stage of the DevSecOps pipeline. The purpose of this slide is to explain the pre-commit phase that includes initial defense on developer laptops, early security implementation, and Git pre-commit hooks for feedback.
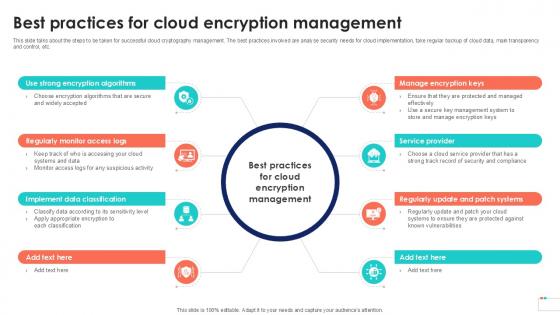
Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template today and make your presentation stand out from the rest This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc.

Estimated Customer Attrition Rate Of IBN Outsourcing Company In 2022 PPT Sample SS
This slide shows future estimated Customer Attrition Rate of IBN Outsourcing Company after strategy implementation. Additionally, this slide provides information on number of Customers at End of Period and Customers at Start of Period along with the formula for calculation of CAR Customer Attrition Rate using these variables. The Attrition Rate has decreased by around 5 percent. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Estimated Customer Attrition Rate Of IBN Outsourcing Company In 2022 PPT Sample SS. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Estimated Customer Attrition Rate Of IBN Outsourcing Company In 2022 PPT Sample SS today and make your presentation stand out from the rest This slide shows future estimated Customer Attrition Rate of IBN Outsourcing Company after strategy implementation. Additionally, this slide provides information on number of Customers at End of Period and Customers at Start of Period along with the formula for calculation of CAR Customer Attrition Rate using these variables. The Attrition Rate has decreased by around 5 percent.
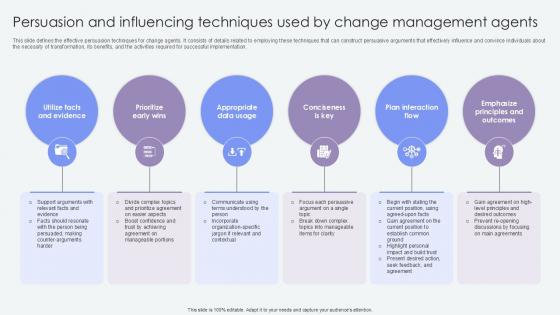
Persuasion And Influencing Techniques Agents Of Change Pioneers PPT Template CM SS V
This slide defines the effective persuasion techniques for change agents. It consists of details related to employing these techniques that can construct persuasive arguments that effectively influence and convince individuals about the necessity of transformation, its benefits, and the activities required for successful implementation. Presenting this PowerPoint presentation, titled Persuasion And Influencing Techniques Agents Of Change Pioneers PPT Template CM SS V, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Persuasion And Influencing Techniques Agents Of Change Pioneers PPT Template CM SS V. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Persuasion And Influencing Techniques Agents Of Change Pioneers PPT Template CM SS V that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide defines the effective persuasion techniques for change agents. It consists of details related to employing these techniques that can construct persuasive arguments that effectively influence and convince individuals about the necessity of transformation, its benefits, and the activities required for successful implementation.

Responsibilities Of Change Management Agents Advise Stakeholders PPT PowerPoint CM SS V
This slide defines a change agent, or agent of change, who promotes and enables change within any group or organization. It includes details related to the responsibilities of change agents, which are crucial in driving successful organizational change, such as advising customers and employees after change implementation. Do you know about Slidesgeeks Responsibilities Of Change Management Agents Advise Stakeholders PPT PowerPoint CM SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide defines a change agent, or agent of change, who promotes and enables change within any group or organization. It includes details related to the responsibilities of change agents, which are crucial in driving successful organizational change, such as advising customers and employees after change implementation.
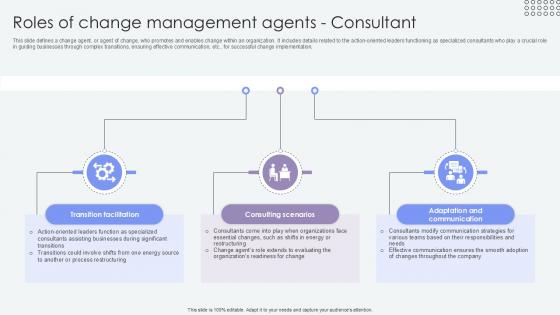
Roles Of Change Management Agents Consultant Agents Of Change Pioneers PPT Presentation CM SS V
This slide defines a change agent, or agent of change, who promotes and enables change within an organization. It includes details related to the action-oriented leaders functioning as specialized consultants who play a crucial role in guiding businesses through complex transitions, ensuring effective communication, etc., for successful change implementation. Present like a pro with Roles Of Change Management Agents Consultant Agents Of Change Pioneers PPT Presentation CM SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide defines a change agent, or agent of change, who promotes and enables change within an organization. It includes details related to the action-oriented leaders functioning as specialized consultants who play a crucial role in guiding businesses through complex transitions, ensuring effective communication, etc., for successful change implementation.
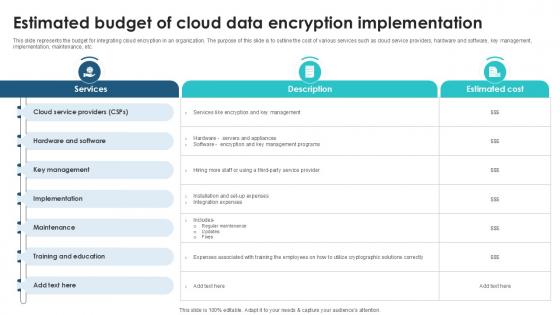
Estimated Budget Of Cloud Data Client Side Encryption PPT Sample
This slide represents the budget for integrating cloud encryption in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Estimated Budget Of Cloud Data Client Side Encryption PPT Sample template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Estimated Budget Of Cloud Data Client Side Encryption PPT Sample that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the budget for integrating cloud encryption in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc.
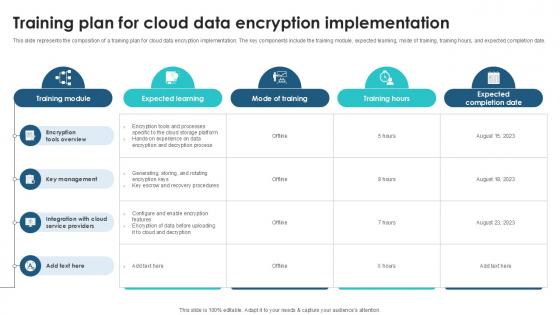
Training Plan For Cloud Data Client Side Encryption PPT Template
This slide represents the composition of a training plan for cloud data encryption implementation. The key components include the training module, expected learning, mode of training, training hours, and expected completion date. Presenting this PowerPoint presentation, titled Training Plan For Cloud Data Client Side Encryption PPT Template, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Training Plan For Cloud Data Client Side Encryption PPT Template. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Training Plan For Cloud Data Client Side Encryption PPT Template that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the composition of a training plan for cloud data encryption implementation. The key components include the training module, expected learning, mode of training, training hours, and expected completion date.
Lessons Learned Project Management Ppt Sample
This is a lessons learned project management ppt sample. This is a four stage process. The stages in this process are new project, audits, implement, begin learning.
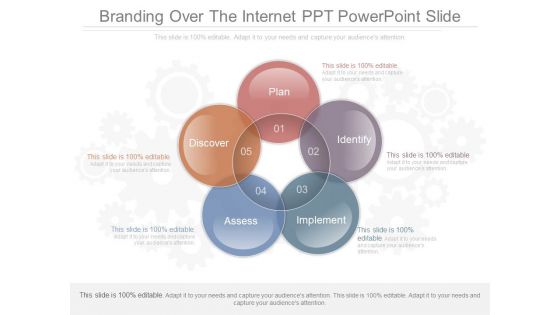
Branding Over The Internet Ppt Powerpoint Slide
This is a branding over the internet ppt powerpoint slide. This is a five stage process. The stages in this process are plan, identify, implement, assess, discover.
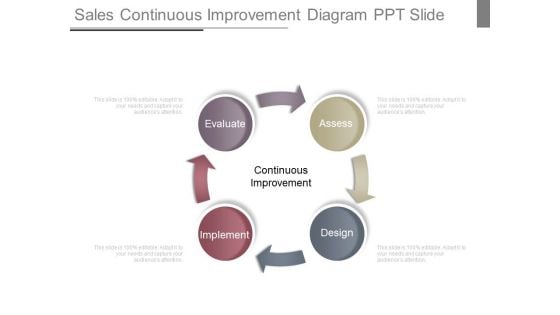
Sales Continuous Improvement Diagram Ppt Slide
This is a sales continuous improvement diagram ppt slide. This is a four stage process. The stages in this process are evaluate, implement, design, assess, continuous improvement.
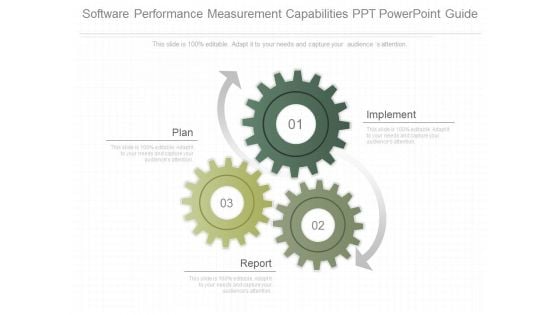
Software Performance Measurement Capabilities Ppt Powerpoint Guide
This is a software performance measurement capabilities ppt powerpoint guide. This is a three stage process. The stages in this process are plan, implement, report.
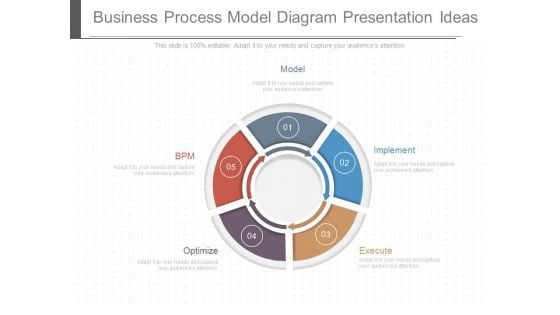
Business Process Model Diagram Presentation Ideas
This is a business process model diagram presentation ideas. This is a five stage process. The stages in this process are model, implement, execute, optimize, bpm.

Marketing Predictive Analytics Ppt Example
This is a marketing predictive analytics ppt example. This is a six stage process. The stages in this process are marketing data, explore, transform, model, validate, implement.
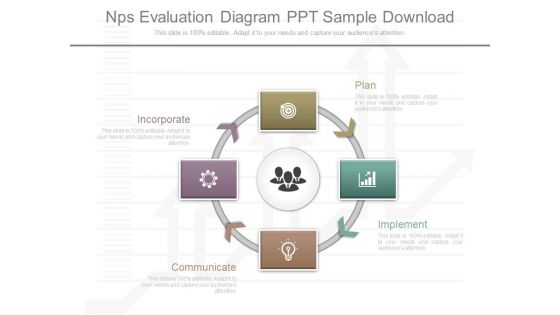
Nps Evaluation Diagram Ppt Sample Download
This is a nps evaluation diagram ppt sample download. This is a four stage process. The stages in this process are plan, implement, communicate, incorporate.


 Continue with Email
Continue with Email

 Home
Home


































