Incident Management
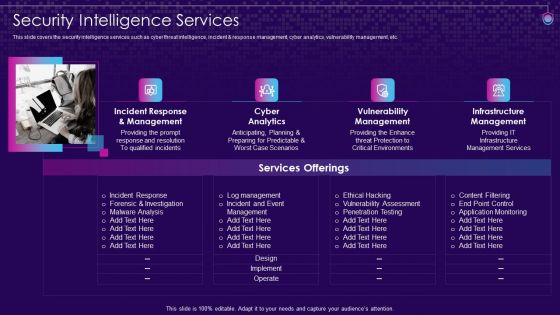
SIEM Services Security Intelligence Services Ppt Show Layouts PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem services security intelligence services ppt show layouts pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management cyber, analytics vulnerability, management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
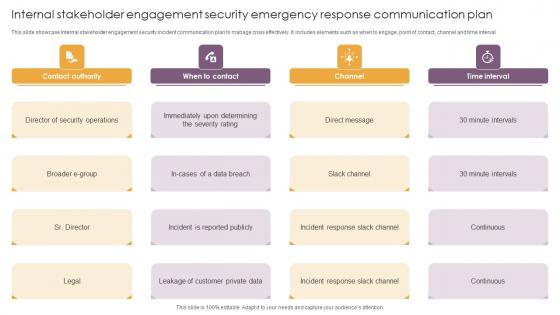
Internal Stakeholder Engagement Security Emergency Response Communication Plan Introduction Pdf
This slide showcase Internal stakeholder engagement security incident communication plan to manage crisis effectively. It includes elements such as when to engage, point of contact, channel and time interval Showcasing this set of slides titled Internal Stakeholder Engagement Security Emergency Response Communication Plan Introduction Pdf The topics addressed in these templates are Contact Authority, Time Interval, Director Of Security Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase Internal stakeholder engagement security incident communication plan to manage crisis effectively. It includes elements such as when to engage, point of contact, channel and time interval

Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks.
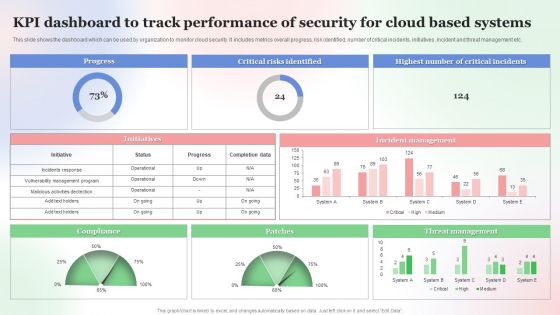
KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF
This slide shows the dashboard which can be used by organization to monitor cloud security. It includes metrics overall progress, risk identified, number of critical incidents, initiatives, incident and threat management etc. Showcasing this set of slides titled KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF. The topics addressed in these templates are Kpi Dashboard To Track, Performance Of Security, Cloud Based Systems . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
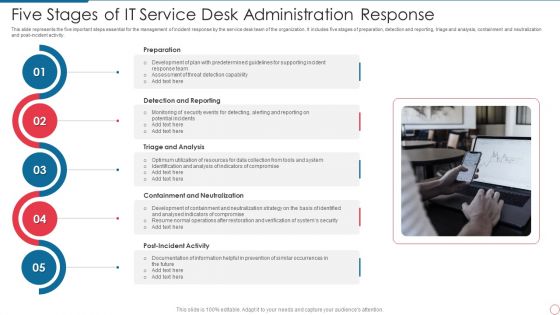
Five Stages Of IT Service Desk Administration Response Inspiration PDF
This slide represents the five important steps essential for the management of incident response by the service desk team of the organization. It includes five stages of preparation, detection and reporting, triage and analysis, containment and neutralization and post incident activity. Persuade your audience using this Five Stages Of IT Service Desk Administration Response Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Analysis, Potential, Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
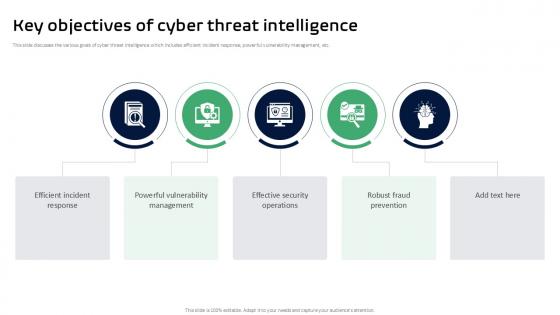
Key Objectives Of Cyber Threat Intelligence Ppt Sample
This slide discusses the various goals of cyber threat intelligence which includes efficient incident response, powerful vulnerability management, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Objectives Of Cyber Threat Intelligence Ppt Sample to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide discusses the various goals of cyber threat intelligence which includes efficient incident response, powerful vulnerability management, etc.
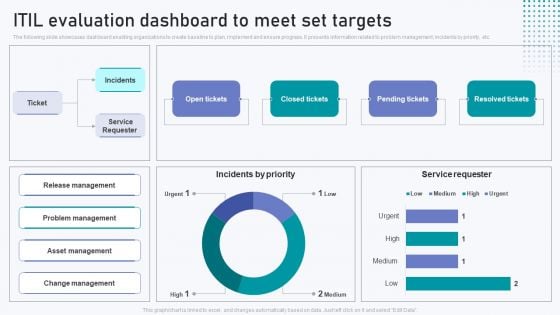
ITIL Evaluation Dashboard To Meet Set Targets Summary PDF
The following slide showcases dashboard enabling organizations to create baseline to plan, implement and ensure progress. It presents information related to problem management, incidents by priority, etc. Pitch your topic with ease and precision using this ITIL Evaluation Dashboard To Meet Set Targets Summary PDF. This layout presents information on Incidents By Priority, Service Requester. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Real Time Assessment Of Security Threats Cloud SIEM Model Icons PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats cloud siem model icons pdf. Use them to share invaluable insights on threat and vulnerability management processes, aggregation, collection, correlation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
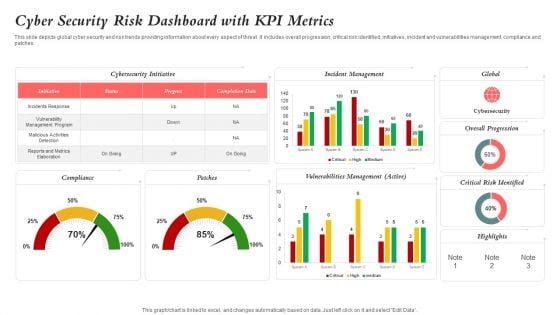
Cyber Security Risk Dashboard With KPI Metrics Elements PDF
This slide depicts global cyber security and risk trends providing information about every aspect of threat. It includes overall progression, critical risk identified, initiatives, incident and vulnerabilities management, compliance and patches. Showcasing this set of slides titled Cyber Security Risk Dashboard With KPI Metrics Elements PDF. The topics addressed in these templates are Vulnerability Management Program, Reports And Metrics Elaboration, Critical Risk Identified. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
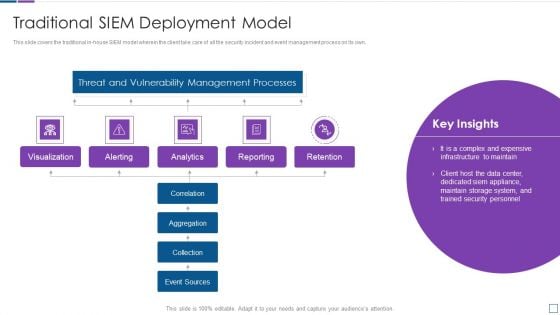
Real Time Assessment Of Security Threats Traditional SIEM Deployment Model Background PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats traditional siem deployment model background pdf. Use them to share invaluable insights on threat and vulnerability management processes, visualization, retention, analytics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
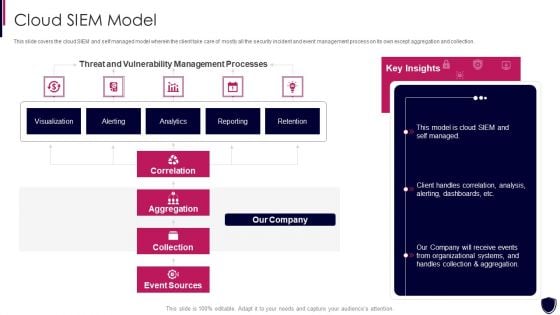
Enhancing Cyber Safety With Vulnerability Administration Cloud SIEM Model Clipart PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this enhancing cyber safety with vulnerability administration cloud siem model clipart pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources, our company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
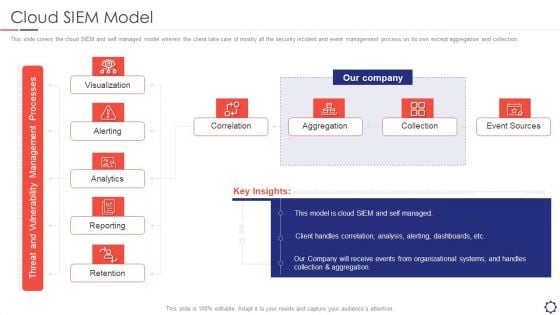
SIEM Cloud SIEM Model Ppt Infographics Picture PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. This is a siem cloud siem model ppt infographics picture pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like visualization, alerting, analytics, reporting, retention. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
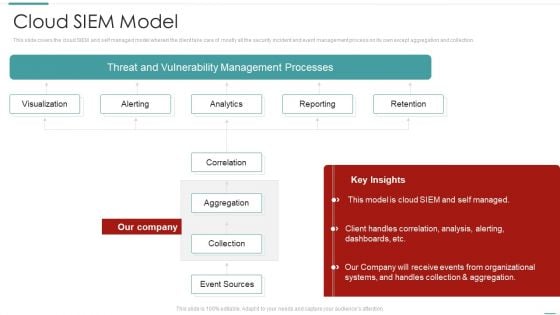
Risk Recognition Automation Cloud Siem Model Ppt Layouts Templates PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this risk recognition automation cloud siem model ppt layouts templates pdf. Use them to share invaluable insights on visualization, alerting, analytics, reporting, retention and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
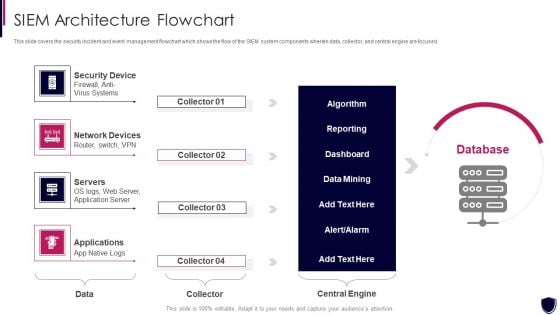
Enhancing Cyber Safety With Vulnerability Administration SIEM Architecture Flowchart Demonstration PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a enhancing cyber safety with vulnerability administration siem architecture flowchart demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
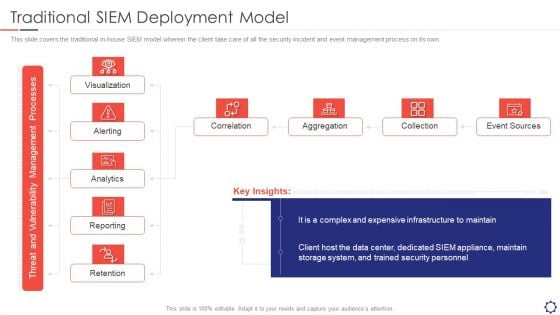
SIEM Traditional SIEM Deployment Model Ppt Model Shapes PDF
This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident and event management process on its own. Presenting siem traditional siem deployment model ppt model shapes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like visualization, alerting, analytics, reporting, retention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
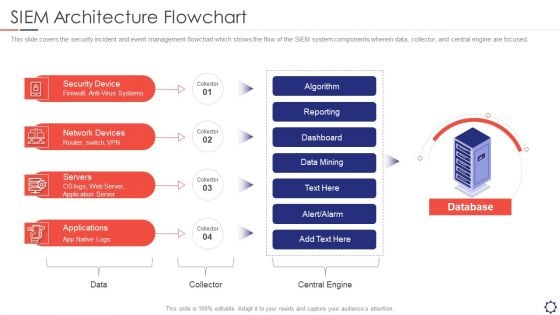
SIEM Architecture Flowchart Ppt Show Introduction PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a siem architecture flowchart ppt show introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SIEM Architecture Flowchart SIEM Services Ppt Infographic Template Graphics Download PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a siem architecture flowchart siem services ppt infographic template graphics download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like siem architecture flowchart. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
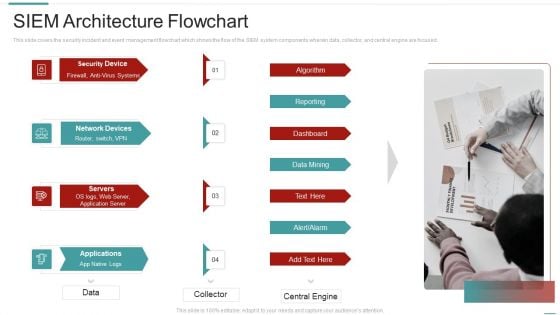
Risk Recognition Automation Siem Architecture Flowchart Ppt Summary Example File PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Presenting risk recognition automation siem architecture flowchart ppt summary example file pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reporting, dashboard, data mining, algorithm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
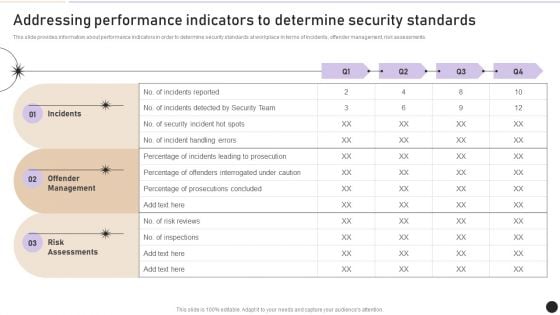
Addressing Performance Indicators To Determine Security Standards Introduction PDF
This slide provides information about performance indicators in order to determine security standards at workplace in terms of incidents, offender management, risk assessments. Boost your pitch with our creative Addressing Performance Indicators To Determine Security Standards Introduction PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF
This slide depicts the main tasks of the command security operations center. The purpose of this slide is to highlight the main responsibilities, responsible team members, and task status. The main tasks include monitoring and analyzing security events, coordinating incident response, managing security operations, etc. Get a simple yet stunning designed Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Best Practices For SRE Ppt PowerPoint Presentation File Icons PDF
The following slide depicts some tips to minimize issues and bugs and ensure error free reports. It also includes elements such as monitoring overload operations, managing policies, handling incidents etc. Presenting Best Practices For SRE Ppt PowerPoint Presentation File Icons PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Monitor Overload Operations, Manage Policies, Handle Incidents. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Program Strategic Agenda Process Microsoft Pdf
This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc. Showcasing this set of slides titled Information Security Program Strategic Agenda Process Microsoft Pdf. The topics addressed in these templates are Assets And Inventory, Evaluate Risk, Manage Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc.
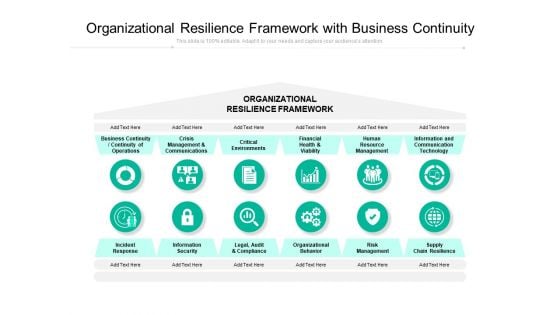
Organizational Resilience Framework With Business Continuity Ppt PowerPoint Presentation Portfolio Guide PDF
Presenting this set of slides with name organizational resilience framework with business continuity ppt powerpoint presentation portfolio guide pdf. This is a one stage process. The stages in this process are business continuity, continuity of operations, crisis management and communications, critical environments, financial health and viability, human resource management, information and communication technology, incident response, information security, legal, audit and compliance, organizational behavior, risk management, supply chain resilience. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
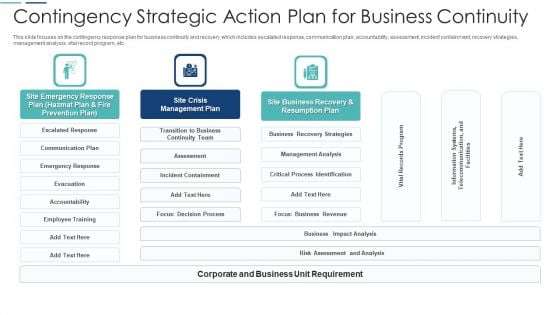
Contingency Strategic Action Plan For Business Continuity Structure PDF
This slide focuses on the contingency response plan for business continuity and recovery which includes escalated response, communication plan, accountability, assessment, incident containment, recovery strategies, management analysis, vital record program, etc. Pitch your topic with ease and precision using this contingency strategic action plan for business continuity structure pdf. This layout presents information on response plan, prevention plan, management plan, business recovery. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
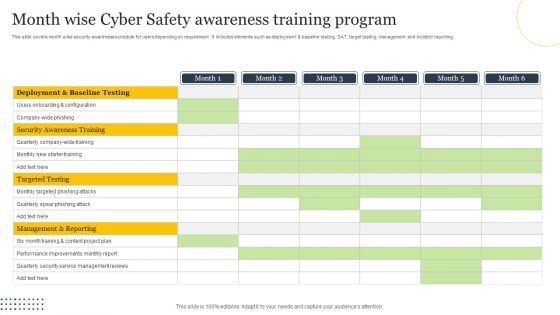
Month Wise Cyber Safety Awareness Training Program Ppt Styles Display PDF
This slide covers month wise security awareness schedule for users depending on requirement. It includes elements such as deployment and baseline testing, SAT, target testing, management and incident reporting. Showcasing this set of slides titled Month Wise Cyber Safety Awareness Training Program Ppt Styles Display PDF. The topics addressed in these templates are Security Awareness Training, Targeted Testing, Management And Reporting. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Data Governance Program With Issues And Resolution Icons PDF
The mentioned slide illustrates the data governance program which includes the issues, incident resolution, data governance role and MDM role.Showcasing this set of slides titled Data Governance Program With Issues And Resolution Icons PDF The topics addressed in these templates are Incident Resolution Role, Data Governance Role, Master Data Management Role All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
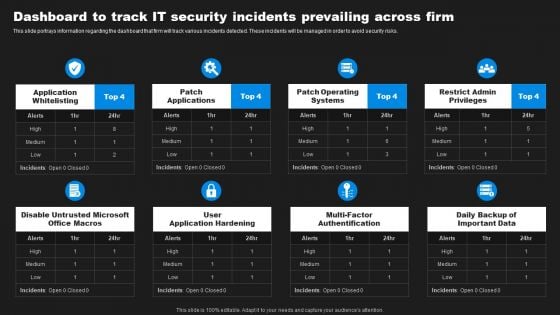
Enhancing Information Technology With Strategic Dashboard To Track IT Security Summary PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Enhancing Information Technology With Strategic Dashboard To Track IT Security Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF bundle. Topics like Asset Management, Protect Data Security, Incident Mitigation Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Improving Restaurant Operations Current Challenges Faced By Restaurant Ppt PowerPoint Presentation Inspiration Sample PDF
Presenting this set of slides with name improving restaurant operations current challenges faced by restaurant ppt powerpoint presentation inspiration sample pdf. The topics discussed in these slides are deteriorating sales, dissatisfied employees, restaurant management system, rise workplace accidents, incidents. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
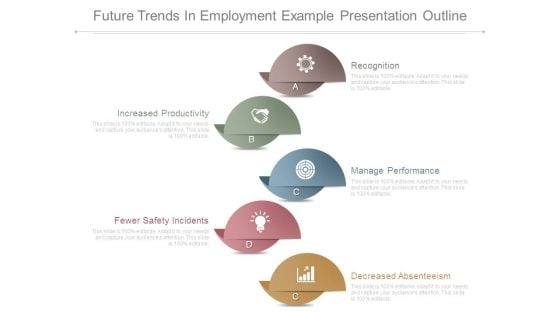
Future Trends In Employment Example Presentation Outline
This is a future trends in employment example presentation outline. This is a five stage process. The stages in this process are recognition, increased productivity, manage performance, decreased absenteeism, fewer safety incidents.

Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
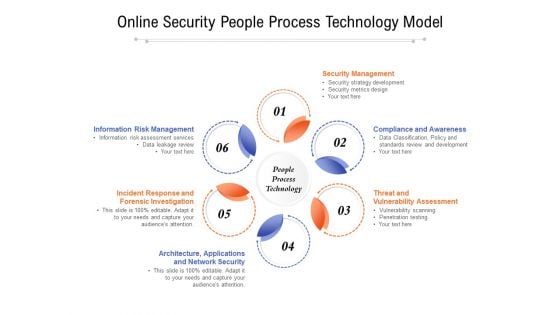
Online Security People Process Technology Model Ppt PowerPoint Presentation Slides Example Introduction PDF
Presenting online security people process technology model ppt powerpoint presentation slides example introduction pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including security management, compliance and awareness, threat and vulnerability assessment, architecture, applications, incident response and forensic investigation, information risk management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
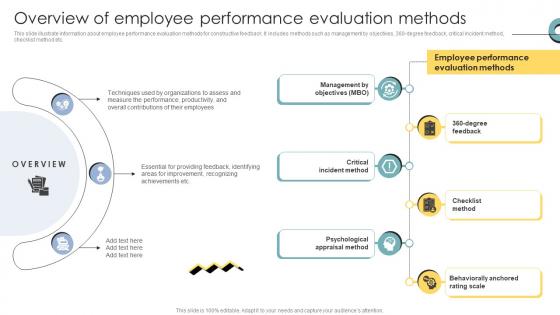
Skill Enhancement Performance Overview Of Employee Performance Evaluation Methods
This slide illustrate information about employee performance evaluation methods for constructive feedback. It includes methods such as management by objectives, 360-degree feedback, critical incident method, checklist method etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Skill Enhancement Performance Overview Of Employee Performance Evaluation Methods and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide illustrate information about employee performance evaluation methods for constructive feedback. It includes methods such as management by objectives, 360-degree feedback, critical incident method, checklist method etc.
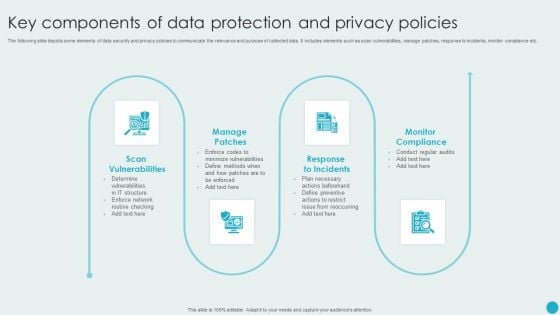
Key Components Of Data Protection And Privacy Policies Graphics PDF
The following slide depicts some elements of data security and privacy policies to communicate the relevance and purpose of collected data. It includes elements such as scan vulnerabilities, manage patches, response to incidents, monitor compliance etc. Presenting Key Components Of Data Protection And Privacy Policies Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Patches, Response To Incidents, Monitor Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
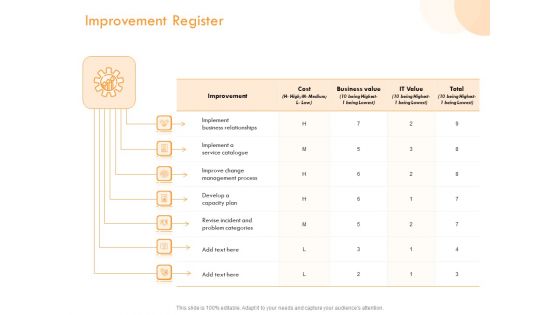
ITIL Operational Evaluation Rigorous Service Enhancement Improvement Register Ppt PowerPoint Presentation Outline Format PDF
Presenting itil operational evaluation rigorous service enhancement improvement register ppt powerpoint presentation outline format pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like implement business relationships, implement service catalogue, improve change management process, develop capacity plan, revise incident and problem categories. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
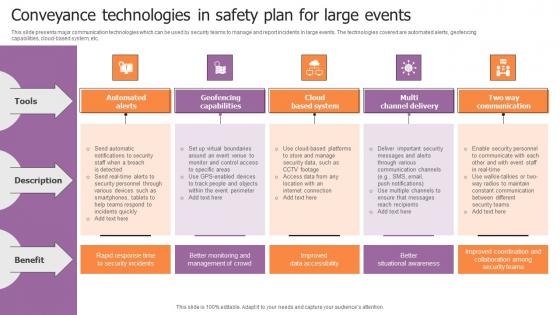
Conveyance Technologies In Safety Plan For Large Events Brochure Pdf
This slide presents major communication technologies which can be used by security teams to manage and report incidents in large events. The technologies covered are automated alerts, geofencing capabilities, cloud-based system, etc. Showcasing this set of slides titled Conveyance Technologies In Safety Plan For Large Events Brochure Pdf. The topics addressed in these templates are Automated Alerts, Geofencing Capabilities, Cloud Based System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents major communication technologies which can be used by security teams to manage and report incidents in large events. The technologies covered are automated alerts, geofencing capabilities, cloud-based system, etc.

Deploying Data Governance Digital Transformation Journey PPT PowerPoint DT SS V
This slide presents strategies for ensuring data governance and compliance in a regulated energy and utilities industry. It includes data governance, access controls, audit trail and reporting, vendor management, regulatory compliance monitoring and data incident response. This modern and well-arranged Deploying Data Governance Digital Transformation Journey PPT PowerPoint DT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide presents strategies for ensuring data governance and compliance in a regulated energy and utilities industry. It includes data governance, access controls, audit trail and reporting, vendor management, regulatory compliance monitoring and data incident response.

Civil Contractors Company Health And Safety Policy Ppt Professional Vector PDF
This slide provides the list of health and safety commitment policy offered by our construction company such as special trainings to managers and foremen, regular safety meetings, etc. Deliver and pitch your topic in the best possible manner with this civil contractors company health and safety policy ppt professional vector pdf. Use them to share invaluable insights on management staff, stop work, dangerous condition or act, incident review committee, employee and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
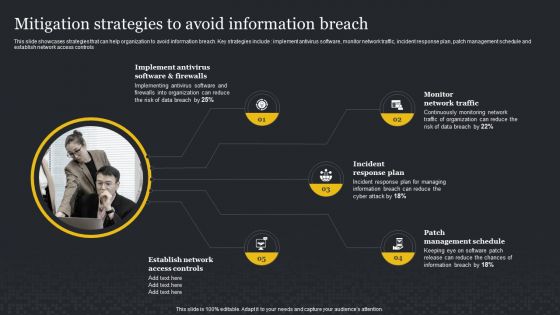
Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Present like a pro with Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
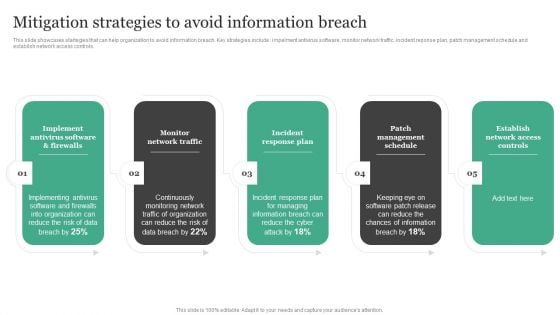
Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Presenting this PowerPoint presentation, titled Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF
The following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Access Control, Patch Management, Security Solution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
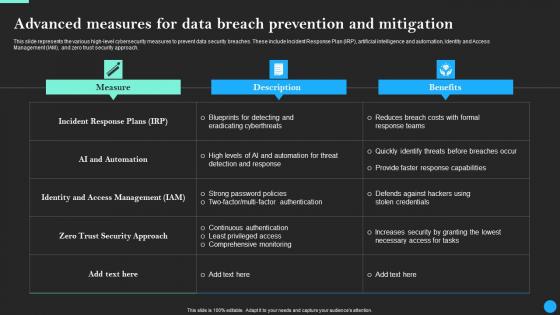
Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.
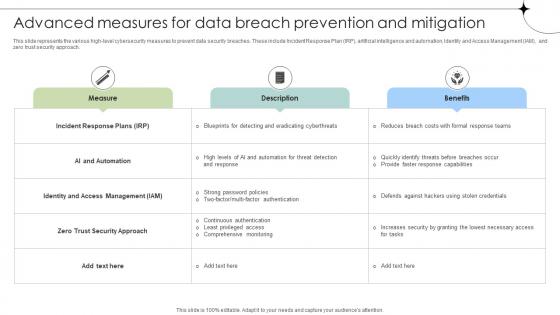
Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.
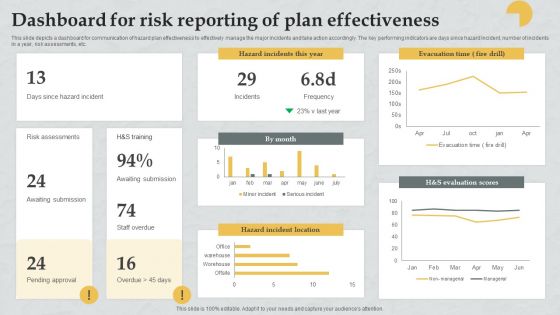
Dashboard For Risk Reporting Of Plan Effectiveness Download PDF
This slide depicts a dashboard for communication of hazard plan effectiveness to effectively manage the major incidents and take action accordingly. The key performing indicators are days since hazard incident, number of incidents in a year, risk assessments, etc. Showcasing this set of slides titled Dashboard For Risk Reporting Of Plan Effectiveness Download PDF. The topics addressed in these templates are Risk Assessments, Awaiting Submission, Awaiting Submission. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
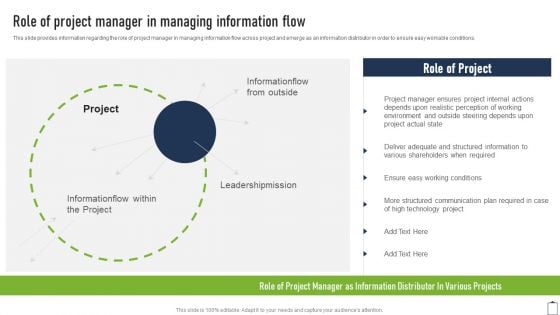
Role Of Project Manager In Managing Information Flow Project Managers Playbook Download PDF
This slide provides information regarding the role of project manager in managing information flow across project and emerge as an information distributor in order to ensure easy workable conditions. Deliver and pitch your topic in the best possible manner with this Role Of Project Manager In Managing Information Flow Project Managers Playbook Download PDF. Use them to share invaluable insights on Project Manager, Structured Communication, Technology Project and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
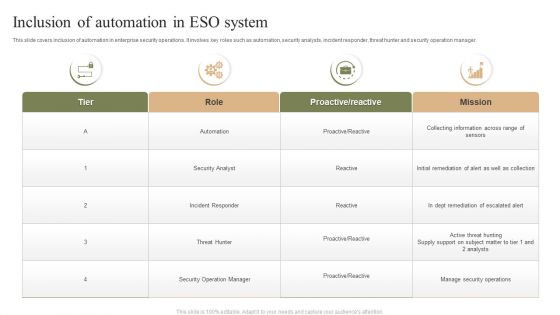
Inclusion Of Automation In ESO System Ppt PowerPoint Presentation File Maker PDF
This slide covers inclusion of automation in enterprise security operations. It involves key roles such as automation, security analysts, incident responder, threat hunter and security operation manager. Pitch your topic with ease and precision using this Inclusion Of Automation In ESO System Ppt PowerPoint Presentation File Maker PDF. This layout presents information on Mission, Role, Tier. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Staff Training Program Key Performance Indicators Diagrams PDF
The following slide highlights the staff training program key performance Indicators illustrating key headings which includes customer satisfaction rate, onboarding, compliance and incident reports, sales closure rates, net promoter score and management effectiveness Presenting Staff Training Program Key Performance Indicators Diagrams PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Turnover Quarter, Turnover Type, Turnover Reasons In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Employee Health And Risk Key Performance Indicator Dashboard Ppt Layouts Brochure PDF
The following slide highlights the employee health and safety key performance indicator dashboard illustrating narrow escapes, potential hazards, improvement opportunity, total incidents, health and safety learning, safety visit by management, ltir and trir, severe injuries and fatalities and safety goals. Showcasing this set of slides titled Employee Health And Risk Key Performance Indicator Dashboard Ppt Layouts Brochure PDF. The topics addressed in these templates are Narrow Escapes, Potential Hazards, Improvement Opportunity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
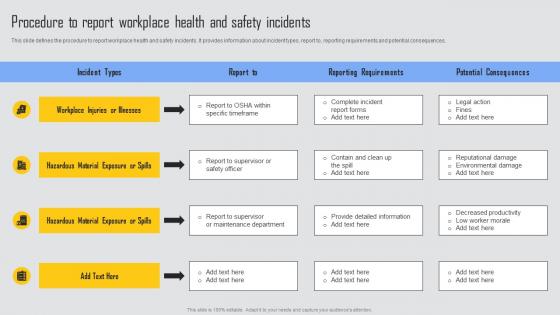
Procedure To Report Workplace Managing Risks And Establishing Trust Through Efficient Structure Pdf
This slide defines the procedure to report workplace health and safety incidents. It provides information about incident types, report to, reporting requirements and potential consequences. The Procedure To Report Workplace Managing Risks And Establishing Trust Through Efficient Structure Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide defines the procedure to report workplace health and safety incidents. It provides information about incident types, report to, reporting requirements and potential consequences.
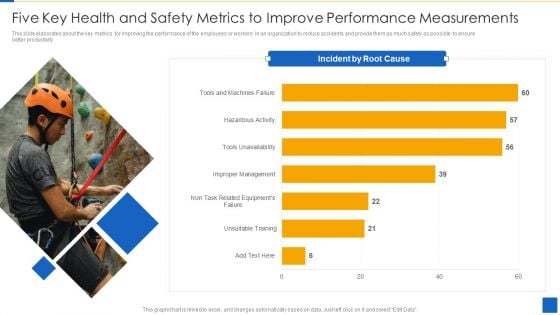
Five Key Health And Safety Metrics To Improve Performance Measurements Brochure PDF
This slide elaborates about the key metrics for improving the performance of the employees or workers in an organization to reduce accidents and provide them as much safety as possible to ensure better productivity.Showcasing this set of slides titled Five Key Health And Safety Metrics To Improve Performance Measurements Brochure PDF The topics addressed in these templates are Incidents Root Cause, Unsuitable Training, Improper Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
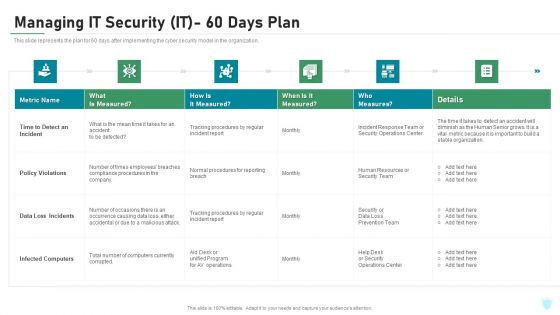
Managing IT Security IT 60 Days Plan Ppt Ideas Graphics PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative managing it security it 60 days plan ppt ideas graphics pdf bundle. Topics like policy violations, infected computers, data loss incidents, time to detect an incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
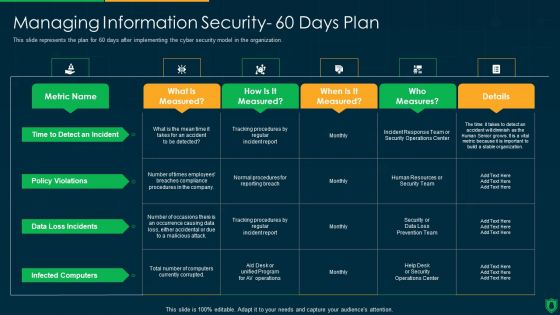
Info Security Managing Information Security 60 Days Plan Ppt PowerPoint Presentation File Graphics Example PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver and pitch your topic in the best possible manner with this info security managing information security 60 days plan ppt powerpoint presentation file graphics example pdf. Use them to share invaluable insights on policy violations, data loss incidents, infected computers, time to detect an incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Information Technology Compliance Procedure Checklist Icons PDF
This slide presents information technology checklist, helpful in defining key tasks to be accomplished for successful completion of compliance process and management. It includes Access and identity control, incident response, disaster recovery, data loss prevention and protection against malware Showcasing this set of slides titled Information Technology Compliance Procedure Checklist Icons PDF. The topics addressed in these templates are Key Elements, Activities Accomplished, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Strategies To Develop Effective Cyber Security Plan Ppt Powerpoint Presentation File Icon Pdf
This slide represents the techniques to be adopted by administration to effectively manage cyber security incidents in order to reduce their impact on business operations. It includes strategies to develop cyber security plan such as establish IR team, conduct threat analysis etc. The Strategies To Develop Effective Cyber Security Plan Ppt Powerpoint Presentation File Icon Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the techniques to be adopted by administration to effectively manage cyber security incidents in order to reduce their impact on business operations. It includes strategies to develop cyber security plan such as establish IR team, conduct threat analysis etc.

ESO System Center Team Roles And Responsibilities Ppt PowerPoint Presentation File Slides PDF
This slide covers enterprise security operation center team roles and responsibilities. It involves key roles such as incident responder, security investigator, advanced security analyst and SOC manager. Pitch your topic with ease and precision using this ESO System Center Team Roles And Responsibilities Ppt PowerPoint Presentation File Slides PDF. This layout presents information on SOC Team Roles, Responsibilities, Tier. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
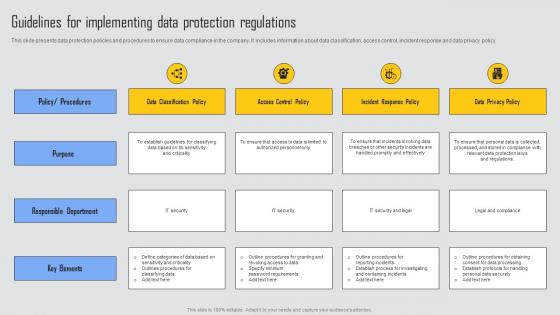
Guidelines For Implementing Managing Risks And Establishing Trust Through Efficient Formats Pdf
This slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Guidelines For Implementing Managing Risks And Establishing Trust Through Efficient Formats Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Guidelines For Implementing Managing Risks And Establishing Trust Through Efficient Formats Pdf today and make your presentation stand out from the rest This slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy.

Managing IT Operating System Lifecycle Adaptive Components Of A Resilience Framework Elements PDF
Presenting this set of slides with name managing it operating system lifecycle adaptive components of a resilience framework elements pdf. This is a four stage process. The stages in this process are post disaster response and recovery, pre incident adaptive prevention, evolving threats predictive problem solution. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Visual Mining Dashboard Diagram Ppt Example
This is a visual mining dashboard diagram ppt example. This is a three stage process. The stages in this process are incident costs range, incident vs incident costs, total incident cost.
Cyber Security Cases Action Plan Risk Tracking Dashboard For Response Ppt PowerPoint Presentation File Graphics Example PDF
This slide highlights dashboard to identify and track security threats occurred in the company. The purpose of this template is to provide information to the management about severities of the incidents along with risk rating in form of heat map. Showcasing this set of slides titled Cyber Security Cases Action Plan Risk Tracking Dashboard For Response Ppt PowerPoint Presentation File Graphics Example PDF. The topics addressed in these templates are Risk Heat Map, Action Plan Breakdown, Risk Rating Breakdown. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
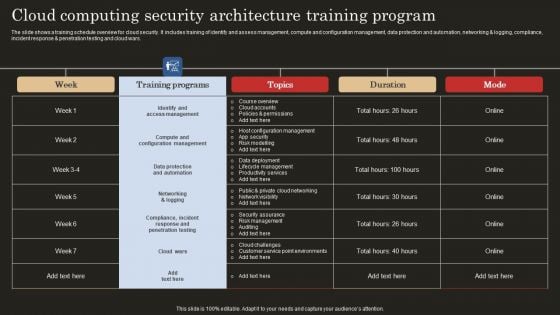
Cloud Computing Security Architecture Training Program Guidelines PDF
The slide shows a training schedule overview for cloud security. It includes training of identify and assess management, compute and configuration management, data protection and automation, networking and logging, compliance, incident response and penetration testing and cloud wars. Showcasing this set of slides titled Cloud Computing Security Architecture Training Program Guidelines PDF. The topics addressed in these templates are Identify Access Management, Compute Configuration Management, Data Protection Automation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































