Industry Security
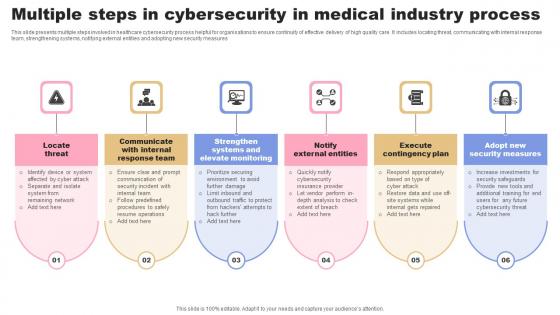
Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf
This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures Pitch your topic with ease and precision using this Multiple Steps In Cybersecurity In Medical Industry Process Formats Pdf This layout presents information on Locate Threat, Response Team, Elevate Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents multiple steps involved in healthcare cybersecurity process helpful for organisations to ensure continuity of effective delivery of high quality care. It includes locating threat, communicating with internal response team, strengthening systems, notifying external entities and adopting new security measures

Key Takeaways And Strategic Port Terminal Industry Ppt PowerPoint
The purpose of this slide is to provide a brief insights related to the ports market and its growth. It covers opportunity protection, macro and geopolitical insights related to the insurers, and demand for cyber security ports and services analysis.Explore a selection of the finest Key Takeaways And Strategic Port Terminal Industry Ppt PowerPoint here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Takeaways And Strategic Port Terminal Industry Ppt PowerPoint to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The purpose of this slide is to provide a brief insights related to the ports market and its growth. It covers opportunity protection, macro and geopolitical insights related to the insurers, and demand for cyber security ports and services analysis.

Top Digital Industry Trends In Banking In 2021 Ideas PDF
This slide shows some of the top digital industry trends in banking that are most widely adopted such as seamless payments, next gen and digital banks, mobile applications, robotics process automation and ai artificial intelligence, cybersecurity etc. This is a top digital industry trends in banking in 2021 ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like seamless payments, mobile applications, cyber security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Applications Of AI In Banking Industry Icons PDF
This slide signifies the smart manufacturing key threats and solutions to overcome. It covers information about challenges like safety in human robot collaboration, security issue and skill development with strategies implemented to overcome them Pitch your topic with ease and precision using this Applications Of AI In Banking Industry Icons PDF. This layout presents information on Experience, Banking, Process. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
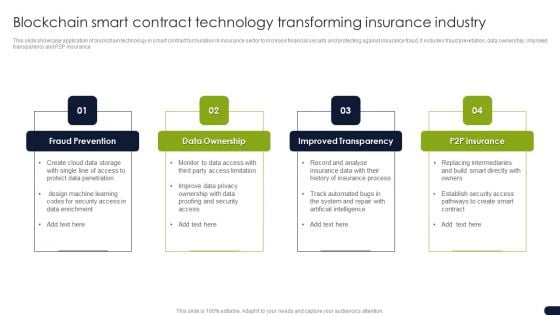
Blockchain Smart Contract Technology Transforming Insurance Industry Diagrams PDF
This slide showcase application of blockchain technology in smart contract formulation in insurance sector to increase financial security and protecting against insurance fraud. It includes fraud prevetation, data ownership, improved transparency and P2P insurance. Persuade your audience using this Blockchain Smart Contract Technology Transforming Insurance Industry Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Ownership, Improved Transparency, Fraud Prevention. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
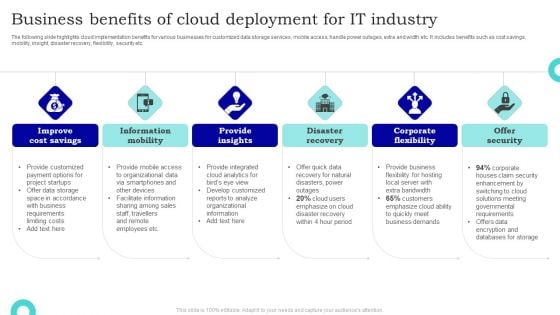
Business Benefits Of Cloud Deployment For IT Industry Sample PDF
The following slide highlights cloud implementation benefits for various businesses for customized data storage services, mobile access, handle power outages, extra and width etc. It includes benefits such as cost savings, mobility, insight, disaster recovery, flexibility, security etc. Presenting Business Benefits Of Cloud Deployment For IT Industry Sample PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Information Mobility, Provide Insights, Disaster Recovery. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
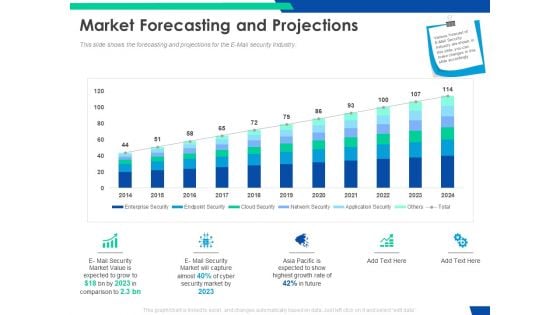
Cloud Based Email Security Market Report Market Forecasting And Projections Ppt Infographics Themes PDF
This slide shows the forecasting and projections for the E Mail security Industry. Deliver and pitch your topic in the best possible manner with this cloud based email security market report market forecasting and projections ppt infographics themes pdf. Use them to share invaluable insights on market forecasting and projections and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
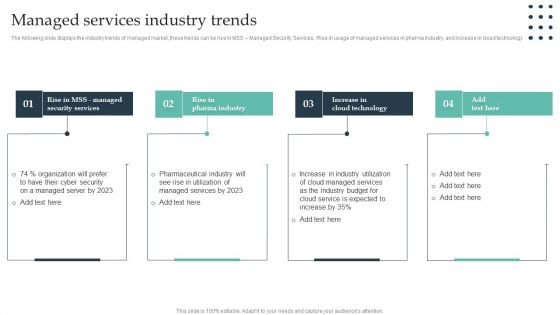
Enterprise Consumer Technology Management Managed Services Industry Trends Slides PDF
The following slide displays the industry trends of managed market, these trends can be rise in MSS Managed Security Services, Rise in usage of managed services in pharma industry, and increase in cloud technology. Slidegeeks is here to make your presentations a breeze with Enterprise Consumer Technology Management Managed Services Industry Trends Slides PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

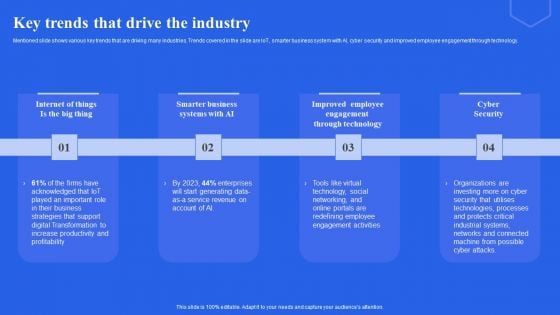
Key Trends That Drive The Industry Ppt Layouts Images PDF
Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology. Get a simple yet stunning designed Key Trends That Drive The Industry Ppt Layouts Images PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Key Trends That Drive The Industry Ppt Layouts Images PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Key Trends That Drive The Industry Ppt Professional Templates PDF
Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology. If you are looking for a format to display your unique thoughts, then the professionally designed Key Trends That Drive The Industry Ppt Professional Templates PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Trends That Drive The Industry Ppt Professional Templates PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
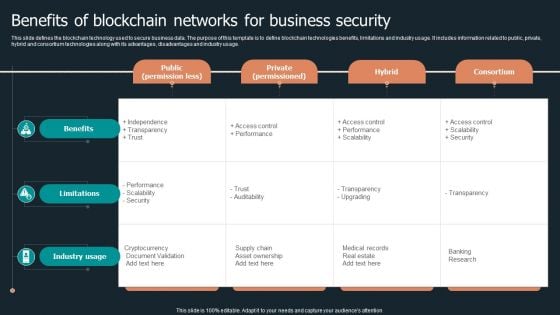
Benefits Of Blockchain Networks For Business Security Structure PDF
This slide defines the blockchain technology used to secure business data. The purpose of this template is to define blockchain technologies benefits, limitations and industry usage. It includes information related to public, private, hybrid and consortium technologies along with its advantages, disadvantages and industry usage. Pitch your topic with ease and precision using this Benefits Of Blockchain Networks For Business Security Structure PDF. This layout presents information on Public Permission Less, Private Permissioned, Hybrid Consortium. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
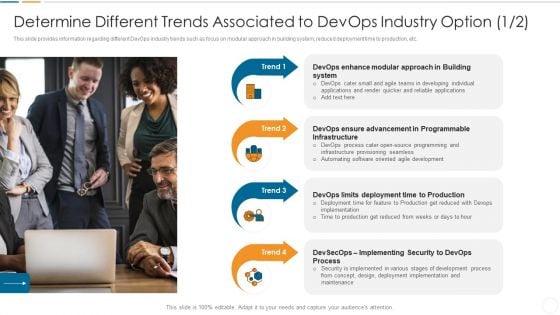
Future Trends Of Devops Industry IT Determine Different Trends Associated To Devops Industry Option 1 2 Sample PDF
This slide provides information regarding different DevOps industry trends such as focus on modular approach in building system, reduced deployment time to production, etc.Presenting future trends of devops industry it determine different trends associated to devops industry option 1 2 sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like programmable infrastructure, implementing security to devops, approach in building. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Log Management Process In Application Security Testing Ppt Powerpoint Brochure
This slide showcases the introduction of log management in application security for decreasing the security threats. The Log Management Process In Application Security Testing Ppt Powerpoint Brochure is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide showcases the introduction of log management in application security for decreasing the security threats.

Table Of Contents For Application Security Testing Ppt Powerpoint Designs
The Table Of Contents For Application Security Testing Ppt Powerpoint Designs is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Our Table Of Contents For Application Security Testing Ppt Powerpoint Designs are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
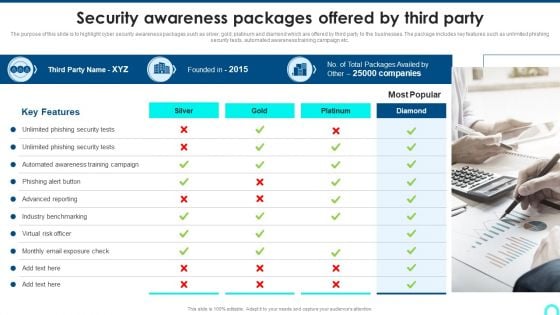
Security Awareness Packages Offered By Third Party Clipart PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. This is a Security Awareness Packages Offered By Third Party Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Unlimited Phishing, Automated Awareness, Industry Benchmarking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

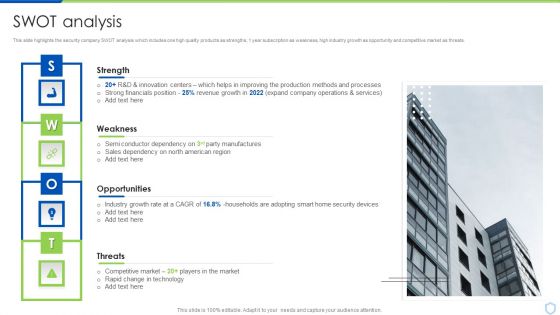
Smart Home Security Solutions Company Profile SWOT Analysis Rules PDF
This slide highlights the security company SWOT analysis which includes one high quality products as strengths, 1 year subscription as weakness, high industry growth as opportunity and competitive market as threats. Presenting Smart Home Security Solutions Company Profile SWOT Analysis Rules PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths Weaknesses Opportunities, Threats Market Technology, Home Security Devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
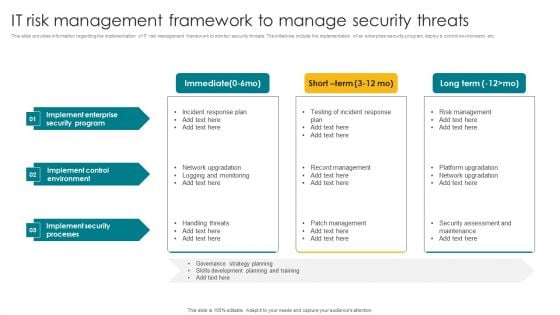
IT Risk Management Framework To Manage Security Threats Template PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. The IT Risk Management Framework To Manage Security Threats Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Green Computing Improving Security By Green Computing Technology
This slide outlineshow green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. The Green Computing Improving Security By Green Computing Technology is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlineshow green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.
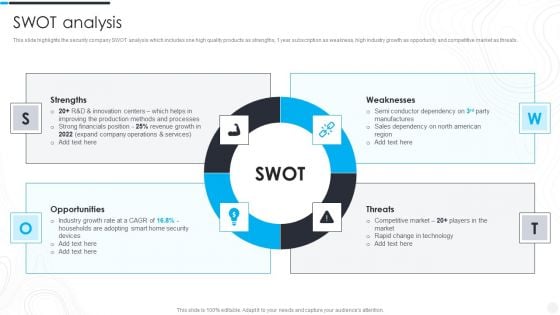
Security And Surveillance Company Profile SWOT Analysis Infographics PDF
This slide highlights the security company SWOT analysis which includes one high quality products as strengths, 1 year subscription as weakness, high industry growth as opportunity and competitive market as threats. This is a Security And Surveillance Company Profile SWOT Analysis Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Financials Position, Innovation Centers, Operations Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security Camera System Company Profile SWOT Analysis Infographics PDF
This slide highlights the security company SWOT analysis which includes one high quality products as strengths, 1 year subscription as weakness, high industry growth as opportunity and competitive market as threats. This is a Security Camera System Company Profile SWOT Analysis Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strengths, Weaknesses, Opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
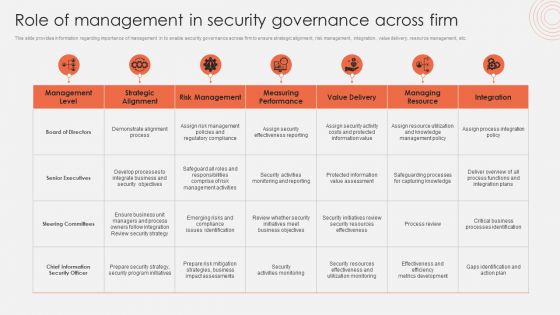
Role Of Management In Security Governance Across Firm Mockup PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. The Role Of Management In Security Governance Across Firm Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
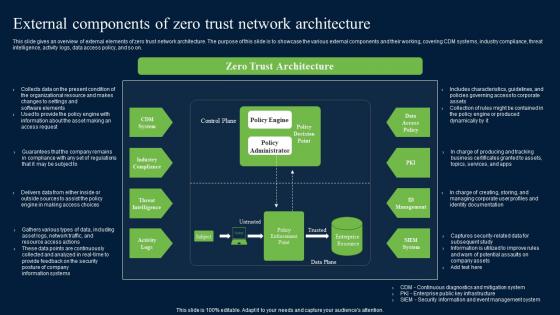
External Components Of Zero Trust Network Security Structure Pdf
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Security Structure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.

Web Consulting Business Website Security Management Action Plan
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc. The Web Consulting Business Website Security Management Action Plan is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc.
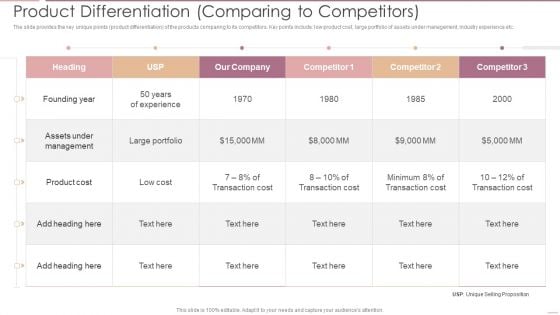
Investment Banking Security Underwriting Pitchbook Product Differentiation Comparing Clipart PDF
The slide provides the key unique points product differentiation of the products comparing to its competitors. Key points include low product cost, large portfolio of assets under management, industry experience etc. Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Product Differentiation Comparing Clipart PDF. Use them to share invaluable insights on Under Management, Transaction Cost, Minimum Transaction and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

SDN Security Architecture Ppt PowerPoint Presentation Complete Deck With Slides
This is a professional and ready to use PowerPoint deck for entrepreneurs, who want to showcase their business in the best light possible. Use this SDN Security Architecture Ppt PowerPoint Presentation Complete Deck With Slides and prepare an engaging pitch to showcase potential in the industry of your choice. Whether you are just starting out or business or planning to scale, deploy this ffity nine slide complete deck to demonstrate your ideas for bringing innovation and creativity in the business. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now.
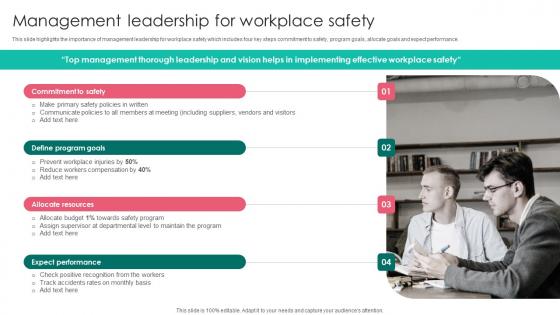
Management Leadership Workplace Safety Protocol And Security Practices Sample Pdf
This slide highlights the importance of management leadership for workplace safety which includes four key steps commitment to safety, program goals, allocate goals and expect performance. The Management Leadership Workplace Safety Protocol And Security Practices Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide highlights the importance of management leadership for workplace safety which includes four key steps commitment to safety, program goals, allocate goals and expect performance.
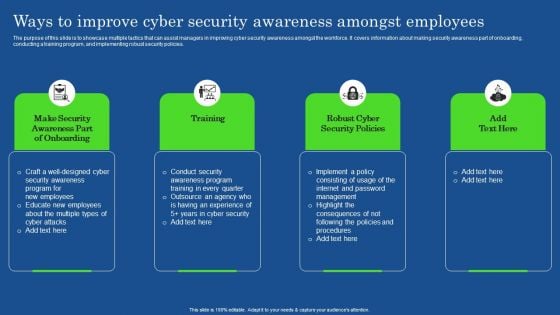
Ways To Improve Cyber Security Awareness Amongst Employees Elements PDF
The purpose of this slide is to showcase multiple tactics that can assist managers in improving cyber security awareness amongst the workforce. It covers information about making security awareness part of onboarding, conducting a training program, and implementing robust security policies. The Ways To Improve Cyber Security Awareness Amongst Employees Elements PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
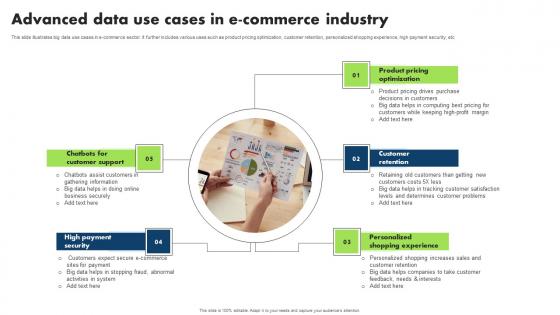
Advanced Data Use Cases In E Commerce Industry Guidelines Pdf
This slide illustrates big data use cases in e commerce sector. It further includes various uses such as product pricing optimization, customer retention, personalized shopping experience, high payment security, etc Pitch your topic with ease and precision using this Advanced Data Use Cases In E Commerce Industry Guidelines Pdf. This layout presents information on Chatbots For Customer Support, High Payment Security, Personalized Shopping Experience. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates big data use cases in e commerce sector. It further includes various uses such as product pricing optimization, customer retention, personalized shopping experience, high payment security, etc
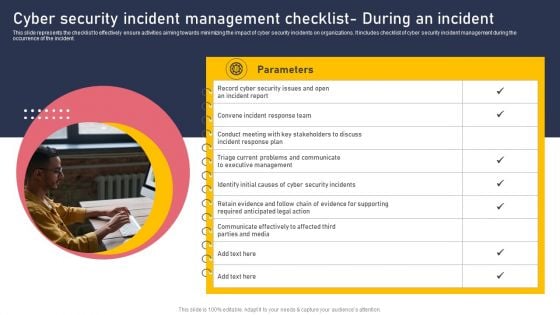
Cyber Security Incident Management Checklist During An Incident Inspiration PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. The Cyber Security Incident Management Checklist During An Incident Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF
This slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. The Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
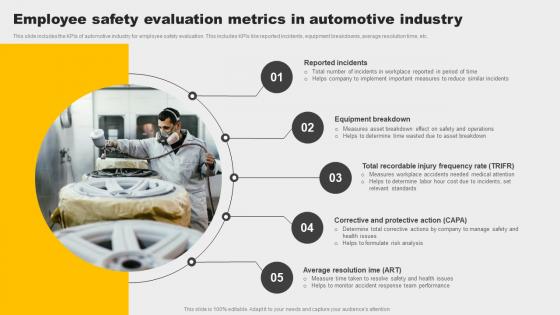
Employee Safety Evaluation Metrics In Automotive Industry Guidelines Pdf
This slide includes the KPIs of automotive industry for employee safety evaluation. This includes KPIs like reported incidents, equipment breakdowns, average resolution time, etc. Pitch your topic with ease and precision using this Employee Safety Evaluation Metrics In Automotive Industry Guidelines Pdf. This layout presents information on Reported Incidents, Equipment Breakdown, Corrective And Protective Action. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide includes the KPIs of automotive industry for employee safety evaluation. This includes KPIs like reported incidents, equipment breakdowns, average resolution time, etc.

Key Industry Evolutions Of Iot In Digital Era Clipart PDF
This slide presents key industry trends in Internet of things helpful in reducing errors, effective cost optimization and increasing production quality. It includes some latest trends in smart homes, security, healthcare and edge computing useful in enhancing safety of processes. Persuade your audience using this Key Industry Evolutions Of Iot In Digital Era Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security, Healthcare, Edge Computing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

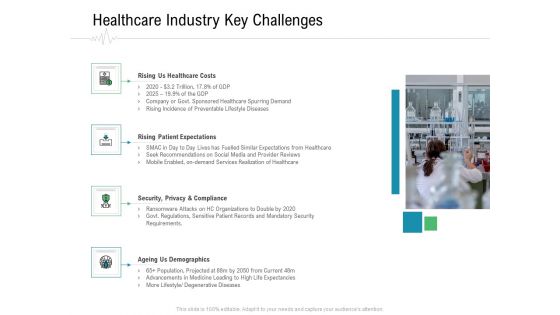
Overview Healthcare Business Management Healthcare Industry Key Challenges Microsoft PDF
Presenting this set of slides with name overview healthcare business management healthcare industry key challenges microsoft pdf. The topics discussed in these slides are rising us healthcare costs, rising patient expectations, security, privacy and compliance, ageing us demographics. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Hospital Management Healthcare Industry Key Challenges Ppt Styles Graphics PDF
Deliver an awe inspiring pitch with this creative hospital management healthcare industry key challenges ppt styles graphics pdf bundle. Topics like rising us healthcare costs, rising patient expectations, security, privacy and compliance, ageing us demographics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Nursing Administration Healthcare Industry Key Challenges Ppt Show Templates PDF
Deliver an awe inspiring pitch with this creative nursing administration healthcare industry key challenges ppt show templates pdf bundle. Topics like rising us healthcare costs, rising patient expectations, security, privacy and compliance, ageing us demographics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

E Healthcare Management System Healthcare Industry Key Challenges Topics PDF
Deliver an awe inspiring pitch with this creative e healthcare management system healthcare industry key challenges topics pdf bundle. Topics like rising us healthcare costs, rising patient expectations, security, privacy and compliance, ageing us demographics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Retail Industry Outlook Retail Price Management Goals Brochure PDF
Deliver and pitch your topic in the best possible manner with this retail industry outlook retail price management goals brochure pdf. Use them to share invaluable insights on enterprise wide price transparency, price monitoring and analysis, system wide security, real time performance metrics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Impact Of RPA In Automotive Industry Topics Pdf
This slide includes the impact of automation and industrial robots in the automotive industry. It includes benefits such as better quality and consistency, maximum productivity, greater safety, and lower investment in labour costs. Pitch your topic with ease and precision using this Key Impact Of RPA In Automotive Industry Topics Pdf. This layout presents information on Maximum Productivity, Greater Safety, Lower Investment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide includes the impact of automation and industrial robots in the automotive industry. It includes benefits such as better quality and consistency, maximum productivity, greater safety, and lower investment in labour costs.

Impact Of IT Cloud Services In Banking Industry Brochure PDF
This slide represents the cloud computing assistance use in banking sector. It includes stages like enhance security, reduced data, increase customer insight and risk safety. Persuade your audience using this impact of it cloud services in banking industry brochure pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including enhance security, data protection, increase customer insight, risk safety. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Challenges Of Big Data In Health Industry Diagrams PDF
The following slide showcases challenges that healthcare organizations face while implementing big data. It include problems such as capturing data, high implementation cost, ensuring data privacy and security, and lack of appropriate staff. Presenting Challenges Of Big Data In Health Industry Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Collection, Implementation Costs, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
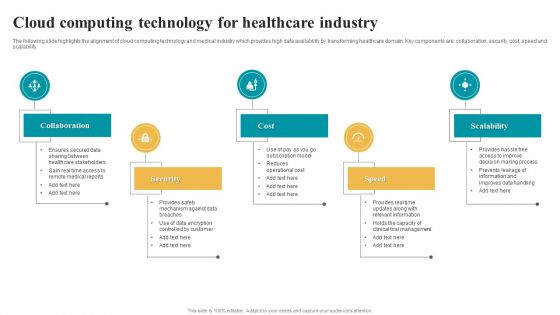
Cloud Computing Technology For Healthcare Industry Topics PDF
The following slide highlights the alignment of cloud computing technology and medical industry which provides high data availability by transforming healthcare domain. Key components are collaboration, security, cost, speed and scalability. Presenting Cloud Computing Technology For Healthcare Industry Topics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Healthcare Stakeholders, Remote Medical Reports, Mechanism Against. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cryptocurrency Investment Playbook Key Trends In Bitcoin Industry Mockup PDF
The following slide displays key trends that will impact the Bitcoin industry, these trends can boost the market towards growth and help an investor to understand the overall shape of the market. These trends can be transparency and data security, adoption of crypto by financial institution etc.Presenting cryptocurrency investment playbook key trends in bitcoin industry mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like transparency and data security, international currency, adoption in banks In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Techniques For Executing Workflow Automation In Industry Procedures Complete Deck
This presentation deck contains fifty four professionally designed templates that eliminate the hassle of creating visually appealing presentations for you. It is your perfect option to communicate your thoughts in an easy-to-understand and effective manner. This Techniques For Executing Workflow Automation In Industry Procedures Complete Deck comes with a wide range of features like high-quality, graphics and 100 percent customizable layout. Graphs, charts, and polls are attention-grabbing visually interactive elements of this presentation bundle that will lock the eye of spectators on the screen. It also contains text styles, colors, background themes, and other design elements that perfectly complement each other and create a stunning template bundle. Take advantage of this PowerPoint Set to upgrade your presentation game and steer back your competitors. Our Techniques For Executing Workflow Automation In Industry Procedures Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
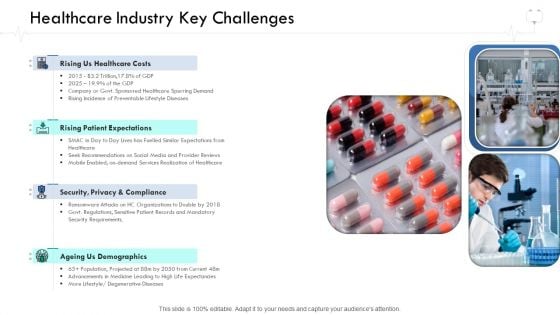
Wellness Management Healthcare Industry Key Challenges Ppt Professional Portfolio PDF
This is a wellness management healthcare industry key challenges ppt professional portfolio pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like patient expectations, ageing us demographics, security, privacy, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
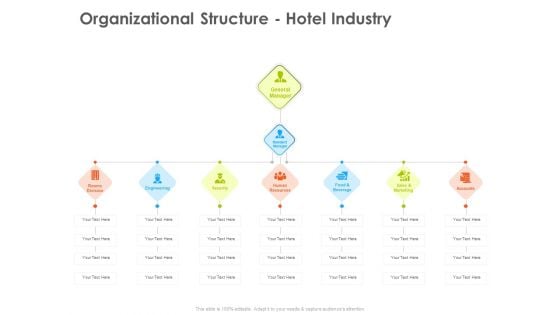
Hotel And Tourism Planning Organizational Structure Hotel Industry Elements PDF
This is a hotel and tourism planning organizational structure hotel industry elements pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like engineering, security, resources, sales and marketing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Hotel Management Plan Organizational Structure Hotel Industry Template PDF
This is a hotel management plan organizational structure hotel industry template pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like engineering, security, resources, sales and marketing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Merchandising Industry Analysis Retail Price Management Goals Graphics PDF
Presenting merchandising industry analysis retail price management goals graphics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like enterprise wide price transparency, price monitoring and analysis, system wide security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
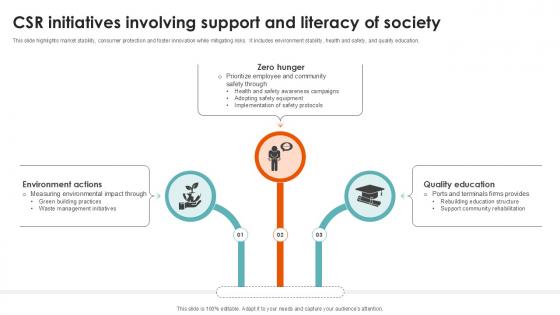
Csr Initiatives Involving Sup Port Terminal Industry Ppt Example
This slide highlights market stability, consumer protection and foster innovation while mitigating risks. It includes environment stability, health and safety, and quality education. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Csr Initiatives Involving Sup Port Terminal Industry Ppt Example a try. Our experts have put a lot of knowledge and effort into creating this impeccable Csr Initiatives Involving Sup Port Terminal Industry Ppt Example. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights market stability, consumer protection and foster innovation while mitigating risks. It includes environment stability, health and safety, and quality education.

Effective Checklist For Cybersecurity In Medical Industry Brochure Pdf
This slide presents effective checklist for setting up cybersecurity in healthcare helpful for organisations to check completion of important tasks. It includes mobility policy, disaster recovery provider, proper password policy and encryption Showcasing this set of slides titled Effective Checklist For Cybersecurity In Medical Industry Brochure Pdf. The topics addressed in these templates are Factors, Description, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents effective checklist for setting up cybersecurity in healthcare helpful for organisations to check completion of important tasks. It includes mobility policy, disaster recovery provider, proper password policy and encryption

Ecommerce Industry Key Challenges With Solution Ppt Pictures Background PDF
This slide exhibit various hurdles faced by ecommerce companies along with their solutions to overcome them. It includes challenges such as cyber and data security, online identity verification, cross-border ecommerce, elements placement and data privacy. Pitch your topic with ease and precision using this Ecommerce Industry Key Challenges With Solution Ppt Pictures Background PDF. This layout presents information on Online Identity Verification, Cross Border Ecommerce, Elements Placement. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Drone Tech Applications In Farming Industry Brochure PDF
The following slide highlights usage of drone technology for surveying topographic boundaries and soil monitoring. It includes components such as planting and seeding, spray treatment, security, livestock management and crop surveillance etc.Showcasing this set of slides titled Drone Tech Applications In Farming Industry Brochure PDF. The topics addressed in these templates are Planting Seeding, Livestock Management, Spray Treatment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
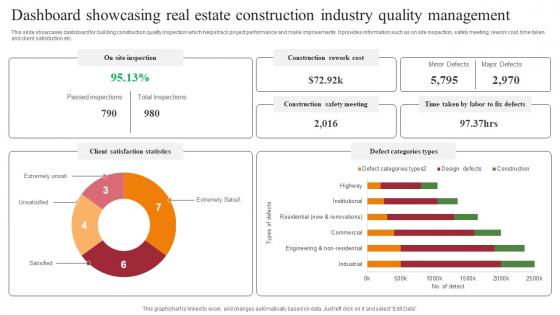
Dashboard Showcasing Real Estate Construction Industry Quality Management Topics Pdf
This slide showcases dashboard for building construction quality inspection which helps track project performance and make improvements. It provides information such as on site inspection, safety meeting, rework cost, time taken and client satisfaction etc. Pitch your topic with ease and precision using this Dashboard Showcasing Real Estate Construction Industry Quality Management Topics Pdf. This layout presents information on Client Satisfaction Statistics, Defect Categories Types. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases dashboard for building construction quality inspection which helps track project performance and make improvements. It provides information such as on site inspection, safety meeting, rework cost, time taken and client satisfaction etc.

RPA Implementation Process For In Automotive Industry Portrait Pdf
This slide exhibits the RPA implementation process aimed at reducing repetitive tasks and improving workforce safety. It includes key steps such as plan, assess, select implementation model, and implement. Pitch your topic with ease and precision using this RPA Implementation Process For In Automotive Industry Portrait Pdf. This layout presents information on Plan, Assess, Select Implementation Model, Implement. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide exhibits the RPA implementation process aimed at reducing repetitive tasks and improving workforce safety. It includes key steps such as plan, assess, select implementation model, and implement.
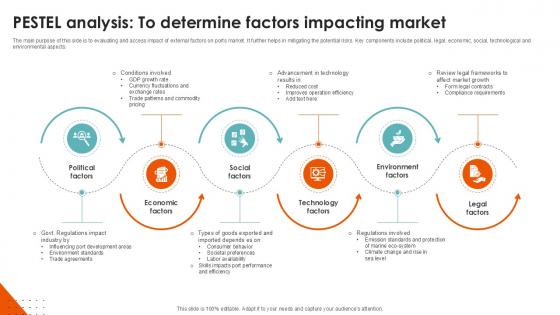
Pestel Analysis To Determine Port Terminal Industry Ppt Template
The main purpose of this side is to evaluating and access impact of external factors on ports market. It further helps in mitigating the potential risks. Key components include political, legal, economic, social, technological and environmental aspects.This Pestel Analysis To Determine Port Terminal Industry Ppt Template from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The main purpose of this side is to evaluating and access impact of external factors on ports market. It further helps in mitigating the potential risks. Key components include political, legal, economic, social, technological and environmental aspects.

Frozen Food Industry Supply Network Process Introduction PDF
This slide represents frozen food industry supply chain process illustrating input for supplier, suppliers, semi manufactured product, manufacturer, inputs for manufactures and finished product. Showcasing this set of slides titled frozen food industry supply network process introduction pdf. The topics addressed in these templates are frozen food industry supply network process. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Latest Industry Trends In Health And Safety One Pager Documents
This slide provides the details of existing industry trend in health and safety with innovative technology. Presenting you an exemplary Latest Industry Trends In Health And Safety One Pager Documents. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Latest Industry Trends In Health And Safety One Pager Documents brilliant piece now.

Sports Industry Action Plan For Ensuring Players Protection Template PDF
This slide covers information regarding the action plan prepared in order to ensure player protection in sports industry. Deliver an awe-inspiring pitch with this creative sports industry action plan for ensuring players protection template pdf bundle. Topics like decision making process, crisis investments, financial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
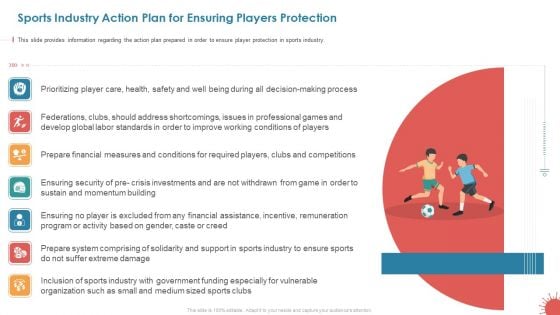
Sports Industry Action Plan For Ensuring Players Protection Clipart PDF
This slide provides information regarding the action plan prepared in order to ensure player protection in sports industry. Deliver an awe inspiring pitch with this creative sports industry action plan for ensuring players protection clipart pdf bundle. Topics like professional, shortcomings, standards can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
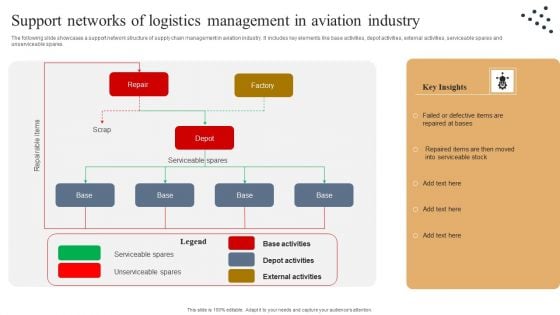
Support Networks Of Logistics Management In Aviation Industry Template PDF
The following slide showcases a support network structure of supply chain management in aviation industry. It includes key elements like base activities, depot activities, external activities, serviceable spares and unserviceable spares. Showcasing this set of slides titled Support Networks Of Logistics Management In Aviation Industry Template PDF. The topics addressed in these templates are Repair, Serviceable Stock, Aviation Industry. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
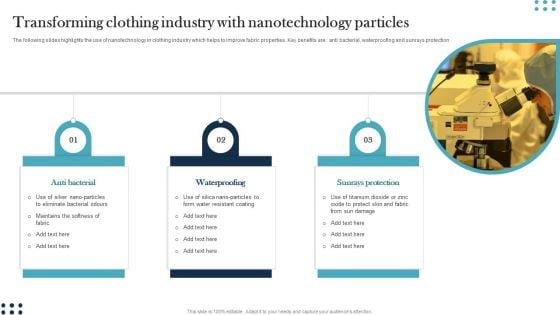
Transforming Clothing Industry With Nanotechnology Particles Infographics PDF
The following slides highlights the use of nanotechnology in clothing industry which helps to improve fabric properties. Key benefits are anti bacterial, waterproofing and sunrays protection. Showcasing this set of slides titled Transforming Clothing Industry With Nanotechnology Particles Infographics PDF. The topics addressed in these templates are Anti Bacterial, Waterproofing, Sunrays Protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































