Information Security Ppt
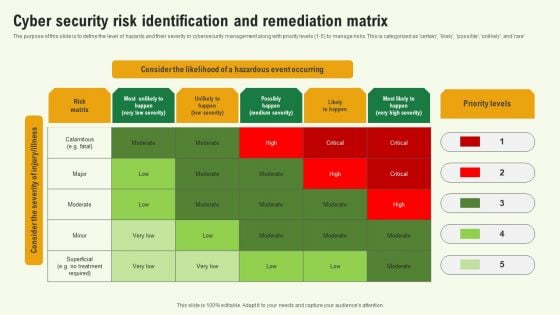
Cyber Security Risk Identification And Remediation Matrix Background PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management along with priority levels 1 to 5 to manage risks. This is categorized as certain, likely, possible, unlikel, and rare. Showcasing this set of slides titled Cyber Security Risk Identification And Remediation Matrix Background PDF. The topics addressed in these templates are Cyber Security Risk Identification, Remediation Matrix. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
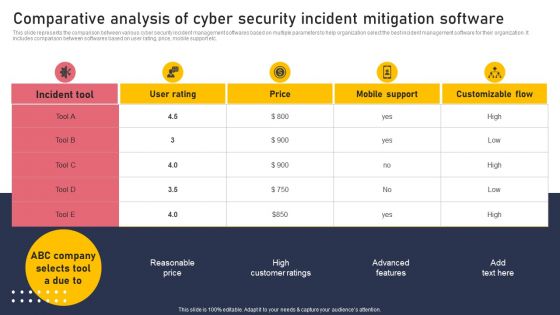
Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cyber Security Crisis Management Action Plan Timeline Topics PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Crisis Management Action Plan Timeline Topics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Crisis Management Action Plan Timeline Topics PDF
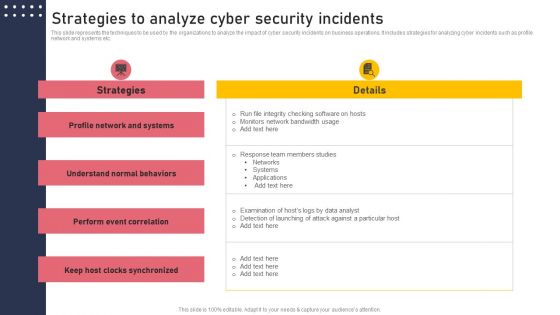
Strategies To Analyze Cyber Security Incidents Structure PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Find highly impressive Strategies To Analyze Cyber Security Incidents Structure PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Strategies To Analyze Cyber Security Incidents Structure PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
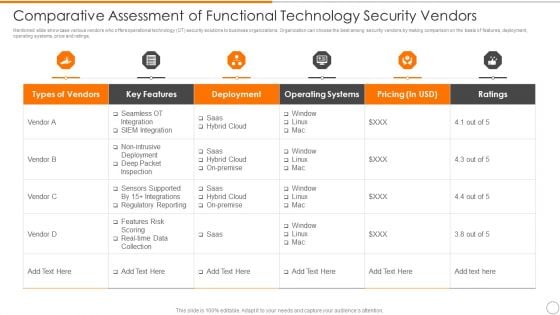
Comparative Assessment Of Functional Technology Security Vendors Professional PDF
Showcasing this set of slides titled comparative assessment of functional technology security vendors professional pdf. The topics addressed in these templates are deployment, operating systems, pricing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
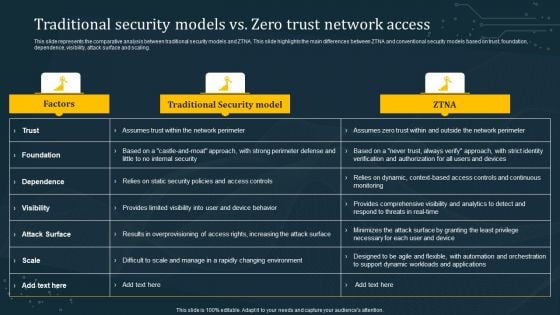
Traditional Security Models Vs Zero Trust Network Access Summary PDF
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. This modern and well-arranged Traditional Security Models Vs Zero Trust Network Access Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
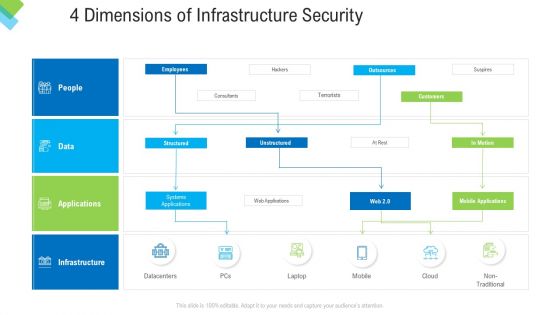
Construction Management Services 4 Dimensions Of Infrastructure Security Summary PDF
This is a construction management services 4 dimensions of infrastructure security summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Are you searching for a Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF from Slidegeeks today.
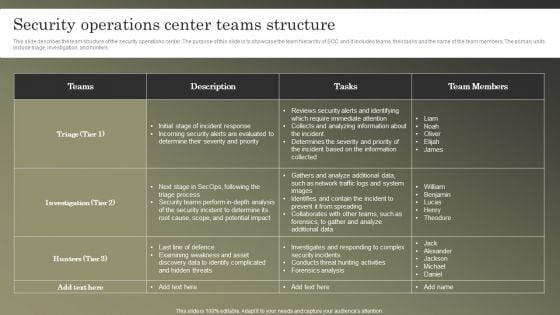
Cybersecurity Operations Cybersecops Security Operations Center Teams Structure Introduction PDF
This slide describes the team structure of the security operations center. The purpose of this slide is to showcase the team hierarchy of SOC and it includes teams, their tasks and the name of the team members. The primary units include triage, investigation, and hunters. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cybersecurity Operations Cybersecops Security Operations Center Teams Structure Introduction PDF can be your best option for delivering a presentation. Represent everything in detail using Cybersecurity Operations Cybersecops Security Operations Center Teams Structure Introduction PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
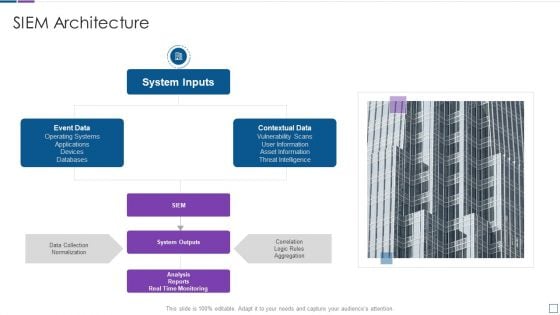
Real Time Assessment Of Security Threats SIEM Architecture Sample PDF
This is a real time assessment of security threats siem architecture sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system inputs, event data, contextual data, system outputs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For IT Security Hacker Background PDF
This is a Table Of Contents For IT Security Hacker Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Current Situation, Impact Of Hacking, Repairing Damages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
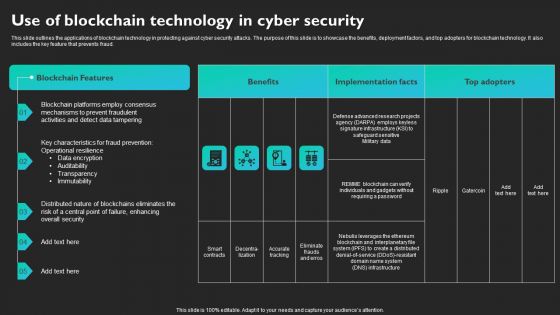
Use Of Blockchain Technology In Cyber Security Slides PDF
This slide outlines the applications of blockchain technology in protecting against cyber security attacks. The purpose of this slide is to showcase the benefits, deployment factors, and top adopters for blockchain technology. It also includes the key feature that prevents fraud. Find a pre-designed and impeccable Use Of Blockchain Technology In Cyber Security Slides PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
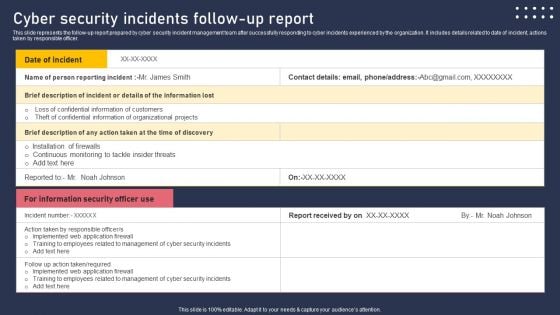
Cyber Security Incidents Follow Up Report Summary PDF
This slide represents the follow-up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. Take your projects to the next level with our ultimate collection of Cyber Security Incidents Follow Up Report Summary PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
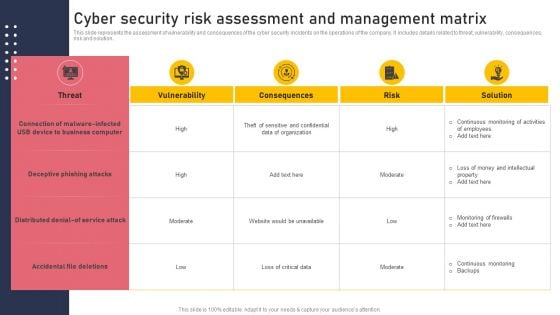
Cyber Security Risk Assessment And Management Matrix Inspiration PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Find a pre designed and impeccable Cyber Security Risk Assessment And Management Matrix Inspiration PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Organizational Network Security Awareness Staff Learning Timeline Download PDF
This is a organizational network security awareness staff learning timeline download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2018 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
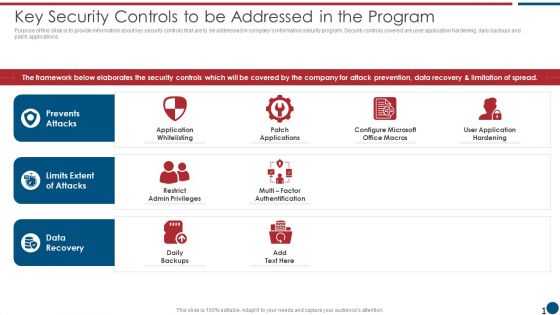
Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Key Security Controls To Be Addressed In The Program Structure PDF bundle. Topics like Prevents Attacks, Limits Extent, Data Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Financing Catalogue For Security Underwriting Agreement Timeline Ideas PDF
This is a financing catalogue for security underwriting agreement timeline ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2017 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
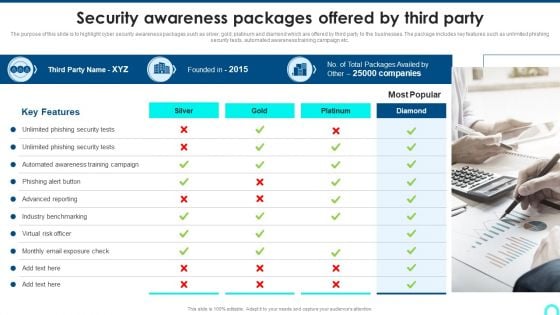
Security Awareness Packages Offered By Third Party Clipart PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. This is a Security Awareness Packages Offered By Third Party Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Unlimited Phishing, Automated Awareness, Industry Benchmarking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Measures And Ways To Mitigate Security Monitoring Challenges Formats PDF
Deliver an awe inspiring pitch with this creative measures and ways to mitigate security monitoring challenges formats pdf bundle. Topics like malware attacks, pnishing attacks, ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
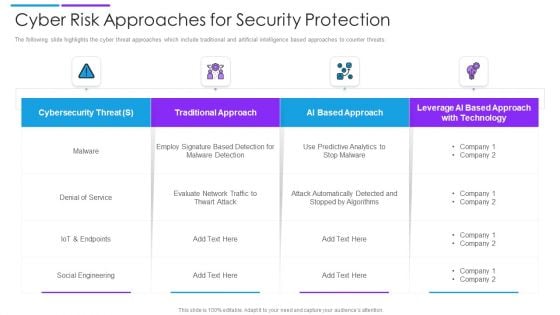
Cyber Risk Approaches For Security Protection Structure PDF
The following slide highlights the cyber threat approaches which include traditional and artificial intelligence based approaches to counter threats. Showcasing this set of slides titled cyber risk approaches for security protection structure pdf. The topics addressed in these templates are traditional approach, ai based approach, cybersecurity threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
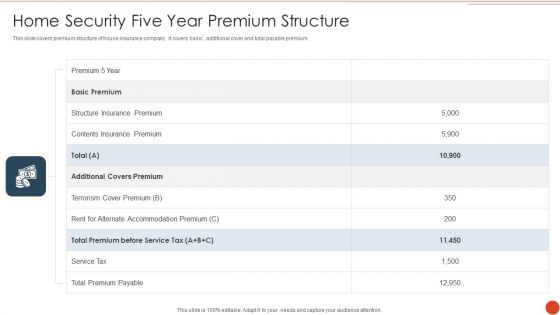
Home Security Five Year Premium Structure Graphics PDF
This slide covers premium structure of house insurance company . it covers basic , additional cover and total payable premium. Showcasing this set of slides titled Home Security Five Year Premium Structure Graphics PDF. The topics addressed in these templates are Additional Covers Premium, Service Tax, Total Premium Payable. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
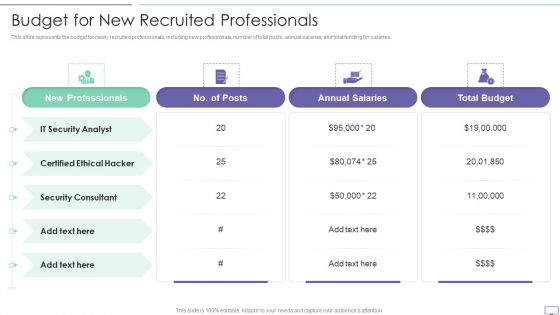
IT Security Hacker Budget For New Recruited Professionals Infographics PDF
This slide represents the budget for newly recruited professionals, including new professionals, number of total posts, annual salaries, and total funding for salaries.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Budget For New Recruited Professionals Infographics PDF. Use them to share invaluable insights on New Professionals, Certified Ethical, Annual Salaries and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
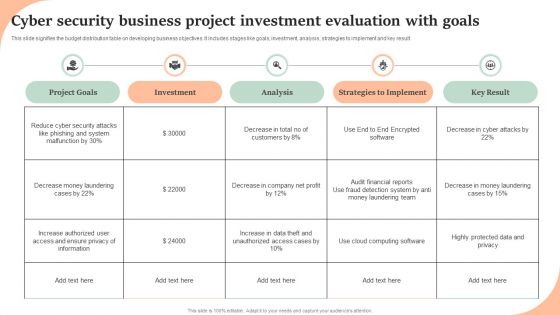
Cyber Security Business Project Investment Evaluation With Goals Structure PDF
This slide signifies the budget distribution table on developing business objectives. It includes stages like goals, investment, analysis, strategies to implement and key result. Showcasing this set of slides titled Cyber Security Business Project Investment Evaluation With Goals Structure PDF. The topics addressed in these templates are Project Goals, Investment, Analysis, Strategies To Implement, Key Result. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
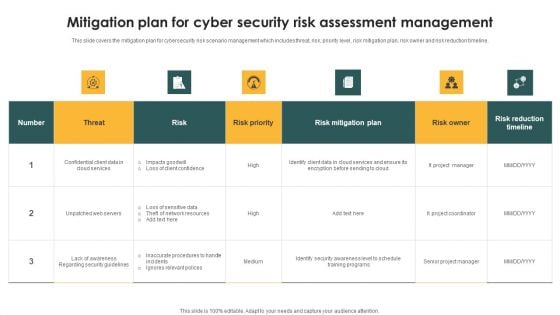
Mitigation Plan For Cyber Security Risk Assessment Management Sample PDF
This slide covers the mitigation plan for cybersecurity risk scenario management which includes threat, risk, priority level, risk mitigation plan, risk owner and risk reduction timeline. Showcasing this set of slides titled Mitigation Plan For Cyber Security Risk Assessment Management Sample PDF. The topics addressed in these templates are Threat, Risk, Risk Priority. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
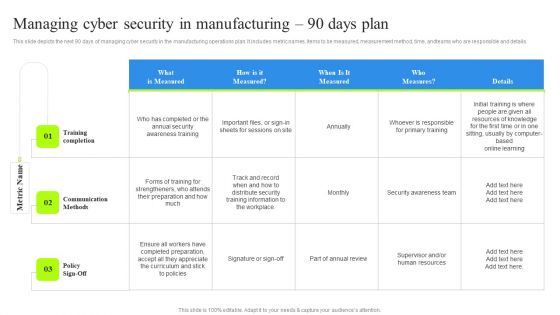
Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, andteams who are responsible and details. Slidegeeks has constructed Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
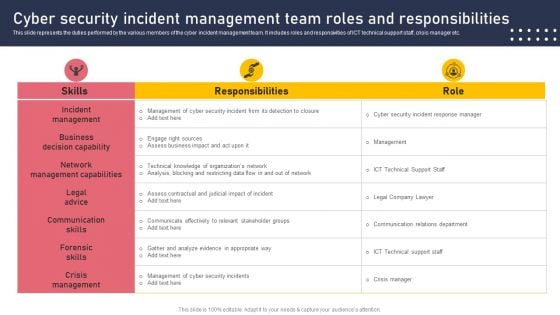
Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Are you searching for a Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cyber Security Incident Management Team Roles And Responsibilities Mockup PDF from Slidegeeks today.
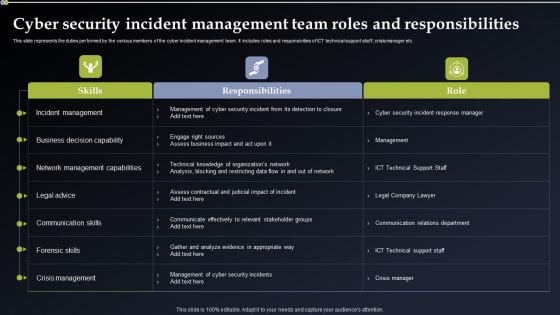
Cyber Security Incident Management Team Roles And Responsibilities Structure PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Security Incident Management Team Roles And Responsibilities Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Security Incident Management Team Roles And Responsibilities Structure PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
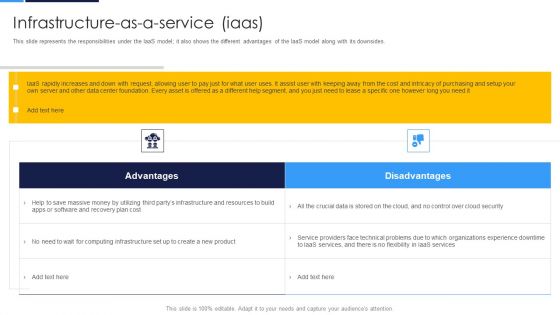
Cloud Security Assessment Infrastructure As A Ervice Iaas Diagrams PDF
This slide represents the responsibilities under the IaaS model it also shows the different advantages of the IaaS model along with its downsides.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Infrastructure As A Ervice Iaas Diagrams PDF bundle. Topics like Service Providers, Computing Infrastructure, Recovery Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Software Company Investor Funding Pitch Deck Quotes Background PDF
This Security Software Company Investor Funding Pitch Deck Quotes Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Threat Security Before And After Artificial Intelligence Formats PDF
This slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Showcasing this set of slides titled Threat Security Before And After Artificial Intelligence Formats PDF. The topics addressed in these templates are Malware, Distributed Denial Service, Social Engineering. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
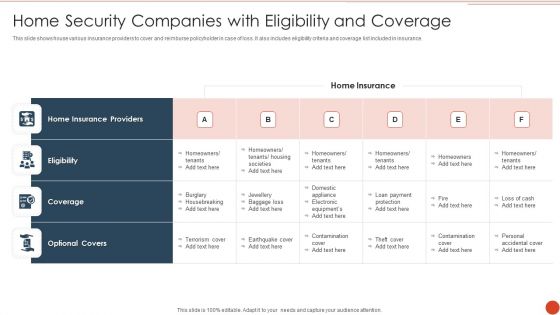
Home Security Companies With Eligibility And Coverage Infographics PDF
This slide shows house various insurance providers to cover and reimburse policyholder in case of loss. It also includes eligibility criteria and coverage list included in insurance. Showcasing this set of slides titled Home Security Companies With Eligibility And Coverage Infographics PDF. The topics addressed in these templates are Home Insurance Providers, Home Insurance, Loan Payment Protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Workplace Risk Mitigation Strategies For HR Security Portrait PDF
This slide highlights techniques for minimizing risk factors in the workplace. the purpose of this template is to employ effective strategies for ensuring workforce safety eventually enhancing overall productivity and efficiency. It also provides details regarding the status of performance along with insights. Showcasing this set of slides titled Workplace Risk Mitigation Strategies For HR Security Portrait PDF. The topics addressed in these templates are Risk Assessment Management, Safety Training And Education, Compliance Regulations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Need Of Implementing HR Security Programs At Workplace Pictures PDF
This slide highlights the need of importance of workplace safety in an organization. This template aims to provide details regarding workplace safety to increase productivity, reduce turnover rates, safe working conditions, reduction in risk factors, avoid loss of resources, reduction in expenses, foster employee wellbeing and follow legal guidelines, etc. Showcasing this set of slides titled Need Of Implementing HR Security Programs At Workplace Pictures PDF. The topics addressed in these templates are Productivity, Working Environment, Absenteeism. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
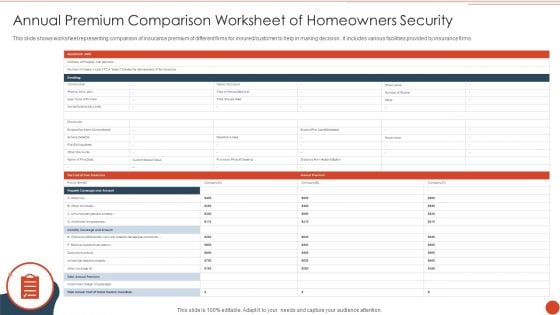
Annual Premium Comparison Worksheet Of Homeowners Security Diagrams PDF
This slide shows worksheet representing comparison of insurance premium of different firms for insured or customer to help in making decision . it includes various facilities provided by insurance firms. Showcasing this set of slides titled Annual Premium Comparison Worksheet Of Homeowners Security Diagrams PDF. The topics addressed in these templates are Purchase Price, Insurance, Medical Payments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
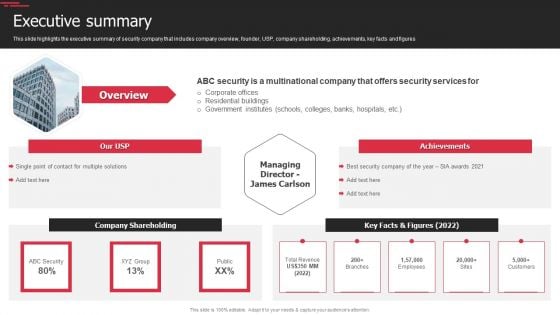
Security Agency Business Profile Executive Summary Graphics PDF
This slide highlights the executive summary of security company that includes company overview, founder, USP, company shareholding, achievements, key facts and figures. This is a Security Agency Business Profile Executive Summary Graphics PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Total Revenue, Employees, Customers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Electronic Voting System Voting System Standards Security Template PDF
This slide represents the security standard of the voting system that ensures the security of voting machines to prevent them from being tempered or manipulated through physical security, auditability, and internet connection.Presenting Electronic Voting System Voting System Standards Security Template PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Manipulated Tampered, Ensuring Security, Security Include. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Workforce Security Realization Coaching Plan Organization Compliance Metrics Introduction PDF
This slide covers the metrics that measure what you are doing with the awareness project, exactly how you will train and how. Such metrics are of particular importance for purposes of compliance and monitoring. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan organization compliance metrics introduction pdf. Use them to share invaluable insights on organization compliance metrics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
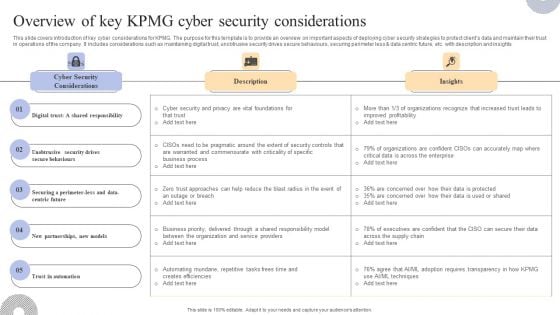
Overview Of Key KPMG Cyber Security Considerations Inspiration PDF
This slide covers an introduction to KPMG company ESG strategy to improve reporting to stakeholders. The purpose of this template is to provide overview on introducing ESG strategy, benefits along with reporting insights. It includes benefits such as helping organization assess and improve sustainable performance, establishing strong reputation and trust, attracting investors and customers, etc. Welcome to our selection of the Overview Of Key KPMG Cyber Security Considerations Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

Timeline Hacking Prevention Awareness Training For IT Security Brochure PDF
Presenting timeline hacking prevention awareness training for it security brochure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like timeline, 2016 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Implementing Security Management Strategy To Mitigate Risk Roadmap Diagrams PDF
Presenting implementing security management strategy to mitigate risk roadmap diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Implementing Security Management Strategy To Mitigate Risk Timeline Rules PDF
Presenting implementing security management strategy to mitigate risk timeline rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like timeline. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Developing Firm Security Strategy Plan Roadmap Introduction PDF
Presenting developing firm security strategy plan roadmap introduction pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Financing Catalogue For Security Underwriting Agreement Roadmap Slides PDF
Presenting financing catalogue for security underwriting agreement roadmap slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Project Security Administration IT Pictures PDF
Presenting table of contents for project security administration it pictures pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like project safety management, security centre implementation, budget assessment, dashboard analysis, project management team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Case Study 2 Banks Cyber Security Infrastructure Mockup PDF
Presenting case study 2 banks cyber security infrastructure mockup pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like case study 2 banks cyber security infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Prepare A Disaster Recovery Plan Demonstration PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a desktop security management prepare a disaster recovery plan demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, location, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
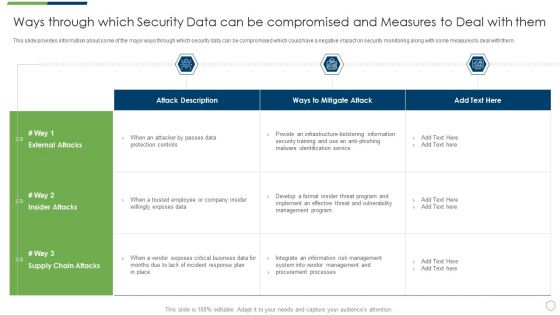
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Ways Through Which Security Data Themes PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach ways through which security data themes pdf bundle. Topics like ways through which security data can be compromised and measures to deal with them can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

3 Key Areas For Document Management Security Controls Ideas PDF
This slide presents the key areas of security control that enable companies to manage information access and permissions. It includes cryptography, best practice guidelines, compliance certifications and attestations. Persuade your audience using this 3 Key Areas For Document Management Security Controls Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cryptography, Practice Guidelines, Attestations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

PCI Certification For Increasing Security Of Online Transactions Designs PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Presenting this PowerPoint presentation, titled PCI Certification For Increasing Security Of Online Transactions Designs PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this PCI Certification For Increasing Security Of Online Transactions Designs PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable PCI Certification For Increasing Security Of Online Transactions Designs PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
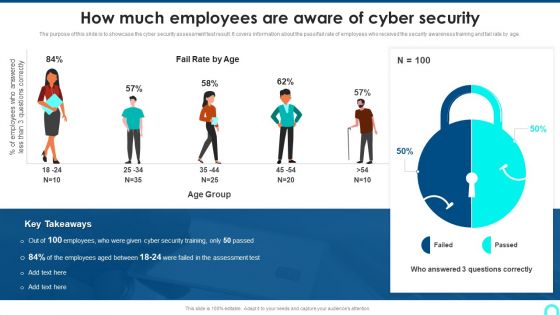
How Much Employees Are Aware Of Cyber Security Introduction PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age.This is a How Much Employees Are Aware Of Cyber Security Introduction PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Questions Correctly, Employees Answered, Employees Between. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
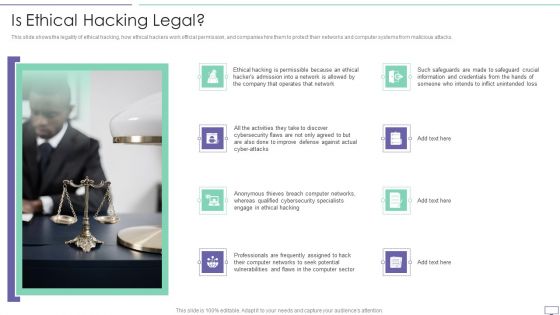
IT Security Hacker Is Ethical Hacking Legal Rules PDF
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks.Presenting IT Security Hacker Is Ethical Hacking Legal Rules PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Improve Defense, Anonymous Thieves, Qualified Cybersecurity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
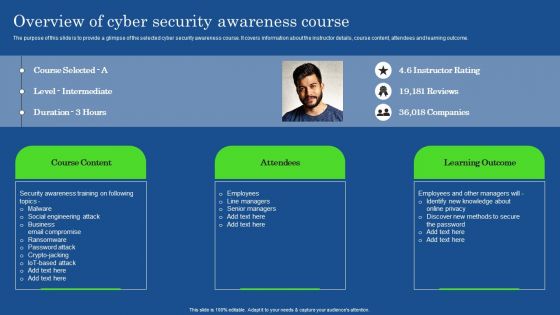
Overview Of Cyber Security Awareness Course Brochure PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Of Cyber Security Awareness Course Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Of Cyber Security Awareness Course Brochure PDF.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Challenges Slides PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring challenges slides pdf bundle. Topics like current security monitoring challenges the company is facing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
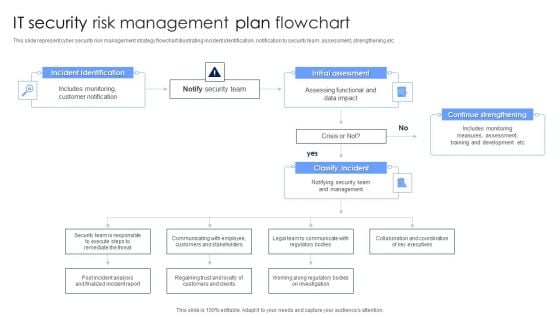
IT Security Risk Management Plan Flowchart Diagrams PDF
This slide represent cyber security risk management strategy flowchart illustrating incident identification, notification to security team, assessment, strengthening etc. Persuade your audience using this IT Security Risk Management Plan Flowchart Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Identification, Initial Assessment, Continue Strengthening. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Business Safety And Security Report Writing Icon Template PDF
Presenting Business Safety And Security Report Writing Icon Template PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Security Report, Business Safety. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cybersecurity Training Workshop On Security Breach Trends Icon Designs PDF
Presenting Cybersecurity Training Workshop On Security Breach Trends Icon Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cybersecurity Training, Workshop On Security, Breach Trends Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Change Analysis And Evaluation Icon Ideas PDF
Presenting Security Change Analysis And Evaluation Icon Ideas PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Security Change, Analysis And Evaluation Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
IT Security Management And Management Icon Introduction PDF
Persuade your audience using this IT Security Management And Management Icon Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including IT, Security, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































