Information Security Ppt
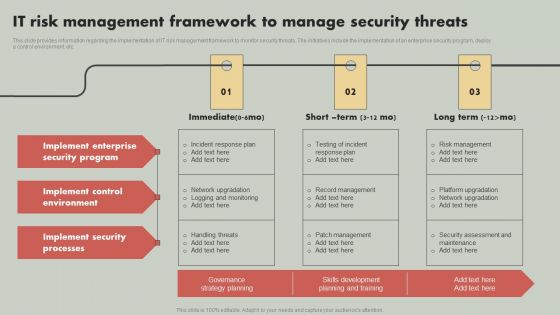
IT Reducing Costs And Management Tips IT Risk Management Framework To Manage Security Threats Mockup PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT Reducing Costs And Management Tips IT Risk Management Framework To Manage Security Threats Mockup PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT Reducing Costs And Management Tips IT Risk Management Framework To Manage Security Threats Mockup PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
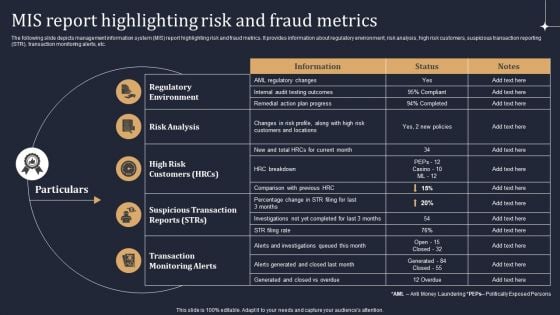
KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF
The following slide depicts management information system MIS report highlighting risk and fraud metrics. It provides information about regulatory environment, risk analysis, high risk customers, suspicious transaction reporting STR, transaction monitoring alerts, etc. Retrieve professionally designed KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
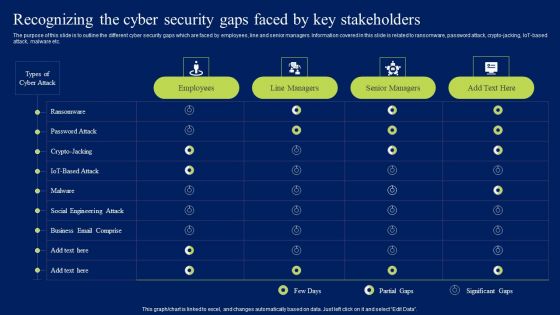
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Get a simple yet stunning designed Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
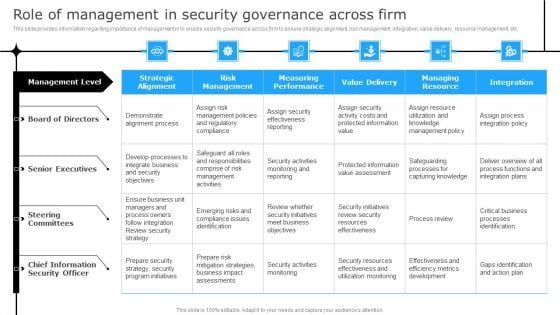
Successful Corporate Technique Enhancing Firms Performance Role Of Management In Security Governance Across Firm Background PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Get a simple yet stunning designed Successful Corporate Technique Enhancing Firms Performance Role Of Management In Security Governance Across Firm Background PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Successful Corporate Technique Enhancing Firms Performance Role Of Management In Security Governance Across Firm Background PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
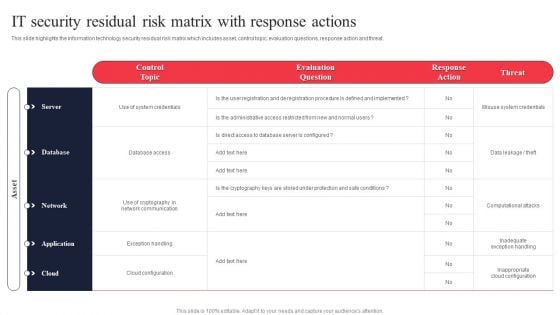
IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT System Risk Management Guide IT Security Residual Risk Matrix With Response Actions Slides PDF.

Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. This Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
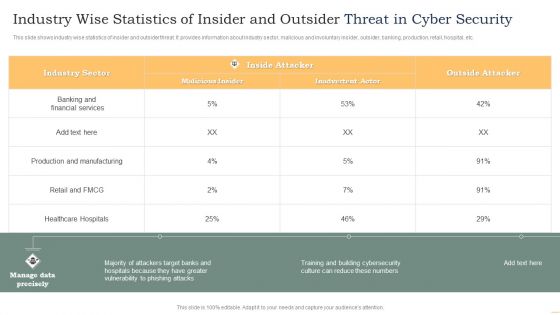
Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF
This slide shows industry wise statistics of insider and outsider threat. It provides information about industry sector, malicious and involuntary insider, outsider, banking, production, retail, hospital, etc. Showcasing this set of slides titled Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF. The topics addressed in these templates are Industry Sector, Malicious Insider, Inside Attacker. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
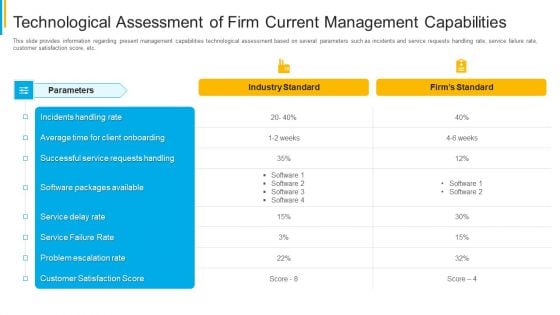
Project Security Administration IT Technological Assessment Of Firm Current Management Capabilities Professional PDF
This slide provides information regarding present management capabilities technological assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this project security administration it technological assessment of firm current management capabilities professional pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
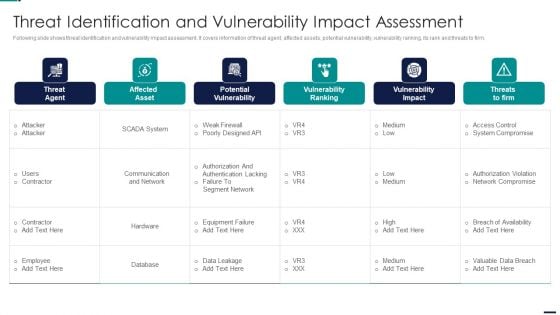
Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF. Use them to share invaluable insights on Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
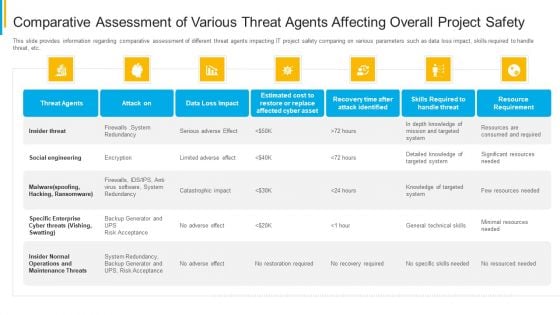
Project Security Administration IT Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Background PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this project security administration it comparative assessment of various threat agents affecting overall project safety background pdf. Use them to share invaluable insights on resource requirement, maintenance threats, cyber threats, social engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
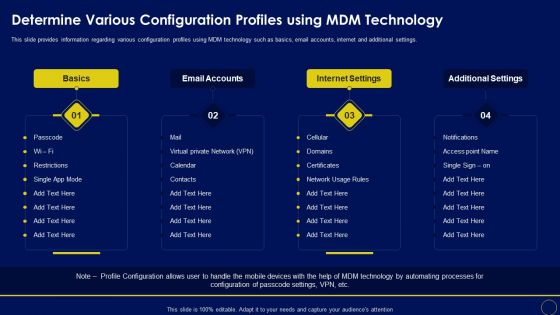
Determine Various Configuration Profiles Using Mdm Technology Business Mobile Device Security Ideas PDF
This slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Presenting this PowerPoint presentation, titled Determine Various Configuration Profiles Using Mdm Technology Business Mobile Device Security Ideas PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Determine Various Configuration Profiles Using Mdm Technology Business Mobile Device Security Ideas PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Determine Various Configuration Profiles Using Mdm Technology Business Mobile Device Security Ideas PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
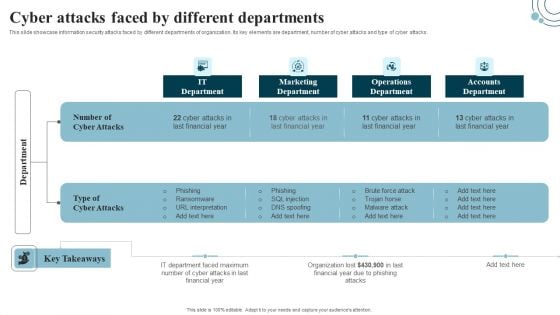
Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF
This slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Are you searching for a Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF from Slidegeeks today.
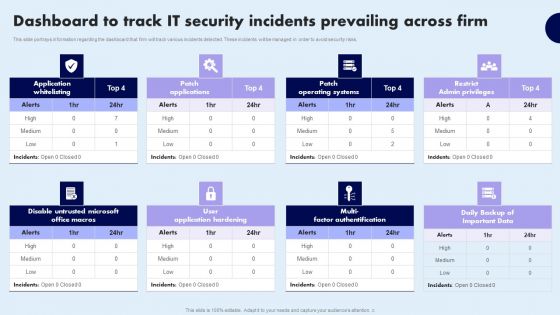
Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF today and make your presentation stand out from the rest

Project Security Administration IT Contingency Plan For Managing Threats To Ensure It Project Safety Mockup PDF
This slide provides information regarding contingency plan for managing threats to ensure IT project safety with aid of technical equipment ensuring contingency plans. Deliver an awe inspiring pitch with this creative project security administration it contingency plan for managing threats to ensure it project safety mockup pdf bundle. Topics like distributes systems, mainframe systems, wide area network, local area network, website can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
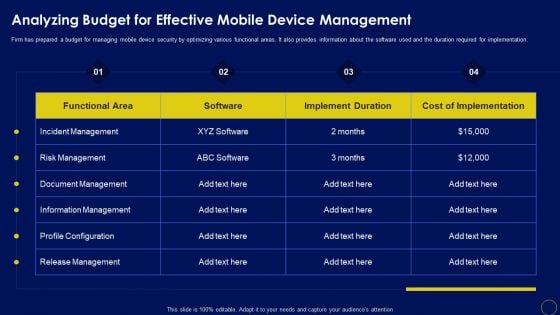
Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF
Firm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Explore a selection of the finest Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Analyzing Budget For Effective Mobile Device Management Business Mobile Device Security Clipart PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
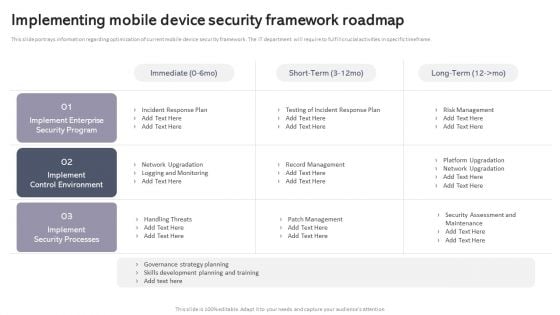
Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Explore a selection of the finest Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
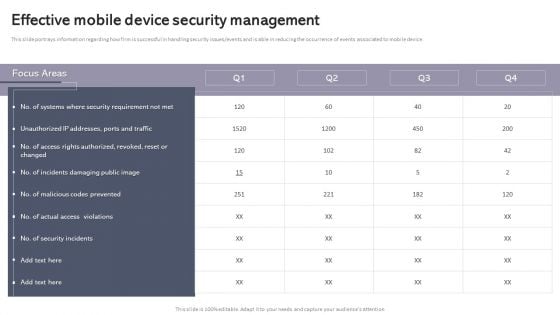
Workplace Portable Device Monitoring And Administration Effective Mobile Device Security Management Pictures PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. This Workplace Portable Device Monitoring And Administration Effective Mobile Device Security Management Pictures PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Workplace Portable Device Monitoring And Administration Effective Mobile Device Security Management Pictures PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
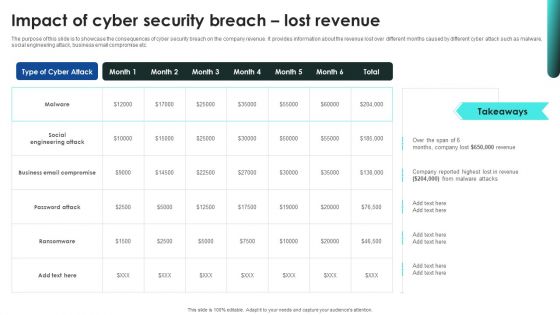
Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach Lost Revenue Template PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach Lost Revenue Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach Lost Revenue Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
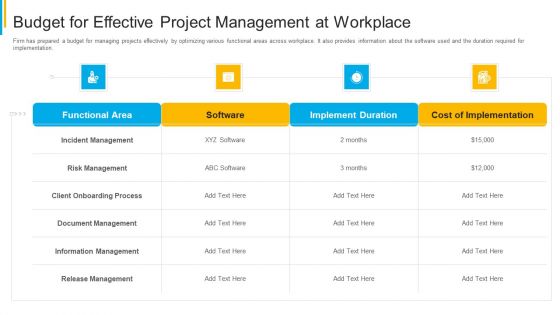
Project Security Administration IT Budget For Effective Project Management At Workplace Themes PDF
Firm has prepared a budget for managing projects effectively by optimizing various functional areas across workplace. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative project security administration it budget for effective project management at workplace themes pdf bundle. Topics like functional area, software, implement duration, cost of implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Project Security Administration IT Different Modes Of Coordination For Project Management Professional PDF
This slide provides information about different ways by which the firm can coordinate with its partners about project. The coordination can be of electronic mode like through email, etc. Deliver an awe inspiring pitch with this creative project security administration it different modes of coordination for project management professional pdf bundle. Topics like group mode of coordination, individual mode of coordination, electronic mode of coordination, impersonal mode of coordination can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
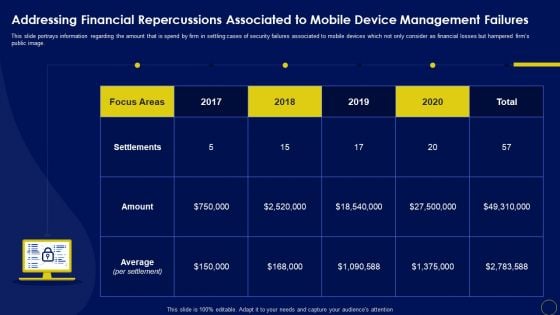
Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF
This slide portrays information regarding the amount that is spend by firm in settling cases of security failures associated to mobile devices which not only consider as financial losses but hampered firms public image. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Addressing Financial Repercussions Associated Business Mobile Device Security Management Elements PDF.
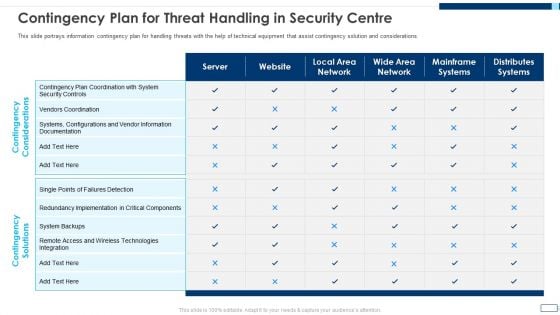
Evolving BI Infrastructure Contingency Plan For Threat Handling In Security Centre Pictures PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this evolving bi infrastructure contingency plan for threat handling in security centre pictures pdf. Use them to share invaluable insights on server, website, local area network, wide area network, mainframe systems, distributes systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
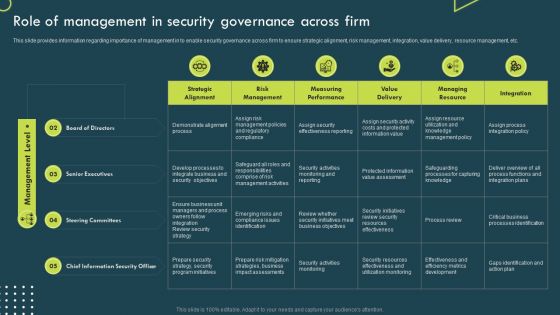
Strategic Corporate Planning To Attain Role Of Management In Security Governance Across Firm Guidelines PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Strategic Corporate Planning To Attain Role Of Management In Security Governance Across Firm Guidelines PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Strategic Corporate Planning To Attain Role Of Management In Security Governance Across Firm Guidelines PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
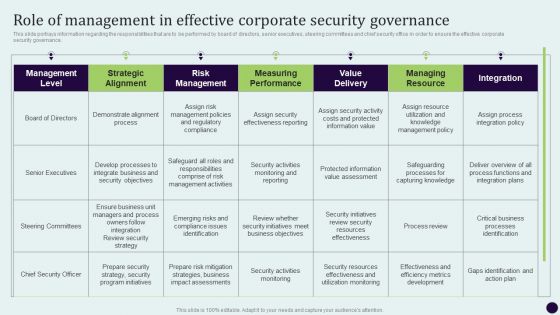
Critical Measures For Ensuring Role Of Management In Effective Corporate Security Themes PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief security office in order to ensure the effective corporate security governance. Slidegeeks is here to make your presentations a breeze with Critical Measures For Ensuring Role Of Management In Effective Corporate Security Themes PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Financing Catalogue For Security Underwriting Agreement Major Investment Banking Deals In Last Summary PDF
The slide provides the top five deals by profit amount of the company in last five years. It comprises, year, client name, deal type and brief information about all the five deals. Deliver an awe inspiring pitch with this creative financing catalogue for security underwriting agreement major investment banking deals in last summary pdf bundle. Topics like automobile, financials services, healthcare, construction can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Assets Security Management Strategy Addressing Risk Response Plan For Firms Demonstration PDF
This slide provides information regarding risk response plan for firms in terms of employee safety, development of cross functional team, ensuring liquidity and developing contingency plan, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Organizational Assets Security Management Strategy Addressing Risk Response Plan For Firms Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF
This slide showcases distinguish between bring your own device and choose your own device policies and programs for mobile devices. It also includes differentiation on basis such as benefits , challenges, etc. Pitch your topic with ease and precision using this Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF. This layout presents information on Basis, Benefits, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
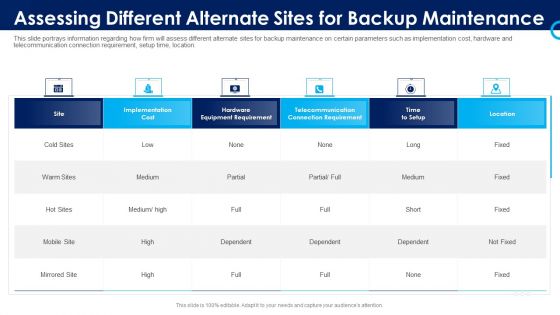
Organizational Security Solutions Assessing Different Alternate Sites For Backup Maintenance Infographics PDF
This slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location. Deliver and pitch your topic in the best possible manner with this organizational security solutions assessing different alternate sites for backup maintenance infographics pdf. Use them to share invaluable insights on implementation, cost, location, telecommunication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Functioning Centre Assessing Different Alternate Sites For Backup Maintenance Icons PDF
This slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location. Deliver and pitch your topic in the best possible manner with this security functioning centre assessing different alternate sites for backup maintenance icons pdf. Use them to share invaluable insights on telecommunication, location, equipment requirement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Process Integration Analysing Various Threats Faced By Firm Download PDF
This slide portrays information regarding the various threats that are faced by firm at present times with their cause of threat, risks associated to threats, occurrence of threats, and monetary loss to firm. Deliver an awe inspiring pitch with this creative security and process integration analysing various threats faced by firm download pdf bundle. Topics like threats, negligent, occurrence, compromised, malicious can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
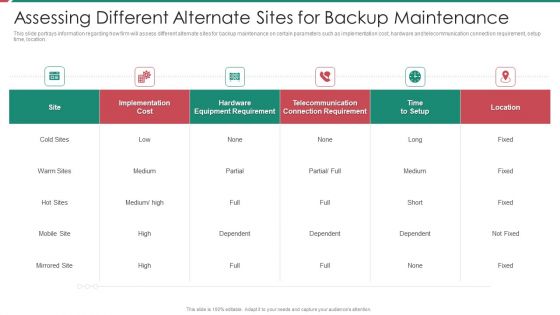
Security And Process Integration Assessing Different Alternate Sites For Backup Maintenance Formats PDF
This slide portrays information regarding how firm will assess different alternate sites for backup maintenance on certain parameters such as implementation cost, hardware and telecommunication connection requirement, setup time, location. Deliver and pitch your topic in the best possible manner with this security and process integration assessing different alternate sites for backup maintenance formats pdf. Use them to share invaluable insights on implementation, cost, location, telecommunication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
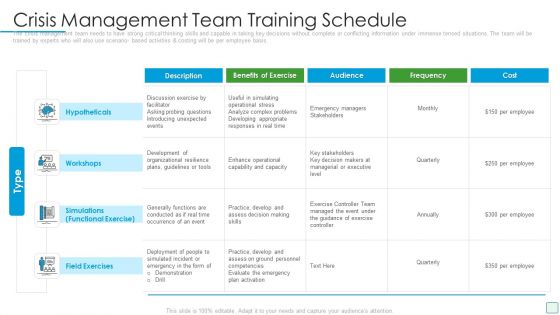
Developing Firm Security Strategy Plan Crisis Management Team Training Schedule Demonstration PDF
The crisis management team needs to have strong critical thinking skills and capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario- based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan crisis management team training schedule demonstration pdf. Use them to share invaluable insights on hypotheticals, workshops, simulations, field exercises and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Addressing Threat Management Team Training Schedule Inspiration PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing threat management team training schedule inspiration pdf. Use them to share invaluable insights on probing, unexpected, decision, skills, managerial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
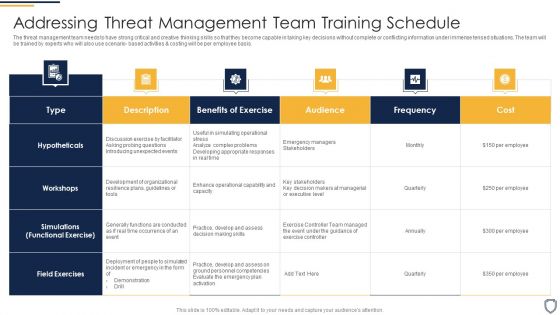
Corporate Security And Risk Management Addressing Threat Management Team Training Schedule Clipart PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario- based activities and costing will be per employee basis. Deliver an awe inspiring pitch with this creative corporate security and risk management addressing threat management team training schedule clipart pdf bundle. Topics like benefits of exercise, audience, frequency, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
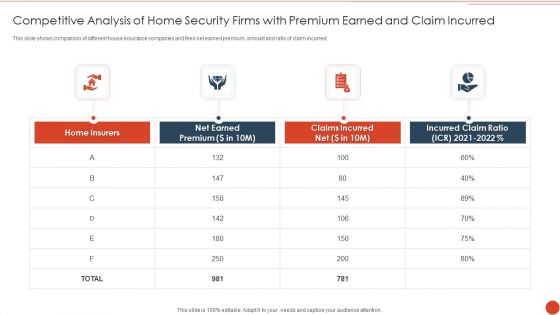
Competitive Analysis Of Home Security Firms With Premium Earned And Claim Incurred Microsoft PDF
This slide shows comparison of different house insurance companies and their net earned premium, amount and ratio of claim incurred. Pitch your topic with ease and precision using this Competitive Analysis Of Home Security Firms With Premium Earned And Claim Incurred Microsoft PDF. This layout presents information on Incurred Claim Ratio, Claims Incurred Net, Net Earned Premium. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

KYC Transaction Monitoring System Business Security Transaction Monitoring And Aml Training Plan Ideas PDF
The following slide represents training program for transaction monitoring and anti money laundering AML. It provides information about certification, assessment, compatibility, surveillance, operational efficiency, escalation, unusual transactions, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Transaction Monitoring And Aml Training Plan Ideas PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
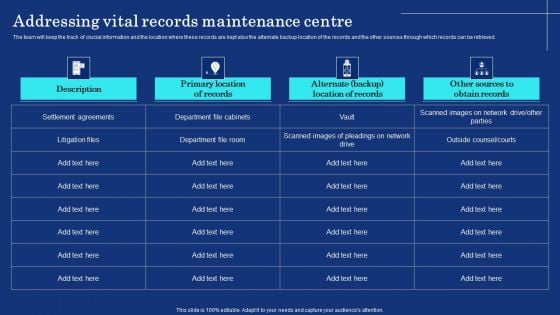
Organizational Assets Security Management Strategy Addressing Vital Records Maintenance Centre Rules PDF
The team will keep the track of crucial information and the location where these records are kept also the alternate backup location of the records and the other sources through which records can be retrieved. Want to ace your presentation in front of a live audience Our Organizational Assets Security Management Strategy Addressing Vital Records Maintenance Centre Rules PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Table Of Contents Critical Measures For Ensuring Business Security Formats PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Table Of Contents Critical Measures For Ensuring Business Security Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
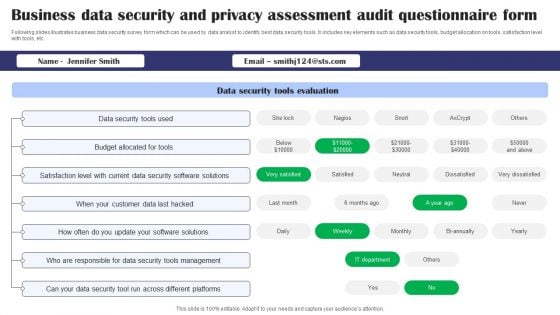
Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS
Following slides illustrates business data security survey form which can be used by data analyst to identify best data security tools. It includes key elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Showcasing this set of slides titled Business Data Security And Privacy Assessment Audit Questionnaire Form Survey SS. The topics addressed in these templates are Data Security Tools Evaluation, Data Security Tools Used, Budget Allocated For Tools, Data Security Software Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF
This slide showcases timeline to introduce transaction monitoring system. It provides information about scenario planning, threshold setting, deployment, project management office PMO, project planning, scenario identification, data source identification, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Timeline Implementing Transaction Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
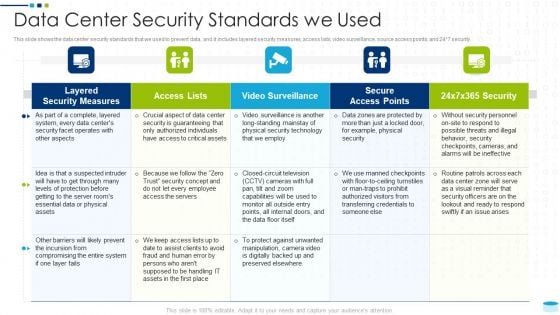
Data Center Infrastructure Management IT Data Center Security Standards We Used Professional PDF
This slide shows the data center security standards that we used to prevent data, and it includes layered security measures, access lists, video surveillance, source access points, and 24 7 security. Deliver and pitch your topic in the best possible manner with this data center infrastructure management it data center security standards we used professional pdf. Use them to share invaluable insights on layered security measures, access lists, video surveillance, secure access points, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present like a pro with IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
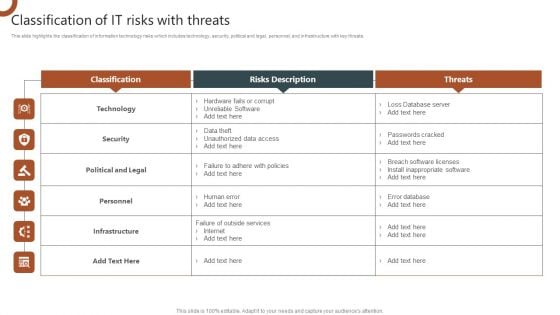
Organizations Risk Management And IT Security Classification Of IT Risks With Threats Structure PDF
This slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Organizations Risk Management And IT Security Classification Of IT Risks With Threats Structure PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.
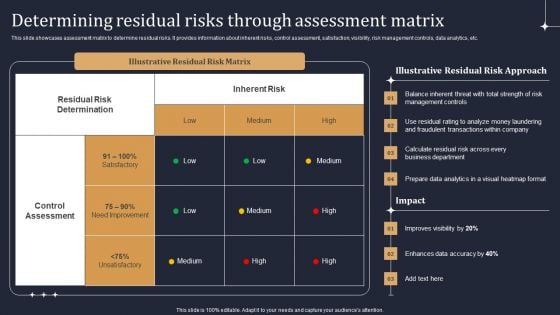
KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Explore a selection of the finest KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
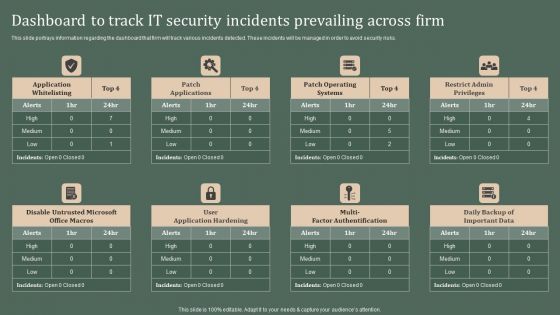
Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF
This slide showcases cryptocurrency transaction monitoring with alert status. It provides information about address, risk level, currencies, bitcoin, Ethereum, date added, deposits, case status, alerts, deposits, darknet, etc. This KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
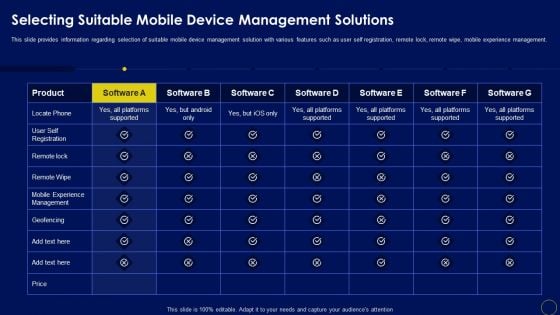
Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF
This slide provides information regarding selection of suitable mobile device management solution with various features such as user self registration, remote lock, remote wipe, mobile experience management. Find highly impressive Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.
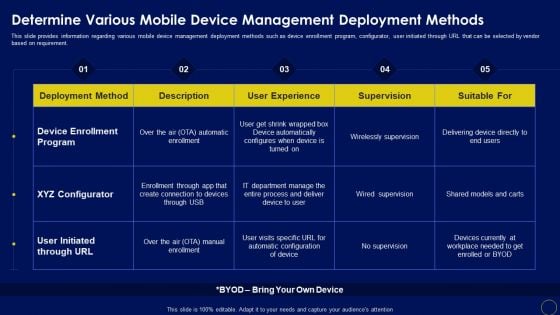
Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF
This slide provides information regarding various mobile device management deployment methods such as device enrollment program, configurator, user initiated through URL that can be selected by vendor based on requirement. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF.
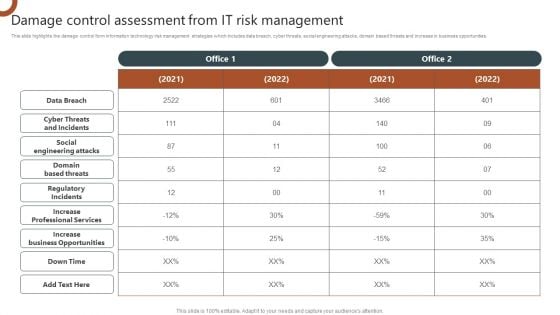
Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. This modern and well arranged Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver an awe inspiring pitch with this creative Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF bundle. Topics like Security And Compliance, Factor Authentication, Security Accounts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
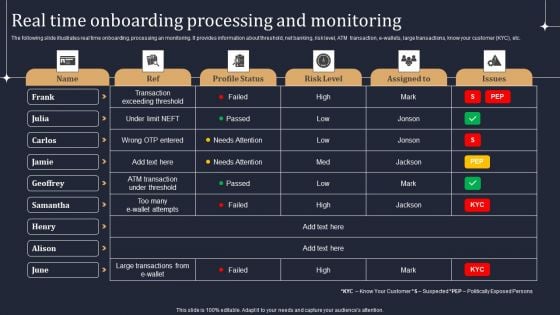
KYC Transaction Monitoring System Business Security Real Time Onboarding Processing And Monitoring Demonstration PDF
The following slide illustrates real time onboarding, processing an monitoring. It provides information about threshold, net banking, risk level, ATM transaction, e-wallets, large transactions, know your customer KYC, etc. Slidegeeks has constructed KYC Transaction Monitoring System Business Security Real Time Onboarding Processing And Monitoring Demonstration PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
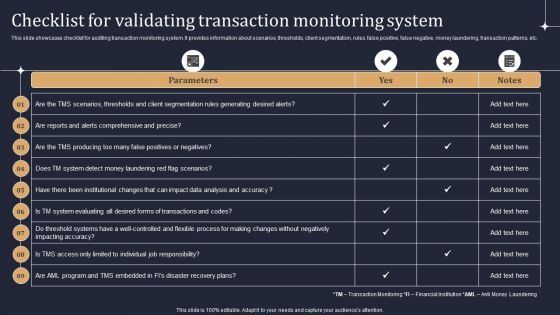
KYC Transaction Monitoring System Business Security Checklist For Validating Transaction Professional PDF
This slide showcases checklist for auditing transaction monitoring system. It provides information about scenarios, thresholds, client segmentation, rules, false positive, false negative, money laundering, transaction patterns, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created KYC Transaction Monitoring System Business Security Checklist For Validating Transaction Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
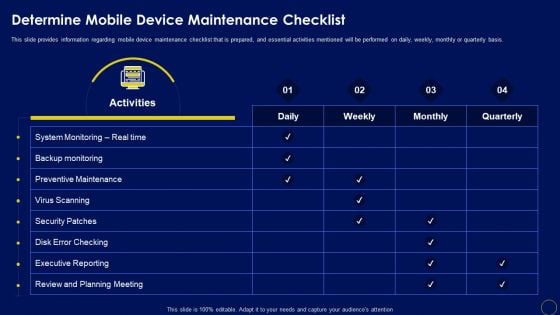
Determine Mobile Device Maintenance Checklist Business Mobile Device Security Management Professional PDF
This slide provides information regarding mobile device maintenance checklist that is prepared, and essential activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Retrieve professionally designed Determine Mobile Device Maintenance Checklist Business Mobile Device Security Management Professional PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Data Breach Prevention Recognition Impact Of Security Awareness Training Sample PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative data breach prevention recognition impact of security awareness training sample pdf bundle. Topics like security awareness program, security threats, network intrusion, inadvertent disclosure, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
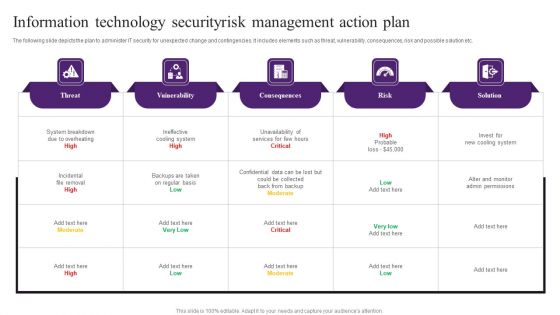
Information Technology Securityrisk Management Action Plan Themes PDF
The following slide depicts the plan to administer IT security for unexpected change and contingencies. It includes elements such as threat, vulnerability, consequences, risk and possible solution etc. Showcasing this set of slides titled Information Technology Securityrisk Management Action Plan Themes PDF. The topics addressed in these templates are Consequences, Vuinerability, System Breakdown. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
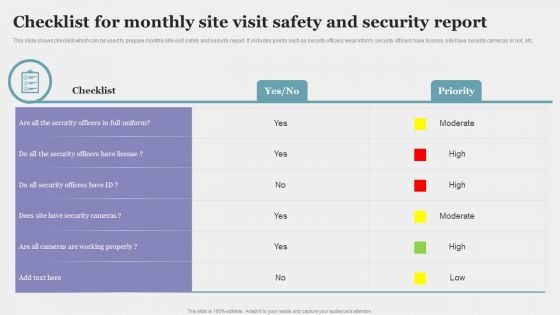
Checklist For Monthly Site Visit Safety And Security Report Guidelines PDF
This slide shows checklist which can be used to prepare monthly site visit safety and security report. It includes points such as security officers wear inform, security officers have license, site have security cameras or not, etc. Showcasing this set of slides titled Checklist For Monthly Site Visit Safety And Security Report Guidelines PDF. The topics addressed in these templates are Security Officers, Monthly Site, Visit Safety. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
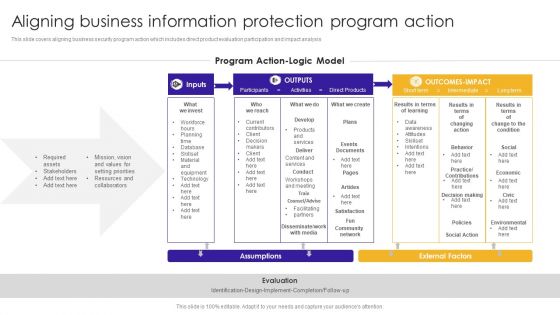
Aligning Business Information Protection Program Action Structure PDF
This slide covers aligning business security program action which includes direct product evaluation participation and impact analysis.Showcasing this set of slides titled Aligning Business Information Protection Program Action Structure PDF. The topics addressed in these templates are Setting Priorities, Assets Stakeholders, Decision Making. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Guidelines To Create An Advanced Security Management Plan Table Of Contents Pictures PDF
Deliver an awe inspiring pitch with this creative guidelines to create an advanced security management plan table of contents pictures pdf bundle. Topics like essential elements, security management challenges, security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































