Information Security Program

Optimization Of IoT Remote Monitoring Edge Ai Used To Reduce Cost And Bandwidth IoT SS V
This slide provides an overview of the edge AI used to enhance data security and improve monitoring. The slide further covers working and benefits that are it provide greater speed, and provides real-time insights. This modern and well-arranged Optimization Of IoT Remote Monitoring Edge Ai Used To Reduce Cost And Bandwidth IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide provides an overview of the edge AI used to enhance data security and improve monitoring. The slide further covers working and benefits that are it provide greater speed, and provides real-time insights.

Why Invest With Us Digital Payment Platform Pitch Deck
This slide mentions the various reasons why potential investors should be investing with the company. Key reasons strong product offering, ROI for investors, security and privacy, AI integrated technology, investment option, growing user base. Explore a selection of the finest Why Invest With Us Digital Payment Platform Pitch Deck here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Why Invest With Us Digital Payment Platform Pitch Deck to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide mentions the various reasons why potential investors should be investing with the company. Key reasons strong product offering, ROI for investors, security and privacy, AI integrated technology, investment option, growing user base.
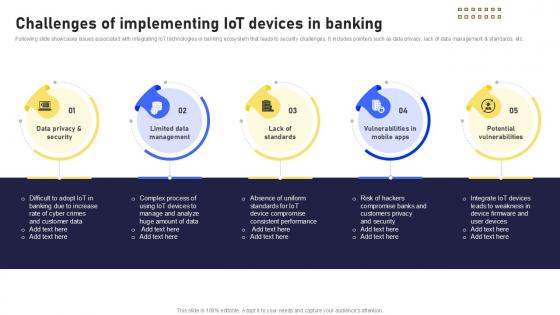
Challenges Of Implementing Banking Future With IoT Ppt Powerpoint IoT SS V
Following slide showcases issues associated with integrating IoT technologies in banking ecosystem that leads to security challenges. It includes pointers such as data privacy, lack of data management and standards, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Challenges Of Implementing Banking Future With IoT Ppt Powerpoint IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Following slide showcases issues associated with integrating IoT technologies in banking ecosystem that leads to security challenges. It includes pointers such as data privacy, lack of data management and standards, etc.

Business Analysis Ability Mapping Model With Techniques Sample Pdf
This slide shows the techniques for mapping business analysis competencies. The purpose of this slides to enhance usability and scalability .It includes various methods of business task under cyber security , data analytics, scrum,etc. Showcasing this set of slides titled Business Analysis Ability Mapping Model With Techniques Sample Pdf The topics addressed in these templates are Business Competency, Proficiency Scale, Specialized Areas All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows the techniques for mapping business analysis competencies. The purpose of this slides to enhance usability and scalability .It includes various methods of business task under cyber security , data analytics, scrum,etc.
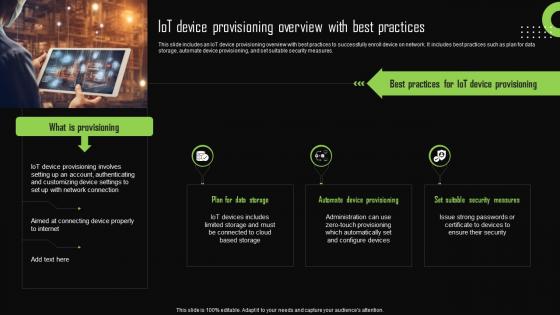
Iot Device Provisioning Overview With Best Practices Iot Device Management Sample Pdf
This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures. Do you know about Slidesgeeks Iot Device Provisioning Overview With Best Practices Iot Device Management Sample Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures.
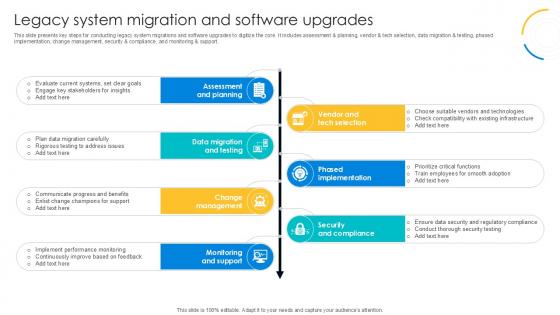
Legacy System Migration And Software Digital Transformation Journey PPT PowerPoint DT SS V
This slide presents key steps for conducting legacy system migrations and software upgrades to digitize the core. It includes assessment and planning, vendor and tech selection, data migration and testing, phased implementation, change management, security and compliance, and monitoring and support. Do you know about Slidesgeeks Vendor And Tech Selection, Phased Implementation, Security And Compliance These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide presents key steps for conducting legacy system migrations and software upgrades to digitize the core. It includes assessment and planning, vendor and tech selection, data migration and testing, phased implementation, change management, security and compliance, and monitoring and support.
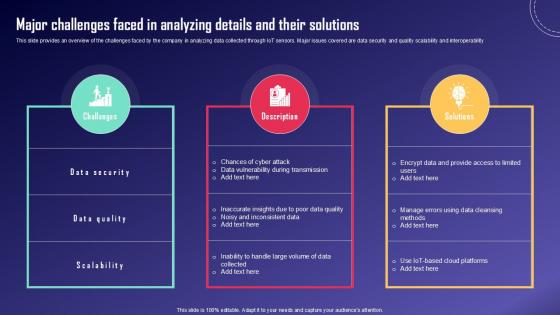
Major Challenges Faced In IoT Fleet Monitoring Ppt Presentation IoT SS V
This slide provides an overview of the challenges faced by the company in analyzing data collected through IoT sensors. Major issues covered are data security and quality scalability and interoperability. Get a simple yet stunning designed Major Challenges Faced In IoT Fleet Monitoring Ppt Presentation IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Major Challenges Faced In IoT Fleet Monitoring Ppt Presentation IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide provides an overview of the challenges faced by the company in analyzing data collected through IoT sensors. Major issues covered are data security and quality scalability and interoperability.
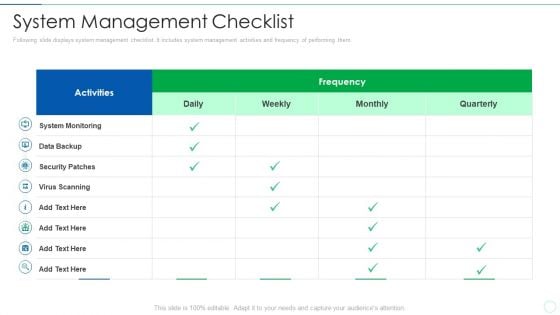
Effective IT Risk Management Process System Management Checklist Brochure PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver and pitch your topic in the best possible manner with this effective it risk management process system management checklist brochure pdf. Use them to share invaluable insights on security patches, data backup, system monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
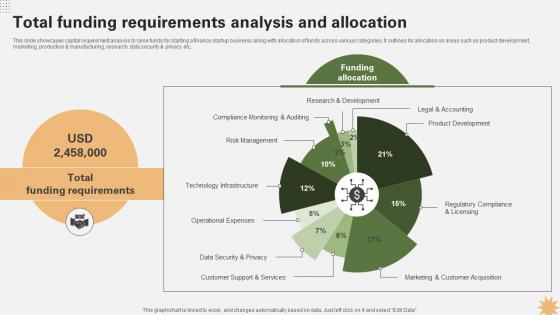
Total Funding Requirements Analysis And Allocation Strategy For Launching A Financial Strategy SS V
This slide showcases capital requirement analysis to raise funds for starting a finance startup business along with allocation of funds across various categories. It outlines its allocation on areas such as product development, marketing, production and manufacturing, research, data security and privacy etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Total Funding Requirements Analysis And Allocation Strategy For Launching A Financial Strategy SS V from Slidegeeks and deliver a wonderful presentation. This slide showcases capital requirement analysis to raise funds for starting a finance startup business along with allocation of funds across various categories. It outlines its allocation on areas such as product development, marketing, production and manufacturing, research, data security and privacy etc..
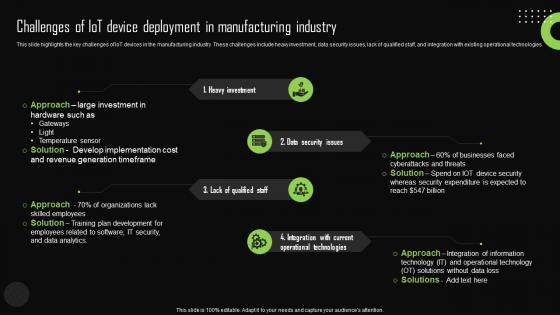
Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf
This slide highlights the key challenges of IoT devices in the manufacturing industry. These challenges include heavy investment, data security issues, lack of qualified staff, and integration with existing operational technologies. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf today and make your presentation stand out from the rest This slide highlights the key challenges of IoT devices in the manufacturing industry. These challenges include heavy investment, data security issues, lack of qualified staff, and integration with existing operational technologies.
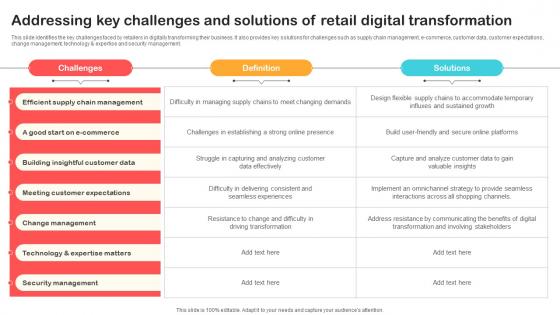
Addressing Key Challenges And Solutions Of Retail Digital Optimizing Retail Operations With Digital DT SS V
This slide identifies the key challenges faced by retailers in digitally transforming their business. It also provides key solutions for challenges such as supply chain management, e-commerce, customer data, customer expectations, change management, technology and expertise and security management.Boost your pitch with our creative Addressing Key Challenges And Solutions Of Retail Digital Optimizing Retail Operations With Digital DT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide identifies the key challenges faced by retailers in digitally transforming their business. It also provides key solutions for challenges such as supply chain management, e-commerce, customer data, customer expectations, change management, technology and expertise and security management.
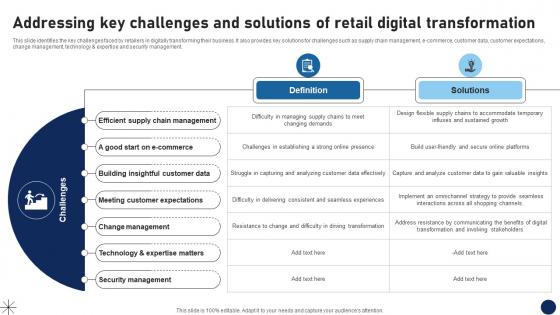
Addressing Key Challenges And Solutions Of Retail Digital Transformation DT SS V
This slide identifies the key challenges faced by retailers in digitally transforming their business. It also provides key solutions for challenges such as supply chain management, e-commerce, customer data, customer expectations, change management, technology and expertise and security management.Boost your pitch with our creative Addressing Key Challenges And Solutions Of Retail Digital Transformation DT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide identifies the key challenges faced by retailers in digitally transforming their business. It also provides key solutions for challenges such as supply chain management, e-commerce, customer data, customer expectations, change management, technology and expertise and security management.

A Comprehensive Approach To Factors To Consider While Choosing A Growth Marketing MKT SS V
This slide provide the major elements to consider while selecting a growth marketing tool. It incorporates factors such as functionality, integration, user friendliness, reporting and analysis, data privacy, security and cost. Want to ace your presentation in front of a live audience Our A Comprehensive Approach To Factors To Consider While Choosing A Growth Marketing MKT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide provide the major elements to consider while selecting a growth marketing tool. It incorporates factors such as functionality, integration, user friendliness, reporting and analysis, data privacy, security and cost.

Strategic Plan To Enhance IoT Revolutionizing Production IoT Ppt Example
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. Take your projects to the next level with our ultimate collection of Strategic Plan To Enhance IoT Revolutionizing Production IoT Ppt Example. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc.
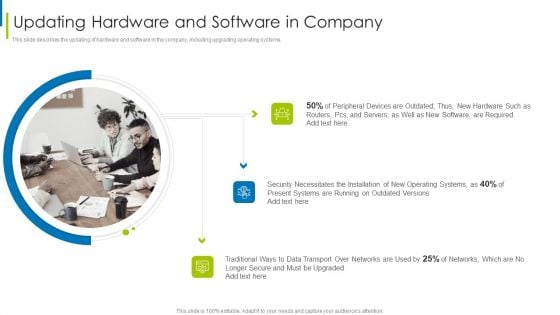
Cyber Terrorism Assault Updating Hardware And Software In Company Infographics PDF
This slide describes the updating of hardware and software in the company, including upgrading operating systems.Deliver an awe inspiring pitch with this creative cyber terrorism assault updating hardware and software in company infographics pdf bundle. Topics like peripheral devices, security necessitates, traditional ways to data transport can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Challenges Faced By Transportation Companies During Applications And Impact Infographics Pdf
This slide represents key challenges transportation companies face during AI adoption. It includes resistance to change, ethical and legal consideration, real-time data processing, safety security and scalability. Retrieve professionally designed Challenges Faced By Transportation Companies During Applications And Impact Infographics Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents key challenges transportation companies face during AI adoption. It includes resistance to change, ethical and legal consideration, real-time data processing, safety security and scalability.

Allocation Of Funds For Finance Startup Strategy For Launching A Financial Strategy SS V
This slide showcases allocation of funds on different operations for a finance startup business. It also includes values product development, marketing, production and manufacturing, research, data security and privacy etc. Boost your pitch with our creative Allocation Of Funds For Finance Startup Strategy For Launching A Financial Strategy SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases allocation of funds on different operations for a finance startup business. It also includes values product development, marketing, production and manufacturing, research, data security and privacy etc.
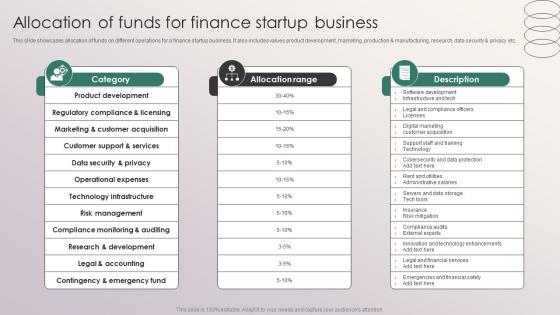
Allocation Of Funds For Finance Startup Business Penetrating Markets With Financial Strategy SS V
This slide showcases allocation of funds on different operations for a finance startup business. It also includes values product development, marketing, production and manufacturing, research, data security and privacy etc. Boost your pitch with our creative Allocation Of Funds For Finance Startup Business Penetrating Markets With Financial Strategy SS V. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases allocation of funds on different operations for a finance startup business. It also includes values product development, marketing, production and manufacturing, research, data security and privacy etc.
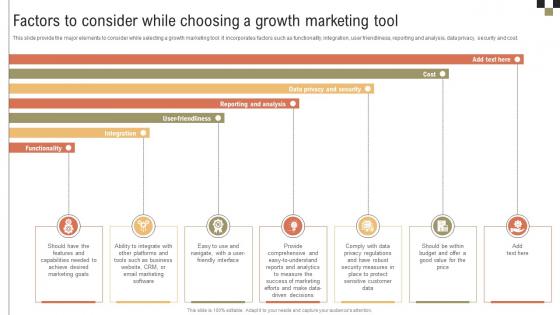
A Comprehensive Guide On Growth Factors To Consider While Choosing A Growth Marketing MKT SS V
This slide provide the major elements to consider while selecting a growth marketing tool. It incorporates factors such as functionality, integration, user friendliness, reporting and analysis, data privacy, security and cost. There are so many reasons you need a A Comprehensive Guide On Growth Factors To Consider While Choosing A Growth Marketing MKT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide provide the major elements to consider while selecting a growth marketing tool. It incorporates factors such as functionality, integration, user friendliness, reporting and analysis, data privacy, security and cost.
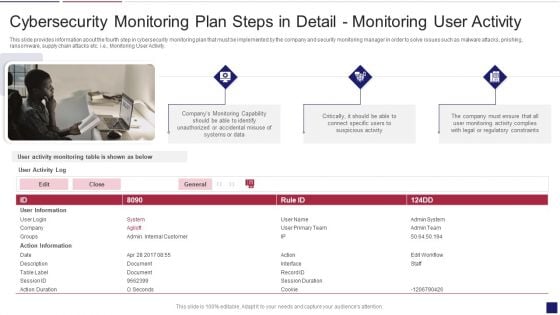
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Activity Structure PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring activity structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring user activity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
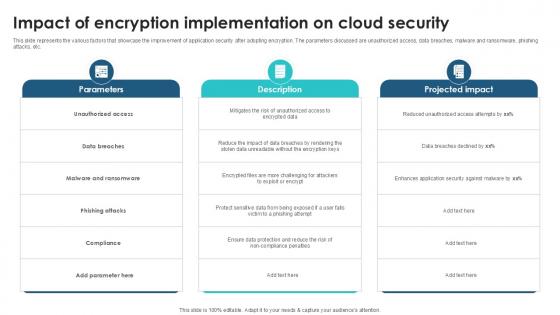
Impact Of Encryption Implementation Client Side Encryption PPT Presentation
This slide represents the various factors that showcase the improvement of application security after adopting encryption. The parameters discussed are unauthorized access, data breaches, malware and ransomware, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Impact Of Encryption Implementation Client Side Encryption PPT Presentation to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the various factors that showcase the improvement of application security after adopting encryption. The parameters discussed are unauthorized access, data breaches, malware and ransomware, phishing attacks, etc.
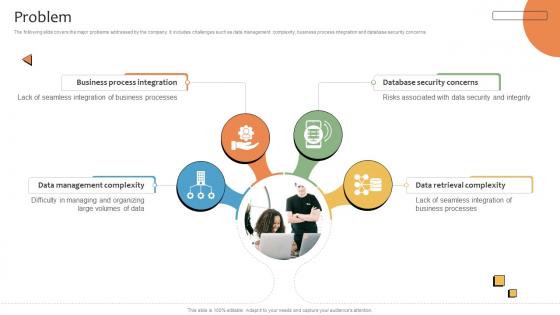
Problem CRMS Platform Business Model BMC SS V
The following slide covers the major problems addressed by the company. It includes challenges such as data management complexity, business process integration and database security concerns. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Problem CRMS Platform Business Model BMC SS V can be your best option for delivering a presentation. Represent everything in detail using Problem CRMS Platform Business Model BMC SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide covers the major problems addressed by the company. It includes challenges such as data management complexity, business process integration and database security concerns.
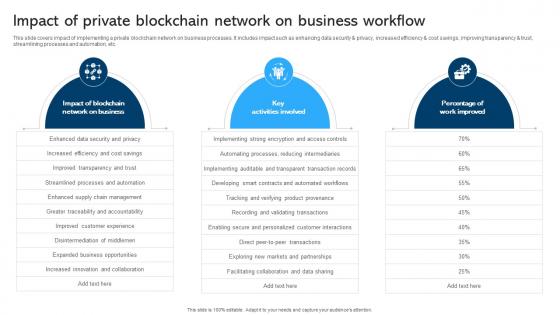
Comprehensive Manual For Blockchain Impact Of Private Blockchain Network BCT SS V
This slide covers impact of implementing a private blockchain network on business processes. It includes impact such as enhancing data security and privacy, increased efficiency and cost savings, improving transparency and trust, streamlining processes and automation, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comprehensive Manual For Blockchain Impact Of Private Blockchain Network BCT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide covers impact of implementing a private blockchain network on business processes. It includes impact such as enhancing data security and privacy, increased efficiency and cost savings, improving transparency and trust, streamlining processes and automation, etc.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Growth Restraints Of Product Analytics Market Driving Business Success Integrating Product
This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals Welcome to our selection of the Growth Restraints Of Product Analytics Market Driving Business Success Integrating Product. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals

Benefits Of Integrating Digital Transformation And Erp Erp And Digital Transformation For Maximizing DT SS V
This slide showcases the benefits of integrating digital transformation and enterprise resource planning system. It includes data security and compliance, accelerated innovation, employee collaboration, business insights, cost optimization, competitive advantage and sustainability.Get a simple yet stunning designed Benefits Of Integrating Digital Transformation And Erp Erp And Digital Transformation For Maximizing DT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Benefits Of Integrating Digital Transformation And Erp Erp And Digital Transformation For Maximizing DT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases the benefits of integrating digital transformation and enterprise resource planning system. It includes data security and compliance, accelerated innovation, employee collaboration, business insights, cost optimization, competitive advantage and sustainability.
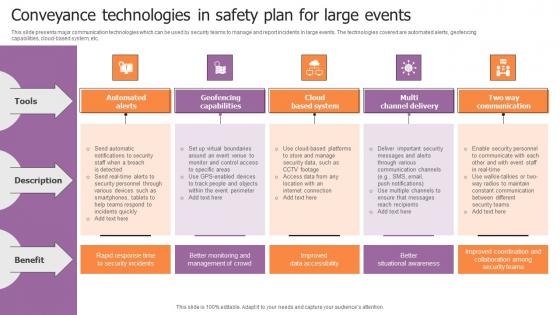
Conveyance Technologies In Safety Plan For Large Events Brochure Pdf
This slide presents major communication technologies which can be used by security teams to manage and report incidents in large events. The technologies covered are automated alerts, geofencing capabilities, cloud-based system, etc. Showcasing this set of slides titled Conveyance Technologies In Safety Plan For Large Events Brochure Pdf. The topics addressed in these templates are Automated Alerts, Geofencing Capabilities, Cloud Based System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents major communication technologies which can be used by security teams to manage and report incidents in large events. The technologies covered are automated alerts, geofencing capabilities, cloud-based system, etc.
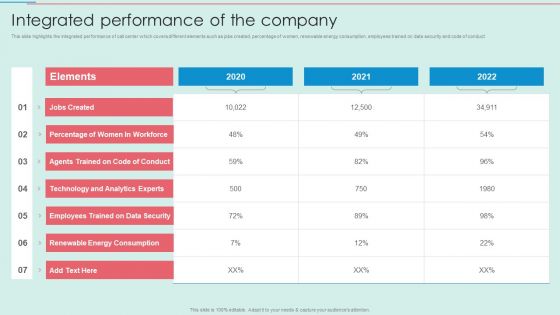
BPO Call Center Company Profile Integrated Performance Of The Company Portrait PDF
This slide highlights the integrated performance of call center which covers different elements such as jobs created, percentage of women, renewable energy consumption, employees trained on data security and code of conduct.Deliver an awe inspiring pitch with this creative BPO Call Center Company Profile Integrated Performance Of The Company Portrait PDF bundle. Topics like Percentage Women, Agents Trained, Technology Analytics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Checklist To Implement Digital Twin Digital Twins For Enhanced Industrial Infographics Pdf
This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team. Present like a pro with Checklist To Implement Digital Twin Digital Twins For Enhanced Industrial Infographics Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team.
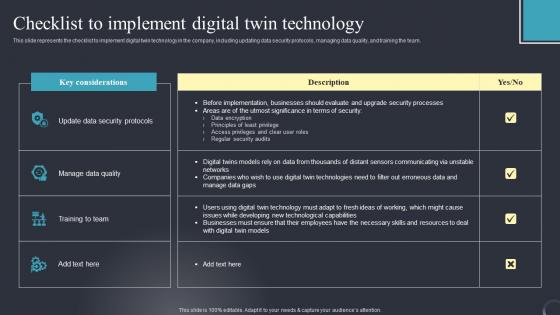
Checklist To Implement Digital Industrial Transformation Using Digital Twin Elements Pdf
This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Checklist To Implement Digital Industrial Transformation Using Digital Twin Elements Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team.
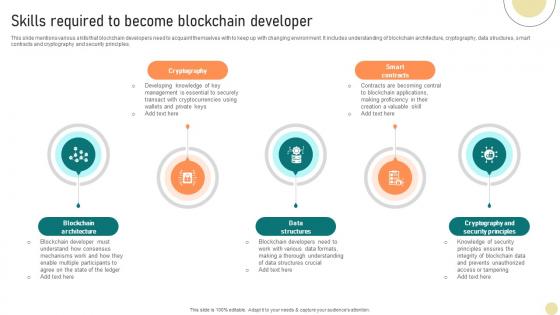
Visionary Guide To Blockchain Skills Required To Become Blockchain Developer BCT SS V
This slide mentions various skills that blockchain developers need to acquaint themselves with to keep up with changing environment. It includes understanding of blockchain architecture, cryptography, data structures, smart contracts and cryptography and security principles. Present like a pro with Visionary Guide To Blockchain Skills Required To Become Blockchain Developer BCT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide mentions various skills that blockchain developers need to acquaint themselves with to keep up with changing environment. It includes understanding of blockchain architecture, cryptography, data structures, smart contracts and cryptography and security principles.
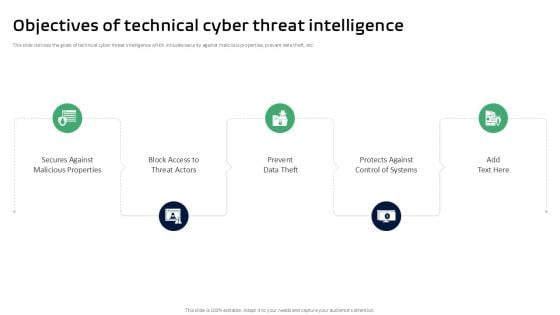
Objectives Of Technical Cyber Threat Intelligence Ppt Slides
This slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc. This Objectives Of Technical Cyber Threat Intelligence Ppt Slides is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Objectives Of Technical Cyber Threat Intelligence Ppt Slides features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc.
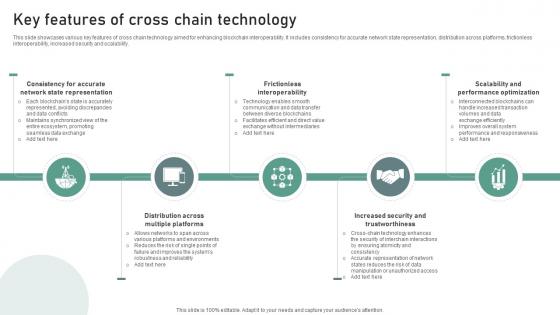
Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Slidegeeks has constructed Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.
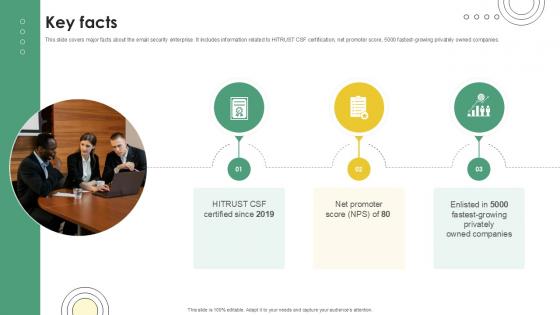
Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint
This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies. If you are looking for a format to display your unique thoughts, then the professionally designed Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies.
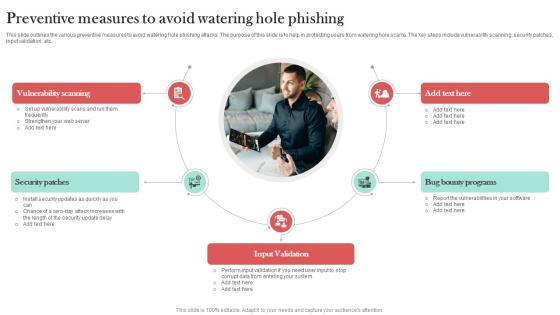
Preventive Measures To Avoid Watering Man In The Middle Phishing IT
This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc. Present like a pro with Preventive Measures To Avoid Watering Man In The Middle Phishing IT. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc.
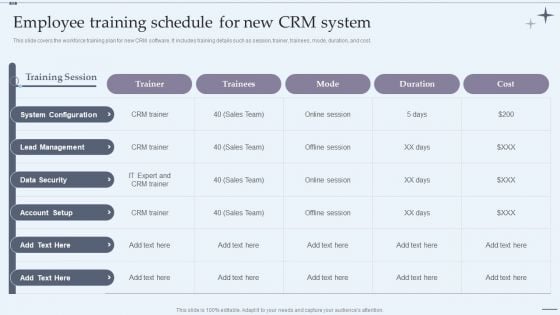
CRM System Implementation Stages Employee Training Schedule For New CRM System Mockup PDF
This slide covers the workforce training plan for new CRM software. It includes training details such as session, trainer, trainees, mode, duration, and cost. Deliver an awe inspiring pitch with this creative CRM System Implementation Stages Employee Training Schedule For New CRM System Mockup PDF bundle. Topics like System Configuration, Lead Management, Data Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
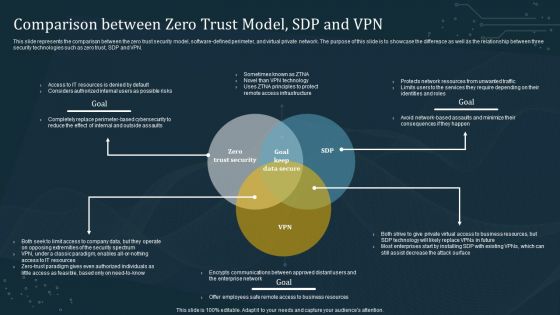
Comparison Between Zero Trust Model SDP And VPN Template PDF
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Zero Trust Model SDP And VPN Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Zero Trust Model SDP And VPN Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
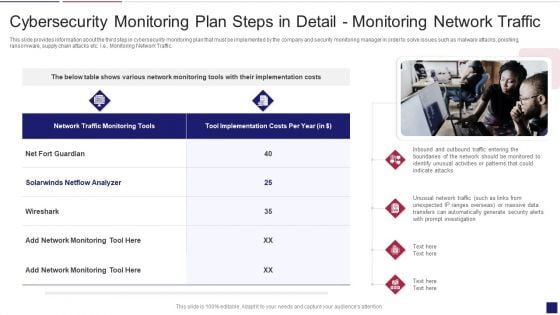
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Traffic Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring traffic sample pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring network traffic. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
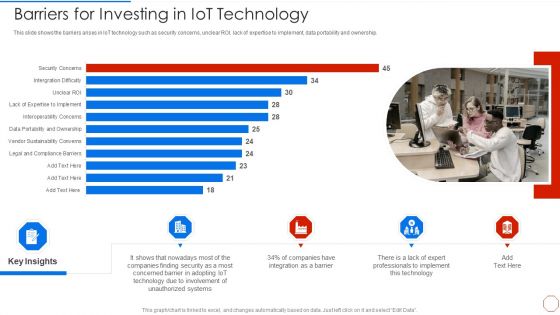
Minimizing Operational Cost Through Iot Virtual Twins Implementation Barriers For Investing In Iot Microsoft PDF
This slide shows the barriers arises in IoT technology such as security concerns, unclear ROI, lack of expertise to implement, data portability and ownership. Deliver and pitch your topic in the best possible manner with this minimizing operational cost through iot virtual twins implementation barriers for investing in iot microsoft pdf. Use them to share invaluable insights on involvement, systems, technology, implement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Global Cyber Terrorism Incidents On The Rise IT Implement Strong IT Guidelines Pictures PDF
This slide depicts the strong IT guidelines which should be implemented in the company, such as security software, backups, fraud detection. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it implement strong it guidelines pictures pdf bundle. Topics like implement strong it guidelines in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Upgrading Total Project Safety IT Determine Project Safety Management Team Structure Introduction PDF
This slide provides information regarding project safety management team generally comprise of senior management personnel that have authority and resources to accelerate IT projects incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a upgrading total project safety it determine project safety management team structure introduction pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like legal advisor, medical advisor, crisis management advisor, security manager, public affair advisor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
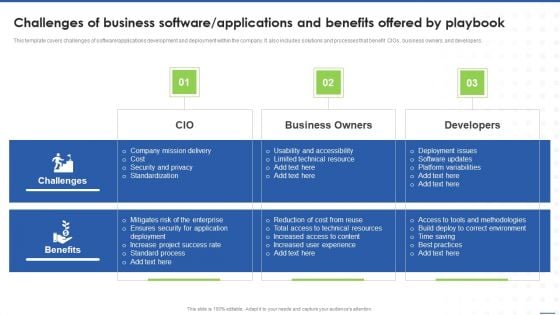
Challenges Of Business Software Applications And Benefits Offered By Playbook Mockup PDF
This template covers challenges of software applications development and deployment within the company. It also includes solutions and processes that benefit CIOs, business owners, and developers.Deliver an awe inspiring pitch with this creative Challenges Of Business Software Applications And Benefits Offered By Playbook Mockup PDF bundle. Topics like Company Mission, Security And Privacy, Limited Technical can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF
This slide depicts the challenges of adopting SOC as a service. The purpose of this slide is to highlight the main limitations of SOC as a service, including the onboarding process, enterprising data security, cost of log delivery, regulatory considerations, no dedicated IT security team, and limited customized options. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cybersecurity Operations Cybersecops Limitations Of SOC As A Service Model Template PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring System Formats PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring system formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
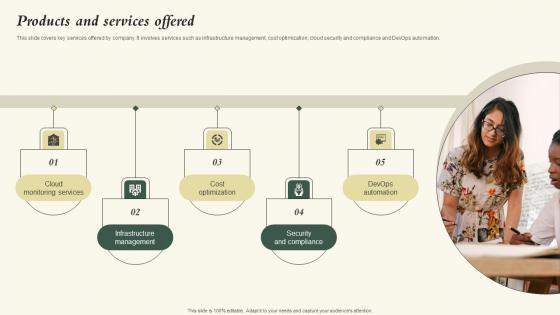
Products And Services Offered Nubity Capital Funding Pitch Deck Guidelines Pdf
This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Nubity Capital Funding Pitch Deck Guidelines Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation.
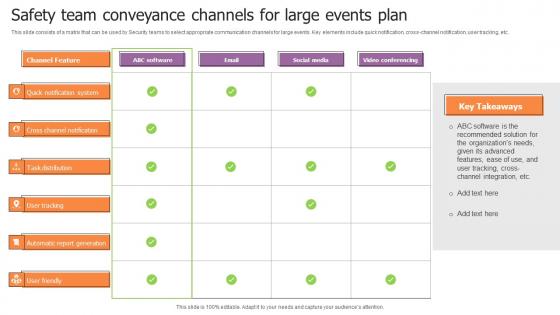
Safety Team Conveyance Channels For Large Events Plan Brochure Pdf
This slide consists of a matrix that can be used by Security teams to select appropriate communication channels for large events. Key elements include quick notification, cross-channel notification, user tracking, etc. Showcasing this set of slides titled Safety Team Conveyance Channels For Large Events Plan Brochure Pdf. The topics addressed in these templates are Channel Feature, Software, Email, Social Media. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide consists of a matrix that can be used by Security teams to select appropriate communication channels for large events. Key elements include quick notification, cross-channel notification, user tracking, etc.
RUP Methodology Management And Control Change Software Icons PDF
This slide represents how management and control change software is easy in the rational unified process methodology RUP also determines work and security domains.Deliver an awe inspiring pitch with this creative RUP Methodology Management And Control Change Software Icons PDF bundle. Topics like Unforeseen Effects On Applications, Management Is Critical, Domains Assuring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
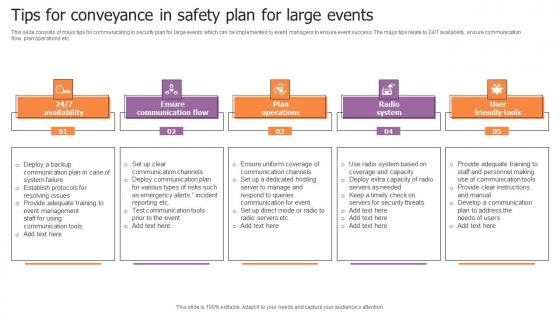
Tips For Conveyance In Safety Plan For Large Events Sample Pdf
This slide consists of major tips for communicating in security plan for large events which can be implemented by event managers to ensure event success. The major tips relate to 247 availability, ensure communication flow, plan operations etc. Showcasing this set of slides titled Tips For Conveyance In Safety Plan For Large Events Sample Pdf. The topics addressed in these templates are Ensure Communication Flow, Plan Operations, Radio System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide consists of major tips for communicating in security plan for large events which can be implemented by event managers to ensure event success. The major tips relate to 247 availability, ensure communication flow, plan operations etc.
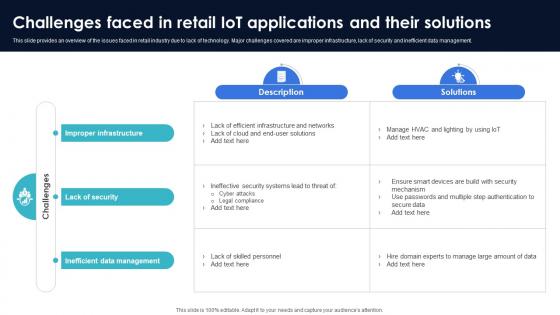
Optimization Of IoT Remote Monitoring Challenges Faced In Retail IoT Applications And Their IoT SS V
This slide provides an overview of the issues faced in retail industry due to lack of technology. Major challenges covered are improper infrastructure, lack of security and inefficient data management. Make sure to capture your audiences attention in your business displays with our gratis customizable Optimization Of IoT Remote Monitoring Challenges Faced In Retail IoT Applications And Their IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide provides an overview of the issues faced in retail industry due to lack of technology. Major challenges covered are improper infrastructure, lack of security and inefficient data management.
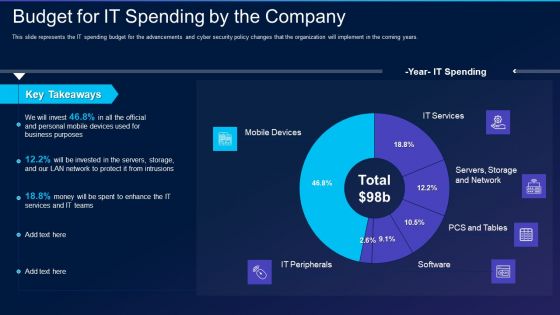
Cyber Exploitation IT Budget For IT Spending By The Company Professional PDF
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years. Deliver an awe inspiring pitch with this creative cyber exploitation it budget for it spending by the company professional pdf bundle. Topics like mobile devices, it peripherals, it services, servers, storage and network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Exit Strategy Paubox Capital Funding Pitch Deck Clipart Pdf
This slide covers the exit strategy of the email security software company. It includes various exit options such as merger and acquisition and initial public offering. Find highly impressive Exit Strategy Paubox Capital Funding Pitch Deck Clipart Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Exit Strategy Paubox Capital Funding Pitch Deck Clipart Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide covers the exit strategy of the email security software company. It includes various exit options such as merger and acquisition and initial public offering.

Strategic Influencer Marketing Plan To Create Exploring Investment Opportunities Ideas Pdf
The following slide depicts influencer promotion plan for security token offerings STO project to generate more leads. It includes elements such as objectives, budget, giveaways, tracking and monitoring performance, etc. Slidegeeks has constructed Strategic Influencer Marketing Plan To Create Exploring Investment Opportunities Ideas Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. The following slide depicts influencer promotion plan for security token offerings STO project to generate more leads. It includes elements such as objectives, budget, giveaways, tracking and monitoring performance, etc.
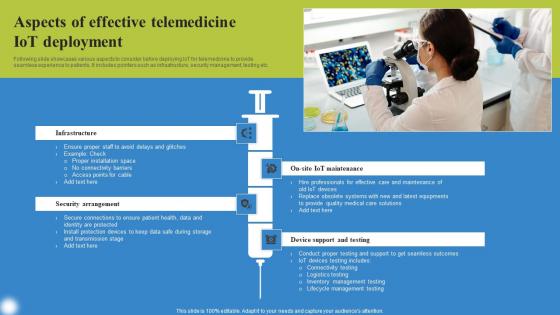
Aspects Of Effective Telemedicine Deploying IoT Solutions For Enhanced Healthcare Portrait Pdf
Following slide showcases various aspects to consider before deploying IoT for telemedicine to provide seamless experience to patients. It includes pointers such as infrastructure, security management, testing etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Aspects Of Effective Telemedicine Deploying IoT Solutions For Enhanced Healthcare Portrait Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. Following slide showcases various aspects to consider before deploying IoT for telemedicine to provide seamless experience to patients. It includes pointers such as infrastructure, security management, testing etc.
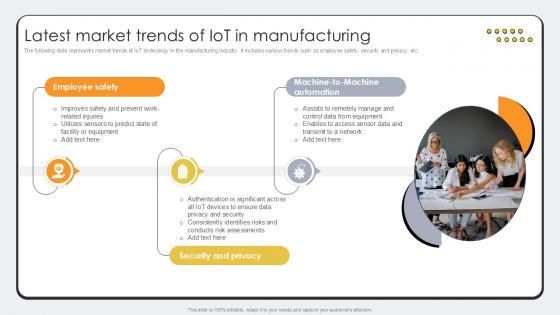
Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example
The following slide represents market trends of IoT technology in the manufacturing industry. It includes various trends such as employee safety, security and privacy, etc. Presenting this PowerPoint presentation, titled Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide represents market trends of IoT technology in the manufacturing industry. It includes various trends such as employee safety, security and privacy, etc.
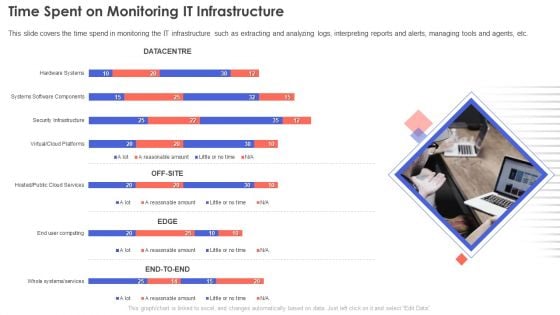
IT Infrastructure Management Time Spent On Monitoring IT Infrastructure Topics PDF
This slide covers the time spend in monitoring the IT infrastructure such as extracting and analyzing logs, interpreting reports and alerts, managing tools and agents, etc.Deliver and pitch your topic in the best possible manner with this IT Infrastructure Management Time Spent On Monitoring IT Infrastructure Topics PDF. Use them to share invaluable insights on Reasonable Amount, Little Time, Security Infrastructure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Career Certifications Benefits Of IT Certifications Technical Certifications And Business Individuals Themes PDF
This template covers IT certification Benefits for the employees such as expand individuals employment opportunities, gaining professional credibility, increase your job security and job stability etc. Deliver an awe inspiring pitch with this creative IT Career Certifications Benefits Of IT Certifications Technical Certifications And Business Individuals Themes PDF bundle. Topics like Expand Individuals, Employment Opportunities, Knowledge And Qualifications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF
This slide talks about the overview of the co-managed security operation center, including its objective and benefits. The purpose of this slide is to highlight the main benefits of co-managed SOC, covering enhancing threat detection and response, scalability, cost savings and increased security knowledge. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
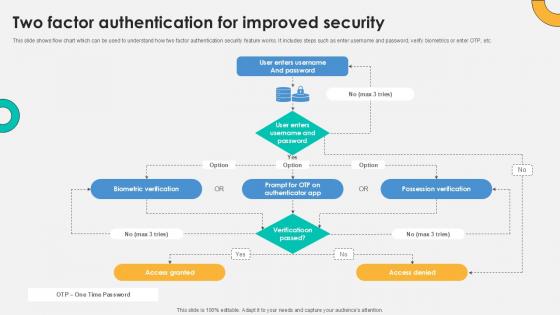
Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.

Incident Conveyance Plan Timeline For Safety Teams In Large Events Inspiration Pdf
The following slide presents an Incident communication plan timeline to be followed by security teams in case of breach or mishappening in large events. Key elements covered are incident communicated by attendee or staff, incident verified, action plan developed, etc. Showcasing this set of slides titled Incident Conveyance Plan Timeline For Safety Teams In Large Events Inspiration Pdf. The topics addressed in these templates are Operations Resume, Treatment Validation . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide presents an Incident communication plan timeline to be followed by security teams in case of breach or mishappening in large events. Key elements covered are incident communicated by attendee or staff, incident verified, action plan developed, etc.

Project Change Management Team Org Chart Digital Project Management Strategies
This slide represents details related to org chart of project change management team. It includes details related to steering committee, sponsor, project security officer, etc. Get a simple yet stunning designed Project Change Management Team Org Chart Digital Project Management Strategies. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Project Change Management Team Org Chart Digital Project Management Strategies can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents details related to org chart of project change management team. It includes details related to steering committee, sponsor, project security officer, etc.


 Continue with Email
Continue with Email

 Home
Home


































