Information Security Program
Implementing Information Security Continuity Ppt PowerPoint Presentation Gallery Files Cpb
Presenting this set of slides with name implementing information security continuity ppt powerpoint presentation gallery files cpb. This is an editable Powerpoint seven stages graphic that deals with topics like implementing information security continuity to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Principle Information Security Ppt PowerPoint Presentation Summary Tips Cpb
Presenting this set of slides with name principle information security ppt powerpoint presentation summary tips cpb. This is an editable Powerpoint seven stages graphic that deals with topics like principle information security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Frameworks Information Security Management Ppt PowerPoint Presentation Inspiration Themes Cpb
Presenting this set of slides with name frameworks information security management ppt powerpoint presentation inspiration themes cpb. This is an editable Powerpoint four stages graphic that deals with topics like frameworks information security management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Information Security Risk Assessment Ppt PowerPoint Presentation Professional Maker Cpb
Presenting this set of slides with name information security risk assessment ppt powerpoint presentation professional maker cpb. This is an editable Powerpoint five stages graphic that deals with topics like information security risk assessment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Information Security Strategy Framework Ppt PowerPoint Presentation Model Skills Cpb
Presenting this set of slides with name information security strategy framework ppt powerpoint presentation model skills cpb. This is an editable Powerpoint four stages graphic that deals with topics like information security strategy framework to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Information Security Governance Ppt PowerPoint Presentation Ideas Slides Cpb
Presenting this set of slides with name information security governance ppt powerpoint presentation ideas slides cpb. This is an editable Powerpoint three stages graphic that deals with topics like information security governance to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Information Security Cases Ppt PowerPoint Presentation Icon Smartart Cpb
Presenting this set of slides with name information security cases ppt powerpoint presentation icon smartart cpb. This is an editable Powerpoint five stages graphic that deals with topics like information security cases to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Key Management Information Security Ppt PowerPoint Presentation Show Picture Cpb
Presenting this set of slides with name key management information security ppt powerpoint presentation show picture cpb. This is an editable Powerpoint two stages graphic that deals with topics like key management information security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Information Security Awareness Ppt PowerPoint Presentation Infographics Sample Cpb Pdf
Presenting this set of slides with name information security awareness ppt powerpoint presentation infographics sample cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like information security awareness to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Communication Plan For Information Technology Asset Security Threats Pictures PDF
This slide consists of a communication plan that can be implemented by managers to safeguard information technology assets from cyber threats and create an effective response plan. Major elements covered are IT security assets, risk, threat, risk impact, etc. Showcasing this set of slides titled Communication Plan For Information Technology Asset Security Threats Pictures PDF. The topics addressed in these templates are ZZZZZZZZZZZZZZZZZZZZIT Servers, Network Systems, ModemZZZZZZZZZZZZZ. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
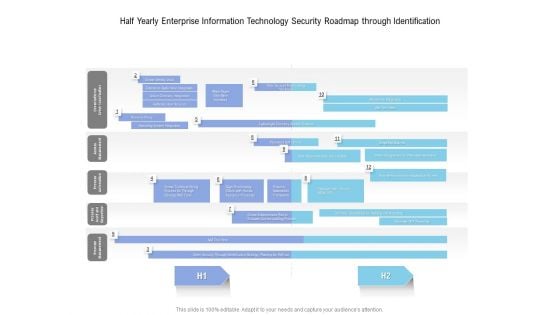
Half Yearly Enterprise Information Technology Security Roadmap Through Identification Summary
We present our half yearly enterprise information technology security roadmap through identification summary. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly enterprise information technology security roadmap through identification summary in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
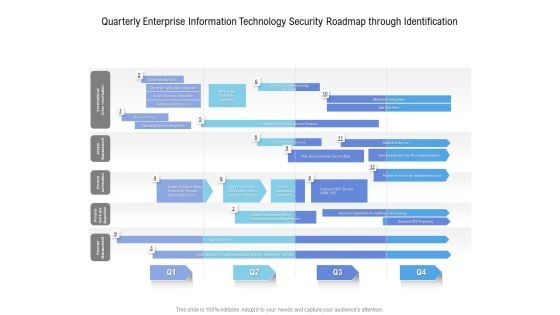
Quarterly Enterprise Information Technology Security Roadmap Through Identification Topics
We present our quarterly enterprise information technology security roadmap through identification topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly enterprise information technology security roadmap through identification topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
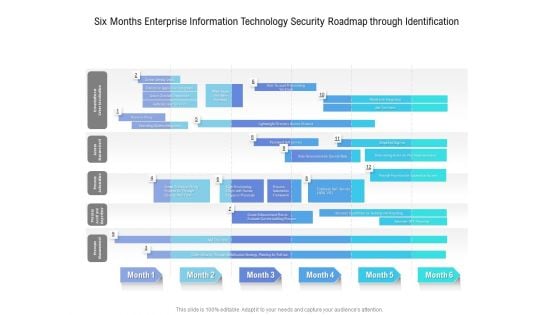
Six Months Enterprise Information Technology Security Roadmap Through Identification Infographics
We present our six months enterprise information technology security roadmap through identification infographics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months enterprise information technology security roadmap through identification infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
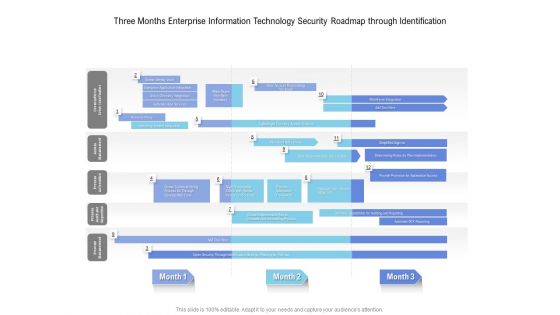
Three Months Enterprise Information Technology Security Roadmap Through Identification Introduction
We present our three months enterprise information technology security roadmap through identification introduction. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched three months enterprise information technology security roadmap through identification introduction in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

SIEM Security Information And Event Management Dashboard Exploit Slides PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver and pitch your topic in the best possible manner with this siem security information and event management dashboard exploit slides pdf. Use them to share invaluable insights on network, authentication, wireless, inventory, access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
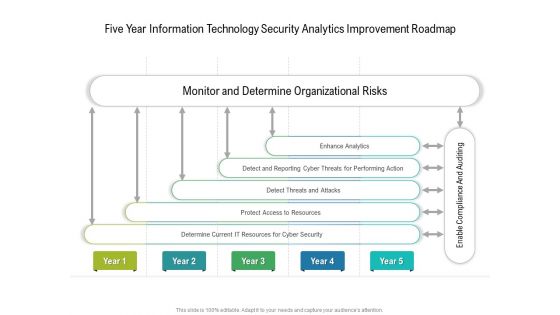
Five Year Information Technology Security Analytics Improvement Roadmap Infographics
We present our five year information technology security analytics improvement roadmap infographics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five year information technology security analytics improvement roadmap infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
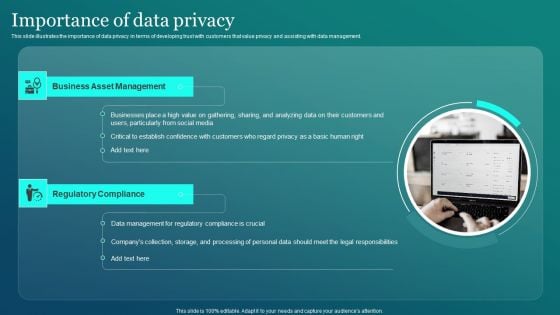
Information Security Importance Of Data Privacy Demonstration PDF
This slide illustrates the importance of data privacy in terms of developing trust with customers that value privacy and assisting with data management. Explore a selection of the finest Information Security Importance Of Data Privacy Demonstration PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Security Importance Of Data Privacy Demonstration PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
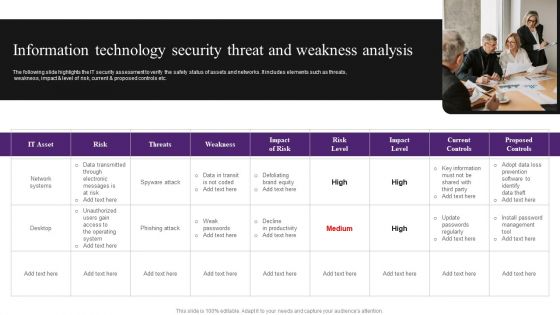
Information Technology Security Threat And Weakness Analysis Diagrams PDF
The following slide highlights the IT security assessment to verify the safety status of assets and networks. It includes elements such as threats, weakness, impact and level of risk, current and proposed controls etc. Persuade your audience using this Information Technology Security Threat And Weakness Analysis Diagrams PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Risk, Network Systems, Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
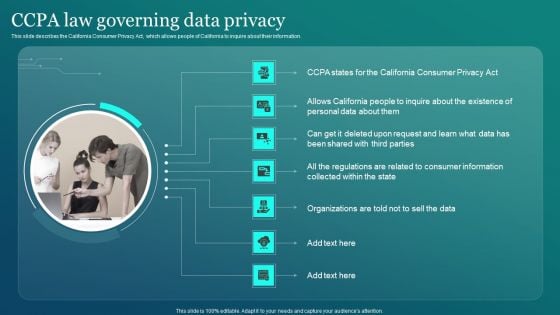
Information Security CCPA Law Governing Data Privacy Clipart PDF
This slide describes the California Consumer Privacy Act, which allows people of California to inquire about their information. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information Security CCPA Law Governing Data Privacy Clipart PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information Security CCPA Law Governing Data Privacy Clipart PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
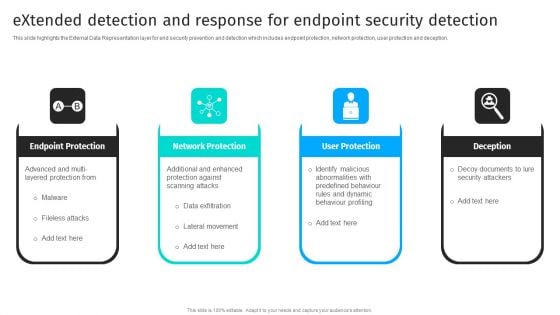
Extended Detection And Response For Endpoint Security Detection Information PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception.There are so many reasons you need a Extended Detection And Response For Endpoint Security Detection Information PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
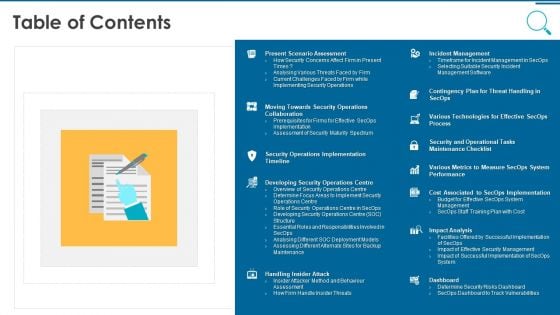
Information And Technology Security Operations Table Of Contents Pictures PDF
This is a information and technology security operations table of contents pictures pdf template with various stages. Focus and dispense information on thirteen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, implementation, analysis, technologies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
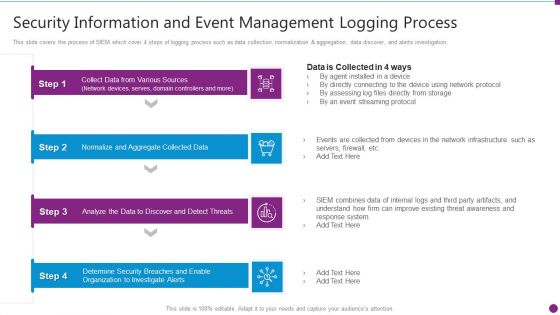
Security Information And Event Management Logging Process Structure PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a security information and event management logging process structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digital Workplace Security Ppt PowerPoint Presentation Portfolio Information Cpb Pdf
Presenting this set of slides with name digital workplace security ppt powerpoint presentation portfolio information cpb pdf. This is an editable Powerpoint one stages graphic that deals with topics like digital workplace security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Table Of Contents For Information Security Law Summary PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Information Security Law Summary PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Information Security Law Summary PDF today and make your presentation stand out from the rest.

Effective IT Risk Management Process Information Security Risk Clipart PDF
Deliver and pitch your topic in the best possible manner with this effective it risk management process information security risk clipart pdf. Use them to share invaluable insights on equipment, software application, service denial, valuable information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Defense Plan Maturity Evaluation Information PDF
This slide represents cyber security defense strategy maturity evaluation mode illustrating culture and organization, governance, visibility and controls, focused defense and intelligence operations. Persuade your audience using this IT Security Defense Plan Maturity Evaluation Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization, Focused Defense, Intelligence Operations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Certified Information Systems Security Professional CISSP Examination Details Infographics PDF
This slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. This is a Certified Information Systems Security Professional CISSP Examination Details Infographics PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Requirements, Network Security, Risk Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
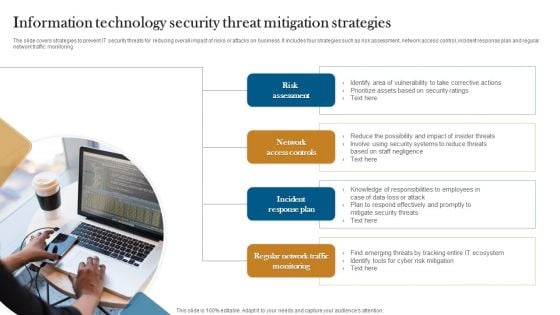
Information Technology Security Threat Mitigation Strategies Formats PDF
The slide covers strategies to prevent IT security threats for reducing overall impact of risks or attacks on business. It includes four strategies such as risk assessment, network access control, incident response plan and regular network traffic monitoring. Persuade your audience using this Information Technology Security Threat Mitigation Strategies Formats PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Assessment, Network Access Controls, Incident Response Plan. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Technology Security Team Analytics Dashboard With KPI Themes PDF
This slide elaborates about the number of incidents that have taken place in cyber security and the malware types with per incident. It also includes the number of open and resolved ticked. Showcasing this set of slides titled Information Technology Security Team Analytics Dashboard With KPI Themes PDF. The topics addressed in these templates are Open Incidents, Resolved Incidents, Open Tickets, Resolved Tickets. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Data Privacy In Financial Institutions Mockup PDF
This slide represents the data privacy in financial institutions which decreases the possibility of fines and reputational damage as a result of unlawful disclosure. This Information Security Data Privacy In Financial Institutions Mockup PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Security Data Privacy In Financial Institutions Mockup PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
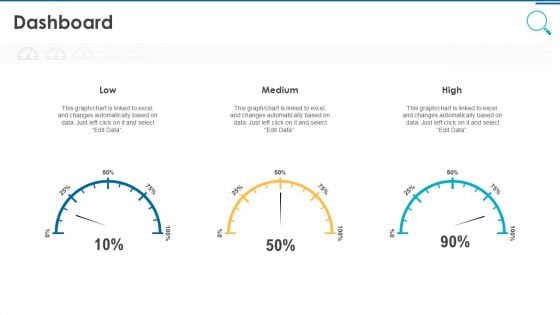
Information And Technology Security Operations Dashboard Pictures PDF
Deliver an awe inspiring pitch with this creative information and technology security operations dashboard pictures pdf bundle. Topics like dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information And Technology Security Operations Quotes Diagrams PDF
Deliver an awe inspiring pitch with this creative information and technology security operations quotes diagrams pdf bundle. Topics like quotes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Protection And Information Security Policy And Procedure Guidelines PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Protection And Information Security Policy And Procedure Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Protection And Information Security Policy And Procedure Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
Information And Technology Security Operations Icons Slide Elements PDF
Introducing our well designed information and technology security operations icons slide elements pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
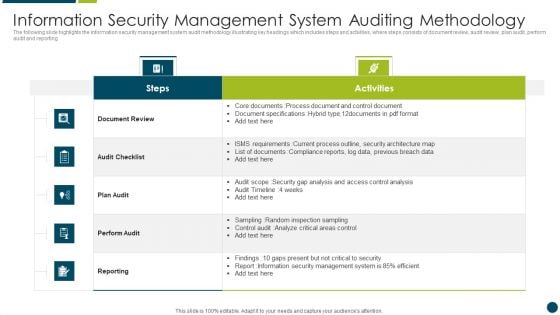
Information Security Management System Auditing Methodology Download PDF
The following slide highlights the information security system audit framework illustrating key headings which includes act, plan, do and check which are used for update and improve isms, establish isms, implement policy and control and monitor and review performance Presenting Information Security Management System Auditing Methodology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Analysis, Data, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
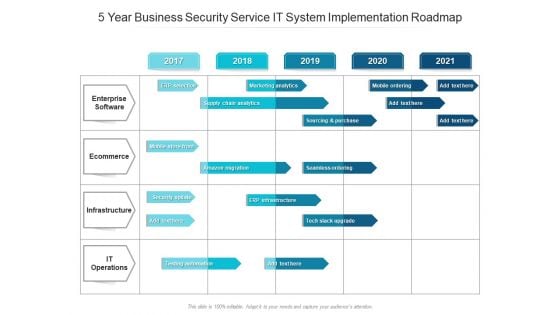
5 Year Business Security Service IT System Implementation Roadmap Information
We present our 5 year business security service it system implementation roadmap information. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched 5 year business security service it system implementation roadmap information in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
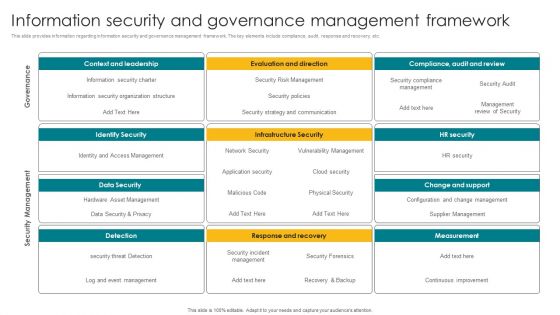
Information Security And Governance Management Framework Summary PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Security And Governance Management Framework Summary PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Security And Governance Management Framework Summary PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
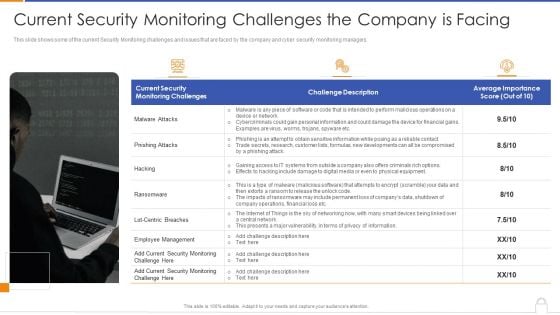
Current Security Monitoring Challenges The Company Is Facing Information PDF
This is a current security monitoring challenges the company is facing information pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware attacks, pnishing attacks, employee management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Security Risk Assessment Framework Demonstration PDF
The following slide highlights the structure to identify best practices to fix risk tolerances. It constitutes of activities such as identify, protect, detect, respond and recover. Presenting Information Technology Security Risk Assessment Framework Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Protect, Detect, Respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
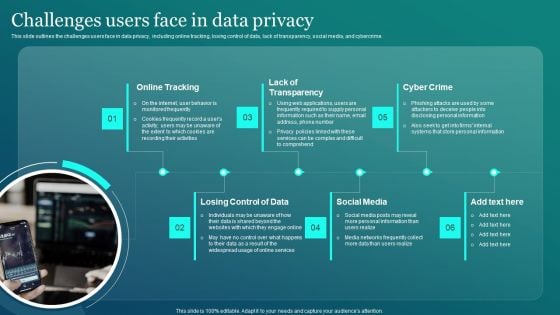
Information Security Challenges Users Face In Data Privacy Sample PDF
This slide outlines the challenges users face in data privacy, including online tracking, losing control of data, lack of transparency, social media, and cybercrime. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Information Security Challenges Users Face In Data Privacy Sample PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Information Security Challenges Users Face In Data Privacy Sample PDF.
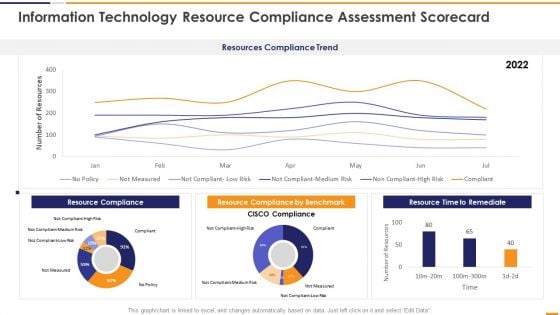
IT Security Evaluation Scorecard Information Technology Resource Compliance Background PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard Information Technology Resource Compliance Background PDF. Use them to share invaluable insights on Resources Compliance Trend, Resource Compliance 2022, Resource Compliance Benchmark, Resource Time Remediate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Allocating Budget For Information Security Risk Management Programme Brochure PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for area like cybersecurity awareness, threat detection and risk management.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Allocating Budget For Information Security Risk Management Programme Brochure PDF from Slidegeeks and deliver a wonderful presentation.
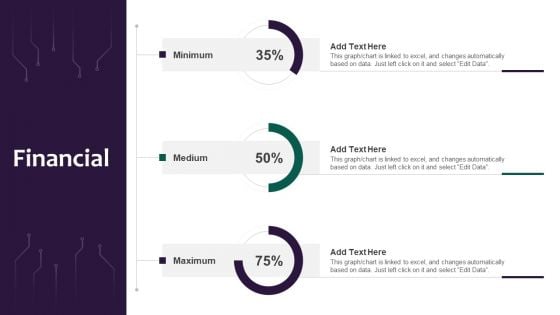
Information Systems Security And Risk Management Plan Financial Professional PDF
Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information Systems Security And Risk Management Plan Financial Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information Systems Security And Risk Management Plan Financial Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Table Of Contents Organizational Assets Security Management Strategy Information PDF
Find highly impressive Table Of Contents Organizational Assets Security Management Strategy Information PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents Organizational Assets Security Management Strategy Information PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Information Security Adhere To Strict Compliance Requirements Diagrams PDF
This slide shows that you can use a data classification engine to locate and categorize regulated and sensitive material also, compliance standards serve as a foundation. If you are looking for a format to display your unique thoughts, then the professionally designed Information Security Adhere To Strict Compliance Requirements Diagrams PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Security Adhere To Strict Compliance Requirements Diagrams PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
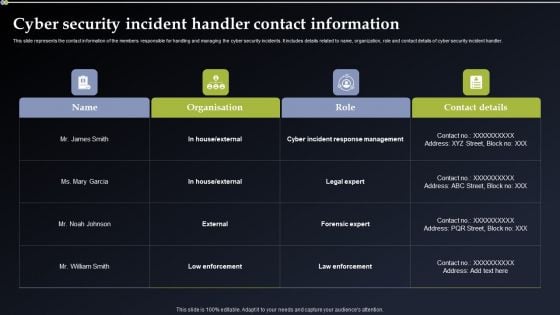
Cyber Security Incident Handler Contact Information Summary PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. This Cyber Security Incident Handler Contact Information Summary PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
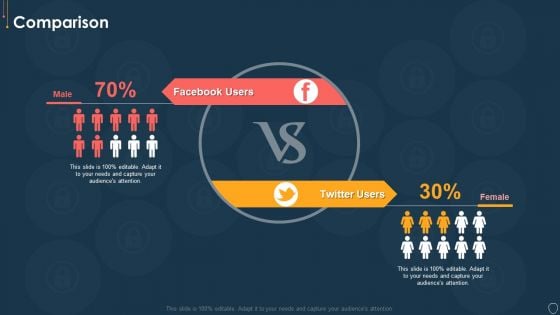
Cyber Security Risk Management Plan Comparison Information PDF
Presenting cyber security risk management plan comparison information pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like facebook users, twitter users. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Systems Security And Risk Management Plan Target Formats PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Information Systems Security And Risk Management Plan Target Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Information Systems Security And Risk Management Plan Target Formats PDF today and make your presentation stand out from the rest.
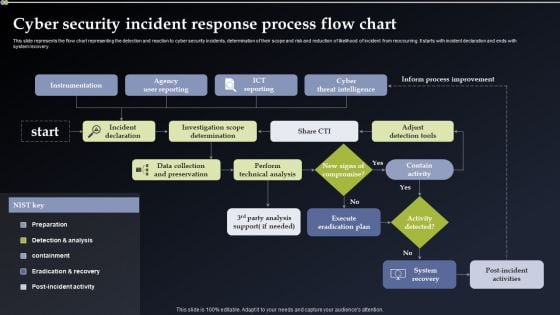
Cyber Security Incident Response Process Flow Chart Information PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Process Flow Chart Information PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Process Flow Chart Information PDF.
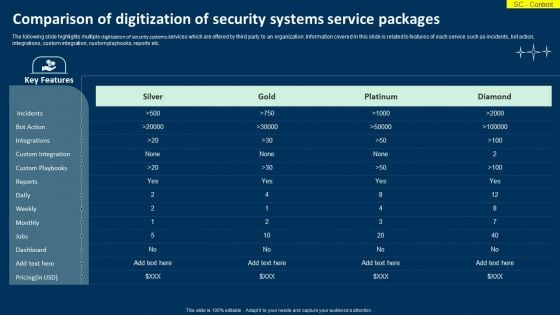
Comparison Of Digitization Of Security Systems Service Packages Information PDF
The following slide highlights multiple digitization of security systems services which are offered by third party to an organization. Information covered in this slide is related to features of each service such as incidents, bot action, integrations, custom integration, custom playbooks, reports etc. Showcasing this set of slides titled Comparison Of Digitization Of Security Systems Service Packages Information PDF. The topics addressed in these templates are Key Features, Custom Integration, Custom Playbooks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Management System Auditing Process Microsoft PDF
The following slide highlights the information security management system audit methodology illustrating key headings which includes steps and activities, where steps consists of document review, audit review, plan audit, perform audit and reporting Showcasing this set of slides titled Information Security Management System Auditing Process Microsoft PDF. The topics addressed in these templates are Plan Audit, Reporting, Audit Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
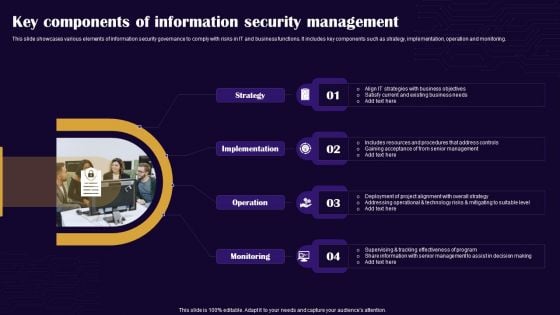
Key Components Of Information Security Management Graphics PDF
This slide showcases various elements of information security governance to comply with risks in IT and business functions. It includes key components such as strategy, implementation, operation and monitoring. Persuade your audience using this Key Components Of Information Security Management Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strategy, Implementation, Operation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
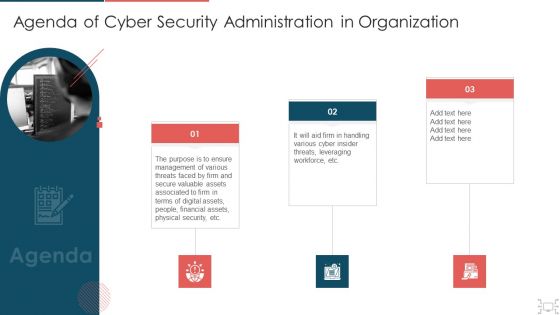
Agenda Of Cyber Security Administration In Organization Information PDF
This is a agenda of cyber security administration in organization information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda, purpose, management, valuable, assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Email Prevention Guidelines For Employees Information PDF
This slide depicts the email prevention guidelines for employees, including spam filters and multi factor authentication for email login credentials.This is a IT Security Hacker Email Prevention Guidelines For Employees Information PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Process, Pieces Of Information, Factor Authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
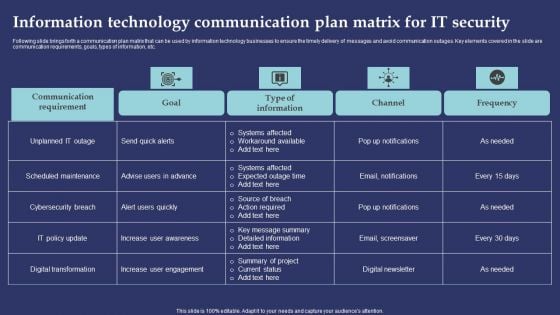
Information Technology Communication Plan Matrix For It Security Professional PDF
Following slide brings forth a communication plan matrix that can be used by information technology businesses to ensure the timely delivery of messages and avoid communication outages. Key elements covered in the slide are communication requirements, goals, types of information, etc. Showcasing this set of slides titled Information Technology Communication Plan Matrix For It Security Professional PDF. The topics addressed in these templates are Systems Affected, Workaround Available, Action Required. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
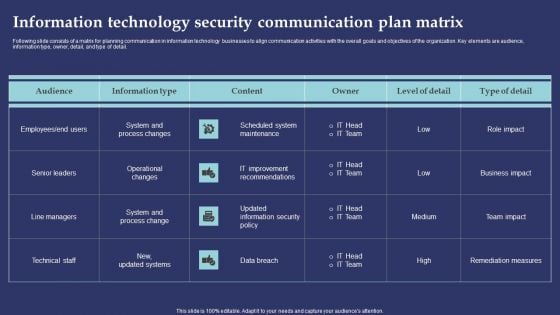
Information Technology Security Communication Plan Matrix Template PDF
Following slide consists of a matrix for planning communication in information technology businesses to align communication activities with the overall goals and objectives of the organization. Key elements are audience, information type, owner, detail, and type of detail. Showcasing this set of slides titled Information Technology Security Communication Plan Matrix Template PDF. The topics addressed in these templates are Scheduled System Maintenance, IT Improvement Recommendations, Data Breach. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Data Privacy In Educational Institutions Introduction PDF
This slide depicts data privacy in educational Information , institutions should issue a notice period of two days for approval before disclosing any information. This modern and well arranged Information Security Data Privacy In Educational Institutions Introduction PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
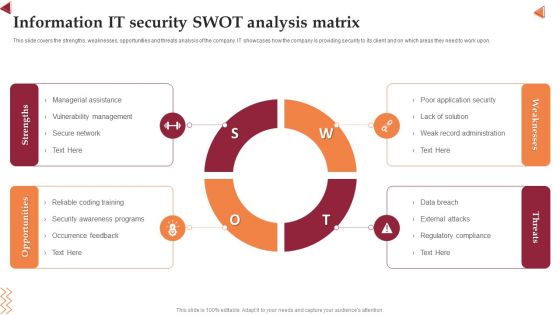
Information IT Security Swot Analysis Matrix Clipart PDF
This slide covers the strengths, weaknesses, opportunities and threats analysis of the company. IT showcases how the company is providing security to its client and on which areas they need to work upon. Persuade your audience using this Information IT Security Swot Analysis Matrix Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strengths, Opportunities, Weaknesses, Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Agenda For Information Security Ppt PowerPoint Presentation File Styles PDF
Find a pre designed and impeccable Agenda For Information Security Ppt PowerPoint Presentation File Styles PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
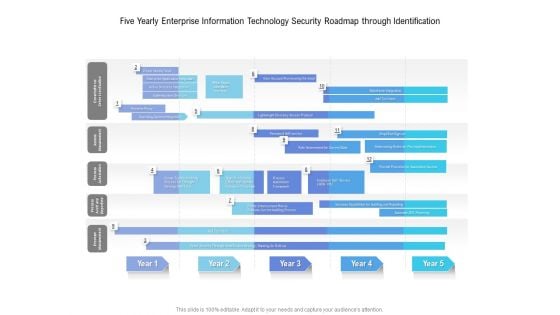
Five Yearly Enterprise Information Technology Security Roadmap Through Identification Sample
Introducing our five yearly enterprise information technology security roadmap through identification sample. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.


 Continue with Email
Continue with Email

 Home
Home


































