Information Security Program
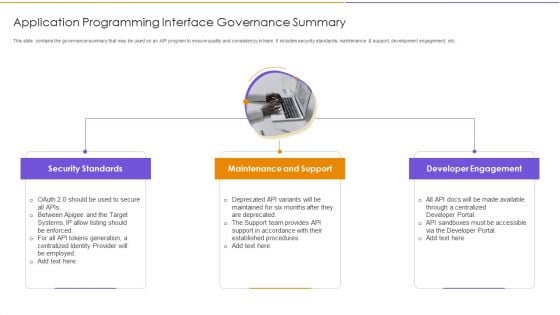
Application Programming Interface Governance Summary Pictures PDF
This slide contains the governance summary that may be used on an API program to ensure quality and consistency in team. It includes security standards, maintenance and support, development engagement, etc. Persuade your audience using this Application Programming Interface Governance Summary Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Maintenance And Support, Developer Engagement, Security Standards. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Steps Insurance Risk Management Procedure Professional PDF
This slide show the risk management process of an insurance company. It includes information security program, security codes, cyber security and training. Persuade your audience using this Five Steps Insurance Risk Management Procedure Professional PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Security Codes, Cyber Security, Stay Informed. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Checklist To Inform New Employee Hire Company Policies Ppt Layouts Graphics Download PDF
This slide covers checklist to provide employees information about different companys policies. It includes policies such as no password sharing, company BYOD, working hours, overtime pay, insurance policies, pension, etc. Presenting Checklist To Inform New Employee Hire Company Policies Ppt Layouts Graphics Download PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Checklist, Completed, Working Hours Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Secure Digital Mail PowerPoint Icon C
3d illustration of a chrome at/email symbol surrounded by a ring of glowing green binary digits with a heavy metallic padlock attached to it on a dark gray reflective surface Begin your endeavour with our Secure Digital Mail PowerPoint Icon C. You will never make a false start.
Secure Digital Mail PowerPoint Icon Cc
3d illustration of a chrome at/email symbol surrounded by a ring of glowing green binary digits with a heavy metallic padlock attached to it on a dark gray reflective surface Our Secure Digital Mail PowerPoint Icon Cc help you think on your feet. They provide you with ready answers.
Secure Digital Mail PowerPoint Icon S
3d illustration of a chrome at/email symbol surrounded by a ring of glowing green binary digits with a heavy metallic padlock attached to it on a dark gray reflective surface Our Secure Digital Mail PowerPoint Icon S are never erratic. They are always balanced and steady.
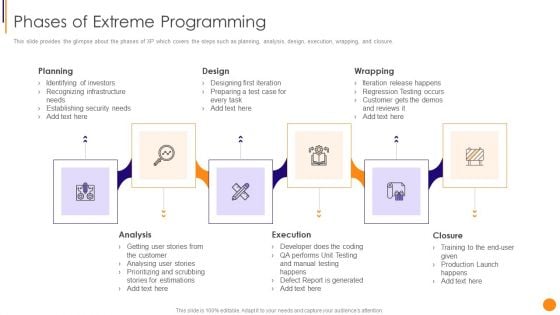
Scrum Crystal And Extreme Programming Procedure Phases Of Extreme Programming Graphics PDF
This slide provides the glimpse about the phases of XP which covers the steps such as planning, analysis, design, execution, wrapping, and closure. This is a scrum crystal and extreme programming procedure phases of extreme programming graphics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, infrastructure, recognizing, investors, security, prioritizing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
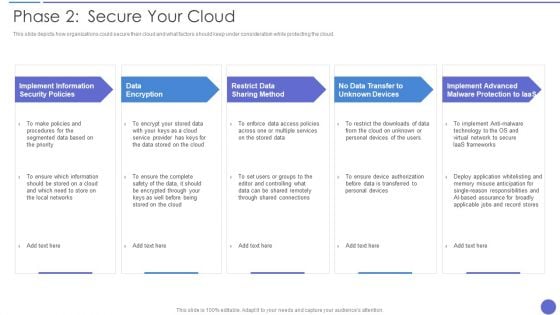
Phase 2 Secure Your Cloud Clipart PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Presenting Phase 2 Secure Your Cloud Clipart PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Encryption, Restrict Data Sharing Method, Implement Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
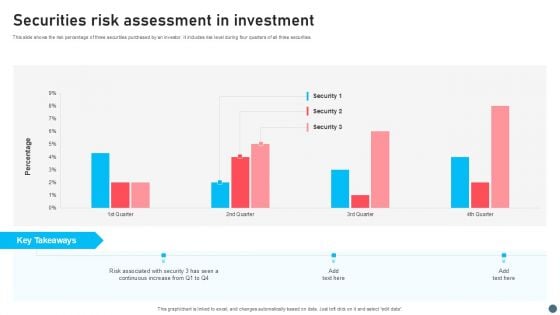
Securities Risk Assessment In Investment Topics PDF

Lockable Informative Laptop PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Lockable Informative Laptop PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity. Download our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will steer your racing mind. Hit the right buttons and spur on your audience. Download and present our Security PowerPoint Templates because You are well armed with penetrative ideas. Our PowerPoint Templates and Slides will provide the gunpowder you need. Present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let your words and thoughts hit bullseye everytime. Present our Shapes PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides.Use these PowerPoint slides for presentations relating to Notebook Lockable, computer, technology, security, signs, shapes. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. Dont create mammoth presentations. Be clear and succinct with our Lockable Informative Laptop PowerPoint Templates Ppt Backgrounds For Slides 0313. You'll always stay ahead of the game.

Data Is Secure Internet PowerPoint Template 1110
3d illustration of a lock sitting in front of a computer display showing a file folder Approve plans with our Data Is Secure Internet PowerPoint Template 1110. You will come out on top.
Secure Computer Database Access Icon Slides PDF
Presenting Secure Computer Database Access Icon Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Secure, Computer, Database Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Securities Finance Ppt PowerPoint Presentation Pictures Cpb
Presenting this set of slides with name securities finance ppt powerpoint presentation pictures cpb. This is an editable Powerpoint four stages graphic that deals with topics like securities finance to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
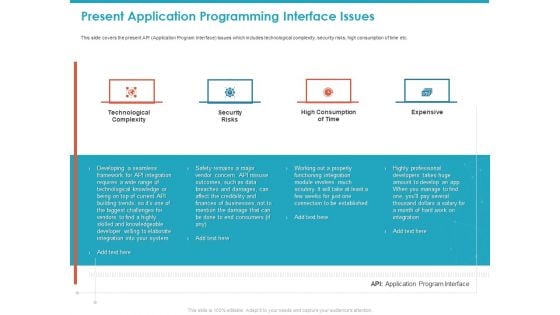
Present Application Programming Interface Issues Ppt Inspiration PDF
This slide covers the present API Application Program Interface issues which includes technological complexity, security risks, high consumption of time etc. This is a present application programming interface issues ppt inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technological complexity, security risks, high consumption of time, expensive. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
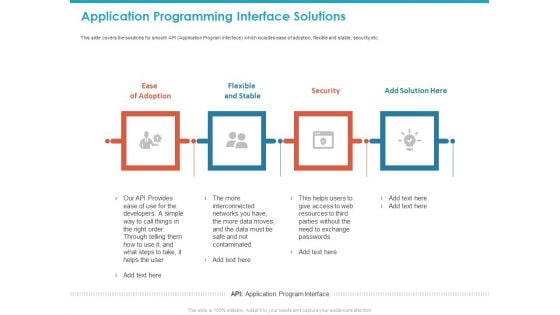
Application Programming Interface Solutions Ppt Infographic Template Background Image PDF
This slide covers the solutions for smooth API Application Program Interface which includes ease of adoption, flexible and stable, security etc. This is a application programming interface solutions ppt infographic template background image pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like flexible and stable, security, ease of adoption, add solution here. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Nanorobotics In Healthcare And Medicine Timeline For Effective Nanorobot Utilization In Organization
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Nanorobotics In Healthcare And Medicine Timeline For Effective Nanorobot Utilization In Organization. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Nanorobotics In Healthcare And Medicine Timeline For Effective Nanorobot Utilization In Organization today and make your presentation stand out from the rest This slide defines an all-inclusive timeline of steps in the execution of nanorobotics in healthcare and medicine by incorporating effective use of nanorobots within an organization. This ranges from preparation and research and eventually to the inclusion of nanorobotics with the existing healthcare systems. The timeline also identifies critical factors including security, regulatory compliance, testing, and safety procedures, where nanorobots would be applied safely and effectively.This slide is perfect for advanced medical technology presentations to help the stakeholders understand the systematic process of how nanorobotics could be introduced in healthcare solutions and paved their way for smooth adoption and use.
Reverse Proxy Web Server Secure Client Connection To Proxy And Secure Proxy Icons PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. Slidegeeks has constructed Reverse Proxy Web Server Secure Client Connection To Proxy And Secure Proxy Icons PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
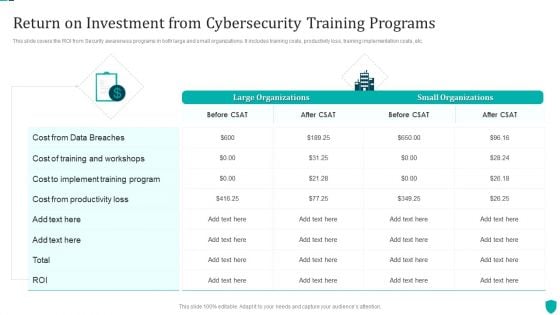
Return On Investment From Cybersecurity Training Programs Demonstration PDF
This slide covers the ROI from Security awareness programs in both large and small organizations. It includes training costs, productivity loss, training implementation costs, etc.Showcasing this set of slides titled Return On Investment From Cybersecurity Training Programs Demonstration PDF. The topics addressed in these templates are Training And Workshops, Implement Training, Cost From Productivity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
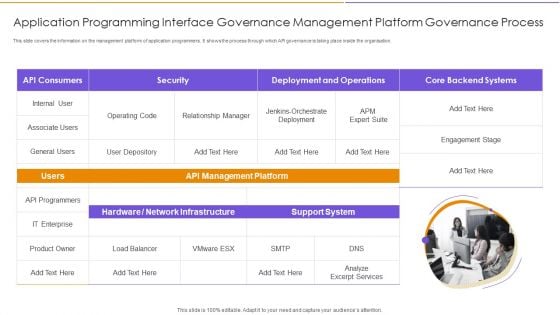
Application Programming Interface Governance Management Platform Governance Process Graphics PDF
This slide covers the information on the management platform of application programmers. It shows the process through which API governance is taking place inside the organisation. Presenting Application Programming Interface Governance Management Platform Governance Process Graphics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Security, Deployment And Operations, Enterprise. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
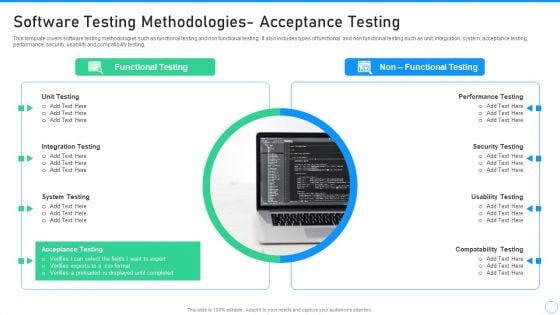
Application Designing And Programming Playbook Software Testing Methodologies Template PDF
This template covers software testing methodologies such as functional testing and non functional testing. It also includes types of functional and non functional testing such as unit, integration, system, acceptance testing, performance, security, usability and compatibility testing. This is a Application Designing And Programming Playbook Software Testing Methodologies Template PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Performance Testing, Usability Testing, Compatibility Testing You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.

Secure Email Technology PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Secure Email Technology PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Technology PowerPoint Templates because Your audience will believe you are the cats whiskers. Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Present our Communication PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download and present our Signs PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium.Use these PowerPoint slides for presentations relating to Illustration of envelope and email sign protect with padloc, security, communication, technology, business, signs. The prominent colors used in the PowerPoint template are Red, Gray, Yellow. Deal a decisive blow with our Secure Email Technology PowerPoint Templates Ppt Backgrounds For Slides 0413. Get clearlyahead in a critical event.
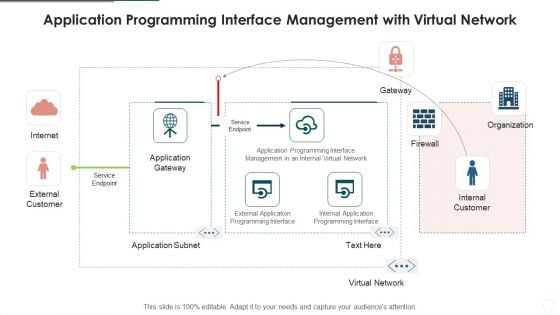
Application Programming Interface Management With Virtual Network Microsoft PDF
Showcasing this set of slides titled application programming interface management with virtual network microsoft pdf. The topics addressed in these templates are application gateway, service endpoint, external customer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
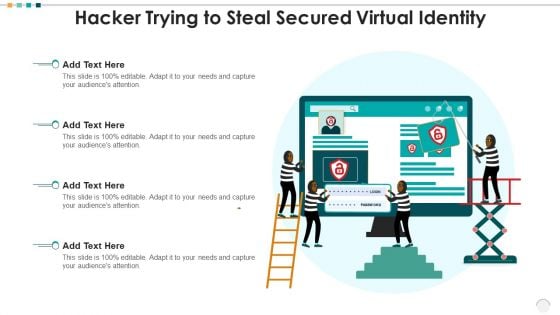
Hacker Trying To Steal Secured Virtual Identity Sample PDF
Persuade your audience using this hacker trying to steal secured virtual identity sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including hacker trying to steal secured virtual identity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Secure Your Money PowerPoint Templates Ppt Backgrounds For Slides 0413
Our Secure Your Money PowerPoint Templates PPT Backgrounds For Slides 0413 allow you to do it with ease. Just like picking the low hanging fruit. Boil the ocean with your thoughts. Our Secure Your Money PowerPoint Templates PPT Backgrounds For Slides 0413 will help create waves. Communicate goals with our Secure Your Money PowerPoint Templates Ppt Backgrounds For Slides 0413. Download without worries with our money back guaranteee.

Secure Internet Browser Computer PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with transparent internet browser with a lock padlock intersecting it List your core competencies with our Secure Internet Browser Computer PowerPoint Templates And PowerPoint Backgrounds 0811. They will make you look good.

Secure Internet Browser Computer PowerPoint Themes And PowerPoint Slides 0811
Microsoft PowerPoint Theme and Slide with transparent internet browser with a lock padlock intersecting it Our Secure Internet Browser Computer PowerPoint Themes And PowerPoint Slides 0811 have amazing characteristics. They educate and entertain on your command.
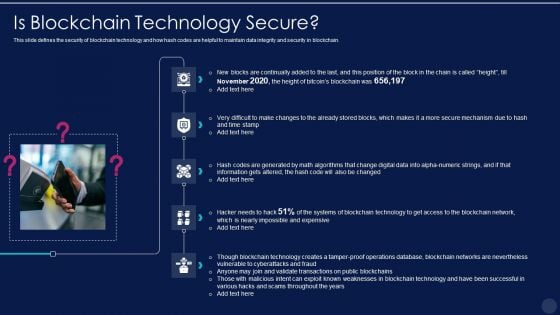
Blockchain Technology Framework IT Is Blockchain Technology Secure Demonstration PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. This is a blockchain technology framework it is blockchain technology secure demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like expensive, systems, blockchain network, operations database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
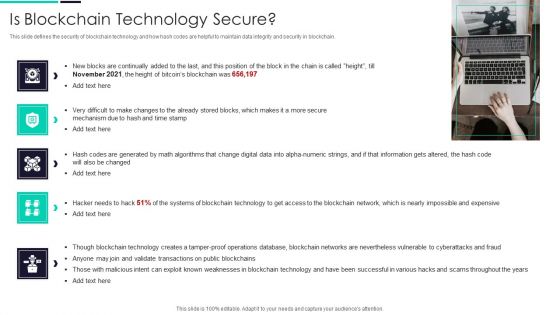
Blockchain And DLT Framework Is Blockchain Technology Secure Ideas PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. This is a Blockchain And DLT Framework Is Blockchain Technology Secure Ideas PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Time Stamp, Blockchain Technology, Weaknesses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
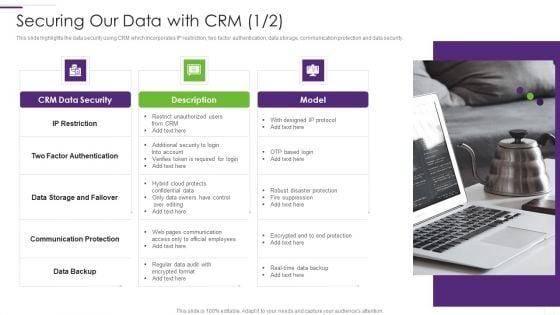
CRM Implementation Strategy Securing Our Data With CRM Summary PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.This is a CRM Implementation Strategy Securing Our Data With CRM Summary PDF template with various stages. Focus and dispense information on One stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Factor Authentication, Communication Protection, Restrict Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
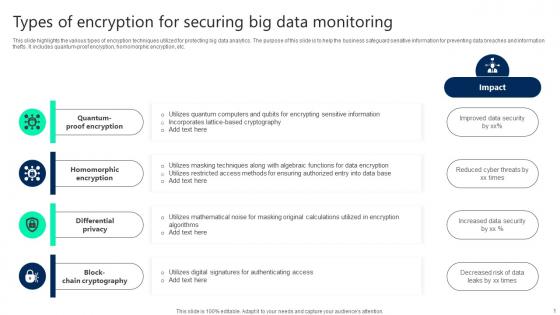
Types Of Encryption For Securing Big Data Monitoring Topics pdf
This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc. Showcasing this set of slides titled Types Of Encryption For Securing Big Data Monitoring Topics pdf. The topics addressed in these templates are Quantum Proof Encryption, Homomorphic Encryption, Differential Privacy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc.
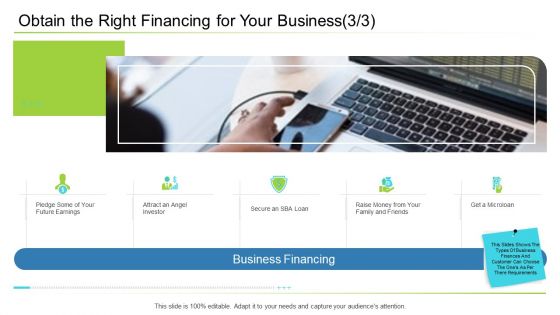
Obtain The Right Financing For Your Business Secure Professional PDF
This is a obtain the right financing for your business secure professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like investor, loan, secure, business financing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Selecting Secured Threat Formats PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities selecting secured threat formats pdf bundle. Topics like information security prevention, api integration, security incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
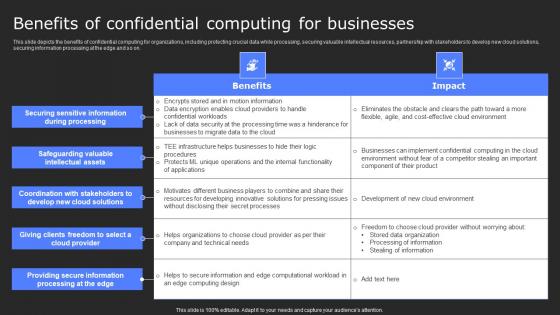
Benefits Of Confidential Computing For Secure Computing Framework Microsoft Pdf
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Confidential Computing For Secure Computing Framework Microsoft Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on.
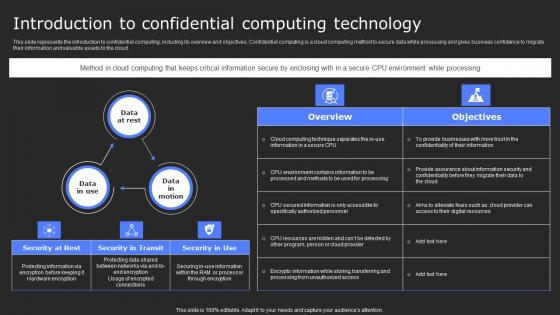
Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Boost your pitch with our creative Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
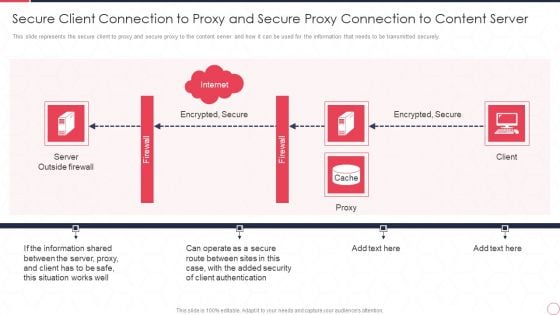
Reverse Proxy Server IT Secure Client Connection To Proxy And Secure Proxy Connection Ppt Infographic Template Design Inspiration PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. This is a reverse proxy server it secure client connection to proxy and secure proxy connection ppt infographic template design inspiration pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like server outside firewall, encrypted, secure, proxy, client. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Secure VPN Vector Icon Ppt PowerPoint Presentation Layouts Images PDF
Pitch your topic with ease and precision using this secure vpn vector icon ppt powerpoint presentation layouts images pdf. This layout presents information on secure vpn vector icon . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Secured Childcare Market Strategic Assessment Icon Topics Pdf
Pitch your topic with ease and precision using this Secured Childcare Market Strategic Assessment Icon Topics Pdf This layout presents information on Secured Childcare, Market Strategic, Assessment Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Secured Childcare Market Strategic Assessment Icon Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
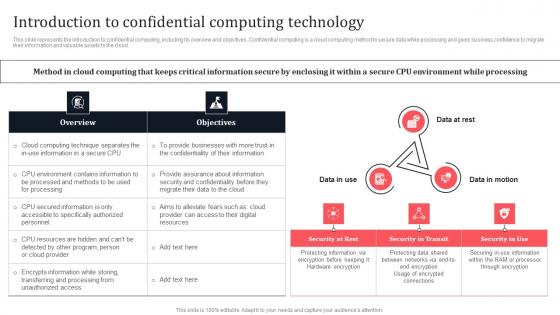
Introduction To Confidential Computing Technology Secure Multi Party Download Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Do you know about Slidesgeeks Introduction To Confidential Computing Technology Secure Multi Party Download Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
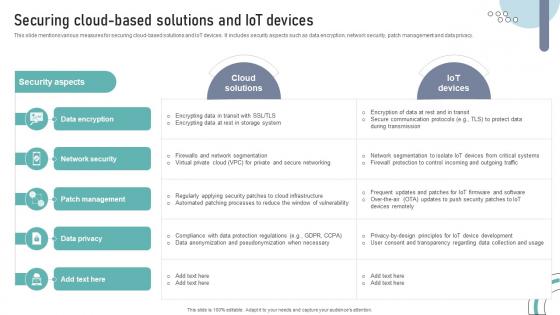
Securing Cloud Based Solutions And IOT Devices DT SS V
This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy. Slidegeeks has constructed Securing Cloud Based Solutions And IOT Devices DT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy.
Cloud Secure Data Lifecycle In Powerpoint And Google Slides Cpb
Introducing our well designed Cloud Secure Data Lifecycle In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cloud Secure Data Lifecycle. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cloud Secure Data Lifecycle In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb
Introducing our well designed Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Sdlc Policy Template. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Sdlc Policy Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Secure Web Gateways Market In Powerpoint And Google Slides Cpb
Introducing our well-designed Secure Web Gateways Market In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Web Gateways Market. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Web Gateways Market In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Secure Communication Encrypted In Powerpoint And Google Slides Cpb
Introducing our well designed Secure Communication Encrypted In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Communication Encrypted. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Communication Encrypted In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Secure Shell Protocol In Powerpoint And Google Slides Cpb
Introducing our well designed Secure Shell Protocol In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Shell Protocol. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Shell Protocol In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Browser Secure Market In Powerpoint And Google Slides Cpb
Introducing our well designed Browser Secure Market In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Browser Secure Market. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Browser Secure Market In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Business Continuity Securing In Powerpoint And Google Slides Cpb
Introducing our well designed Business Continuity Securing In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Business Continuity Securing. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Business Continuity Securing In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
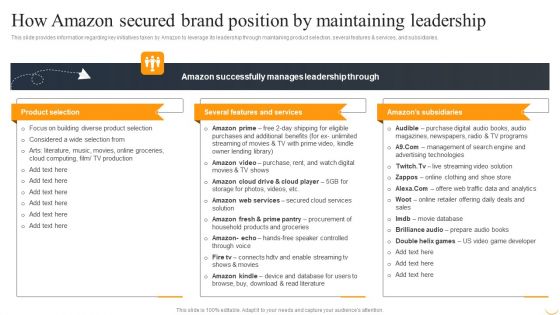
How Amazon Secured Brand Position By Maintaining Leadership Designs PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. Get a simple yet stunning designed How Amazon Secured Brand Position By Maintaining Leadership Designs PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit How Amazon Secured Brand Position By Maintaining Leadership Designs PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses
This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. This Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc.
Securing Your Data With Tokenization Table Of Contents Ppt Sample
Want to ace your presentation in front of a live audience Our Securing Your Data With Tokenization Table Of Contents Ppt Sample can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. Our Securing Your Data With Tokenization Table Of Contents Ppt Sample are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
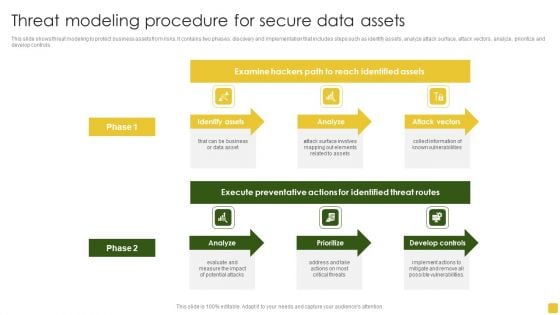
Threat Modeling Procedure For Secure Data Assets Formats PDF
This slide shows threat modeling to protect business assets from risks. It contains two phases discovery and implementation that includes steps such as identify assets, analyze attack surface, attack vectors, analyze, prioritize and develop controls. Pitch your topic with ease and precision using this Threat Modeling Procedure For Secure Data Assets Formats PDF. This layout presents information on Execute Preventative, Identified Threat, Develop Controls. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
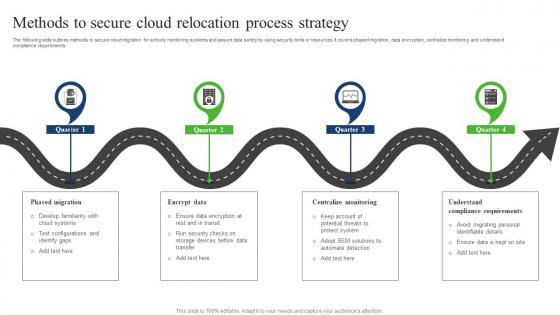
Methods To Secure Cloud Relocation Process Strategy Sample Pdf
The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements. Showcasing this set of slides titled Methods To Secure Cloud Relocation Process Strategy Sample Pdf. The topics addressed in these templates are Centralize Monitoring, Understand Compliance Requirements, Phased Migration, Encrypt Data . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements.
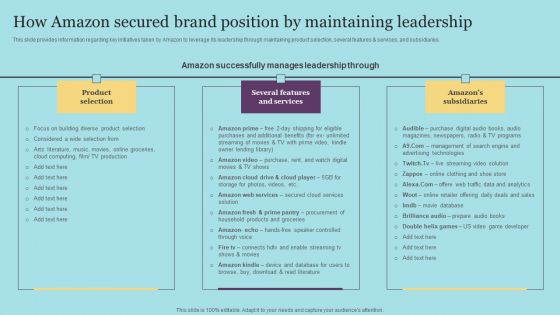
How Amazon Secured Brand Position By Maintaining Leadership Download PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. This modern and well-arranged How Amazon Secured Brand Position By Maintaining Leadership Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
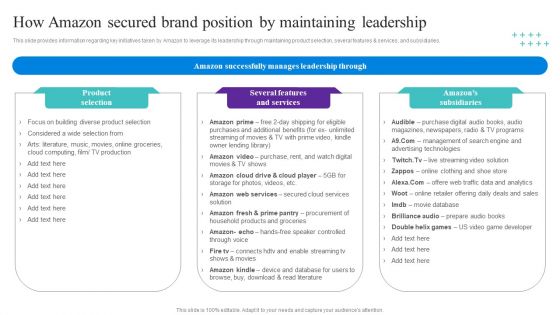
How Amazon Secured Brand Position By Maintaining Leadership Topics PDF
Icons Slide For Securing Your Data With Tokenization Ppt Slide
Download our innovative and attention grabbing Icons Slide For Securing Your Data With Tokenization Ppt Slide template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide For Securing Your Data With Tokenization Ppt Slide are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf
Showcasing this set of slides titled Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf. The topics addressed in these templates are Encryption Techniques, IconSecuring, Big Data Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Secure Web Gateway Architecture And Working Web Threat Protection System
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. This Secure Web Gateway Architecture And Working Web Threat Protection System from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc.
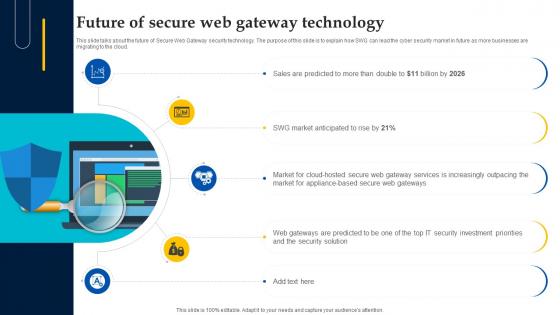
Web Access Control Solution Future Of Secure Web Gateway Technology
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. This modern and well-arranged Web Access Control Solution Future Of Secure Web Gateway Technology provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.
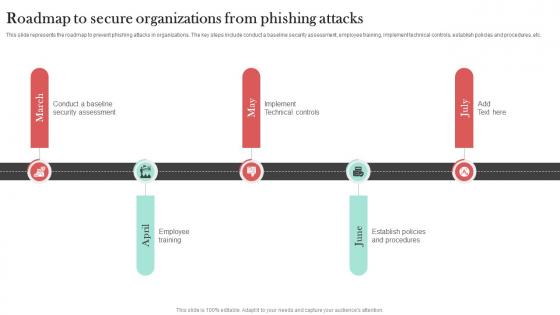
Roadmap To Secure Organizations Man In The Middle Phishing IT
This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Roadmap To Secure Organizations Man In The Middle Phishing IT and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc.

Securing Your Data with Tokenization Powerpoint Presentation Slides PPT Example


 Continue with Email
Continue with Email

 Home
Home


































