Information Security Roadmap
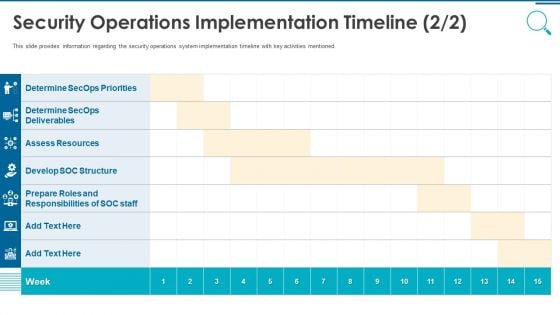
Information And Technology Security Operations Security Operations Implementation Timeline Staff Template PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this information and technology security operations security operations implementation timeline staff template pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
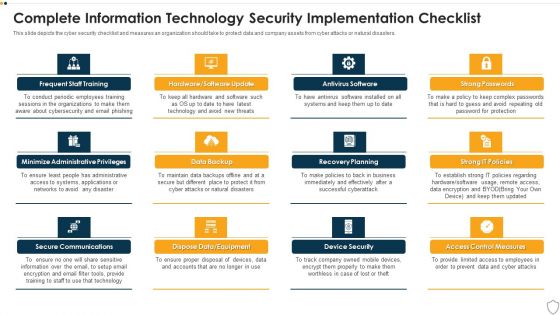
IT Security Complete Information Technology Security Implementation Checklist Ppt Inspiration Templates PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting it security complete information technology security implementation checklist ppt inspiration templates pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like frequent staff training, secure communications, data backup, recovery planning, device security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
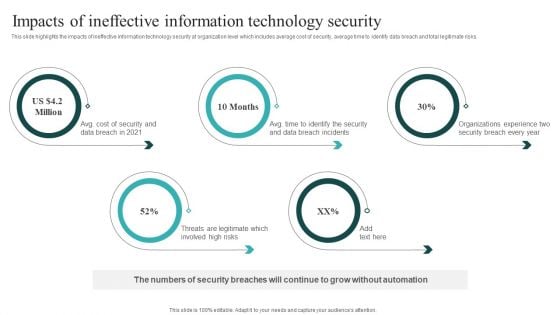
IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Get a simple yet stunning designed IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Information Security Complete Data Security Implementation Checklist Ppt Icon Clipart PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a information security complete data security implementation checklist ppt icon clipart pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong passwords, antivirus software, frequent staff training, recovery planning, device security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
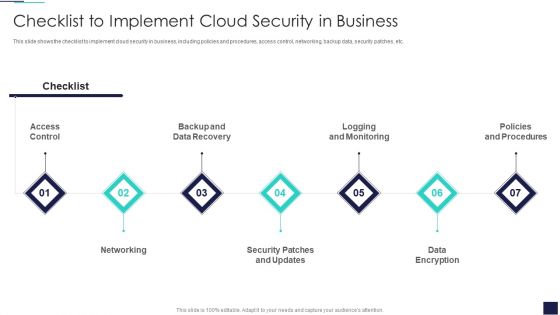
Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. This is a Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Policies And Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Checklist Access Control Ppt Inspiration Professional PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. This is a Cloud Information Security Cloud Security Checklist Access Control Ppt Inspiration Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Control Identity, Security Breaches, Data Servers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
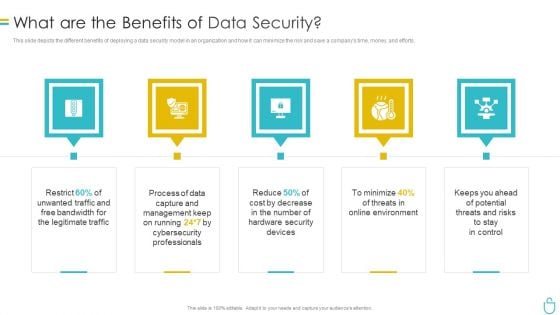
Information Security What Are The Benefits Of Data Security Ppt Infographics Example Topics PDF
This slide depicts the different benefits of deploying a data security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting information security what are the benefits of data security ppt infographics example topics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, hardware security, devices, environment, risks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
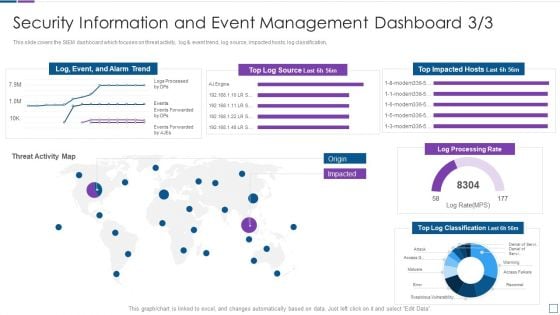
Security Information And Event Management Real Time Assessment Of Security Threats Template PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification. Deliver an awe inspiring pitch with this creative security information and event management real time assessment of security threats template pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Defining The Information Security Management System Download PDF
Presenting security management plan steps in detail defining the information security management system download pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like processes, procedures, instructions, implementation, security management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Checklist Policies And Procedures Ppt Inspiration Objects PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. Presenting Cloud Information Security Cloud Security Checklist Policies And Procedures Ppt Inspiration Objects PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Implement Policies, Protect Data, Security Procedures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing IT Security Strategy Impact Of Information Security Loss On Organization Demonstration PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Developing IT Security Strategy Impact Of Information Security Loss On Organization Demonstration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Developing IT Security Strategy Impact Of Information Security Loss On Organization Demonstration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
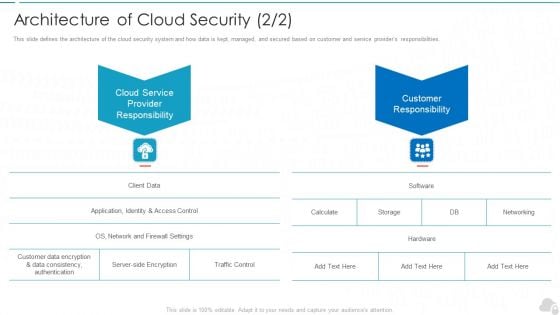
Architecture Of Cloud Security Service Cloud Computing Security IT Ppt Professional Information PDF
This slide defines the architecture of the cloud security system and how data is kept, managed, and secured based on customer and service providers responsibilities. This is a architecture of cloud security service cloud computing security it ppt professional information pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cloud service provider responsibility, customer responsibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Contd Brochure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Presenting developing firm security strategy plan information security process to manage firms sensitive data contd brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like firewall audit checklist, vpn configuration, penetrating testing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
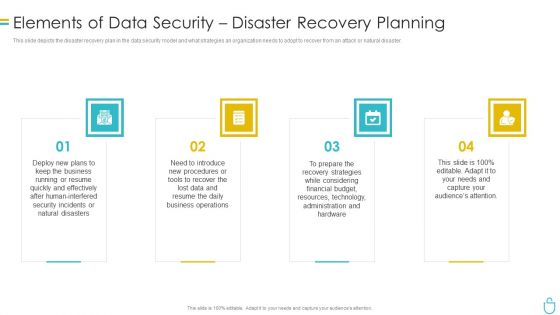
Information Security Elements Of Data Security Disaster Recovery Planning Ppt Inspiration Example Topics PDF
This slide depicts the disaster recovery plan in the data security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. This is a information security elements of data security disaster recovery planning ppt inspiration example topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plans, procedures, strategies, technology, resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
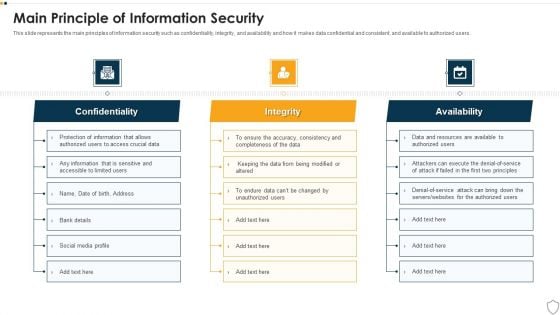
IT Security Main Principle Of Information Security Ppt Infographics Example Topics PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. This is a it security main principle of information security ppt infographics example topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like confidentiality, integrity, availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
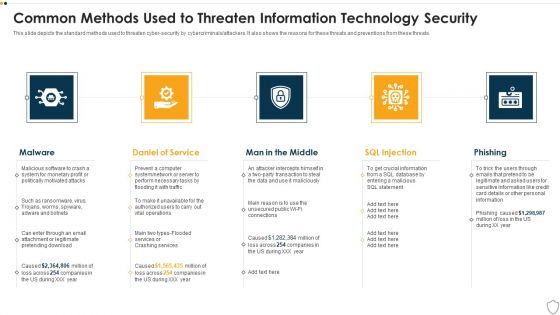
IT Security Common Methods Used To Threaten Information Technology Security Ppt Layouts Graphics PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a it security common methods used to threaten information technology security ppt layouts graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
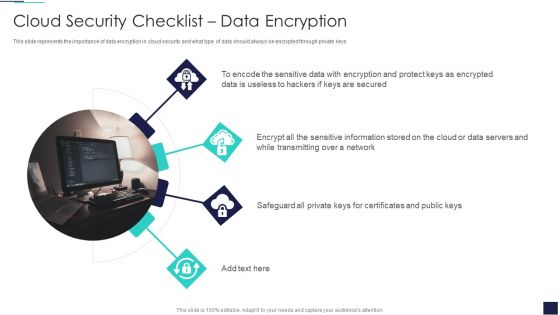
Cloud Information Security Cloud Security Checklist Data Encryption Ppt Summary Shapes PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. This is a Cloud Information Security Cloud Security Checklist Data Encryption Ppt Summary Shapes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Sensitive Data, Protect Keys, Data Servers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
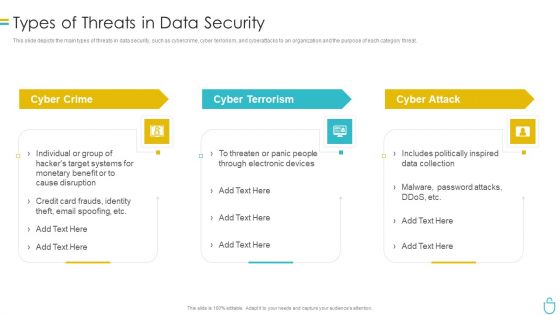
Information Security Types Of Threats In Data Security Ppt Layouts File Formats PDF
This slide depicts the main types of threats in data security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a information security types of threats in data security ppt layouts file formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Contd Graphics PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Deliver and pitch your topic in the best possible manner with this project security administration it information security process to manage firms sensitive data contd graphics pdf. Use them to share invaluable insights on firewall audit checklist, vpn configuration, penetrating testing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Defining Categories Of Information Security Threats Structure PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures. This is a cyber security risk management plan defining categories of information security threats structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like human error, natural disaster, environmental control failures, deliberate software attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Info Security Complete Information Security Implementation Checklist Ppt PowerPoint Presentation Icon Portfolio PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a info security complete information security implementation checklist ppt powerpoint presentation icon portfolio pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like frequent, staff training, antivirus software, strong passwords, data backup, recovery planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
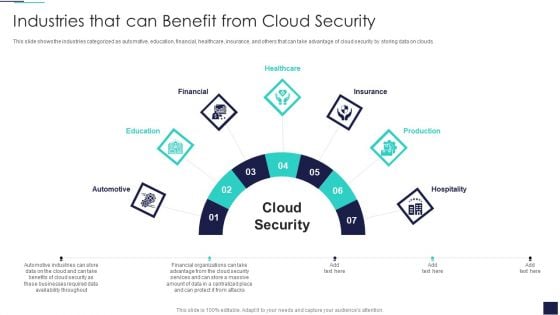
Cloud Information Security Industries That Can Benefit From Cloud Security Ppt Summary Graphics PDF
This slide shows the industries categorized as automotive, education, financial, healthcare, insurance, and others that can take advantage of cloud security by storing data on clouds. This is a Cloud Information Security Industries That Can Benefit From Cloud Security Ppt Summary Graphics PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Automotive Education, Financial Healthcare, Insurance Production. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
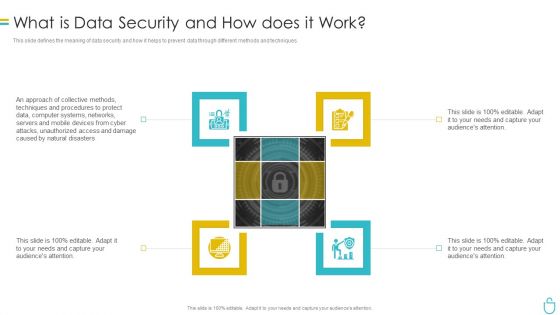
Information Security What Is Data Security And How Does It Work Ppt Professional Infographics PDF
This slide defines the meaning of data security and how it helps to prevent data through different methods and techniques. Presenting information security what is data security and how does it work ppt professional infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like techniques, computer systems, protect. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
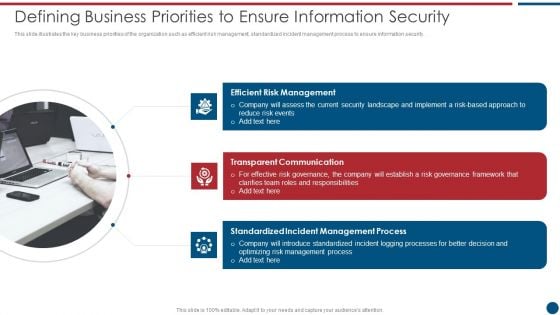
Risk Based Procedures To IT Security Defining Business Priorities To Ensure Information Security Diagrams PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Presenting Risk Based Procedures To IT Security Defining Business Priorities To Ensure Information Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Risk Management, Transparent Communication, Standardized Incident. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
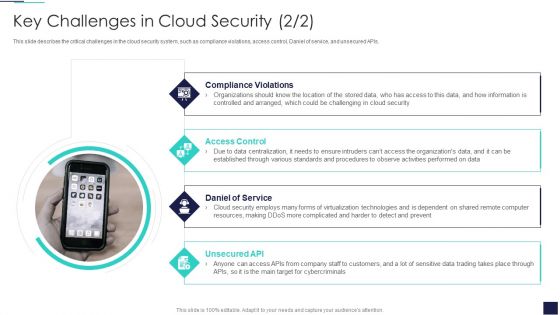
Cloud Information Security Key Challenges In Cloud Security Ppt Gallery Guidelines PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs. This is a Cloud Information Security Key Challenges In Cloud Security Ppt Gallery Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Compliance Violations, Access Control, Daniel Service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Threats End User Control Ppt Summary Ideas PDF
This slide represents the end-user threat in cloud security and how an organization needs to control user access and be aware of potential threats. This is a Cloud Information Security Cloud Security Threats End User Control Ppt Summary Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer List, Rival Organizations, Could Upload. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
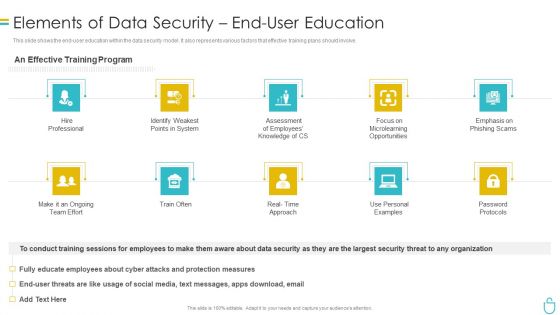
Information Security Elements Of Data Security End User Education Ppt Ideas Professional PDF
This slide shows the end user education within the data security model. It also represents various factors that effective training plans should involve. Presenting information security elements of data security end user education ppt ideas professional pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like system, opportunities, employees, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
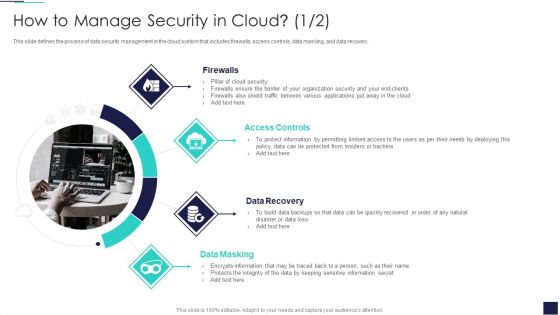
Cloud Information Security How To Manage Security In Cloud Ppt Ideas Example Topics PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting Cloud Information Security How To Manage Security In Cloud Ppt Ideas Example Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Controls, Data Recovery, Data Masking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
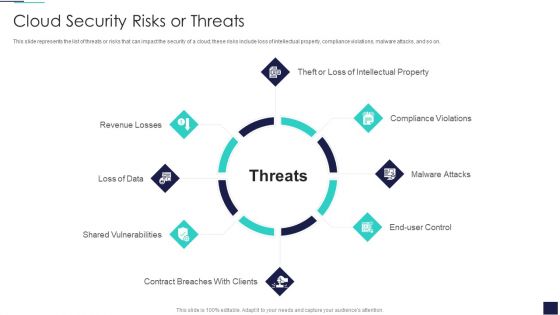
Cloud Information Security Cloud Security Risks Or Threats Ppt Model Clipart PDF
This slide represents the list of threats or risks that can impact the security of a cloud, these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting Cloud Information Security Cloud Security Risks Or Threats Ppt Model Clipart PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Shared Vulnerabilities, Malware Attacks, Compliance Violations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Threats Contract Breaches With Clients Background PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. This is a Cloud Information Security Cloud Security Threats Contract Breaches With Clients Background PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Could, Business Partners, Data Stored. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
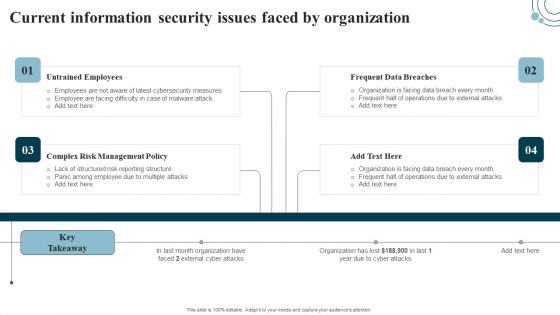
Developing IT Security Strategy Current Information Security Issues Faced By Organization Pictures PDF
The Developing IT Security Strategy Current Information Security Issues Faced By Organization Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Information Security How Is Automation Used In Data Security Ppt Model Graphics Template PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting information security how is automation used in data security ppt model graphics template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
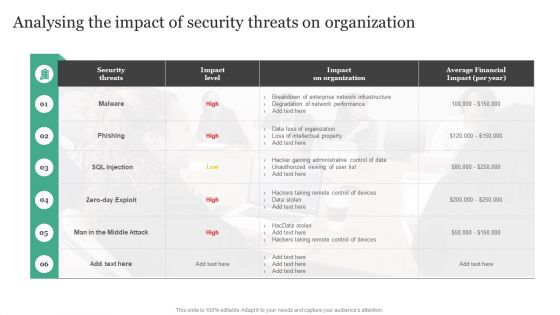
Analysing The Impact Of Security Threats On Organization Information Security Risk Administration Sample PDF
The Analysing The Impact Of Security Threats On Organization Information Security Risk Administration Sample PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
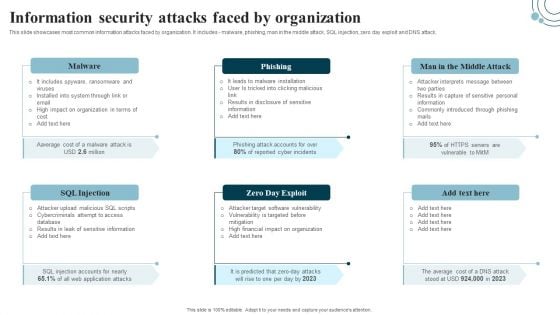
Developing IT Security Strategy Information Security Attacks Faced By Organization Rules PDF
This slide showcases most common information attacks faced by organization. It includes - malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Slidegeeks is here to make your presentations a breeze with Developing IT Security Strategy Information Security Attacks Faced By Organization Rules PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Enhancing Information Technology With Strategic Information Security And Governance Icons PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Enhancing Information Technology With Strategic Information Security And Governance Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Information Technology Strategy Role Of Chief Information Security Officer Rules PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. This is a information technology strategy role of chief information security officer rules pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information, stay informed, monthly reports. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
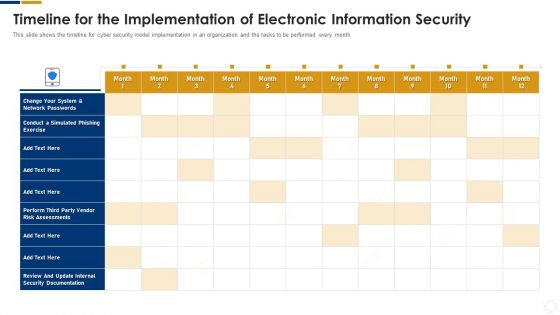
Cybersecurity Timeline For The Implementation Of Electronic Information Security Ppt Infographic Template Information PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative cybersecurity timeline for the implementation of electronic information security ppt infographic template information pdf bundle. Topics like security documentation, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
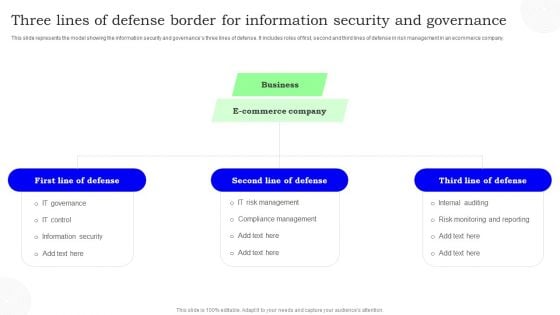
Three Lines Of Defense Border For Information Security And Governance Information PDF
This slide represents the model showing the information security and governances three lines of defense. It includes roles of first, second and third lines of defense in risk management in an ecommerce company. Persuade your audience using this Three Lines Of Defense Border For Information Security And Governance Information PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Defense, Commerce Company, Business. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
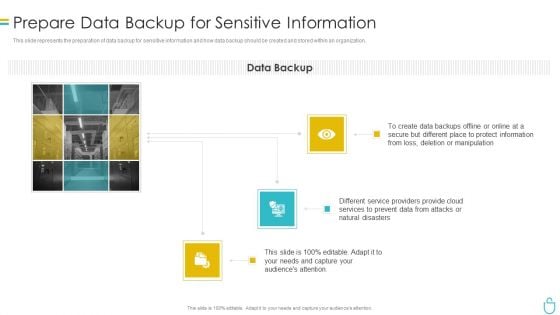
Information Security Prepare Data Backup For Sensitive Information Ppt Introduction PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a information security prepare data backup for sensitive information ppt introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect information, manipulation, services, natural disasters, secure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Systems Security And Risk Management Plan 30 60 90 Days Plan Information PDF
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Information Systems Security And Risk Management Plan 30 60 90 Days Plan Information PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

IT Security Roadmap In Powerpoint And Google Slides Cpb
Introducing our well designed IT Security Roadmap In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like IT Security Roadmap. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our IT Security Roadmap In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
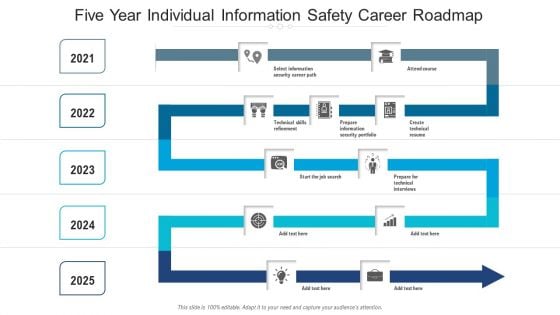
Five Year Individual Information Safety Career Roadmap Information
Presenting our innovatively structured five year individual information safety career roadmap information Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
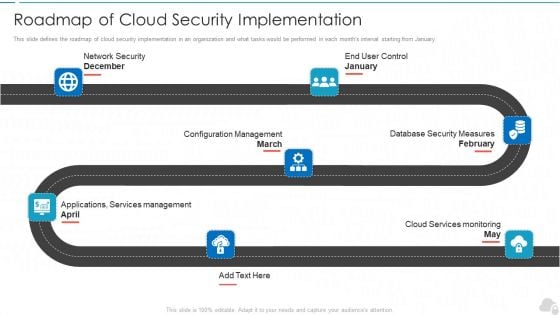
Roadmap Of Cloud Security Implementation Cloud Computing Security IT Ppt Outline Files PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. This is a roadmap of cloud security implementation cloud computing security it ppt outline files pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like configuration management, database security measures, cloud services monitoring, applications, services management, network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
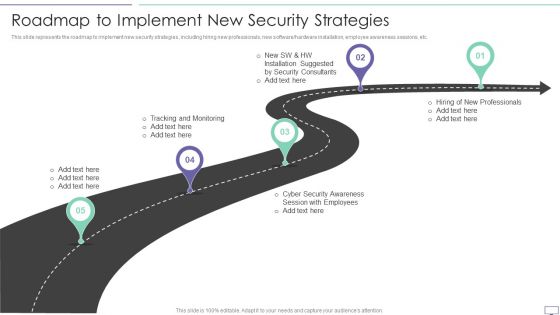
IT Security Hacker Roadmap To Implement New Security Strategies Professional PDF
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software hardware installation, employee awareness sessions, etc.This is a IT Security Hacker Roadmap To Implement New Security Strategies Professional PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Tracking And Monitoring, Security Awareness, Installation Suggested. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
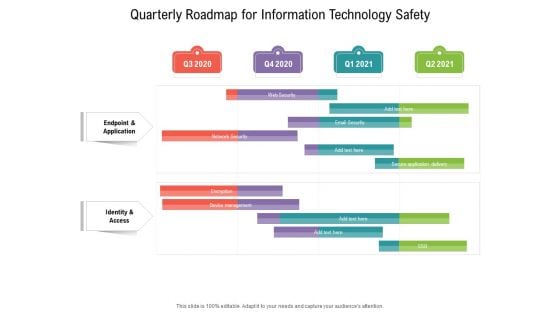
Quarterly Roadmap For Information Technology Safety Elements
Introducing our quarterly roadmap for information technology safety elements. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
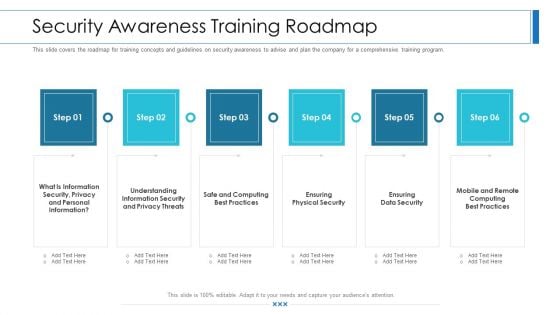
Workforce Security Realization Coaching Plan Security Awareness Training Roadmap Ppt Slides Visual Aids PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a workforce security realization coaching plan security awareness training roadmap ppt slides visual aids pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security, privacy threats, physical security, data security, security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness Training Roadmap Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a security awareness training roadmap hacking prevention awareness training for it security template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data security, physical security, privacy threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
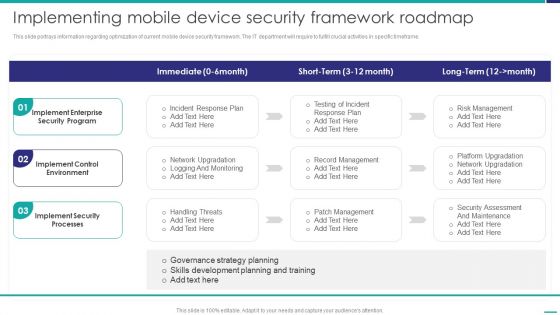
Implementing Mobile Device Security Framework Roadmap Mobile Device Security Management Infographics PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Deliver and pitch your topic in the best possible manner with this Implementing Mobile Device Security Framework Roadmap Mobile Device Security Management Infographics PDF. Use them to share invaluable insights on Implement Enterprise, Security Program, Implement Control and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
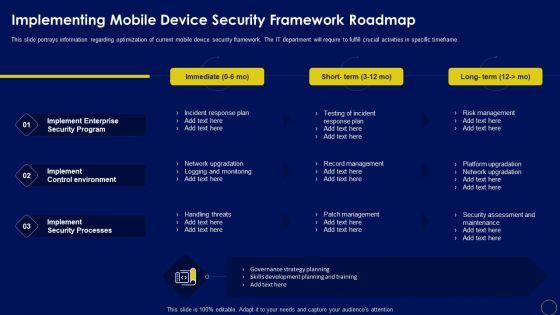
Implementing Mobile Device Security Framework Roadmap Business Mobile Device Security Sample PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. There are so many reasons you need a Implementing Mobile Device Security Framework Roadmap Business Mobile Device Security Sample PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Best Data Security Software Roadmap For Company Online Database Security Proposal Graphics PDF
Presenting this set of slides with name best data security software roadmap for company online database security proposal graphics pdf. This is a five stage process. The stages in this process are roadmap, company, online database security, 2016 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
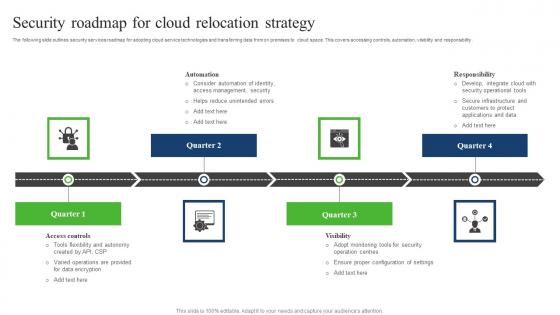
Security Roadmap For Cloud Relocation Strategy Sample Pdf
The following slide outlines security services roadmap for adopting cloud service technologies and transferring data from on premises to cloud space. This covers accessing controls, automation, visibility and responsibility. Showcasing this set of slides titled Security Roadmap For Cloud Relocation Strategy Sample Pdf. The topics addressed in these templates are Responsibility, Automation, Security Roadmap, Cloud Relocation Strategy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide outlines security services roadmap for adopting cloud service technologies and transferring data from on premises to cloud space. This covers accessing controls, automation, visibility and responsibility.
Roadmap Hacking Prevention Awareness Training For IT Security Brochure PDF
This is a roadmap hacking prevention awareness training for it security brochure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roadmap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Security Risk Management Plan Roadmap Themes PDF
This is a cyber security risk management plan roadmap themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roadmap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
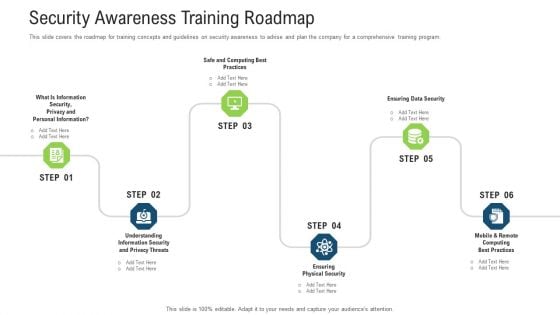
Security Awareness Training Roadmap Ppt Portfolio Demonstration PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a Security Awareness Training Roadmap Ppt Portfolio Demonstration Pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Damage Security Insurance Proposal Roadmap Ppt Layouts Infographics PDF
This is a damage security insurance proposal roadmap ppt layouts infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roadmap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
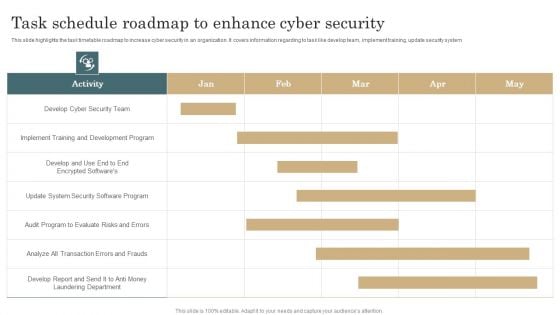
Task Schedule Roadmap To Enhance Cyber Security Template PDF
This slide highlights the task timetable roadmap to increase cyber security in an organization. It covers information regarding to task like develop team, implement training, update security system. Pitch your topic with ease and precision using this Task Schedule Roadmap To Enhance Cyber Security Template PDF. This layout presents information on Development Program, Implement Training, Evaluate Risks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
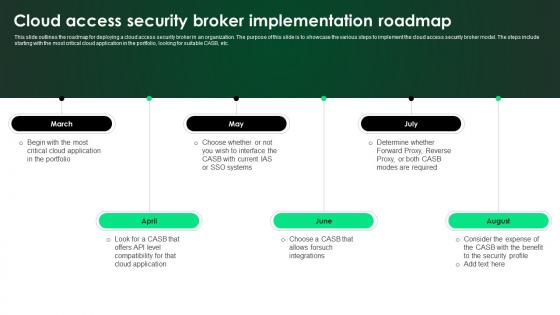
CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Welcome to our selection of the CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc.

Roadmap To Implement Tokenization For Data Security PPT Presentation
This slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc. Boost your pitch with our creative Roadmap To Implement Tokenization For Data Security PPT Presentation. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc.
Roadmap IT Security IT Ppt Pictures Deck PDF
Presenting roadmap it security it ppt pictures deck pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like roadmap, 2018 to 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Implementing Security Management Strategy To Mitigate Risk Roadmap Diagrams PDF
Presenting implementing security management strategy to mitigate risk roadmap diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































