Information Security Roadmap
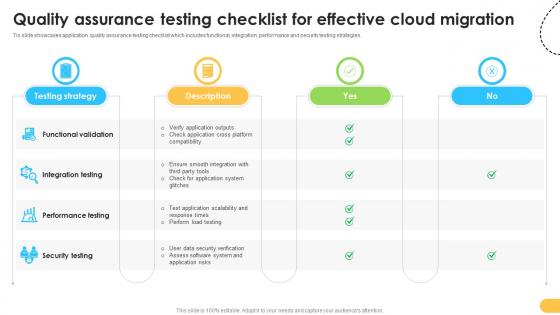
Quality Assurance Testing Checklist For Effective Data Migration From On Premises
Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies. The Quality Assurance Testing Checklist For Effective Data Migration From On Premises is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies.

Implement General Data Protection Regulation DT SS V
This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Find a pre-designed and impeccable Implement General Data Protection Regulation DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance.

New Website Launch Strategy Web Bug Testing For Improving Virtual Sales Clipart PDF
Mentioned slide provides insights into various testing strategies which can be implemented by web developers to deploy bug free applications. It includes testing strategies such as cross browser, accessibility, HTML and CSS, web security login, performance, and beta testing. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. New Website Launch Strategy Web Bug Testing For Improving Virtual Sales Clipart PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
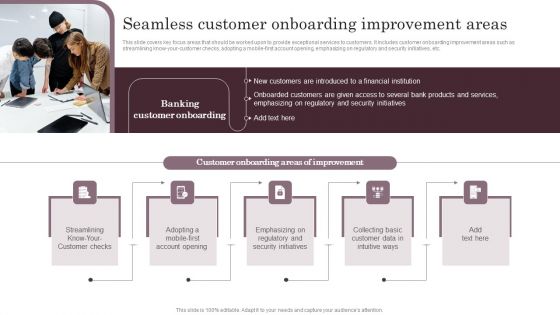
Omnichannel Services Solution In Financial Sector Seamless Customer Onboarding Graphics PDF
This slide covers key focus areas that should be worked upon to provide exceptional services to customers. It includes customer onboarding improvement areas such as streamlining know-your-customer checks, adopting a mobile-first account opening, emphasizing on regulatory and security initiatives, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Omnichannel Services Solution In Financial Sector Seamless Customer Onboarding Graphics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
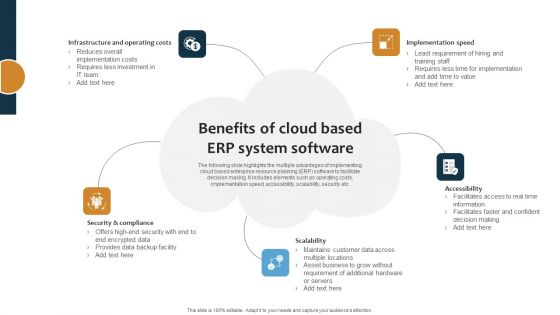
Improving Business Procedures Enterprise Resource Planning System Benefits Of Cloud Based Erp Inspiration PDF
The following slide highlights the multiple advantages of implementing cloud based enterprise resource planning ERP software to facilitate decision making. It includes elements such as operating costs, implementation speed, accessibility, scalability, security etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Improving Business Procedures Enterprise Resource Planning System Benefits Of Cloud Based Erp Inspiration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
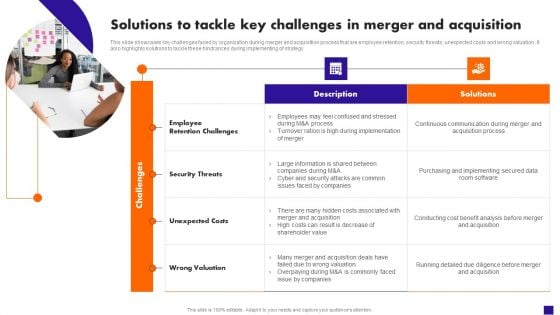
Solutions To Tackle Key Challenges In Merger And Acquisition Portrait PDF
This slide showcases key challenges faced by organization during merger and acquisition process that are employee retention, security threats, unexpected costs and wrong valuation. It also highlights solutions to tackle these hindrances during implementing of strategy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Solutions To Tackle Key Challenges In Merger And Acquisition Portrait PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
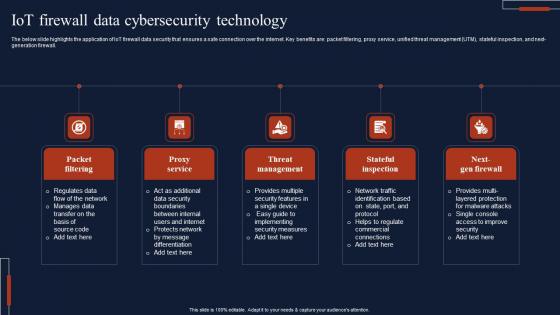
IOT Firewall Data Cybersecurity Technology Brochure Pdf
The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall. Showcasing this set of slides titled IOT Firewall Data Cybersecurity Technology Brochure Pdf The topics addressed in these templates are Packet Filtering, Proxy Service, Threat Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The below slide highlights the application of IoT firewall data security that ensures a safe connection over the internet. Key benefits are packet filtering, proxy service, unified threat management UTM, stateful inspection, and next-generation firewall.
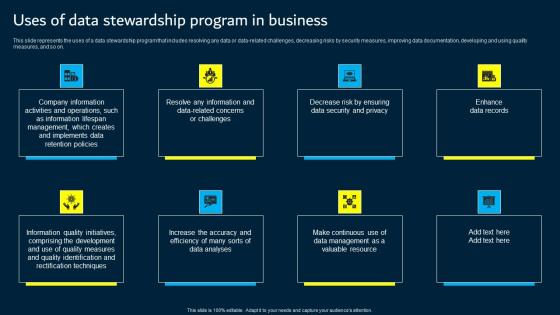
Uses Of Data Stewardship Program In Business Data Custodianship Structure Pdf
This slide represents the uses of a data stewardship program that includes resolving any data or data related challenges, decreasing risks by security measures, improving data documentation, developing and using quality measures, and so on. Do you know about Slidesgeeks Uses Of Data Stewardship Program In Business Data Custodianship Structure Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the uses of a data stewardship program that includes resolving any data or data related challenges, decreasing risks by security measures, improving data documentation, developing and using quality measures, and so on.

The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory.
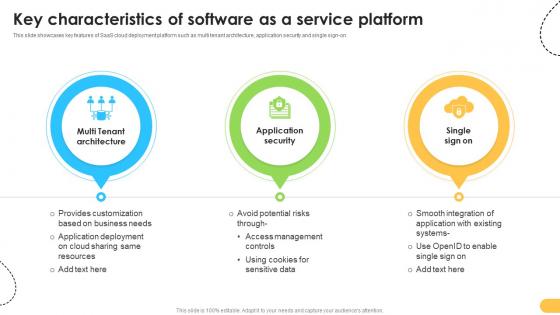
Key Characteristics Of Software As A Service Platform Data Migration From On Premises
This slide showcases key features of SaaS cloud deployment platform such as multi tenant architecture, application security and single sign-on. Retrieve professionally designed Key Characteristics Of Software As A Service Platform Data Migration From On Premises to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases key features of SaaS cloud deployment platform such as multi tenant architecture, application security and single sign-on.

Ukraine Vs Russia Examining War Timeline Highlighting Major Events Occurred Cont Sample PDF
This slide provides information regarding Russia Ukraine war timeline highlighting major events occurred in FY2022 and FY2021 in terms of initiation of military training by Russian soldiers, security assistance to Ukraine by US, etc. . Deliver an awe inspiring pitch with this creative Ukraine Vs Russia Examining War Timeline Highlighting Major Events Occurred Cont Sample PDF bundle. Topics like US Tracked Unusual Russian, Russia Initiated Military Maneuvers, Controlled Crimea editable template. It is available for immediate download depending on the needs and requirements of the user.
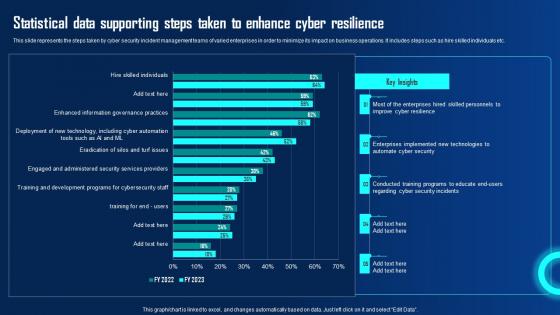
Statistical Data Supporting Steps Taken To Enhance Cyber Ppt Powerpoint Presentation File Outline Pdf
This slide represents the steps taken by cyber security incident management teams of varied enterprises in order to minimize its impact on business operations. It includes steps such as hire skilled individuals etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Statistical Data Supporting Steps Taken To Enhance Cyber Ppt Powerpoint Presentation File Outline Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents the steps taken by cyber security incident management teams of varied enterprises in order to minimize its impact on business operations. It includes steps such as hire skilled individuals etc.

Electronic Playbook Digital Transformation Trends We Can Adopt Microsoft PDF
The following slide displays the key trends that can be adopted by the organization, these trends can impact the transformation journey can help in achieving operational excellence. These trends can be usage of Hyperautomation, cyber security tools, usage of AI etc.Presenting electronic playbook digital transformation trends we can adopt microsoft pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like digital transformation trends we can adopt In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
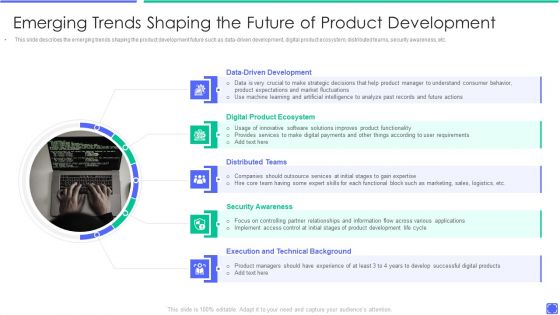
Best Techniques To Enhance New Product Management Efficiency Emerging Trends Shaping Inspiration PDF
This slide describes the emerging trends shaping the product development future such as data driven development, digital product ecosystem, distributed teams, security awareness, etc. Presenting best techniques to enhance new product management efficiency emerging trends shaping inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like data driven development, digital product ecosystem, distributed teams. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
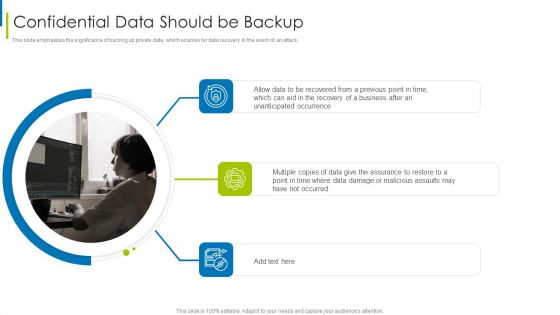
Cyber Terrorism Assault Confidential Data Should Be Backup Brochure PDF
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack.Presenting cyber terrorism assault confidential data should be backup brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cyber Security Assessment, Limited Access Privileges, Employee Training In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
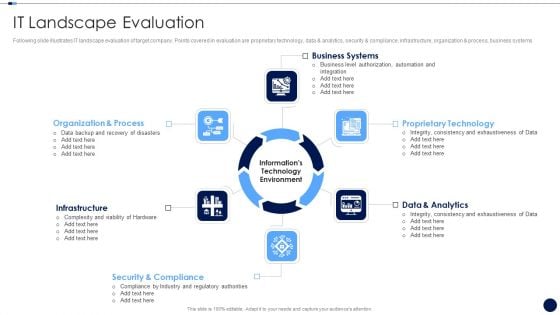
Merger And Acquisition Due Diligence Checklist IT Landscape Evaluation Designs PDF
Following slide illustrates IT landscape evaluation of target company. Points covered in evaluation are proprietary technology, data and analytics, security and compliance, infrastructure, organization and process, business systems Presenting merger and acquisition due diligence checklist it landscape evaluation designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like key financial highlights In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack Cyber Officials Urge Agencies To Armor Download PDF
This slide represents that officials from the Department of Homeland Security have urged agencies to prepare for possible Russian cyberattacks, and CISA has amended its shields up guidelines.Presenting data wiper spyware attack cyber officials urge agencies to armor download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like warning government, corporations to be cautious, russian cyberattacks In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
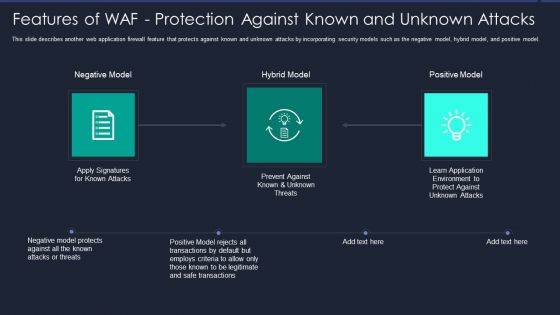
Web App Firewall Services IT Features Of WAF Protection Against Known Clipart PDF
This slide describes another web application firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. Presenting web app firewall services it features of waf protection against known clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like negative model, hybrid model, positive model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack Should We Be Concerned About Russian Cyberattacks Professional PDF
This slide shows that US citizens should not be concerned about Russian cyberattacks as nothing has happened so far. However, the US Department of Homeland Security issued a warning to organizations to look for Russian cyberattacks.Presenting data wiper spyware attack should we be concerned about russian cyberattacks professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like already been targeted, methods america, russians could impose In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
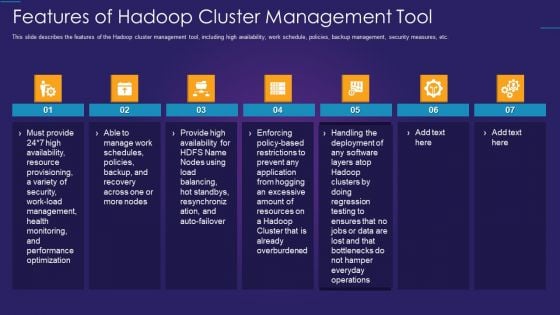
Apache Hadoop IT Features Of Hadoop Cluster Management Tool Sample PDF
This slide describes the features of the Hadoop cluster management tool, including high availability, work schedule, policies, backup management, security measures, etc.Presenting apache hadoop it features of hadoop cluster management tool sample pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like resource provisioning, performance optimization, provide high availability In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Features Of WAF Protection Against Known And Unknown Attacks WAF Platform Inspiration PDF
This slide describes another web application firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. Presenting Features Of WAF Protection Against Known And Unknown Attacks WAF Platform Inspiration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Hybrid Model, Negative Model, Positive Model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
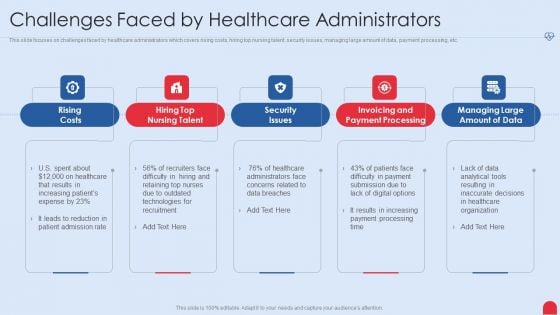
Enhancing Hospital Software System Challenges Faced By Healthcare Administrators Clipart PDF
This slide focuses on challenges faced by healthcare administrators which covers rising costs, hiring top nursing talent, security issues, managing large amount of data, payment processing, etc. Presenting enhancing hospital software system challenges faced by healthcare administrators clipart pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like challenges faced by healthcare administrators. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
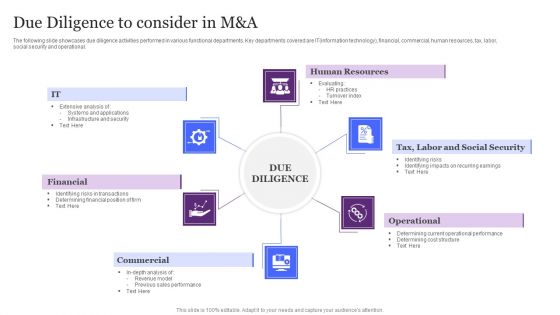
Due Diligence To Consider In M And A Ppt Summary Model PDF
The following slide showcases due diligence activities performed in various functional departments. Key departments covered are IT information technology, financial, commercial, human resources, tax, labor, social security and operational. Persuade your audience using this Due Diligence To Consider In M And A Ppt Summary Model PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Human Resources, Operational, Financial, Commercial. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Construction Project Instructions Playbook Essential Guidelines To Ensure Workers Safety Background PDF
This slide provides information regarding essential guidelines to ensure workers safety with details about workers clothing and PPE, site protection and security and tools and equipment. Create an editable Construction Project Instructions Playbook Essential Guidelines To Ensure Workers Safety Background PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Construction Project Instructions Playbook Essential Guidelines To Ensure Workers Safety Background PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
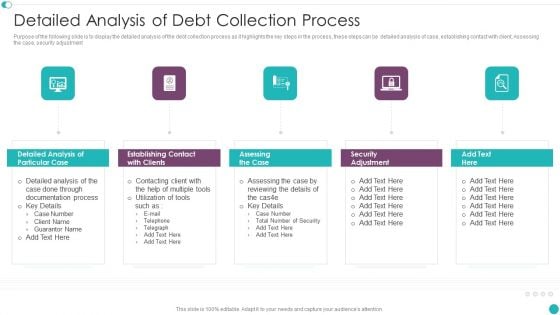
Credit Management And Recovery Policies Detailed Analysis Of Debt Collection Process Sample PDF
Purpose of the following slide is to display the detailed analysis of the debt collection process as it highlights the key steps in the process, these steps can be detailed analysis of case, establishing contact with client, Assessing the case, security adjustment. Presenting Credit Management And Recovery Policies Detailed Analysis Of Debt Collection Process Sample PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Detailed Analysis, Establishing Contact, Assessing Case. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
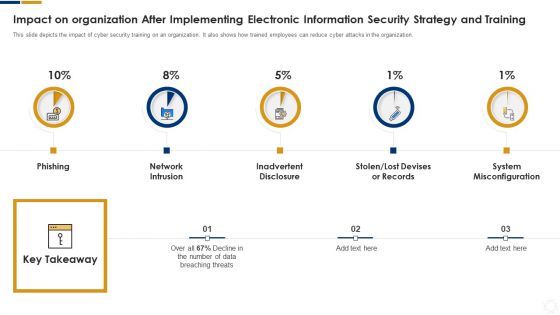
Cybersecurity Impact On Organization After Implementing Ppt Summary Influencers PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Presenting cybersecurity impact on organization after implementing ppt summary influencers pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network intrusion, inadvertent disclosure, system misconfiguration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies Of Private Wealth Administration System Professional PDF
The following slide showcases strategies that help to achieve financial security and growth in wealth. It presents information related to debt management, insurance policies, budgeting, etc. Persuade your audience using this Strategies Of Private Wealth Administration System Professional PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Budgeting, Debt Management, Insurance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
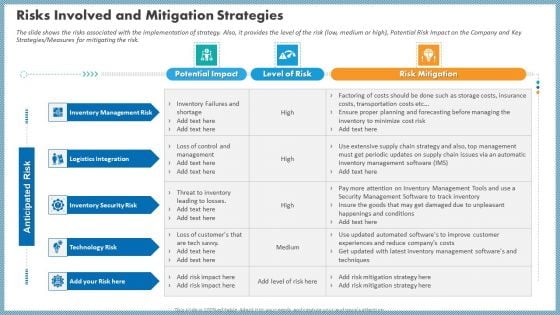
Case Competition Inflated Fuel Price In Logistics Firm Risks Involved And Mitigation Strategies Rules PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies Measures for mitigating the risk. Presenting case competition inflated fuel price in logistics firm risks involved and mitigation strategies rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like management risk, logistics integration, inventory security risk, potential impact, level of risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Computer Virtualization Managing End User Computing In The Company Topics PDF
This slide represents how we will manage to end user computing and it includes to adopt centralized application deployment, preparation for changing job roles, know users and so on.Presenting Computer Virtualization Managing End User Computing In The Company Topics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Security Implications, Storage Consumption, Experience Server. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
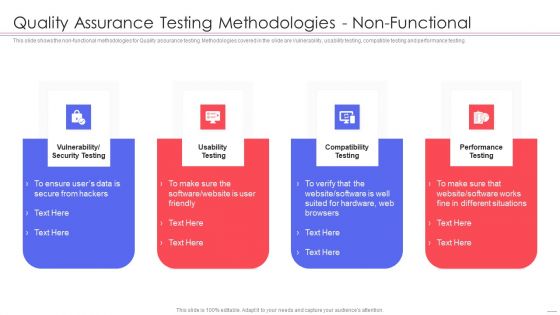
Agile QA Procedure Quality Assurance Testing Methodologies Non Functional Download PDF
This slide shows the non-functional methodologies for Quality assurance testing. Methodologies covered in the slide are Vulnerability, usability testing, compatible testing and performance testing. Presenting agile qa procedure quality assurance testing methodologies non functional download pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like vulnerability security testing, compatibility testing, performance testing. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Areas Where ML Will Deliver Strong Outcomes For The Organization Icons PDF
This template covers the outcomes derived by the machine learning operations for the organization such as Fraud detection and prevention, Security detection and prevention, Optimization research etc.Presenting Areas Where ML Will Deliver Strong Outcomes For The Organization Icons PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Detection And Prevention, Optimization, Detection And Regulation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
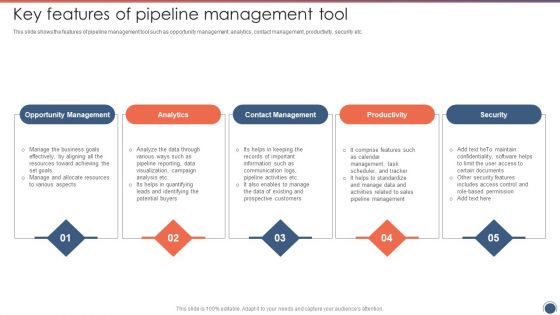
Key Features Of Pipeline Management Tool Sales Funnel Management Strategies To Increase Sales Microsoft PDF
This slide shows the features of pipeline management tool such as opportunity management, analytics, contact management, productivity, security etc. Presenting Key Features Of Pipeline Management Tool Sales Funnel Management Strategies To Increase Sales Microsoft PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Opportunity Management, Contact Management, Productivity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
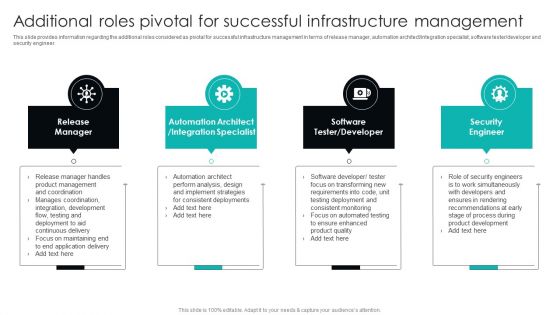
Additional Roles Pivotal For Successful Infrastructure Management Summary PDF
This slide provides information regarding the additional roles considered as pivotal for successful infrastructure management in terms of release manager, automation architect integration specialist, software tester developer and security engineer. Find a pre designed and impeccable Additional Roles Pivotal For Successful Infrastructure Management Summary PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

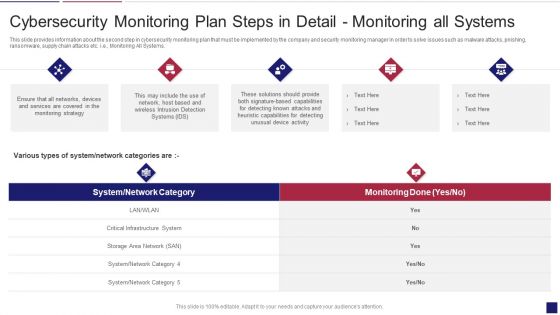
Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems Introduction PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring all systems introduction pdf bundle. Topics like system network category, monitoring done can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
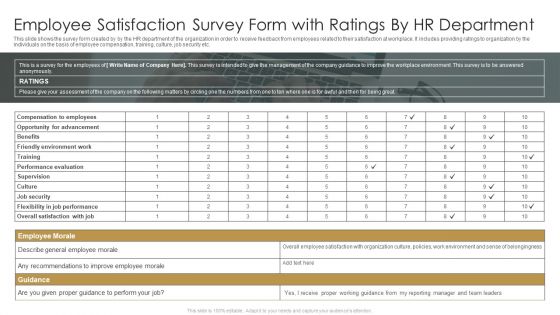
Employee Satisfaction Survey Form With Ratings By HR Department Ppt Infographic Template Topics PDF
This slide shows the survey form created by by the HR department of the organization in order to receive feedback from employees related to their satisfaction at workplace. It includes providing ratings to organization by the individuals on the basis of employee compensation, training, culture, job security etc. Pitch your topic with ease and precision using this Employee Satisfaction Survey Form With Ratings By HR Department Ppt Infographic Template Topics PDF. This layout presents information on Compensation To Employees, Opportunity For Advancement, Performance Evaluation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Analysis Brochure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring analysis brochure pdf bundle. Topics like cybersecurity monitoring plan steps in detail review and risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Systems Graphics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring All Systems. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring systems graphics pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Timing Clipart PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring timing clipart pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Monitoring Plan Steps In Detail Providing Resilient And Synchronized Timing Background PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this cybersecurity monitoring plan steps in detail providing resilient and synchronized timing background pdf. Use them to share invaluable insights on monitoring and analysis, incident response, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Methods To Develop Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis Structure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Review and Risk Analysis. Deliver an awe inspiring pitch with this creative methods to develop cybersecurity monitoring plan steps in detail review and risk analysis structure pdf bundle. Topics like potential consequence, low, medium, high can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
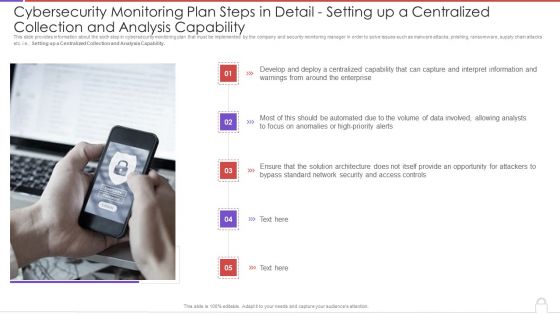
Cybersecurity Monitoring Plan Steps In Detail Setting Up A Centralized Collection And Elements PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Setting up a Centralized Collection and Analysis Capability. This is a cybersecurity monitoring plan steps in detail setting up a centralized collection and elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interpret information, high priority alerts, analysts, access controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
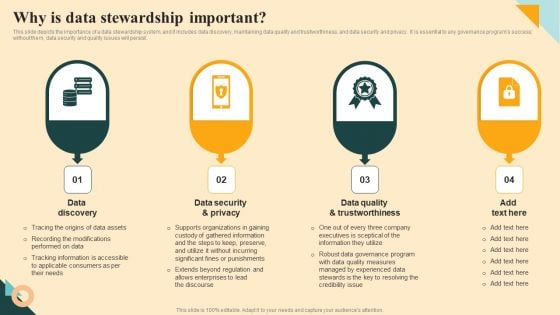
Why Is Data Stewardship Important Sample PDF
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance programs success without them, data security and quality issues will persist. Slidegeeks has constructed Why Is Data Stewardship Important Sample PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

CASB 2 0 IT 30 60 90 Days Plan To Deploy CASB Model
This slide represents the 30-0-90 days plan to implement the cloud access security broker model in an organization. The purpose of this slide is to showcase the various steps to be taken to deploy CASB at the interval every 30 days. Boost your pitch with our creative CASB 2 0 IT 30 60 90 Days Plan To Deploy CASB Model. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the 30-0-90 days plan to implement the cloud access security broker model in an organization. The purpose of this slide is to showcase the various steps to be taken to deploy CASB at the interval every 30 days.
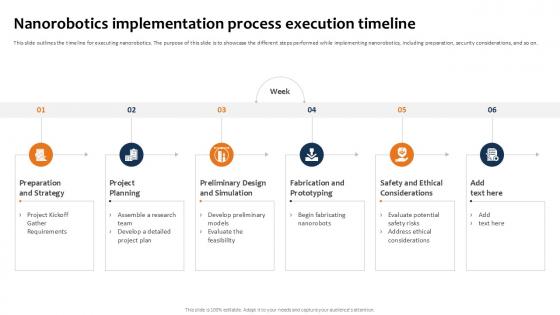
Nanorobotics Implementation Building The Future Of Robotic Ppt Slide
This slide outlines the timeline for executing nanorobotics. The purpose of this slide is to showcase the different steps performed while implementing nanorobotics, including preparation, security considerations, and so on.The Nanorobotics Implementation Building The Future Of Robotic Ppt Slide is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlines the timeline for executing nanorobotics. The purpose of this slide is to showcase the different steps performed while implementing nanorobotics, including preparation, security considerations, and so on.

Digital Project Management Strategies Significance Of Digital Tools In Project Management
The purpose of the mentioned slide is to illustrate the importance of incorporating digital solutions in project management. It includes advantages such as efficiency and automation, centralized information, task monitoring, and security and access control. Find a pre-designed and impeccable Digital Project Management Strategies Significance Of Digital Tools In Project Management. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. The purpose of the mentioned slide is to illustrate the importance of incorporating digital solutions in project management. It includes advantages such as efficiency and automation, centralized information, task monitoring, and security and access control.

Need Of Implementing Ble Technique For Asset RFID Solutions For Asset Traceability Clipart Pdf
This slide covers key benefits of implementing Bluetooth low energy method in asset tracking and management. It involves advantages such as high return on investment, enhanced security and high broadcast capacity. The Need Of Implementing Ble Technique For Asset RFID Solutions For Asset Traceability Clipart Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide covers key benefits of implementing Bluetooth low energy method in asset tracking and management. It involves advantages such as high return on investment, enhanced security and high broadcast capacity.
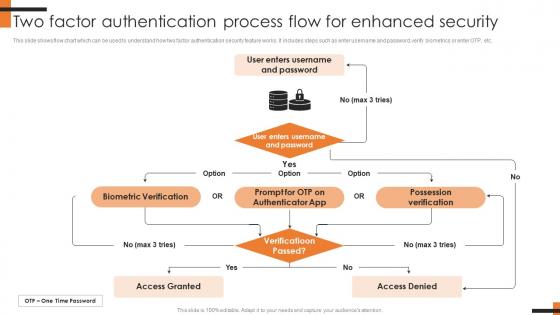
Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. The Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
Zero Trust Model Zero Trust Network Access Performance Tracking
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Model Zero Trust Network Access Performance Tracking is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.
Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow.

Biomedical Technology Role For Environment Sustainability Topics PDF
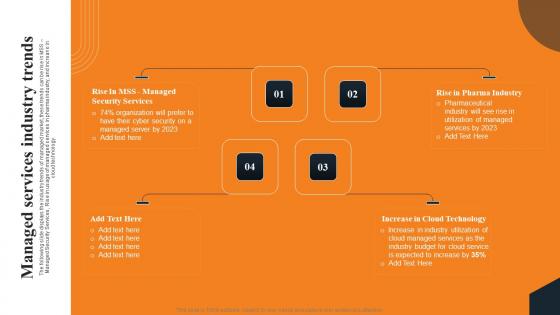
Managed Services Industry Trends Layered Pricing Strategy For Managed Services Brochure Pdf
The following slide displays the industry trends of managed market, these trends can be rise in MSS Managed Security Services, Rise in usage of managed services in pharma industry, and increase in cloud technology. This modern and well arranged Managed Services Industry Trends Layered Pricing Strategy For Managed Services Brochure Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The following slide displays the industry trends of managed market, these trends can be rise in MSS Managed Security Services, Rise in usage of managed services in pharma industry, and increase in cloud technology.
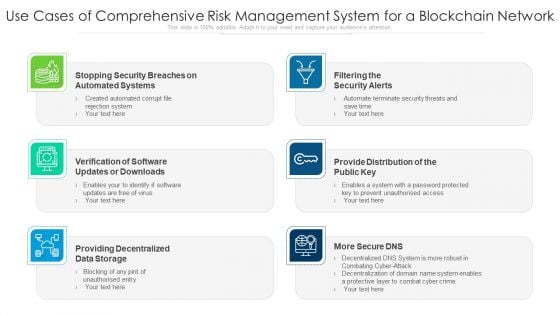
Use Cases Of Comprehensive Risk Management System For A Blockchain Network Ppt PowerPoint Presentation Outline Background Designs PDF
Presenting use cases of comprehensive risk management system for a blockchain network ppt powerpoint presentation outline background designs pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including filtering the security alerts, provide distribution of the public key, providing decentralized data storage. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
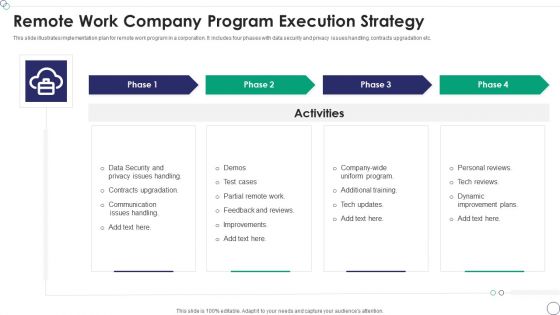
Remote Work Company Program Execution Strategy Rules PDF
This slide illustrates implementation plan for remote work program in a corporation. It includes four phases with data security and privacy issues handling, contracts upgradation etc.Presenting Remote Work Company Program Execution Strategy Rules PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Contracts Upgradation, Communication Issues Handling, Dynamic Improvement Plans This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
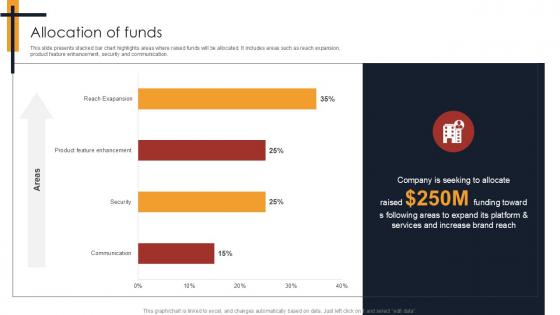
Allocation Of Funds Writing Enhancement Software Pitch Deck PPT Template
This slide presents stacked bar chart highlights areas where raised funds will be allocated. It includes areas such as reach expansion, product feature enhancement, security and communication. The Allocation Of Funds Writing Enhancement Software Pitch Deck PPT Template is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide presents stacked bar chart highlights areas where raised funds will be allocated.It includes areas such as reach expansion, product feature enhancement, security and communication.
Interconnected Functions Of Cybersecurity Resilience Framework Icons PDF
The slide showcases the interconnected functions of a framework used to guide the organizations security measures. It covers identify, protect, detect, respond and recover. Presenting Interconnected Functions Of Cybersecurity Resilience Framework Icons PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify, Protect, Detect. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
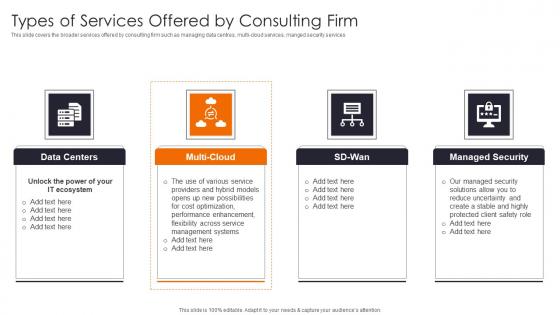
Types Of Services Offered Enhancing Workload Efficiency Through Cloud Architecture Introduction Pdf
This slide covers the broader services offered by consulting firm such as managing data centres, multi cloud services, manged security services If you are looking for a format to display your unique thoughts, then the professionally designed Types Of Services Offered Enhancing Workload Efficiency Through Cloud Architecture Introduction Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Types Of Services Offered Enhancing Workload Efficiency Through Cloud Architecture Introduction Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers the broader services offered by consulting firm such as managing data centres, multi cloud services, manged security services
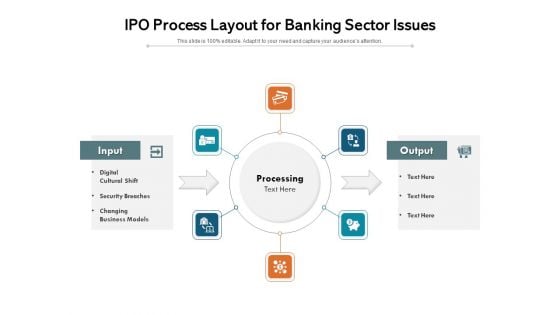
IPO Process Layout For Banking Sector Issues Ppt PowerPoint Presentation Show Design Templates PDF
Presenting ipo process layout for banking sector issues ppt powerpoint presentation show design templates pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including processing, output, input, digital cultural shift, security breaches, changing business models. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
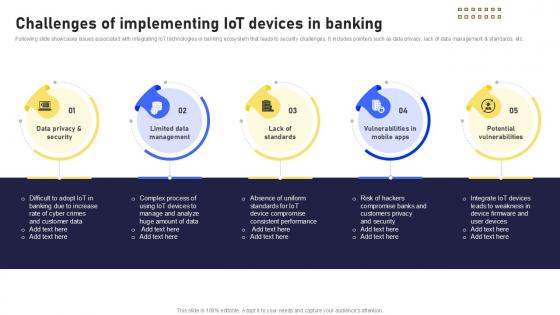
Challenges Of Implementing Banking Future With IoT Ppt Powerpoint IoT SS V
Following slide showcases issues associated with integrating IoT technologies in banking ecosystem that leads to security challenges. It includes pointers such as data privacy, lack of data management and standards, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Challenges Of Implementing Banking Future With IoT Ppt Powerpoint IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Following slide showcases issues associated with integrating IoT technologies in banking ecosystem that leads to security challenges. It includes pointers such as data privacy, lack of data management and standards, etc.

Visionary Guide To Blockchain Scope Of Using Blockchain Technology In Cloud BCT SS V
This slide mentions the scope of integrating blockchain technology in cloud computing. It includes elevated security measures, immutable data integrity, decentralization and data recovery or backup. Get a simple yet stunning designed Visionary Guide To Blockchain Scope Of Using Blockchain Technology In Cloud BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Visionary Guide To Blockchain Scope Of Using Blockchain Technology In Cloud BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide mentions the scope of integrating blockchain technology in cloud computing. It includes elevated security measures, immutable data integrity, decentralization and data recovery or backup.


 Continue with Email
Continue with Email

 Home
Home


































