Information Security

Types Of Data Breach Ppt PowerPoint Presentation Inspiration Ideas PDF
Presenting this set of slides with name types of data breach ppt powerpoint presentation inspiration ideas pdf. This is a five stage process. The stages in this process are inadequate cyber secure technology, lack of skilled human resource, security projects may fail if they are not financially supported adequately, security program is not aligned to business objective . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
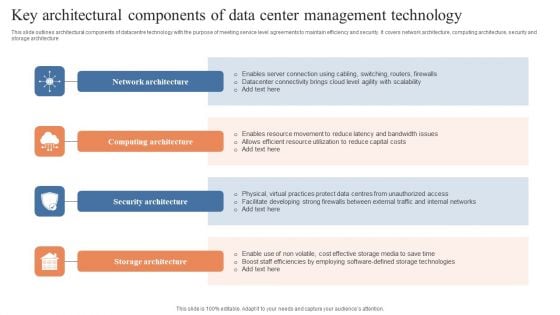
Key Architectural Components Of Data Center Management Technology Introduction PDF
This slide outlines architectural components of datacentre technology with the purpose of meeting service level agreements to maintain efficiency and security. It covers network architecture, computing architecture, security and storage architecture. Presenting Key Architectural Components Of Data Center Management Technology Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Network Architecture, Computing Architecture, Security Architecture. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
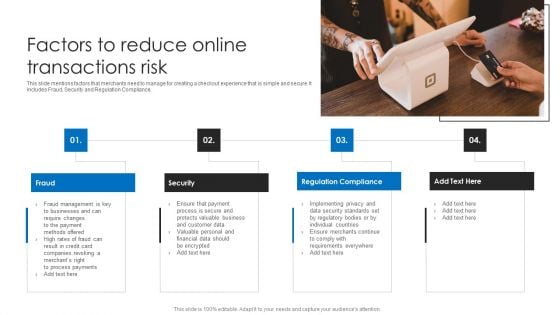
Factors To Reduce Online Transactions Risk Ppt Ideas Graphics Design PDF
This slide mentions factors that merchants need to manage for creating a checkout experience that is simple and secure. It includes Fraud, Security and Regulation Compliance. Presenting Factors To Reduce Online Transactions Risk Ppt Ideas Graphics Design PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Fraud, Security, Regulation Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Strategies For Data Protection And Privacy Rules PDF
The following slide showcases some techniques to ensure data security and privacy. It includes elements such as authentication, data encryption, network security, access controls etc. Persuade your audience using this Key Strategies For Data Protection And Privacy Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Data Encryption, Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
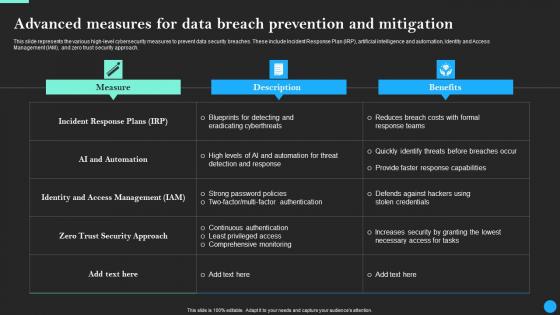
Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.
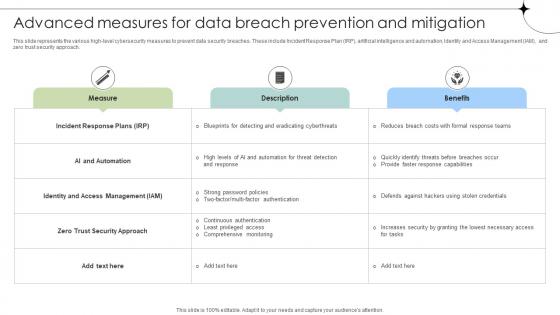
Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.

Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.
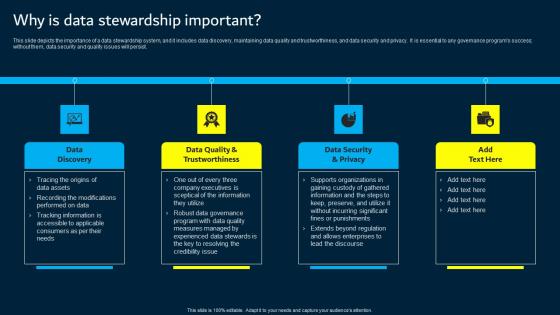
Why Is Data Stewardship Important Data Custodianship Formats Pdf
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance program s success without them, data security and quality issues will persist. Boost your pitch with our creative Why Is Data Stewardship Important Data Custodianship Formats Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance program s success without them, data security and quality issues will persist.
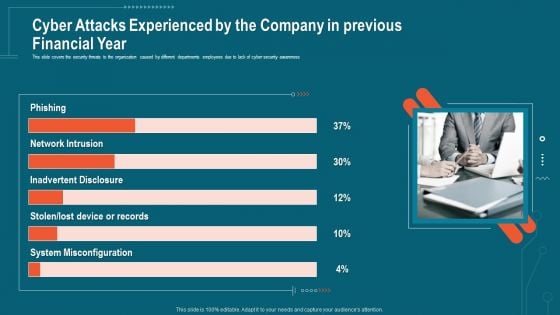
Companys Data Safety Recognition Cyber Attacks Experienced By The Company In Previous Financial Year Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. This is a companys data safety recognition cyber attacks experienced by the company in previous financial year sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system misconfiguration, inadvertent disclosure, network intrusion. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF
The following slide highlights the steps of cyber security in organisation depicting network security, awareness, malware, external media, configuration, user privilege, incident management, monitoring and distant working. Presenting Steps Of Digital Risk Assessment In Organisation Ppt Infographics Templates PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Network Security, Awareness, Malware, External Media. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
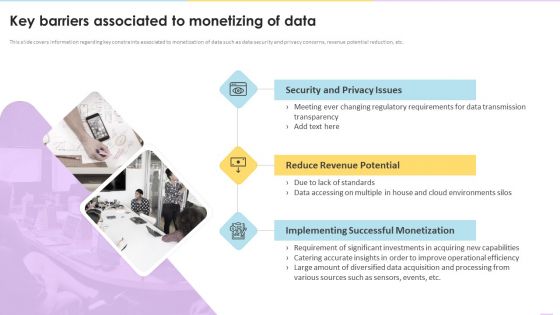
Data Valuation And Monetization Key Barriers Associated To Monetizing Of Data Sample PDF
This slide covers information regarding key constraints associated to monetization of data such as data security and privacy concerns, revenue potential reduction, etc.Presenting Data Valuation And Monetization Key Barriers Associated To Monetizing Of Data Sample PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Security Privacy, Reduce Revenue, Implementing Successful. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF
The following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Access Control, Patch Management, Security Solution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Software Development And IT Operations Infrastructure Development IT Determine Additional Roles Pivotal Structure PDF
This slide provides information regarding the additional roles considered as pivotal for successful DevOps in terms of software tester or developer, security engineer and experience assurance professional. Presenting software development and it operations infrastructure development it determine additional roles pivotal structure pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like software tester or developer, security engineer, experience assurance professional. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Stock Photo Ball With Big Data Text For Data Protection Concept PowerPoint Slide
Graphic of ball with big data text has been used to craft this power point template. This image template contains the concept of data protection. Use this image for data security related topics in any presentation.
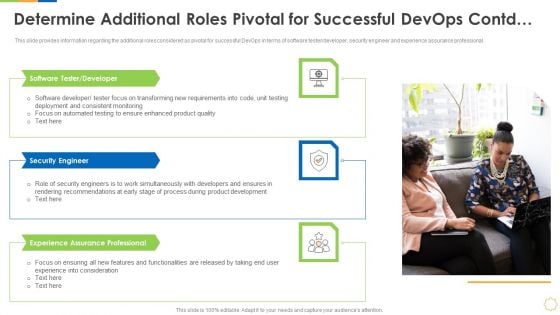
Infrastructure As Code For Devops Growth IT Determine Additional Roles Pivotal For Successful Devops Contd Clipart PDF
This slide provides information regarding the additional roles considered as pivotal for successful DevOps in terms of software tester or developer, security engineer and experience assurance professional. Presenting infrastructure as code for devops growth it determine additional roles pivotal for successful devops contd clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like software tester or developer, security engineer, experience assurance professional. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Advantages Of IT Communication For Businesses Themes PDF
The following slide highlights various advantages of information and communication technology to improve business communication globally. It includes components such as fast communication, cost effectiveness and IT security etc. Presenting Advantages Of IT Communication For Businesses Themes PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Fast Communication, Cost Effectiveness, Improved It Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF
The following slide highlights the process of cyber security asset management depicting four steps which include asset inventory, synchronization, security gaps and response to save assets and mitigate the risk in minimum time. Presenting Process Of Digital Risk Assessment Management Ppt Summary Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Asset Inventory, Synchronization, Response, Security Gaps. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Formulating Product Development Action Plan To Enhance Client Experience Emerging Trends Shaping Infographics PDF
This slide describes the emerging trends shaping the product development future such as data-driven development, digital product ecosystem, distributed teams, security awareness, etc. This is a formulating product development action plan to enhance client experience emerging trends shaping infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data driven development, digital product ecosystem, distributed teams, security awareness, execution and technical background. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
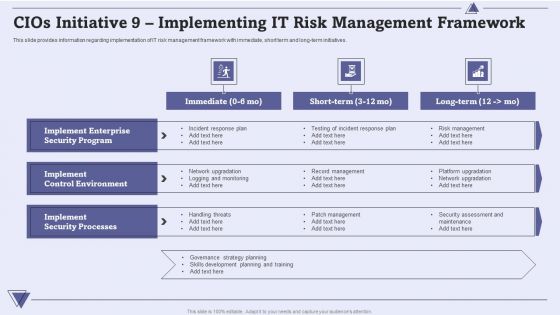
CIO For IT Cost Optimization Techniques Cios Initiative 9 Implementing IT Risk Management Framework Graphics PDF
This slide provides information regarding implementation of IT risk management framework with immediate, short term and long-term initiatives. Presenting CIO For IT Cost Optimization Techniques Cios Initiative 9 Implementing IT Risk Management Framework Graphics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Implement Control Environment, Implement Enterprise Security, Implement Security Processes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Market Trends Sample PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. Presenting continuous development evaluation plan eliminate cyber attacks current market trends sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like increasing digitization of sensitive data, general data protection laws, data breach notification laws. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
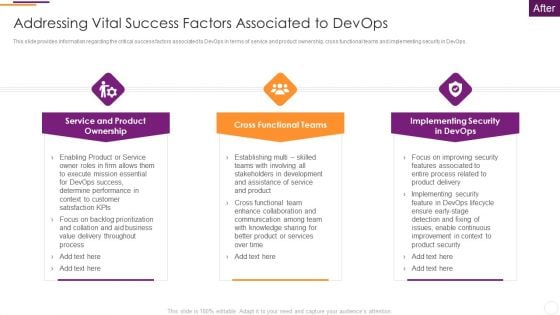
Key Parameters To Establish Overall Devops Value IT Addressing Vital Success Factors Associated To Devops Themes PDF
This slide provides information regarding the critical success factors associated to DevOps in terms of service and product ownership, cross functional teams and implementing security in DevOps. Presenting key parameters to establish overall devops value it addressing vital success factors associated to devops themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like service and product ownership, cross functional teams, implementing security in devops. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
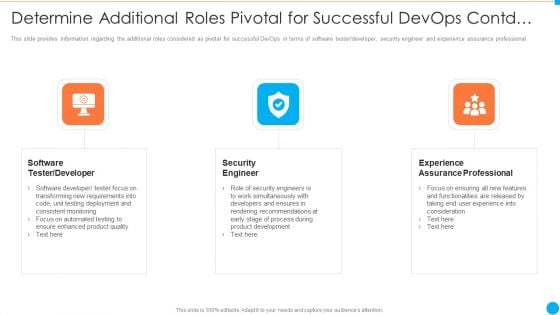
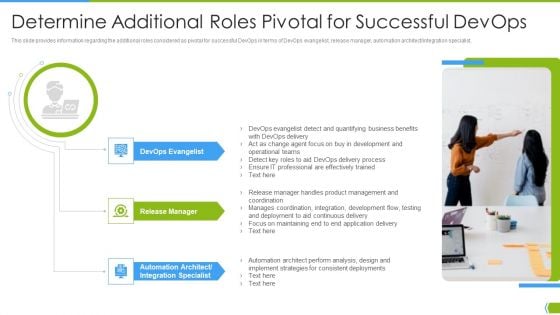
Determine Additional Roles Pivotal For Successful Devops Contd IT Infrastructure By Executing Devops Approach Elements PDF
This slide provides information regarding the additional roles considered as pivotal for successful DevOps in terms of software tester or developer, security engineer and experience assurance professional. Presenting determine additional roles pivotal for successful devops contd it infrastructure by executing devops approach elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like software tester or developer, security engineer, experience assurance professional. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Components Critical To Devops Viability IT Determine New Roles Pivotal Themes PDF
This slide provides information regarding the new roles considered as pivotal for successful DevOps in terms of software tester or developer, security engineer and experience assurance professional. Presenting key components critical to devops viability it determine new roles pivotal themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like software tester or developer, security engineer, experience assurance professional. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Partnership Tactical Plan To Promote Expansion And Value Formation Methods Of Payment For Merger And Acquisition Activity Guidelines PDF
This slide provides information about the payment methods for an M and A activity or transaction such as stock purchase, asset purchase, cash offering and security offerings. Presenting partnership tactical plan to promote expansion and value formation methods of payment for merger and acquisition activity guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security offering, cash offering, asset purchase, stock purchase. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
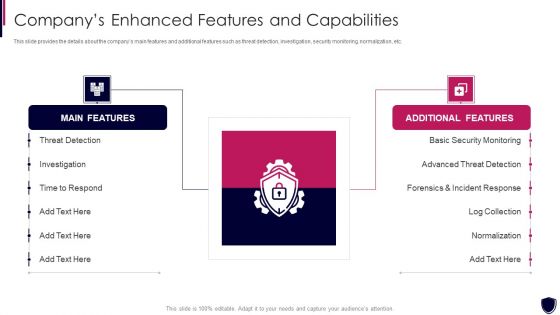
Enhancing Cyber Safety With Vulnerability Administration Companys Enhanced Features Download PDF
This slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. This is a enhancing cyber safety with vulnerability administration companys enhanced features download pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like main features, additional features, threat detection, investigation, basic security monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Portable Home Safety Systems Company Profile Our Expertise Ppt Summary Graphics Example PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. This is a Portable Home Safety Systems Company Profile Our Expertise Ppt Summary Graphics Example PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Integrated Control, Voice Assistant, Internet Protocol, RFID Based. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Architecture Transformation Playbook Essential Guidelines To Ensure Workers Safety Topics PDF
This slide provides information regarding essential guidelines to ensure workers safety with details about workers clothing and PPE, site protection and security and tools and equipment. Presenting Architecture Transformation Playbook Essential Guidelines To Ensure Workers Safety Topics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Site Protection And Security, Tools And Equipment, Personal Protective Equipment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
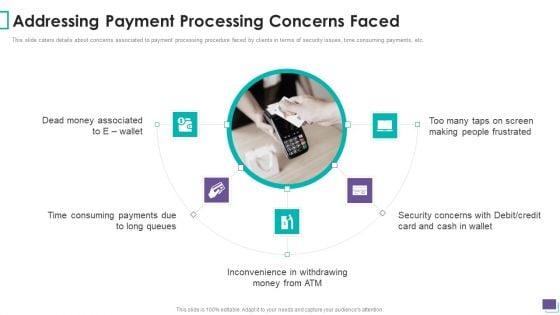
Payment Gateway Firm Addressing Payment Processing Concerns Faced Demonstration PDF
This slide caters details about concerns associated to payment processing procedure faced by clients in terms of security issues, time consuming payments, etc. This is a Payment Gateway Firm Addressing Payment Processing Concerns Faced Demonstration PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Dead Money Associated, Time Consuming Payments, Due To Long Queues, Security Concerns. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
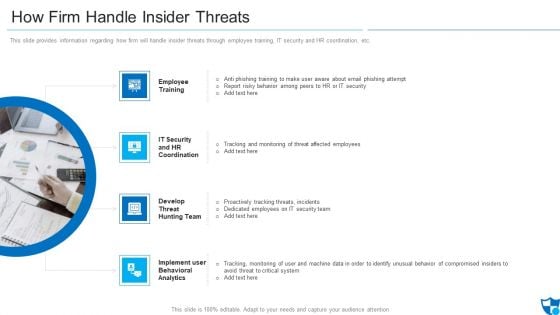
How Firm Handle Insider Threats Formats PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc.Presenting how firm handle insider threats formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like employee training, it security and hr coordination, develop threat hunting team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
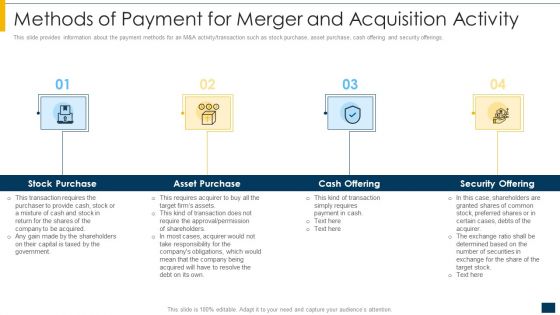
Methods Of Payment For Merger And Acquisition Activity Ppt Professional Vector PDF
This slide provides information about the payment methods for an M and A activity transaction such as stock purchase, asset purchase, cash offering and security offerings. Presenting methods of payment for merger and acquisition activity ppt professional vector pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like stock purchase, asset purchase, cash offering, security offering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Intelligence Framework For Application Consumption Determining The Suitable Software For Organization Icons PDF
The slide provides the key features comparison of various software that will help the company to achieve its objective of process automation and data security. Deliver and pitch your topic in the best possible manner with this cloud intelligence framework for application consumption determining the suitable software for organization icons pdf. Use them to share invaluable insights on process automation, data security, improve productivity, process automation and data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
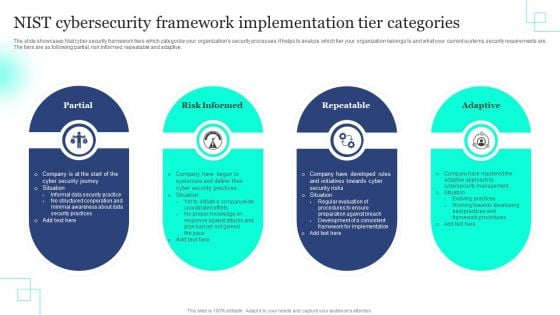
NIST Cybersecurity Framework Implementation Tier Categories Rules PDF
The slide showcases Nist cyber security framework tiers which categorize your organizations security processes, it helps to analyze which tier your organization belongs to and what your current systems security requirements are. The tiers are as following partial, risk informed, repeatable and adaptive. Persuade your audience using this NIST Cybersecurity Framework Implementation Tier Categories Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Partial, Risk Informed, Repeatable . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security. If you are looking for a format to display your unique thoughts, then the professionally designed Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.
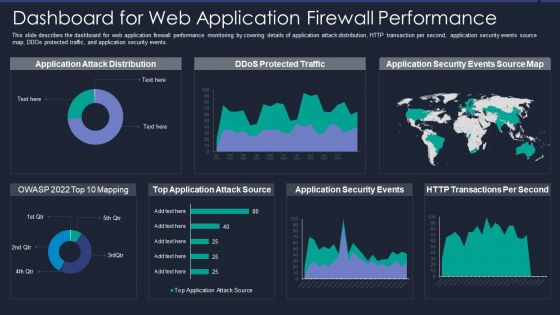
Web App Firewall Services IT Dashboard For Web Application Firewall Performance Microsoft PDF
This slide describes the dashboard for web application firewall performance monitoring by covering details of application attack distribution, HTTP transaction per second, application security events source map, DDOs protected traffic, and application security events. Deliver and pitch your topic in the best possible manner with this web app firewall services it dashboard for web application firewall performance microsoft pdf. Use them to share invaluable insights on application, source, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
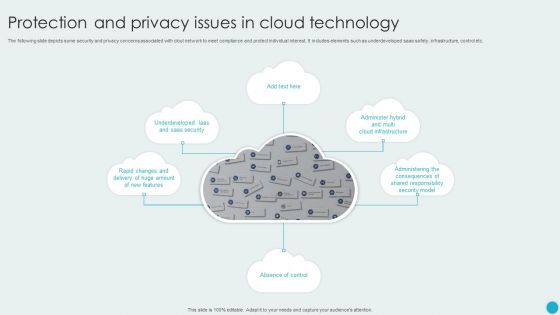
Protection And Privacy Issues In Cloud Technology Rules PDF
The following slide depicts some security and privacy concerns associated with clout network to meet compliance and protect individual interest. It includes elements such as underdeveloped saas safety, infrastructure, control etc. Persuade your audience using this Protection And Privacy Issues In Cloud Technology Rules PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Absence Of Control, Saas Security, Security Model. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Influencer Marketing 4 Months Project Status Update Icon Slides PDF
This slide covers the four months project status update of software implementation project undertaken by the IT team. It includes various activities to be performed under IT help desk, web server, network and global security.Showcasing this set of slides titled Influencer Marketing 4 Months Project Status Update Icon Slides PDF. The topics addressed in these templates are Global Security, Network Speed, Security Plan . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
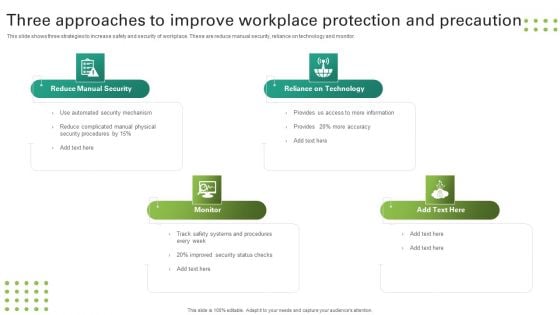
Three Approaches To Improve Workplace Protection And Precaution Background PDF
This slide shows three strategies to increase safety and security of workplace. These are reduce manual security, reliance on technology and monitor. Persuade your audience using this Three Approaches To Improve Workplace Protection And Precaution Background PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Reduce Manual Security, Reliance On Technology, Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
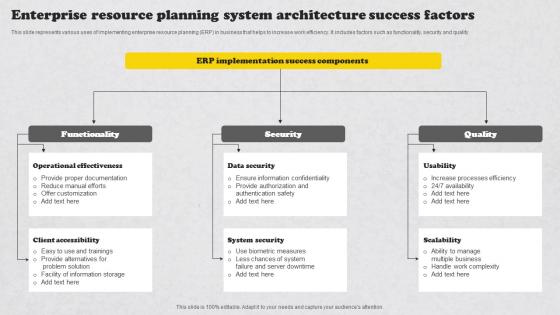
Enterprise Resource Planning System Architecture Success Factors Background Pdf
This slide represents various uses of implementing enterprise resource planning ERP in business that helps to increase work efficiency. It includes factors such as functionality, security and quality Showcasing this set of slides titled Enterprise Resource Planning System Architecture Success Factors Background Pdf. The topics addressed in these templates are Quality, Security, Functionality. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents various uses of implementing enterprise resource planning ERP in business that helps to increase work efficiency. It includes factors such as functionality, security and quality
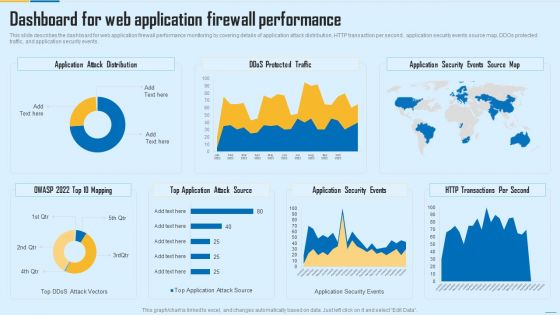
Dashboard For Web Application Firewall Performance WAF Platform Diagrams PDF
This slide describes the dashboard for web application firewall performance monitoring by covering details of application attack distribution, HTTP transaction per second, application security events source map, DDOs protected traffic, and application security events. Deliver an awe inspiring pitch with this creative Dashboard For Web Application Firewall Performance WAF Platform Diagrams PDF bundle. Topics like Application Attack Distribution, Application Security Events, Transactions Per Second can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
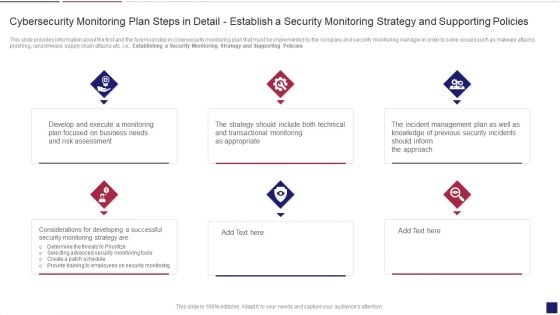
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Policies Inspiration PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Presenting continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring policies inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
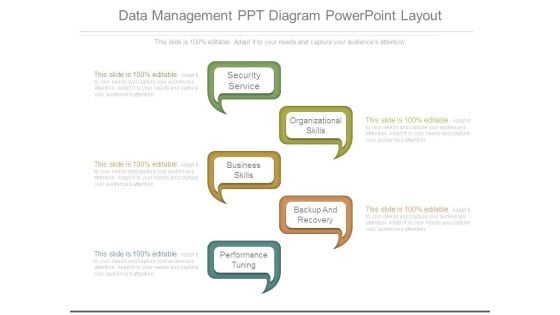
Data Management Ppt Diagram Powerpoint Layout
This is a data management ppt diagram powerpoint layout. This is a five stage process. The stages in this process are security service, organizational skills, business skills, backup and recovery, performance tuning.
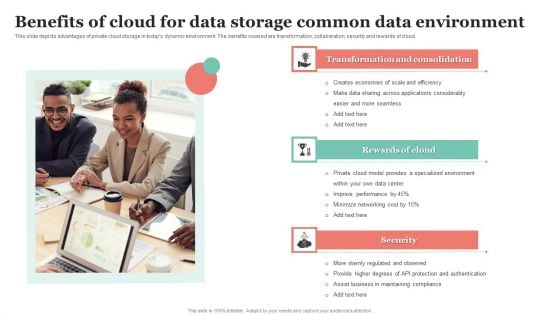
Benefits Of Cloud For Data Storage Common Data Environment Ppt Pictures Slides PDF
This slide depicts advantages of private cloud storage in todays dynamic environment. The benefits covered are transformation, collaboration, security and rewards of cloud. Presenting Benefits Of Cloud For Data Storage Common Data Environment Ppt Pictures Slides PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Transformation And Consolidation, Rewards Cloud, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Stock Photo 3d Dollar Symbol With Chain And Text Boxes PowerPoint Slide
This image slide has been designed with graphic of dollar notes locked with chain. This slide depicts concept of financial security and investment. Use this editable slide for your wealth and finance related topics.
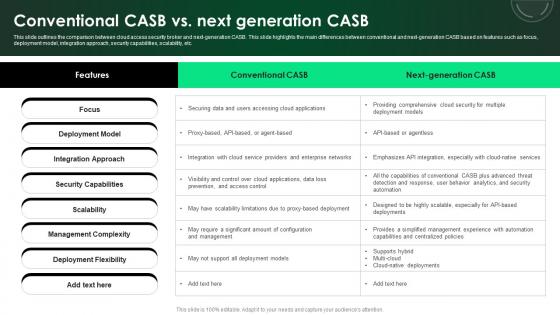
CASB 2 0 IT Conventional CASB Vs Next Generation CASB
This slide outlines the comparison between cloud access security broker and next-generation CASB. This slide highlights the main differences between conventional and next-generation CASB based on features such as focus, deployment model, integration approach, security capabilities, scalability, etc. Find a pre-designed and impeccable CASB 2 0 IT Conventional CASB Vs Next Generation CASB. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the comparison between cloud access security broker and next-generation CASB. This slide highlights the main differences between conventional and next-generation CASB based on features such as focus, deployment model, integration approach, security capabilities, scalability, etc.

Major Data Quality Control Issues For Organizations Portrait PDF
The following slide highlights the quality control issues which includes duplicate data, unstructured data, security issues, hidden data and inaccurate data. Presenting major data quality control issues for organizations portrait pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including duplicate data, unstructured data, security issues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
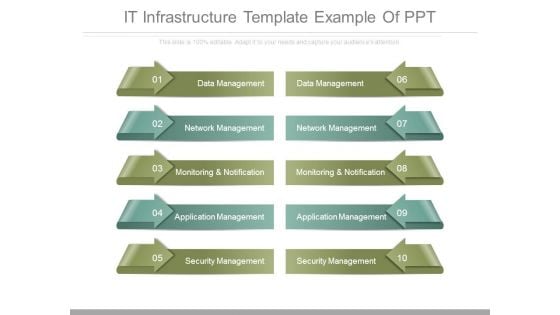
It Infrastructure Template Example Of Ppt
This is a it infrastructure template example of ppt. This is a ten stage process. The stages in this process are data management, network management, monitoring and notification, application management, security management.
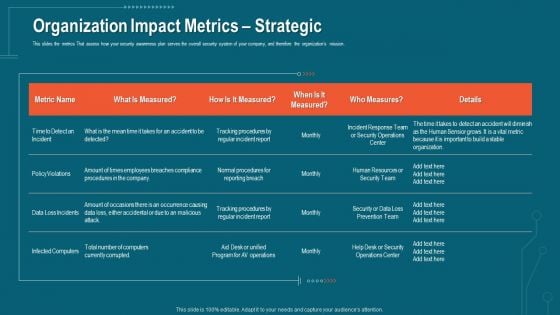
Companys Data Safety Recognition Organization Impact Metrics Strategic Topics PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver an awe-inspiring pitch with this creative companys data safety recognition organization impact metrics strategic topics pdf bundle. Topics like organization impact metrics strategic can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
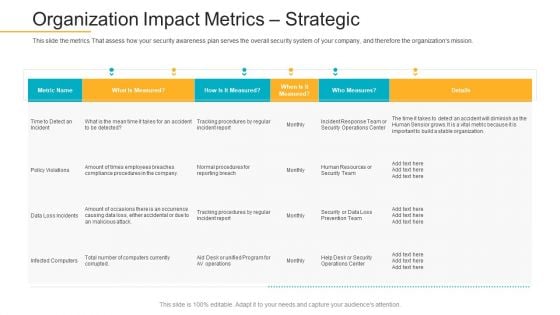
Data Breach Prevention Recognition Organization Impact Metrics Strategic Microsoft PDF
This slide the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition organization impact metrics strategic microsoft pdf. Use them to share invaluable insights on organization impact metrics strategic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Page Experience Signals In Google Search Console Training Ppt
This slide covers search signals for page experience largely known as core web vitals. It also includes KPIs such as mobile-friendly experience, safe browsing experience, HTTPS security and no intrusive interstitials.
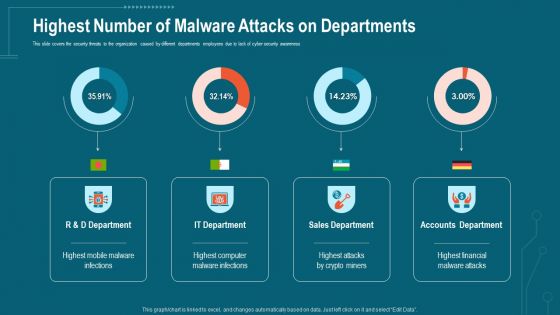
Companys Data Safety Recognition Highest Number Of Malware Attacks On Departments Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative companys data safety recognition highest number of malware attacks on departments sample pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Safety Initiatives Action Plan In Case Of Breaches Mockup PDF
Mentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an awe inspiring pitch with this creative data safety initiatives action plan in case of breaches mockup pdf bundle. Topics like threat encountered, security breach, system failure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
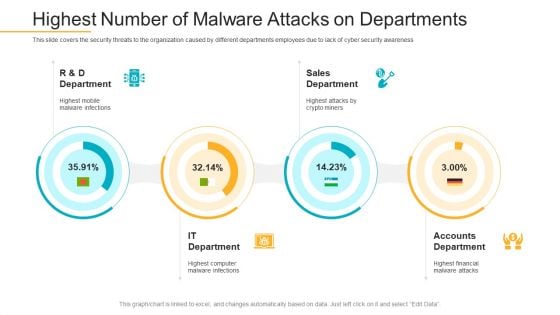
Data Breach Prevention Recognition Highest Number Of Malware Attacks On Departments Pictures PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition highest number of malware attacks on departments pictures pdf. Use them to share invaluable insights on sales department, accounts department, it department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Stock Photo Blue Colored Pen Drive With Combination Lock PowerPoint Slide
Graphic of blue colored pen drive and combination lock has been used to design this power point template. This PPT contains the concept of data security and data technology. Use this PPT for your business and marketing related presentations.

Challenges Faced During Technology Implementation Infographics PDF
This slide shows three challenges faced by an organization in technology implementation. It includes training, security and monitoring. Presenting Challenges Faced During Technology Implementation Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Training, Security, Monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
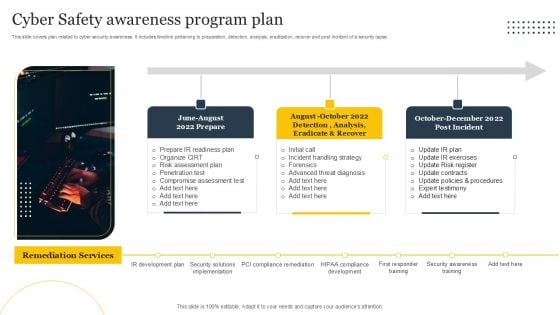
Cyber Safety Awareness Program Plan Ppt Icon Smartart PDF
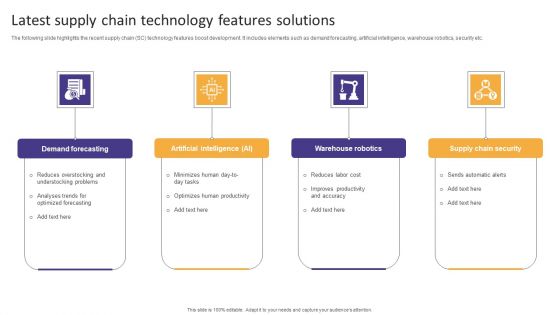
Latest Supply Chain Technology Features Solutions Formats PDF
The following slide highlights the recent supply chain SC technology features boost development. It includes elements such as demand forecasting, artificial intelligence, warehouse robotics, security etc. Presenting Latest Supply Chain Technology Features Solutions Formats PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Warehouse Robotics, Supply Chain Security, Demand Forecasting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

AI Applications In Banking And Financial Services Formats PDF
This slide covers use of artificial intelligence in banking and financial services. It involves applications such as customer engagement, predictive analytics, cyber security and credit scoring.Presenting AI Applications In Banking And Financial Services Formats PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Customer Engagement, Predictive Analytics, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
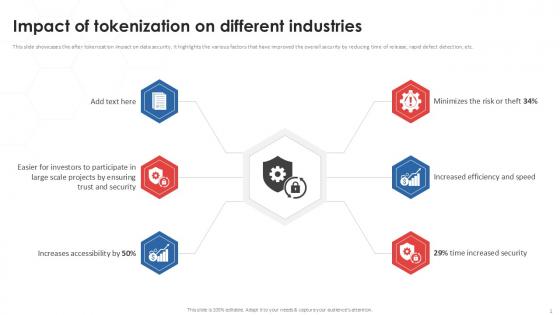
Impact Of Tokenization On Different Industries PPT Template
This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc. Find a pre-designed and impeccable Impact Of Tokenization On Different Industries PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc.
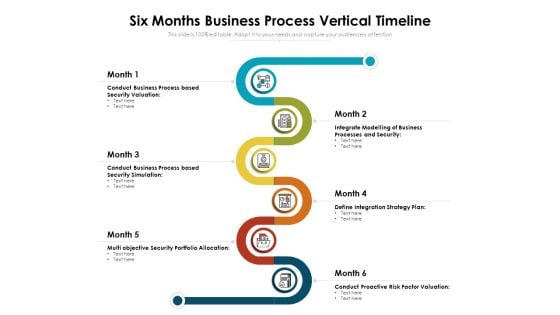
Six Months Business Process Vertical Timeline Ppt Model Design Inspiration PDF
Presenting six months business process vertical timeline ppt model design inspiration pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including conduct business process based security valuation, integrate modelling of business processes and security, define integration strategy plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
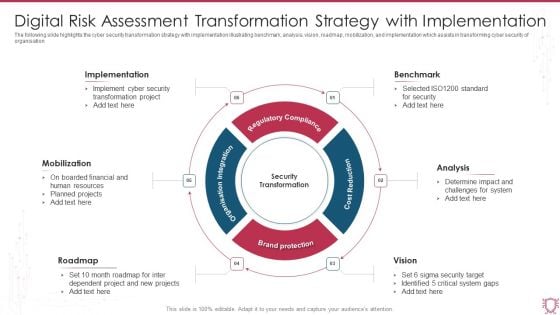
Digital Risk Assessment Transformation Strategy With Implementation Slides PDF
The following slide highlights the cyber security transformation strategy with implementation illustrating benchmark, analysis, vision, roadmap, mobilization, and implementation which assists in transforming cyber security of organisation. Presenting Digital Risk Assessment Transformation Strategy With Implementation Slides PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Implementation, Benchmark, Analysis, Vision. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































