Information Security

Cloud Security Checklist Networking Cloud Computing Security IT Ppt Show Samples PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. Presenting cloud security checklist networking cloud computing security it ppt show samples pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, mechanisms, security, critical data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
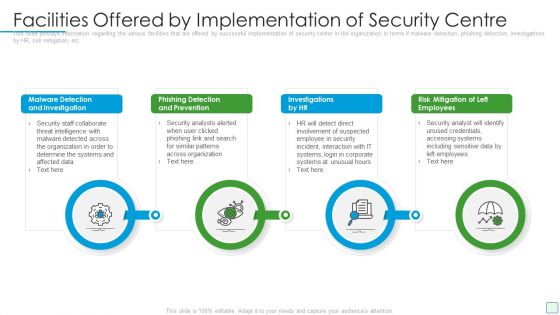
Developing Firm Security Strategy Plan Facilities Offered By Implementation Of Security Centre Formats PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a developing firm security strategy plan facilities offered by implementation of security centre formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
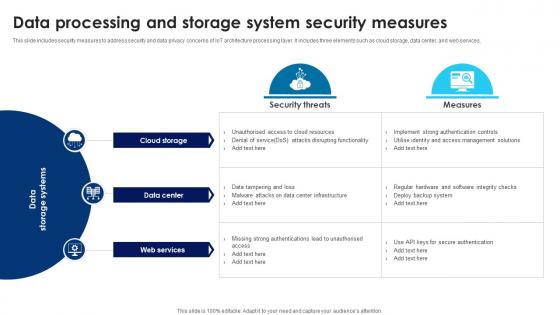
Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V
This slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services.

Security Training Program Frameworks Contd Hacking Prevention Awareness Training For IT Security Background PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative security training program frameworks contd hacking prevention awareness training for it security background pdf bundle. Topics like management, implement, security policy, monitor can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
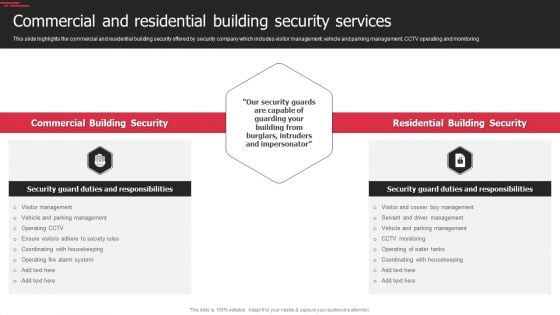
Security Agency Business Profile Commercial And Residential Building Security Services Designs PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Presenting Security Agency Business Profile Commercial And Residential Building Security Services Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Commercial Building Security, Residential Building Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Commercial And Residential Building Security Services Clipart PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Presenting Manpower Corporate Security Business Profile Commercial And Residential Building Security Services Clipart PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Commercial Building Security, Residential Building Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
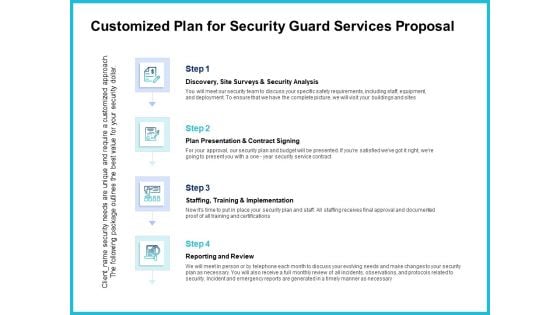
Uniformed Security Customized Plan For Security Guard Services Proposal Portrait PDF
Presenting uniformed security customized plan for security guard services proposal portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security analysis, plan presentation, training and implementation, reporting and review. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Workforce Security Realization Coaching Plan Security Awareness Program Checklist Background PDF
This slide covers the Checklist that will help organizations prepare and implement their safety awareness training. The details listed below can be used to promote preparation and education planning in the area of security awareness. Presenting workforce security realization coaching plan security awareness program checklist background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like implementing security awareness, sustaining security awareness, security awareness program. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
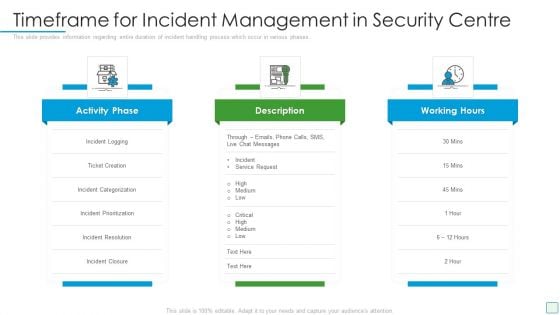
Developing Firm Security Strategy Plan Timeframe For Incident Management In Security Centre Download PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. Presenting developing firm security strategy plan timeframe for incident management in security centre download pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like activity phase, description, working hours. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Elements Of IT Security IT Cloud Security Ppt Infographics Ideas PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting elements of it security it cloud security ppt infographics ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, service, vulnerabilities, implemented, digital resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
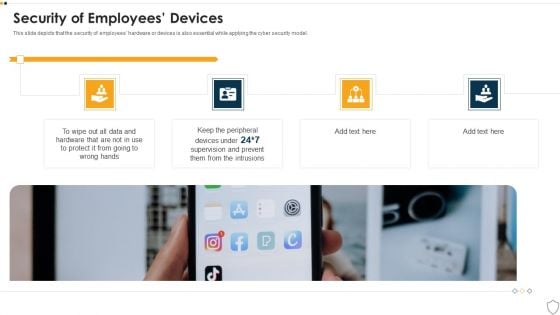
IT Security Security Of Employees Devices Ppt Summary Layout Ideas PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Presenting it security security of employees devices ppt summary layout ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security of employees devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
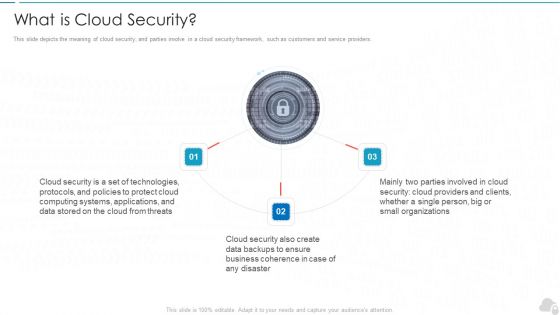
What Is Cloud Security Cloud Computing Security IT Ppt File Graphics PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers. Presenting what is cloud security cloud computing security it ppt file graphics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud security, technologies, protocols, business, organizations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
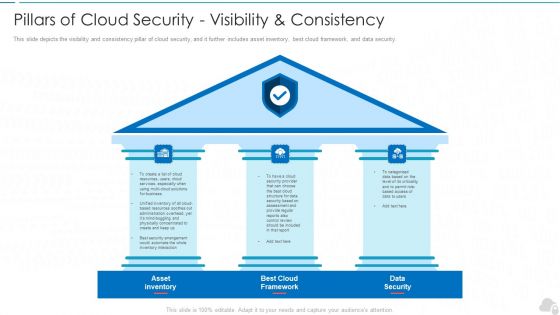
Pillars Of Cloud Security Visibility And Consistency Cloud Computing Security IT Ppt Slide PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security. Presenting pillars of cloud security visibility and consistency cloud computing security it ppt slide pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like asset inventory, best cloud framework, data security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
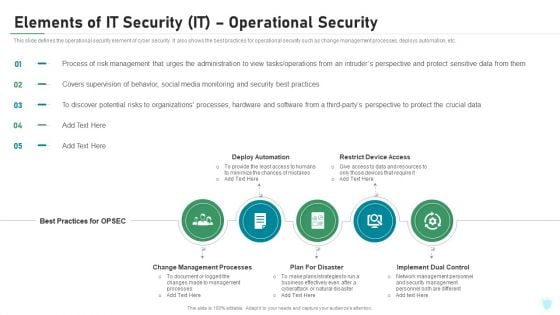
Elements Of IT Security IT Operational Security Ppt Outline Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting elements of it security it operational security ppt outline ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like change management processes, deploy automation, restrict device access, plan for disaster, implement dual control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Checklist Policies And Procedures Background PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization.Presenting Cloud Security Assessment Cloud Security Checklist Policies And Procedures Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Implement Policies, Security Solutions, Security Procedures In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Info Security Security Of Employees Devices Ppt PowerPoint Presentation Icon Files PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Presenting info security security of employees devices ppt powerpoint presentation icon files pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, employees devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Training Program Frameworks Hacking Prevention Awareness Training For IT Security Themes PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this security training program frameworks hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on target, training, maintain, secure, implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V
This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V from Slidegeeks and deliver a wonderful presentation. This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc.
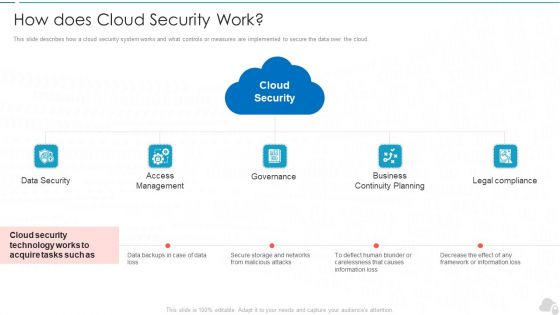
How Does Cloud Security Work Cloud Computing Security IT Ppt Show Graphics Design PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Presenting how does cloud security work cloud computing security it ppt show graphics design pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like data security, access management, governance, business continuity planning, legal compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Best Practices For Cloud Security Ppt Icon Pictures PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting it security best practices for cloud security ppt icon pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like operations management, security and compliance monitoring, data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
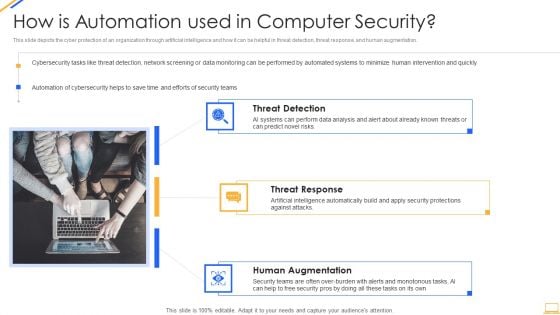
Desktop Security Management How Is Automation Used In Computer Security Elements PDF
Presenting desktop security management how is automation used in computer security elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Home Security Solutions Company Profile Our Security Services And Solutions Slides PDF
This slide highlights the security company services which includes CCTV, mobile app and software, occupancy sensor, audio video solution. Co2 monitor, door sensor, leak detector, smoke detector and indoor camera. Presenting Smart Home Security Solutions Company Profile Our Security Services And Solutions Slides PDF to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like CCTV And Security, Wireless And Networking, Storage And Server, Fire Fighting System. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
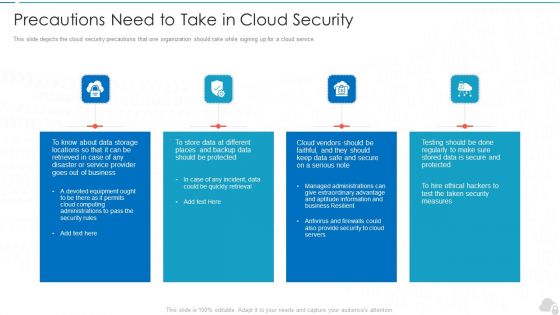
Precautions Need To Take In Cloud Security Cloud Computing Security IT Ppt Inspiration Templates PDF
This slide depicts the cloud security precautions that one organization should take while signing up for a cloud service. Presenting precautions need to take in cloud security cloud computing security it ppt inspiration templates pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, service, security measures, computing administrations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
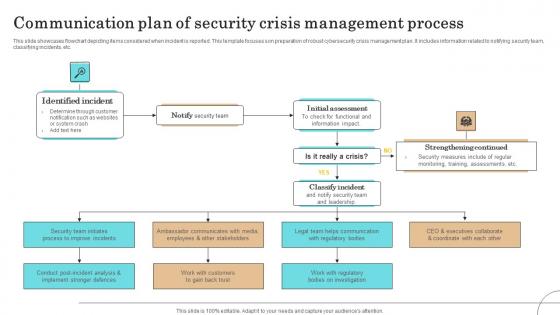
Communication Plan Of Security Crisis Management Process Pictures Pdf
This slide showcases flowchart depicting items considered when incident is reported. This template focuses son preparation of robust cybersecurity crisis management plan. It includes information related to notifying security team, classifying incidents, etc.Pitch your topic with ease and precision using this Communication Plan Of Security Crisis Management Process Pictures Pdf This layout presents information on Identified Incident, Initial Assessment, Strengthening Continued It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases flowchart depicting items considered when incident is reported. This template focuses son preparation of robust cybersecurity crisis management plan. It includes information related to notifying security team, classifying incidents, etc.
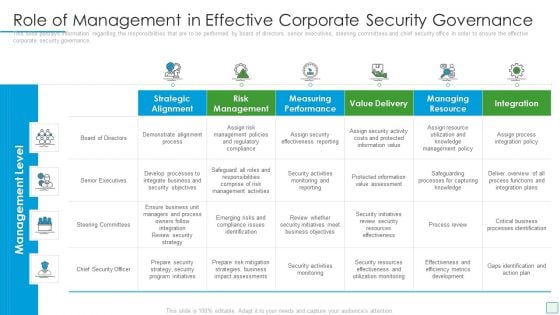
Developing Firm Security Strategy Plan Role Of Management In Effective Corporate Security Governance Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief security office in order to ensure the effective corporate security governance. Deliver an awe inspiring pitch with this creative developing firm security strategy plan role of management in effective corporate security governance slides pdf bundle. Topics like strategic alignment, risk management, measuring performance, value delivery, managing resource can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Desktop Security Management What Are The Benefits Of Computer Security Icons PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting desktop security management what are the benefits of computer security icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, environment, potential, devices, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Elements Of Computer Security Disaster Recovery Planning Guidelines PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Presenting desktop security management elements of computer security disaster recovery planning guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, resources, financial budget, strategies, plans. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
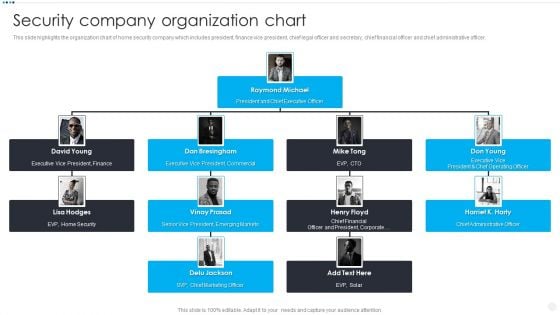
Smart Home Security Solutions Company Profile Security Company Organization Chart Diagrams PDF
This slide highlights the organization chart of home security company which includes president, finance vice president, chief legal officer and secretary, chief financial officer and chief administrative officer. Presenting Smart Home Security Solutions Company Profile Security Company Organization Chart Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Executive Vice President, EVP Home Security, Chief Marketing Officer, Chief Administrative Officer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups.Presenting Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Storage Locations, Natural Disasters, Massive Impact. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Parameters To Prepare Security Strategic Agenda Summary Pdf
This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion. Pitch your topic with ease and precision using this Key Parameters To Prepare Security Strategic Agenda Summary Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion.

Cloud Security Threats Malware Attacks Cloud Computing Security IT Ppt Show Diagrams PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. Presenting cloud security threats malware attacks cloud computing security it ppt show diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cloud administrations, cyber criminals, technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
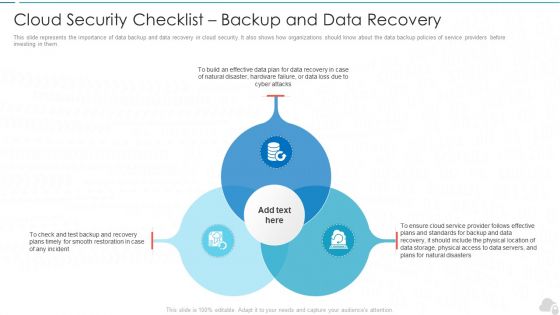
Cloud Security Checklist Backup And Data Recovery Cloud Computing Security IT Ppt Styles Rules PDF
This slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Presenting cloud security checklist backup and data recovery cloud computing security it ppt styles rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like effective, cloud service, natural disasters, data plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Checklist Backup And Data Recovery Diagrams PDF
This slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Presenting Cloud Security Assessment Cloud Security Checklist Backup And Data Recovery Diagrams PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Service Provider, Effective Plans, Natural Disasters In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Shared Vulnerabilities Cloud Computing Security IT Ppt Slides Picture PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. Presenting cloud security threats shared vulnerabilities cloud computing security it ppt slides picture pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, cloud service, responsibility, cloud data security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
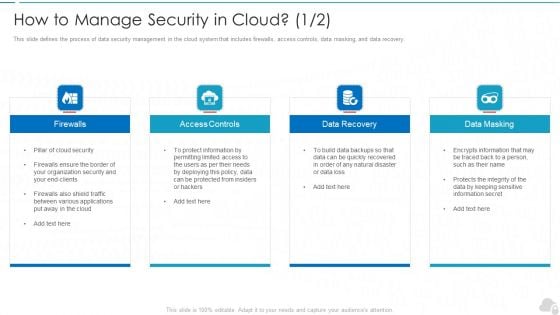
How To Manage Security In Cloud Cloud Computing Security IT Ppt Model Graphic Images PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting how to manage security in cloud cloud computing security it ppt model graphic images pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like firewalls, access controls, data recovery, data masking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Email Security Encryption And Data Loss Prevention Your Problem E Mail Security Proposal Rules PDF
This slide covers the problems that are faced by the clients. Presenting email security encryption and data loss prevention your problem e mail security proposal rules pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security confidential data, protection against malware, protection phishing scams, threat weak password. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
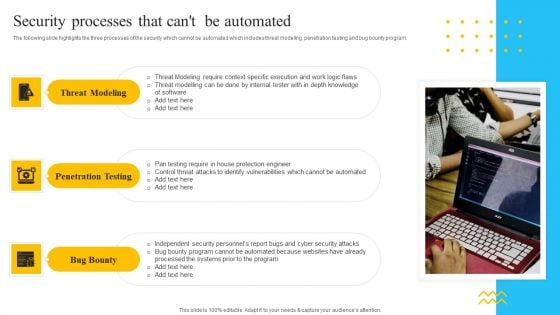
IT Security Automation Tools Integration Security Processes That Cant Be Automated Background PDF
The following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Presenting IT Security Automation Tools Integration Security Processes That Cant Be Automated Background PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Threat Modeling, Penetration Testing, Bug Bounty. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Security Risks Or Threats Cloud Computing Security IT Ppt Icon PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting cloud security risks or threats cloud computing security it ppt icon pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like revenue losses, loss of data, shared vulnerabilities, compliance violations, malware attacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
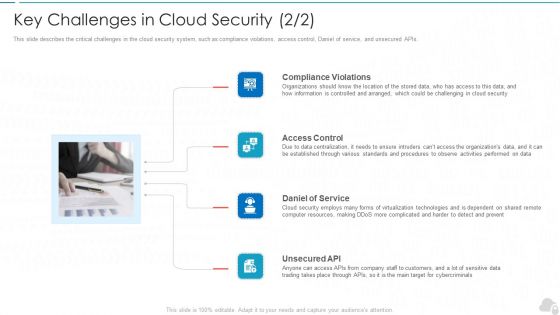
Key Challenges In Cloud Security Cloud Computing Security IT Ppt Infographic Template Graphics Example PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs. Presenting key challenges in cloud security cloud computing security it ppt infographic template graphics example pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like compliance violations, access control, daniel of service, unsecured api. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
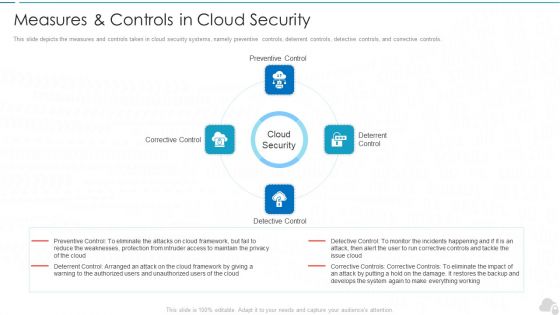
Measures And Controls In Cloud Security Cloud Computing Security IT Ppt Styles Example File PDF
This slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls. Presenting measures and controls in cloud security cloud computing security it ppt styles example file pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like corrective control, preventive control, deterrent control, detective control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
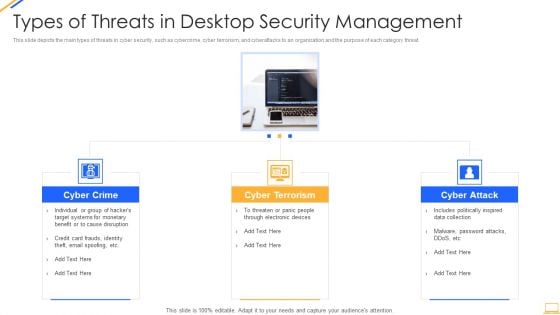
Desktop Security Management Types Of Threats In Desktop Security Management Themes PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting desktop security management types of threats in desktop security management themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like target systems, devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Home Security Solutions Company Profile Security Company Case Study Brochure PDF
This slide highlights the case study of security company which includes key problems such as theft, fire breakout with integrated solution and business value delivered. Presenting Smart Home Security Solutions Company Profile Security Company Case Study Brochure PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like High Value Brand, Client Problem Storing, Integrated Solution Warehousing, Business Value Delivered. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
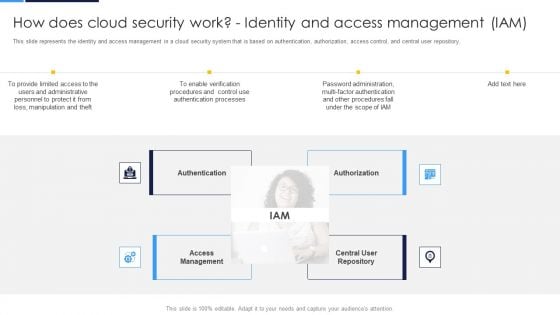
Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.Presenting Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Accessibility, Knowledge, Technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V
This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc.
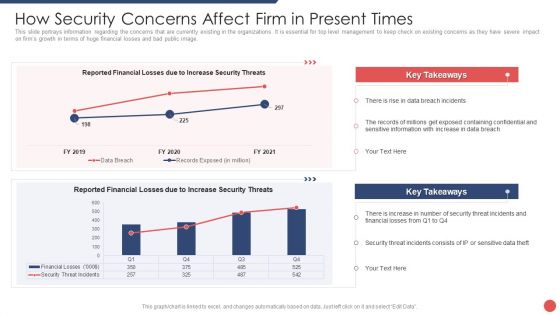
Security Functioning Centre How Security Concerns Affect Firm In Present Times Ideas PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver and pitch your topic in the best possible manner with this security functioning centre how security concerns affect firm in present times ideas pdf. Use them to share invaluable insights on financial, security threat, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
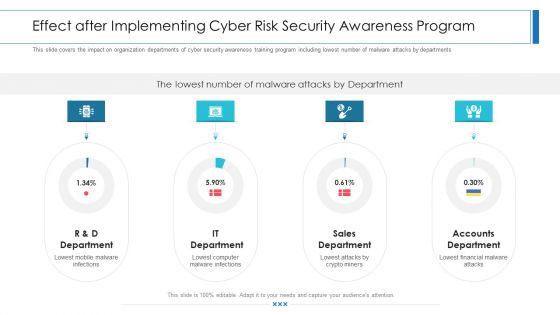
Workforce Security Realization Coaching Plan Effect After Implementing Cyber Risk Security Awareness Program Structure PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments. Presenting workforce security realization coaching plan effect after implementing cyber risk security awareness program structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like it department, sales department, accounts department. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Camera System Company Profile Our Security Services And Solutions Topics PDF
This slide highlights the security company services which includes CCTV, mobile app software, occupancy sensor, audio video solution. Co2 monitor, door sensor, leak detector, smoke detector and indoor camera.Presenting Security Camera System Company Profile Our Security Services And Solutions Topics PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Networking Solution, Display Solutions, Occupancy Sensor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
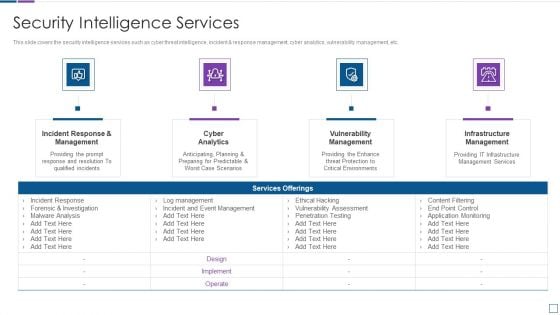
Real Time Assessment Of Security Threats Security Intelligence Services Formats PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting real time assessment of security threats security intelligence services formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
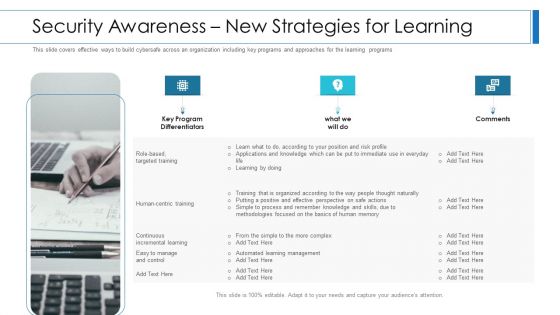
Workforce Security Realization Coaching Plan Security Awareness New Strategies For Learning Clipart PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Presenting workforce security realization coaching plan security awareness new strategies for learning clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security awareness new strategies for learning. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
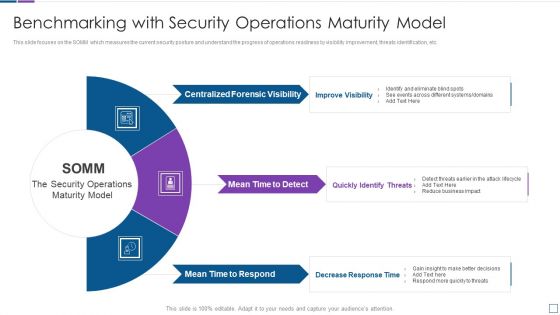
Real Time Assessment Of Security Threats Benchmarking With Security Operations Maturity Model Infographics PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting real time assessment of security threats benchmarking with security operations maturity model infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like centralized forensic visibility, mean time to detect, mean time to respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Surveillance Company Profile Security Company Case Study Demonstration PDF
This slide highlights the case study of security company which includes key problems such as theft, fire breakout with integrated solution and business value delivered. Presenting Security And Surveillance Company Profile Security Company Case Study Demonstration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Client Problem, Integrated Solution, Business Value. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
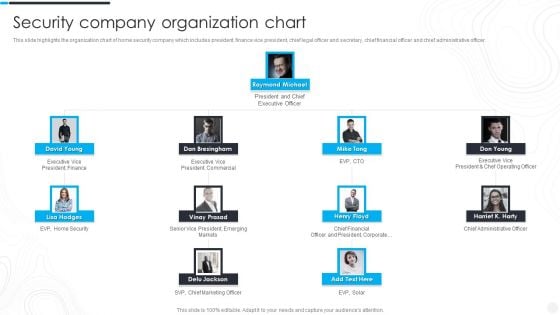
Security Camera System Company Profile Security Company Organization Chart Ideas PDF
This slide highlights the organization chart of home security company which includes president, finance vice president, chief legal officer and secretary, chief financial officer and chief administrative officer. Presenting Security Camera System Company Profile Security Company Organization Chart Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like President Finance, President And Chief, Executive Officer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
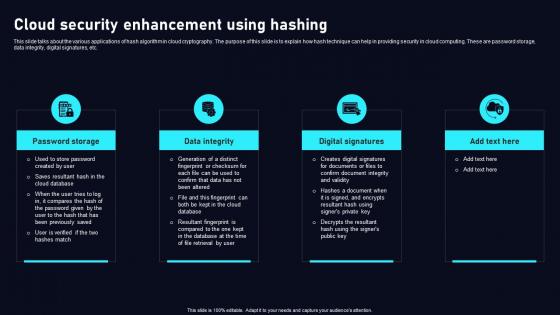
Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. This Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc.
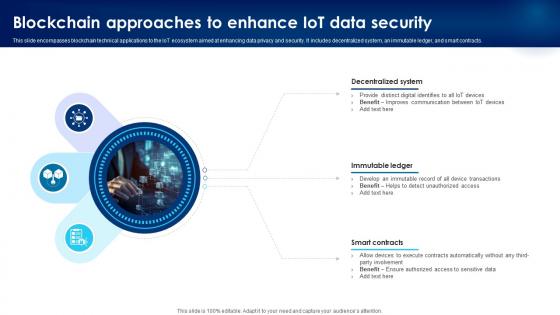
Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V
This slide encompasses blockchain technical applications to the IoT ecosystem aimed at enhancing data privacy and security. It includes decentralized system, an immutable ledger, and smart contracts. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide encompasses blockchain technical applications to the IoT ecosystem aimed at enhancing data privacy and security. It includes decentralized system, an immutable ledger, and smart contracts.

Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Are you searching for a Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf from Slidegeeks today. The following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc.

Data Security In Cloud Computing Data Security In Cloud Computing Ppt Example
This slide represents the architecture of data security in cloud computing. The purpose of this slide is to illustrate how data is secured in cloud using cryptography. The key components included are organization, users, cloud storage, etc. This modern and well-arranged Data Security In Cloud Computing Data Security In Cloud Computing Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the architecture of data security in cloud computing. The purpose of this slide is to illustrate how data is secured in cloud using cryptography. The key components included are organization, users, cloud storage, etc.

Overview Of Secure Access Service Edge Network Security Download Pdf
This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc. Boost your pitch with our creative Overview Of Secure Access Service Edge Network Security Download Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Overview Of Secure Access Service Edge Network Security Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
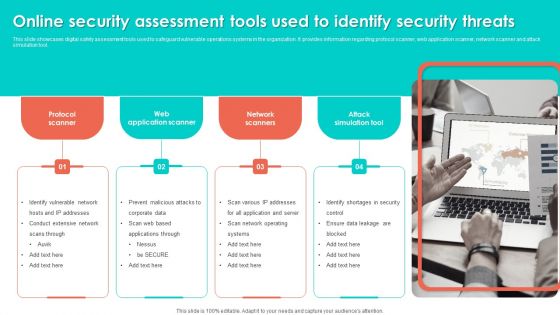
Online Security Assessment Tools Used To Identify Security Threats Slides PDF
This slide showcases digital safety assessment tools used to safeguard vulnerable operations systems in the organization. It provides information regarding protocol scanner, web application scanner, network scanner and attack simulation tool. Persuade your audience using this Online Security Assessment Tools Used To Identify Security Threats Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Scanners, Attack Simulation Tool, Web Application Scanner. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Threats Contract Breaches With Clients Cloud Computing Security IT Ppt Ideas Introduction PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting cloud security threats contract breaches with clients cloud computing security it ppt ideas introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, organization, sensitive data stored. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
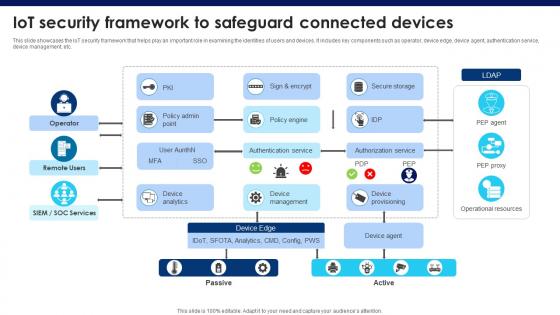
Building Trust With IoT Security IoT Security Framework To Safeguard Connected Devices IoT SS V
This slide showcases the IoT security framework that helps play an important role in examining the identities of users and devices. It includes key components such as operator, device edge, device agent, authentication service, device management, etc. This Building Trust With IoT Security IoT Security Framework To Safeguard Connected Devices IoT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases the IoT security framework that helps play an important role in examining the identities of users and devices. It includes key components such as operator, device edge, device agent, authentication service, device management, etc.


 Continue with Email
Continue with Email

 Home
Home


































