Information Security

Courses For Malware Cyber Security Breach Awareness Download Pdf
This slides shows various training programs of cyber security awareness to aware staff. The purpose of this slide is to reducing threat in future. The various course are Cofense online security, webroot security training, etc. Showcasing this set of slides titled Courses For Malware Cyber Security Breach Awareness Download Pdf The topics addressed in these templates are Awareness Training, Webroot Security, Cybsafe Borderless All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slides shows various training programs of cyber security awareness to aware staff. The purpose of this slide is to reducing threat in future. The various course are Cofense online security, webroot security training, etc.

Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc.

Scope For Security Camera Services One Pager Sample Example Document
This slide depicts the project scope providing information about the multiple activities to be performed by the bidding company for the client. Presenting you an exemplary Scope For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Scope For Security Camera Services One Pager Sample Example Document brilliant piece now.

Determine Focus Areas To Implement Security Operations Centre Diagrams PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. Deliver an awe inspiring pitch with this creative determine focus areas to implement security operations centre diagrams pdf bundle. Topics like digital forensics and control, risk monitoring and management, system and network administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
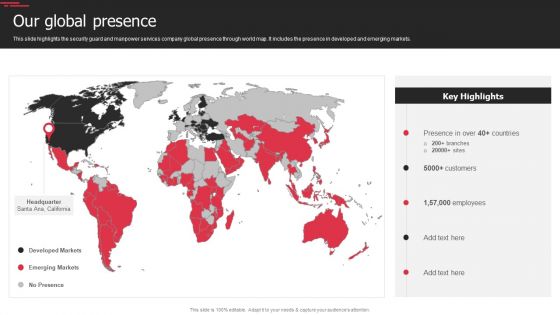
Security Agency Business Profile Our Global Presence Themes PDF
This slide highlights the security guard and manpower services company global presence through world map. It includes the presence in developed and emerging markets. Presenting Security Agency Business Profile Our Global Presence Themes PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Developed Markets, Customers, Employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF
This slide defines the flowchart for web attack incident response. It includes information related to the steps taken to resolve the web attack incident taken place using the cybersecurity. Persuade your audience using this Cyber Security Attack Incident Response Flowchart Ppt Summary Show PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Prioritizing Security Response, Investigating, Preparing Report Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills

Zero Trust Security Table Of Contents Ideas Pdf
If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Security Table Of Contents Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Security Table Of Contents Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Our Zero Trust Security Table Of Contents Ideas Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
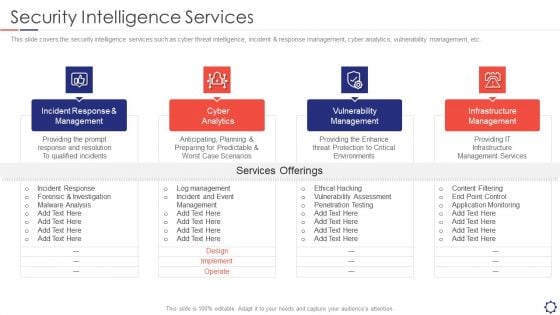
SIEM Security Intelligence Services Ppt Professional Format PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem security intelligence services ppt professional format pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
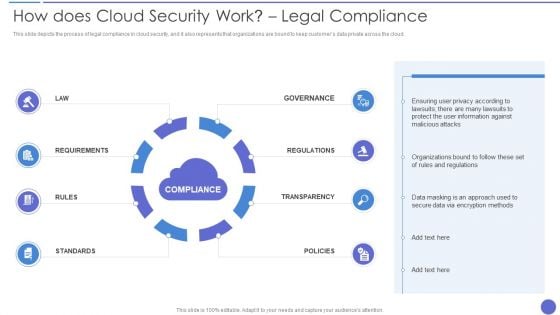
How Does Cloud Security Work Legal Compliance Background PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting How Does Cloud Security Work Legal Compliance Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authorization, Authentication, Access Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
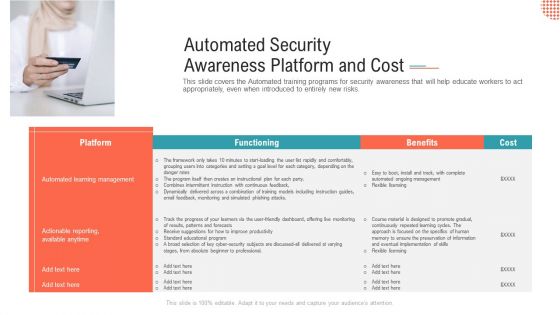
Automated Security Awareness Platform And Cost Graphics PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks.Presenting automated security awareness platform and cost graphics pdf. to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like automated learning management, actionable reporting, available anytime. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security And Surveillance Company Profile Business Development Strategy Icons PDF
This slide highlights the security company channel expansion strategy which showcases strategies for retail, multifamily and professional channels including instore lead generation and robust product offerings.Presenting Security And Surveillance Company Profile Business Development Strategy Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Professional Channels, National Operations, Remove Insurance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
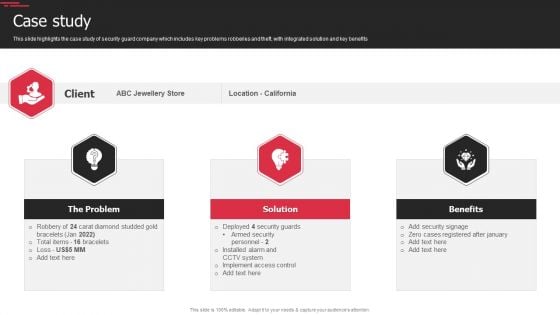
Security Agency Business Profile Case Study Elements PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. Presenting Security Agency Business Profile Case Study Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like The Problem, Solution, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Our Business Approach Introduction PDF
This slide highlights the business approach of security company which includes strategic planning, human resource management, participatory management and productivity management. Presenting Manpower Corporate Security Business Profile Our Business Approach Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Hr Management, Participatory Management, Productivity Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
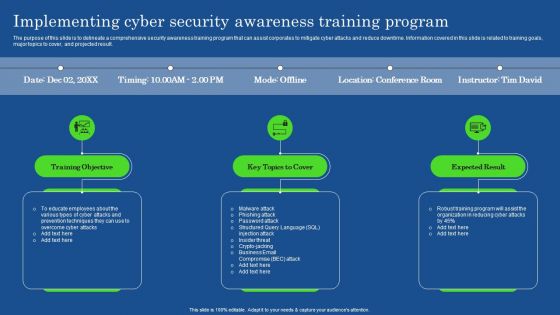
Implementing Cyber Security Awareness Training Program Professional PDF
The purpose of this slide is to delineate a comprehensive security awareness training program that can assist corporates to mitigate cyber attacks and reduce downtime. Information covered in this slide is related to training goals, major topics to cover, and projected result. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cyber Security Awareness Training Program Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Info Safety And ISO 27001 Current Security Management Capabilities Overview Ideas PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative Info Safety And ISO 27001 Current Security Management Capabilities Overview Ideas PDF bundle. Topics like Core Functions, Rating Scale, Key Enablers, Required Standard Rating, Actual Rating can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf
This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi tenancy, cloud provider vulnerability, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Cryptography Challenges Cloud Data Security Using Cryptography Graphics Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi tenancy, cloud provider vulnerability, etc.
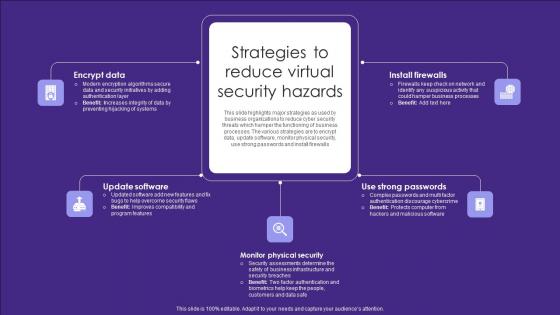
Strategies To Reduce Virtual Security Hazards Summary Pdf
This slide highlights major strategies as used by business organizations to reduce cyber security threats which hamper the functioning of business processes. The various strategies are to encrypt data, update software, monitor physical security, use strong passwords and install firewalls Showcasing this set of slides titled Strategies To Reduce Virtual Security Hazards Summary Pdf. The topics addressed in these templates are Install Firewalls, Strong Passwords, Physical Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights major strategies as used by business organizations to reduce cyber security threats which hamper the functioning of business processes. The various strategies are to encrypt data, update software, monitor physical security, use strong passwords and install firewalls

Security Software Company Investor Funding Pitch Deck Client Testimonials Diagrams PDF
The following slide showcases perceptive of expert analysts about IT company i.e. Awake Society. It showcase reviews of IT manager, chief information security officer and IT director. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Software Company Investor Funding Pitch Deck Client Testimonials Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Ways To Accomplish ISO 27001 Accreditation Current Security Management Capabilities Overview Summary PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Current Security Management Capabilities Overview Summary PDF. Use them to share invaluable insights on Core Functions, Key Enablers, Required Standard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
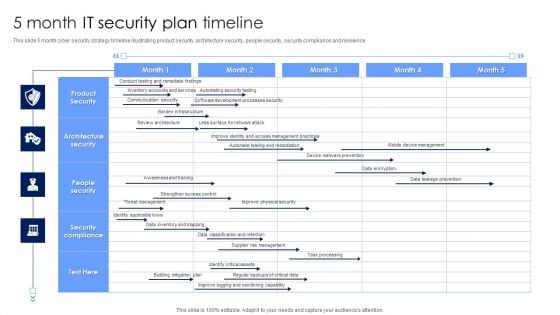
5 Month IT Security Plan Timeline Pictures PDF
This slide 5 month cyber security strategy timeline illustrating product security, architecture security, people security, security compliance and resilience. Showcasing this set of slides titled 5 Month IT Security Plan Timeline Pictures PDF. The topics addressed in these templates are Architecture Security, People Security, Security Compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
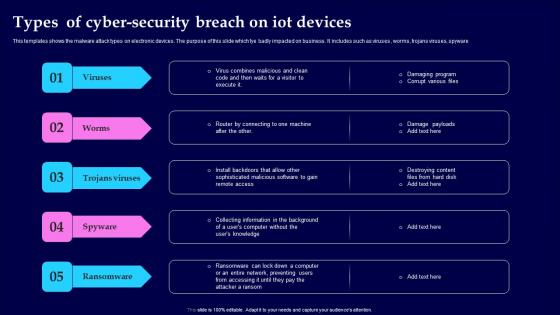
Types Of Cyber Security Breach On IOT Devices Themes Pdf
This templates shows the malware attack types on electronic devices. The purpose of this slide which tye badly impacted on business. It includes such as viruses, worms, trojans viruses, spyware Pitch your topic with ease and precision using this Types Of Cyber Security Breach On IOT Devices Themes Pdf This layout presents information on Viruses, Trojans Viruses, Spyware, Ransomware It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the malware attack types on electronic devices. The purpose of this slide which tye badly impacted on business. It includes such as viruses, worms, trojans viruses, spyware
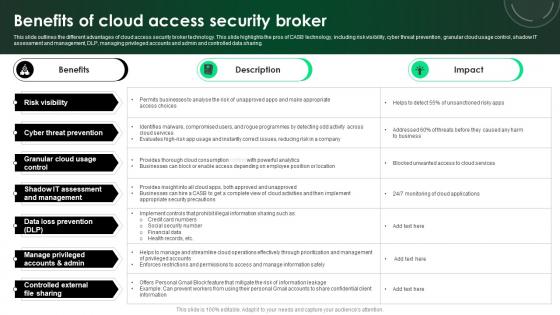
CASB 2 0 IT Benefits Of Cloud Access Security Broker
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. There are so many reasons you need a CASB 2 0 IT Benefits Of Cloud Access Security Broker. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing.

CASB 2 0 IT Emerging Cloud Security Risks And Threats
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Boost your pitch with our creative CASB 2 0 IT Emerging Cloud Security Risks And Threats. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on.
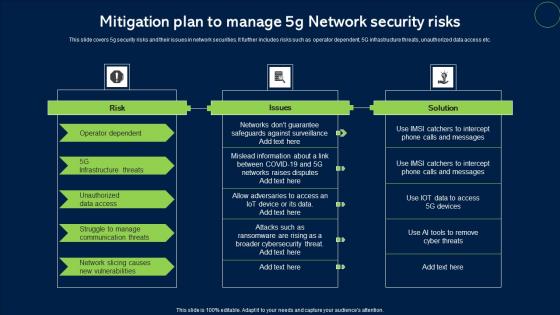
Mitigation Plan To Manage 5G Network Security Risks Microsoft Pdf
This slide covers 5g security risks and their issues in network securities. It further includes risks such as operator dependent, 5G infrastructure threats, unauthorized data access etc. Showcasing this set of slides titled Mitigation Plan To Manage 5G Network Security Risks Microsoft Pdf. The topics addressed in these templates are Risk, Issues, Solution. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide covers 5g security risks and their issues in network securities. It further includes risks such as operator dependent, 5G infrastructure threats, unauthorized data access etc.
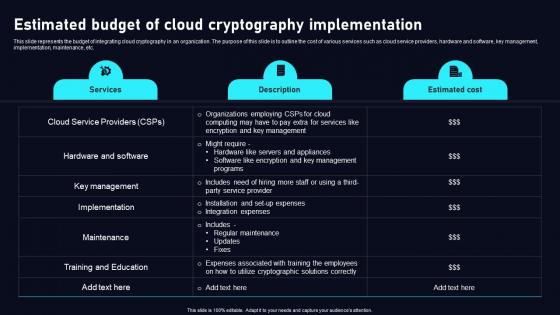
Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. This Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc.

Tokenization Strategies For Data Security Powerpoint Presentation Slides
This Tokenization Strategies For Data Security Powerpoint Presentation Slides is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready-made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This eighty three slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now. Our Tokenization Strategies For Data Security Powerpoint Presentation Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Breach Events Tracking Dashboard Data Fortification Strengthening Defenses
This slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks.Create an editable Security Breach Events Tracking Dashboard Data Fortification Strengthening Defenses that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Security Breach Events Tracking Dashboard Data Fortification Strengthening Defenses is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks.
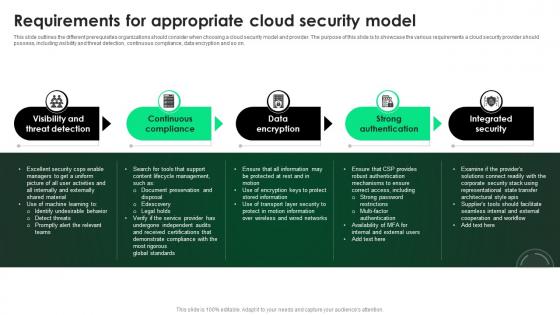
CASB 2 0 IT Requirements For Appropriate Cloud Security Model
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Find highly impressive CASB 2 0 IT Requirements For Appropriate Cloud Security Model on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download CASB 2 0 IT Requirements For Appropriate Cloud Security Model for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on.
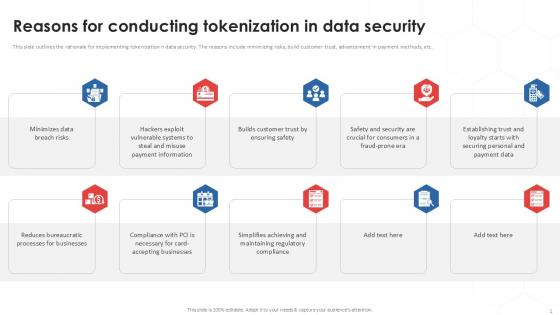
Reasons For Conducting Tokenization In Data Security PPT Template
This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc. Boost your pitch with our creative Reasons For Conducting Tokenization In Data Security PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc.

Best Practices For Tokenization In Data Security PPT Slides
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. Boost your pitch with our creative Best Practices For Tokenization In Data Security PPT Slides. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc.

Challenges And Related Tokenization Strategies For Data Security PPT Sample
This slide outlines the issues faced by utility tokens in data security. The purpose of this slide is to showcase utility token challenges which include absence of inherent mechanism, inadequate promotion, etc. Boost your pitch with our creative Challenges And Related Tokenization Strategies For Data Security PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the issues faced by utility tokens in data security. The purpose of this slide is to showcase utility token challenges which include absence of inherent mechanism, inadequate promotion, etc.
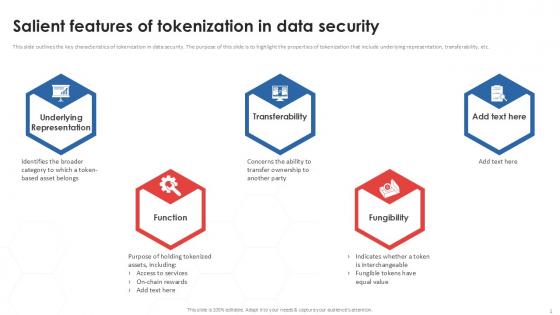
Salient Features Of Tokenization In Data Security PPT Sample
This slide outlines the key characteristics of tokenization in data security. The purpose of this slide is to highlight the properties of tokenization that include underlying representation, transferability, etc. Boost your pitch with our creative Salient Features Of Tokenization In Data Security PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the key characteristics of tokenization in data security. The purpose of this slide is to highlight the properties of tokenization that include underlying representation, transferability, etc.
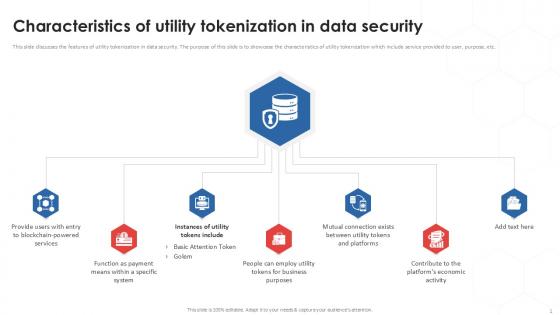
Characteristics Of Utility Tokenization In Data Security PPT Sample
This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. Find a pre-designed and impeccable Characteristics Of Utility Tokenization In Data Security PPT Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc.

CASB 2 0 IT Cloud Access Security Broker Pillar Overview
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Are you searching for a CASB 2 0 IT Cloud Access Security Broker Pillar Overview that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CASB 2 0 IT Cloud Access Security Broker Pillar Overview from Slidegeeks today. This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security.
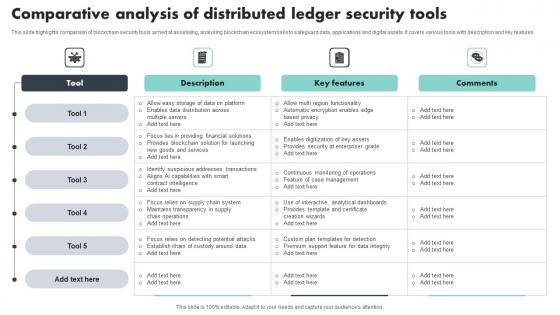
Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf
This slide highlights comparison of blockchain security tools aimed at assessing, analysing blockchain ecosystem risks to safeguard data, applications and digital assets. It covers various tools with description and key features Showcasing this set of slides titled Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf The topics addressed in these templates are Key Features, Comparative Analysis, Security Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights comparison of blockchain security tools aimed at assessing, analysing blockchain ecosystem risks to safeguard data, applications and digital assets. It covers various tools with description and key features
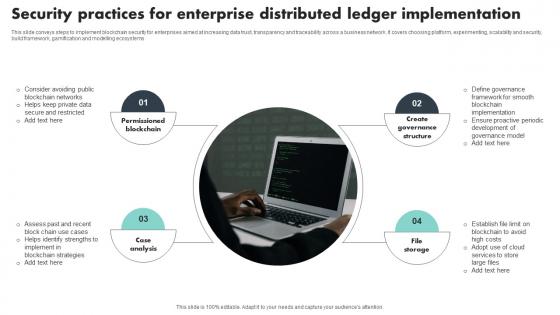
Security Practices For Enterprise Distributed Ledger Implementation Template Pdf
This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems Showcasing this set of slides titled Security Practices For Enterprise Distributed Ledger Implementation Template Pdf The topics addressed in these templates are Permissioned Blockchain, Case Analysis, Create Governance Structure All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems
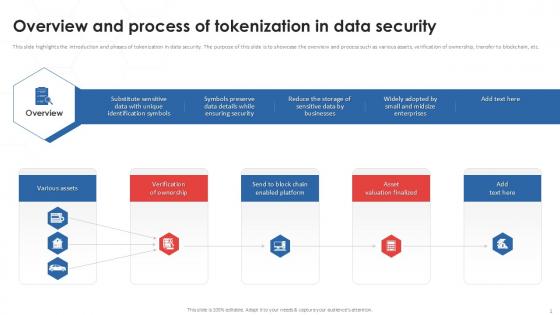
Overview And Process Of Tokenization In Data Security PPT Example
This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Find a pre-designed and impeccable Overview And Process Of Tokenization In Data Security PPT Example. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc.
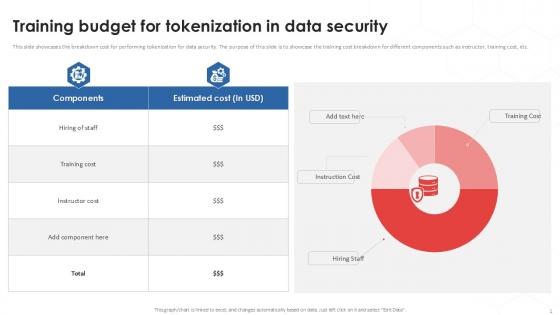
Training Budget For Tokenization In Data Security PPT Template
This slide showcases the breakdown cost for performing tokenization for data security. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor, training cost, etc. Find a pre-designed and impeccable Training Budget For Tokenization In Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide showcases the breakdown cost for performing tokenization for data security. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor, training cost, etc.

It Security Training Courses Strategic Agenda To Employees Portrait Pdf
This slide represents action plan for various training courses. It includes training courses such as complete cyber security courses, etc and their description, mode, duration, and budget. Showcasing this set of slides titled It Security Training Courses Strategic Agenda To Employees Portrait Pdf. The topics addressed in these templates are Training Courses, Description, Trainer Name. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan for various training courses. It includes training courses such as complete cyber security courses, etc and their description, mode, duration, and budget.
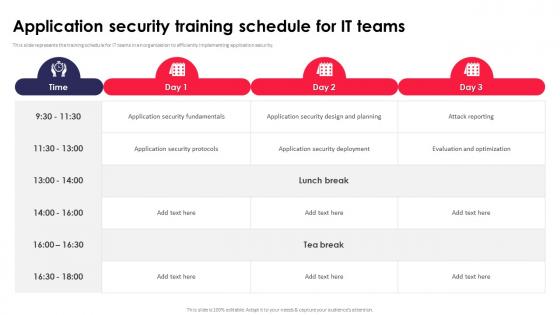
Application Security Training Schedule For IT Teams Ppt Powerpoint Portrait
This slide represents the training schedule for IT teams in an organization to efficiently implementing application security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Application Security Training Schedule For IT Teams Ppt Powerpoint Portrait will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the training schedule for IT teams in an organization to efficiently implementing application security.
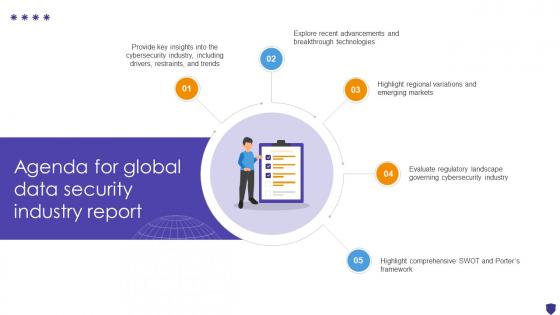
Agenda For Global Data Security Industry Report IR SS V
Find a pre-designed and impeccable Agenda For Global Data Security Industry Report IR SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda For Global Data Security Industry Report IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
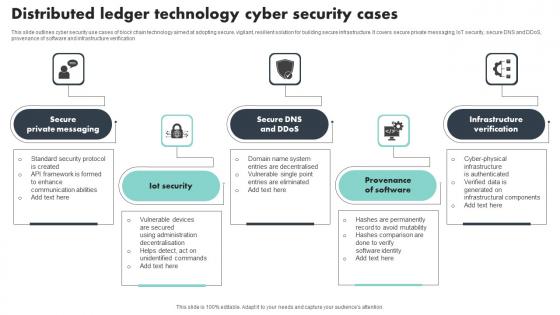
Distributed Ledger Technology Cyber Security Cases Brochure Pdf
This slide outlines cyber security use cases of block chain technology aimed at adopting secure, vigilant, resilient solution for building secure infrastructure. It covers secure private messaging, IoT security, secure DNS and DDoS, provenance of software and infrastructure verification Showcasing this set of slides titled Distributed Ledger Technology Cyber Security Cases Brochure Pdf The topics addressed in these templates are Private Messaging, Provenance Of Software, Infrastructure Verification All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide outlines cyber security use cases of block chain technology aimed at adopting secure, vigilant, resilient solution for building secure infrastructure. It covers secure private messaging, IoT security, secure DNS and DDoS, provenance of software and infrastructure verification

Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.

Web Consulting Business Website Security Management Action Plan
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc. The Web Consulting Business Website Security Management Action Plan is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc.
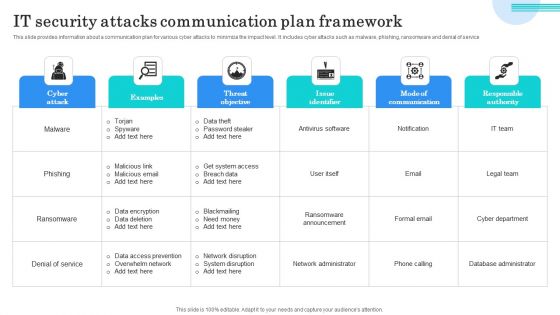
IT Security Attacks Communication Plan Framework Graphics PDF
This slide provides information about a communication plan for various cyber attacks to minimize the impact level. It includes cyber attacks such as malware, phishing, ransomware and denial of service. Showcasing this set of slides titled IT Security Attacks Communication Plan Framework Graphics PDF. The topics addressed in these templates are Data Theft, Password Stealer, Get System Access. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
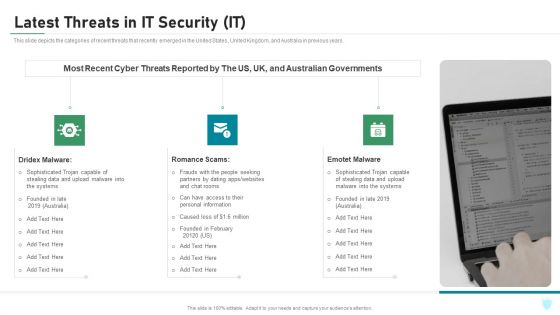
Latest Threats In IT Security IT Ppt Gallery Elements PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting latest threats in it security it ppt gallery elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dridex malware, romance scams, emotet malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf
The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management.

Internet Security Challenges And Solutions In Banking Industry Download Pdf
This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.Showcasing this set of slides titled Internet Security Challenges And Solutions In Banking Industry Download Pdf The topics addressed in these templates are Installing Intergraded, Introducing Firewall, Learning Algorisms All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.

Desktop Security Management Assessment Matrix Of Cyber Risks Infographics PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Presenting desktop security management assessment matrix of cyber risks infographics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like retail, systems, systems, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Cloud Security Firewall Proposal
Take your presentations to the next level with our Table Of Contents For Cloud Security Firewall Proposal template. With its sleek design and seamless editing features, this single-slide PPT template is a game-changer for professionals who want to make an impact. Impress your audience with stunning visuals and engaging content that will capture their attention from start to finish. Get your hands on our template and elevate your presentations to new heights. Our Table Of Contents For Cloud Security Firewall Proposal are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
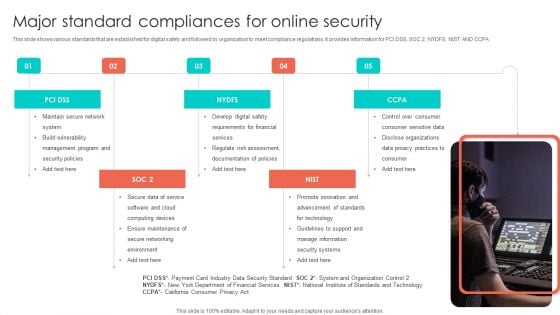
Major Standard Compliances For Online Security Pictures PDF
This slide shows various standards that are established for digital safety and followed by organization to meet compliance regulations. It provides information for PCI DSS, SOC 2, NYDFS, NIST AND CCPA. Persuade your audience using this Major Standard Compliances For Online Security Pictures PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Develop Digital Safety, Requirements For Financial, Regulate Risk Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

CYBER Security Breache Response Strategy Ppt PowerPoint Presentation Complete Deck
Whether it is for your individual use or business purpose, providing information in a clear format is often an added advantage, as this CYBER Security Breache Response Strategy Ppt PowerPoint Presentation Complete Deck does so wonderfully well. Incorporate this content-ready, versatile PowerPoint complete deck in sixty eight slides to significantly enhance your chances of success. It will help you talk about multiple components of business and be more efficient. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now.
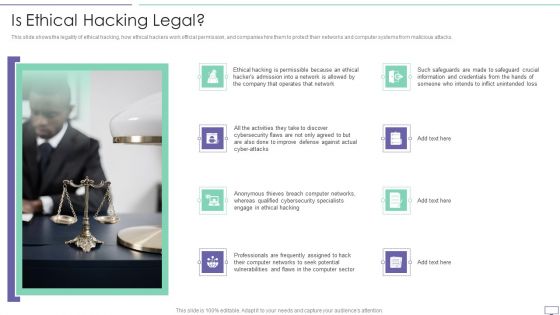
IT Security Hacker Is Ethical Hacking Legal Rules PDF
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks.Presenting IT Security Hacker Is Ethical Hacking Legal Rules PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Improve Defense, Anonymous Thieves, Qualified Cybersecurity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
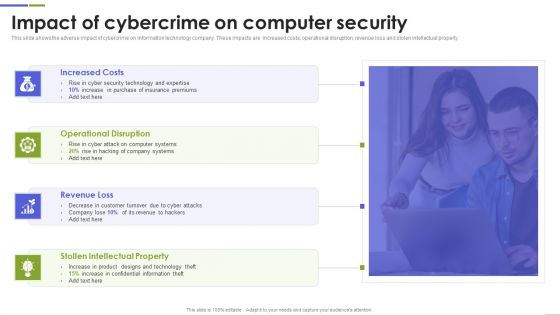
Impact Of Cybercrime On Computer Security Formats PDF
This slide shows the adverse impact of cybercrime on information technology company. These impacts are increased costs, operational disruption, revenue loss and stolen intellectual property. Persuade your audience using this Impact Of Cybercrime On Computer Security Formats PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Increased Costs, Operational Disruption, Revenue Loss Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents For Zero Trust Network Security Introduction Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Table Of Contents For Zero Trust Network Security Introduction Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. Our Table Of Contents For Zero Trust Network Security Introduction Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Case Study 2 Banks Cyber Security Infrastructure Topics PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges Presenting case study 2 banks cyber security infrastructure topics pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like implemented, integrated, our approach. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Checklist For Online Security Threat And Risk Assessment Designs PDF
This slide represents digital safety threat and assessment checklist which ensure risk management in cost effective manner. It provides information regarding conducting assessment, perform threat analysis, risk mitigation and process completion. Showcasing this set of slides titled Checklist For Online Security Threat And Risk Assessment Designs PDF. The topics addressed in these templates are Perform Threat Analysis, Conduct Assessment, Risk Mitigation And Recommendations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
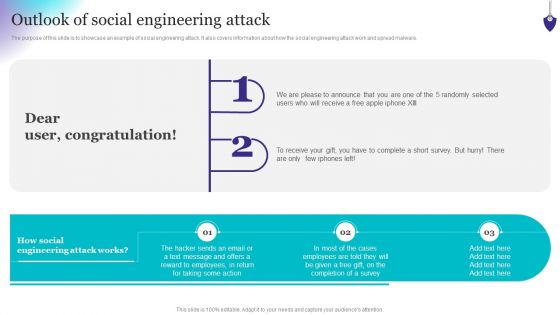
Organizing Security Awareness Outlook Of Social Engineering Attack Ideas PDF
The purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Slidegeeks has constructed Organizing Security Awareness Outlook Of Social Engineering Attack Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide
This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc. Find highly impressive Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Cryptography Challenges Data Security In Cloud Computing Ppt Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the key challenges of implementing cryptographic techniques in cloud computing. The purpose of this slide is to outline the solutions to such problems. These include key management complexity, multi-tenancy, cloud provider vulnerability, etc.
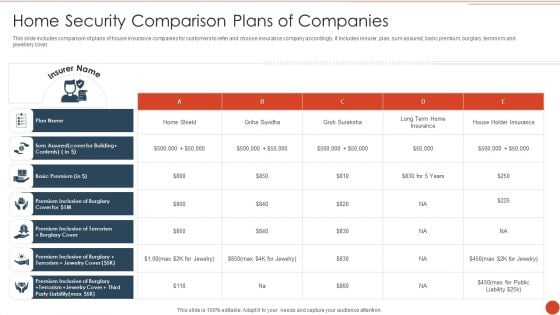
Home Security Comparison Plans Of Companies Formats PDF
This slide includes comparison of plans of house insurance companies for customers to refer and choose insurance company accordingly. It includes insurer, plan, sum assured, basic premium, burglary, terrorism and jewellery cover. Pitch your topic with ease and precision using this Home Security Comparison Plans Of Companies Formats PDF. This layout presents information on Basic Premium, Plan Name, House Holder Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.


 Continue with Email
Continue with Email

 Home
Home


































